Cloud Computing for SMEs in the UK: Performance and Security Issues
VerifiedAdded on 2023/05/27
|9
|2262
|350
Report
AI Summary
This report explores the impact of cloud computing on small and medium-sized enterprises (SMEs) in the United Kingdom, focusing on its potential to enhance performance and profitability while addressing associated security challenges. It investigates the concept of cloud computing, evaluates its importance for SMEs in the UK, and identifies prevalent security threats. The research methodology employs a mixed-methods approach, combining quantitative and qualitative data collection through surveys and literature reviews. Ethical considerations are addressed to ensure privacy and proper citation. Data analysis techniques are outlined to interpret both primary and secondary data, aiming to provide insights into how SMEs can leverage cloud computing to improve their operations and competitiveness, while mitigating security risks. Desklib provides access to similar documents and study tools for students.

Cloud Computing
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CLOUD COMPUTING
1
Table of Contents
Introduction...........................................................................................................................................2
Research Question.................................................................................................................................2
Research aims and objectives................................................................................................................2
Literature review...................................................................................................................................2
Proposed Methodology.........................................................................................................................4
Research design.................................................................................................................................4
Research strategy..............................................................................................................................5
Data collection method.....................................................................................................................5
Ethical issues......................................................................................................................................5
Data analysis......................................................................................................................................6
Bibliography...........................................................................................................................................7
Appendices............................................................................................................................................8
Timetable...........................................................................................................................................8
Reflection..........................................................................................................................................8
1
Table of Contents
Introduction...........................................................................................................................................2
Research Question.................................................................................................................................2
Research aims and objectives................................................................................................................2
Literature review...................................................................................................................................2
Proposed Methodology.........................................................................................................................4
Research design.................................................................................................................................4
Research strategy..............................................................................................................................5
Data collection method.....................................................................................................................5
Ethical issues......................................................................................................................................5
Data analysis......................................................................................................................................6
Bibliography...........................................................................................................................................7
Appendices............................................................................................................................................8
Timetable...........................................................................................................................................8
Reflection..........................................................................................................................................8

CLOUD COMPUTING
2
Introduction
Cloud computing technique is one of the advanced computer technology that has the
ability to increase the efficiency and performance of the minor and medium business.
The use of cloud computing is growing rapidly and many companies are using this
approach to control and monitor a large amount of consumer data.1 This report aim is to
analysis the role of cloud technology for SME business in the United Kingdom and
describes their security-related issues. In the last five years the rate of cloud computing
has increased by 49% and with the help of this technique, the SMEs will be able to
obtain the advanced computer technologies without the requirement for the upfront
cost. This report divided into main three parts such as research question, research aims
and objectives, literature review and methodology.
Research Question
How can small and medium business in the UK can increase their performance
and profitability by using cloud computing?
What are the Security challenges and issues faced by cloud computing
technology?
Research aims and objectives
There are following aims and objectives of this investigation:
To analysis the concept of cloud computing technology
To evaluate the importance of the cloud technique in order to increase the
performance and productivity of small and medium business in the UK
To identify the security threats and challenged faced by cloud computing
Literature review
Cloud computing is a very popular technology which is used by many companies to
handle the huge amount of data sets. With the help of this method, the consumer can
secure their personal data or information from hackers because it provides a way to
1 Reza Sahandi, Adel Alkhalil, and Justice Opara-Martins, ‘Cloud computing from SMEs perspective: a
survey based investigation’ (2013) 24(1) Journal of Information Technology Management 1-12.
2
Introduction
Cloud computing technique is one of the advanced computer technology that has the
ability to increase the efficiency and performance of the minor and medium business.
The use of cloud computing is growing rapidly and many companies are using this
approach to control and monitor a large amount of consumer data.1 This report aim is to
analysis the role of cloud technology for SME business in the United Kingdom and
describes their security-related issues. In the last five years the rate of cloud computing
has increased by 49% and with the help of this technique, the SMEs will be able to
obtain the advanced computer technologies without the requirement for the upfront
cost. This report divided into main three parts such as research question, research aims
and objectives, literature review and methodology.
Research Question
How can small and medium business in the UK can increase their performance
and profitability by using cloud computing?
What are the Security challenges and issues faced by cloud computing
technology?
