Cloud Computing Assignment: Webb's Store Security and Risk Analysis
VerifiedAdded on 2021/04/20
|15
|3065
|69
Report
AI Summary
This report analyzes the cloud computing strategy of Webb's Store, focusing on the migration of their MS SQL Server 2012 R2 database to an IaaS instance. It examines security deployments, benefits, and issues associated with these measures, emphasizing the importance of security intelligence and regulatory compliance. The report identifies various risks associated with database migration, including data breaches and account hijacking, along with risks related to the IaaS infrastructure and communication. It then considers the use of the cloud for backup and archival, detailing the risks associated with backing up, storing, and retrieving data. Finally, the report provides recommendations for protecting access to Webb's IaaS infrastructure, SQL Server instance, cloud network, and backup infrastructure, highlighting the need for robust security measures and disaster recovery planning. The report emphasizes the importance of Amazon AWS cloud solutions for Webb's store.

ASSIGNMENT COVER SHEET
Student Id: 11632403 Family name: ACHARYA
Given names: NIRANJAN
Subject name: CLOUD COMPUTING Subject code: ITC561
Lecturer: LINH PHAM Assignment No: 2
PENALTY ON LATE ASSIGNMENTS
The penalty for late submission of assignment without obtaining lecturer's approval for an
extension will be 10% deduction per day, including weekends, of the maximum marks
allocated for the assignment, i.e. 1 day late = 10% deduction, 2 days late = 20% deduction.
PLAGIARISM
The University treats plagiarism very seriously. Plagiarism is included under the Student
Academic Misconduct Rule as published in the Rules and Regulations section of the
academic handbook.
I am aware of the University’s requirement for academic integrity
(http://www.csu.edu.au/division.studserv/learning/_plagiarism/) and I declare that my
assignment is my own work and conforms with these requirements.
I certify that the attached assignment is solely my work, based on my personal study and
research. I also certify that appropriate and full acknowledgement has been made of all
sources used in the preparation of this assignment.
Signature of student: Niraj Assignment due date: 25/09/2017
Student Id: 11632403 Family name: ACHARYA
Given names: NIRANJAN
Subject name: CLOUD COMPUTING Subject code: ITC561
Lecturer: LINH PHAM Assignment No: 2
PENALTY ON LATE ASSIGNMENTS
The penalty for late submission of assignment without obtaining lecturer's approval for an
extension will be 10% deduction per day, including weekends, of the maximum marks
allocated for the assignment, i.e. 1 day late = 10% deduction, 2 days late = 20% deduction.
PLAGIARISM
The University treats plagiarism very seriously. Plagiarism is included under the Student
Academic Misconduct Rule as published in the Rules and Regulations section of the
academic handbook.
I am aware of the University’s requirement for academic integrity
(http://www.csu.edu.au/division.studserv/learning/_plagiarism/) and I declare that my
assignment is my own work and conforms with these requirements.
I certify that the attached assignment is solely my work, based on my personal study and
research. I also certify that appropriate and full acknowledgement has been made of all
sources used in the preparation of this assignment.
