IT Risk Assessment Report: Analysis of Cloud Migration Risks for Aztek
VerifiedAdded on 2020/03/23
|21
|4990
|342
Report
AI Summary
This IT Risk Assessment Report examines the implications of migrating a fictional financial firm, Aztek, to a cloud hosting solution. It begins by outlining cloud computing characteristics and their application within the financial sector, including discussions on cloud delivery and deployment models like SaaS, IaaS, PaaS, and hybrid cloud solutions. The report then delves into security risks and vulnerabilities associated with cloud technology, emphasizing issues relevant to financial institutions. It highlights the importance of risk assessment, security requirements, and mitigation measures. The report provides recommendations for Aztek's management regarding cloud security strategies, considering the relationship between financial organizations, cloud service providers, and the need for clarity, assertion, and information promotion. The report concludes with an analysis of future cloud adoption trends, including analytical risk calculations, performance acknowledgment, operational identity, and positional data implications, making it a comprehensive resource for understanding cloud migration challenges and opportunities in the financial industry.
IT Risk Assessment Report
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Executive Summary
Today, the current exhortation in technology is cloud computing. Through the implicit of
storage space, processing power, and utilizations, Cloud computing is considered to be similar to
the grid computing model. But, the cloud computing proffers more technology prototypes when
compared to other type of computing models.
The Australian financial industry is slowly adopting the cloud computing technology. But most
of the companies in financial sector depend upon their domestic infrastructure. The financial
sector organizations are aware of the financial advantages accompanied by both the private cloud
and public cloud exploitation models.
However they are wary on the risk of dropping control over sensitive information. And, the most
general cloud model deployed by financial organization is hybrid cloud. But National Financial
Supervisory Authorities (NFSA) generally recommends the private cloud strategy since more
data manipulation is provided by private cloud.
The main objective of this report is to provide the case study on risk assessment when the
business critical applications of fictional company “Aztek” operating in financial sector are
migrated to an external cloud hosting solution. Initially, the report focuses on the characteristics
of cloud computing and its application on the financial firm. Then the different type of security
risks and vulnerabilities confronted after the application of cloud technology are discussed.
As an IT risk assessment lead, the recommendations on different cloud security strategies for the
Aztek management based on the analysis are illustrated in the report.
Today, the current exhortation in technology is cloud computing. Through the implicit of
storage space, processing power, and utilizations, Cloud computing is considered to be similar to
the grid computing model. But, the cloud computing proffers more technology prototypes when
compared to other type of computing models.
The Australian financial industry is slowly adopting the cloud computing technology. But most
of the companies in financial sector depend upon their domestic infrastructure. The financial
sector organizations are aware of the financial advantages accompanied by both the private cloud
and public cloud exploitation models.
However they are wary on the risk of dropping control over sensitive information. And, the most
general cloud model deployed by financial organization is hybrid cloud. But National Financial
Supervisory Authorities (NFSA) generally recommends the private cloud strategy since more
data manipulation is provided by private cloud.
The main objective of this report is to provide the case study on risk assessment when the
business critical applications of fictional company “Aztek” operating in financial sector are
migrated to an external cloud hosting solution. Initially, the report focuses on the characteristics
of cloud computing and its application on the financial firm. Then the different type of security
risks and vulnerabilities confronted after the application of cloud technology are discussed.
As an IT risk assessment lead, the recommendations on different cloud security strategies for the
Aztek management based on the analysis are illustrated in the report.

