Analyzing Security, Privacy Issues & Solutions for Cloud in Finance
VerifiedAdded on 2023/06/10
|46
|14528
|272
Report
AI Summary
This research paper delves into the impact of cloud computing on the financial industry, highlighting both its benefits and the associated security and privacy challenges. It examines the influence of GDPR on cloud computing within the financial sector, particularly concerning data protection and the management of personal information of European citizens. The paper identifies key issues such as compliance risks, transparency of Cloud Service Providers (CSPs), and the need for clear regulatory guidance. Furthermore, it proposes potential solutions to current and future security and privacy concerns, including enhanced regulatory compliance and improved security schemes, emphasizing the importance of mitigating these risks to encourage wider adoption of cloud computing in financial organizations. The research aims to clarify the mitigation processes of security issues, thereby fostering greater trust in cloud computing for data management within the financial sector.

Running head: RESEARCH PAPER
Cloud Computing in Financial Sector: Current Security, Privacy Issues and
its Solutions
Name of Student-
Name of University-
Author’s Note-
Cloud Computing in Financial Sector: Current Security, Privacy Issues and
its Solutions
Name of Student-
Name of University-
Author’s Note-
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1RESEARCH PAPER
Copyright
The materials and the content of this research paper are subjected only for the academic
study and for personal use. This research papers is created to provide a detailed study for the next
generation. Accessing knowledge is human right and all humans will be able to get idea from
this research paper. There are exceptions as well as limitations that are attached to the copyright
to protect the public interest and also for dissemination of knowledge.
Copyright
The materials and the content of this research paper are subjected only for the academic
study and for personal use. This research papers is created to provide a detailed study for the next
generation. Accessing knowledge is human right and all humans will be able to get idea from
this research paper. There are exceptions as well as limitations that are attached to the copyright
to protect the public interest and also for dissemination of knowledge.

2RESEARCH PAPER
Acknowledgement
Thank you to all of those who have helped listened and encouraged me throughout this
study. I am indebted to my supervisor ......................... whose guidance, advice and patience has
been immeasurable. My sincere thanks to all members of the............... [Mention your
university/college name], both staff and students, whose continuous support have made this
thesis possible.
I would like to thank all of the participants in the study: students, teachers and Local
Education Authorities, for the time and help given throughout. Without their participation, this
research would not have been possible. In this context, I am also thankful to them, whose
research work helped me to execute this paper well.
Finally, I thank my family, without whom this thesis would not have been started or
completed! Your encouragement and support has never faltered; thank you.
Acknowledgement
Thank you to all of those who have helped listened and encouraged me throughout this
study. I am indebted to my supervisor ......................... whose guidance, advice and patience has
been immeasurable. My sincere thanks to all members of the............... [Mention your
university/college name], both staff and students, whose continuous support have made this
thesis possible.
I would like to thank all of the participants in the study: students, teachers and Local
Education Authorities, for the time and help given throughout. Without their participation, this
research would not have been possible. In this context, I am also thankful to them, whose
research work helped me to execute this paper well.
Finally, I thank my family, without whom this thesis would not have been started or
completed! Your encouragement and support has never faltered; thank you.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3RESEARCH PAPER
Abstract
Cloud computing is one such type of artificial intelligence that mainly helps the companies in
many sectors including the banking sector or financial sectors, who mainly deals with data and
aims to keeping the data storage safe from any intruder. Cloud computing provides a high degree
of regulation in the financial sector. The concept of cloud computing is mainly a rapid
developing technology that has mostly gained traction in the recent years. The cloud is mainly an
enabler of many other technologies that includes big data, Internet of Things, artificial
intelligence and many other technologies. The main service that the cloud computing provides
mainly concern with interoperability, security of storage and provides service to their customers
irrespective of time and place. The cloud computing enables wider scale as well as utilization of
the IT resources as some shared services in an organization. In financial industries, the
information technology is considered as the most essential factor in solving the issues. The issues
that are related with the cloud computing are addressed in this research paper along with the
mitigation processes. This research paper also deals with the importance of GDPR of cloud
computing the in the financial sectors. This research paper clearly solves all the issues related to
cloud computing that are faced in the financial sectors.
