Cloud Computing: Data Storage - Research, Analysis, and Future Trends
VerifiedAdded on 2020/03/04
|13
|2355
|468
Report
AI Summary
This report delves into the realm of cloud computing and data storage, examining its evolution from personal computers to centralized infrastructure. It explores the rationale behind cloud storage, its advantages like scalability and security, and the associated challenges, including performance and privacy concerns. The report investigates research questions surrounding cloud storage, such as data access, the future of computing, and the risks involved. It presents a conceptual framework, reviews existing literature, and outlines the methodology used, including data collection methods and ethical considerations. The project plan includes deliverables like a literature review and a research report, along with risk analysis, a work breakdown structure, and a Gantt chart. The report concludes with a discussion of future trends and the impact of cloud computing on the IT landscape.

Running head: CLOUD COMPUTING- DATA STORAGE
Cloud computing- Data storage
Name of the student:
Name of the university:
Author Note
Cloud computing- Data storage
Name of the student:
Name of the university:
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1CLOUD COMPUTING- DATA STORAGE
Abstract
The large effect of the cloud computing has turned the software applications, data storage and
computer processing into the utilities that are served from the centralized infrastructure. Utility of
this type of technology made few important alterations in the computing economics. The cloud
computing has lowered down the points of prices and widened the computing availability in the
manner that it made the capacity constraints over the users. To this end the what that was once only
the personal computer has currently turned into the terminal via which the users could manipulate
the gigantic machines of computing. They have been able to expand for meeting the necessities. The
ability has made the jobs that were once unattainable. They have been now within the reach.
Abstract
The large effect of the cloud computing has turned the software applications, data storage and
computer processing into the utilities that are served from the centralized infrastructure. Utility of
this type of technology made few important alterations in the computing economics. The cloud
computing has lowered down the points of prices and widened the computing availability in the
manner that it made the capacity constraints over the users. To this end the what that was once only
the personal computer has currently turned into the terminal via which the users could manipulate
the gigantic machines of computing. They have been able to expand for meeting the necessities. The
ability has made the jobs that were once unattainable. They have been now within the reach.

2CLOUD COMPUTING- DATA STORAGE
Table of Contents
2. Rationale............................................................................................................................................3
2.1 Problem domain...........................................................................................................................3
2.2 Purpose and justification..............................................................................................................3
3. Research Questions............................................................................................................................4
4. Conceptual or Theoretical Framework..............................................................................................4
5. Literature Review..............................................................................................................................5
6. Methodology......................................................................................................................................6
6.1 Data collection or systems design methods.................................................................................6
6.2 Ethical Issues...............................................................................................................................6
6.3 Analysis of data...........................................................................................................................7
7. Project Plan........................................................................................................................................8
7.1 Deliverables (Conclusions, Recommendations, Software code etc)...........................................8
7.2 Risk Analysis...............................................................................................................................8
7.3 Work breakdown structure (WBS)................................................................................................9
7.4 Gantt chart:....................................................................................................................................10
8. References:......................................................................................................................................11
Table of Contents
2. Rationale............................................................................................................................................3
2.1 Problem domain...........................................................................................................................3
2.2 Purpose and justification..............................................................................................................3
3. Research Questions............................................................................................................................4
4. Conceptual or Theoretical Framework..............................................................................................4
5. Literature Review..............................................................................................................................5
6. Methodology......................................................................................................................................6
6.1 Data collection or systems design methods.................................................................................6
6.2 Ethical Issues...............................................................................................................................6
6.3 Analysis of data...........................................................................................................................7
7. Project Plan........................................................................................................................................8
7.1 Deliverables (Conclusions, Recommendations, Software code etc)...........................................8
7.2 Risk Analysis...............................................................................................................................8
7.3 Work breakdown structure (WBS)................................................................................................9
7.4 Gantt chart:....................................................................................................................................10
8. References:......................................................................................................................................11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3CLOUD COMPUTING- DATA STORAGE
2. Rationale
2.1 Problem domain
Regarding few owners of the computers, the recognizing of the sufficient storage spaces
holding every data they have been acquiring has been the most important challenge. Few individuals
have been investing in the bigger hard drives. The others have preferred the external devices to store
such as the compact discs or the thumb drives. However the owners have been deleting the complete
folders containing the old files for making space for the latest information. Despite that some has
been opting to depend upon the rising trend which is the cloud storage. The technology has been
mush popular and used most by the common people and various other companies. However the
question that has been rising that as the technology has been growing into more advanced mode,
would the data center of future be lying on the basis of cloud?
