Comprehensive Risk Assessment Report: Cloud Architecture Security
VerifiedAdded on 2021/04/17
|15
|2969
|384
Report
AI Summary
This report presents a comprehensive risk assessment of a proposed cloud architecture, conducted using the ISO 27001 standards. It begins with an executive summary, followed by an introduction outlining the benefits of the ISO 27001 framework for security risk analysis, including improved security measures and standardized reporting. The report details owner specifications for various assets like cloud storage, virtual servers, and firewalls. It identifies potential threats associated with each asset, such as data theft and unauthorized access, and lists relevant vulnerabilities with CVE numbers. The Boston grid method is used to compute risk levels, and an impact table is provided. The report concludes with an overall analysis of the findings and a justification for the selected security measures, emphasizing the importance of certified security systems for building customer trust and streamlining business operations.

Running head: CLOUD ARCHITECTURE RISK ASSESSMENT
CLOUD ARCHITECTURE RISK ASSESSMENT
Name of the student:
Name of the university:
Author note:
CLOUD ARCHITECTURE RISK ASSESSMENT
Name of the student:
Name of the university:
Author note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1CLOUD ARCHITECTURE RISK ASSESSMENT
Executive summary:
The cloud architecture has several primary and secondary assets which constitutes the overall
architecture. The asset poses security threats for the network and the cloud system. The security
concern can be network security, data security and overall system security due to data theft and illegal
access of the customer database.
In order to provide security assessment for the proposed architectural model the ISO 27001 model is
recommended. There are various benefits of using the ISO 27001 standards for the risk assessment. The
advantages are the improved security measures, standard security report, identifications of flaws in the
cloud system and standard security assessment which is independent and unbiased thus increasing the
reliability of the assessment.
In order to deal with the sensitive data of the customers, there are various legal constraints
imposed on the operations. These kind of legal constrains affect the business flow in various levels. In
order to avoid the legal issues of dealing with the customer data, certifications for the security system is
very necessary. The certifications must be well recognized to increase the authenticity of the security
system and The ISO 27001 provides that necessary assurance of the security standards that assure
smooth business operation.
It is important to have certified security hallmark for the security system. The prime benefit of
having a security system that has international certifications is that it increases the confidence of the
customer in the system as well as in the organization. It assures the customers that the data they are
providing to the organization is safe and secure. It also reduces the necessity for conducting onsite
security audits that is not only lengthy but costly as well.
Executive summary:
The cloud architecture has several primary and secondary assets which constitutes the overall
architecture. The asset poses security threats for the network and the cloud system. The security
concern can be network security, data security and overall system security due to data theft and illegal
access of the customer database.
In order to provide security assessment for the proposed architectural model the ISO 27001 model is
recommended. There are various benefits of using the ISO 27001 standards for the risk assessment. The
advantages are the improved security measures, standard security report, identifications of flaws in the
cloud system and standard security assessment which is independent and unbiased thus increasing the
reliability of the assessment.
In order to deal with the sensitive data of the customers, there are various legal constraints
imposed on the operations. These kind of legal constrains affect the business flow in various levels. In
order to avoid the legal issues of dealing with the customer data, certifications for the security system is
very necessary. The certifications must be well recognized to increase the authenticity of the security
system and The ISO 27001 provides that necessary assurance of the security standards that assure
smooth business operation.
It is important to have certified security hallmark for the security system. The prime benefit of
having a security system that has international certifications is that it increases the confidence of the
customer in the system as well as in the organization. It assures the customers that the data they are
providing to the organization is safe and secure. It also reduces the necessity for conducting onsite
security audits that is not only lengthy but costly as well.

