Cloud Computing Strategy and Microservices for VideoDev: Report
VerifiedAdded on 2022/09/30
|16
|4280
|141
Report
AI Summary
This report provides a comprehensive analysis of VideoDev's cloud computing strategy, focusing on the adoption of microservices. It begins with an introduction to cloud computing, defining IaaS, PaaS, and SaaS. The report then delves into VideoDev's case study, detailing their transition to the cloud and the rationale behind it. It explores suitable cloud architectures, specifically IaaS and PaaS, and their advantages for VideoDev. The report identifies and analyzes the risks associated with the microservices approach, presenting mitigation strategies for data breaches, data loss, account hijacking, and other threats. Furthermore, it discusses information security measures, including general steps and controls, and recommends a business continuity plan (BCP) considering application resilience and disaster recovery. The report also outlines requirements for remote administration, resource management, and SLA management. Finally, it recommends a migration strategy and process for transitioning web services to a microservices approach, including migration steps and identification of critical points and issues. The report concludes with a summary of the key findings and recommendations.

Running head: CLOUD COMPUTING
Cloud Computing
Name of the Student
Name of the University
Author’s Note:
Cloud Computing
Name of the Student
Name of the University
Author’s Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
CLOUD COMPUTING
Table of Contents
1. Introduction............................................................................................................................2
2. Discussion..............................................................................................................................2
2.1 Brief Idea of the Case Study............................................................................................2
2.2 Description of the Cloud Architectures that can be employed for assisting VideoDev
for meeting the strategy of the Board to move their web services to a Micro Service
Approach................................................................................................................................3
2.3 Description of the Risks that are associated with the New Micro Services Strategy in a
Tabular form...........................................................................................................................6
2.4 Description of the general steps and controls for Information Security, recommended to
the Board for securing the Micro Services with Relevant Reasons.......................................9
2.5 Discussion of recommendation for the BCP of VideoDev as a result of their adoption
of a Micro Services approach after considering issues of Application Resilience, Disaster
Recovery and Backup..........................................................................................................10
2.6 Discussion of the Requirements that VideoDev require to consider for conducting
Remote Administration, Resource Management and SLA Management for the Micro
Services Approach...............................................................................................................11
2.7 Recommendation of the best Migration Strategy and Process for Migration of the Web
Services to a Micro Services Approach with steps for migration and Identification of
Critical Points and Issues occurred at each of these Steps...................................................12
3. Conclusion............................................................................................................................13
References................................................................................................................................14
CLOUD COMPUTING
Table of Contents
1. Introduction............................................................................................................................2
2. Discussion..............................................................................................................................2
2.1 Brief Idea of the Case Study............................................................................................2
2.2 Description of the Cloud Architectures that can be employed for assisting VideoDev
for meeting the strategy of the Board to move their web services to a Micro Service
Approach................................................................................................................................3
2.3 Description of the Risks that are associated with the New Micro Services Strategy in a
Tabular form...........................................................................................................................6
2.4 Description of the general steps and controls for Information Security, recommended to
the Board for securing the Micro Services with Relevant Reasons.......................................9
2.5 Discussion of recommendation for the BCP of VideoDev as a result of their adoption
of a Micro Services approach after considering issues of Application Resilience, Disaster
Recovery and Backup..........................................................................................................10
2.6 Discussion of the Requirements that VideoDev require to consider for conducting
Remote Administration, Resource Management and SLA Management for the Micro
Services Approach...............................................................................................................11
2.7 Recommendation of the best Migration Strategy and Process for Migration of the Web
Services to a Micro Services Approach with steps for migration and Identification of
Critical Points and Issues occurred at each of these Steps...................................................12
3. Conclusion............................................................................................................................13
References................................................................................................................................14

2
CLOUD COMPUTING
1. Introduction
Cloud computing can be referred to as the generalized term for anything, which
majorly includes the delivering of different hosted services on the Internet connection. Such
distinctive services are being broadly sub divided into three sections, which are IaaS or
infrastructure as a service, PaaS or platform as a service and SaaS or software as a service
(Rittinghouse & Ransome, 2017). This cloud computing is extremely important for sharing of
data and information in the most safe and secured manner. This report provides a detailed
outlining of the case study of the organization of VideoDev and their movement to cloud
approach. Various risks will be identified with the MicroServices approach with suitable
recommendations for BCP, resource management and SLA management.
2. Discussion
2.1 Brief Idea of the Case Study
Video Dev Limited is a popular organization that is responsible for video as well as
production development and it works for their customers in both New Zealand and Australia.
They are considering to move few of their computerized infrastructure to the cloud, so that
better responsiveness and flexibility is being obtained. It would even be required for save the
cost of maintenance of the ICT infrastructure. They are having around 100 staff for video
production, supporting and engineering, who are serving different clients in the various parts
of New Zealand and Australia. Video Dev needs advise on the re factoring of the respective
application of video processing for utilizing a micro services approach. The entire board of
the organization wants to start their move to the direction for checking if there are any type of
possibility in the future.
