Cloud Technology Fundamentals: Security Threats and Solutions Report
VerifiedAdded on 2022/09/07
|19
|3715
|23
Report
AI Summary
This report provides a comprehensive analysis of cloud technology fundamentals, focusing on security threats, vulnerabilities, and potential solutions for ABC Company's adoption of Amazon Cloud Services. The report begins with an introduction to cloud computing and its increasing adoption, highlighting the associated risks and the need for robust security measures. The discussion section delves into communication, architectural, and contractual security issues, emphasizing the challenges posed by ACS's PaaS model. It identifies threats like denial-of-service attacks, data storage vulnerabilities, and legal compliance concerns. The report then proposes security measures to mitigate these threats, including the use of VLANs, firewalls, intrusion detection systems, and advanced cloud protection systems. It also explores encryption techniques, such as substitution and transposition ciphers, and the symmetric key cryptography. The report concludes with recommendations for preventing cyber-attacks and implementing effective mitigation strategies to ensure the secure and successful implementation of cloud technology for ABC Company.

Running head: CLOUD TECHNOLOGY FUNDAMENTALS
CLOUD TECHNOLOGY FUNDAMENTALS
Name of the Student:
Name of the University:
Author Note:
CLOUD TECHNOLOGY FUNDAMENTALS
Name of the Student:
Name of the University:
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1CLOUD TECHNOLOGY FUNDAMENTALS
Table of Contents
Introduction..........................................................................................................................2
Discussion............................................................................................................................3
Cloud Technology Threats..............................................................................................3
Security Measures............................................................................................................7
Encryption Techniques....................................................................................................9
Preventing the Cyber-attacks.........................................................................................13
Mitigation Strategies......................................................................................................14
Conclusion.........................................................................................................................15
References..........................................................................................................................16
Table of Contents
Introduction..........................................................................................................................2
Discussion............................................................................................................................3
Cloud Technology Threats..............................................................................................3
Security Measures............................................................................................................7
Encryption Techniques....................................................................................................9
Preventing the Cyber-attacks.........................................................................................13
Mitigation Strategies......................................................................................................14
Conclusion.........................................................................................................................15
References..........................................................................................................................16

2CLOUD TECHNOLOGY FUNDAMENTALS
Introduction
In this modern world cloud computing technology has emerged in a gigantic manner.
Adoption of the cloud technology has increased in these recent days. Multiple businesses are
using this technology to run and develop their business. Cloud technology provides both
scalability and flexibility to the businesses and also allow them to run their business smoothly.
However, with the development of various technologies the cloud is surrounded with numerous
threats and vulnerabilities (Arora, Parashar & Transforming, 2013). These threats are highly
hazardous for any business. Any sort of data leakage or misuse of the sensitive data can hamper
the business. Thus, business can use the cloud solution to improve their business performance
but they also require high security controls to secure their sensitive data. An effective adoption of
the cloud solution in a business means that the business also adopt some tight security solutions
to secure the cloud devices.
This study mainly deals with cloud vulnerabilities and some security measures to secure
the cloud solution. The selected organization for this report is ABC Company which is planning
to adopt a cloud vendor namely, Amazon Cloud Services. This report will focus on potential
vulnerabilities of the cloud technology that can negative hamper the business of ABC Company.
However, the report also prepared a security solution for the concerned organization which can
be used to secure the cloud solution. An effective adoption of the cloud vendor will help the
concerned organization to achieve its business goals. The report also described some encryption
methods that can be used to secure the proposed cloud solution for the concerned organization
and also recommend an encryption technique that is appropriate for the business.
Introduction
In this modern world cloud computing technology has emerged in a gigantic manner.
Adoption of the cloud technology has increased in these recent days. Multiple businesses are
using this technology to run and develop their business. Cloud technology provides both
scalability and flexibility to the businesses and also allow them to run their business smoothly.
However, with the development of various technologies the cloud is surrounded with numerous
threats and vulnerabilities (Arora, Parashar & Transforming, 2013). These threats are highly
hazardous for any business. Any sort of data leakage or misuse of the sensitive data can hamper
the business. Thus, business can use the cloud solution to improve their business performance
but they also require high security controls to secure their sensitive data. An effective adoption of
the cloud solution in a business means that the business also adopt some tight security solutions
to secure the cloud devices.