2CLOUD ARCHITECTURE RISK ASSESSMENT
Table of Contents
Executive summary:....................................................................................................................................1
Introduction:...............................................................................................................................................3
Risk Assessment:.........................................................................................................................................4
Owner specification:...............................................................................................................................4
Type of assets:.........................................................................................................................................5
Threats for each asset:............................................................................................................................6
Threats with cloud storage:................................................................................................................6
Threats with virtual servers:...............................................................................................................6
Threats with firewall:..........................................................................................................................6
Threats with the intranet:...................................................................................................................6
Threats with web and mail servers:....................................................................................................7
Threats with the firmware and the admin and user pc:......................................................................7
Vulnerabilities for each asset:.................................................................................................................8
Level computation, using Boston gird:..................................................................................................10
Impact table specification:....................................................................................................................11
Risk identification with the risk level, using Boston grid:......................................................................12
Reference:.................................................................................................................................................13
Table of Contents
Executive summary:....................................................................................................................................1
Introduction:...............................................................................................................................................3
Risk Assessment:.........................................................................................................................................4
Owner specification:...............................................................................................................................4
Type of assets:.........................................................................................................................................5
Threats for each asset:............................................................................................................................6
Threats with cloud storage:................................................................................................................6
Threats with virtual servers:...............................................................................................................6
Threats with firewall:..........................................................................................................................6
Threats with the intranet:...................................................................................................................6
Threats with web and mail servers:....................................................................................................7
Threats with the firmware and the admin and user pc:......................................................................7
Vulnerabilities for each asset:.................................................................................................................8
Level computation, using Boston gird:..................................................................................................10
Impact table specification:....................................................................................................................11
Risk identification with the risk level, using Boston grid:......................................................................12
Reference:.................................................................................................................................................13
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3CLOUD ARCHITECTURE RISK ASSESSMENT
Introduction:
The risk assessment of the proposed cloud architecture will be done using the ISO 27001
standards. It is a standard method used for the security risk analysis and gives a clear overview of the
security related factors. There are various benefits of using the ISO 27001 standards for the risk
assessment. The advantages are the improved security measures, standard security report, identifications
of flaws in the cloud system and standard security assessment (Alebrahim et al. 2015)
The standard provides a systematic approach to examine the risk of the implemented information
security system with a reference to the associated threats, vulnerabilities and impact of the threat that is
unique to the organization (Kurnianto, Isnanto and Widodo 2018).
Based on the analysis, it provides the most effective solutions to address those needs that will
improve the security of the system. It also provides the continuous assessments of security infrastructure
to meet with issues related to the system infrastructure.
The ISO 27001 is well a well recognized international standard for security assessment that
follows the criteria mentioned above. The certification, being independent and unbiased increases the
authenticity. The certification provides a systematic and scientific overview of the existing information
security practices (Hoy and Foley 2015).
The assessment report first discuses about the owner specifications that basically describes about
the hardware and software specifications used for the cloud system design. The threats associated with
each asset have also been discussed in the report. The Vulnerabilities associated with those assets has also
been highlighted with official CVE number. The Boston grid method has been used to compute the risk
level. The impact table specification has been provided in the report. With the help of the Boston grid the
risk associated with the project has been identified with the appropriate risk level. The report concludes
with the overall findings of the report with a justification for the chosen security measure.
Introduction:
The risk assessment of the proposed cloud architecture will be done using the ISO 27001
standards. It is a standard method used for the security risk analysis and gives a clear overview of the
security related factors. There are various benefits of using the ISO 27001 standards for the risk
assessment. The advantages are the improved security measures, standard security report, identifications
of flaws in the cloud system and standard security assessment (Alebrahim et al. 2015)
The standard provides a systematic approach to examine the risk of the implemented information
security system with a reference to the associated threats, vulnerabilities and impact of the threat that is
unique to the organization (Kurnianto, Isnanto and Widodo 2018).
Based on the analysis, it provides the most effective solutions to address those needs that will
improve the security of the system. It also provides the continuous assessments of security infrastructure
to meet with issues related to the system infrastructure.
The ISO 27001 is well a well recognized international standard for security assessment that
follows the criteria mentioned above. The certification, being independent and unbiased increases the
authenticity. The certification provides a systematic and scientific overview of the existing information
security practices (Hoy and Foley 2015).
