Detailed IT Risk Assessment Report: Aztec's Cloud Migration Project
VerifiedAdded on 2020/04/07
|16
|5432
|38
Report
AI Summary
This report provides a detailed IT risk assessment for Aztec, a financial services company in Australia, focusing on the migration of critical applications to a cloud environment. The report begins with an executive summary and introduction, outlining the project's scope and objectives. It then delves into a financial review of cloud adoption, highlighting cost benefits, improved management, scalability, and accessibility. The assessment addresses compliance issues within the financial sector, emphasizing the importance of data encryption, tokenization, and security measures. The report also analyzes the impact on security posture, discussing the shift in responsibilities and the need for adapting business applications. Furthermore, it identifies potential threats and vulnerabilities, including hardware and software failures, malware, and human error, while assessing the consequences of IT operations. Data security risks are explored, including access control, data flow, and authentication. The report concludes by summarizing the merits and challenges of cloud migration and providing recommendations for managing IT risks and ensuring data security.
IT RISK Assessment
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Executive Summary
Aztec is the company that is operating in the Australia under the financial service sector.
The business technologists of that organization has designed some portfolios for their future
projects. In the five different types of projects, the migration of the critical applications to the
cloud service is taken and the impact of the security posture because of this migration is
being discussed and then the financial review, compliance of the cloud computing is
specified. The threats and vulnerabilities of adopting the cloud computing technology is
explained in detail. The risk management plan to be made by Aztec is explained in detail. The
data security issues and the type of data that is managed by Aztec is verified. The access to
the data and the flow of data is being discussed. Thus the merits and issues that is involved in
the migration of applications to cloud is being described in detail.
1
Aztec is the company that is operating in the Australia under the financial service sector.
The business technologists of that organization has designed some portfolios for their future
projects. In the five different types of projects, the migration of the critical applications to the
cloud service is taken and the impact of the security posture because of this migration is
being discussed and then the financial review, compliance of the cloud computing is
specified. The threats and vulnerabilities of adopting the cloud computing technology is
explained in detail. The risk management plan to be made by Aztec is explained in detail. The
data security issues and the type of data that is managed by Aztec is verified. The access to
the data and the flow of data is being discussed. Thus the merits and issues that is involved in
the migration of applications to cloud is being described in detail.
1

Table of Contents
Executive Summary.............................................................................................................................1
Introduction.........................................................................................................................................3
Financial Review on the Project.........................................................................................................3
Impact on the Security Posture..........................................................................................................8
Threats, Vulnerabilities and Consequences.......................................................................................9
Threats of IT operations.................................................................................................................9
Vulnerabilities in IT Operations Outsourcing.............................................................................10
Assessing the consequences of IT operations...............................................................................11
Risks in Data Security.......................................................................................................................11
Conclusion..........................................................................................................................................13
2
Executive Summary.............................................................................................................................1
Introduction.........................................................................................................................................3
Financial Review on the Project.........................................................................................................3
Impact on the Security Posture..........................................................................................................8
Threats, Vulnerabilities and Consequences.......................................................................................9
Threats of IT operations.................................................................................................................9
Vulnerabilities in IT Operations Outsourcing.............................................................................10
Assessing the consequences of IT operations...............................................................................11
Risks in Data Security.......................................................................................................................11
Conclusion..........................................................................................................................................13
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Introduction
The Project is about the Risks that are included in the Information Technology.
Information Technology is the well-known latest technology that is used in all over the
world. When a business is relied on the Information technology (IT) system known as
computer systems and networks, then there is a chance for IT Risks. The IT risks that are
faced by the IT companies are Hardware and Software failure, malware, viruses, human error
and then phishing. IT Risks that are involved in the Organization called Aztec which is a
company under the financial services sector in Australia. Aztec is the leading company in
Australia which works in the field of Engineering, manufacturing, Aggregation and mining.
The company source the equipment from the world's number one mining company. The
Aztec Resources Limited is a resource company that assess the mining projects in advanced
stage. The Company's main focus is on the koolan Island Ore and the Brockman Tantalum
Projects. This Assessment is about the IT Risks involved in the projects that are handled by
the Aztec. The senior executives in the Business and Technology divisions of the Aztec has
collected some portfolio of the projects. The Selected portfolio consists of 5 IT projects.
Among those 5 projects, one of the project has to be selected in this assessment for review.
Migration of business critical applications and their associated data sources to an external
cloud solution is the project that is selected for this assessment. The IT risks that are involved
in the migration of applications to the cloud solution are to be discussed in this assessment.
This project is reviewed on the basis of financial services sector and the impact of the
selected project is being reviewed on the security of the Aztec. The existing IT risks in the
selected project has to be analysed and the threats, vulnerabilities involved in it is discussed
in detail. The recommendations are to be recommended to manage the IT risks involved in
the project. The data security risks are to be addressed and the authentication problem is also
discussed in this assessment.
Financial Review on the Project
The Financial service sectors are still in the early stages in adopting the cloud computing.
According to a survey in the year 2015 it is found that 61 percentage of financial institutions
are in the developing stages of cloud computing. It is the wish of the company for adopting
the cloud computing technology for their organization's critical applications. They adopt this
cloud computing technology only if those services provide specific functions and salient
features. One of the significant thing that is a widely growing phenomenon on the internet
3
The Project is about the Risks that are included in the Information Technology.
Information Technology is the well-known latest technology that is used in all over the
world. When a business is relied on the Information technology (IT) system known as
computer systems and networks, then there is a chance for IT Risks. The IT risks that are
faced by the IT companies are Hardware and Software failure, malware, viruses, human error
and then phishing. IT Risks that are involved in the Organization called Aztec which is a
company under the financial services sector in Australia. Aztec is the leading company in
Australia which works in the field of Engineering, manufacturing, Aggregation and mining.