This study mainly deals with cloud vulnerabilities and some security measures to secure
the cloud solution. The selected organization for this report is ABC Company which is planning
to adopt a cloud vendor namely, Amazon Cloud Services. This report will focus on potential
vulnerabilities of the cloud technology that can negative hamper the business of ABC Company.
However, the report also prepared a security solution for the concerned organization which can
be used to secure the cloud solution. An effective adoption of the cloud vendor will help the
concerned organization to achieve its business goals. The report also described some encryption
methods that can be used to secure the proposed cloud solution for the concerned organization
and also recommend an encryption technique that is appropriate for the business.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3CLOUD TECHNOLOGY FUNDAMENTALS
Discussion
Cloud Technology Threats
ACS is a PaaS cloud model which comprised of IDE (Integrated Development
Environment), platform layer resources and Operating system. The technologies used in the
deployment model of the ACS (Amazon Cloud Services) introduce numerous potential threats
for the concerned organization (Carlin & Curran, 2013). The security threats in the cloud
solution is different from the threats in the IT infrastructure either in intensity or in nature or
both. The technologies introduce vast elasticity as well as optimal management of the cloud
resources which increases the level of risk for the concerned business. The multi – tenancy
feature of the ACS also allow the users to view and access the data easily which also increases
the risk for the ABC Company. The on – demand self-service feature causes the probability of
the unauthorized access to other users. Any sort of unauthorized access in the cloud can lead to
data leakage as well as they can misuse the data of the system. The potential threats of the
Amazon Cloud Services can be divided in three main abstract domains namely: communication
level security issues, Architectural security issues and contractual security issues (Fernando,
Loke & Rahayu, 2013).
Discussion
Cloud Technology Threats
ACS is a PaaS cloud model which comprised of IDE (Integrated Development
Environment), platform layer resources and Operating system. The technologies used in the
deployment model of the ACS (Amazon Cloud Services) introduce numerous potential threats
for the concerned organization (Carlin & Curran, 2013). The security threats in the cloud
solution is different from the threats in the IT infrastructure either in intensity or in nature or
both. The technologies introduce vast elasticity as well as optimal management of the cloud
resources which increases the level of risk for the concerned business. The multi – tenancy
feature of the ACS also allow the users to view and access the data easily which also increases
the risk for the ABC Company. The on – demand self-service feature causes the probability of
the unauthorized access to other users. Any sort of unauthorized access in the cloud can lead to
data leakage as well as they can misuse the data of the system. The potential threats of the
Amazon Cloud Services can be divided in three main abstract domains namely: communication
level security issues, Architectural security issues and contractual security issues (Fernando,
Loke & Rahayu, 2013).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4CLOUD TECHNOLOGY FUNDAMENTALS
Figure 1: ACS Security Challenges
(Source: Rittinghouse & Ransome, 2017)
Communication Level Challenges:
The cloud services are generally provided to the customers through the internet
technology. The ABC Company will use some standard internet protocols and methods for
communicating with their clients. The whole communication process mainly deals with the
transmission of the services from the organization end and receiving the services from the user
end (Garg, Versteeg & Buyya, 2013). Moreover, the organization also deals with some
communication process among the virtual machines (VMs). Thus communication in the cloud
can be divided in two domains: communication external to cloud (Communication between the
Figure 1: ACS Security Challenges
(Source: Rittinghouse & Ransome, 2017)
Communication Level Challenges:
The cloud services are generally provided to the customers through the internet
technology. The ABC Company will use some standard internet protocols and methods for
communicating with their clients. The whole communication process mainly deals with the
transmission of the services from the organization end and receiving the services from the user
end (Garg, Versteeg & Buyya, 2013). Moreover, the organization also deals with some
communication process among the virtual machines (VMs). Thus communication in the cloud
can be divided in two domains: communication external to cloud (Communication between the

5CLOUD TECHNOLOGY FUNDAMENTALS
cloud and the customers of the concerned organization) and communication internal to cloud
(Communication within the cloud infrastructure) (Botta et al., 2016). The security challenges
faced by the communication level are:
Denial – of – Service:
Eavesdropping
Man – in – the – middle attack.
