Utilizing Cloud Computing for Image Retrieval Optimization: Review
VerifiedAdded on 2024/06/28
|86
|10423
|268
Literature Review
AI Summary
This literature review examines various techniques for optimizing image retrieval processes using cloud computing, with a focus on mobile devices. It covers approaches such as content-based multi-source encrypted image retrieval, efficient privacy-preserving content-based image retrieval schemes, and distributed image-retrieval methods in multi-camera systems for smart cities. The review highlights the goals, components, processes, advantages, and limitations of each technique, considering factors like privacy preservation, security, processing rate, and feature extraction. The studies also explore the use of algorithms like k-nearest neighbor and fault-tolerant processing to enhance efficiency and security in cloud-based image retrieval systems, addressing challenges related to data leakage, slow processing speeds, and image management in large cities. Desklib provides access to similar solved assignments and resources for students.

Literature Review
Student Name & CSU ID
Project Topic Title Utilising cloud computing for the optimization of image retrieval process used in mobile devices
1
Student Name & CSU ID
Project Topic Title Utilising cloud computing for the optimization of image retrieval process used in mobile devices
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Version 1.0 _ Week 1 (5 Journal Papers from CSU Library)
1
Reference in APA format that will be in
'Reference List'
Shen, M., Cheng, G., Zhu, L., Du, X., & Hu, J. (2018). Content-based multi-source encrypted image retrieval
in clouds with privacy preservation. Future Generation Computer Systems.
Citation that will be in the content Shen et. al., 2018
URL of the Reference Level of Journal (Q1, Q2, …Qn) Keywords in this Reference
https://www-sciencedirect-
com.ezproxy.csu.edu.au/science/article/
pii/S0167739X17321969
Level of Journal: Q1 Privacy-preserving, Secure, image retrieval, Multi-source,
Content-based image retrieval, Searchable encryption, Image
encryption
The Name of the Current Solution
(Technique/ Method/ Scheme/
Algorithm/ Model/ Tool/ Framework/ ...
etc )
The Goal (Objective) of this Solution &
What is the Problem that need to be solved
What are the components of it?
Technique/Algorithm name:
Homomorphic encryption
Tools:
Multiple Image owners with Privacy
Protection
Applied Area:
Medical diagnoses
Art collection
Problem:
The major problem with the Content-based
image retrieval major issue is that when
images are outsourced to the servers it has
chances of data leakage.
Goal: The goal is to overcome problems and
make data secure and to allow Multiple Image
owners with Privacy Protection (MIPP).
Image owner
Keys
The cloud
The KMC
The Process (Mechanism) of this Work; The process steps of the Technique/system
2
1
Reference in APA format that will be in
'Reference List'
Shen, M., Cheng, G., Zhu, L., Du, X., & Hu, J. (2018). Content-based multi-source encrypted image retrieval
in clouds with privacy preservation. Future Generation Computer Systems.
Citation that will be in the content Shen et. al., 2018
URL of the Reference Level of Journal (Q1, Q2, …Qn) Keywords in this Reference
https://www-sciencedirect-
com.ezproxy.csu.edu.au/science/article/
pii/S0167739X17321969
Level of Journal: Q1 Privacy-preserving, Secure, image retrieval, Multi-source,
Content-based image retrieval, Searchable encryption, Image
encryption
The Name of the Current Solution
(Technique/ Method/ Scheme/
Algorithm/ Model/ Tool/ Framework/ ...
etc )
The Goal (Objective) of this Solution &
What is the Problem that need to be solved
What are the components of it?
Technique/Algorithm name:
Homomorphic encryption
Tools:
Multiple Image owners with Privacy
Protection
Applied Area:
Medical diagnoses
Art collection
Problem:
The major problem with the Content-based
image retrieval major issue is that when
images are outsourced to the servers it has
chances of data leakage.
Goal: The goal is to overcome problems and
make data secure and to allow Multiple Image
owners with Privacy Protection (MIPP).
Image owner
Keys
The cloud
The KMC
The Process (Mechanism) of this Work; The process steps of the Technique/system
2
Process Steps Advantage (Purpose of this step) Disadvantage (Limitation/Challenge)
1
Generation of key: A secret image encryption
key is obtained so that authorized users and
image owners can use it.