The company source the equipment from the world's number one mining company. The
Aztec Resources Limited is a resource company that assess the mining projects in advanced
stage. The Company's main focus is on the koolan Island Ore and the Brockman Tantalum
Projects. This Assessment is about the IT Risks involved in the projects that are handled by
the Aztec. The senior executives in the Business and Technology divisions of the Aztec has
collected some portfolio of the projects. The Selected portfolio consists of 5 IT projects.
Among those 5 projects, one of the project has to be selected in this assessment for review.
Migration of business critical applications and their associated data sources to an external
cloud solution is the project that is selected for this assessment. The IT risks that are involved
in the migration of applications to the cloud solution are to be discussed in this assessment.
This project is reviewed on the basis of financial services sector and the impact of the
selected project is being reviewed on the security of the Aztec. The existing IT risks in the
selected project has to be analysed and the threats, vulnerabilities involved in it is discussed
in detail. The recommendations are to be recommended to manage the IT risks involved in
the project. The data security risks are to be addressed and the authentication problem is also
discussed in this assessment.
Financial Review on the Project
The Financial service sectors are still in the early stages in adopting the cloud computing.
According to a survey in the year 2015 it is found that 61 percentage of financial institutions
are in the developing stages of cloud computing. It is the wish of the company for adopting
the cloud computing technology for their organization's critical applications. They adopt this
cloud computing technology only if those services provide specific functions and salient
features. One of the significant thing that is a widely growing phenomenon on the internet
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cloud Computing which is a revolutionary concept taken by many banks and the financial
service sectors. By the migration of the critical applications to the cloud computing
technology, te organization gets more benefits in financial services. Some of the enormous
benefits of adopting the cloud computing is listed below ("How Cloud is Being Used in the
Financial Sector: Survey Report", 2015).
Economical Benefit
By the migration of cloud computing technology, unwanted capital expenditure as well
as infrastructure’s implementation cost can be restricted as financial service sector can keep
its focus on all significant projects ("How Cloud is Being Used in the Financial Sector:
Survey Report", 2015).
Improvement in management
The cloud computing technology services makes many adjustments to the resources of
the financial service sectors for all the unexpected and oscillating business policies as well as
fastly their applications gets uploaded in online. It need not required to be maintained ("THE
BENEFITS OF CLOUD COMPUTING FOR THE BANKING & FINANCIAL
INDUSTRY", 2017).
Resilient
The migration of critical applications to the cloud computing service are very helpful for
banks and financial service sector related companies because of the capability for the creation
of big enterprise which widely helps in the continuation of a business venture. The
continuation of the business venture is considered to be the significant part in financial
service sectors.
Scalable
The Scalability is an important feature in the banking and financial sectors. Large
amount of acquisitions and mergers are very often in the banking and in the financial service
sectors. The Cloud service is considered to be the concept which can scale the IT operations
for the needs of the company and this concept is also considered to be an affordable concept.
Accessible
The Cloud computing technology has some limitations in client server systems which is
not applicable in accessing the stored data and the applications that are available in other
computers can be achieved at anywhere during any time.
The data that is stored in the cloud environment offered a context to investigate the
customers impact of the financial services sector. The restrictions regarding the regulations
are considered as another top most hurdle for the companies that relies on the cloud services.
4
service sectors. By the migration of the critical applications to the cloud computing
technology, te organization gets more benefits in financial services. Some of the enormous
benefits of adopting the cloud computing is listed below ("How Cloud is Being Used in the
Financial Sector: Survey Report", 2015).
Economical Benefit
By the migration of cloud computing technology, unwanted capital expenditure as well
as infrastructure’s implementation cost can be restricted as financial service sector can keep
its focus on all significant projects ("How Cloud is Being Used in the Financial Sector:
Survey Report", 2015).
Improvement in management
The cloud computing technology services makes many adjustments to the resources of
the financial service sectors for all the unexpected and oscillating business policies as well as
fastly their applications gets uploaded in online. It need not required to be maintained ("THE
BENEFITS OF CLOUD COMPUTING FOR THE BANKING & FINANCIAL
INDUSTRY", 2017).
Resilient
The migration of critical applications to the cloud computing service are very helpful for
banks and financial service sector related companies because of the capability for the creation
of big enterprise which widely helps in the continuation of a business venture. The
continuation of the business venture is considered to be the significant part in financial
service sectors.
Scalable
The Scalability is an important feature in the banking and financial sectors. Large
amount of acquisitions and mergers are very often in the banking and in the financial service
sectors. The Cloud service is considered to be the concept which can scale the IT operations
for the needs of the company and this concept is also considered to be an affordable concept.
Accessible
The Cloud computing technology has some limitations in client server systems which is
not applicable in accessing the stored data and the applications that are available in other
computers can be achieved at anywhere during any time.
The data that is stored in the cloud environment offered a context to investigate the
customers impact of the financial services sector. The restrictions regarding the regulations
are considered as another top most hurdle for the companies that relies on the cloud services.