Table of Contents
Executive Summary 2
1. Introduction 4
1.1. Scope and Purpose 4
1.2. Target Audience 4
1.3. Research Methods 5
2. Cloud Delivery and Deployment Models 5
2.1. Cloud Delivery Models 5
2.1. Cloud Deployment Models 6
3. Deployment of cloud solution in Finance Sector 6
4. Future Trends in Cloud Adoption 9
4.1. Analytical Calculation of Risks 9
4.2. Performance Acknowledgement 10
4.3. Operational Identity and Resolution 10
4.4. Positional data implicit 10
5. Risks and Confrontations 11
5.1. Security Issues 11
5.2. Risk Assessment by Enterprise 12
6. Security Necessities and Alleviation Measures 13
6.1. Cloud Security Requirements 13
6.2. Alleviation Measures 15
7. Recommendations 16
7.1 Relationship between financial organizations, fictional firm, and Cloud Service Providers. 16
7.2. Cloud Based Method 16
7.3. Lucidity and Assertion 16
7.4. Information Promotion 17
8. Conclusion 17
8. References 18
Executive Summary 2
1. Introduction 4
1.1. Scope and Purpose 4
1.2. Target Audience 4
1.3. Research Methods 5
2. Cloud Delivery and Deployment Models 5
2.1. Cloud Delivery Models 5
2.1. Cloud Deployment Models 6
3. Deployment of cloud solution in Finance Sector 6
4. Future Trends in Cloud Adoption 9
4.1. Analytical Calculation of Risks 9
4.2. Performance Acknowledgement 10
4.3. Operational Identity and Resolution 10
4.4. Positional data implicit 10
5. Risks and Confrontations 11
5.1. Security Issues 11
5.2. Risk Assessment by Enterprise 12
6. Security Necessities and Alleviation Measures 13
6.1. Cloud Security Requirements 13
6.2. Alleviation Measures 15
7. Recommendations 16
7.1 Relationship between financial organizations, fictional firm, and Cloud Service Providers. 16
7.2. Cloud Based Method 16
7.3. Lucidity and Assertion 16
7.4. Information Promotion 17
8. Conclusion 17
8. References 18
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1. Introduction
Cloud representation containing 5 distinctive behaviors, 4 operation models, and 3 distribution
replicas endorses accessibility. Moreover, the amalgamation of automated processing and
communal services like telephone or power makes the core of cloud computing (Borking &
Raab, 2010). Similar to public utilities, the payment is made by the cloud users only based on the
utilization of the computing resources. The cloud computing is a system that administers the pool
of dispersed computing sources by its own self. The next section discusses about the cloud
delivery and deployment models.
1.1. Scope and Purpose
The main objective of this case study is to emphasize the risks and prospects associated with the
cloud, and for presenting the counseling relative to the employment of cloud computing in
organization. The purpose of this study is enlisted below:
To present a summary on the implementation of cloud computing amenities in the
Australian financial sector
For revaluating the existing adaptation related to cloud computing espousal mainly in the
financial industry.
To provide a deliberate method for the adoption on cloud services.
For ascertaining the imp editions for cloud adoption.
The risks due to the migration of critical business decisions to external cloud hosting
solution are identified.
To review and explain the cloud computing prospects in financial segment.
1.2. Target Audience
The report outcomes are mainly intended for the spectators enlisted below:
Financial companies like indemnity firm, asset traders, and bank conviction enterprises.
Cloud mediators and cloud service contributors requiring addition assistance on the
safety policies and procedures. By this way, they can effectively evaluate the
requirements for enhancing their prevailing cloud service.
Cloud representation containing 5 distinctive behaviors, 4 operation models, and 3 distribution
replicas endorses accessibility. Moreover, the amalgamation of automated processing and
communal services like telephone or power makes the core of cloud computing (Borking &
Raab, 2010). Similar to public utilities, the payment is made by the cloud users only based on the
utilization of the computing resources. The cloud computing is a system that administers the pool
of dispersed computing sources by its own self. The next section discusses about the cloud
delivery and deployment models.
1.1. Scope and Purpose
The main objective of this case study is to emphasize the risks and prospects associated with the
cloud, and for presenting the counseling relative to the employment of cloud computing in
organization. The purpose of this study is enlisted below:
To present a summary on the implementation of cloud computing amenities in the
Australian financial sector
For revaluating the existing adaptation related to cloud computing espousal mainly in the
financial industry.
To provide a deliberate method for the adoption on cloud services.
For ascertaining the imp editions for cloud adoption.
The risks due to the migration of critical business decisions to external cloud hosting
solution are identified.
To review and explain the cloud computing prospects in financial segment.