It will ensure image content privacy and its
features privacy.
N/A
2
Encryption and decryption of image: A
standard key is used for image encryption
which is secured by Chosen-Plaintext Attacks
(CPA).
The only authorized user can communicate
with image encryption and decryption key.
N/A
3
Encrypting the features of image: Used for
preserving the image features and features
should be encrypted before uploading it to
cloud.
Without communicating with others the owner
of image and user can select it. Also,
parameters can be discarded.
With KMC, the algorithm is used to decrypt
images.
Validation Criteria (Measurement Criteria)
Dependent Variable Independent Variable
Retrieval scheme Images
Input and Output Critical Thinking: Feature of this work,
and Why (Justify)
Critical Thinking: Limitations of the
research current solution, and Why
(Justify)
3
1
Generation of key: A secret image encryption
key is obtained so that authorized users and
image owners can use it.
It will ensure image content privacy and its
features privacy.
N/A
2
Encryption and decryption of image: A
standard key is used for image encryption
which is secured by Chosen-Plaintext Attacks
(CPA).
The only authorized user can communicate
with image encryption and decryption key.
N/A
3
Encrypting the features of image: Used for
preserving the image features and features
should be encrypted before uploading it to
cloud.
Without communicating with others the owner
of image and user can select it. Also,
parameters can be discarded.
With KMC, the algorithm is used to decrypt
images.
Validation Criteria (Measurement Criteria)
Dependent Variable Independent Variable
Retrieval scheme Images
Input and Output Critical Thinking: Feature of this work,
and Why (Justify)
Critical Thinking: Limitations of the
research current solution, and Why
(Justify)
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Input (Data) Output (View)
Input in the medical sector
is a medical image.
Image retrieval is done
efficiently and images are
gathered with a guarantee of
maintaining the privacy
aspects.
The techniques used in this increases the
privacy on an image and make it secure.
Also, accuracy while retrieval increases.
The third point is efficiency. It shows the
time used for retrieving a secured image.
The major limitations are:
Privacy of images and features of
images that belong to the different
owner their privacy should be
ensured.
Eavesdroppers
Cloud
(Describe the research/current solution) Evaluation Criteria How this research/current solution is
valuable for your project
In this, an image retrieval scheme that is used in clouds with
privacy concerns using content-based multi-source encryption
technique is explained. Also with secure multi-party computation,
we used features of the encrypted image so that owner of that
image can encrypt the features by his own key (Shen et. al., 2018).
Image owner provides image database.
Then an authorised user demands an image
retrieval. The cloud is responsible for
storing and retrieving an image. And at last
Key management centre is responsible for
managing encryption and decryption key.
This solution helps in CBIR with
multiple image sources. And it helps in
maintaining the image content privacy
plus the features of the image.
Diagram/Flowchart
4
Input in the medical sector
is a medical image.
Image retrieval is done
efficiently and images are
gathered with a guarantee of
maintaining the privacy
aspects.
The techniques used in this increases the
privacy on an image and make it secure.
Also, accuracy while retrieval increases.
The third point is efficiency. It shows the
time used for retrieving a secured image.
The major limitations are:
Privacy of images and features of
images that belong to the different
owner their privacy should be
ensured.
Eavesdroppers
Cloud
(Describe the research/current solution) Evaluation Criteria How this research/current solution is
valuable for your project
In this, an image retrieval scheme that is used in clouds with
privacy concerns using content-based multi-source encryption
technique is explained. Also with secure multi-party computation,
we used features of the encrypted image so that owner of that
image can encrypt the features by his own key (Shen et. al., 2018).
Image owner provides image database.
Then an authorised user demands an image
retrieval. The cloud is responsible for
storing and retrieving an image. And at last
Key management centre is responsible for
managing encryption and decryption key.
This solution helps in CBIR with
multiple image sources. And it helps in
maintaining the image content privacy
plus the features of the image.