4
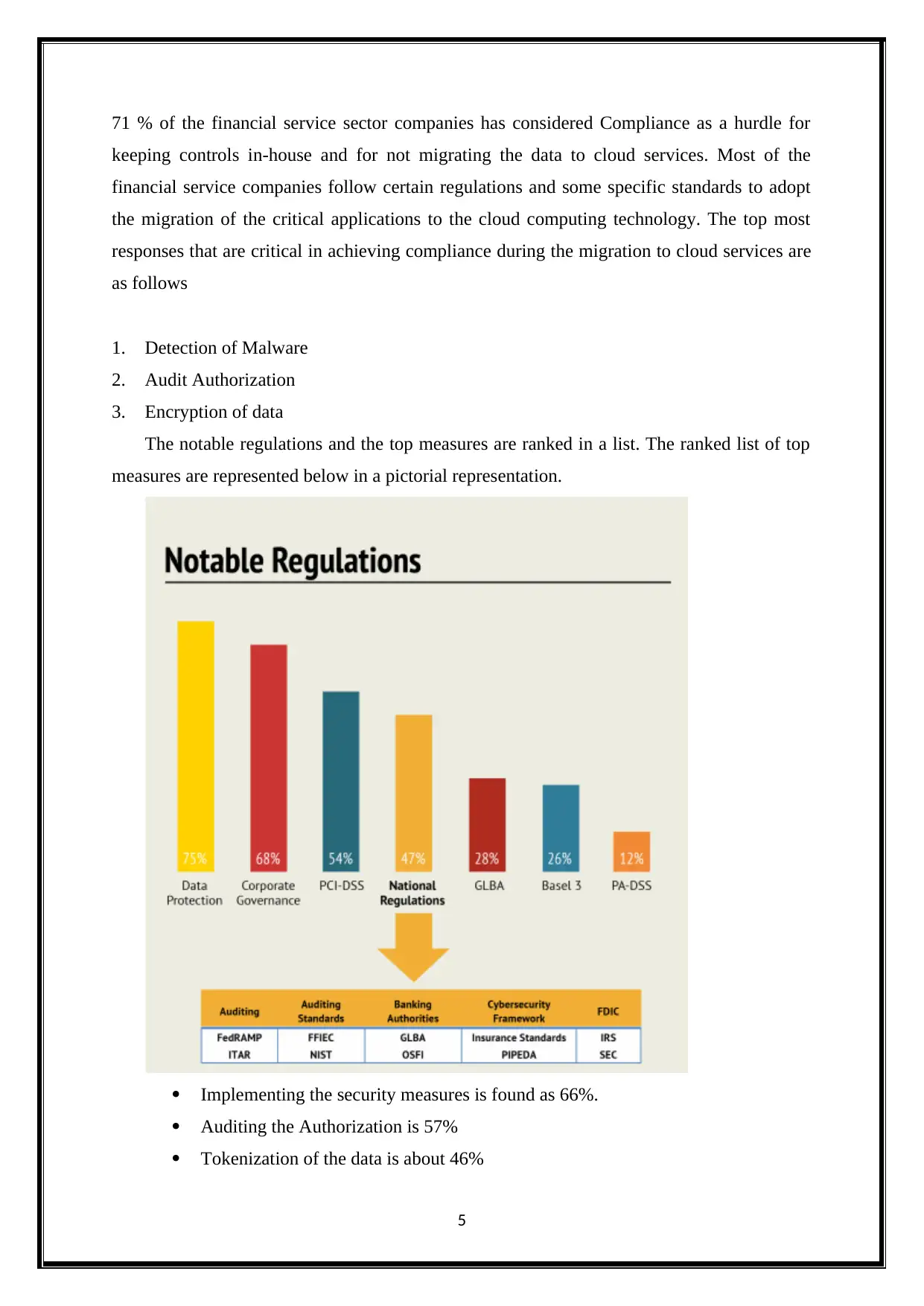
71 % of the financial service sector companies has considered Compliance as a hurdle for
keeping controls in-house and for not migrating the data to cloud services. Most of the
financial service companies follow certain regulations and some specific standards to adopt
the migration of the critical applications to the cloud computing technology. The top most
responses that are critical in achieving compliance during the migration to cloud services are
as follows
1. Detection of Malware
2. Audit Authorization
3. Encryption of data
The notable regulations and the top measures are ranked in a list. The ranked list of top
measures are represented below in a pictorial representation.
Implementing the security measures is found as 66%.
Auditing the Authorization is 57%
Tokenization of the data is about 46%
5
keeping controls in-house and for not migrating the data to cloud services. Most of the
financial service companies follow certain regulations and some specific standards to adopt
the migration of the critical applications to the cloud computing technology. The top most
responses that are critical in achieving compliance during the migration to cloud services are
as follows
1. Detection of Malware
2. Audit Authorization
3. Encryption of data
The notable regulations and the top measures are ranked in a list. The ranked list of top
measures are represented below in a pictorial representation.
Implementing the security measures is found as 66%.