Moreover, they have even decided to start their planning for migrating the existing
web based services from the 2 on premise data centres to the public cloud. They want to
CLOUD COMPUTING
1. Introduction
Cloud computing can be referred to as the generalized term for anything, which
majorly includes the delivering of different hosted services on the Internet connection. Such
distinctive services are being broadly sub divided into three sections, which are IaaS or
infrastructure as a service, PaaS or platform as a service and SaaS or software as a service
(Rittinghouse & Ransome, 2017). This cloud computing is extremely important for sharing of
data and information in the most safe and secured manner. This report provides a detailed
outlining of the case study of the organization of VideoDev and their movement to cloud
approach. Various risks will be identified with the MicroServices approach with suitable
recommendations for BCP, resource management and SLA management.
2. Discussion
2.1 Brief Idea of the Case Study
Video Dev Limited is a popular organization that is responsible for video as well as
production development and it works for their customers in both New Zealand and Australia.
They are considering to move few of their computerized infrastructure to the cloud, so that
better responsiveness and flexibility is being obtained. It would even be required for save the
cost of maintenance of the ICT infrastructure. They are having around 100 staff for video
production, supporting and engineering, who are serving different clients in the various parts
of New Zealand and Australia. Video Dev needs advise on the re factoring of the respective
application of video processing for utilizing a micro services approach. The entire board of
the organization wants to start their move to the direction for checking if there are any type of
possibility in the future.
Moreover, they have even decided to start their planning for migrating the existing
web based services from the 2 on premise data centres to the public cloud. They want to
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
CLOUD COMPUTING
retain the data centre of Sydney for better storage of data and it would entail up gradation of
the Active Directory and infrastructure of data storage for moving the other infrastructure to
cloud. Moreover, the web services are also needed to be moved to cloud for providing an
increased responsiveness to customer demands and enhanced HA level for data supply. The
existing architecture of web software is also required to be change for better flexibility or
scalability after moving to micro services model. The business continuity planning and threat
and risk assessment is needed to be updated with these new changes in the architecture.
2.2 Description of the Cloud Architectures that can be employed for assisting VideoDev
for meeting the strategy of the Board to move their web services to a Micro Service
Approach
Cloud computing architecture eventually refers to the several significant elements like
databases, applications and software capabilities, present in the organization for leveraging
the subsequent power of various cloud resources for solving business problems
(Whaiduzzaman et al., 2014). This type of cloud architecture provides the relationships and
components effectively. The main components of cloud are on premise resources, cloud
resources, middleware and software services and other components. It has the aim of
providing the users with higher bandwidth and allowing the users in having any type of
uninterrupted accessibility to the applications and data and on demand agile networks with
the core probability of moving quickly within servers and even between clouds or network
security. The three types of popular architectures of cloud computing are software as a
service or SaaS, platform as a service or PaaS and infrastructure as a service or IaaS.
VideoDev, being a video production company, would be highly benefitted if they would
involve IaaS and PaaS (Chen et al., 2015).
a) The description of these two cloud architectures with relevant reason is provided
below:
CLOUD COMPUTING
retain the data centre of Sydney for better storage of data and it would entail up gradation of
the Active Directory and infrastructure of data storage for moving the other infrastructure to
cloud. Moreover, the web services are also needed to be moved to cloud for providing an
increased responsiveness to customer demands and enhanced HA level for data supply. The
existing architecture of web software is also required to be change for better flexibility or
scalability after moving to micro services model. The business continuity planning and threat
and risk assessment is needed to be updated with these new changes in the architecture.
2.2 Description of the Cloud Architectures that can be employed for assisting VideoDev
for meeting the strategy of the Board to move their web services to a Micro Service
Approach
Cloud computing architecture eventually refers to the several significant elements like
databases, applications and software capabilities, present in the organization for leveraging
the subsequent power of various cloud resources for solving business problems
(Whaiduzzaman et al., 2014). This type of cloud architecture provides the relationships and
components effectively. The main components of cloud are on premise resources, cloud
resources, middleware and software services and other components. It has the aim of
providing the users with higher bandwidth and allowing the users in having any type of
uninterrupted accessibility to the applications and data and on demand agile networks with
the core probability of moving quickly within servers and even between clouds or network
security. The three types of popular architectures of cloud computing are software as a
service or SaaS, platform as a service or PaaS and infrastructure as a service or IaaS.
VideoDev, being a video production company, would be highly benefitted if they would
involve IaaS and PaaS (Chen et al., 2015).
a) The description of these two cloud architectures with relevant reason is provided
below:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
CLOUD COMPUTING
i) Infrastructure as a Service: This is the first and the most important architecture of
cloud computing that would be beneficial for the respective company would be IaaS or
infrastructure as a service. This particular cloud based architecture is solely responsible for
providing hardware and infrastructure like networks, devices of storage and even servers for
running in the cloud that are available to the users against any type of payment on per usage
basis (Almorsy, Grundy & Müller, 2016). This particular form of cloud computing is
responsible for providing several virtualized computing resources on the Internet connection.