1.2. Target Audience
The report outcomes are mainly intended for the spectators enlisted below:
Financial companies like indemnity firm, asset traders, and bank conviction enterprises.
Cloud mediators and cloud service contributors requiring addition assistance on the
safety policies and procedures. By this way, they can effectively evaluate the
requirements for enhancing their prevailing cloud service.

1.3. Research Methods
This report comprises sources from
1. Significant Market Analyst reports
2. Technical web pages, white papers, and blogs obtainable from the Internet
3. Methodical Journals, and
4. White papers specific to cloud service traders
2. Cloud Delivery and Deployment Models
2.1. Cloud Delivery Models
The cloud computing is dispersed by means of delivery prototypes as given below:
Software as a Service (SaaS)
An intermediary cloud service provider congregates the applications that are accessible
by the users through Internet by means of SaaS model. Examples of SaaS provider
include Google Docs and Salesforce.com.
Infrastructure as a Service (IaaS)
IaaS, a kind of cloud computing, offers effective enumerative schemes over the computer
network. The examples of IaaS are Rackspace, Amazon EC2, and NYSE Euronext
CMCP.
Platform as a Service (PaaS)
PaaS proffers a policy to the users for letting them to draft, execute, and handle the cloud
applications devoid of building and maintaining complex infrastructure. Examples of
PaaS are inclusive of Google App Engine and Microsoft Azure.
Business Process as a Service (BPaaS)
BPaaS is a cloud model based on Business Process Outsourcing, whose main objective is
the reduction in manual labor by means of augmented computerization, so as to suppress
the overall process cost.
This report comprises sources from
1. Significant Market Analyst reports
2. Technical web pages, white papers, and blogs obtainable from the Internet
3. Methodical Journals, and
4. White papers specific to cloud service traders
2. Cloud Delivery and Deployment Models
2.1. Cloud Delivery Models
The cloud computing is dispersed by means of delivery prototypes as given below:
Software as a Service (SaaS)
An intermediary cloud service provider congregates the applications that are accessible
by the users through Internet by means of SaaS model. Examples of SaaS provider
include Google Docs and Salesforce.com.
Infrastructure as a Service (IaaS)
IaaS, a kind of cloud computing, offers effective enumerative schemes over the computer
network. The examples of IaaS are Rackspace, Amazon EC2, and NYSE Euronext
CMCP.
Platform as a Service (PaaS)
PaaS proffers a policy to the users for letting them to draft, execute, and handle the cloud
applications devoid of building and maintaining complex infrastructure. Examples of
PaaS are inclusive of Google App Engine and Microsoft Azure.
Business Process as a Service (BPaaS)
BPaaS is a cloud model based on Business Process Outsourcing, whose main objective is
the reduction in manual labor by means of augmented computerization, so as to suppress
the overall process cost.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

2.2. Cloud Deployment Models
The aforementioned cloud amenities disseminated by the following cloud exploitation models.
Public Cloud:
All users are able to access the public cloud by using Internet. The whole thing ranging
from amenities, computing sources, to maneuvers are administered and possessed by the
cloud supplier. Examples for public cloud are inclusive of Microsoft Azure, Amazon
EC2, and Google App Engine.
Community Cloud:
The members of an outsized area comprising several groups or enterprises can have
access to the community cloud. The business activities ranging from processes to features
are co-administered by the cloud contributors and associate enterprises.
Private Cloud:
The private cloud can be handled by cloud service contributor or the firm. The legitimate
organizational users alone can acquire permission to use the private cloud.
Hybrid Cloud:
It is a unified model of both private and public clouds. The confrontations encountered by
means of private or public cloud can be tackled by the hybrid cloud.
3. Deployment of Cloud solution in Finance Sector
Cloud reception is in the beginning periods in Australian finance related industry. The
constrained scopes of cloud based administrations are utilized by numerous financial industries.
By means of expanded utilization of information escalated software that requires the utilization
of back-end cloud applications, the Australia’s interest for cloud administrations is increased. A
normal IT cost investment funds of 12% is revealed by using distributed computing
administrations and hence the cost sparing is the key factor for cloud with associations . During
the year 2013, the IaaS, PaaS, and SaaS have transformed the Australian’s cloud computing
market to generate an income of 1.23 billion dollars.
