CSU Literature Review: Data Security Risk Mitigation in Cloud VMs
VerifiedAdded on 2024/06/28
|85
|8688
|398
Literature Review
AI Summary
This literature review investigates data security risks and mitigation strategies in cloud computing through virtual machine monitoring, drawing upon five journal papers from the CSU Library. It examines various techniques, including firewalls, intrusion detection systems, and Virtual Machine Introspection (VMI), focusing on challenges in cloud service layers and virtualization. The review covers solutions like Crypto-Cloud architecture, which aims to enhance security and scalability, and OpCloudSec, designed for IoT security in software-defined wireless networks. Key aspects include data leakage prevention, attack detection mechanisms, and the integration of machine learning for improved security. The papers also address virtual machine placement schemes and migration strategies, highlighting the importance of secure data storage and efficient resource management in cloud environments. The review identifies limitations and future research directions, such as enhancing detection algorithms and improving the performance of data security systems.

Literature Review (Secondary Research)
Student Name& CSU ID
Project Topic Title Data Security risk mitigation in the cloud through virtual machine monitoring
1
Student Name& CSU ID
Project Topic Title Data Security risk mitigation in the cloud through virtual machine monitoring
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
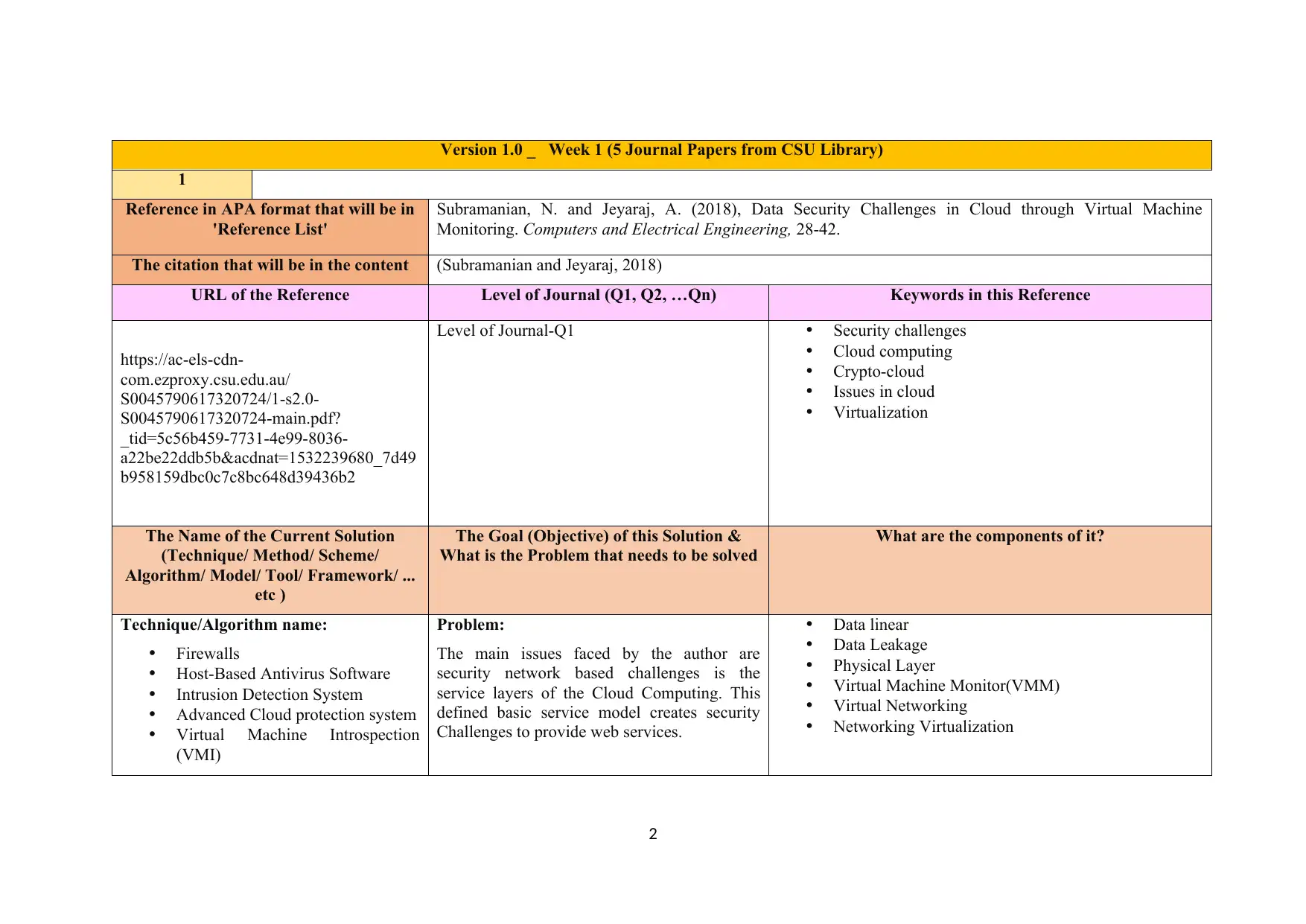
Version 1.0 _ Week 1 (5 Journal Papers from CSU Library)
1
Reference in APA format that will be in
'Reference List'
Subramanian, N. and Jeyaraj, A. (2018), Data Security Challenges in Cloud through Virtual Machine
Monitoring. Computers and Electrical Engineering, 28-42.
The citation that will be in the content (Subramanian and Jeyaraj, 2018)
URL of the Reference Level of Journal (Q1, Q2, …Qn) Keywords in this Reference
https://ac-els-cdn-
com.ezproxy.csu.edu.au/
S0045790617320724/1-s2.0-
S0045790617320724-main.pdf?
_tid=5c56b459-7731-4e99-8036-
a22be22ddb5b&acdnat=1532239680_7d49
b958159dbc0c7c8bc648d39436b2
Level of Journal-Q1 Security challenges
Cloud computing
Crypto-cloud
Issues in cloud
Virtualization
The Name of the Current Solution
(Technique/ Method/ Scheme/
Algorithm/ Model/ Tool/ Framework/ ...
etc )
The Goal (Objective) of this Solution &
What is the Problem that needs to be solved
What are the components of it?