Signature of student: Niraj Assignment due date: 25/09/2017
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Niranjan Acharya 11632403
Table of Contents
Executive Summary...................................................................................................................2
Introduction................................................................................................................................2
Question 1..................................................................................................................................3
1. Webb’s decision to migrate their MS SQL Server 2012 R2 database to IaaS instance.........3
1. a. Security deployment to protect this migration of database to IaaS instance...............3
1. b. Benefits and issues related to deployment of these security measures.......................4
Question 2..................................................................................................................................6
2. Risks associated with migrating database to the cloud with respect to-................................6
2. a. The database..................................................................................................................6
2. b. The IaaS infrastructure...................................................................................................6
2. c. Communications between Webb’s and their IaaS database in the cloud.....................7
Question 3..................................................................................................................................8
3. Webb’s consideration for the use of the Cloud for backup and possibly also for archival of
records........................................................................................................................................8
3. a. Risks associated to..........................................................................................................8
I. Backing up data to the Cloud..........................................................................................8
II. Storage of data in the Cloud..........................................................................................8
III. Retrieval of data from the cloud...................................................................................8
3. b. Webb’s use of a Cloud backup and its impact on the company and DR plan...............9
Question 4................................................................................................................................10
4. Recommendations to Webb for protecting access to the following services that they want
to move to the Cloud................................................................................................................10
4.a. Their IaaS infrastructure................................................................................................10
4.b. Their Ms SQL Server 2012 R2 cloud instance................................................................11
4.c. Their Cloud network infrastructure...............................................................................11
4.d. Their Cloud backup and restore infrastructure............................................................12
Conclusion................................................................................................................................12
References................................................................................................................................13
1 Niranjan Acharya 11632403
Table of Contents
Executive Summary...................................................................................................................2
Introduction................................................................................................................................2
Question 1..................................................................................................................................3
1. Webb’s decision to migrate their MS SQL Server 2012 R2 database to IaaS instance.........3
1. a. Security deployment to protect this migration of database to IaaS instance...............3
1. b. Benefits and issues related to deployment of these security measures.......................4
Question 2..................................................................................................................................6
2. Risks associated with migrating database to the cloud with respect to-................................6
2. a. The database..................................................................................................................6
2. b. The IaaS infrastructure...................................................................................................6
2. c. Communications between Webb’s and their IaaS database in the cloud.....................7
Question 3..................................................................................................................................8
3. Webb’s consideration for the use of the Cloud for backup and possibly also for archival of
records........................................................................................................................................8
3. a. Risks associated to..........................................................................................................8
I. Backing up data to the Cloud..........................................................................................8
II. Storage of data in the Cloud..........................................................................................8
III. Retrieval of data from the cloud...................................................................................8
3. b. Webb’s use of a Cloud backup and its impact on the company and DR plan...............9
Question 4................................................................................................................................10
4. Recommendations to Webb for protecting access to the following services that they want
to move to the Cloud................................................................................................................10
4.a. Their IaaS infrastructure................................................................................................10
4.b. Their Ms SQL Server 2012 R2 cloud instance................................................................11
4.c. Their Cloud network infrastructure...............................................................................11
4.d. Their Cloud backup and restore infrastructure............................................................12
Conclusion................................................................................................................................12
References................................................................................................................................13
1 Niranjan Acharya 11632403

Niranjan Acharya 11632403
Executive Summary
Webb's Store has planned to shift their business activities to the cloud platform.
Amazon is famous to cater best cloud solutions and so they are widely used all over the
world. Webb must adapt to enhance the retailing activities. The risks, threats and
vulnerabilities related to the cloud platform have been elaborately discussed in the report. The
procedures to reduce the risks associated with the cloud has been explained in the report.
Introduction
Webb's Store, the retail store in Australia has a proposed plan to shift their business
activities to the cloud. The various parameters of the Webb have been explained in the
report (Beck, Hao & Campan, 2017). The report will highlight risks, threats and the
vulnerabilities and risk diminishing procedures. The report will highlight why Webb should
adopt Amazon AWS for good.
Question 1
1. Webb’s decision to migrate their MS SQL
Server 2012 R2 database to IaaS instance
1. a. Security deployment to protect this migration of database to IaaS instance
Webb has planned to shift their business operations to the cloud, therefore they have
to consider the issues relevant to the cloud technology (Shufeng & Xu, 2012). The problems
associated with the cloud technology are an illegitimate entry to APIs, the attacks conducted
by the hacktivists alike the malware attack and the virus attack. Webb Store should follow
certain policies to stay protected from all kinds of threats and the risks.
2 Niranjan Acharya 11632403
Executive Summary
Webb's Store has planned to shift their business activities to the cloud platform.
Amazon is famous to cater best cloud solutions and so they are widely used all over the
world. Webb must adapt to enhance the retailing activities. The risks, threats and
vulnerabilities related to the cloud platform have been elaborately discussed in the report. The
procedures to reduce the risks associated with the cloud has been explained in the report.
Introduction
Webb's Store, the retail store in Australia has a proposed plan to shift their business
activities to the cloud. The various parameters of the Webb have been explained in the
report (Beck, Hao & Campan, 2017). The report will highlight risks, threats and the
vulnerabilities and risk diminishing procedures. The report will highlight why Webb should
adopt Amazon AWS for good.