2.2 Purpose and justification
The purpose of the research has been to find the future level of significance of the cloud
storage and the investigation on the current advances in the cloud storage. It also discusses the open
problems in the sectors that are related to the cloud computing. The common query has been that
who could access the data in that cloud? The question envelops a small meaning. The cloud has not
been the entity like that and it has been up to the user for deciding which of the services is to be
used. Every service has different approach to the data. In general considerations the services that are
bough from the vendors of the cloud have been the private services that the resources and the data
have been belonging to. This could not be accessed to the others till it is made so.
2. Rationale
2.1 Problem domain
Regarding few owners of the computers, the recognizing of the sufficient storage spaces
holding every data they have been acquiring has been the most important challenge. Few individuals
have been investing in the bigger hard drives. The others have preferred the external devices to store
such as the compact discs or the thumb drives. However the owners have been deleting the complete
folders containing the old files for making space for the latest information. Despite that some has
been opting to depend upon the rising trend which is the cloud storage. The technology has been
mush popular and used most by the common people and various other companies. However the
question that has been rising that as the technology has been growing into more advanced mode,
would the data center of future be lying on the basis of cloud?
2.2 Purpose and justification
The purpose of the research has been to find the future level of significance of the cloud
storage and the investigation on the current advances in the cloud storage. It also discusses the open
problems in the sectors that are related to the cloud computing. The common query has been that
who could access the data in that cloud? The question envelops a small meaning. The cloud has not
been the entity like that and it has been up to the user for deciding which of the services is to be
used. Every service has different approach to the data. In general considerations the services that are
bough from the vendors of the cloud have been the private services that the resources and the data
have been belonging to. This could not be accessed to the others till it is made so.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4CLOUD COMPUTING- DATA STORAGE
3. Research Questions
How could the files be stored in the cloud? Why should we need to store the files in the
cloud?
Have the tablets and the storages of cloud the fate of computing?
Why should we user the storage of cloud in spite of the local storages?
How has been the habits been changed by the cloud storages?
Has it been safe to store the sensitive data into the cloud?
How could we manage the risks regarding the cloud?
Has the cloud storage been meant for every kind of data?
Does the storage of cloud eradicate the necessity of the technical resources in-house?
4. Conceptual or Theoretical Framework
The cloud computing has been referring to the storage and processing of data via Internet.
The storage and computing turns to be the services instead of the physical resources. The other data
and the files could be stored in this cloud and could be accessed from any of the Internet
connections. It has been the computing style where the facilities related to the IT have been
delivered as the service. This has also been allowing the users to get access the services that are
enabled with technology from the cloud or the Internet. This is without the prior knowledge of the
expertise with or the control over this infrastructure of the technology that has been supporting them.
The cloud has been distinguishing the information resources and the applications from this
infrastructure and the methods used for delivering them. It has been the technology that has been
using the remote servers of the central and the internet to the primary data and application. This has
been done by permitting the consumers and the business to utilize the applications. This has been
3. Research Questions
How could the files be stored in the cloud? Why should we need to store the files in the
cloud?
Have the tablets and the storages of cloud the fate of computing?
Why should we user the storage of cloud in spite of the local storages?
How has been the habits been changed by the cloud storages?
Has it been safe to store the sensitive data into the cloud?
How could we manage the risks regarding the cloud?
Has the cloud storage been meant for every kind of data?
Does the storage of cloud eradicate the necessity of the technical resources in-house?
4. Conceptual or Theoretical Framework
The cloud computing has been referring to the storage and processing of data via Internet.
The storage and computing turns to be the services instead of the physical resources. The other data
and the files could be stored in this cloud and could be accessed from any of the Internet
connections. It has been the computing style where the facilities related to the IT have been
delivered as the service. This has also been allowing the users to get access the services that are
enabled with technology from the cloud or the Internet. This is without the prior knowledge of the
expertise with or the control over this infrastructure of the technology that has been supporting them.
The cloud has been distinguishing the information resources and the applications from this
infrastructure and the methods used for delivering them. It has been the technology that has been
using the remote servers of the central and the internet to the primary data and application. This has
been done by permitting the consumers and the business to utilize the applications. This has been

5CLOUD COMPUTING- DATA STORAGE
without the need of installing and has also permitted them in accessing the personal profiles at the
any computer of their chose with the Internet access (Chinyao, Yahsueh & Mingchang, 2011).