Abstract
Cloud computing is one such type of artificial intelligence that mainly helps the companies in
many sectors including the banking sector or financial sectors, who mainly deals with data and
aims to keeping the data storage safe from any intruder. Cloud computing provides a high degree
of regulation in the financial sector. The concept of cloud computing is mainly a rapid
developing technology that has mostly gained traction in the recent years. The cloud is mainly an
enabler of many other technologies that includes big data, Internet of Things, artificial
intelligence and many other technologies. The main service that the cloud computing provides
mainly concern with interoperability, security of storage and provides service to their customers
irrespective of time and place. The cloud computing enables wider scale as well as utilization of
the IT resources as some shared services in an organization. In financial industries, the
information technology is considered as the most essential factor in solving the issues. The issues
that are related with the cloud computing are addressed in this research paper along with the
mitigation processes. This research paper also deals with the importance of GDPR of cloud
computing the in the financial sectors. This research paper clearly solves all the issues related to
cloud computing that are faced in the financial sectors.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4RESEARCH PAPER
Table of Contents
1. Introduction..................................................................................................................................5
1.1 Background of the study........................................................................................................5
1.2 Aims and Objectives..............................................................................................................9
1.3 Research Questions..............................................................................................................10
2. Literature Review......................................................................................................................10
2.1 GDPR (General Data Protection Regulation)......................................................................15
2.2 Impact of GDPR on Cloud Computing in Financial Sector................................................16
2.3 Impact of GDPR on Security Issue and Privacy issues of Cloud Computing in Financial
Sector.........................................................................................................................................17
2.4 Future security and privacy issues of Cloud Computing in Financial Sector......................18
3. Methodology and Approach......................................................................................................22
4. Result and Discussion................................................................................................................26
5. Analysis and Conclusion...........................................................................................................37
References......................................................................................................................................45
Table of Contents
1. Introduction..................................................................................................................................5
1.1 Background of the study........................................................................................................5
1.2 Aims and Objectives..............................................................................................................9
1.3 Research Questions..............................................................................................................10
2. Literature Review......................................................................................................................10
2.1 GDPR (General Data Protection Regulation)......................................................................15
2.2 Impact of GDPR on Cloud Computing in Financial Sector................................................16
2.3 Impact of GDPR on Security Issue and Privacy issues of Cloud Computing in Financial
Sector.........................................................................................................................................17
2.4 Future security and privacy issues of Cloud Computing in Financial Sector......................18
3. Methodology and Approach......................................................................................................22
4. Result and Discussion................................................................................................................26
5. Analysis and Conclusion...........................................................................................................37
References......................................................................................................................................45

5RESEARCH PAPER
1. Introduction
1.1 Background of the study
According to the data privacy rules of Europe, the GDPR (General Data Protection
Regulation) has already been in use from 25th May, 2018. After implementing the GDPR in
Europe, many data privacy rules are been introduced in the financial sector of Europe. The
concept of GDPR regulates the European organizations which uses as well as possesses all
personal pertaining of data to all the citizens living in Europe. The data pertaining takes place
regardless the place of data that has taken place (Qiu et al. 2018). There are many new
regulations that will be implemented in many companies as well as organizations in the financial
sectors so that they can compete the development as well as using the artificial intelligence.
