Analysis of Security and Privacy Issues in Cloud Computing Systems
VerifiedAdded on 2020/03/23
|10
|2358
|36
Report
AI Summary
This report provides a detailed analysis of security and privacy issues within cloud computing environments. It begins with an introduction to cloud computing and explores various service models (IaaS, PaaS, and SaaS) and deployment models. The core of the report focuses on the significant challenges, including data privacy concerns, compliance issues with international laws, risks associated with data deletion and portability, lack of common cloud standards, data segregation vulnerabilities, data breaches, and network security threats. The report emphasizes the importance of addressing these issues for the widespread adoption of cloud computing, highlighting how technological giants are working to resolve them. It concludes that while cloud computing offers substantial financial benefits, addressing security and compliance is crucial for its continued growth. The report also includes references to relevant research papers and articles.

Running Head: SECURITY AND PRIVACY ISSUES IN CLOUD COMPUTING
Security and privacy issues in Cloud Computing
Student’s name
Name of the Institute
Security and privacy issues in Cloud Computing
Student’s name
Name of the Institute
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

SECURITY AND PRIVACY ISSUES IN CLOUD COMPUTING
Contents
1 Introduction to Cloud Computing..........................................................................................................3
2 Cloud Computing service Models and Deployment Models.................................................................4
2.1 Service & Deployment Models......................................................................................................4
3 Security and privacy issues in Cloud computing...................................................................................5
4 Conclusion............................................................................................................................................8
References...................................................................................................................................................9
Contents
1 Introduction to Cloud Computing..........................................................................................................3
2 Cloud Computing service Models and Deployment Models.................................................................4
2.1 Service & Deployment Models......................................................................................................4
3 Security and privacy issues in Cloud computing...................................................................................5
4 Conclusion............................................................................................................................................8
References...................................................................................................................................................9

SECURITY AND PRIVACY ISSUES IN CLOUD COMPUTING
1 Introduction to Cloud Computing
This is the age of digitalization and disruption where new technology is constantly retiring
and replacing the old technology as well as new emerging business and delivery models are
replacing the traditional models. These new models are much more elastic, scalable as well as
cost efficient. Cloud computing is also one such promising delivery model where data and
programs will be stored on a remote machine and will be accessed using internet while
traditionally organization has to buy and maintain the entire infrastructure in-house and maintain
data as well as programs in-house. As a result, there are many benefits in terms of cost savings as
the organization is not maintaining the infrastructure however there are challenges and benefits
also in adopting the cloud computing. This is the reason that although Cloud has been there since
more than a decade, it is still far from mainstream adoption due to various security and privacy
and other open ended issues.
Also, most of the big companies and technological giants like Google, Amazon, IBM,
Microsoft, Oracle, EMC and many other players like Salesforce.com are counting heavily on this
technology and bringing most of the products developed on cloud. The purpose of this report is
to deeply analyze the security and privacy issues that are delaying the widespread adoption of the
Cloud computing. This will also discusses various service models and deployment models
associated with the cloud very briefly however it will not talk about the benefits of cloud
computing as there is already large number of reports on the same. It is expected that cloud
computing would continue to be a key technology trend that would shape the use of Information
Technology for large and small organizations.
1 Introduction to Cloud Computing
This is the age of digitalization and disruption where new technology is constantly retiring
and replacing the old technology as well as new emerging business and delivery models are
replacing the traditional models. These new models are much more elastic, scalable as well as
cost efficient. Cloud computing is also one such promising delivery model where data and
programs will be stored on a remote machine and will be accessed using internet while
traditionally organization has to buy and maintain the entire infrastructure in-house and maintain
data as well as programs in-house. As a result, there are many benefits in terms of cost savings as
the organization is not maintaining the infrastructure however there are challenges and benefits
also in adopting the cloud computing. This is the reason that although Cloud has been there since
more than a decade, it is still far from mainstream adoption due to various security and privacy
and other open ended issues.