It is one of the major three categories of the cloud services with software as a service and
platform as a service. In the model of infrastructure as a service, a specific provider of cloud
is responsible for hosting the various components of infrastructure present within the on
premise data centre like hypervisor layer, virtualization, networking hardware, storage and
servers.
ii) Platform as a Service: The second significant and vital architecture of cloud
computing that would be beneficial for the respective company would be PaaS or platform as
a service. This particular architecture provides users with the various databases and
application platforms that are equal to the services of middleware (Zhan et al., 2015). The
platform as a service is one of the most significant model of cloud computing, where a third
party provider can deliver different tools of both software and hardware, majorly that are
required for the development of applications. These tools are provided to the users on the
Internet connection and they can easily and promptly host the software and hardware on the
infrastructure.
b) Advantages of IaaS: The provider of this particular cloud architecture even can
supply different types of services for accompanying these components of infrastructure. It
CLOUD COMPUTING
i) Infrastructure as a Service: This is the first and the most important architecture of
cloud computing that would be beneficial for the respective company would be IaaS or
infrastructure as a service. This particular cloud based architecture is solely responsible for
providing hardware and infrastructure like networks, devices of storage and even servers for
running in the cloud that are available to the users against any type of payment on per usage
basis (Almorsy, Grundy & Müller, 2016). This particular form of cloud computing is
responsible for providing several virtualized computing resources on the Internet connection.
It is one of the major three categories of the cloud services with software as a service and
platform as a service. In the model of infrastructure as a service, a specific provider of cloud
is responsible for hosting the various components of infrastructure present within the on
premise data centre like hypervisor layer, virtualization, networking hardware, storage and
servers.
ii) Platform as a Service: The second significant and vital architecture of cloud
computing that would be beneficial for the respective company would be PaaS or platform as
a service. This particular architecture provides users with the various databases and
application platforms that are equal to the services of middleware (Zhan et al., 2015). The
platform as a service is one of the most significant model of cloud computing, where a third
party provider can deliver different tools of both software and hardware, majorly that are
required for the development of applications. These tools are provided to the users on the
Internet connection and they can easily and promptly host the software and hardware on the
infrastructure.
b) Advantages of IaaS: The provider of this particular cloud architecture even can
supply different types of services for accompanying these components of infrastructure. It

5
CLOUD COMPUTING
even can involve log access, clustering, monitoring, load balancing, and security and detailed
billing effectively (Wang et al., 2015). The storage resiliency like recovery, replication and
backup are also being focused and the services could be incrementally be termed as driven by
policies and hence allowing the users of IaaS for implementation of policies and driving the
load balancing for successful maintenance of better performances and availability of
applications. VideoDev would be able to access the resources or services with the help of a
WAN or wide area network and could even utilize the services of the cloud provider for
successful installation of every remaining element of application stack. It would be extremely
beneficial for them since the overall performances to be monitored and disaster recovery
would be managed.
Issues: Privacy and security are the major concerns of this particular cloud
infrastructure (Yang et al., 2017). Moreover, IaaS has higher issues of limited control and
flexibility. Moreover, IaaS is also vulnerable to excess downtime and associated technical
difficulties.
Advantages of PaaS: This type of architecture cannot replace the entire IT
infrastructure of a business, as it is dependent on the providers of PaaS for important services
like application hosting and program development. The provider of the PaaS can easily build
and supply an optimized or resilient environment over which the users could easily install the
data sets or applications. Moreover, these users could even focus on the proper creation and
running of applications and not only on construction or maintenance of every underlying
service or infrastructure (González-Martínez et al., 2015). The various products of this
architecture are being geared towards better development of software and the platforms can
offer storage and computing infrastructure for gaining efficiency majorly. VideoDev hence
can easily enable their video development teams in better collaboration and working together,
in spite of the location.
CLOUD COMPUTING
even can involve log access, clustering, monitoring, load balancing, and security and detailed
billing effectively (Wang et al., 2015). The storage resiliency like recovery, replication and
backup are also being focused and the services could be incrementally be termed as driven by
policies and hence allowing the users of IaaS for implementation of policies and driving the
load balancing for successful maintenance of better performances and availability of
applications. VideoDev would be able to access the resources or services with the help of a
WAN or wide area network and could even utilize the services of the cloud provider for
successful installation of every remaining element of application stack. It would be extremely
beneficial for them since the overall performances to be monitored and disaster recovery
would be managed.
Issues: Privacy and security are the major concerns of this particular cloud
infrastructure (Yang et al., 2017). Moreover, IaaS has higher issues of limited control and
flexibility. Moreover, IaaS is also vulnerable to excess downtime and associated technical
difficulties.
Advantages of PaaS: This type of architecture cannot replace the entire IT
infrastructure of a business, as it is dependent on the providers of PaaS for important services
like application hosting and program development. The provider of the PaaS can easily build
and supply an optimized or resilient environment over which the users could easily install the
data sets or applications. Moreover, these users could even focus on the proper creation and
running of applications and not only on construction or maintenance of every underlying
service or infrastructure (González-Martínez et al., 2015). The various products of this
architecture are being geared towards better development of software and the platforms can
offer storage and computing infrastructure for gaining efficiency majorly. VideoDev hence
can easily enable their video development teams in better collaboration and working together,
in spite of the location.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
CLOUD COMPUTING
Issues: The first issue of PaaS is that they do not allow vendor migration and hence
the organization might be facing issues related to application changing (Jalali et al., 2016).
Lack of data privacy is the second significant issue that is common for this infrastructure.