Artificial intelligence includes some set of processes or technologies which mainly allows the
computers to perform the tasks similar like human beings. Cloud computing is one such type of
artificial intelligence that mainly helps the companies in many sectors including the banking
sector or financial sectors, who mainly deals with data and aims to keeping the data storage safe
from any intruder. This cloud computing helps to increase the productivity by increasing the
efficiency of the processes and making their services as a high quality of outputs. Many artificial
intelligence does not have involvement of personal data (Li et al. 2017). The consumers who
mainly interacts with the service of artificial intelligence such as cloud computing, personal
assistants, robo-advisors who will instruct the financial advice, provides recommendations for
the streaming services will get affected. Every established companies in Europe deals with
personal data that includes payroll and uses the advantages of artificial intelligence for
management of such data. The way to use the personal data on the European citizens are being
limited now and raising legal risks for the companies are active for the artificial intelligence. The
GDPR deals with data protection and will impact negatively on the development and the use of
the artificial intelligence by the companies of Europe in financial sectors.
Cloud computing has the power to change the business opportunities as well as business
demands. Cloud computing helps a business to become more agile and scale all their resources
with elasticity and speed (Hashem et al. 2015). For all the business leaders, the cloud computing
enables the LOB (Lines of Business) to provision the computing resources and applications to
1. Introduction
1.1 Background of the study
According to the data privacy rules of Europe, the GDPR (General Data Protection
Regulation) has already been in use from 25th May, 2018. After implementing the GDPR in
Europe, many data privacy rules are been introduced in the financial sector of Europe. The
concept of GDPR regulates the European organizations which uses as well as possesses all
personal pertaining of data to all the citizens living in Europe. The data pertaining takes place
regardless the place of data that has taken place (Qiu et al. 2018). There are many new
regulations that will be implemented in many companies as well as organizations in the financial
sectors so that they can compete the development as well as using the artificial intelligence.
Artificial intelligence includes some set of processes or technologies which mainly allows the
computers to perform the tasks similar like human beings. Cloud computing is one such type of
artificial intelligence that mainly helps the companies in many sectors including the banking
sector or financial sectors, who mainly deals with data and aims to keeping the data storage safe
from any intruder. This cloud computing helps to increase the productivity by increasing the
efficiency of the processes and making their services as a high quality of outputs. Many artificial
intelligence does not have involvement of personal data (Li et al. 2017). The consumers who
mainly interacts with the service of artificial intelligence such as cloud computing, personal
assistants, robo-advisors who will instruct the financial advice, provides recommendations for
the streaming services will get affected. Every established companies in Europe deals with
personal data that includes payroll and uses the advantages of artificial intelligence for
management of such data. The way to use the personal data on the European citizens are being
limited now and raising legal risks for the companies are active for the artificial intelligence. The
GDPR deals with data protection and will impact negatively on the development and the use of
the artificial intelligence by the companies of Europe in financial sectors.
Cloud computing has the power to change the business opportunities as well as business
demands. Cloud computing helps a business to become more agile and scale all their resources
with elasticity and speed (Hashem et al. 2015). For all the business leaders, the cloud computing
enables the LOB (Lines of Business) to provision the computing resources and applications to
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6RESEARCH PAPER
rollout the key business initiatives. The cloud computing enables wider scale as well as
utilization of the IT resources as some shared services in an organization.
In financial industries, the information technology is considered as the most essential
factor in solving the issues (Dove et al. 2015). The information technology that is considered in
this research paper is the cloud computing, which plays an important role in the financial sector.
The cloud computing in the financial sector delivers IT services which is more flexible as well as
cost efficient. This makes the cloud computing a perfect information technology factor in the
financial industry. Cloud computing provides a high degree of regulation in the financial sector.
Cloud computing is very much useful in various sectors and from which the sector that is
considered in this research paper is the financial industry. The financial industry gets much
influenced with the cloud computing implementation (Hert and Papakonstantinou 2016). The
financial industry gets benefited with the implementation of cloud computing particularly for
customers because the customers can get access to different options that are offered by the
financial sector. The customers of the financial sector gets benefited from the cloud computing.