Research aims and objectives
There are following aims and objectives of this investigation:
To analysis the concept of cloud computing technology
To evaluate the importance of the cloud technique in order to increase the
performance and productivity of small and medium business in the UK
To identify the security threats and challenged faced by cloud computing
Literature review
Cloud computing is a very popular technology which is used by many companies to
handle the huge amount of data sets. With the help of this method, the consumer can
secure their personal data or information from hackers because it provides a way to
1 Reza Sahandi, Adel Alkhalil, and Justice Opara-Martins, ‘Cloud computing from SMEs perspective: a
survey based investigation’ (2013) 24(1) Journal of Information Technology Management 1-12.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

CLOUD COMPUTING
3
back up their private data files.2 In the last few years, many researchers investigated on
this topic and they observed that security is one of the serious problem faced by
consumers which occur due to use of unauthentic servers. According to Ezer Osei,
Yeboah-Boateng, and Kofi Asare Essandoh, (2014) the small and medium enterprises in
the UK have very fewer advantages due to their limited resources if they adopt cloud
computing than they can enhance their productivity. SMEs play a significant role for an
organization because it offers a huge quantity of employment for which the small and
medium business in the UK found a new approach to improve their efficiency. For which
information technology produced a new method (cloud computing) that has the
potential to reduce operational cost and expend their overall performance. Recent
survey observed that the infrastructure of cloud computing can address the data
analysis issues and allow SMEs to be more effective, competitive and also provide a
degree of flexibility.3 Nabil Sultan, (2010) identified that cloud computing provides a
way to commercial agility and provisions a earlier time to marketplace by delivering the
ready to consumer services to their consumer. Many investigations have concentrated
on two main issues, for example, business agility and catalysts for more innovation.
However, security is one if the biggest issue faced by this technology and Anabel,
Gutierrez, Elias Boukrami, and Ranald Lumsden, (2015) identified that many consumers
use third-party application and unauthentic networks by which they can lose their
personal information and data. They conducted a survey to analyse the views of other
experts and more than 40% small and medium business businesses in the UK adopted
this technique to control and manage their operations.4 Nabil Sultan, (2010) evaluated
that SMEs are very interested in the field of cloud computing because of their several
advantages like, reduce cost and efforts, and improves the efficiency of business, more
flexible and scalability of IT resources.5 In this kind of technique business industries can
2 Nabil Sultan,’ Cloud computing for education: A new dawn?’ (2010) 30(2) International Journal of
Information Management 109-116.
3 Fátima, Neves, Trindade, Fernando Cruz Marta, Ana Maria R. Correia, and Miguel de Castro Neto,
‘The adoption of cloud computing by SMEs: identifying and coping with external factors.’ (2011) 12(2)
International Journal of Information Management 12-16.
4 Anabel, Gutierrez, Elias Boukrami, and Ranald Lumsden. ‘Technological, organisational and
environmental factors influencing managers’ decision to adopt cloud computing in the UK.’ (2015)
28(6) Journal of Enterprise Information Management 788-807.
5 Yazn, Alshamaila, Savvas Papagiannidis, and Feng Li, ‘Cloud computing adoption by SMEs in the
north east of England: A multi-perspective framework’ (2013) 26(3) Journal of Enterprise Information
Management 250-275.
3
back up their private data files.2 In the last few years, many researchers investigated on
this topic and they observed that security is one of the serious problem faced by
consumers which occur due to use of unauthentic servers. According to Ezer Osei,
Yeboah-Boateng, and Kofi Asare Essandoh, (2014) the small and medium enterprises in
the UK have very fewer advantages due to their limited resources if they adopt cloud
computing than they can enhance their productivity. SMEs play a significant role for an
organization because it offers a huge quantity of employment for which the small and
medium business in the UK found a new approach to improve their efficiency. For which
information technology produced a new method (cloud computing) that has the
potential to reduce operational cost and expend their overall performance. Recent
survey observed that the infrastructure of cloud computing can address the data
analysis issues and allow SMEs to be more effective, competitive and also provide a
degree of flexibility.3 Nabil Sultan, (2010) identified that cloud computing provides a
way to commercial agility and provisions a earlier time to marketplace by delivering the
ready to consumer services to their consumer. Many investigations have concentrated
on two main issues, for example, business agility and catalysts for more innovation.