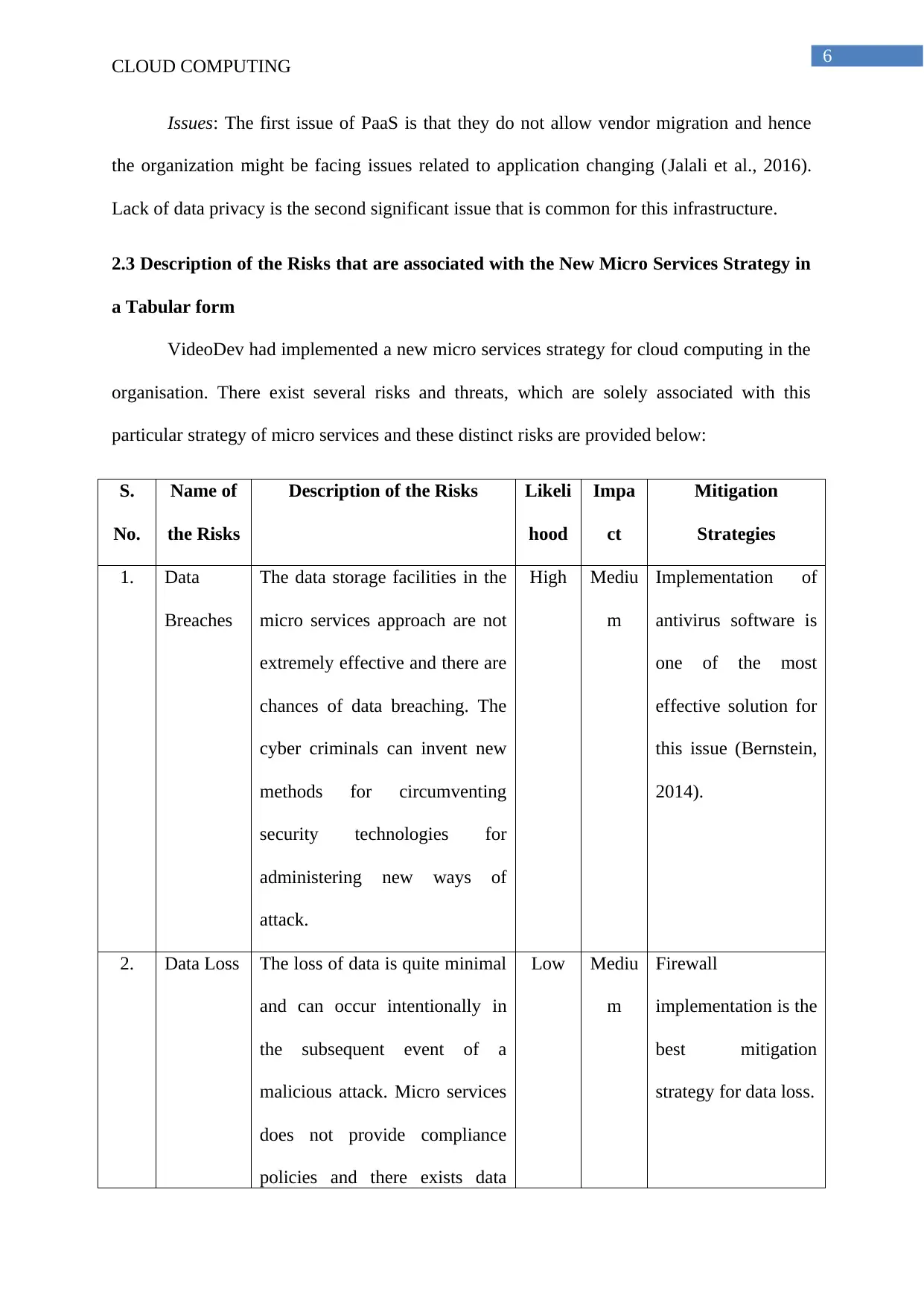
2.3 Description of the Risks that are associated with the New Micro Services Strategy in
a Tabular form
VideoDev had implemented a new micro services strategy for cloud computing in the
organisation. There exist several risks and threats, which are solely associated with this
particular strategy of micro services and these distinct risks are provided below:
S.
No.
Name of
the Risks
Description of the Risks Likeli
hood
Impa
ct
Mitigation
Strategies
1. Data
Breaches
The data storage facilities in the
micro services approach are not
extremely effective and there are
chances of data breaching. The
cyber criminals can invent new
methods for circumventing
security technologies for
administering new ways of
attack.
High Mediu
m
Implementation of
antivirus software is
one of the most
effective solution for
this issue (Bernstein,
2014).
2. Data Loss The loss of data is quite minimal
and can occur intentionally in
the subsequent event of a
malicious attack. Micro services
does not provide compliance
policies and there exists data
Low Mediu
m
Firewall
implementation is the
best mitigation
strategy for data loss.
CLOUD COMPUTING
Issues: The first issue of PaaS is that they do not allow vendor migration and hence
the organization might be facing issues related to application changing (Jalali et al., 2016).
Lack of data privacy is the second significant issue that is common for this infrastructure.
2.3 Description of the Risks that are associated with the New Micro Services Strategy in
a Tabular form
VideoDev had implemented a new micro services strategy for cloud computing in the
organisation. There exist several risks and threats, which are solely associated with this
particular strategy of micro services and these distinct risks are provided below:
S.
No.