IP Spoofing
Shared Communication Infrastructure
The resource pooling is not only used to share the storage and computational
resources abut also is used to sanction sharing of the components present in the networking
infrastructure. This method of sharing the network components allow the attacker to trigger the
cross tenant attack (Tang, Sandhu & Li, 2015). The users of the cloud are generally provided
with super access of the data which allow the attacker to trigger some vulnerable attack like
sniffing and spoofing and sniffing over the networking layer.
Virtual Network
Virtual Network is the logical network that is built over the physical network of
the concerned organization. These networks allow the VMs to communicate among themselves
or to communicate with the users (Rajpoot, Jensen & Krishnan, 2015). The virtualized network
is distributed between multiple Virtual machines which increases the threat of the DDoS attack
in the networking layer and can lead to high damage in the communication layer of the proposed
cloud solution. Sometimes misconfiguration in the cloud infrastructure also lead to negative
cloud and the customers of the concerned organization) and communication internal to cloud
(Communication within the cloud infrastructure) (Botta et al., 2016). The security challenges
faced by the communication level are:
Denial – of – Service:
Eavesdropping
Man – in – the – middle attack.
IP Spoofing
Shared Communication Infrastructure
The resource pooling is not only used to share the storage and computational
resources abut also is used to sanction sharing of the components present in the networking
infrastructure. This method of sharing the network components allow the attacker to trigger the
cross tenant attack (Tang, Sandhu & Li, 2015). The users of the cloud are generally provided
with super access of the data which allow the attacker to trigger some vulnerable attack like
sniffing and spoofing and sniffing over the networking layer.
Virtual Network
Virtual Network is the logical network that is built over the physical network of
the concerned organization. These networks allow the VMs to communicate among themselves
or to communicate with the users (Rajpoot, Jensen & Krishnan, 2015). The virtualized network
is distributed between multiple Virtual machines which increases the threat of the DDoS attack
in the networking layer and can lead to high damage in the communication layer of the proposed
cloud solution. Sometimes misconfiguration in the cloud infrastructure also lead to negative
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6CLOUD TECHNOLOGY FUNDAMENTALS
result for the concerned organization such as data leakage which can exploit the business of the
ABC Company.
Architectural Level Security Issues
Virtualization Issues
Virtualization is one the major component of Amazon cloud Services. This allow
multiple customers to use one cloud resource at the same time. Each and every customers are
assigned with a separate VM individually which virtually give an operating system to their user.
In the method of VM sharing the attacker can insert malware which can destroy the data. For
example, if a user upload a malicious image then the VM assigned by that malicious image will
transform as the source of the malware and will inject the whole cloud computing system. The
VM are required to be isolated from both the ends as they are run over the physical network and
are vulnerable to multiple threats. The access to the same resource can also result in cross VM
attacks or data breach attack. The roll back feature of the VM can enable all the security
credentials of the Amazon cloud services. These credentials are initially disabled such that they
cannot be misused by the attackers.
Data Storage issues
The data stored in the cloud is more vulnerable to multiple risks with respect to the
availability, integrity and confidentiality of the business data. The business data can be
vulnerable to numerous risk due to the emerging technologies and evolving threats from those
technologies. Moreover the insecure API also increases the level of the risk for the ABC
Company. The insecure API allows the attacker to easily access the cloud system and misuse the
data.
result for the concerned organization such as data leakage which can exploit the business of the
ABC Company.
Architectural Level Security Issues
Virtualization Issues
Virtualization is one the major component of Amazon cloud Services. This allow
multiple customers to use one cloud resource at the same time. Each and every customers are
assigned with a separate VM individually which virtually give an operating system to their user.
In the method of VM sharing the attacker can insert malware which can destroy the data. For
example, if a user upload a malicious image then the VM assigned by that malicious image will
transform as the source of the malware and will inject the whole cloud computing system. The
VM are required to be isolated from both the ends as they are run over the physical network and
are vulnerable to multiple threats. The access to the same resource can also result in cross VM
attacks or data breach attack. The roll back feature of the VM can enable all the security
credentials of the Amazon cloud services. These credentials are initially disabled such that they
cannot be misused by the attackers.