Also, most of the big companies and technological giants like Google, Amazon, IBM,
Microsoft, Oracle, EMC and many other players like Salesforce.com are counting heavily on this
technology and bringing most of the products developed on cloud. The purpose of this report is
to deeply analyze the security and privacy issues that are delaying the widespread adoption of the
Cloud computing. This will also discusses various service models and deployment models
associated with the cloud very briefly however it will not talk about the benefits of cloud
computing as there is already large number of reports on the same. It is expected that cloud
computing would continue to be a key technology trend that would shape the use of Information
Technology for large and small organizations.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

SECURITY AND PRIVACY ISSUES IN CLOUD COMPUTING
2 Cloud Computing service Models and Deployment Models
There are different service and deployment models for cloud installation. The widely used
service and deployment models for cloud computing can be discussed as:
2.1 Service & Deployment Models
There are three service models in Cloud computing based on the level abstraction and
resourced vendor provide. They are as follows:
2.1.2 IAAS (Infrastructure-as-a-Service) - In this service model, Cloud Service Provider (CSP)
will provide the network, storage and processing capability to the customers. Customer can
select their own applications and middleware, operating systems and can deploy them on IAAS.
2.1.2 PAAS (Platform-as-a-Service) – In this service model, CSP will provide the middleware,
programming languages, operating systems needed to build the applications. Also, customers do
not have the choice for using separate storage. It should be what is supported by the PAAS.
However, customers have full liberty to deploy and run whatever application and software they
want to run (Puthal & Sahoo, 2015).
2.1.3 SAAS (Software-as-a-Service) – In this service model, CSP will provide the application to
the customer. Salesforce.com is a very popular example of this. Apart from it, Microsoft outlook,
Gmail are also examples of SAAS. In this vendor will manage the underlying systems like IAAS
and PAAS and customers can access the application using the Internet. It is an alternative to
local application.
Across the industry, there are various vendors that provide cloud services. Below are the
popular vendors or Cloud Service Providers.
2 Cloud Computing service Models and Deployment Models
There are different service and deployment models for cloud installation. The widely used
service and deployment models for cloud computing can be discussed as:
2.1 Service & Deployment Models
There are three service models in Cloud computing based on the level abstraction and
resourced vendor provide. They are as follows:
2.1.2 IAAS (Infrastructure-as-a-Service) - In this service model, Cloud Service Provider (CSP)
will provide the network, storage and processing capability to the customers. Customer can
select their own applications and middleware, operating systems and can deploy them on IAAS.
2.1.2 PAAS (Platform-as-a-Service) – In this service model, CSP will provide the middleware,
programming languages, operating systems needed to build the applications. Also, customers do
not have the choice for using separate storage. It should be what is supported by the PAAS.
However, customers have full liberty to deploy and run whatever application and software they