The assessment report first discuses about the owner specifications that basically describes about
the hardware and software specifications used for the cloud system design. The threats associated with
each asset have also been discussed in the report. The Vulnerabilities associated with those assets has also
been highlighted with official CVE number. The Boston grid method has been used to compute the risk
level. The impact table specification has been provided in the report. With the help of the Boston grid the
risk associated with the project has been identified with the appropriate risk level. The report concludes
with the overall findings of the report with a justification for the chosen security measure.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4CLOUD ARCHITECTURE RISK ASSESSMENT
Risk Assessment:
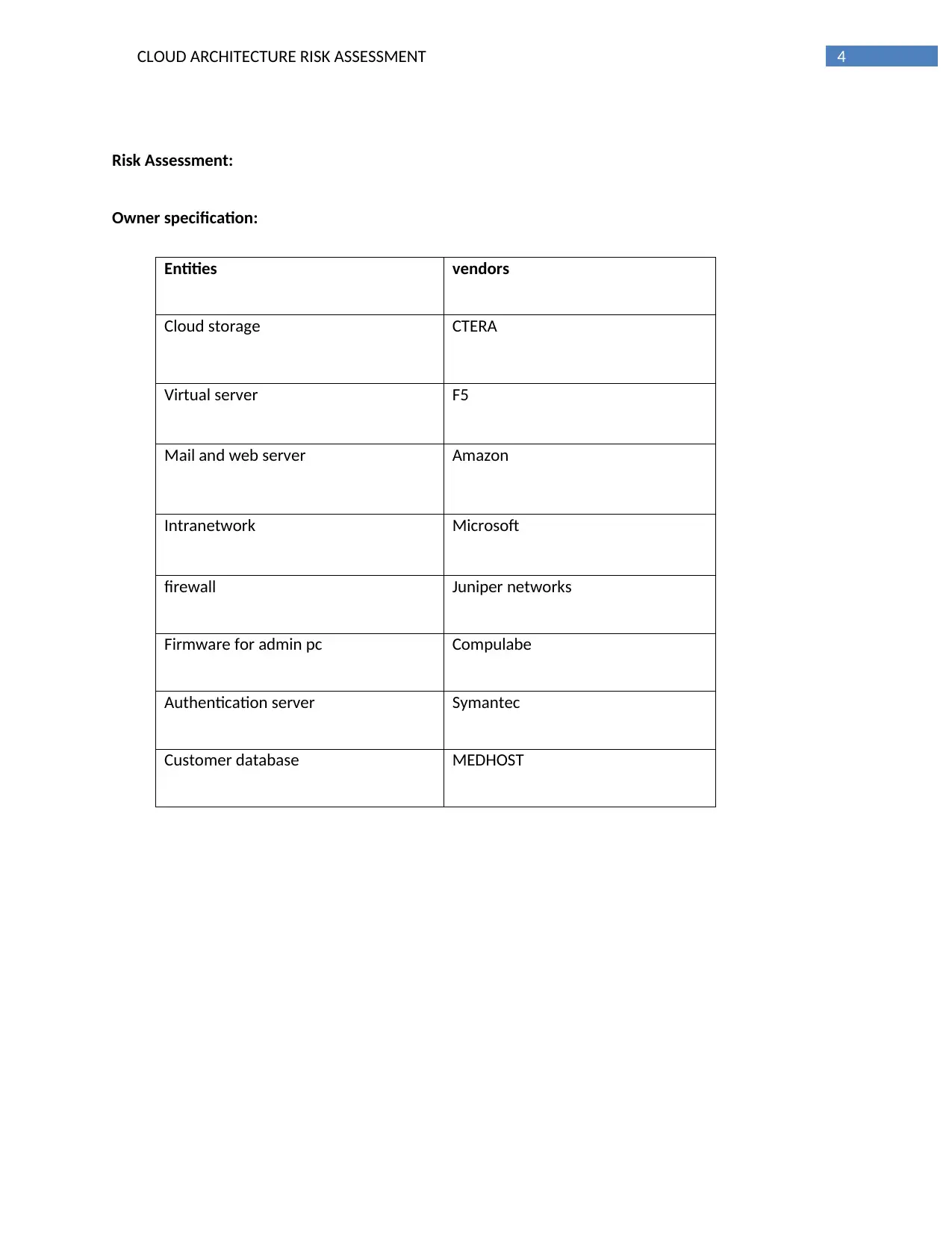
Owner specification:
Entities vendors
Cloud storage CTERA
Virtual server F5
Mail and web server Amazon
Intranetwork Microsoft
firewall Juniper networks
Firmware for admin pc Compulabe
Authentication server Symantec
Customer database MEDHOST
Risk Assessment:
Owner specification:
Entities vendors
Cloud storage CTERA
Virtual server F5
Mail and web server Amazon
Intranetwork Microsoft
firewall Juniper networks
Firmware for admin pc Compulabe
Authentication server Symantec
Customer database MEDHOST

5CLOUD ARCHITECTURE RISK ASSESSMENT
Type of assets:
The primary assets are those that need to be incorporated at the first place to implement other
assets. The second type of assets are known as secondary assets (Puiler, Martinez and Hill 2015).