5. Literature Review
The paper has been completed for identifying the development and advantages in the future
as the storage of the cloud possesses the efficiency to impart greater influence. This could be both
positively or negatively on the fate of the IT. There have been various advantages to use the cloud
computing. This has been including the security, reliability and scalability. There have been
numerous problems like the performance, availability, privacy and trusts (James W. Smith, 2007).
The cloud computing has been seen by various expertise as the future wave in the field of
information technology for the government, organization and the people. Moreover, by the reduction
of the operation costs the cloud technologists turned the basic platform of the innovation of radical
business and the latest business models. This has also been including the important enhancements in
effectiveness of the people utilizing the information technologies of the current days for most of the
world. The cloud computing like various other latest technologies has also been generating the
potential risks and the disruptive possibilities. The case that the cloud computing has been including
the aggregation of the power of computing and the information have turned into the source of rising
concern (Joanna Gordon, ChiemiHayshi & Dan Elron, 2010).
The cloud computing has been encompassing many things from the consumer oriented file
and media compression to the conventional desktop replacement into an entire infrastructure of any
company. Regarding this paper, the cloud computing would denote the delivery of the software,
application platforms, storage and compute as the set of the services supporting the business
application of any company. Unlike the necessity of the IT departments for allocating and managing
without the need of installing and has also permitted them in accessing the personal profiles at the
any computer of their chose with the Internet access (Chinyao, Yahsueh & Mingchang, 2011).
5. Literature Review
The paper has been completed for identifying the development and advantages in the future
as the storage of the cloud possesses the efficiency to impart greater influence. This could be both
positively or negatively on the fate of the IT. There have been various advantages to use the cloud
computing. This has been including the security, reliability and scalability. There have been
numerous problems like the performance, availability, privacy and trusts (James W. Smith, 2007).
The cloud computing has been seen by various expertise as the future wave in the field of
information technology for the government, organization and the people. Moreover, by the reduction
of the operation costs the cloud technologists turned the basic platform of the innovation of radical
business and the latest business models. This has also been including the important enhancements in
effectiveness of the people utilizing the information technologies of the current days for most of the
world. The cloud computing like various other latest technologies has also been generating the
potential risks and the disruptive possibilities. The case that the cloud computing has been including
the aggregation of the power of computing and the information have turned into the source of rising
concern (Joanna Gordon, ChiemiHayshi & Dan Elron, 2010).
The cloud computing has been encompassing many things from the consumer oriented file
and media compression to the conventional desktop replacement into an entire infrastructure of any
company. Regarding this paper, the cloud computing would denote the delivery of the software,
application platforms, storage and compute as the set of the services supporting the business
application of any company. Unlike the necessity of the IT departments for allocating and managing
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6CLOUD COMPUTING- DATA STORAGE
the virtual and physical machines for supporting the business resources and applications, the cloud is
different. It has been allowing the IT to get delivered by the set of services that has been abstract.
They have been permitting to share the economies and resources of scale (Brian Jimerson, 2012).
The cloud computing has been regarding as the fifth utility after the water, gas, electricity
and communication and it has been the promising paradigm to deliver the IT services as the
computing usages. The paper has presented the comprehensive comparison of various aspects of the
platforms of the cloud. In the present cloud till we have the issues like the data privacy and security
and the continuous availability. In the present cloud scenario the user could not recognize the status
of their data. The data could be used by others for specific reasons. The future work of us lies in the
sectors of data scheduling and data replication in the cloud computing and the assimilation of their
scheduling and replication techniques (Nawsher et al., 2012).
6. Methodology
6.1 Data collection or systems design methods
Reviewing of the articles and the white papers has been useful for Data collection.
Additionally there have been various approaches like the Questioner, the interviews, the case studies,
the observing and recording of the well defined events, the surveys, the focus Groups and the diaries.
6.2 Ethical Issues
There could be various ethical issues, but those have been relying on the research. Few
important things that has been under the in depth consideration such as the misrepresenting,
falsifying and fabricating of the research data has been promoting the reality. Nest, as the research
has been including various deal of coronation and cooperation among the various people in
numerous institutions and disciplines, the ethical standards have been promoting the values. These
the virtual and physical machines for supporting the business resources and applications, the cloud is
different. It has been allowing the IT to get delivered by the set of services that has been abstract.