Technique/Algorithm name:
Firewalls
Host-Based Antivirus Software
Intrusion Detection System
Advanced Cloud protection system
Virtual Machine Introspection
(VMI)
Problem:
The main issues faced by the author are
security network based challenges is the
service layers of the Cloud Computing. This
defined basic service model creates security
Challenges to provide web services.
Data linear
Data Leakage
Physical Layer
Virtual Machine Monitor(VMM)
Virtual Networking
Networking Virtualization
2
1
Reference in APA format that will be in
'Reference List'
Subramanian, N. and Jeyaraj, A. (2018), Data Security Challenges in Cloud through Virtual Machine
Monitoring. Computers and Electrical Engineering, 28-42.
The citation that will be in the content (Subramanian and Jeyaraj, 2018)
URL of the Reference Level of Journal (Q1, Q2, …Qn) Keywords in this Reference
https://ac-els-cdn-
com.ezproxy.csu.edu.au/
S0045790617320724/1-s2.0-
S0045790617320724-main.pdf?
_tid=5c56b459-7731-4e99-8036-
a22be22ddb5b&acdnat=1532239680_7d49
b958159dbc0c7c8bc648d39436b2
Level of Journal-Q1 Security challenges
Cloud computing
Crypto-cloud
Issues in cloud
Virtualization
The Name of the Current Solution
(Technique/ Method/ Scheme/
Algorithm/ Model/ Tool/ Framework/ ...
etc )
The Goal (Objective) of this Solution &
What is the Problem that needs to be solved
What are the components of it?
Technique/Algorithm name:
Firewalls
Host-Based Antivirus Software
Intrusion Detection System
Advanced Cloud protection system
Virtual Machine Introspection
(VMI)
Problem:
The main issues faced by the author are
security network based challenges is the
service layers of the Cloud Computing. This
defined basic service model creates security
Challenges to provide web services.
Data linear
Data Leakage
Physical Layer
Virtual Machine Monitor(VMM)
Virtual Networking
Networking Virtualization
2
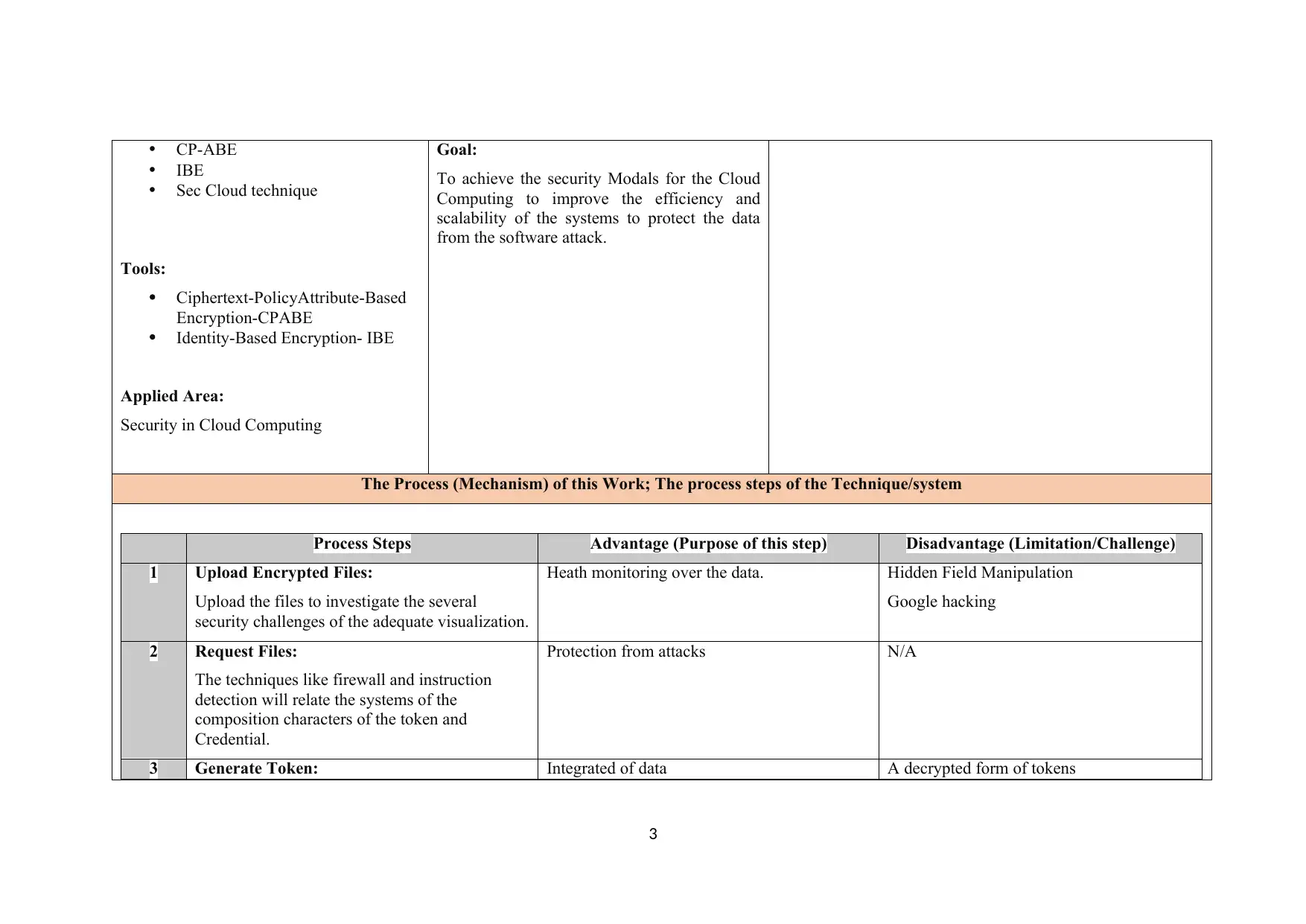
CP-ABE
IBE
Sec Cloud technique
Tools:
Ciphertext-PolicyAttribute-Based
Encryption-CPABE
Identity-Based Encryption- IBE
Applied Area:
Security in Cloud Computing
Goal:
To achieve the security Modals for the Cloud
Computing to improve the efficiency and
scalability of the systems to protect the data
from the software attack.