According to the most recent report provided by Frost and Sullivan, the Growth Partnership firm,
the Australian cloud computing market has now risen up out of the earlier adopter stage to the
The aforementioned cloud amenities disseminated by the following cloud exploitation models.
Public Cloud:
All users are able to access the public cloud by using Internet. The whole thing ranging
from amenities, computing sources, to maneuvers are administered and possessed by the
cloud supplier. Examples for public cloud are inclusive of Microsoft Azure, Amazon
EC2, and Google App Engine.
Community Cloud:
The members of an outsized area comprising several groups or enterprises can have
access to the community cloud. The business activities ranging from processes to features
are co-administered by the cloud contributors and associate enterprises.
Private Cloud:
The private cloud can be handled by cloud service contributor or the firm. The legitimate
organizational users alone can acquire permission to use the private cloud.
Hybrid Cloud:
It is a unified model of both private and public clouds. The confrontations encountered by
means of private or public cloud can be tackled by the hybrid cloud.
3. Deployment of Cloud solution in Finance Sector
Cloud reception is in the beginning periods in Australian finance related industry. The
constrained scopes of cloud based administrations are utilized by numerous financial industries.
By means of expanded utilization of information escalated software that requires the utilization
of back-end cloud applications, the Australia’s interest for cloud administrations is increased. A
normal IT cost investment funds of 12% is revealed by using distributed computing
administrations and hence the cost sparing is the key factor for cloud with associations . During
the year 2013, the IaaS, PaaS, and SaaS have transformed the Australian’s cloud computing
market to generate an income of 1.23 billion dollars.
According to the most recent report provided by Frost and Sullivan, the Growth Partnership firm,
the Australian cloud computing market has now risen up out of the earlier adopter stage to the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

earlier developer phase of cloud reception by means of extensive market ((Cavoukian &
Crompton, 2001). Even though the cloud computing has seen solid improvement in the year
2014, the cloud market has started to decrease since it achieves a higher condition of
development.
From the year 2013-2018, the CAGR of 30% will be attained and the revenues are about to reach
4.45 billion dollars. The growth of IaaS and PaaS will be higher when compared to SaaS model.
Hence it is evident that the confidence is grown among the people after the incorporation of
cloud service models in their own organization. But while migrating the business critical
applications to cloud, some range of cautions are noted down. Most of the users have some
concerns in transforming the banking pursuits to the cloud (Hall & Liedtka, 2007). Instead of
that, they are utilizing it to digitally convert their business.
Major causes for the financial organizations not possessing a well-structured cloud solution are
There are certain limitations on the regulations imposed on the financial organizations for
utilizing the cloud services (Rose, 2011).
The cloud computing is not approached strategically intrinsic to the enterprises.
Users have some issues related to the security breaches.
The cloud prospects are not assessed due to the absence of significance for cloud
products.
Issues because of the investigation by Government
To conclude with, about 10% of the organizations are not interested to deploy cloud strategy for
their financial activities.
Major causes for not employing cloud service in the financial organizations are
Data privacy and safety issues
Legal Conformity
Most of the cloud intrinsic policies are not fulfilled by the cloud contributors.
The users are waiting for the extensive implementation of the cloud solutions.
The cloud applications adopted by most of the financial organizations are:
Crompton, 2001). Even though the cloud computing has seen solid improvement in the year
2014, the cloud market has started to decrease since it achieves a higher condition of
development.
From the year 2013-2018, the CAGR of 30% will be attained and the revenues are about to reach
4.45 billion dollars. The growth of IaaS and PaaS will be higher when compared to SaaS model.
Hence it is evident that the confidence is grown among the people after the incorporation of
cloud service models in their own organization. But while migrating the business critical
applications to cloud, some range of cautions are noted down. Most of the users have some
concerns in transforming the banking pursuits to the cloud (Hall & Liedtka, 2007). Instead of
that, they are utilizing it to digitally convert their business.