The independent variable that is the financial industry in this study enjoys the benefit for
utilizing the resources properly with fast consuming operations and with less effort (Martínez-
Pérez, Torre-Díez and López-Coronado 2015). The benefits that are included with cloud
computing also has some disadvantages that are included in this study. The flaws that are
associated with the cloud computing in financial sector involves security as well as privacy.
These flaws are considered as a main concern for the financial industry.
With the business in the finance sector, there is loss of control as well as compliance on
top of the Financial Industries and regulating all the risks that are associated with the business
processes. The risks that is perceived by the use of cloud computing in financial markets poses
challenges to the users of cloud. The challenges that are includes are stated below:
Managing the compliance risks as well as managing governance.
Providing better tool for the contract or SLA negotiation, mainly in smaller financial
companies (Gai et al. 2015).
Increasing the transparency level of CSPs (Cloud Service Providers).
Increasing the level of information understanding of the cloud security in the Financial
Industries.
rollout the key business initiatives. The cloud computing enables wider scale as well as
utilization of the IT resources as some shared services in an organization.
In financial industries, the information technology is considered as the most essential
factor in solving the issues (Dove et al. 2015). The information technology that is considered in
this research paper is the cloud computing, which plays an important role in the financial sector.
The cloud computing in the financial sector delivers IT services which is more flexible as well as
cost efficient. This makes the cloud computing a perfect information technology factor in the
financial industry. Cloud computing provides a high degree of regulation in the financial sector.
Cloud computing is very much useful in various sectors and from which the sector that is
considered in this research paper is the financial industry. The financial industry gets much
influenced with the cloud computing implementation (Hert and Papakonstantinou 2016). The
financial industry gets benefited with the implementation of cloud computing particularly for
customers because the customers can get access to different options that are offered by the
financial sector. The customers of the financial sector gets benefited from the cloud computing.
The independent variable that is the financial industry in this study enjoys the benefit for
utilizing the resources properly with fast consuming operations and with less effort (Martínez-
Pérez, Torre-Díez and López-Coronado 2015). The benefits that are included with cloud
computing also has some disadvantages that are included in this study. The flaws that are
associated with the cloud computing in financial sector involves security as well as privacy.
These flaws are considered as a main concern for the financial industry.
With the business in the finance sector, there is loss of control as well as compliance on
top of the Financial Industries and regulating all the risks that are associated with the business
processes. The risks that is perceived by the use of cloud computing in financial markets poses
challenges to the users of cloud. The challenges that are includes are stated below:
Managing the compliance risks as well as managing governance.
Providing better tool for the contract or SLA negotiation, mainly in smaller financial
companies (Gai et al. 2015).
Increasing the transparency level of CSPs (Cloud Service Providers).
Increasing the level of information understanding of the cloud security in the Financial
Industries.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7RESEARCH PAPER
Clarify all differences in between the cloud computing as well as outsourcing.
Push all National Financial Supervisory Authorities (NFSAs) for providing advanced
guidance on the concept of cloud.
Improve the all available security as well as privacy schemes of certification.
From all the information that will be collected and analyzed in this research paper, there
are short term issues that helps to promote as well as adopt the cloud service. The issues are
stated below:
o Reduce information gap- None of the sectors, that is FIs or NFSAs considered the
security of cloud computing as the main factor while using the service. The security is
considered as the main factor only by the Cloud Service Providers (CSPs).
o Provide clear as well as perfect regulatory guidance- The service provider of cloud and
the financial industries have different views as well as understanding the regulation of the
cloud computing that seems to confirms that the financial markets needs some better
guidance as well as communication in between the users.
o Simplifying as well as streamlining the compliance- The NFSA mainly facilitate the
cloud service adoption mostly in the financial sectors for meeting regulatory
requirements (Gazzar, Hustad and Olsen 2016). There are different Financial Industries
that have Cloud Computing Security Risk Assessment, which is a helping tool that
develops a corporate risks of cloud computing.