Diagram/Flowchart
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
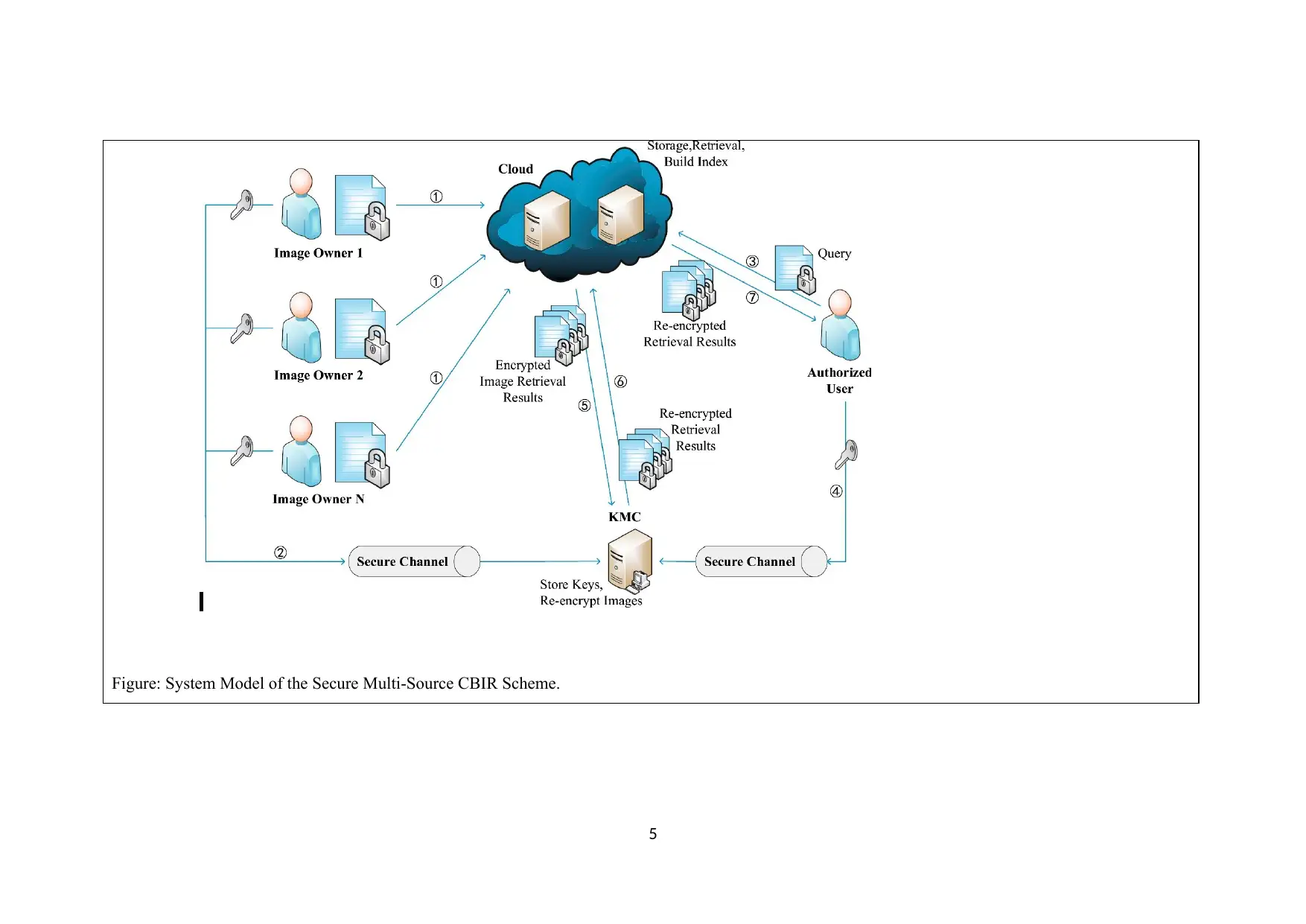
Figure: System Model of the Secure Multi-Source CBIR Scheme.
5
5
2
Reference in APA format that will be in
'Reference List'
Xia, Z., Xiong, N. N., Vasilakos, A. V., & Sun, X. (2017). EPCBIR: An efficient and privacy-preserving
content-based image retrieval scheme in cloud computing. Information Sciences, 387, 195-204.