Major causes for the financial organizations not possessing a well-structured cloud solution are
There are certain limitations on the regulations imposed on the financial organizations for
utilizing the cloud services (Rose, 2011).
The cloud computing is not approached strategically intrinsic to the enterprises.
Users have some issues related to the security breaches.
The cloud prospects are not assessed due to the absence of significance for cloud
products.
Issues because of the investigation by Government
To conclude with, about 10% of the organizations are not interested to deploy cloud strategy for
their financial activities.
Major causes for not employing cloud service in the financial organizations are
Data privacy and safety issues
Legal Conformity
Most of the cloud intrinsic policies are not fulfilled by the cloud contributors.
The users are waiting for the extensive implementation of the cloud solutions.
The cloud applications adopted by most of the financial organizations are:
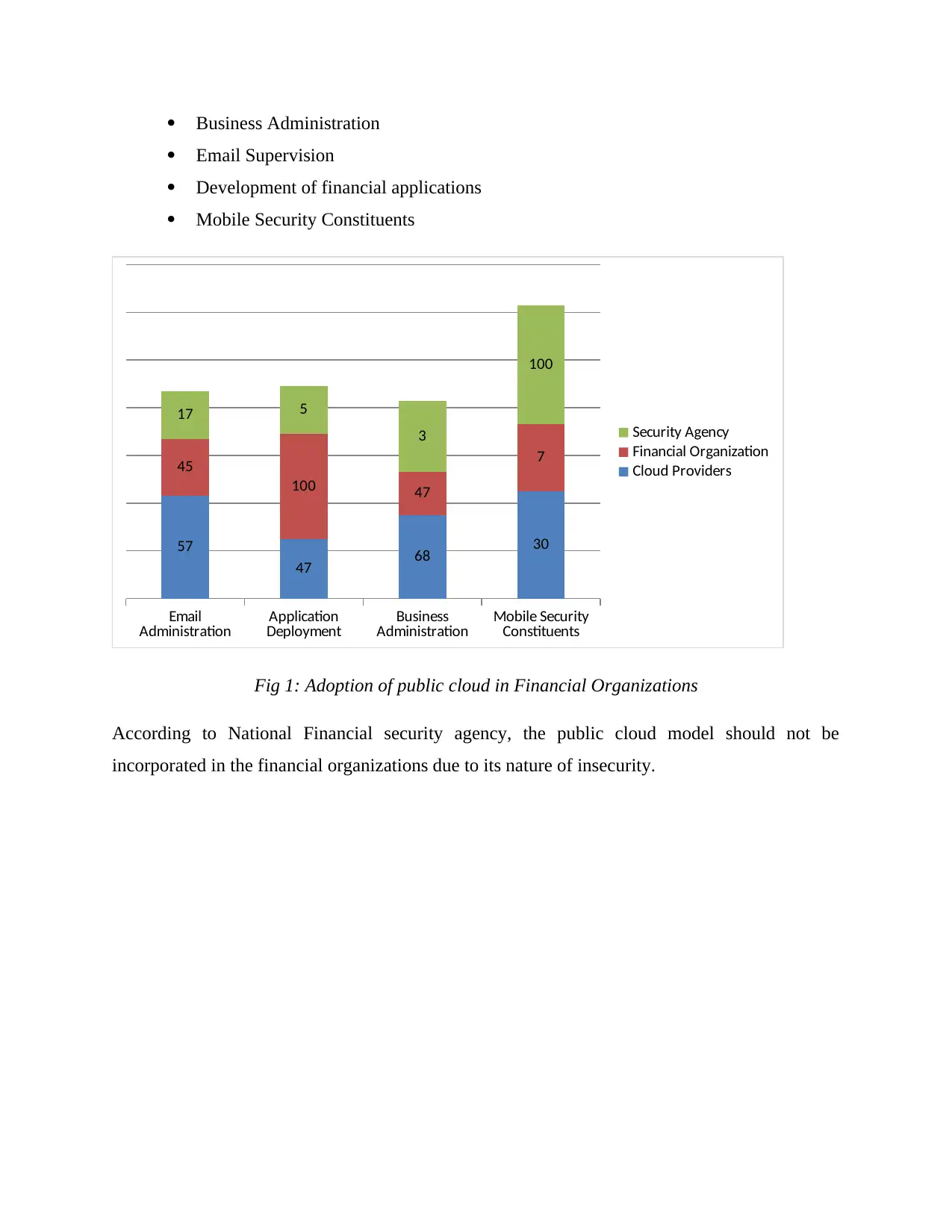
Business Administration
Email Supervision
Development of financial applications
Mobile Security Constituents
Email
Administration Application
Deployment Business
Administration Mobile Security
Constituents
57
47 68 30
45
100 47
7
17 5
3
100
Security Agency
Financial Organization
Cloud Providers
Fig 1: Adoption of public cloud in Financial Organizations
According to National Financial security agency, the public cloud model should not be
incorporated in the financial organizations due to its nature of insecurity.