The Process (Mechanism) of this Work; The process steps of the Technique/system
Process Steps Advantage (Purpose of this step) Disadvantage (Limitation/Challenge)
1 Upload Encrypted Files:
Upload the files to investigate the several
security challenges of the adequate visualization.
Heath monitoring over the data. Hidden Field Manipulation
Google hacking
2 Request Files:
The techniques like firewall and instruction
detection will relate the systems of the
composition characters of the token and
Credential.
Protection from attacks N/A
3 Generate Token: Integrated of data A decrypted form of tokens
3
IBE
Sec Cloud technique
Tools:
Ciphertext-PolicyAttribute-Based
Encryption-CPABE
Identity-Based Encryption- IBE
Applied Area:
Security in Cloud Computing
Goal:
To achieve the security Modals for the Cloud
Computing to improve the efficiency and
scalability of the systems to protect the data
from the software attack.
The Process (Mechanism) of this Work; The process steps of the Technique/system
Process Steps Advantage (Purpose of this step) Disadvantage (Limitation/Challenge)
1 Upload Encrypted Files:
Upload the files to investigate the several
security challenges of the adequate visualization.
Heath monitoring over the data. Hidden Field Manipulation
Google hacking
2 Request Files:
The techniques like firewall and instruction
detection will relate the systems of the
composition characters of the token and
Credential.
Protection from attacks N/A
3 Generate Token: Integrated of data A decrypted form of tokens
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
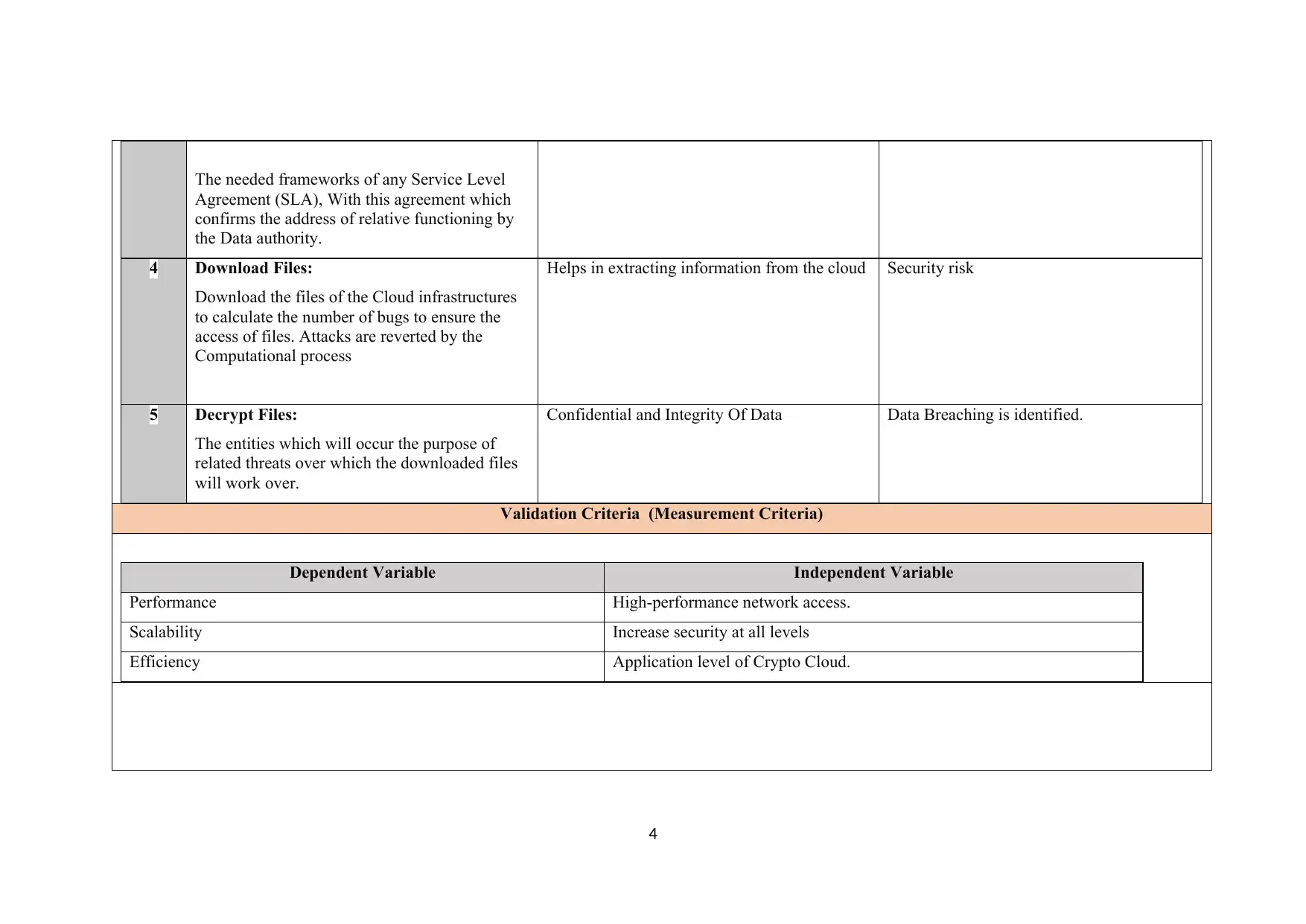
The needed frameworks of any Service Level
Agreement (SLA), With this agreement which
confirms the address of relative functioning by
the Data authority.
4 Download Files:
Download the files of the Cloud infrastructures
to calculate the number of bugs to ensure the
access of files. Attacks are reverted by the
Computational process
Helps in extracting information from the cloud Security risk
5 Decrypt Files:
The entities which will occur the purpose of
related threats over which the downloaded files
will work over.
Confidential and Integrity Of Data Data Breaching is identified.
Validation Criteria (Measurement Criteria)
Dependent Variable Independent Variable
Performance High-performance network access.
Scalability Increase security at all levels
Efficiency Application level of Crypto Cloud.