Citation that will be in the content Xia, et. Al., 2017
URL of the Reference Level of Journal (Q1, Q2, …Qn) Keywords in this Reference
https://www-sciencedirect-
com.ezproxy.csu.edu.au/science/article/
pii/S0020025516321971
Level of Journal: Q1 Locality-sensitive hashing, Content-based image retrieval,
Searchable encryption, Secure k-nearest neighbour algorithm
The Name of the Current Solution
(Technique/ Method/ Scheme/
Algorithm/ Model/ Tool/ Framework/ ...
etc )
The Goal (Objective) of this Solution &
What is the Problem that need to be solved
What are the components of it?
Technique/Algorithm name:
k-nearest neighbour
min-hash algorithm
Tools:
Mobile computing
Cloud computing
Applied Area:
Mobile Commerce
Mobile Healthcare
Mobile Gaming
Problem:
The major problem is to store images on cloud
servers. Also, privacy is not preserved for
sensitive images.
Goal:
The two major goals are, first is to maintain
efficiency and second is to maintain the
security of data.
Keys
Images
Cloud
6
Reference in APA format that will be in
'Reference List'
Xia, Z., Xiong, N. N., Vasilakos, A. V., & Sun, X. (2017). EPCBIR: An efficient and privacy-preserving
content-based image retrieval scheme in cloud computing. Information Sciences, 387, 195-204.
Citation that will be in the content Xia, et. Al., 2017
URL of the Reference Level of Journal (Q1, Q2, …Qn) Keywords in this Reference
https://www-sciencedirect-
com.ezproxy.csu.edu.au/science/article/
pii/S0020025516321971
Level of Journal: Q1 Locality-sensitive hashing, Content-based image retrieval,
Searchable encryption, Secure k-nearest neighbour algorithm
The Name of the Current Solution
(Technique/ Method/ Scheme/
Algorithm/ Model/ Tool/ Framework/ ...
etc )
The Goal (Objective) of this Solution &
What is the Problem that need to be solved
What are the components of it?
Technique/Algorithm name:
k-nearest neighbour
min-hash algorithm
Tools:
Mobile computing
Cloud computing
Applied Area:
Mobile Commerce
Mobile Healthcare
Mobile Gaming
Problem:
The major problem is to store images on cloud
servers. Also, privacy is not preserved for
sensitive images.
Goal:
The two major goals are, first is to maintain
efficiency and second is to maintain the
security of data.
Keys
Images
Cloud
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Mobile Learning
Mobile social networking
The Process (Mechanism) of this Work; The process steps of the Technique/system
Process Steps Advantage (Purpose of this step) Disadvantage (Limitation/Challenge)
1 The generation of unencrypted index: By
some methods image feature vector is extracted.
It helps to rank query image with the help of
one-one map index.
N/A
2 The index encryption:
The pain-text based information is revealed via
image feature vector format regarding the
content of image
It helps in saving the time. N/A
Validation Criteria (Measurement Criteria)
Dependent Variable Independent Variable
Private content-based image retrieval Privacy of unencrypted image.
Homomorphic-encryption High complexities
Input and Output Critical Thinking: Feature of this work, and
Why (Justify)
Critical Thinking: Limitations of the research
current solution, and Why (Justify)
Input (Data) Output (View)
Data: text and images These image features
These encryption techniques and algorithm help to
maintain the privacy of an image. Also in index
feature vectors in trapdoors are encrypted and are
The security of image features should be
improved. And the extraction features of
encrypted image help the future work for securing
7
Mobile social networking
The Process (Mechanism) of this Work; The process steps of the Technique/system
Process Steps Advantage (Purpose of this step) Disadvantage (Limitation/Challenge)
1 The generation of unencrypted index: By
some methods image feature vector is extracted.
It helps to rank query image with the help of
one-one map index.
N/A
2 The index encryption:
The pain-text based information is revealed via
image feature vector format regarding the
content of image
It helps in saving the time. N/A
Validation Criteria (Measurement Criteria)
Dependent Variable Independent Variable
Private content-based image retrieval Privacy of unencrypted image.