Data Storage issues
The data stored in the cloud is more vulnerable to multiple risks with respect to the
availability, integrity and confidentiality of the business data. The business data can be
vulnerable to numerous risk due to the emerging technologies and evolving threats from those
technologies. Moreover the insecure API also increases the level of the risk for the ABC
Company. The insecure API allows the attacker to easily access the cloud system and misuse the
data.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7CLOUD TECHNOLOGY FUNDAMENTALS
Contractual or Legal Security Issues
As ABC Company is migrating all their application in Amazon cloud services, the
migration deals with numerous legal and contractual concerns. Some contractual security issues
of the proposed cloud system include SLA, physical location of information and legalities. It is a
complex process to comply with innovative legal jurisdictions
Security Measures
Security Measures for the communication Issues
It is recommended to the ABC organization to use the mixture of VLANs (Virtual LAN),
IPS, firewall and IDS to protect the sensitive data associated with the business. The mentioned
security tools can be used effectively by maintaining a strict access management policies.
Moreover advanced cloud protection system (ACPS) can also be used to provide better security
to the proposed cloud resources. It also provides security against the malicious data attacks. The
most important and amazing characteristics of the ACPS is that it appears as a transparent and
undetectable for various virtual machines. The prototypes of the ACPS was implemented on the
openECP and Eucalyptus which are referred as the open source cloud system. The
CyberGuarder can also be used to secure the virtual machines. The VMs can be also be isolated
using the DCPortalsNg technique. This technique maintains SDN methodology which interacts
with open stack with the help of the neuron plug in and then achieve all the data that are required
for the isolation of the virtual machines. The intrusion in the cloud environment can be prevented
using the SnortFlow. This system uses the characteristics of the OpenFlow and Snort systems.
.
Contractual or Legal Security Issues
As ABC Company is migrating all their application in Amazon cloud services, the
migration deals with numerous legal and contractual concerns. Some contractual security issues
of the proposed cloud system include SLA, physical location of information and legalities. It is a
complex process to comply with innovative legal jurisdictions
Security Measures
Security Measures for the communication Issues
It is recommended to the ABC organization to use the mixture of VLANs (Virtual LAN),
IPS, firewall and IDS to protect the sensitive data associated with the business. The mentioned
security tools can be used effectively by maintaining a strict access management policies.
Moreover advanced cloud protection system (ACPS) can also be used to provide better security
to the proposed cloud resources. It also provides security against the malicious data attacks. The
most important and amazing characteristics of the ACPS is that it appears as a transparent and
undetectable for various virtual machines. The prototypes of the ACPS was implemented on the