want to run (Puthal & Sahoo, 2015).
2.1.3 SAAS (Software-as-a-Service) – In this service model, CSP will provide the application to
the customer. Salesforce.com is a very popular example of this. Apart from it, Microsoft outlook,
Gmail are also examples of SAAS. In this vendor will manage the underlying systems like IAAS
and PAAS and customers can access the application using the Internet. It is an alternative to
local application.
Across the industry, there are various vendors that provide cloud services. Below are the
popular vendors or Cloud Service Providers.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
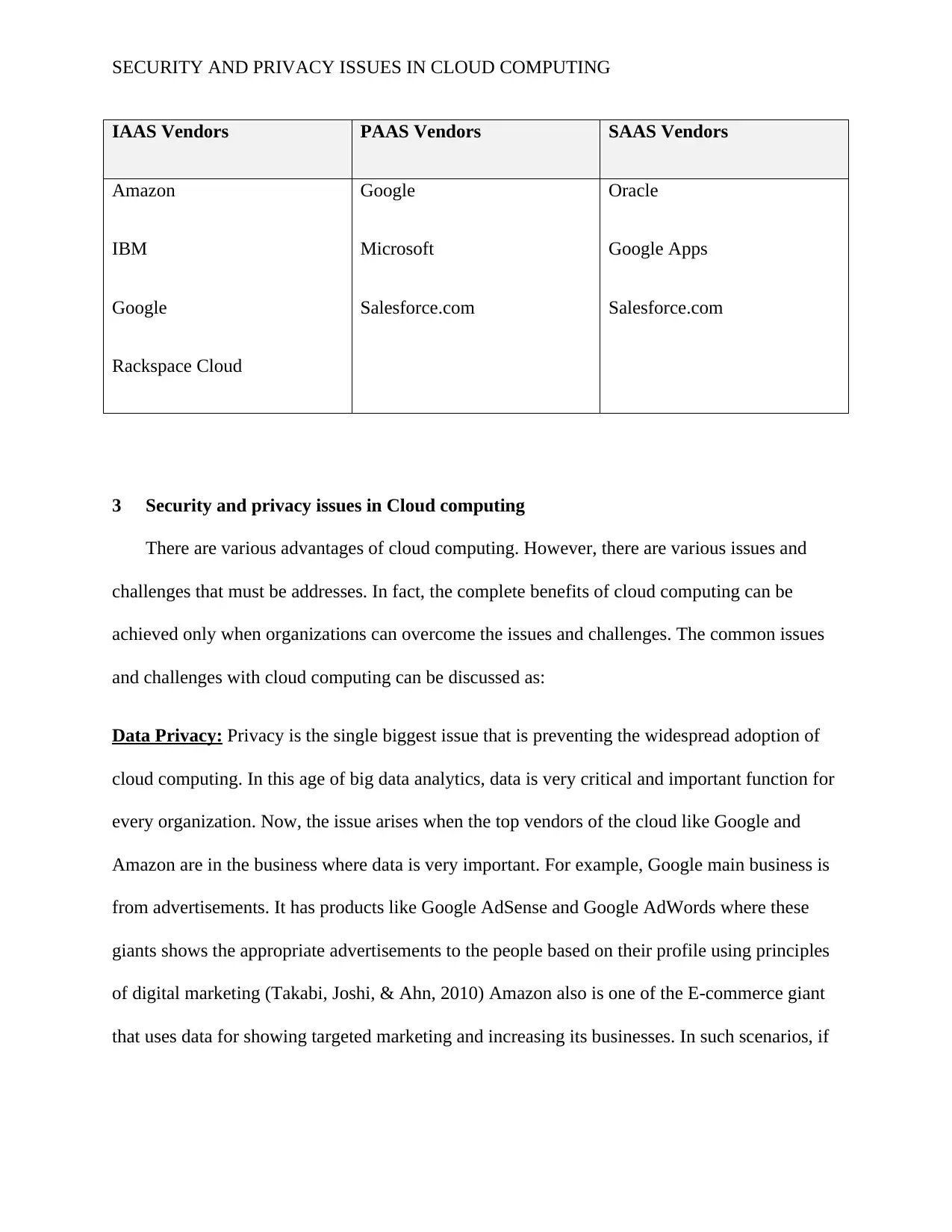
SECURITY AND PRIVACY ISSUES IN CLOUD COMPUTING
IAAS Vendors PAAS Vendors SAAS Vendors
Amazon
IBM
Google
Rackspace Cloud
Google
Microsoft
Salesforce.com
Oracle
Google Apps
Salesforce.com
3 Security and privacy issues in Cloud computing
There are various advantages of cloud computing. However, there are various issues and
challenges that must be addresses. In fact, the complete benefits of cloud computing can be
achieved only when organizations can overcome the issues and challenges. The common issues
and challenges with cloud computing can be discussed as:
Data Privacy: Privacy is the single biggest issue that is preventing the widespread adoption of
cloud computing. In this age of big data analytics, data is very critical and important function for
every organization. Now, the issue arises when the top vendors of the cloud like Google and
Amazon are in the business where data is very important. For example, Google main business is
from advertisements. It has products like Google AdSense and Google AdWords where these
giants shows the appropriate advertisements to the people based on their profile using principles
of digital marketing (Takabi, Joshi, & Ahn, 2010) Amazon also is one of the E-commerce giant
that uses data for showing targeted marketing and increasing its businesses. In such scenarios, if
IAAS Vendors PAAS Vendors SAAS Vendors
Amazon
IBM
Rackspace Cloud
Microsoft
Salesforce.com
Oracle
Google Apps
Salesforce.com
3 Security and privacy issues in Cloud computing
There are various advantages of cloud computing. However, there are various issues and
challenges that must be addresses. In fact, the complete benefits of cloud computing can be
achieved only when organizations can overcome the issues and challenges. The common issues
and challenges with cloud computing can be discussed as:
Data Privacy: Privacy is the single biggest issue that is preventing the widespread adoption of
cloud computing. In this age of big data analytics, data is very critical and important function for
every organization. Now, the issue arises when the top vendors of the cloud like Google and
Amazon are in the business where data is very important. For example, Google main business is
from advertisements. It has products like Google AdSense and Google AdWords where these
giants shows the appropriate advertisements to the people based on their profile using principles
of digital marketing (Takabi, Joshi, & Ahn, 2010) Amazon also is one of the E-commerce giant
that uses data for showing targeted marketing and increasing its businesses. In such scenarios, if

SECURITY AND PRIVACY ISSUES IN CLOUD COMPUTING
any customers are using the services of these vendors, there is a conflict of interest and there can
be a risk to confidential customer data.