Auditing the Authorization is 57%
Tokenization of the data is about 46%
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Encryption of the data is about 46%
Penalty for some of the incidents is about 42%
No data about the customer in cloud is 20%
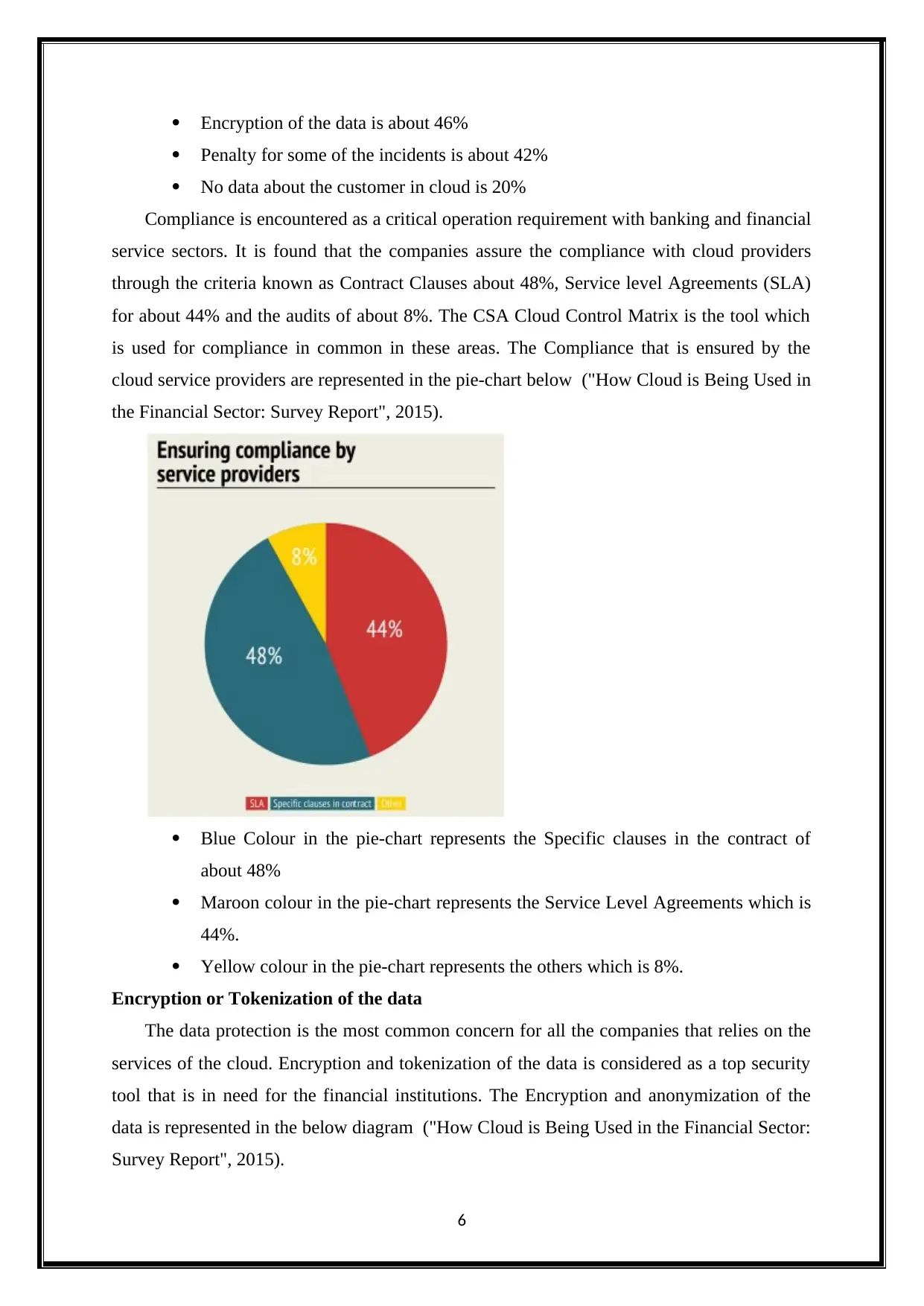
Compliance is encountered as a critical operation requirement with banking and financial
service sectors. It is found that the companies assure the compliance with cloud providers
through the criteria known as Contract Clauses about 48%, Service level Agreements (SLA)
for about 44% and the audits of about 8%. The CSA Cloud Control Matrix is the tool which
is used for compliance in common in these areas. The Compliance that is ensured by the
cloud service providers are represented in the pie-chart below ("How Cloud is Being Used in
the Financial Sector: Survey Report", 2015).
Blue Colour in the pie-chart represents the Specific clauses in the contract of
about 48%
Maroon colour in the pie-chart represents the Service Level Agreements which is
44%.
Yellow colour in the pie-chart represents the others which is 8%.
Encryption or Tokenization of the data
The data protection is the most common concern for all the companies that relies on the
services of the cloud. Encryption and tokenization of the data is considered as a top security
tool that is in need for the financial institutions. The Encryption and anonymization of the
data is represented in the below diagram ("How Cloud is Being Used in the Financial Sector:
Survey Report", 2015).
6
Penalty for some of the incidents is about 42%
No data about the customer in cloud is 20%
Compliance is encountered as a critical operation requirement with banking and financial
service sectors. It is found that the companies assure the compliance with cloud providers
through the criteria known as Contract Clauses about 48%, Service level Agreements (SLA)
for about 44% and the audits of about 8%. The CSA Cloud Control Matrix is the tool which
is used for compliance in common in these areas. The Compliance that is ensured by the
cloud service providers are represented in the pie-chart below ("How Cloud is Being Used in
the Financial Sector: Survey Report", 2015).
Blue Colour in the pie-chart represents the Specific clauses in the contract of
about 48%
Maroon colour in the pie-chart represents the Service Level Agreements which is
44%.
Yellow colour in the pie-chart represents the others which is 8%.
Encryption or Tokenization of the data
The data protection is the most common concern for all the companies that relies on the
services of the cloud. Encryption and tokenization of the data is considered as a top security
tool that is in need for the financial institutions. The Encryption and anonymization of the
data is represented in the below diagram ("How Cloud is Being Used in the Financial Sector:
Survey Report", 2015).