Email Supervision
Development of financial applications
Mobile Security Constituents
Administration Application
Deployment Business
Administration Mobile Security
Constituents
57
47 68 30
45
100 47
7
17 5
3
100
Security Agency
Financial Organization
Cloud Providers
Fig 1: Adoption of public cloud in Financial Organizations
According to National Financial security agency, the public cloud model should not be
incorporated in the financial organizations due to its nature of insecurity.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Email
Administration Application
Deployment Business
Administration Mobile Security
Constituents
83
64 80 40
40
80 47
17
7 5
3
100
Security Agency
Financial Organization
Cloud Providers
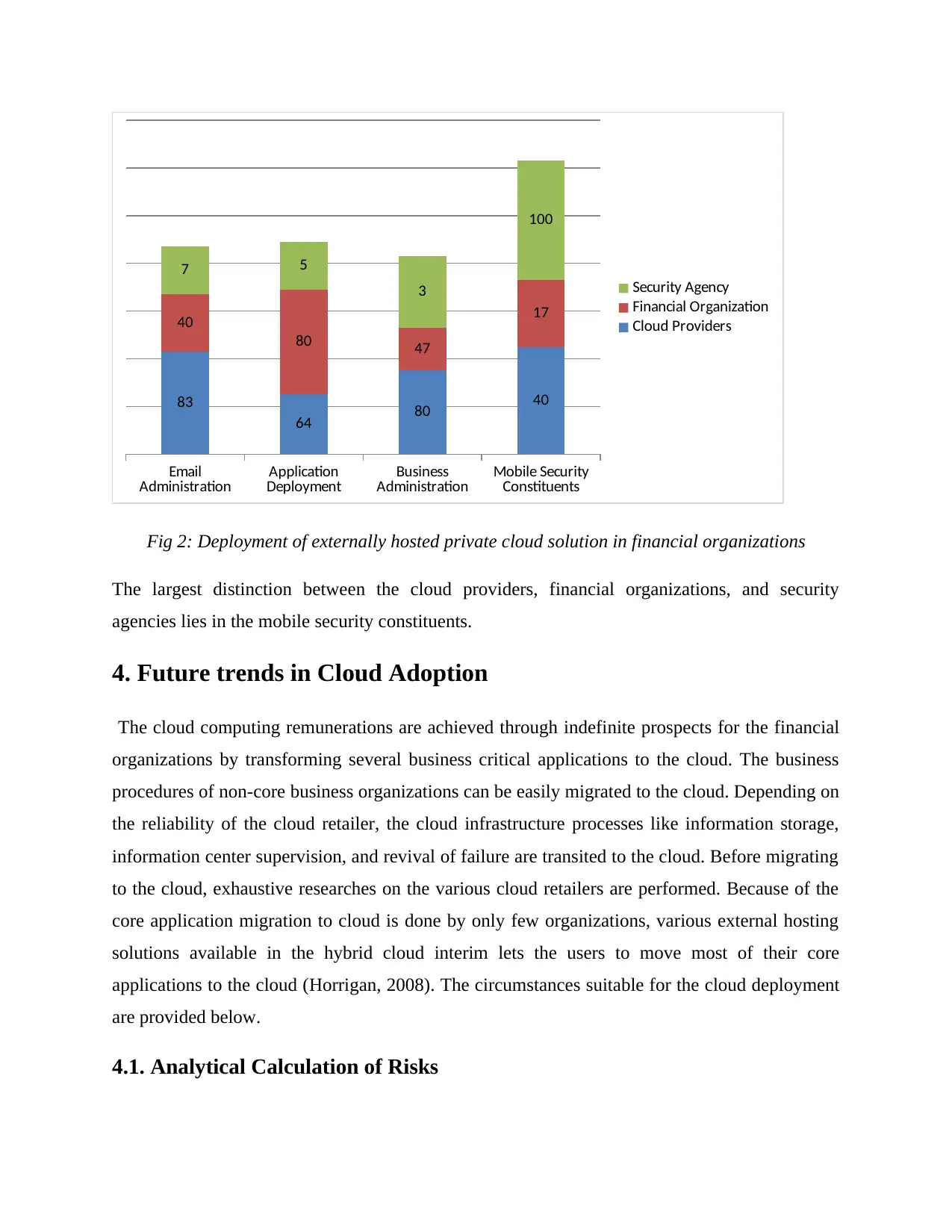
Fig 2: Deployment of externally hosted private cloud solution in financial organizations
The largest distinction between the cloud providers, financial organizations, and security
agencies lies in the mobile security constituents.
4. Future trends in Cloud Adoption
The cloud computing remunerations are achieved through indefinite prospects for the financial
organizations by transforming several business critical applications to the cloud. The business
procedures of non-core business organizations can be easily migrated to the cloud. Depending on
the reliability of the cloud retailer, the cloud infrastructure processes like information storage,
information center supervision, and revival of failure are transited to the cloud. Before migrating
to the cloud, exhaustive researches on the various cloud retailers are performed. Because of the
core application migration to cloud is done by only few organizations, various external hosting
solutions available in the hybrid cloud interim lets the users to move most of their core
applications to the cloud (Horrigan, 2008). The circumstances suitable for the cloud deployment
are provided below.
4.1. Analytical Calculation of Risks
Administration Application
Deployment Business
Administration Mobile Security
Constituents
83
64 80 40
40
80 47
17
7 5
3
100
Security Agency
Financial Organization
Cloud Providers
Fig 2: Deployment of externally hosted private cloud solution in financial organizations
The largest distinction between the cloud providers, financial organizations, and security
agencies lies in the mobile security constituents.
4. Future trends in Cloud Adoption
The cloud computing remunerations are achieved through indefinite prospects for the financial