Name of
the Risks
Description of the Risks Likeli
hood
Impa
ct
Mitigation
Strategies
1. Data
Breaches
The data storage facilities in the
micro services approach are not
extremely effective and there are
chances of data breaching. The
cyber criminals can invent new
methods for circumventing
security technologies for
administering new ways of
attack.
High Mediu
m
Implementation of
antivirus software is
one of the most
effective solution for
this issue (Bernstein,
2014).
2. Data Loss The loss of data is quite minimal
and can occur intentionally in
the subsequent event of a
malicious attack. Micro services
does not provide compliance
policies and there exists data
Low Mediu
m
Firewall
implementation is the
best mitigation
strategy for data loss.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
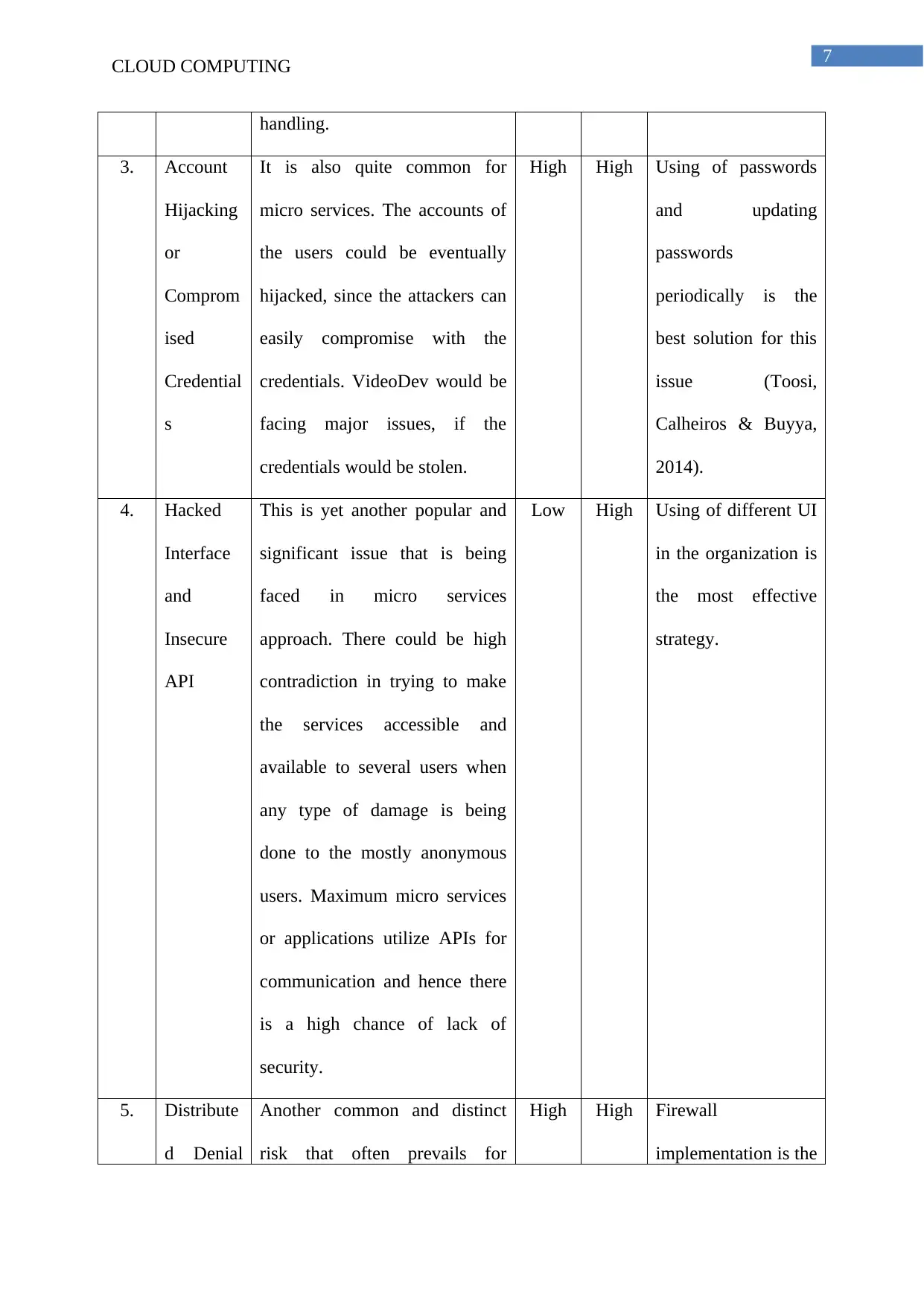
CLOUD COMPUTING
handling.
3. Account
Hijacking
or
Comprom
ised
Credential
s
It is also quite common for
micro services. The accounts of
the users could be eventually
hijacked, since the attackers can
easily compromise with the
credentials. VideoDev would be
facing major issues, if the
credentials would be stolen.
High High Using of passwords
and updating
passwords
periodically is the
best solution for this
issue (Toosi,
Calheiros & Buyya,
2014).
4. Hacked
Interface
and
Insecure
API
This is yet another popular and
significant issue that is being
faced in micro services
approach. There could be high
contradiction in trying to make
the services accessible and
available to several users when
any type of damage is being
done to the mostly anonymous
users. Maximum micro services
or applications utilize APIs for
communication and hence there
is a high chance of lack of
security.