Homomorphic-encryption High complexities
Input and Output Critical Thinking: Feature of this work, and
Why (Justify)
Critical Thinking: Limitations of the research
current solution, and Why (Justify)
Input (Data) Output (View)
Data: text and images These image features
These encryption techniques and algorithm help to
maintain the privacy of an image. Also in index
feature vectors in trapdoors are encrypted and are
The security of image features should be
improved. And the extraction features of
encrypted image help the future work for securing
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
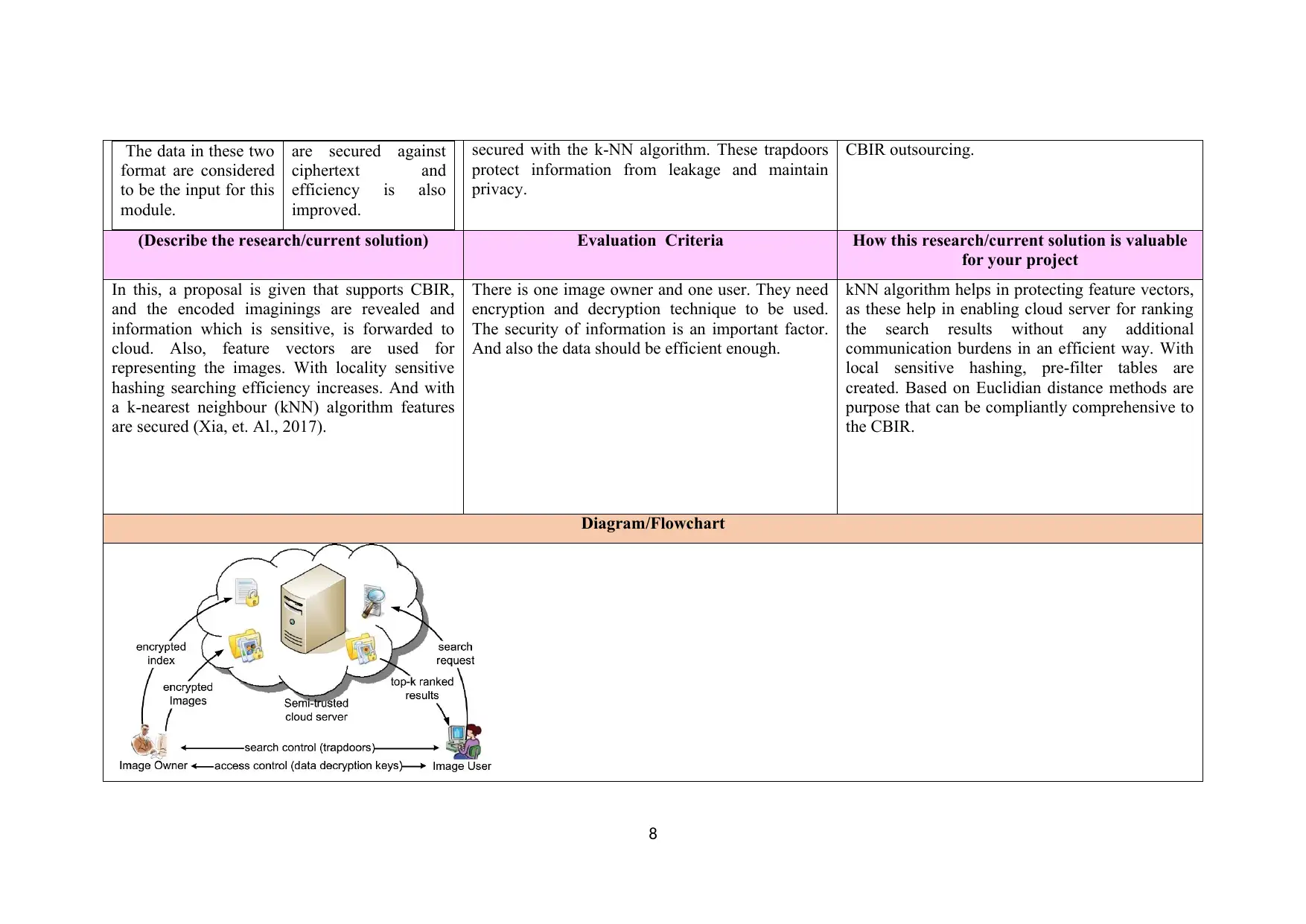
The data in these two
format are considered
to be the input for this
module.
are secured against
ciphertext and
efficiency is also
improved.
secured with the k-NN algorithm. These trapdoors
protect information from leakage and maintain
privacy.