Question 1
1. Webb’s decision to migrate their MS SQL
Server 2012 R2 database to IaaS instance
1. a. Security deployment to protect this migration of database to IaaS instance
Webb has planned to shift their business operations to the cloud, therefore they have
to consider the issues relevant to the cloud technology (Shufeng & Xu, 2012). The problems
associated with the cloud technology are an illegitimate entry to APIs, the attacks conducted
by the hacktivists alike the malware attack and the virus attack. Webb Store should follow
certain policies to stay protected from all kinds of threats and the risks.
2 Niranjan Acharya 11632403
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Niranjan Acharya 11632403
Follow-through: The Webb Store's database administrators must be acknowledged
about every aspect of the cloud technology and the risks associated with the cloud (Azam et
al., 2013). They must arrange the files stored in the database accordingly so that they can
acquire files stored in the database with ease and that is why they have planned to mark the
files
Security associated with network information: The rules and regulations and
policies must be implied on both the customers and the employees to limit their access to
the database, that will protect the data of Webb's database to the maximum extent
(Sadooghi et al., 2017).
Security Intelligence process: The defence mechanism for the Webb system must be
really strong enough to restrict hacktivists of any kind, proper cryptographic methodologies
applied within the system can protect the Webb Store from all kinds of data breaches. The
cryptographic methodologies are not easy to decipher by the hackers (Dinh et al., 2013).
Therefore, the security Intelligence must look upon the defence system in a constant
manner to keep the database of Webb Store protected all the time.
1. b. Benefits and issues related to deployment of these security measures
Benefits of security -
i. DDoS attack and security- The cloud solutions provided by the cloud vendor are
capable to cater the security and privacy to the customers, the cloud vendor's security is
also responsible to provide authentication, integrity and confidentiality.
3 Niranjan Acharya 11632403
Follow-through: The Webb Store's database administrators must be acknowledged
about every aspect of the cloud technology and the risks associated with the cloud (Azam et
al., 2013). They must arrange the files stored in the database accordingly so that they can
acquire files stored in the database with ease and that is why they have planned to mark the
files
Security associated with network information: The rules and regulations and
policies must be implied on both the customers and the employees to limit their access to
the database, that will protect the data of Webb's database to the maximum extent
(Sadooghi et al., 2017).
Security Intelligence process: The defence mechanism for the Webb system must be
really strong enough to restrict hacktivists of any kind, proper cryptographic methodologies
applied within the system can protect the Webb Store from all kinds of data breaches. The
cryptographic methodologies are not easy to decipher by the hackers (Dinh et al., 2013).
Therefore, the security Intelligence must look upon the defence system in a constant
manner to keep the database of Webb Store protected all the time.
1. b. Benefits and issues related to deployment of these security measures
Benefits of security -
i. DDoS attack and security- The cloud solutions provided by the cloud vendor are
capable to cater the security and privacy to the customers, the cloud vendor's security is
also responsible to provide authentication, integrity and confidentiality.
3 Niranjan Acharya 11632403
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Niranjan Acharya 11632403
ii. Security of the data- The enhanced cloud security solutions providing security and
privacy features of the sensitive information to Webb can help Webb to stay protected from
all kinds of threats and risks that can make the Webb database vulnerable to attack.
iii. Regulatory compliance- The bank details and the purchase records of Webb’s
customers, all kinds of financial information of Webb can be regulated or governed by
means of advanced security solutions provided by cloud vendor (Varia & Mathew, 2014).
iv. Probable solutions- The server currently being used by the customers can get
crashed and the Webb has the scope to cut down the heavy costs when the cloud traffic
gets improved.
v. Allowing 24x7 services- The cloud solutions enable the customers and the
organisation to communicate all day long.
vi. Costing- Webb will have to pay a minimal charge to the cloud vendor, Amazon
AWS for hiring their cloud platform to perform the business activities over the cloud. They
do not have to worry about purchasing costly application programs, hardware and software
and also the operating system.
vii. Integrity- The data integrity grandstands that Amazon being a reputed company
must be loyal to the customers and should not leak their customers’ data at any cost. The
enhanced security solutions provided by Amazon is sure to provide the maximum benefits
to Webb Store (Dillon & Vossen, 2015).