openECP and Eucalyptus which are referred as the open source cloud system. The
CyberGuarder can also be used to secure the virtual machines. The VMs can be also be isolated
using the DCPortalsNg technique. This technique maintains SDN methodology which interacts
with open stack with the help of the neuron plug in and then achieve all the data that are required
for the isolation of the virtual machines. The intrusion in the cloud environment can be prevented
using the SnortFlow. This system uses the characteristics of the OpenFlow and Snort systems.
.
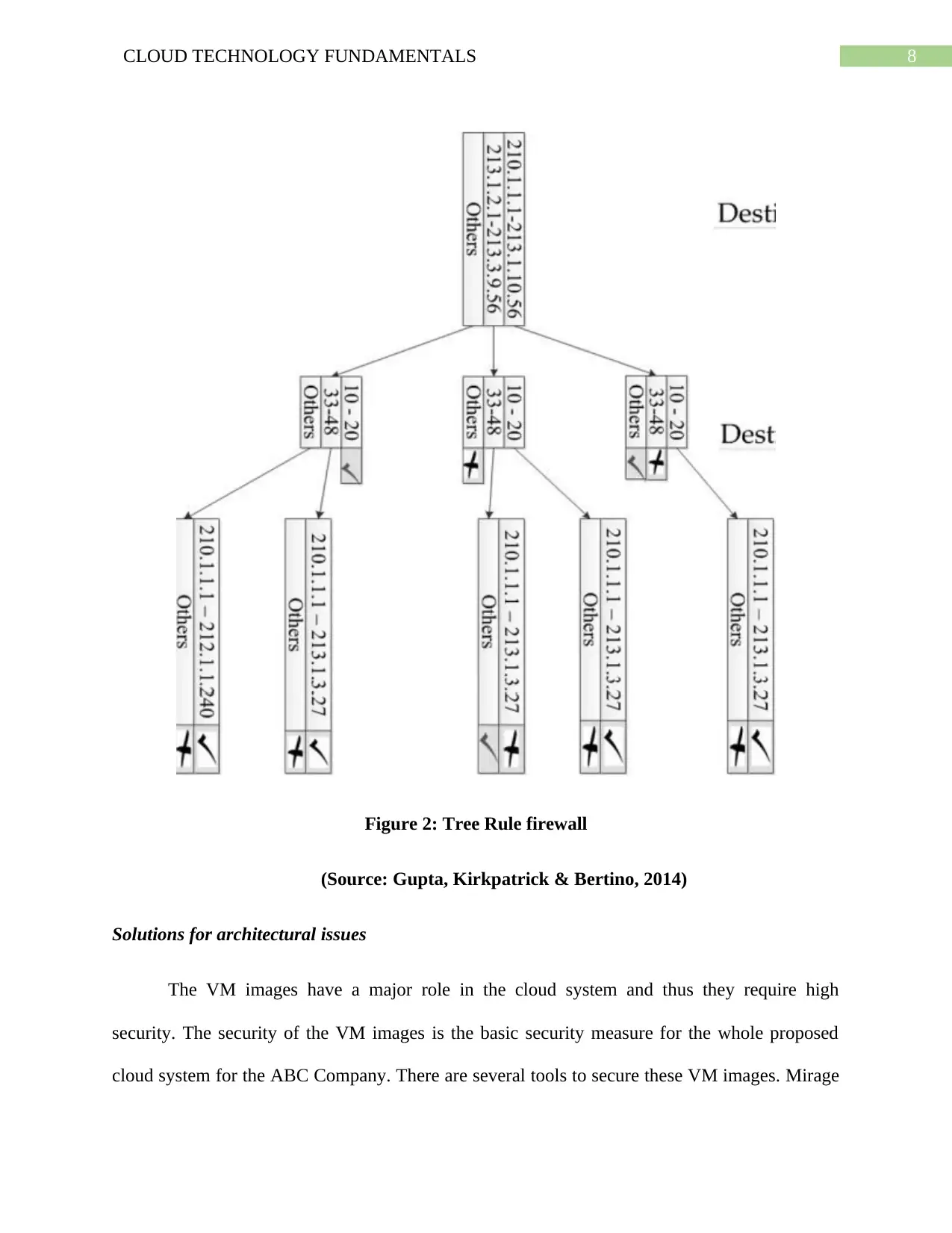
8CLOUD TECHNOLOGY FUNDAMENTALS
Figure 2: Tree Rule firewall
(Source: Gupta, Kirkpatrick & Bertino, 2014)
Solutions for architectural issues
The VM images have a major role in the cloud system and thus they require high
security. The security of the VM images is the basic security measure for the whole proposed
cloud system for the ABC Company. There are several tools to secure these VM images. Mirage
Figure 2: Tree Rule firewall
(Source: Gupta, Kirkpatrick & Bertino, 2014)
Solutions for architectural issues
The VM images have a major role in the cloud system and thus they require high
security. The security of the VM images is the basic security measure for the whole proposed
cloud system for the ABC Company. There are several tools to secure these VM images. Mirage
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9CLOUD TECHNOLOGY FUNDAMENTALS
is the image management system which provides fourfold security to the VM images.
HyperCheck can also be used for ensuring the secure execution of hypervisor. The SecCloud can
be used to secure not only the business data but also can be used to secure the computation
measures.
Solutions for Contractual Issues
It is recommended for ABC Company to maintain web services – agreement which is
used to define the syntax as well as semantics of the competences of the proposed cloud system.
The extended version of the web services agreement is the SecAgreement which is used to
articulate security services and parameters for the provision of the SLA. SPEC can also be used
as the solutions for the legal issues. This architecture can be used to give SLA based security.
This architecture divides the life cycle of SLA in three various parts namely enforcement,
monitoring and negotiation.
Encryption Techniques
Encryption is the practice of converting any information in the form of secret code which
is used to hide the original meaning or value of the data. In this process the sender encrypts the
data such that in case of data leakage the attacker cannot access the data. The senders have to
select a type of cipher (Barker & Mouha, 2017). Cipher can be of two types symmetric and
asymmetric. In symmetric cipher the sender has to share secret key with every entities which are
authorized for decrypting the message. In asymmetric ciphers prime numbers are used to
generate keys. Multiple encryption algorithms are there that are used to encrypt a sensitive
information (Wang & Luan, 2013). Three types of encryption algorithms are key based, hash
based and substitution based encryption technique.
is the image management system which provides fourfold security to the VM images.