4
Agreement (SLA), With this agreement which
confirms the address of relative functioning by
the Data authority.
4 Download Files:
Download the files of the Cloud infrastructures
to calculate the number of bugs to ensure the
access of files. Attacks are reverted by the
Computational process
Helps in extracting information from the cloud Security risk
5 Decrypt Files:
The entities which will occur the purpose of
related threats over which the downloaded files
will work over.
Confidential and Integrity Of Data Data Breaching is identified.
Validation Criteria (Measurement Criteria)
Dependent Variable Independent Variable
Performance High-performance network access.
Scalability Increase security at all levels
Efficiency Application level of Crypto Cloud.
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
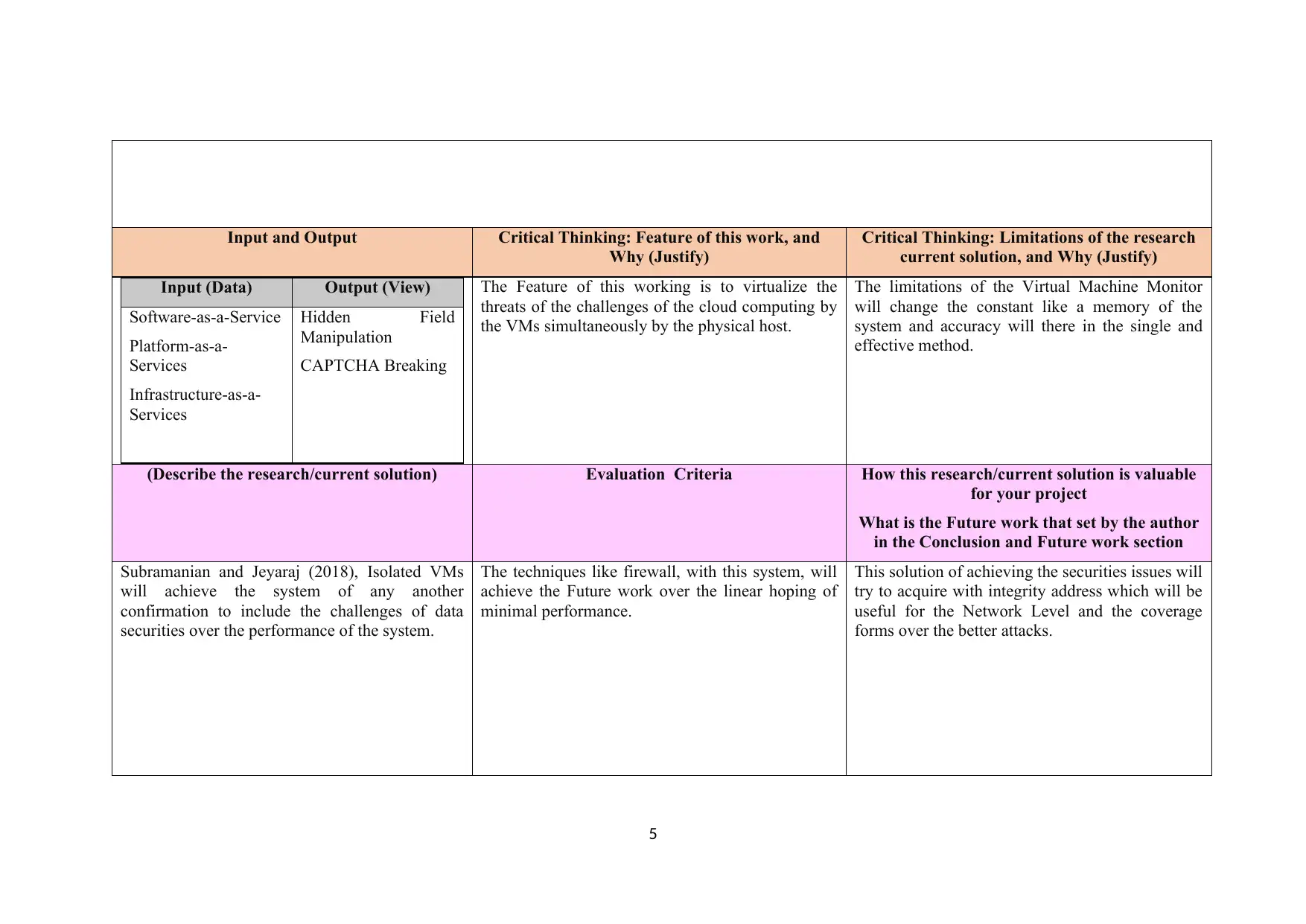
Input and Output Critical Thinking: Feature of this work, and
Why (Justify)
Critical Thinking: Limitations of the research
current solution, and Why (Justify)
Input (Data) Output (View)
Software-as-a-Service
Platform-as-a-
Services
Infrastructure-as-a-
Services
Hidden Field
Manipulation
CAPTCHA Breaking
The Feature of this working is to virtualize the
threats of the challenges of the cloud computing by
the VMs simultaneously by the physical host.
The limitations of the Virtual Machine Monitor
will change the constant like a memory of the
system and accuracy will there in the single and
effective method.
(Describe the research/current solution) Evaluation Criteria How this research/current solution is valuable
for your project
What is the Future work that set by the author
in the Conclusion and Future work section
Subramanian and Jeyaraj (2018), Isolated VMs
will achieve the system of any another
confirmation to include the challenges of data
securities over the performance of the system.
The techniques like firewall, with this system, will
achieve the Future work over the linear hoping of
minimal performance.
This solution of achieving the securities issues will
try to acquire with integrity address which will be
useful for the Network Level and the coverage
forms over the better attacks.
5
Why (Justify)
Critical Thinking: Limitations of the research
current solution, and Why (Justify)
Input (Data) Output (View)
Software-as-a-Service
Platform-as-a-
Services
Infrastructure-as-a-
Services
Hidden Field
Manipulation
CAPTCHA Breaking
The Feature of this working is to virtualize the
threats of the challenges of the cloud computing by
the VMs simultaneously by the physical host.
The limitations of the Virtual Machine Monitor
will change the constant like a memory of the
system and accuracy will there in the single and
effective method.