The primary issue is that Webb will have to pay heavy revenues to Amazon on a
yearly basis and monthly basis to acquire the enhanced cloud solutions and the security
solutions, Amazon will provide the latest software, hardware and operating system to Webb
4 Niranjan Acharya 11632403
ii. Security of the data- The enhanced cloud security solutions providing security and
privacy features of the sensitive information to Webb can help Webb to stay protected from
all kinds of threats and risks that can make the Webb database vulnerable to attack.
iii. Regulatory compliance- The bank details and the purchase records of Webb’s
customers, all kinds of financial information of Webb can be regulated or governed by
means of advanced security solutions provided by cloud vendor (Varia & Mathew, 2014).
iv. Probable solutions- The server currently being used by the customers can get
crashed and the Webb has the scope to cut down the heavy costs when the cloud traffic
gets improved.
v. Allowing 24x7 services- The cloud solutions enable the customers and the
organisation to communicate all day long.
vi. Costing- Webb will have to pay a minimal charge to the cloud vendor, Amazon
AWS for hiring their cloud platform to perform the business activities over the cloud. They
do not have to worry about purchasing costly application programs, hardware and software
and also the operating system.
vii. Integrity- The data integrity grandstands that Amazon being a reputed company
must be loyal to the customers and should not leak their customers’ data at any cost. The
enhanced security solutions provided by Amazon is sure to provide the maximum benefits
to Webb Store (Dillon & Vossen, 2015).
The primary issue is that Webb will have to pay heavy revenues to Amazon on a
yearly basis and monthly basis to acquire the enhanced cloud solutions and the security
solutions, Amazon will provide the latest software, hardware and operating system to Webb
4 Niranjan Acharya 11632403
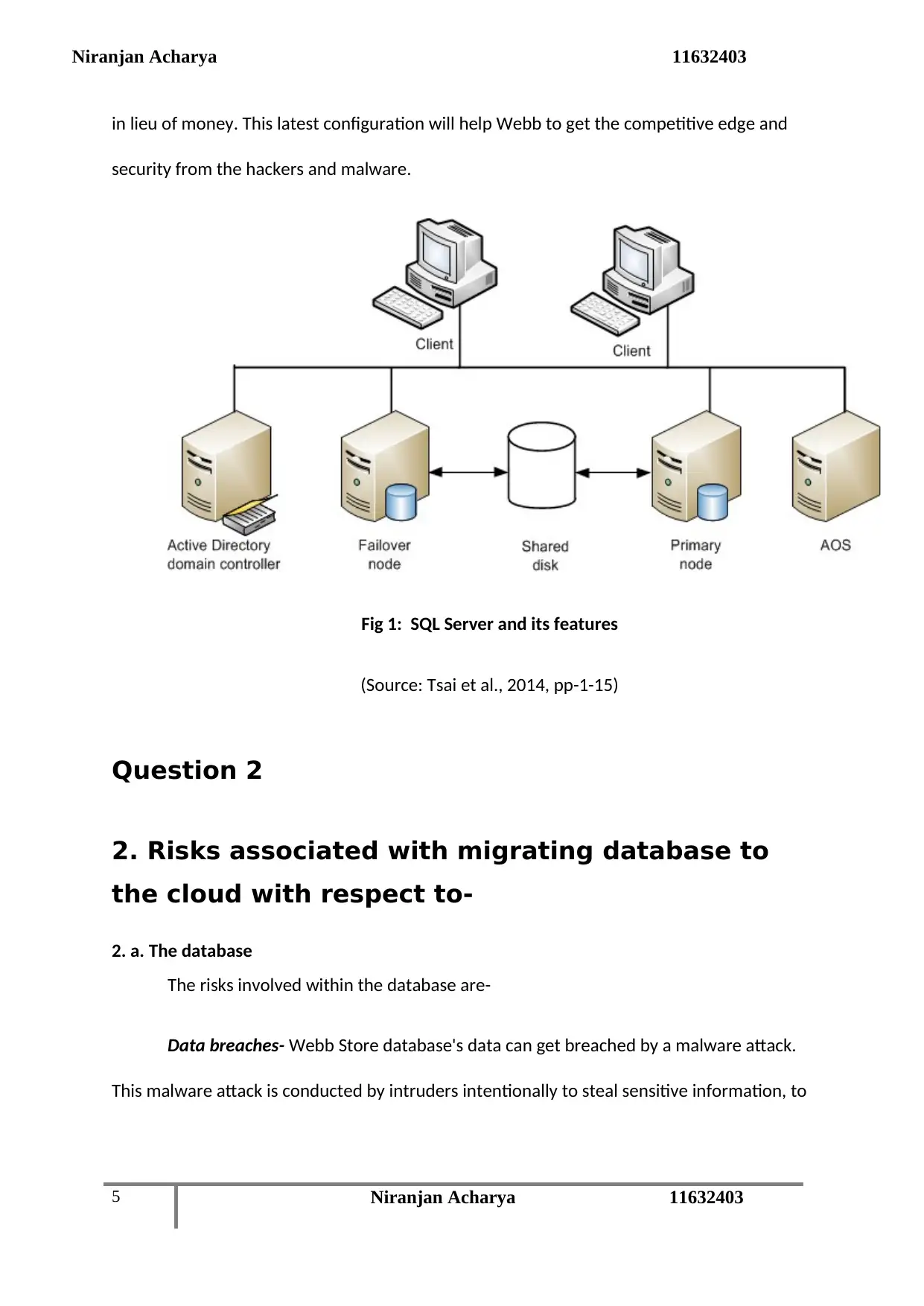
Niranjan Acharya 11632403
in lieu of money. This latest configuration will help Webb to get the competitive edge and
security from the hackers and malware.
Fig 1: SQL Server and its features
(Source: Tsai et al., 2014, pp-1-15)
Question 2
2. Risks associated with migrating database to
the cloud with respect to-
2. a. The database
The risks involved within the database are-
Data breaches- Webb Store database's data can get breached by a malware attack.
This malware attack is conducted by intruders intentionally to steal sensitive information, to