This paper describes all the flaws that are related with the security as well as privacy that
is considered as a major part of the financial industry. This paper also shed light on the
challenges that cloud computing offers in financial sectors and all processes that cloud
computing contribute to the financial sector. This research paper also provides some potential
solutions to the current cloud computing and also provide solutions for future privacy issues as
well as security concerned with the financial sector. There are also some proposed regulatory as
well as compliance that helps the cloud computing to increase its security and solve the privacy
issues in financial industries. The following section in this chapter offers the aims and objectives
of this paper and finally provides some research questions related to cloud computing in financial
industries.
Clarify all differences in between the cloud computing as well as outsourcing.
Push all National Financial Supervisory Authorities (NFSAs) for providing advanced
guidance on the concept of cloud.
Improve the all available security as well as privacy schemes of certification.
From all the information that will be collected and analyzed in this research paper, there
are short term issues that helps to promote as well as adopt the cloud service. The issues are
stated below:
o Reduce information gap- None of the sectors, that is FIs or NFSAs considered the
security of cloud computing as the main factor while using the service. The security is
considered as the main factor only by the Cloud Service Providers (CSPs).
o Provide clear as well as perfect regulatory guidance- The service provider of cloud and
the financial industries have different views as well as understanding the regulation of the
cloud computing that seems to confirms that the financial markets needs some better
guidance as well as communication in between the users.
o Simplifying as well as streamlining the compliance- The NFSA mainly facilitate the
cloud service adoption mostly in the financial sectors for meeting regulatory
requirements (Gazzar, Hustad and Olsen 2016). There are different Financial Industries
that have Cloud Computing Security Risk Assessment, which is a helping tool that
develops a corporate risks of cloud computing.
This paper describes all the flaws that are related with the security as well as privacy that
is considered as a major part of the financial industry. This paper also shed light on the
challenges that cloud computing offers in financial sectors and all processes that cloud
computing contribute to the financial sector. This research paper also provides some potential
solutions to the current cloud computing and also provide solutions for future privacy issues as
well as security concerned with the financial sector. There are also some proposed regulatory as
well as compliance that helps the cloud computing to increase its security and solve the privacy
issues in financial industries. The following section in this chapter offers the aims and objectives
of this paper and finally provides some research questions related to cloud computing in financial
industries.

8RESEARCH PAPER
1.2 Aims and Objectives
The aim of this research paper is to discuss the impact of cloud computing in the financial
industry. The cloud service provides benefits to the financial industry along with security as well
as privacy issues. The aim of this research paper is to discuss all the security issues related to
cloud computing in the financial industry. This paper also aims to know the effect of GDPR on
security issues of cloud computing. The challenges related to the cloud computing are discussed
along with the mitigation technique needed to mitigate those challenges. Different processes that
are needed to mitigate the issues of cloud computing in financial sectors are investigated in this
research paper.
H1: If security and the privacy issues are mitigated in Cloud Computing, more
organizations will be encouraged to implement Cloud Computing in their business processes.
H2: If all companies in financial sector uses Cloud Computing, data storage system will
become very easy.
The expected output of this research paper is to study all the security issues of cloud
computing and know the mitigation techniques of cloud computing privacy and security issues.
This research paper clearly defines all such mitigation process of security issues that will help
other organization to depend of the service of cloud computing. This research paper also shows
the importance of GDPR (General Data Protection Regulation) of cloud computing that mainly
impacts on the financial industries. As because of the privacy and the security issues of cloud
computing, many organization in the financial sectors do not trust on cloud computing for its
data management. This research paper explains clearly the mitigation process of cloud
computing.
The below mentioned are the objectives that are followed to carry out this research paper.