Data compliance issue: There are numerous issues related to compliance using cloud
computing. Each nation has their own laws, rules and policies related to how the organizations
can store the data. For example, there is a government rule of European Union (EU) Data
Privacy Directive that prevents that data of the country members to be stored outside the country.
Now, in cloud computing, there are various copies maintains at various locations of the world
and thus this type of compliance will make it impossible for the organization to use cloud
computing (Amorsy, Grunday, & Muller, 2016). Cloud vendors needs to be more transparent and
must tell the customers where they are storing the data and how many copies they are
maintaining.
Data deletion risks: Data portability and data deletion has been one of the main challenges of
cloud computing which is quite under researched. There are no solutions and workarounds to
handle this and as a result of this vendors are not quite transparent about (Rittinghouse, &
Ransome, 2016). For instance, consider a scenario where 1 customer is maintaining their data
with one of the cloud service provide. Now, due to some issue or requirement, customer decided
to use the in-house application or switch to a different Cloud service provider, it is difficult to
ensure that the cloud vendor has removed all customer data from the cloud. It is because usually
the cloud stores data in a complex mesh of interrelated data and also maintain numerous copies
in form of backups that are located across the world (Theoharidou etal., 2013). As long as it is
private cloud, Vendor can reset or flush the complete data but how it will be handled in case of a
community cloud. Also, if customers want to delete some data, how it will ensure that it is
permanently removed from all the clouds.
any customers are using the services of these vendors, there is a conflict of interest and there can
be a risk to confidential customer data.
Data compliance issue: There are numerous issues related to compliance using cloud
computing. Each nation has their own laws, rules and policies related to how the organizations
can store the data. For example, there is a government rule of European Union (EU) Data
Privacy Directive that prevents that data of the country members to be stored outside the country.
Now, in cloud computing, there are various copies maintains at various locations of the world
and thus this type of compliance will make it impossible for the organization to use cloud
computing (Amorsy, Grunday, & Muller, 2016). Cloud vendors needs to be more transparent and
must tell the customers where they are storing the data and how many copies they are
maintaining.
Data deletion risks: Data portability and data deletion has been one of the main challenges of
cloud computing which is quite under researched. There are no solutions and workarounds to
handle this and as a result of this vendors are not quite transparent about (Rittinghouse, &
Ransome, 2016). For instance, consider a scenario where 1 customer is maintaining their data
with one of the cloud service provide. Now, due to some issue or requirement, customer decided
to use the in-house application or switch to a different Cloud service provider, it is difficult to
ensure that the cloud vendor has removed all customer data from the cloud. It is because usually
the cloud stores data in a complex mesh of interrelated data and also maintain numerous copies
in form of backups that are located across the world (Theoharidou etal., 2013). As long as it is
private cloud, Vendor can reset or flush the complete data but how it will be handled in case of a
community cloud. Also, if customers want to delete some data, how it will ensure that it is
permanently removed from all the clouds.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

SECURITY AND PRIVACY ISSUES IN CLOUD COMPUTING
No Common Cloud Standards: Currently, there is poor interoperability between clouds
maintained by different vendors due to lack of common standards. This lack of interoperability
has makes the migration from 1 cloud to another cloud very difficult and depending on the single
cloud vendor will simple increases the risk for the customers (Latif, et al., 2014). Customers will
prefer to distribute their data over the clouds managed by various provides in order to minimize
the risk but this is not possible. Apart from this, there is another issue of compatibility. Amazon
and Microsoft are mainly the IAAS providers which provides the storage and computing services
however the reason most of the organization are looking for cloud is the SAAS (software-as-a-
service). Now, if you run the software on the IAAS owned by the amazon and there are some
issues, you will be permanently lost in what is creating the issue and also integrations will also
be needed. Amazon is quite good for those cases where client is planning to build and deploy
their own custom applications but not well in a situation where customers wants to use 3rd party
software. Oracle and Salesforce.com are two such vendors that own and provides entire cloud
stack that is IAAS, PAAS and SAAS (Ali & Khan, 2015). However, other vendors also need to
work in this space.
Data Segregation: software multitenancy is the major feature of the cloud computing where a
single instance of software will be used to serves the multiple tenants. Thus, data of various users
will be storing at the same location, which makes the intrusion of a data of 1 user by another user
possible. This is the single biggest risk and thus SAAS should define and maintain clear
boundary for the data belonging to each user and thus boundary must be protected at physical as
well as application level (Toosi & Calheiros, 2014).