5 Niranjan Acharya 11632403
in lieu of money. This latest configuration will help Webb to get the competitive edge and
security from the hackers and malware.
Fig 1: SQL Server and its features
(Source: Tsai et al., 2014, pp-1-15)
Question 2
2. Risks associated with migrating database to
the cloud with respect to-
2. a. The database
The risks involved within the database are-
Data breaches- Webb Store database's data can get breached by a malware attack.
This malware attack is conducted by intruders intentionally to steal sensitive information, to
5 Niranjan Acharya 11632403
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Niranjan Acharya 11632403
harm one company's reputation as well. Webb due to the attack from the hackers can face
huge monitory loss. The reputation of Webb can be threatened as well.
Account hijacking of customers and employees- The malware attack can cause
severe damage to one’s company (Tsai et al., 2014). The DDoS attack can affect Webb's
employees, Webb's system can get disrupted due to this attack. Again by means of phishing,
the customers' credentials like their username, the password can get stolen due to the
phishing attack.
2. b. The IaaS infrastructure
The risks involved in IaaS Cloud are-
Misconfigure issues- Webb’s existing hardware, software and the application
programs must comply with Amazon AWS cloud architecture. The misconfiguration may
arise if hardware, software, operating system and application programs failed to comply
with the cloud vendor’s components.
Threat issues- The elements associated with IaaS cloud framework that is vulnerable
to malicious threats can be foreseen by the Prioritize and Scan and Remediate
methodologies (Manvi, & Shyam, 2014).
Shadow-IT- Shadow-IT generally addresses the assets and the resources that are not
being used for long. After adopting the cloud technology, Webb will certainly not use the
prevalent database or if used they will not use one or two database components for sure.
That unused component scan is vulnerable to threats.
6 Niranjan Acharya 11632403
harm one company's reputation as well. Webb due to the attack from the hackers can face
huge monitory loss. The reputation of Webb can be threatened as well.
Account hijacking of customers and employees- The malware attack can cause
severe damage to one’s company (Tsai et al., 2014). The DDoS attack can affect Webb's
employees, Webb's system can get disrupted due to this attack. Again by means of phishing,
the customers' credentials like their username, the password can get stolen due to the
phishing attack.