To implement the cloud architecture both hardware and software is needed. However the
software must be first incorporated first to enable the hardware to support the cloud architecture.
Hence software is the primary assets and supported hardware is the secondary asset. The primary
assets include
Cloud storage
Virtual servers
Firewall
Firmware
Intranet
Internet
Web and email server
The secondary assets include:
Admin pc
Human resource pc
User pc
Type of assets:
The primary assets are those that need to be incorporated at the first place to implement other
assets. The second type of assets are known as secondary assets (Puiler, Martinez and Hill 2015).
To implement the cloud architecture both hardware and software is needed. However the
software must be first incorporated first to enable the hardware to support the cloud architecture.
Hence software is the primary assets and supported hardware is the secondary asset. The primary
assets include
Cloud storage
Virtual servers
Firewall
Firmware
Intranet
Internet
Web and email server
The secondary assets include:
Admin pc
Human resource pc
User pc
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6CLOUD ARCHITECTURE RISK ASSESSMENT
Threats for each asset:
Threats with cloud storage:
The cloud storage is provided by the third party service provider and located remotely. It is not
possible to take full control over the storage (Almorsy, Grundy and Muller 2016).
The options used for login to grant storage access is not totally secure which has been identified
by the hackers. Hence, there is high risk of data theft stored in the cloud storage (Almorsy, Grundy and
Muller 2016).
Threats with virtual servers:
Virtual server needs high level of administrations knowledge and if the administrator has lack of
understanding of the servers, then the server is likely to face security issues due to unauthorized access.
Virtual servers should be updated with the regular security patches; otherwise the server
becomes less secure and makes it easy to hack (Jokar, Arianpoo and Leung 2016).
Threats with firewall:
Firewall helps to create protection for the internal network against the attacks made via the
external internet. However, it is not suitable to defend the network against the internal security flaws.
If the system allows external communication like receiving emails from the outside sources, the
firewall cannot prevent the communication and detect flaws, if any (Singh, Jeong and Park 2016).
Threats with the intranet:
Intranet is used for the internal communication within the organization. This makes employees
fell that the network is fully secured and is not accessible from outside and due to this often weak
password is used for the login to profiles hosted on the network. This has the potential to make the
network less secure (Wang, Wei and Vangury 2014).
The access to the network is easily given to the peoples belonging to the organizations which
pose a security threats if the network is not handled properly.
Threats for each asset:
Threats with cloud storage:
The cloud storage is provided by the third party service provider and located remotely. It is not
possible to take full control over the storage (Almorsy, Grundy and Muller 2016).
The options used for login to grant storage access is not totally secure which has been identified
by the hackers. Hence, there is high risk of data theft stored in the cloud storage (Almorsy, Grundy and
Muller 2016).
Threats with virtual servers:
Virtual server needs high level of administrations knowledge and if the administrator has lack of
understanding of the servers, then the server is likely to face security issues due to unauthorized access.
Virtual servers should be updated with the regular security patches; otherwise the server
becomes less secure and makes it easy to hack (Jokar, Arianpoo and Leung 2016).
Threats with firewall:
Firewall helps to create protection for the internal network against the attacks made via the
external internet. However, it is not suitable to defend the network against the internal security flaws.
If the system allows external communication like receiving emails from the outside sources, the
firewall cannot prevent the communication and detect flaws, if any (Singh, Jeong and Park 2016).
Threats with the intranet:
Intranet is used for the internal communication within the organization. This makes employees
fell that the network is fully secured and is not accessible from outside and due to this often weak
password is used for the login to profiles hosted on the network. This has the potential to make the
network less secure (Wang, Wei and Vangury 2014).
The access to the network is easily given to the peoples belonging to the organizations which
pose a security threats if the network is not handled properly.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7CLOUD ARCHITECTURE RISK ASSESSMENT
Threats with web and mail servers:
The web and mail servers in the network are secured using the firewall. However, the firewall
too has limitations and it is not a complete solution for network security. The attackers, by finding
security flaws in the firewall can get access to the servers and steal important data (Wang, Wei and
Vangury 2014).
Threats with the firmware and the admin and user pc:
Firmware is not protected using the signed cryptography. This makes firmware easy to hack,
thus gaining access to the computer systems and the hardware it contains which allows to access and
steal important data in the system (Singh, Jeong and Park 2016) .