Data breaches: Clouds have the data from multiple people belonging to multiple countries.
Now, if any of the person or users of the cloud has been attacked by malware, there is a risk of
No Common Cloud Standards: Currently, there is poor interoperability between clouds
maintained by different vendors due to lack of common standards. This lack of interoperability
has makes the migration from 1 cloud to another cloud very difficult and depending on the single
cloud vendor will simple increases the risk for the customers (Latif, et al., 2014). Customers will
prefer to distribute their data over the clouds managed by various provides in order to minimize
the risk but this is not possible. Apart from this, there is another issue of compatibility. Amazon
and Microsoft are mainly the IAAS providers which provides the storage and computing services
however the reason most of the organization are looking for cloud is the SAAS (software-as-a-
service). Now, if you run the software on the IAAS owned by the amazon and there are some
issues, you will be permanently lost in what is creating the issue and also integrations will also
be needed. Amazon is quite good for those cases where client is planning to build and deploy
their own custom applications but not well in a situation where customers wants to use 3rd party
software. Oracle and Salesforce.com are two such vendors that own and provides entire cloud
stack that is IAAS, PAAS and SAAS (Ali & Khan, 2015). However, other vendors also need to
work in this space.
Data Segregation: software multitenancy is the major feature of the cloud computing where a
single instance of software will be used to serves the multiple tenants. Thus, data of various users
will be storing at the same location, which makes the intrusion of a data of 1 user by another user
possible. This is the single biggest risk and thus SAAS should define and maintain clear
boundary for the data belonging to each user and thus boundary must be protected at physical as
well as application level (Toosi & Calheiros, 2014).
Data breaches: Clouds have the data from multiple people belonging to multiple countries.
Now, if any of the person or users of the cloud has been attacked by malware, there is a risk of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

SECURITY AND PRIVACY ISSUES IN CLOUD COMPUTING
malware entering into a complete cloud and can impact the data of all the other organizations. In
such cases, organization are arguing that they are giving training to their users not to click on any
phishing mail but what if someone who do not belong to their organization has clicked on such
emails and the impact is compromise of their data (Mouratidis, et al., 2014).
Network security: In a community cloud, there are large number of organizations that will
interact with their own partners, customer and suppliers. As a result, there will be flow of
sensitive data over network and thus it needs to be protected to avoid the seepage of confidential
data and sensitive information. This involves the use of strong encryption techniques like SSL
for security purposes (Sanaei & Abolfazli, 2014).
4 Conclusion
No doubt cloud is a flavor of today as it provides lot of financial benefits to the organization
however there are still many open issues and questions that must be answered before it will be
adopted widespread. With Globalization, as the organizations are increasing beyond their
boundaries, maintain on premise IT systems for every site will be quite expensive for them and
cloud scalability is perfect solution for them but security, audit, compliance related issues of
cloud computing has delayed the speed of its adoption. This report discusses about the key
privacy and compliance issues that are associated with the cloud computing. And as most of the
technological giants like IBM, Microsoft, Oracle, Amazon, Google are working in this area, the
open items will probably be solved in coming times leading to a cloud revolution.
malware entering into a complete cloud and can impact the data of all the other organizations. In
such cases, organization are arguing that they are giving training to their users not to click on any
phishing mail but what if someone who do not belong to their organization has clicked on such
emails and the impact is compromise of their data (Mouratidis, et al., 2014).
Network security: In a community cloud, there are large number of organizations that will
interact with their own partners, customer and suppliers. As a result, there will be flow of
sensitive data over network and thus it needs to be protected to avoid the seepage of confidential
data and sensitive information. This involves the use of strong encryption techniques like SSL
for security purposes (Sanaei & Abolfazli, 2014).
4 Conclusion
No doubt cloud is a flavor of today as it provides lot of financial benefits to the organization
however there are still many open issues and questions that must be answered before it will be
adopted widespread. With Globalization, as the organizations are increasing beyond their
boundaries, maintain on premise IT systems for every site will be quite expensive for them and
cloud scalability is perfect solution for them but security, audit, compliance related issues of
cloud computing has delayed the speed of its adoption. This report discusses about the key
privacy and compliance issues that are associated with the cloud computing. And as most of the
technological giants like IBM, Microsoft, Oracle, Amazon, Google are working in this area, the
open items will probably be solved in coming times leading to a cloud revolution.