HyperCheck can also be used for ensuring the secure execution of hypervisor. The SecCloud can
be used to secure not only the business data but also can be used to secure the computation
measures.
Solutions for Contractual Issues
It is recommended for ABC Company to maintain web services – agreement which is
used to define the syntax as well as semantics of the competences of the proposed cloud system.
The extended version of the web services agreement is the SecAgreement which is used to
articulate security services and parameters for the provision of the SLA. SPEC can also be used
as the solutions for the legal issues. This architecture can be used to give SLA based security.
This architecture divides the life cycle of SLA in three various parts namely enforcement,
monitoring and negotiation.
Encryption Techniques
Encryption is the practice of converting any information in the form of secret code which
is used to hide the original meaning or value of the data. In this process the sender encrypts the
data such that in case of data leakage the attacker cannot access the data. The senders have to
select a type of cipher (Barker & Mouha, 2017). Cipher can be of two types symmetric and
asymmetric. In symmetric cipher the sender has to share secret key with every entities which are
authorized for decrypting the message. In asymmetric ciphers prime numbers are used to
generate keys. Multiple encryption algorithms are there that are used to encrypt a sensitive
information (Wang & Luan, 2013). Three types of encryption algorithms are key based, hash
based and substitution based encryption technique.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10CLOUD TECHNOLOGY FUNDAMENTALS
Substitution Ciphers: This type of encryption was developed during 600BC. In this
encryption technique each letter of the plain text is converted to different letter. The position of
the letters are not changed only the identity of ever letter is changed to hide their value (Zhang,
Guo & Wei, 2013). A mapping algorithm is maintained in this technique. Every plain text (P) is
replace by the cipher text (C) maintaining the following equation:
C = E(k, p) = (p + k) mod 26 where k is the number of shift and 1 ≤ k ≤ 25
And decryption is done by:
P = D(k, C) = (Ck) mod 26.
Some of the popular substitution cipher are Playfair Cipher, Monoalphabetic cipher, Hill
Cipher, One-Time Pad and Polyalphabetic Cipher (Li, 2016).
Transposition Ciphers: In this encryption techniques the position of the letters is
changed by maintaining a constant position shift. These ciphers uses the rail fence
method. In this method the letters are rearranged. For instance: the word “WELCOME”
is represented as
W..O..L
.E.C.M.E
This is the encrypted which cannot be read by normal person. The receiver can easily
decrypt the received text by the rail fence method.
Substitution Ciphers: This type of encryption was developed during 600BC. In this
encryption technique each letter of the plain text is converted to different letter. The position of
the letters are not changed only the identity of ever letter is changed to hide their value (Zhang,
Guo & Wei, 2013). A mapping algorithm is maintained in this technique. Every plain text (P) is
replace by the cipher text (C) maintaining the following equation:
C = E(k, p) = (p + k) mod 26 where k is the number of shift and 1 ≤ k ≤ 25
And decryption is done by:
P = D(k, C) = (Ck) mod 26.
Some of the popular substitution cipher are Playfair Cipher, Monoalphabetic cipher, Hill
Cipher, One-Time Pad and Polyalphabetic Cipher (Li, 2016).
Transposition Ciphers: In this encryption techniques the position of the letters is
changed by maintaining a constant position shift. These ciphers uses the rail fence
method. In this method the letters are rearranged. For instance: the word “WELCOME”
is represented as
W..O..L
.E.C.M.E
This is the encrypted which cannot be read by normal person. The receiver can easily
decrypt the received text by the rail fence method.