However, security is one if the biggest issue faced by this technology and Anabel,
Gutierrez, Elias Boukrami, and Ranald Lumsden, (2015) identified that many consumers
use third-party application and unauthentic networks by which they can lose their
personal information and data. They conducted a survey to analyse the views of other
experts and more than 40% small and medium business businesses in the UK adopted
this technique to control and manage their operations.4 Nabil Sultan, (2010) evaluated
that SMEs are very interested in the field of cloud computing because of their several
advantages like, reduce cost and efforts, and improves the efficiency of business, more
flexible and scalability of IT resources.5 In this kind of technique business industries can
2 Nabil Sultan,’ Cloud computing for education: A new dawn?’ (2010) 30(2) International Journal of
Information Management 109-116.
3 Fátima, Neves, Trindade, Fernando Cruz Marta, Ana Maria R. Correia, and Miguel de Castro Neto,
‘The adoption of cloud computing by SMEs: identifying and coping with external factors.’ (2011) 12(2)
International Journal of Information Management 12-16.
4 Anabel, Gutierrez, Elias Boukrami, and Ranald Lumsden. ‘Technological, organisational and
environmental factors influencing managers’ decision to adopt cloud computing in the UK.’ (2015)
28(6) Journal of Enterprise Information Management 788-807.
5 Yazn, Alshamaila, Savvas Papagiannidis, and Feng Li, ‘Cloud computing adoption by SMEs in the
north east of England: A multi-perspective framework’ (2013) 26(3) Journal of Enterprise Information
Management 250-275.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CLOUD COMPUTING
4
analysis the consumer data and they can easily store the huge amount of data in a single
computer device. It is a kind of perfect for allowing convenient, and also provide on-
demand services to their consumers by which they can share data or information from
one person to another. More than 50% of experts observed that small and medium
enterprises have very limited of cloud computing by which they are not able to perform
numbers of the task at a time.6 If they adopt the advanced cloud computing approach
with their infrastructure then they can easily monitor and analysis the consumer's
datasets by which they can also increase the overall performance. Stephen, Biggs, and
Stilianos Vidalis, (2009) observed that there are numerous safety related issues occur in
the cloud, for example, denial of service attack, malware attack, ransom ware, wanna
cry, phishing, and other cyber-crimes. Such kinds of issues can be addressed by
adopting advanced security tools, for example, firewall, encryption, and cryptography
technologies.7
Proposed Methodology
It will comprise dissimilar classes of procedures, strategies and approaches which will
be utilized by the author during their research. There are main five methods will be
used in the research, such as, data group, design, approach and viewpoint of the study.
With the help of these methods, research will enhance the effectiveness of the
investigation. The aim of this research is to analysis the concept of cloud technology and
how this technique is used for SMEs business to improve their performance.
Research design
In which a mixed investigation design will be used which contains both quantitative and
qualitative processes. In the qualitative method the pertinent material will be collected
from specialists in order to understand the security challenges faced by cloud
computing. A research survey will be adopted by the researcher to analysis the views of
other experts and participants. The observation based on the survey will help the
researcher to achieve the objectives of this research paper.
6 Stephen, Biggs, and Stilianos Vidalis.’ Cloud computing: The impact on digital forensic
investigations.’ (2009) 12(4) Internet Technology and Secured Transactions 12-29.
7 Ezer Osei, Yeboah-Boateng, and Kofi Asare Essandoh. ‘Factors influencing the adoption of cloud
computing by small and medium enterprises in developing economies.’ (2014) 2(4) International
Journal of Emerging Science and Engineering 13-20.
4
analysis the consumer data and they can easily store the huge amount of data in a single
computer device. It is a kind of perfect for allowing convenient, and also provide on-
demand services to their consumers by which they can share data or information from
one person to another. More than 50% of experts observed that small and medium
enterprises have very limited of cloud computing by which they are not able to perform
numbers of the task at a time.6 If they adopt the advanced cloud computing approach
with their infrastructure then they can easily monitor and analysis the consumer's
datasets by which they can also increase the overall performance. Stephen, Biggs, and
Stilianos Vidalis, (2009) observed that there are numerous safety related issues occur in
the cloud, for example, denial of service attack, malware attack, ransom ware, wanna
cry, phishing, and other cyber-crimes. Such kinds of issues can be addressed by
adopting advanced security tools, for example, firewall, encryption, and cryptography
technologies.7
Proposed Methodology
It will comprise dissimilar classes of procedures, strategies and approaches which will
be utilized by the author during their research. There are main five methods will be
used in the research, such as, data group, design, approach and viewpoint of the study.