CBIR outsourcing.
(Describe the research/current solution) Evaluation Criteria How this research/current solution is valuable
for your project
In this, a proposal is given that supports CBIR,
and the encoded imaginings are revealed and
information which is sensitive, is forwarded to
cloud. Also, feature vectors are used for
representing the images. With locality sensitive
hashing searching efficiency increases. And with
a k-nearest neighbour (kNN) algorithm features
are secured (Xia, et. Al., 2017).
There is one image owner and one user. They need
encryption and decryption technique to be used.
The security of information is an important factor.
And also the data should be efficient enough.
kNN algorithm helps in protecting feature vectors,
as these help in enabling cloud server for ranking
the search results without any additional
communication burdens in an efficient way. With
local sensitive hashing, pre-filter tables are
created. Based on Euclidian distance methods are
purpose that can be compliantly comprehensive to
the CBIR.
Diagram/Flowchart
8
format are considered
to be the input for this
module.
are secured against
ciphertext and
efficiency is also
improved.
secured with the k-NN algorithm. These trapdoors
protect information from leakage and maintain
privacy.
CBIR outsourcing.
(Describe the research/current solution) Evaluation Criteria How this research/current solution is valuable
for your project
In this, a proposal is given that supports CBIR,
and the encoded imaginings are revealed and
information which is sensitive, is forwarded to
cloud. Also, feature vectors are used for
representing the images. With locality sensitive
hashing searching efficiency increases. And with
a k-nearest neighbour (kNN) algorithm features
are secured (Xia, et. Al., 2017).
There is one image owner and one user. They need
encryption and decryption technique to be used.
The security of information is an important factor.
And also the data should be efficient enough.
kNN algorithm helps in protecting feature vectors,
as these help in enabling cloud server for ranking
the search results without any additional
communication burdens in an efficient way. With
local sensitive hashing, pre-filter tables are
created. Based on Euclidian distance methods are
purpose that can be compliantly comprehensive to
the CBIR.
Diagram/Flowchart
8
Figure: A framework with CBIR scheme for preserving privacy.
9
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
Reference in APA format that will be in
'Reference List'
Yang, J., Jiang, B., & Song, H. (2018). A distributed image-retrieval method in the multi-camera system of the
smart city based on cloud computing. Future Generation Computer Systems, 81, 244-251.
Citation that will be in the content Yang. et. al., 2018
URL of the Reference Level of Journal (Q1, Q2, …Qn) Keywords in this Reference
https://www-sciencedirect-
com.ezproxy.csu.edu.au/science/article/pii/
S0167739X17321362#sec3
Level of Journal: Q1 Cloud computing, Smart city, Multi-camera system,
Distributed image-retrieval method
The Name of the Current Solution
(Technique/ Method/ Scheme/
Algorithm/ Model/ Tool/ Framework/ ...
etc )
The Goal (Objective) of this Solution &
What is the Problem that need to be solved
What are the components of it?
Technique/Algorithm name:
Distributed fault-tolerant processing (DFP)
method.
Tools:
Multi camera system
Applied Area:
Development of smart cities
Problem: The major problem is performing
video sensing for the whole city. Also to
correctly retrieve image in the multi-camera
system is difficult.
Goal:
The goal is to use cloud computing and
improve processing rate.
Cameras
Monitor
Coaxial cable
Converter
Connector
The Process (Mechanism) of this Work; The process steps of the Technique/system
Process Steps Advantage (Purpose of this step) Disadvantage (Limitation/Challenge)
1 Client Requests: For a particular purpose a It will improve the processing rate. N/A
10
Reference in APA format that will be in
'Reference List'
Yang, J., Jiang, B., & Song, H. (2018). A distributed image-retrieval method in the multi-camera system of the
smart city based on cloud computing. Future Generation Computer Systems, 81, 244-251.
Citation that will be in the content Yang. et. al., 2018
URL of the Reference Level of Journal (Q1, Q2, …Qn) Keywords in this Reference
https://www-sciencedirect-
com.ezproxy.csu.edu.au/science/article/pii/
S0167739X17321362#sec3
Level of Journal: Q1 Cloud computing, Smart city, Multi-camera system,
Distributed image-retrieval method
The Name of the Current Solution
(Technique/ Method/ Scheme/
Algorithm/ Model/ Tool/ Framework/ ...
etc )
The Goal (Objective) of this Solution &
What is the Problem that need to be solved
What are the components of it?