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
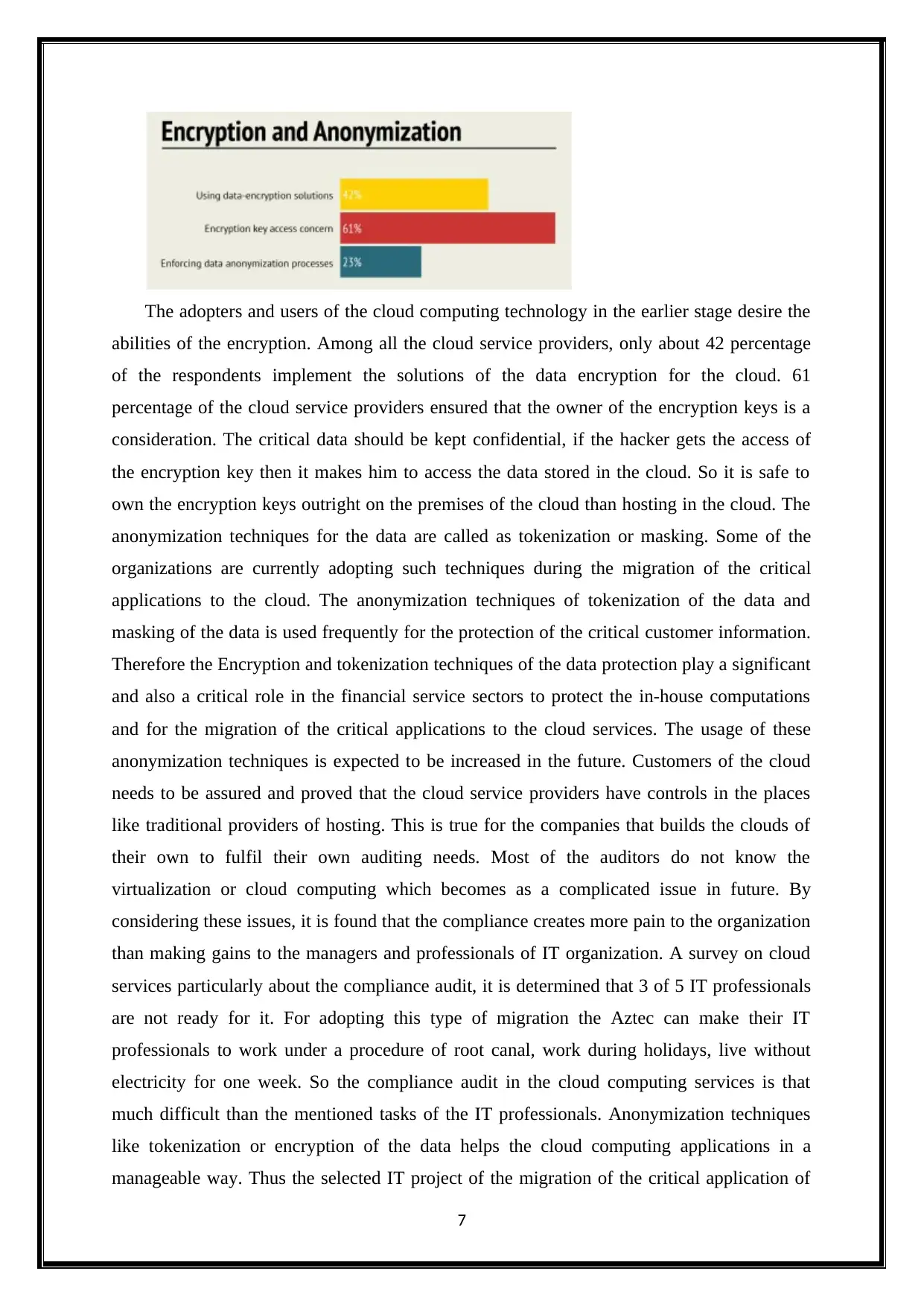
The adopters and users of the cloud computing technology in the earlier stage desire the
abilities of the encryption. Among all the cloud service providers, only about 42 percentage
of the respondents implement the solutions of the data encryption for the cloud. 61
percentage of the cloud service providers ensured that the owner of the encryption keys is a
consideration. The critical data should be kept confidential, if the hacker gets the access of
the encryption key then it makes him to access the data stored in the cloud. So it is safe to
own the encryption keys outright on the premises of the cloud than hosting in the cloud. The
anonymization techniques for the data are called as tokenization or masking. Some of the
organizations are currently adopting such techniques during the migration of the critical
applications to the cloud. The anonymization techniques of tokenization of the data and
masking of the data is used frequently for the protection of the critical customer information.
Therefore the Encryption and tokenization techniques of the data protection play a significant
and also a critical role in the financial service sectors to protect the in-house computations
and for the migration of the critical applications to the cloud services. The usage of these
anonymization techniques is expected to be increased in the future. Customers of the cloud
needs to be assured and proved that the cloud service providers have controls in the places
like traditional providers of hosting. This is true for the companies that builds the clouds of
their own to fulfil their own auditing needs. Most of the auditors do not know the
virtualization or cloud computing which becomes as a complicated issue in future. By
considering these issues, it is found that the compliance creates more pain to the organization
than making gains to the managers and professionals of IT organization. A survey on cloud
services particularly about the compliance audit, it is determined that 3 of 5 IT professionals
are not ready for it. For adopting this type of migration the Aztec can make their IT
professionals to work under a procedure of root canal, work during holidays, live without
electricity for one week. So the compliance audit in the cloud computing services is that
much difficult than the mentioned tasks of the IT professionals. Anonymization techniques
like tokenization or encryption of the data helps the cloud computing applications in a
manageable way. Thus the selected IT project of the migration of the critical application of
7
abilities of the encryption. Among all the cloud service providers, only about 42 percentage
of the respondents implement the solutions of the data encryption for the cloud. 61
percentage of the cloud service providers ensured that the owner of the encryption keys is a
consideration. The critical data should be kept confidential, if the hacker gets the access of
the encryption key then it makes him to access the data stored in the cloud. So it is safe to
own the encryption keys outright on the premises of the cloud than hosting in the cloud. The
anonymization techniques for the data are called as tokenization or masking. Some of the
organizations are currently adopting such techniques during the migration of the critical
applications to the cloud. The anonymization techniques of tokenization of the data and
masking of the data is used frequently for the protection of the critical customer information.