With the help of these methods, research will enhance the effectiveness of the
investigation. The aim of this research is to analysis the concept of cloud technology and
how this technique is used for SMEs business to improve their performance.
Research design
In which a mixed investigation design will be used which contains both quantitative and
qualitative processes. In the qualitative method the pertinent material will be collected
from specialists in order to understand the security challenges faced by cloud
computing. A research survey will be adopted by the researcher to analysis the views of
other experts and participants. The observation based on the survey will help the
researcher to achieve the objectives of this research paper.
6 Stephen, Biggs, and Stilianos Vidalis.’ Cloud computing: The impact on digital forensic
investigations.’ (2009) 12(4) Internet Technology and Secured Transactions 12-29.
7 Ezer Osei, Yeboah-Boateng, and Kofi Asare Essandoh. ‘Factors influencing the adoption of cloud
computing by small and medium enterprises in developing economies.’ (2014) 2(4) International
Journal of Emerging Science and Engineering 13-20.

CLOUD COMPUTING
5
Research strategy
In this investigation, the relevant data will be obtained with the help of a survey using
the questionnaire in order to collect the opinion of other experts in the field of cloud
computing. This investigation design will allow the writer to collect first hand and
relevant information about the research topic. Microsoft office will be involved to
prepare the questionnaire for the investigation and participants will receive the
questionnaire with the help of social media or emails. A literature review will be used
which is based on secondary resources and relevant information will be gathered from
various resources, for example, previous journal papers, online websites, books and
offline resources. The theoretical information about cloud computing will be collected
from this literature review and survey will provide the primary data. With the help of
both approaches, the researcher will be able to achieve the objective of their
investigation.
Data collection method
To collect the relevant data both primary and secondary methods will be used in this
investigation. The secondary data will be obtained from different resources, for
example, books, online websites, journal articles, previous investigation and other. The
primary data will be gathered with the help of a questionnaire that will be transferred
to the participants. With the help of these methods, the researcher will able to collect
the data or information about cloud computing by which research can enhance the
effectiveness of the paper.
Ethical issues
A research scholar would use the privacy act for controlling and maintains the secrecy
of the investigation candidates throughout the accomplishment of the exploration
education. For providing credit to the writer the researcher would use the in-text
citation in each paragraph of the investigation. It can help to obtain accurate and
consistent results and achieve the objectives of this investigation. In order to maintain
the quality of research study, investigator and research scholar will use their own
words and knowledge during the investigation.
5
Research strategy
In this investigation, the relevant data will be obtained with the help of a survey using
the questionnaire in order to collect the opinion of other experts in the field of cloud
computing. This investigation design will allow the writer to collect first hand and
relevant information about the research topic. Microsoft office will be involved to
prepare the questionnaire for the investigation and participants will receive the
questionnaire with the help of social media or emails. A literature review will be used
which is based on secondary resources and relevant information will be gathered from
various resources, for example, previous journal papers, online websites, books and
offline resources. The theoretical information about cloud computing will be collected
from this literature review and survey will provide the primary data. With the help of
both approaches, the researcher will be able to achieve the objective of their
investigation.
Data collection method
To collect the relevant data both primary and secondary methods will be used in this
investigation. The secondary data will be obtained from different resources, for
example, books, online websites, journal articles, previous investigation and other. The
primary data will be gathered with the help of a questionnaire that will be transferred
to the participants. With the help of these methods, the researcher will able to collect
the data or information about cloud computing by which research can enhance the
effectiveness of the paper.
Ethical issues
A research scholar would use the privacy act for controlling and maintains the secrecy
of the investigation candidates throughout the accomplishment of the exploration
education. For providing credit to the writer the researcher would use the in-text
citation in each paragraph of the investigation. It can help to obtain accurate and
consistent results and achieve the objectives of this investigation. In order to maintain
the quality of research study, investigator and research scholar will use their own
words and knowledge during the investigation.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

CLOUD COMPUTING
6
Data analysis
The data analysis process will be adopted by the investigator to describe both primary
and secondary data to track the pattern of the research topic. This approach will assist
the investigator in interpreting the information which is obtained from primary and
secondary resources. However, research can select another data analysis approaches,
for example, content analysis, disclosure analysis, statistical analysis and many more.