Technique/Algorithm name:
Distributed fault-tolerant processing (DFP)
method.
Tools:
Multi camera system
Applied Area:
Development of smart cities
Problem: The major problem is performing
video sensing for the whole city. Also to
correctly retrieve image in the multi-camera
system is difficult.
Goal:
The goal is to use cloud computing and
improve processing rate.
Cameras
Monitor
Coaxial cable
Converter
Connector
The Process (Mechanism) of this Work; The process steps of the Technique/system
Process Steps Advantage (Purpose of this step) Disadvantage (Limitation/Challenge)
1 Client Requests: For a particular purpose a It will improve the processing rate. N/A
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
request is send to cloud computation source.
2 Cloud computation: In this, it considers the
chore and makes a decision.
Fast image retrieval is done. N/A
3 Reply to the client: Final calculated information
and analysis are sent back.
Client get back the helpful information N/A
Validation Criteria (Measurement Criteria)
Dependent Variable Independent Variable
Processing rate Cloud computing
Multi-camera system Regenerative code
Input and Output Critical Thinking: Feature of this work, and
Why (Justify)
Critical Thinking: Limitations of the research
current solution, and Why (Justify)
Input (Data) Output (View)
Large information set
is in need to be feed
as input in this journal
as illuminated by the
author.
These are sent to
clients and then the
computation is
performed. And then
again it is sent back to
the client.
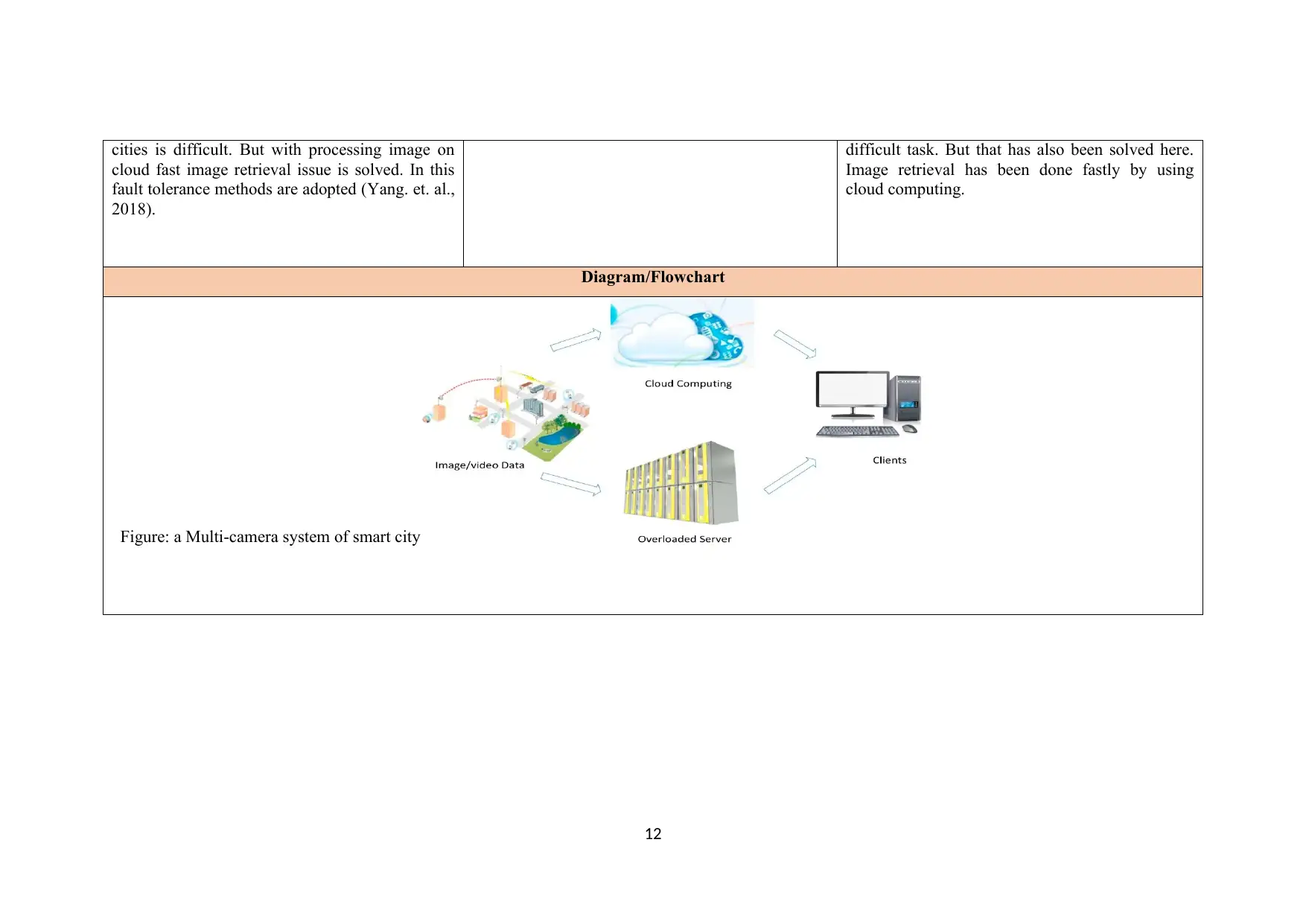
In this, it is grounded on a distributed fault-tolerant
processing (DFP) method. The DFP improves
dispensation rate within cloud computing, hence
will overcome slow speed issue of processing rate.
Also dispersed image-retrieval method is
envisioned using cloud-based on a multi-camera
system by using data encryption, data retrieval and
cloud storage.
Dispensation rate based on the cloud has a very
slow speed. In this it mainly used fault tolerant
processing.
(Describe the research/current solution) Evaluation Criteria How this research/current solution is valuable
for your project
In research distributed fault-tolerant processing
(DFP) method is used. It will improve the rate of
processing. Also, management of image in big
The client is the end user. They need to retrieve the
data from large blocks and in less processing time.
The distributed fault-tolerant processing (DFP)
method will improve the processing rate of cloud