Therefore the Encryption and tokenization techniques of the data protection play a significant
and also a critical role in the financial service sectors to protect the in-house computations
and for the migration of the critical applications to the cloud services. The usage of these
anonymization techniques is expected to be increased in the future. Customers of the cloud
needs to be assured and proved that the cloud service providers have controls in the places
like traditional providers of hosting. This is true for the companies that builds the clouds of
their own to fulfil their own auditing needs. Most of the auditors do not know the
virtualization or cloud computing which becomes as a complicated issue in future. By
considering these issues, it is found that the compliance creates more pain to the organization
than making gains to the managers and professionals of IT organization. A survey on cloud
services particularly about the compliance audit, it is determined that 3 of 5 IT professionals
are not ready for it. For adopting this type of migration the Aztec can make their IT
professionals to work under a procedure of root canal, work during holidays, live without
electricity for one week. So the compliance audit in the cloud computing services is that
much difficult than the mentioned tasks of the IT professionals. Anonymization techniques
like tokenization or encryption of the data helps the cloud computing applications in a
manageable way. Thus the selected IT project of the migration of the critical application of
7

Aztec into a cloud computing technology is reviewed with respect to the financial service
sectors which includes the compliance issue of the cloud service technology ("How Cloud is
Being Used in the Financial Sector: Survey Report", 2015).
Impact on the Security Posture
Security Posture in an organization provides a point-in-time validation through the methods
called vulnerability assessment and the method of test in Penetration. The migration of the
data and critical applications to the cloud computing services do not restrict the existing
requirements of the security ("Security Posture Assessment | Locuz", 2017). The only change
that occurs in the migration is that the responsibility of maintaining the day to day security in
the data is given to the cloud service providers. This also reveals that the technical staffs of
the onsite will be handling uncovered potential risks, so if the applications are migrated to
cloud then it is easy to avoid those potential risks. The risks has to managed by the Aztec
organization is shifted to the cloud service providers. The migration of the critical
applications to the cloud service makes lot of changes in the IT security at the basic level.
This results that the business needs to make some changes to their business applications for
handling the data security once implementing the cloud platform. A clear cut view should be
reviewed between the responsibilities of the organization and of the cloud service providers.
In the business process of Aztec, the fundamentals of IT has created the sense making for that
organization. The experts say that the sense making is considered as one of the important
process in the companies that rely on the financial service sector. Sense making is the process
of scanning the entire surrounding and interact with every one in a proper way. The
interactive approach helps to take necessary actions (Lindqvist, 2013). The IT basics
outsourcing for Aztec is the significant method to maintain security and the process of
operations. When the migration of critical applications to the cloud computing services takes
place, then the access is given to the cloud service providers which makes an interactive
approach. The On-premise solutions are the solutions that are created in the traditional way.
Servers, Operating System and other hardware services may be included but these all happen
only within the data center. The outsourcing is given to the integrator who integrates the
service, but there is a need to offer physical security to the data, the electricity and the entries
of balance sheet for carrying the assets. When the critical application are hosted into a cloud,
then it is the responsibility of the cloud service provider. The service providers of the cloud
are agreed or contracted over a tenure and they offer some special functions for the
organization. The cloud service providers host the data in many locations, but the locations of
the cloud are known to the organization and it is fixed. The cloud service providers are
8
sectors which includes the compliance issue of the cloud service technology ("How Cloud is
Being Used in the Financial Sector: Survey Report", 2015).
Impact on the Security Posture
Security Posture in an organization provides a point-in-time validation through the methods
called vulnerability assessment and the method of test in Penetration. The migration of the
data and critical applications to the cloud computing services do not restrict the existing
requirements of the security ("Security Posture Assessment | Locuz", 2017). The only change
that occurs in the migration is that the responsibility of maintaining the day to day security in
the data is given to the cloud service providers. This also reveals that the technical staffs of
the onsite will be handling uncovered potential risks, so if the applications are migrated to
cloud then it is easy to avoid those potential risks. The risks has to managed by the Aztec
organization is shifted to the cloud service providers. The migration of the critical
applications to the cloud service makes lot of changes in the IT security at the basic level.
This results that the business needs to make some changes to their business applications for
handling the data security once implementing the cloud platform. A clear cut view should be
reviewed between the responsibilities of the organization and of the cloud service providers.
In the business process of Aztec, the fundamentals of IT has created the sense making for that
organization. The experts say that the sense making is considered as one of the important
process in the companies that rely on the financial service sector. Sense making is the process
of scanning the entire surrounding and interact with every one in a proper way. The
interactive approach helps to take necessary actions (Lindqvist, 2013). The IT basics
outsourcing for Aztec is the significant method to maintain security and the process of
operations. When the migration of critical applications to the cloud computing services takes
place, then the access is given to the cloud service providers which makes an interactive
approach. The On-premise solutions are the solutions that are created in the traditional way.
Servers, Operating System and other hardware services may be included but these all happen
only within the data center. The outsourcing is given to the integrator who integrates the
service, but there is a need to offer physical security to the data, the electricity and the entries
of balance sheet for carrying the assets. When the critical application are hosted into a cloud,
then it is the responsibility of the cloud service provider. The service providers of the cloud
are agreed or contracted over a tenure and they offer some special functions for the
organization. The cloud service providers host the data in many locations, but the locations of
the cloud are known to the organization and it is fixed. The cloud service providers are
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

responsible for all the offers that they provide to the organization. The future impacts or any
issues are responsible for them only. The critical application hosting provider offers all the
support and the configuration that is required for the application. If the organization Aztec
cannot offer as much as staff who are expertise, then it is best to adopt the cloud service
offerings. If the organization has to provide services and support for 24 hours in all the 7 days
of the week, then it is best to select the cloud service rather than trusting on the labours. The
IT operations of the Aztec on premise has to rely on the man power for the security policies
and procedures. It may not be fair that every time the person may be alert. Human beings are
liable to make errors. So it is best to believe a system called Cloud computing service than
having belief in a person. The system can also make errors but it can be recovered. Then the
cloud service providers are responsible for the errors that they make. So the organization may
be stress free. The persons with less expertise can be appointed for the cloud computing
services. Thus the review is performed in the project of migrating the critical applications to
be hosted in the cloud in the basis of security posture. The current security policies and
postures of the Aztec is compared in contrast with cloud computing services ("On-premise
vs. cloud-based solutions", 2017).