6
Data analysis
The data analysis process will be adopted by the investigator to describe both primary
and secondary data to track the pattern of the research topic. This approach will assist
the investigator in interpreting the information which is obtained from primary and
secondary resources. However, research can select another data analysis approaches,
for example, content analysis, disclosure analysis, statistical analysis and many more.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CLOUD COMPUTING
7
Bibliography
Alshamaila, Y, Papagiannidis S, and Li F, ‘Cloud computing adoption by SMEs in the
north east of England: A multi-perspective framework’ (2013) 26(3) Journal of
Enterprise Information Management 250-275.
Biggs, S, and Vidalis S.’ Cloud computing: The impact on digital forensic investigations.’
(2009) 12(4) Internet Technology and Secured Transactions 12-29.
Gutierrez, A, Boukrami E, and Lumsden R. ‘Technological, organisational and
environmental factors influencing managers’ decision to adopt cloud computing in the
UK.’ (2015) 28(6) Journal of Enterprise Information Management 788-807.
Neves, FT, Marta FC, Correia AMR, and Neto MDC, ‘The adoption of cloud computing by
SMEs: identifying and coping with external factors.’ (2011) 12(2) International Journal
of Information Management 12-16.
Sahandi, R, Alkhalil A, and Opara-Martins J, ‘Cloud computing from SMEs perspective: a
survey based investigation’ (2013) 24(1) Journal of Information Technology
Management 1-12.
Sultan, N,’ Cloud computing for education: A new dawn?’ (2010) 30(2) International
Journal of Information Management 109-116.
Yeboah-Boateng, EO, and Essandoh KA. ‘Factors influencing the adoption of cloud
computing by small and medium enterprises in developing economies.’ (2014) 2(4)
International Journal of Emerging Science and Engineering 13-20.
7
Bibliography
Alshamaila, Y, Papagiannidis S, and Li F, ‘Cloud computing adoption by SMEs in the
north east of England: A multi-perspective framework’ (2013) 26(3) Journal of
Enterprise Information Management 250-275.
Biggs, S, and Vidalis S.’ Cloud computing: The impact on digital forensic investigations.’
(2009) 12(4) Internet Technology and Secured Transactions 12-29.
Gutierrez, A, Boukrami E, and Lumsden R. ‘Technological, organisational and
environmental factors influencing managers’ decision to adopt cloud computing in the
UK.’ (2015) 28(6) Journal of Enterprise Information Management 788-807.
Neves, FT, Marta FC, Correia AMR, and Neto MDC, ‘The adoption of cloud computing by
SMEs: identifying and coping with external factors.’ (2011) 12(2) International Journal
of Information Management 12-16.
Sahandi, R, Alkhalil A, and Opara-Martins J, ‘Cloud computing from SMEs perspective: a
survey based investigation’ (2013) 24(1) Journal of Information Technology