Low High Using of different UI
in the organization is
the most effective
strategy.
5. Distribute
d Denial
Another common and distinct
risk that often prevails for
High High Firewall
implementation is the
CLOUD COMPUTING
handling.
3. Account
Hijacking
or
Comprom
ised
Credential
s
It is also quite common for
micro services. The accounts of
the users could be eventually
hijacked, since the attackers can
easily compromise with the
credentials. VideoDev would be
facing major issues, if the
credentials would be stolen.
High High Using of passwords
and updating
passwords
periodically is the
best solution for this
issue (Toosi,
Calheiros & Buyya,
2014).
4. Hacked
Interface
and
Insecure
API
This is yet another popular and
significant issue that is being
faced in micro services
approach. There could be high
contradiction in trying to make
the services accessible and
available to several users when
any type of damage is being
done to the mostly anonymous
users. Maximum micro services
or applications utilize APIs for
communication and hence there
is a high chance of lack of
security.
Low High Using of different UI
in the organization is
the most effective
strategy.
5. Distribute
d Denial
Another common and distinct
risk that often prevails for
High High Firewall
implementation is the
8
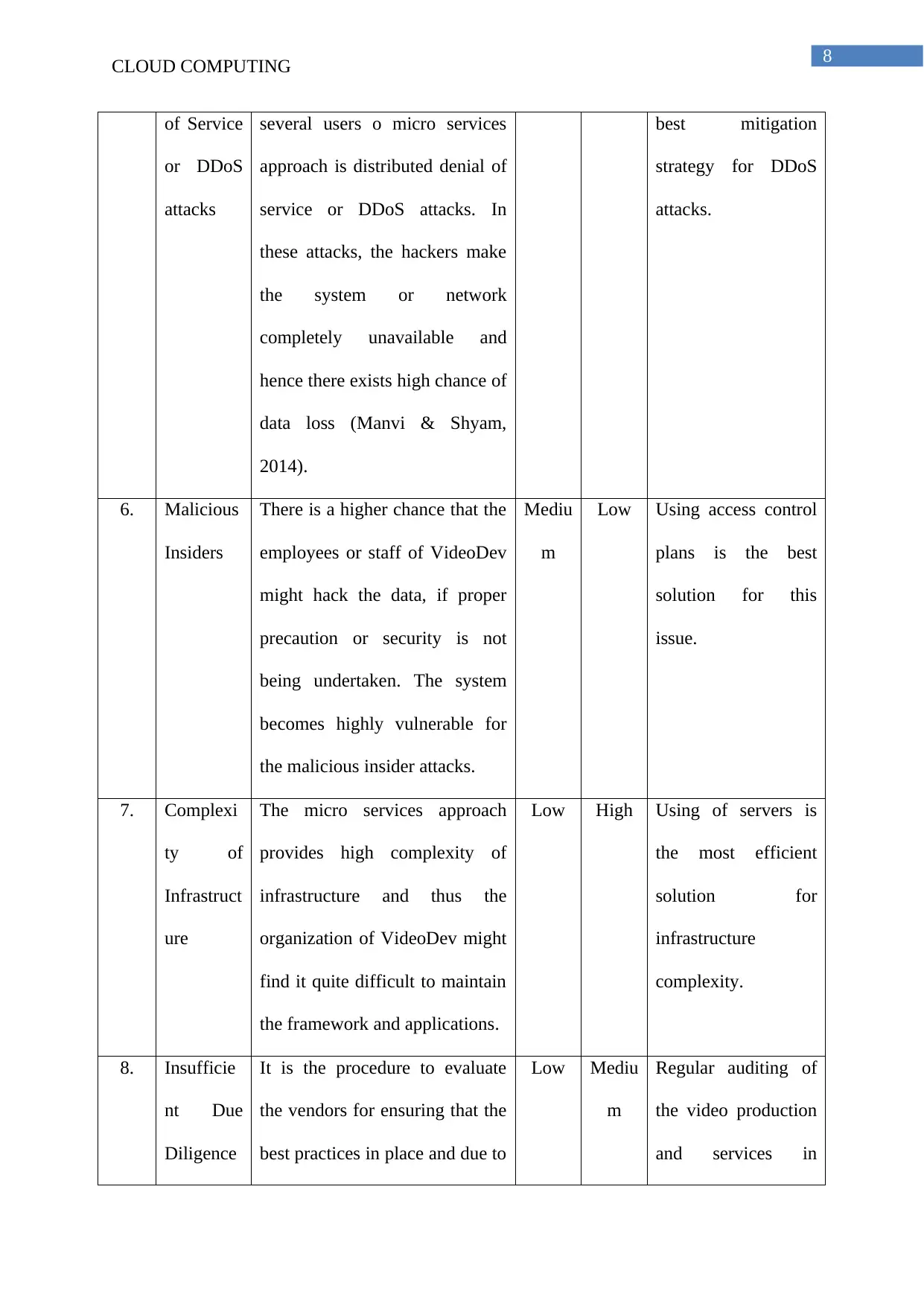
CLOUD COMPUTING
of Service
or DDoS
attacks
several users o micro services
approach is distributed denial of
service or DDoS attacks. In
these attacks, the hackers make
the system or network
completely unavailable and
hence there exists high chance of
data loss (Manvi & Shyam,
2014).
best mitigation
strategy for DDoS
attacks.