(Describe the research/current solution) Evaluation Criteria How this research/current solution is valuable
for your project
What is the Future work that set by the author
in the Conclusion and Future work section
Subramanian and Jeyaraj (2018), Isolated VMs
will achieve the system of any another
confirmation to include the challenges of data
securities over the performance of the system.
The techniques like firewall, with this system, will
achieve the Future work over the linear hoping of
minimal performance.
This solution of achieving the securities issues will
try to acquire with integrity address which will be
useful for the Network Level and the coverage
forms over the better attacks.
5
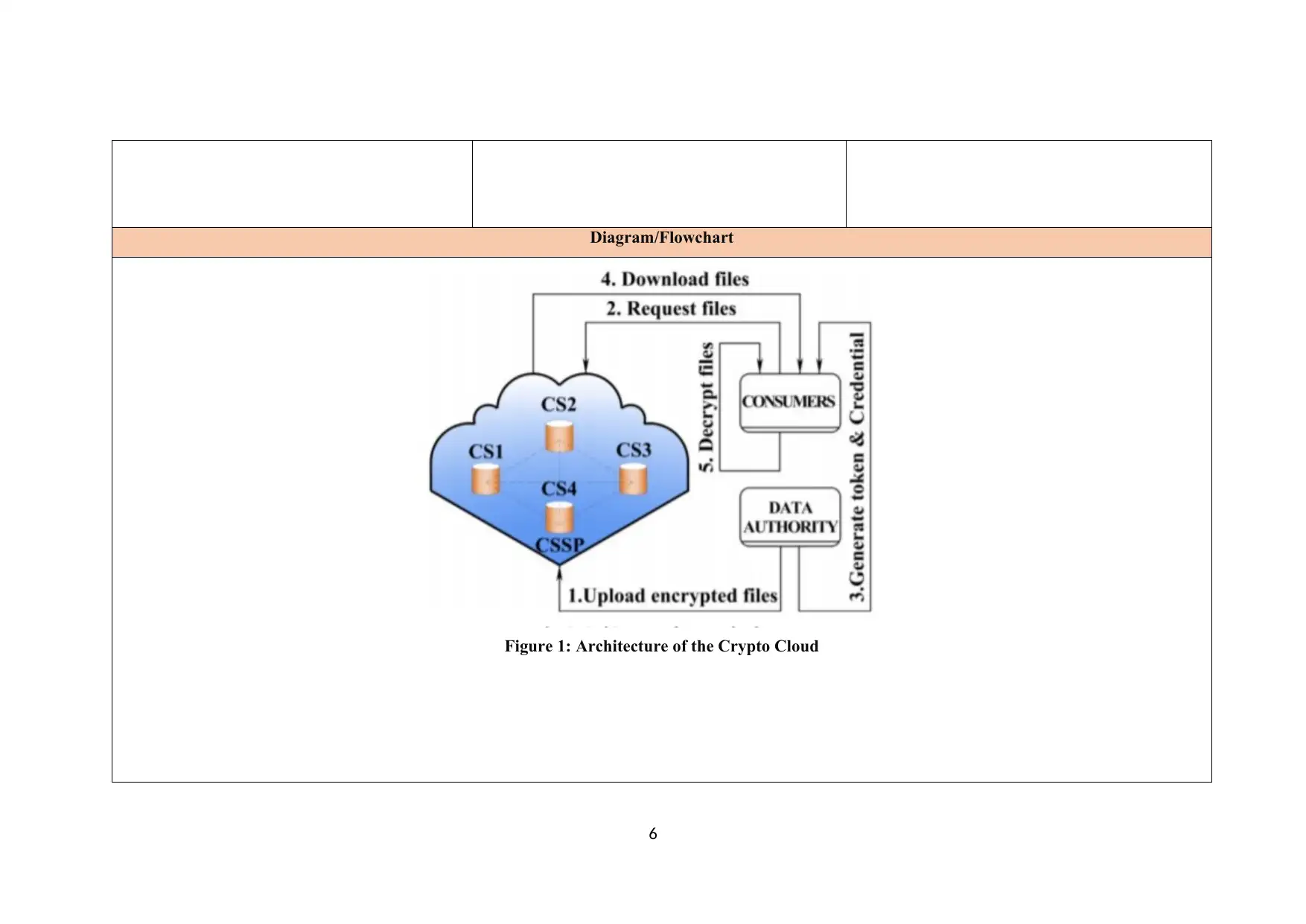
Diagram/Flowchart
Figure 1: Architecture of the Crypto Cloud
6
Figure 1: Architecture of the Crypto Cloud
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
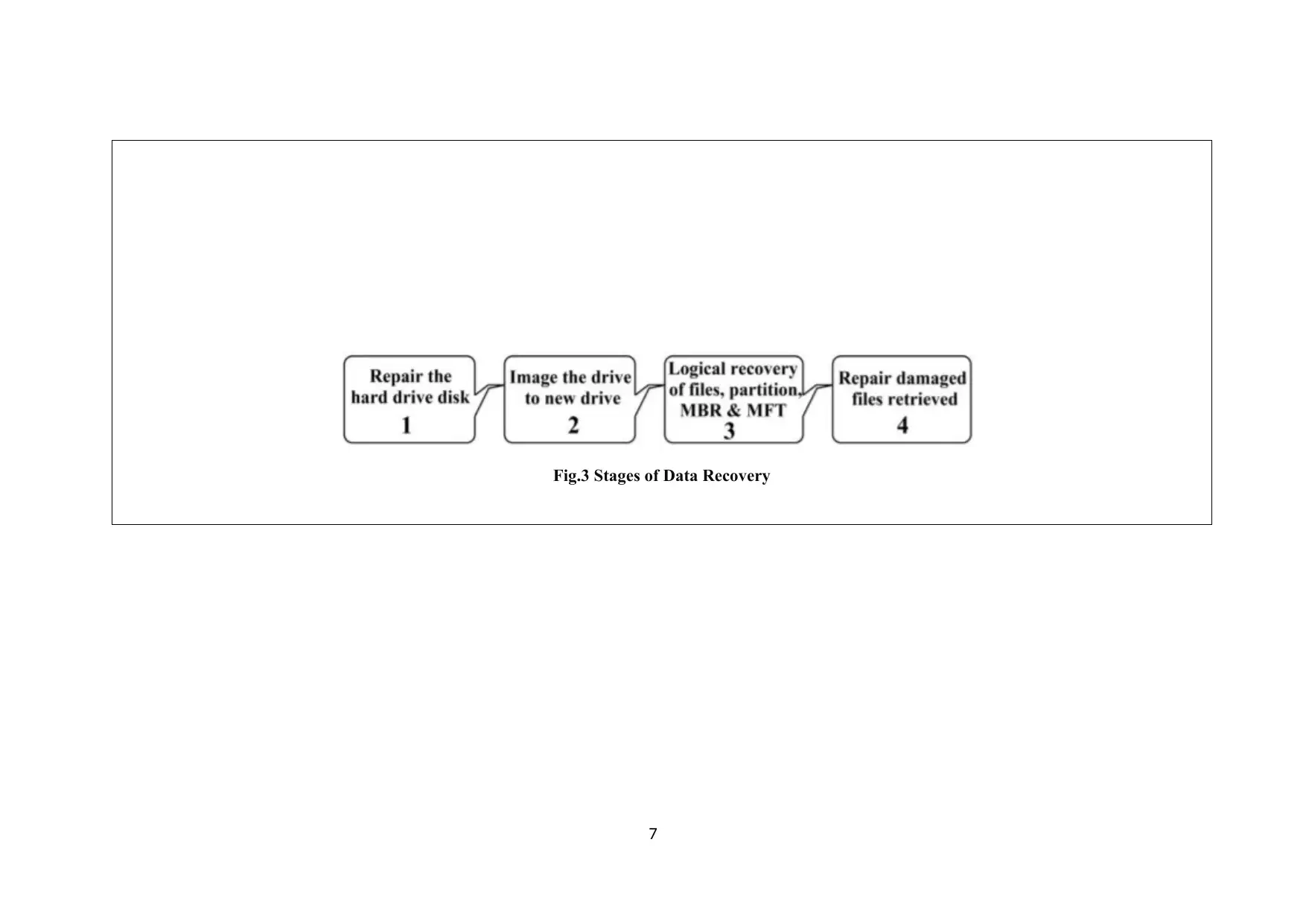
Fig.3 Stages of Data Recovery
7
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
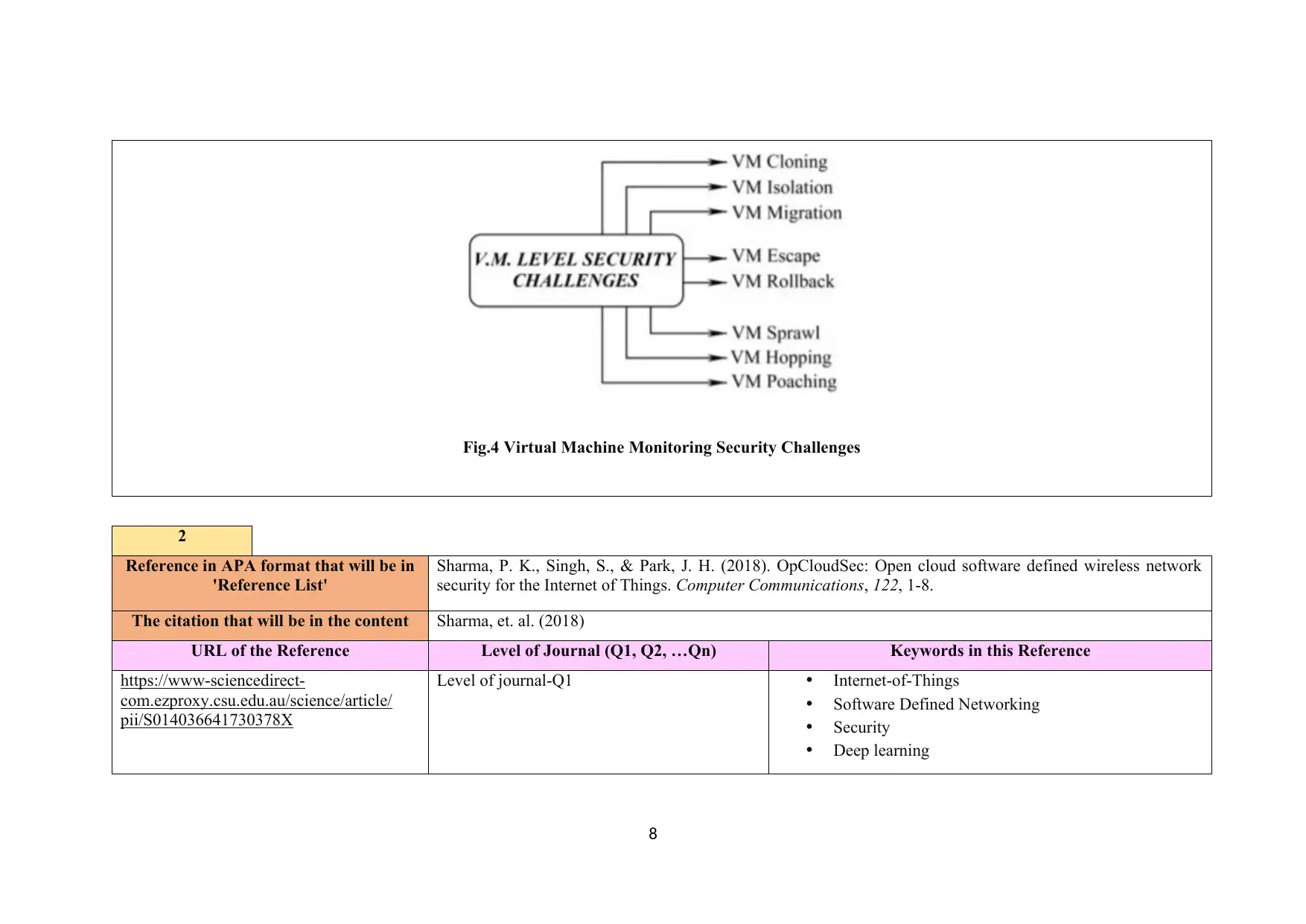
Fig.4 Virtual Machine Monitoring Security Challenges
2
Reference in APA format that will be in
'Reference List'
Sharma, P. K., Singh, S., & Park, J. H. (2018). OpCloudSec: Open cloud software defined wireless network
security for the Internet of Things. Computer Communications, 122, 1-8.