To study the security as well as privacy issues of Cloud Computing related to Financial
Industry
To study the effect of GDPR on Security and Privacy issues of Cloud Computing in
Financial Sector
To understand the challenges associated with Cloud Computing
1.2 Aims and Objectives
The aim of this research paper is to discuss the impact of cloud computing in the financial
industry. The cloud service provides benefits to the financial industry along with security as well
as privacy issues. The aim of this research paper is to discuss all the security issues related to
cloud computing in the financial industry. This paper also aims to know the effect of GDPR on
security issues of cloud computing. The challenges related to the cloud computing are discussed
along with the mitigation technique needed to mitigate those challenges. Different processes that
are needed to mitigate the issues of cloud computing in financial sectors are investigated in this
research paper.
H1: If security and the privacy issues are mitigated in Cloud Computing, more
organizations will be encouraged to implement Cloud Computing in their business processes.
H2: If all companies in financial sector uses Cloud Computing, data storage system will
become very easy.
The expected output of this research paper is to study all the security issues of cloud
computing and know the mitigation techniques of cloud computing privacy and security issues.
This research paper clearly defines all such mitigation process of security issues that will help
other organization to depend of the service of cloud computing. This research paper also shows
the importance of GDPR (General Data Protection Regulation) of cloud computing that mainly
impacts on the financial industries. As because of the privacy and the security issues of cloud
computing, many organization in the financial sectors do not trust on cloud computing for its
data management. This research paper explains clearly the mitigation process of cloud
computing.
The below mentioned are the objectives that are followed to carry out this research paper.
To study the security as well as privacy issues of Cloud Computing related to Financial
Industry
To study the effect of GDPR on Security and Privacy issues of Cloud Computing in
Financial Sector
To understand the challenges associated with Cloud Computing
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9RESEARCH PAPER
To study the mitigation process related to Cloud Computing in Financial Industry
To understand the future/emerging security and privacy issues of Cloud Computing in
Financial Sector
1.3 Research Questions
What are the potential factors associate with General Data Protection Regulation (GDPR)
use in cloud computing?
What are the impacts of GDPR on Cloud Computing in Financial Sector?
How GDPR can affect the Security and Privacy issues of Cloud Computing in Financial
Sector?
How to mitigate the issues related to GDPR on Cloud Computing in Financial Sector?
2. Literature Review
According to Rittinghouse and Ransome (2016), cloud computing is one of the most
important technological advancements that are used in the financial industries by the CIOs, and
the CFOs of the organizations. The concept of cloud computing is mainly a rapid developing
technology that has mostly gained traction in the recent years. The cloud is mainly an enabler of
many other technologies that includes big data, Internet of Things, artificial intelligence and
many other technologies. The main service that the cloud computing provides mainly concern
with interoperability, security of storage and provides service to their customers irrespective of
time and place. Cloud computing serves many benefits that are also associated with the
applications included in the financial sectors as well as in banking sectors.
To study the mitigation process related to Cloud Computing in Financial Industry
To understand the future/emerging security and privacy issues of Cloud Computing in
Financial Sector
1.3 Research Questions
What are the potential factors associate with General Data Protection Regulation (GDPR)
use in cloud computing?
What are the impacts of GDPR on Cloud Computing in Financial Sector?
How GDPR can affect the Security and Privacy issues of Cloud Computing in Financial
Sector?
How to mitigate the issues related to GDPR on Cloud Computing in Financial Sector?