organizations by transforming several business critical applications to the cloud. The business
procedures of non-core business organizations can be easily migrated to the cloud. Depending on
the reliability of the cloud retailer, the cloud infrastructure processes like information storage,
information center supervision, and revival of failure are transited to the cloud. Before migrating
to the cloud, exhaustive researches on the various cloud retailers are performed. Because of the
core application migration to cloud is done by only few organizations, various external hosting
solutions available in the hybrid cloud interim lets the users to move most of their core
applications to the cloud (Horrigan, 2008). The circumstances suitable for the cloud deployment
are provided below.
4.1. Analytical Calculation of Risks
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The grid-computing model includes risk assessment applications for evaluating measurements
like trade cost, outcomes, current worth, etc. Based on the data consignment, the cloud-based
grid computing model can be flexibly extended up and down. Thereby the maintenance expenses
can be reduced when the applications are continually employed on various grid operating points.
The CPU cycles formed by the committed device that are not utilized because of the execution of
the applications for certain periods can be suppressed through the utilization of grid based cloud.
The prevailing computing authority existing as on-demand service can be made fundamental.
4.2. Performance Acknowledgement
The performance associated with revenue and its trademark can be investigated by means of
recital ascription. The accomplishment of the cloud speculation strategy is quantified through
performance ascription. The attributes of the asset procedures containing both the positive and
negative association with the performance stages are obtained by the asset administrators. Larger
range of historical information can be acquired by the data centered processes for the purpose of
estimating the performance measurements. The process of estimating the risk analytics by
executing the applications at definite periods is similar to that of the performance ascription
technique. Hence, the utilization of computing energy can be optimized and the performance
advantages of the cloud based grid can be realized by deploying the external cloud host.