The citation that will be in the content Sharma, et. al. (2018)
URL of the Reference Level of Journal (Q1, Q2, …Qn) Keywords in this Reference
https://www-sciencedirect-
com.ezproxy.csu.edu.au/science/article/
pii/S014036641730378X
Level of journal-Q1 Internet-of-Things
Software Defined Networking
Security
Deep learning
8
2
Reference in APA format that will be in
'Reference List'
Sharma, P. K., Singh, S., & Park, J. H. (2018). OpCloudSec: Open cloud software defined wireless network
security for the Internet of Things. Computer Communications, 122, 1-8.
The citation that will be in the content Sharma, et. al. (2018)
URL of the Reference Level of Journal (Q1, Q2, …Qn) Keywords in this Reference
https://www-sciencedirect-
com.ezproxy.csu.edu.au/science/article/
pii/S014036641730378X
Level of journal-Q1 Internet-of-Things
Software Defined Networking
Security
Deep learning
8
The Name of the Current Solution
(Technique/ Method/ Scheme/
Algorithm/ Model/ Tool/ Framework/ ...
etc )
The Goal (Objective) of this Solution &
What is the Problem that needs to be solved
What are the components of it?
Technique/Algorithm name: security
detection techniques, machine learning
techniques, attack prevention model
Tools: mobile application
Applied Area: cloud computing
Problem: The challenges of this solution is in
terms of security, reliability, and flexibility that
these cutting-edge frameworks.
Goal: The goal of this paper is to create a new
network paradigm for meeting the security
challenges
Private cloud
Networking device
The Process (Mechanism) of this Work; The process steps of the Technique/system
Process Steps Advantage (Purpose of this step) Disadvantage (Limitation/Challenge)
1 application logic
Data mapping is created in the application logic
module
Data request from one area to another N/A
2 device registry
Device is recorded with the device registry
Insurance service app connection N/A
3 data store
The configured application are stored in the
system
Support in setting up of application N/A
Validation Criteria (Measurement Criteria)
Dependent Variable Independent Variable
mobile app Cloud service
9
(Technique/ Method/ Scheme/
Algorithm/ Model/ Tool/ Framework/ ...
etc )
The Goal (Objective) of this Solution &
What is the Problem that needs to be solved
What are the components of it?
Technique/Algorithm name: security
detection techniques, machine learning
techniques, attack prevention model
Tools: mobile application
Applied Area: cloud computing
Problem: The challenges of this solution is in
terms of security, reliability, and flexibility that
these cutting-edge frameworks.
Goal: The goal of this paper is to create a new
network paradigm for meeting the security
challenges
Private cloud
Networking device
The Process (Mechanism) of this Work; The process steps of the Technique/system
Process Steps Advantage (Purpose of this step) Disadvantage (Limitation/Challenge)
1 application logic
Data mapping is created in the application logic
module
Data request from one area to another N/A
2 device registry
Device is recorded with the device registry
Insurance service app connection N/A
3 data store
The configured application are stored in the
system
Support in setting up of application N/A
Validation Criteria (Measurement Criteria)
Dependent Variable Independent Variable
mobile app Cloud service
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
security attack algorithms Detection
Input and Output Critical Thinking: Feature of this work, and
Why (Justify)
Critical Thinking: Limitations of the research
current solution, and Why (Justify)
Input (Data) Output (View)
The connection of IoT
devices into the cloud
system
Data protection of the
IoT application
The feature of this work is that it assists in
providing on-demand self-service to the customers.
The scalability problem is the main limitation of
the current solution.
(Describe the research/current solution) Evaluation Criteria How this research/current solution is valuable
for your project
Sharma, et. al. (2018) suggested OpCloudSec
architecture model for resolving the security
challenges effectively
The end user of the solution is the user who is using
IoT application for their daily use
This research is essential for the project because it
provides a new model for resolving the security
challenges
Diagram/Flowchart
10
Input and Output Critical Thinking: Feature of this work, and
Why (Justify)
Critical Thinking: Limitations of the research
current solution, and Why (Justify)
Input (Data) Output (View)
The connection of IoT
devices into the cloud
system
Data protection of the
IoT application
The feature of this work is that it assists in
providing on-demand self-service to the customers.
The scalability problem is the main limitation of
the current solution.