2. Literature Review
According to Rittinghouse and Ransome (2016), cloud computing is one of the most
important technological advancements that are used in the financial industries by the CIOs, and
the CFOs of the organizations. The concept of cloud computing is mainly a rapid developing
technology that has mostly gained traction in the recent years. The cloud is mainly an enabler of
many other technologies that includes big data, Internet of Things, artificial intelligence and
many other technologies. The main service that the cloud computing provides mainly concern
with interoperability, security of storage and provides service to their customers irrespective of
time and place. Cloud computing serves many benefits that are also associated with the
applications included in the financial sectors as well as in banking sectors.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
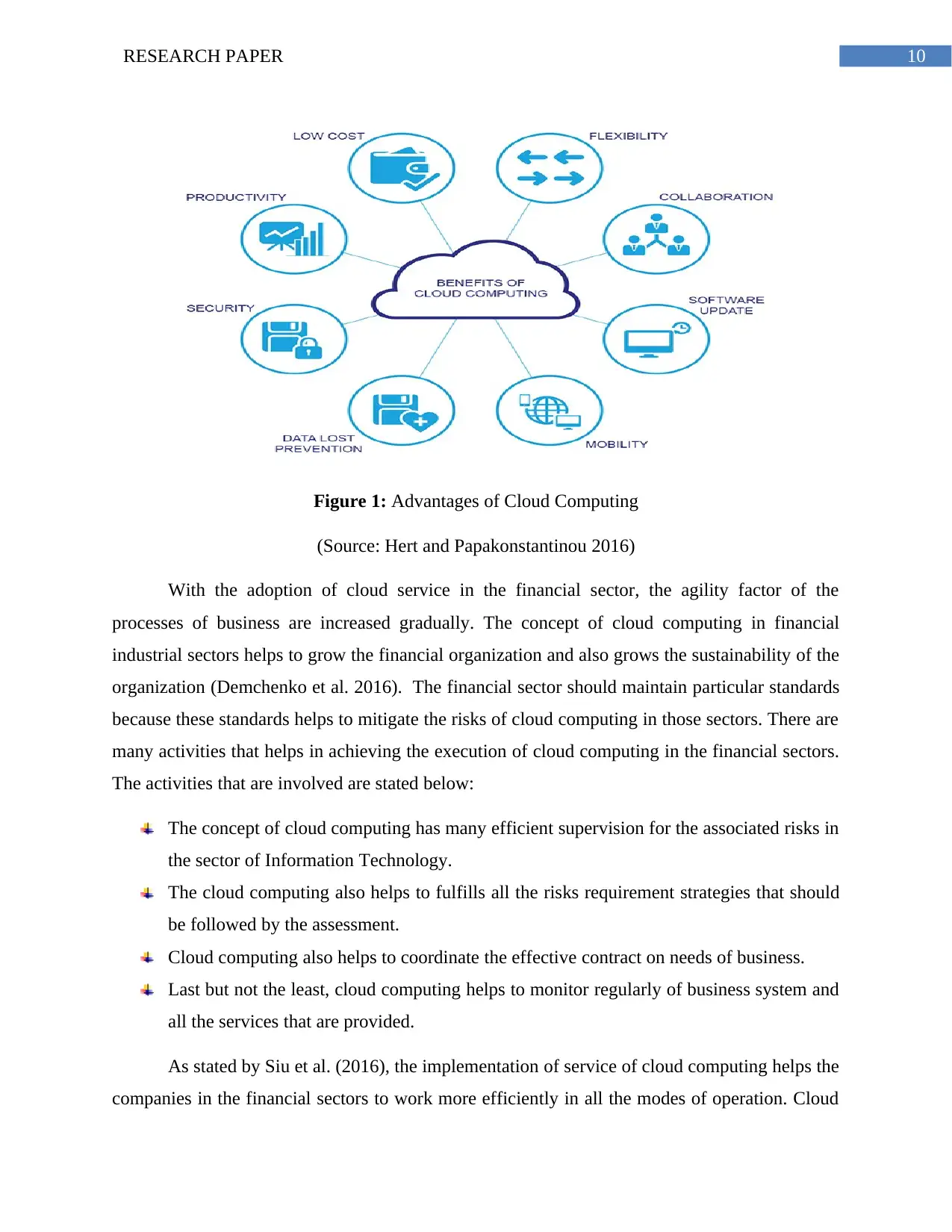
10RESEARCH PAPER
Figure 1: Advantages of Cloud Computing
(Source: Hert and Papakonstantinou 2016)
With the adoption of cloud service in the financial sector, the agility factor of the
processes of business are increased gradually. The concept of cloud computing in financial
industrial sectors helps to grow the financial organization and also grows the sustainability of the
organization (Demchenko et al. 2016). The financial sector should maintain particular standards
because these standards helps to mitigate the risks of cloud computing in those sectors. There are
many activities that helps in achieving the execution of cloud computing in the financial sectors.