6. Malicious
Insiders
There is a higher chance that the
employees or staff of VideoDev
might hack the data, if proper
precaution or security is not
being undertaken. The system
becomes highly vulnerable for
the malicious insider attacks.
Mediu
m
Low Using access control
plans is the best
solution for this
issue.
7. Complexi
ty of
Infrastruct
ure
The micro services approach
provides high complexity of
infrastructure and thus the
organization of VideoDev might
find it quite difficult to maintain
the framework and applications.
Low High Using of servers is
the most efficient
solution for
infrastructure
complexity.
8. Insufficie
nt Due
Diligence
It is the procedure to evaluate
the vendors for ensuring that the
best practices in place and due to
Low Mediu
m
Regular auditing of
the video production
and services in
CLOUD COMPUTING
of Service
or DDoS
attacks
several users o micro services
approach is distributed denial of
service or DDoS attacks. In
these attacks, the hackers make
the system or network
completely unavailable and
hence there exists high chance of
data loss (Manvi & Shyam,
2014).
best mitigation
strategy for DDoS
attacks.
6. Malicious
Insiders
There is a higher chance that the
employees or staff of VideoDev
might hack the data, if proper
precaution or security is not
being undertaken. The system
becomes highly vulnerable for
the malicious insider attacks.
Mediu
m
Low Using access control
plans is the best
solution for this
issue.
7. Complexi
ty of
Infrastruct
ure
The micro services approach
provides high complexity of
infrastructure and thus the
organization of VideoDev might
find it quite difficult to maintain
the framework and applications.
Low High Using of servers is
the most efficient
solution for
infrastructure
complexity.
8. Insufficie
nt Due
Diligence
It is the procedure to evaluate
the vendors for ensuring that the
best practices in place and due to
Low Mediu
m
Regular auditing of
the video production
and services in
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
CLOUD COMPUTING
insufficient due diligence,
misalignment can occur between
service and customers.
VideoDev could be
effective (Rahimi et
al., 2014).
Table 1: Risks and Mitigation Strategies for Micro Services Approach
(Source: Created by the Author in MS Word)
2.4 Description of the general steps and controls for Information Security,
recommended to the Board for securing the Micro Services with Relevant Reasons
VideoDev will have to use few general steps and controls for ensuring information
security and securing the micro services approach. These are recommended to the board of
VideoDev. The steps and controls are as follows:
i) Risk Management Regime: VideoDev should know about the prevailing risks,
which are being faced while implementation of the security measures for information
(Barbarossa, Sardellitti & Di Lorenzo, 2014). It would allow them in prioritizing the
exceptional threats and making correct responses.
ii) Securing the Configuration: The respective configuration of micro services should
be safe and secured so that the databases are absolutely secured and an importance of
configuration would be maintained.
iii) Incident Management: The most robust defence measures are needed to be
enhanced and hence any type of security incidents could be effectively prevented without
much complexity.
iv) Prevention of the Malware: The various malware and malicious viruses could be
prevented so that they do not infect into the systems of the company. Implementation of anti-
malware policies and software are required for VideoDev.
CLOUD COMPUTING
insufficient due diligence,
misalignment can occur between
service and customers.
VideoDev could be
effective (Rahimi et
al., 2014).
Table 1: Risks and Mitigation Strategies for Micro Services Approach
(Source: Created by the Author in MS Word)
2.4 Description of the general steps and controls for Information Security,
recommended to the Board for securing the Micro Services with Relevant Reasons
VideoDev will have to use few general steps and controls for ensuring information
security and securing the micro services approach. These are recommended to the board of
VideoDev. The steps and controls are as follows:
i) Risk Management Regime: VideoDev should know about the prevailing risks,
which are being faced while implementation of the security measures for information
(Barbarossa, Sardellitti & Di Lorenzo, 2014). It would allow them in prioritizing the
exceptional threats and making correct responses.
ii) Securing the Configuration: The respective configuration of micro services should
be safe and secured so that the databases are absolutely secured and an importance of
configuration would be maintained.
iii) Incident Management: The most robust defence measures are needed to be
enhanced and hence any type of security incidents could be effectively prevented without
much complexity.
iv) Prevention of the Malware: The various malware and malicious viruses could be
prevented so that they do not infect into the systems of the company. Implementation of anti-
malware policies and software are required for VideoDev.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
CLOUD COMPUTING
v) Management of the User Privileges: The user privileges and access controls
should be managed properly, so that only authenticated employees get the chance of
accessing the data (Gangwar, Date & Ramaswamy, 2015).
vi) Monitoring of the Services: The respective services of the organization should be
monitored properly and hence it would help in reducing complexities related to attempted
attacks.
vii) Network Security: The network of the organization should be safe and secured
and all types of network vulnerabilities would be removed.
viii) Employee Awareness: Each and every employee should be educated and an
awareness should be spread for prevention of data breaches in VideoDev.