(Describe the research/current solution) Evaluation Criteria How this research/current solution is valuable
for your project
Sharma, et. al. (2018) suggested OpCloudSec
architecture model for resolving the security
challenges effectively
The end user of the solution is the user who is using
IoT application for their daily use
This research is essential for the project because it
provides a new model for resolving the security
challenges
Diagram/Flowchart
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
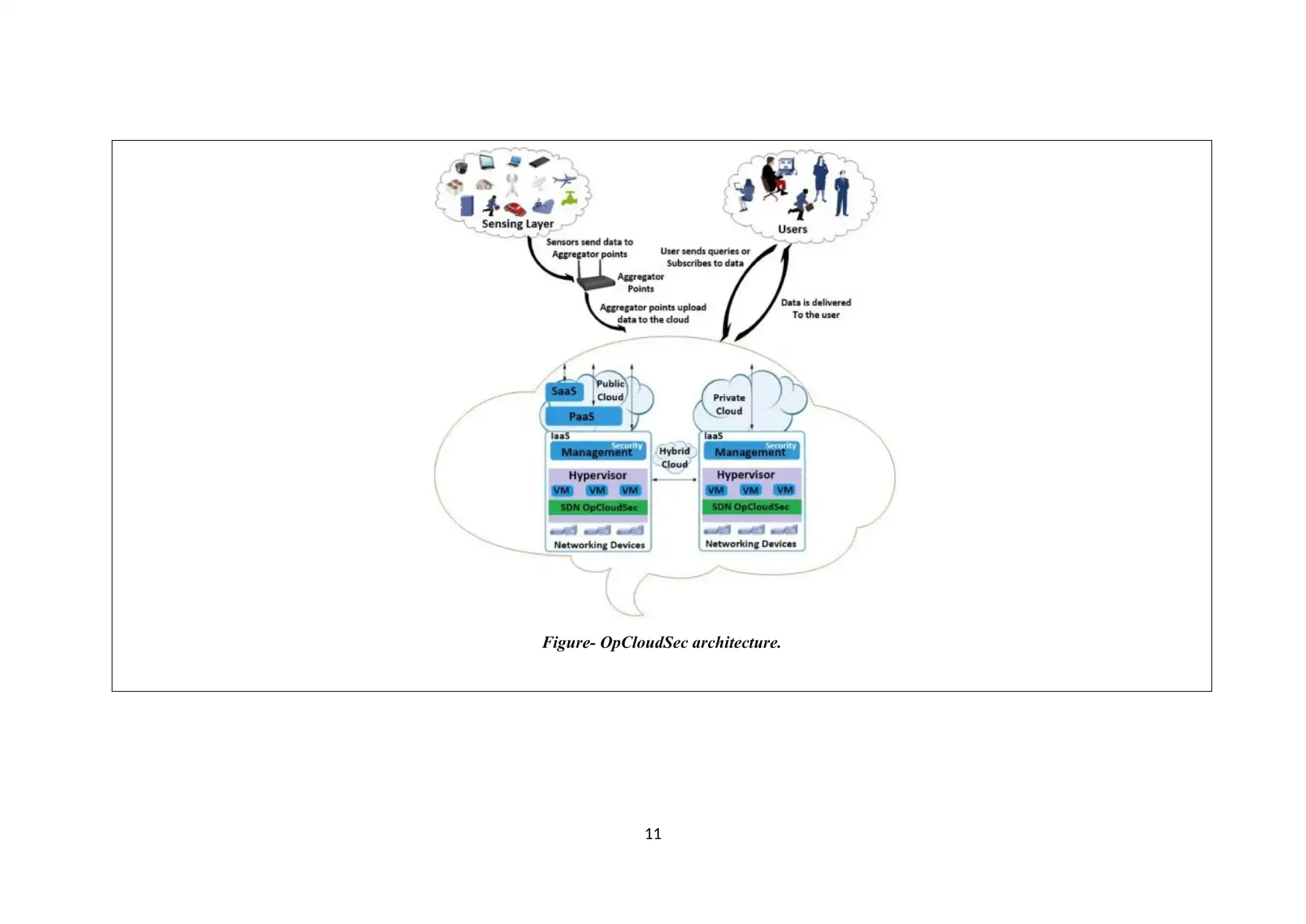
Figure- OpCloudSec architecture.
11
11
2
Reference in APA format that will be in
'Reference List'
Sharma, P. K., Singh, S., & Park, J. H. (2018). OpCloudSec: Open cloud software defined wireless network
security for the Internet of Things. Computer Communications, 122, 1-8.
The citation that will be in the content (Sharma, et. al., 2018)
URL of the Reference Level of Journal (Q1, Q2, …Qn) Keywords in this Reference
https://ac-els-cdn-
com.ezproxy.csu.edu.au/
S014036641730378X/1-s2.0-
S014036641730378X-main.pdf?
_tid=75a294e7-e96c-4627-b1a7-
e8670fb95496&acdnat=1532255858_4aad
de18ccd985c398d9c5c75d59e6ea
Level of journal-Q1 Internet-of-Things
Software Defined
Networking Security
Deep learning
The Name of the Current Solution
(Technique/ Method/ Scheme/
Algorithm/ Model/ Tool/ Framework/ ...
etc )
The Goal (Objective) of this Solution &
What is the Problem that needs to be solved
What are the components of it?
Technique/Algorithm name:
Intrusion Detection Systems (IDSs)
Machine learning techniques
Like self-organizing maps
Bayesian networks
Buzzy logic
Artificial neural networks
SDN platform
Problem: The problems which are a need to
solved is flexibility, security, reliability which
becomes a weapon of measure to cyber-
terrorists, hackers, and cyber-extortionists.
Goal: The goal is to identify the attacks made
in the system by monitoring the security
attacks. This technology is used to enhance the
technological flexibility to manage the security
Infrastructure-as-a-Service (IaaS)
technological flexibility
Virtual Machines (VMs)
Internet of Things (IoT)
12
Reference in APA format that will be in
'Reference List'
Sharma, P. K., Singh, S., & Park, J. H. (2018). OpCloudSec: Open cloud software defined wireless network
security for the Internet of Things. Computer Communications, 122, 1-8.
The citation that will be in the content (Sharma, et. al., 2018)
URL of the Reference Level of Journal (Q1, Q2, …Qn) Keywords in this Reference
https://ac-els-cdn-
com.ezproxy.csu.edu.au/
S014036641730378X/1-s2.0-
S014036641730378X-main.pdf?
_tid=75a294e7-e96c-4627-b1a7-
e8670fb95496&acdnat=1532255858_4aad
de18ccd985c398d9c5c75d59e6ea
Level of journal-Q1 Internet-of-Things
Software Defined
Networking Security
Deep learning
The Name of the Current Solution
(Technique/ Method/ Scheme/
Algorithm/ Model/ Tool/ Framework/ ...
etc )
The Goal (Objective) of this Solution &
What is the Problem that needs to be solved
What are the components of it?
Technique/Algorithm name:
Intrusion Detection Systems (IDSs)
Machine learning techniques
Like self-organizing maps
Bayesian networks
Buzzy logic
Artificial neural networks
SDN platform
Problem: The problems which are a need to
solved is flexibility, security, reliability which
becomes a weapon of measure to cyber-
terrorists, hackers, and cyber-extortionists.
Goal: The goal is to identify the attacks made
in the system by monitoring the security
attacks. This technology is used to enhance the
technological flexibility to manage the security
Infrastructure-as-a-Service (IaaS)
technological flexibility
Virtual Machines (VMs)
Internet of Things (IoT)
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 85
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