4.3. Operational Identity and Resolution
The process of operational identity acquires operational data from various dealers and then the
data are resolved. During the times of maximum operation, the operational identification process
is subjective to high volumes. A hybrid cloud can be crafted in such a way that the resolution
operation is conducted on the public cloud for achieving flexibility. The data remain in the
committed servers residing the private cloud. Thereby, creation of an individual connection to
new users can be avoided and the connections can be synchronized.
4.4. Positional data implicit
The various kinds of information sources hold multiple types of positional information like
reference information, master data, dealer, and the data belonging to other party. This type of
information sources belong to intrinsic database system, outer supplies, or file systems.
like trade cost, outcomes, current worth, etc. Based on the data consignment, the cloud-based
grid computing model can be flexibly extended up and down. Thereby the maintenance expenses
can be reduced when the applications are continually employed on various grid operating points.
The CPU cycles formed by the committed device that are not utilized because of the execution of
the applications for certain periods can be suppressed through the utilization of grid based cloud.
The prevailing computing authority existing as on-demand service can be made fundamental.
4.2. Performance Acknowledgement
The performance associated with revenue and its trademark can be investigated by means of
recital ascription. The accomplishment of the cloud speculation strategy is quantified through
performance ascription. The attributes of the asset procedures containing both the positive and
negative association with the performance stages are obtained by the asset administrators. Larger
range of historical information can be acquired by the data centered processes for the purpose of
estimating the performance measurements. The process of estimating the risk analytics by
executing the applications at definite periods is similar to that of the performance ascription
technique. Hence, the utilization of computing energy can be optimized and the performance
advantages of the cloud based grid can be realized by deploying the external cloud host.
4.3. Operational Identity and Resolution
The process of operational identity acquires operational data from various dealers and then the
data are resolved. During the times of maximum operation, the operational identification process
is subjective to high volumes. A hybrid cloud can be crafted in such a way that the resolution
operation is conducted on the public cloud for achieving flexibility. The data remain in the
committed servers residing the private cloud. Thereby, creation of an individual connection to
new users can be avoided and the connections can be synchronized.
4.4. Positional data implicit
The various kinds of information sources hold multiple types of positional information like
reference information, master data, dealer, and the data belonging to other party. This type of
information sources belong to intrinsic database system, outer supplies, or file systems.

Challenge exists in the creation of techniques to access information from these data sources and
the aggregation the information within the application. As a solution for this, a data virtualization
layer should be constructed for accessing and aggregating the data within this data sources. The
constructed virtualization layer should be adaptable for combining various data courses based on
the application needs. Moreover, an addition layer for providing assistance for monetary
analysis, effective description, and risk administration is also provided. All the data are made
available to the users from the central information services.
5. Risk and Confrontations
Cloud computing is associated with multiple challenges related to data safety, security,
accessibility, conformity, and standard deficiency (Pearson, Casassa, Crane & Herrmann, 2005).
These types of risks are the focal points in standardized and safety-perceptive situations like
fictional services.
Fig 3: Confronted cloud risks
5.1. Security Issues
Risks
the aggregation the information within the application. As a solution for this, a data virtualization
layer should be constructed for accessing and aggregating the data within this data sources. The
constructed virtualization layer should be adaptable for combining various data courses based on
the application needs. Moreover, an addition layer for providing assistance for monetary
analysis, effective description, and risk administration is also provided. All the data are made
available to the users from the central information services.
5. Risk and Confrontations
Cloud computing is associated with multiple challenges related to data safety, security,
accessibility, conformity, and standard deficiency (Pearson, Casassa, Crane & Herrmann, 2005).
These types of risks are the focal points in standardized and safety-perceptive situations like
fictional services.
Fig 3: Confronted cloud risks
5.1. Security Issues
Risks
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 21
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