They have been permitting to share the economies and resources of scale (Brian Jimerson, 2012).
The cloud computing has been regarding as the fifth utility after the water, gas, electricity
and communication and it has been the promising paradigm to deliver the IT services as the
computing usages. The paper has presented the comprehensive comparison of various aspects of the
platforms of the cloud. In the present cloud till we have the issues like the data privacy and security
and the continuous availability. In the present cloud scenario the user could not recognize the status
of their data. The data could be used by others for specific reasons. The future work of us lies in the
sectors of data scheduling and data replication in the cloud computing and the assimilation of their
scheduling and replication techniques (Nawsher et al., 2012).
6. Methodology
6.1 Data collection or systems design methods
Reviewing of the articles and the white papers has been useful for Data collection.
Additionally there have been various approaches like the Questioner, the interviews, the case studies,
the observing and recording of the well defined events, the surveys, the focus Groups and the diaries.
6.2 Ethical Issues
There could be various ethical issues, but those have been relying on the research. Few
important things that has been under the in depth consideration such as the misrepresenting,
falsifying and fabricating of the research data has been promoting the reality. Nest, as the research
has been including various deal of coronation and cooperation among the various people in
numerous institutions and disciplines, the ethical standards have been promoting the values. These
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7CLOUD COMPUTING- DATA STORAGE
values have been important for collaborative tasks like the fairness, mutual respect, accountability
and trusts. Additionally things such as the patenting and copyright policies, confidentiality rules and
the data sharing policies have been kept in mind while writing this research (David B. Resnik, J.D,
2011)
More challenges that have been originating are as follows:
Collection of data without the appropriate controls
The omitting of controls that the others pointed out
The using of the improper sample sizes
The selecting of what to view
The failing to see the events or the non-events
The failing in preserving the data for the sufficient quantity of time
The editing or the making up of data
The reporting of only the positive or the significant results
The using of other people's data or words
The changing of the hypothesis of this paper
The failing to report the negative findings
6.3 Analysis of data
We have reviewed the documents and the relevant paper. We have collected every
appropriate data from the online libraries. We have also used the other form of methods to collect
data like the survey and the interviews. Next, we filtered the data collected and then finalized the
most important and relevant material for this topic. The visual display of this data would be in the
form of a chart or in any histogram form. Through this process we could recognize the important
things over which we could make the enhancements in this paper.
values have been important for collaborative tasks like the fairness, mutual respect, accountability
and trusts. Additionally things such as the patenting and copyright policies, confidentiality rules and
the data sharing policies have been kept in mind while writing this research (David B. Resnik, J.D,
2011)
More challenges that have been originating are as follows:
Collection of data without the appropriate controls
The omitting of controls that the others pointed out
The using of the improper sample sizes
The selecting of what to view
The failing to see the events or the non-events
The failing in preserving the data for the sufficient quantity of time
The editing or the making up of data
The reporting of only the positive or the significant results
The using of other people's data or words
The changing of the hypothesis of this paper
The failing to report the negative findings
6.3 Analysis of data
We have reviewed the documents and the relevant paper. We have collected every
appropriate data from the online libraries. We have also used the other form of methods to collect
data like the survey and the interviews. Next, we filtered the data collected and then finalized the
most important and relevant material for this topic. The visual display of this data would be in the
form of a chart or in any histogram form. Through this process we could recognize the important
things over which we could make the enhancements in this paper.

8CLOUD COMPUTING- DATA STORAGE
7. Project Plan
7.1 Deliverables (Conclusions, Recommendations, Software code etc)
Developing the in-depth project plan. This is done by using the project management software
like the Microsoft project Pro with the WBS and the Gantt chart
Developing the Literature Review where the new technology is identified along with the
special features in this new invention.
Developing the research report on the topic selected.
7.2 Risk Analysis.
The initial step has been in recognizing that the risk is there as the result of the uncertainty.
However, there has been some risk which has been in concern in this paper all through.
Establishing the plan in dealing with the risk as they occur
Initiating the further investigation for reducing the uncertainty by better information
Reviewing of the past document and then selecting information which is relevant
Understand the options
The Risk profiles regarding various contexts that are the popular subjects for the academic
papers like doing a survey, grinding some numbers and getting the publication credit. They
have been typically riveting the reading. However they have been well worth in reviewing
(Aristide Ouédraogo, AmelaGroso & Thierry Meyer, 2011).