computing. In smart cities, image management is a
11
2 Cloud computation: In this, it considers the
chore and makes a decision.
Fast image retrieval is done. N/A
3 Reply to the client: Final calculated information
and analysis are sent back.
Client get back the helpful information N/A
Validation Criteria (Measurement Criteria)
Dependent Variable Independent Variable
Processing rate Cloud computing
Multi-camera system Regenerative code
Input and Output Critical Thinking: Feature of this work, and
Why (Justify)
Critical Thinking: Limitations of the research
current solution, and Why (Justify)
Input (Data) Output (View)
Large information set
is in need to be feed
as input in this journal
as illuminated by the
author.
These are sent to
clients and then the
computation is
performed. And then
again it is sent back to
the client.
In this, it is grounded on a distributed fault-tolerant
processing (DFP) method. The DFP improves
dispensation rate within cloud computing, hence
will overcome slow speed issue of processing rate.
Also dispersed image-retrieval method is
envisioned using cloud-based on a multi-camera
system by using data encryption, data retrieval and
cloud storage.
Dispensation rate based on the cloud has a very
slow speed. In this it mainly used fault tolerant
processing.
(Describe the research/current solution) Evaluation Criteria How this research/current solution is valuable
for your project
In research distributed fault-tolerant processing
(DFP) method is used. It will improve the rate of
processing. Also, management of image in big
The client is the end user. They need to retrieve the
data from large blocks and in less processing time.
The distributed fault-tolerant processing (DFP)
method will improve the processing rate of cloud
computing. In smart cities, image management is a
11
cities is difficult. But with processing image on
cloud fast image retrieval issue is solved. In this
fault tolerance methods are adopted (Yang. et. al.,
2018).
difficult task. But that has also been solved here.
Image retrieval has been done fastly by using
cloud computing.
Diagram/Flowchart
Figure: a Multi-camera system of smart city
12
cloud fast image retrieval issue is solved. In this
fault tolerance methods are adopted (Yang. et. al.,
2018).
difficult task. But that has also been solved here.
Image retrieval has been done fastly by using
cloud computing.
Diagram/Flowchart
Figure: a Multi-camera system of smart city
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 86
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