2. b. The IaaS infrastructure
The risks involved in IaaS Cloud are-
Misconfigure issues- Webb’s existing hardware, software and the application
programs must comply with Amazon AWS cloud architecture. The misconfiguration may
arise if hardware, software, operating system and application programs failed to comply
with the cloud vendor’s components.
Threat issues- The elements associated with IaaS cloud framework that is vulnerable
to malicious threats can be foreseen by the Prioritize and Scan and Remediate
methodologies (Manvi, & Shyam, 2014).
Shadow-IT- Shadow-IT generally addresses the assets and the resources that are not
being used for long. After adopting the cloud technology, Webb will certainly not use the
prevalent database or if used they will not use one or two database components for sure.
That unused component scan is vulnerable to threats.
6 Niranjan Acharya 11632403
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Niranjan Acharya 11632403
Fig 2: SQL Server risks and their detection
(Source: Gai, & Steenkamp, 2014, pp-28)
2. c. Communications between Webb’s and their IaaS database in the cloud
Amazon AWS is known to cater the best cloud solutions and they are highly
appreciated all over the globe (Gai, & Steenkamp, 2014. Webb in order to adhere to the
cloud architecture catered by Amazon they have to make littlest changes to their existing
hardware, software components so that they can go well with the cloud architectural
components of Amazon AWS.
7 Niranjan Acharya 11632403
Fig 2: SQL Server risks and their detection
(Source: Gai, & Steenkamp, 2014, pp-28)
2. c. Communications between Webb’s and their IaaS database in the cloud
Amazon AWS is known to cater the best cloud solutions and they are highly
appreciated all over the globe (Gai, & Steenkamp, 2014. Webb in order to adhere to the
cloud architecture catered by Amazon they have to make littlest changes to their existing
hardware, software components so that they can go well with the cloud architectural
components of Amazon AWS.
7 Niranjan Acharya 11632403

Niranjan Acharya 11632403
Question 3
3. Webb’s consideration for the use of the Cloud
for backup and possibly also for archival of
records
3. a. Risks associated to
I. Backing up data to the Cloud
The threats and the security risks associated with backup of data are-
i. High-speed Internet bandwidth is required to carry out business activities over the cloud
platform that is uploading and downloading data. Webb will have to pay a huge amount to
get the high-speed Internet bandwidth access.
ii. The Webb’s financial records, personal files can get compromised while those sensitive
data get passed on over the cloud (Manvi, & Shyam, 2014).
iii. The server crash can cost Webb a lot as there is a chance that Webb can lose all the data
of their company.
II. Storage of data in the Cloud
i. If the data of the database is not encrypted properly while storing data in the database,
the data can be hacked very easily from the database.
ii. Webb must be careful while processing the data over the cloud and storing the file in the
database otherwise those data can be a risk, they can get compromised (Manvi, & Shyam,
2014).
8 Niranjan Acharya 11632403
Question 3
3. Webb’s consideration for the use of the Cloud
for backup and possibly also for archival of
records
3. a. Risks associated to
I. Backing up data to the Cloud
The threats and the security risks associated with backup of data are-
i. High-speed Internet bandwidth is required to carry out business activities over the cloud
platform that is uploading and downloading data. Webb will have to pay a huge amount to
get the high-speed Internet bandwidth access.
ii. The Webb’s financial records, personal files can get compromised while those sensitive
data get passed on over the cloud (Manvi, & Shyam, 2014).
iii. The server crash can cost Webb a lot as there is a chance that Webb can lose all the data
of their company.
II. Storage of data in the Cloud
i. If the data of the database is not encrypted properly while storing data in the database,
the data can be hacked very easily from the database.
ii. Webb must be careful while processing the data over the cloud and storing the file in the
database otherwise those data can be a risk, they can get compromised (Manvi, & Shyam,
2014).
8 Niranjan Acharya 11632403
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Niranjan Acharya 11632403
III. Retrieval of data from the cloud
i. The high-speed Internet is required to retrieve files from the database, Webb will have to
spend extra for the high-speed Internet.
ii. The files while being transmitted may get affected by the virus and thus those files when
get downloaded may affect Webb's system.