These points are to be considered in the research that must be discussed in more details.
7. Project Plan
7.1 Deliverables (Conclusions, Recommendations, Software code etc)
Developing the in-depth project plan. This is done by using the project management software
like the Microsoft project Pro with the WBS and the Gantt chart
Developing the Literature Review where the new technology is identified along with the
special features in this new invention.
Developing the research report on the topic selected.
7.2 Risk Analysis.
The initial step has been in recognizing that the risk is there as the result of the uncertainty.
However, there has been some risk which has been in concern in this paper all through.
Establishing the plan in dealing with the risk as they occur
Initiating the further investigation for reducing the uncertainty by better information
Reviewing of the past document and then selecting information which is relevant
Understand the options
The Risk profiles regarding various contexts that are the popular subjects for the academic
papers like doing a survey, grinding some numbers and getting the publication credit. They
have been typically riveting the reading. However they have been well worth in reviewing
(Aristide Ouédraogo, AmelaGroso & Thierry Meyer, 2011).
These points are to be considered in the research that must be discussed in more details.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9CLOUD COMPUTING- DATA STORAGE
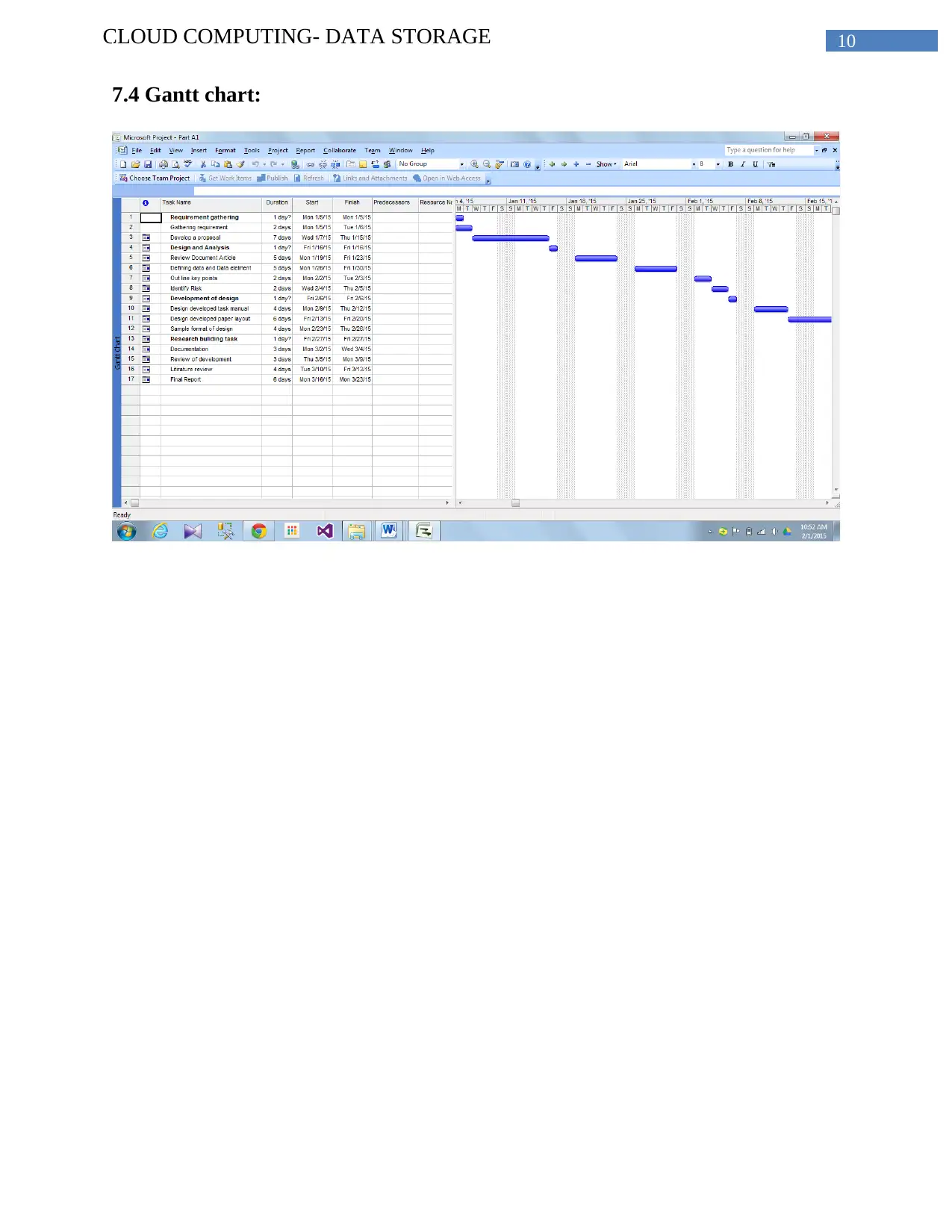
7.3 Work breakdown structure (WBS)
Requirement Gathering
Gathering of the requirements of this project-2 days.