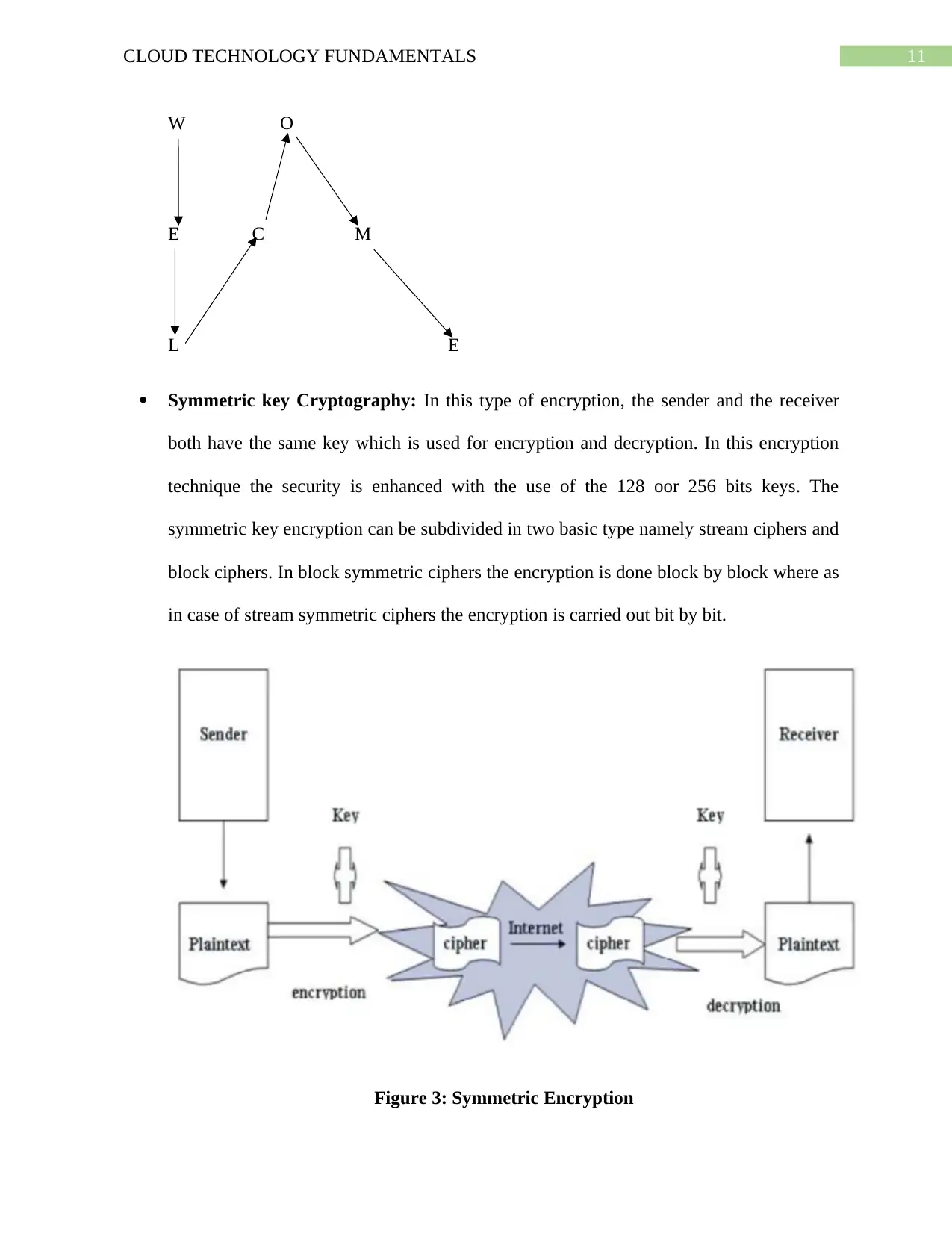
11CLOUD TECHNOLOGY FUNDAMENTALS
W O
E C M
L E
Symmetric key Cryptography: In this type of encryption, the sender and the receiver
both have the same key which is used for encryption and decryption. In this encryption
technique the security is enhanced with the use of the 128 oor 256 bits keys. The
symmetric key encryption can be subdivided in two basic type namely stream ciphers and
block ciphers. In block symmetric ciphers the encryption is done block by block where as
in case of stream symmetric ciphers the encryption is carried out bit by bit.
Figure 3: Symmetric Encryption
W O
E C M
L E
Symmetric key Cryptography: In this type of encryption, the sender and the receiver
both have the same key which is used for encryption and decryption. In this encryption
technique the security is enhanced with the use of the 128 oor 256 bits keys. The
symmetric key encryption can be subdivided in two basic type namely stream ciphers and
block ciphers. In block symmetric ciphers the encryption is done block by block where as
in case of stream symmetric ciphers the encryption is carried out bit by bit.
Figure 3: Symmetric Encryption
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