3. b. Webb’s use of a Cloud backup and its impact on the company and DR plan
The benefits that Webb is about to get-
i. The existing database of the Webb can be enhanced to get best solutions and profitable
solutions from the cloud.
ii. Amazon AWS provides the cloud services to Webb, they provide the maintenance and
the updating of the cloud database as well (Sharma et al., 2017).
iii. Amazon is widely known to cater best security solutions so Webb will not have to worry
about the security matter and can carry out their normal business activities with peace.
They should have a disaster recovery plan ready, they must store their important
files, financial record on the external drive so that they can retrieve those files offline in the
absence of Internet. Moreover, offline business activities leave no chance for hackers to
attack Webb’s database
9 Niranjan Acharya 11632403
III. Retrieval of data from the cloud
i. The high-speed Internet is required to retrieve files from the database, Webb will have to
spend extra for the high-speed Internet.
ii. The files while being transmitted may get affected by the virus and thus those files when
get downloaded may affect Webb's system.
3. b. Webb’s use of a Cloud backup and its impact on the company and DR plan
The benefits that Webb is about to get-
i. The existing database of the Webb can be enhanced to get best solutions and profitable
solutions from the cloud.
ii. Amazon AWS provides the cloud services to Webb, they provide the maintenance and
the updating of the cloud database as well (Sharma et al., 2017).
iii. Amazon is widely known to cater best security solutions so Webb will not have to worry
about the security matter and can carry out their normal business activities with peace.
They should have a disaster recovery plan ready, they must store their important
files, financial record on the external drive so that they can retrieve those files offline in the
absence of Internet. Moreover, offline business activities leave no chance for hackers to
attack Webb’s database
9 Niranjan Acharya 11632403
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Niranjan Acharya 11632403
Fig 3: Securing Cloud Data
(Source: Manvi, & Shyam, 2014, pp-424-440)
Question 4
4. Recommendations to Webb for protecting
access to the following services that they want to
move to the Cloud
4.a. Their IaaS infrastructure
Webb Store can enjoy the Amazon's AWS services and can carry out their business
operations in the fast efficient way (Dillon & Vossen, 2015). Webb though will have to pay
to Amazon annually for subscribing their cloud platform, however, they must know that the
Amazon's cloud service will help them in their business in the long run.
10 Niranjan Acharya 11632403
Fig 3: Securing Cloud Data
(Source: Manvi, & Shyam, 2014, pp-424-440)
Question 4
4. Recommendations to Webb for protecting
access to the following services that they want to
move to the Cloud
4.a. Their IaaS infrastructure
Webb Store can enjoy the Amazon's AWS services and can carry out their business
operations in the fast efficient way (Dillon & Vossen, 2015). Webb though will have to pay
to Amazon annually for subscribing their cloud platform, however, they must know that the
Amazon's cloud service will help them in their business in the long run.
10 Niranjan Acharya 11632403

Niranjan Acharya 11632403
4.b. Their Ms SQL Server 2012 R2 cloud instance
Amazon RDS for the SQL server caters excellent services to Webb Store in deploying
web applications on the cloud (Varia & Mathew, 2014). Along with that, Web must apply
physical security and along with that they must apply digital certificate for ensuring security
of their database.
4.c. Their Cloud network infrastructure
Webb can flourish their business activities with the aid of Amazon's advanced cloud
and security solutions and the latest configuration of AWS has the capability to provide
them with the facility to run cloud apps and cloud relevant tasks (Sharma et al., 2017).
Fig 4: Amazon AWS and its services
(Source: Muthui & SISAT, 2013)
11 Niranjan Acharya 11632403
4.b. Their Ms SQL Server 2012 R2 cloud instance
Amazon RDS for the SQL server caters excellent services to Webb Store in deploying
web applications on the cloud (Varia & Mathew, 2014). Along with that, Web must apply
physical security and along with that they must apply digital certificate for ensuring security
of their database.
4.c. Their Cloud network infrastructure
Webb can flourish their business activities with the aid of Amazon's advanced cloud
and security solutions and the latest configuration of AWS has the capability to provide
them with the facility to run cloud apps and cloud relevant tasks (Sharma et al., 2017).
Fig 4: Amazon AWS and its services
(Source: Muthui & SISAT, 2013)
11 Niranjan Acharya 11632403
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