Developing the Proposal -7 days
Design and Analysis
Reviewing the document and the articles - 5days
Defining the required information and the data element – 5days
Outlining the Key points- 2days
Identifying the Risk- 4days
Research Design Task
Designing the research task manuals– 4days
Designing the layout of the research paper- 6days
Designing the sample format. It has considered how the data or information has been going
to the document in the paper.- 4 days
Research Build Task
Documenting the information collected -3days
Reviewing of the research paper for various times and investigating the error -3days
Developing the literature review - 4days
Developing the final report with the appropriate referencing- 6days
7.3 Work breakdown structure (WBS)
Requirement Gathering
Gathering of the requirements of this project-2 days.
Developing the Proposal -7 days
Design and Analysis
Reviewing the document and the articles - 5days
Defining the required information and the data element – 5days
Outlining the Key points- 2days
Identifying the Risk- 4days
Research Design Task
Designing the research task manuals– 4days
Designing the layout of the research paper- 6days
Designing the sample format. It has considered how the data or information has been going
to the document in the paper.- 4 days
Research Build Task
Documenting the information collected -3days
Reviewing of the research paper for various times and investigating the error -3days
Developing the literature review - 4days
Developing the final report with the appropriate referencing- 6days
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10CLOUD COMPUTING- DATA STORAGE
7.4 Gantt chart:
7.4 Gantt chart:

11CLOUD COMPUTING- DATA STORAGE
8. References:
Aristide Ouédraogo, AmelaGroso, & Thierry Meyer.(2011).Risk analysis in research environment.
Retrieve from EBook Database.
Brian Jimerson.(2012). Software Architecture for High Availability in the Cloud. Retrieve from
EBook Library
Chinyao Low, Yahsueh Chen &Mingchang Wu.(2011).Understanding the determinants of cloud
computing adoption .Retrieve from EBook Database Library.
David B. Resnik, J.D.(2011). What is Ethics in Research & Why is it Important? Retrieve from
EBook database of National institute of environmental and health sciences
James W. Smith.(2007). Green Cloud: A literature review of Energy-Aware Computing. Retrieve
from EBook Library
Joanna Gordon, ChiemiHayshi& Dan Elron.(2010).Exploring the Future of Cloud Computing:
Riding the Next Wave of Technology-Driven Transformation. Retrieve from EBook Library.
Nawsher Khan, A.Noraziah, Elrasheed I. Ismail, Mustafa Mat Deris,&TututHerawan.(2012). DOI:
10.4018/jeei.2012040104, ISSN: 1947-8585, EISSN: 1947-8593 .
8. References:
Aristide Ouédraogo, AmelaGroso, & Thierry Meyer.(2011).Risk analysis in research environment.
Retrieve from EBook Database.
Brian Jimerson.(2012). Software Architecture for High Availability in the Cloud. Retrieve from
EBook Library
Chinyao Low, Yahsueh Chen &Mingchang Wu.(2011).Understanding the determinants of cloud
computing adoption .Retrieve from EBook Database Library.
David B. Resnik, J.D.(2011). What is Ethics in Research & Why is it Important? Retrieve from
EBook database of National institute of environmental and health sciences
James W. Smith.(2007). Green Cloud: A literature review of Energy-Aware Computing. Retrieve
from EBook Library
Joanna Gordon, ChiemiHayshi& Dan Elron.(2010).Exploring the Future of Cloud Computing:
Riding the Next Wave of Technology-Driven Transformation. Retrieve from EBook Library.
Nawsher Khan, A.Noraziah, Elrasheed I. Ismail, Mustafa Mat Deris,&TututHerawan.(2012). DOI:
10.4018/jeei.2012040104, ISSN: 1947-8585, EISSN: 1947-8593 .
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