2.5 Discussion of recommendation for the BCP of VideoDev as a result of their adoption
of a Micro Services approach after considering issues of Application Resilience, Disaster
Recovery and Backup
Micro services approach helps in lowering the operating costs and running
infrastructure much more effectively so that the business can afford changes. The first and the
foremost important advantage of cloud computing is its cost effectiveness (Sen, 2015). This
particular approach helps in eradicating the total capital expenses for purchasing hardware or
software and even setting up or running the onsite data centres. The various experts of
information technology are required to manage the infrastructure and also provide faster
services. Speed is the next vital benefit that is being provided to the user. Bandwidth and
storage issues are well resolved with this specific approach.
VideoDev is eventually facing issues related to application resilience, backup and
disaster recovery. These could be easily and promptly resolved with the successful
implementation of BCP or business continuity planning in their business. It is the major
CLOUD COMPUTING
v) Management of the User Privileges: The user privileges and access controls
should be managed properly, so that only authenticated employees get the chance of
accessing the data (Gangwar, Date & Ramaswamy, 2015).
vi) Monitoring of the Services: The respective services of the organization should be
monitored properly and hence it would help in reducing complexities related to attempted
attacks.
vii) Network Security: The network of the organization should be safe and secured
and all types of network vulnerabilities would be removed.
viii) Employee Awareness: Each and every employee should be educated and an
awareness should be spread for prevention of data breaches in VideoDev.
2.5 Discussion of recommendation for the BCP of VideoDev as a result of their adoption
of a Micro Services approach after considering issues of Application Resilience, Disaster
Recovery and Backup
Micro services approach helps in lowering the operating costs and running
infrastructure much more effectively so that the business can afford changes. The first and the
foremost important advantage of cloud computing is its cost effectiveness (Sen, 2015). This
particular approach helps in eradicating the total capital expenses for purchasing hardware or
software and even setting up or running the onsite data centres. The various experts of
information technology are required to manage the infrastructure and also provide faster
services. Speed is the next vital benefit that is being provided to the user. Bandwidth and
storage issues are well resolved with this specific approach.
VideoDev is eventually facing issues related to application resilience, backup and
disaster recovery. These could be easily and promptly resolved with the successful
implementation of BCP or business continuity planning in their business. It is the major

11
CLOUD COMPUTING
procedure to create different systems for better prevention as well as recovery for effectively
dealing with all types of potential threats and risks and are recovery for dealing with these
threats to an organization (Toosi, Calheiros & Buyya, 2014). The major objectives of an
effective BCP implementation would be allowing the ongoing operations during successful
execution of the disaster recovery in their business. Thus, VideoDev would be able to
successfully eradicate the issues of application resilience and DR with high efficiency and the
organization would be highly benefitted with this recommendation of BCP.
2.6 Discussion of the Requirements that VideoDev require to consider for conducting
Remote Administration, Resource Management and SLA Management for the Micro
Services Approach
i) Remote Administration: Remote administration is required for providing
subsequent user interfaces and tools for the administrator so that they can easily and promptly
configure the cloud based resources of IT. Two types of portals are required for this purpose.
The 1st kind is administrating and usage portal, whereas the 2nd kind is the self services portal.
The 1st type ensures that better administration is possible without much complexity and the
2nd type is the vendor portal to enable various cloud clients for searching updated list of
services (Jalali et al., 2016). These are the major requirements of remote administration in
VideoDev. Moreover, RDP should also be included to enable the user with GUI for getting
connected to the next system.
ii) Resource Management: Various resource management techniques mainly
emphasize on subsequent sharing of the various cloud based resources within users. It would
be required for VideoDev to coordinate various resources of IT to execute management
activities. The main requirement of resource management implementation is the management
of virtualized infrastructure that can coordinate server hardware to create virtualized server
instances. Hence, VideoDev would be able to store their operational information.
CLOUD COMPUTING
procedure to create different systems for better prevention as well as recovery for effectively
dealing with all types of potential threats and risks and are recovery for dealing with these
threats to an organization (Toosi, Calheiros & Buyya, 2014). The major objectives of an
effective BCP implementation would be allowing the ongoing operations during successful
execution of the disaster recovery in their business. Thus, VideoDev would be able to
successfully eradicate the issues of application resilience and DR with high efficiency and the
organization would be highly benefitted with this recommendation of BCP.
2.6 Discussion of the Requirements that VideoDev require to consider for conducting
Remote Administration, Resource Management and SLA Management for the Micro
Services Approach
i) Remote Administration: Remote administration is required for providing
subsequent user interfaces and tools for the administrator so that they can easily and promptly
configure the cloud based resources of IT. Two types of portals are required for this purpose.
The 1st kind is administrating and usage portal, whereas the 2nd kind is the self services portal.
The 1st type ensures that better administration is possible without much complexity and the
2nd type is the vendor portal to enable various cloud clients for searching updated list of
services (Jalali et al., 2016). These are the major requirements of remote administration in
VideoDev. Moreover, RDP should also be included to enable the user with GUI for getting
connected to the next system.
ii) Resource Management: Various resource management techniques mainly
emphasize on subsequent sharing of the various cloud based resources within users. It would
be required for VideoDev to coordinate various resources of IT to execute management
activities. The main requirement of resource management implementation is the management
of virtualized infrastructure that can coordinate server hardware to create virtualized server
instances. Hence, VideoDev would be able to store their operational information.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