The activities that are involved are stated below:
The concept of cloud computing has many efficient supervision for the associated risks in
the sector of Information Technology.
The cloud computing also helps to fulfills all the risks requirement strategies that should
be followed by the assessment.
Cloud computing also helps to coordinate the effective contract on needs of business.
Last but not the least, cloud computing helps to monitor regularly of business system and
all the services that are provided.
As stated by Siu et al. (2016), the implementation of service of cloud computing helps the
companies in the financial sectors to work more efficiently in all the modes of operation. Cloud
Figure 1: Advantages of Cloud Computing
(Source: Hert and Papakonstantinou 2016)
With the adoption of cloud service in the financial sector, the agility factor of the
processes of business are increased gradually. The concept of cloud computing in financial
industrial sectors helps to grow the financial organization and also grows the sustainability of the
organization (Demchenko et al. 2016). The financial sector should maintain particular standards
because these standards helps to mitigate the risks of cloud computing in those sectors. There are
many activities that helps in achieving the execution of cloud computing in the financial sectors.
The activities that are involved are stated below:
The concept of cloud computing has many efficient supervision for the associated risks in
the sector of Information Technology.
The cloud computing also helps to fulfills all the risks requirement strategies that should
be followed by the assessment.
Cloud computing also helps to coordinate the effective contract on needs of business.
Last but not the least, cloud computing helps to monitor regularly of business system and
all the services that are provided.
As stated by Siu et al. (2016), the implementation of service of cloud computing helps the
companies in the financial sectors to work more efficiently in all the modes of operation. Cloud

11RESEARCH PAPER
computing consists of many benefits when all the risks included in cloud are managed. The cloud
computing helps all the organizations in the financial sector to make new entry in the markets,
get benefits from all new opportunities and strengthen all processes of the business involved in
the financial sectors (Gai et al. 2015). The financial firms can get benefitted in many ways
among which another way is that the cloud computing reduces their setup and the operating cost
that are related with the installation of the of new hardware and the software that is required for
the storage in the data centers that makes the infrastructure resource needed that are needed or is
available.
Figure 2: Cloud computing process
(Source: Weber 2015)
Importance of this Research Study:
This research study is important because Cloud Computing plays an important role in
storing of data in Financial Sector. The cloud is mainly considered as digital agenda in this world
of digitization. The firms in the financial sector also have concern related to regulatory
compliance which holds the concept of cloud computing with very wide adoption scale (Lučić,
Boban and Mileta 2018). The main concerns that are related with the cloud computing in
financial sectors are described below:
computing consists of many benefits when all the risks included in cloud are managed. The cloud
computing helps all the organizations in the financial sector to make new entry in the markets,
get benefits from all new opportunities and strengthen all processes of the business involved in
the financial sectors (Gai et al. 2015). The financial firms can get benefitted in many ways
among which another way is that the cloud computing reduces their setup and the operating cost
that are related with the installation of the of new hardware and the software that is required for
the storage in the data centers that makes the infrastructure resource needed that are needed or is
available.
Figure 2: Cloud computing process
(Source: Weber 2015)
Importance of this Research Study:
This research study is important because Cloud Computing plays an important role in
storing of data in Financial Sector. The cloud is mainly considered as digital agenda in this world
of digitization. The firms in the financial sector also have concern related to regulatory
compliance which holds the concept of cloud computing with very wide adoption scale (Lučić,
Boban and Mileta 2018). The main concerns that are related with the cloud computing in
financial sectors are described below:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 46
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