SECURITY AND PRIVACY ISSUES IN CLOUD COMPUTING
References
Ali, M., Khan, S. U., & Vasilakos, A. V. (2015). Security in cloud computing: Opportunities and
challenges. Information Sciences, 305, 357-383.
Almorsy, M., Grundy, J., & Müller, I. (2016). An analysis of the cloud computing security
problem. arXiv preprint arXiv:1609.01107.
Latif, R., Abbas, H., Assar, S., & Ali, Q. (2014). Cloud computing risk assessment: a systematic
literature review. In Future Information Technology(pp. 285-295). Springer, Berlin,
Heidelberg.
Mouratidis, H., Islam, S., Kalloniatis, C., & Gritzalis, S. (2013). A framework to support
selection of cloud providers based on security and privacy requirements. Journal of Systems
and Software, 86(9), 2276-2293.
Puthal, D., Sahoo, B. P. S., Mishra, S., & Swain, S. (2015, January). Cloud computing features,
issues, and challenges: a big picture. In Computational Intelligence and Networks (CINE),
2015 International Conference on (pp. 116-123). IEEE.
Rittinghouse, J. W., & Ransome, J. F. (2016). Cloud computing: implementation, management,
and security. CRC press.
Sanaei, Z., Abolfazli, S., Gani, A., & Buyya, R. (2014). Heterogeneity in mobile cloud
computing: taxonomy and open challenges. IEEE Communications Surveys &
Tutorials, 16(1), 369-392.
References
Ali, M., Khan, S. U., & Vasilakos, A. V. (2015). Security in cloud computing: Opportunities and
challenges. Information Sciences, 305, 357-383.
Almorsy, M., Grundy, J., & Müller, I. (2016). An analysis of the cloud computing security
problem. arXiv preprint arXiv:1609.01107.
Latif, R., Abbas, H., Assar, S., & Ali, Q. (2014). Cloud computing risk assessment: a systematic
literature review. In Future Information Technology(pp. 285-295). Springer, Berlin,
Heidelberg.
Mouratidis, H., Islam, S., Kalloniatis, C., & Gritzalis, S. (2013). A framework to support
selection of cloud providers based on security and privacy requirements. Journal of Systems
and Software, 86(9), 2276-2293.
Puthal, D., Sahoo, B. P. S., Mishra, S., & Swain, S. (2015, January). Cloud computing features,
issues, and challenges: a big picture. In Computational Intelligence and Networks (CINE),
2015 International Conference on (pp. 116-123). IEEE.
Rittinghouse, J. W., & Ransome, J. F. (2016). Cloud computing: implementation, management,
and security. CRC press.
Sanaei, Z., Abolfazli, S., Gani, A., & Buyya, R. (2014). Heterogeneity in mobile cloud
computing: taxonomy and open challenges. IEEE Communications Surveys &
Tutorials, 16(1), 369-392.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

SECURITY AND PRIVACY ISSUES IN CLOUD COMPUTING
Takabi, H., Joshi, J. B., & Ahn, G. J. (2010). Security and privacy challenges in cloud computing
environments. IEEE Security & Privacy, 8(6), 24-31.
Theoharidou, M., Papanikolaou, N., Pearson, S., & Gritzalis, D. (2013, December). Privacy risk,
security, accountability in the cloud. In Cloud Computing Technology and Science
(CloudCom), 2013 IEEE 5th International Conference on (Vol. 1, pp. 177-184). IEEE.
Toosi, A. N., Calheiros, R. N., & Buyya, R. (2014). Interconnected cloud computing
environments: Challenges, taxonomy, and survey. ACM Computing Surveys (CSUR), 47(1),
7.
Takabi, H., Joshi, J. B., & Ahn, G. J. (2010). Security and privacy challenges in cloud computing
environments. IEEE Security & Privacy, 8(6), 24-31.
Theoharidou, M., Papanikolaou, N., Pearson, S., & Gritzalis, D. (2013, December). Privacy risk,
security, accountability in the cloud. In Cloud Computing Technology and Science
(CloudCom), 2013 IEEE 5th International Conference on (Vol. 1, pp. 177-184). IEEE.
Toosi, A. N., Calheiros, R. N., & Buyya, R. (2014). Interconnected cloud computing
environments: Challenges, taxonomy, and survey. ACM Computing Surveys (CSUR), 47(1),
7.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