Management 1-12.
Sultan, N,’ Cloud computing for education: A new dawn?’ (2010) 30(2) International
Journal of Information Management 109-116.
Yeboah-Boateng, EO, and Essandoh KA. ‘Factors influencing the adoption of cloud
computing by small and medium enterprises in developing economies.’ (2014) 2(4)
International Journal of Emerging Science and Engineering 13-20.
CLOUD COMPUTING
8
Appendices
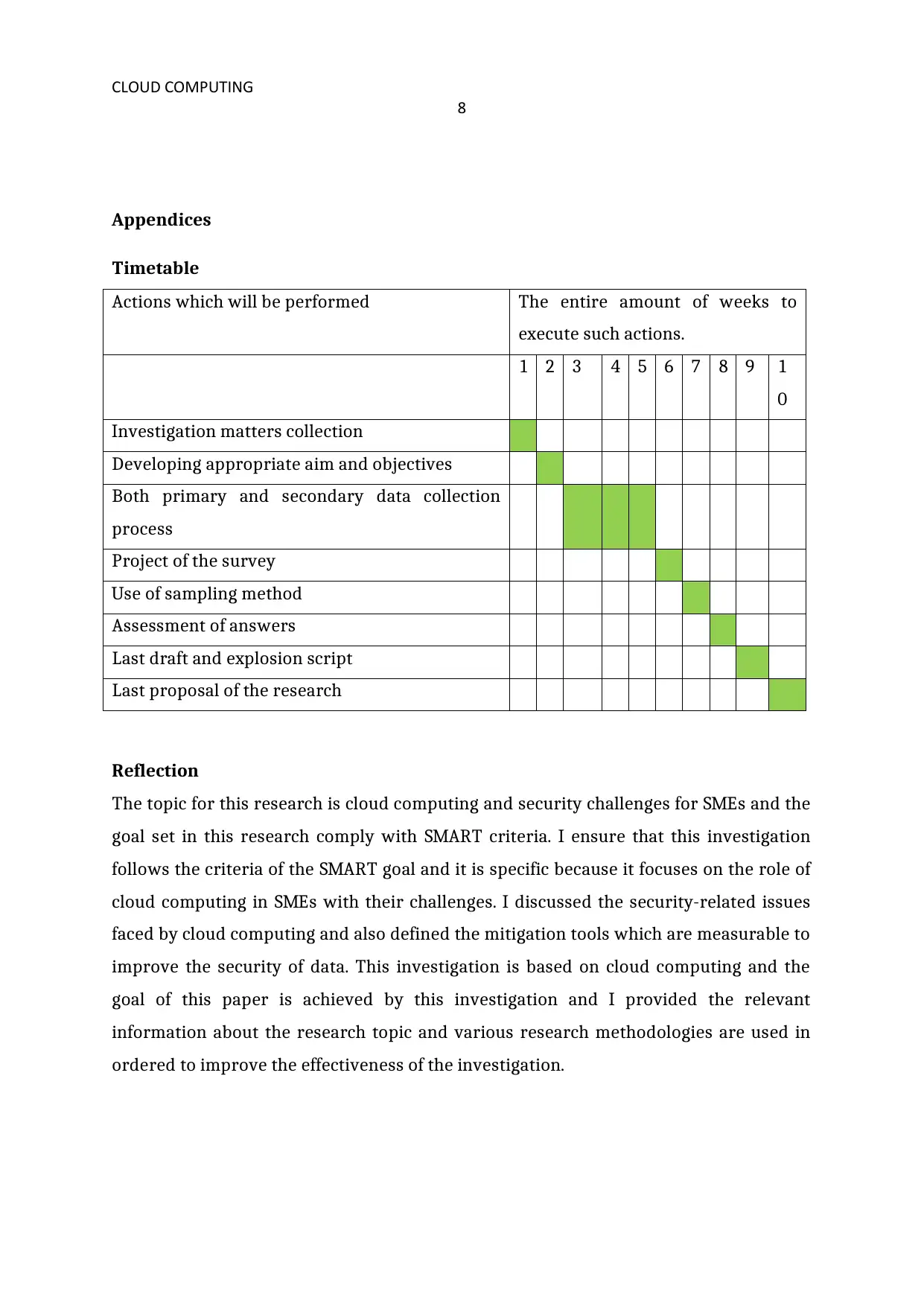
Timetable
Actions which will be performed The entire amount of weeks to
execute such actions.
1 2 3 4 5 6 7 8 9 1
0
Investigation matters collection
Developing appropriate aim and objectives
Both primary and secondary data collection
process
Project of the survey
Use of sampling method
Assessment of answers
Last draft and explosion script
Last proposal of the research
Reflection
The topic for this research is cloud computing and security challenges for SMEs and the
goal set in this research comply with SMART criteria. I ensure that this investigation
follows the criteria of the SMART goal and it is specific because it focuses on the role of
cloud computing in SMEs with their challenges. I discussed the security-related issues
faced by cloud computing and also defined the mitigation tools which are measurable to
improve the security of data. This investigation is based on cloud computing and the
goal of this paper is achieved by this investigation and I provided the relevant
information about the research topic and various research methodologies are used in
ordered to improve the effectiveness of the investigation.
8
Appendices
Timetable
Actions which will be performed The entire amount of weeks to
execute such actions.
1 2 3 4 5 6 7 8 9 1
0
Investigation matters collection
Developing appropriate aim and objectives
Both primary and secondary data collection
process
Project of the survey
Use of sampling method
Assessment of answers
Last draft and explosion script
Last proposal of the research
Reflection
The topic for this research is cloud computing and security challenges for SMEs and the
goal set in this research comply with SMART criteria. I ensure that this investigation
follows the criteria of the SMART goal and it is specific because it focuses on the role of
cloud computing in SMEs with their challenges. I discussed the security-related issues
faced by cloud computing and also defined the mitigation tools which are measurable to
improve the security of data. This investigation is based on cloud computing and the
goal of this paper is achieved by this investigation and I provided the relevant
information about the research topic and various research methodologies are used in
ordered to improve the effectiveness of the investigation.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