Threats, Vulnerabilities and Consequences
In today's world there are new inventions and improvements in the information
technology. The organization that are operating in the financial service sector is undergoing
into many problems and challenges in innovations and adoptions of the new technologies
(Dahbur, Mohammad & Tarakji, 2011). The upcoming sections describes about the threats,
vulnerabilities and consequences that rely on the IT service outsourcing in Aztec organization
(Lindqvist, 2013).
Threats of IT operations
The threats that affect the security in financial service sector organizations like Aztec are
in increased rate (Grundey, 2008). To secure the entire system of the Aztec organization that
is connected with the public network is not that much easy. A single system that is
maintained by the organization is not a secured system and so the organization has planned to
migrate the applications to the cloud service. The different types of services and offerings are
provided by the cloud service providers. The information has been hacked in an increasing
rate in today's technology. As the advantages of the technology becomes more reliable, the
chance of hacking is also increased. Different types of attacks like spamming, malware
injection, spoofing and other attacks like DDoS, man in the middle and eavesdropping are in
the increasing rate. It is significant in the financial service sector to protect the system and
9
issues are responsible for them only. The critical application hosting provider offers all the
support and the configuration that is required for the application. If the organization Aztec
cannot offer as much as staff who are expertise, then it is best to adopt the cloud service
offerings. If the organization has to provide services and support for 24 hours in all the 7 days
of the week, then it is best to select the cloud service rather than trusting on the labours. The
IT operations of the Aztec on premise has to rely on the man power for the security policies
and procedures. It may not be fair that every time the person may be alert. Human beings are
liable to make errors. So it is best to believe a system called Cloud computing service than
having belief in a person. The system can also make errors but it can be recovered. Then the
cloud service providers are responsible for the errors that they make. So the organization may
be stress free. The persons with less expertise can be appointed for the cloud computing
services. Thus the review is performed in the project of migrating the critical applications to
be hosted in the cloud in the basis of security posture. The current security policies and
postures of the Aztec is compared in contrast with cloud computing services ("On-premise
vs. cloud-based solutions", 2017).
Threats, Vulnerabilities and Consequences
In today's world there are new inventions and improvements in the information
technology. The organization that are operating in the financial service sector is undergoing
into many problems and challenges in innovations and adoptions of the new technologies
(Dahbur, Mohammad & Tarakji, 2011). The upcoming sections describes about the threats,
vulnerabilities and consequences that rely on the IT service outsourcing in Aztec organization
(Lindqvist, 2013).
Threats of IT operations
The threats that affect the security in financial service sector organizations like Aztec are
in increased rate (Grundey, 2008). To secure the entire system of the Aztec organization that
is connected with the public network is not that much easy. A single system that is
maintained by the organization is not a secured system and so the organization has planned to
migrate the applications to the cloud service. The different types of services and offerings are
provided by the cloud service providers. The information has been hacked in an increasing
rate in today's technology. As the advantages of the technology becomes more reliable, the
chance of hacking is also increased. Different types of attacks like spamming, malware
injection, spoofing and other attacks like DDoS, man in the middle and eavesdropping are in
the increasing rate. It is significant in the financial service sector to protect the system and
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

credentials, they need to take high measures for securing those information. Aztec should
make sure that their information are secured and the customers of the organization should
believe the system that it is secured. When the organization migrates the critical applications
to the cloud services, the organization should make sure that the credentials and transactions
of the customers are confidential. The organization should make sure of the data recovery in
case of any failures (Javaid, 2013).
Vulnerabilities in IT Operations Outsourcing
The organization Aztec that is under the financial service sector may get misloaded
because of the exposure of the security risks and also becomes a victim for the security
breach. When the applications of the organization is migrated to a cloud, it is not sure that the
service providers will illegally monitor the transactions and the credentials of the customers
of the organization. The cloud service provider may not perform any illegal actions but there
are possibilities in hacking the cloud computing service. The hackers may use the system of
cloud to steal the information of the customers. Because of this hacking, there may be a
leakage of the customer information, hacking the personal credentials like username and
password, personal data extraction from the customer database that is being stored in the
cloud computing services, authentication risks and also they may sell these information to
other organizations which makes the loss in business operations and affects the growth of
Aztec. This information shows that the vulnerability in the IT services of the organization is
the weakness or less concentration on the security of the assets. As it is financial
organization, there is a chance of withdrawal of the funds by using the user's credentials.
There may be vulnerability in the security breach as the system and data is totally based on
the cloud service providers (Sheetlani, 2017).
Breach of data
The data breach or loss in data occurs only when the important area of the data of the
client gets accessed by the hacker or any unauthorized person. The organization has to do
periodic monitoring process to make sure that there is no leakage in the customer information
(Rao & Selvamani, 2015).
Location of the data
In some organizations, the customer do not know where their data is physically located.
Aztec must make sure of the location of the data physically (Rao & Selvamani, 2015).
Storage of the data
The data that is stored in the cloud can be divided into 2 divisions such as The data that
is stored in the IaaS environment and the data that is stored in the PaaS or SaaS environment
10
make sure that their information are secured and the customers of the organization should
believe the system that it is secured. When the organization migrates the critical applications
to the cloud services, the organization should make sure that the credentials and transactions
of the customers are confidential. The organization should make sure of the data recovery in
case of any failures (Javaid, 2013).
Vulnerabilities in IT Operations Outsourcing
The organization Aztec that is under the financial service sector may get misloaded
because of the exposure of the security risks and also becomes a victim for the security
breach. When the applications of the organization is migrated to a cloud, it is not sure that the
service providers will illegally monitor the transactions and the credentials of the customers
of the organization. The cloud service provider may not perform any illegal actions but there
are possibilities in hacking the cloud computing service. The hackers may use the system of
cloud to steal the information of the customers. Because of this hacking, there may be a
leakage of the customer information, hacking the personal credentials like username and
password, personal data extraction from the customer database that is being stored in the
cloud computing services, authentication risks and also they may sell these information to
other organizations which makes the loss in business operations and affects the growth of
Aztec. This information shows that the vulnerability in the IT services of the organization is
the weakness or less concentration on the security of the assets. As it is financial
organization, there is a chance of withdrawal of the funds by using the user's credentials.
There may be vulnerability in the security breach as the system and data is totally based on
the cloud service providers (Sheetlani, 2017).
Breach of data
The data breach or loss in data occurs only when the important area of the data of the
client gets accessed by the hacker or any unauthorized person. The organization has to do
periodic monitoring process to make sure that there is no leakage in the customer information
(Rao & Selvamani, 2015).
Location of the data
In some organizations, the customer do not know where their data is physically located.
Aztec must make sure of the location of the data physically (Rao & Selvamani, 2015).
Storage of the data
The data that is stored in the cloud can be divided into 2 divisions such as The data that
is stored in the IaaS environment and the data that is stored in the PaaS or SaaS environment
10

which is related to the cloud computing applications. The data of the organization that is
stored in the cloud environment should be considered in 3 different aspects like
confidentiality, integrity and availability (Omotunde, Adekogbe, Ernest & Uchendu, 2016).
Archival of the Data
Archiving for the data that is being focused on the storage of the cloud either to offer the
storage in off-site or in the storage duration. If the service providers of the cloud computing
environment does not offer archiving in the off-sit, then there occurs the threat in the data
availability (Omotunde, Adekogbe, Ernest & Uchendu, 2016).
Assessing the consequences of IT operations
The threats and the vulnerabilities that are involved in the organization is discussed
above. To avoid or handle those threats and vulnerabilities, the company has to follow a risk
management plan in an organized way. The risk management plan should be able to make
interaction with customers and the Aztec via the applications (Balbás & Garrido, 2014). The
risk management plan includes the steps as follows
Risk Identification
The threats and vulnerabilities that are included in the service provided by the
organization should be identified through a regular monitoring process (Douglass, 2009).
Risk Assessment
The Aztec should perform and develop a matrix on the identified threats and
vulnerabilities. Aztec should find the different varieties of the threats and vulnerabilities.
Treating the Risk
The identified risk has to be treated. Different strategies should be followed for different
threats. Each and every risk has to be handled in different ways like mitigation, transfer and
avoidance.
Risk Report
Aztec has to maintain a log to keep track of the risks and their strategies how they solved
it, so that they can find if similar risk is identified in future (Balbás & Garrido, 2014).
Risks in Data Security
Data Security is the common thing for any type of service or technology. But it becomes
a big challenge for the organization and user who rely on their service providers. In SaaS, the
data that is provided by the organization is frequently being processed in the form of plaintext
and it is stored in the cloud technology. The critical aspect in the use of SaaS service provider
is that the backing up the data which is used in recovery in the future during any disasters
(Omotunde, Adekogbe, Ernest & Uchendu, 2016).
11
stored in the cloud environment should be considered in 3 different aspects like
confidentiality, integrity and availability (Omotunde, Adekogbe, Ernest & Uchendu, 2016).
Archival of the Data
Archiving for the data that is being focused on the storage of the cloud either to offer the
storage in off-site or in the storage duration. If the service providers of the cloud computing
environment does not offer archiving in the off-sit, then there occurs the threat in the data
availability (Omotunde, Adekogbe, Ernest & Uchendu, 2016).
Assessing the consequences of IT operations
The threats and the vulnerabilities that are involved in the organization is discussed
above. To avoid or handle those threats and vulnerabilities, the company has to follow a risk
management plan in an organized way. The risk management plan should be able to make
interaction with customers and the Aztec via the applications (Balbás & Garrido, 2014). The
risk management plan includes the steps as follows
Risk Identification
The threats and vulnerabilities that are included in the service provided by the
organization should be identified through a regular monitoring process (Douglass, 2009).
Risk Assessment
The Aztec should perform and develop a matrix on the identified threats and
vulnerabilities. Aztec should find the different varieties of the threats and vulnerabilities.
Treating the Risk
The identified risk has to be treated. Different strategies should be followed for different
threats. Each and every risk has to be handled in different ways like mitigation, transfer and
avoidance.
Risk Report
Aztec has to maintain a log to keep track of the risks and their strategies how they solved
it, so that they can find if similar risk is identified in future (Balbás & Garrido, 2014).
Risks in Data Security
Data Security is the common thing for any type of service or technology. But it becomes
a big challenge for the organization and user who rely on their service providers. In SaaS, the
data that is provided by the organization is frequently being processed in the form of plaintext
and it is stored in the cloud technology. The critical aspect in the use of SaaS service provider
is that the backing up the data which is used in recovery in the future during any disasters
(Omotunde, Adekogbe, Ernest & Uchendu, 2016).
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