The admin pc as well as the user pc connected to the overall network is subject to security
threats.
Threats with web and mail servers:
The web and mail servers in the network are secured using the firewall. However, the firewall
too has limitations and it is not a complete solution for network security. The attackers, by finding
security flaws in the firewall can get access to the servers and steal important data (Wang, Wei and
Vangury 2014).
Threats with the firmware and the admin and user pc:
Firmware is not protected using the signed cryptography. This makes firmware easy to hack,
thus gaining access to the computer systems and the hardware it contains which allows to access and
steal important data in the system (Singh, Jeong and Park 2016) .
The admin pc as well as the user pc connected to the overall network is subject to security
threats.

8CLOUD ARCHITECTURE RISK ASSESSMENT
Vulnerabilities for each asset:
CVE-2013-2639
Vulnerability was found in the CTERA cloud storage. The vulnerability is related to the Cross-site
scripting (XSS). With the help of the scripting, remote attackers can inject web script arbitrarily. The
script can also inject HTML through description contained in a project folder (Cvedetails.com 2018).
CVE-2016-9245
The vulnerability is related to the F5 BIG-IP systems, the platform used for the Virtual servers.
The attackers can make malicious request that will be passed to the virtual servers through an HTTP
profile. This has the capability to restart the TMM. This Vulnerability is applicable to the all the BIG-IP
APM profiles irrespective of the settings applied to the profiles. The issue is also applicable non-default
"Normalize URI”, a configuration used for iRules. The issue is also exposed with the BIG-IP LTM policies.
With the help of this Vulnerability, it is possible for the attackers to create disruption in the traffic or
create failure in the BIG-IP system (Cve.mitre.org 2018).
CVE-2008-6096
This vulnerability is related with Juniper NetScreen ScreenOS that is used for the DMZ network
in the cloud architecture. With the help of the cross-site scripting, it is possible for the remote attackers
to inject web script arbitrarily. The script can also inject HTML through user name parameters used in
the web interface of the user login page (Cve.mitre.org 2018).
CVE-2017-6062
The "OpenID Connect Relying Party and OAuth 2.0 Resource Server" also known as the
mod_auth_openidc is used for the HTTP authentication server maintained by Apache software
foundation. The server does not have the ability to skip the OIDC_CLAIM_ and OIDCAuthNHeader
headers in an "OIDCUnAuthAction pass" configuration. This enables the attackers in bypassing the
authentication request made through the HTTP traffic (Cve.mitre.org 2018).
CVE-2017-11693
The vulnerability is related with the MEDHOST, a document management system that is used for
creating customer database in the cloud infrastructure. The system uses hard-coded credentials that are
necessary to request access to the database. It is not impossible for the unauthorized users to access the
database. All it takes is the knowledge of those credentials. With the help of those hard coded
credentials, it is possible for the attackers to directly communicate with the database. It is even possible
for the attackers to create modifications in the database by accessing the sensitive information
contained in the database. The database is designed with the PostgreSQL. The Account name is dms and
Vulnerabilities for each asset:
CVE-2013-2639
Vulnerability was found in the CTERA cloud storage. The vulnerability is related to the Cross-site
scripting (XSS). With the help of the scripting, remote attackers can inject web script arbitrarily. The
script can also inject HTML through description contained in a project folder (Cvedetails.com 2018).
CVE-2016-9245
The vulnerability is related to the F5 BIG-IP systems, the platform used for the Virtual servers.
The attackers can make malicious request that will be passed to the virtual servers through an HTTP
profile. This has the capability to restart the TMM. This Vulnerability is applicable to the all the BIG-IP
APM profiles irrespective of the settings applied to the profiles. The issue is also applicable non-default
"Normalize URI”, a configuration used for iRules. The issue is also exposed with the BIG-IP LTM policies.
With the help of this Vulnerability, it is possible for the attackers to create disruption in the traffic or
create failure in the BIG-IP system (Cve.mitre.org 2018).
CVE-2008-6096
This vulnerability is related with Juniper NetScreen ScreenOS that is used for the DMZ network
in the cloud architecture. With the help of the cross-site scripting, it is possible for the remote attackers
to inject web script arbitrarily. The script can also inject HTML through user name parameters used in
the web interface of the user login page (Cve.mitre.org 2018).
CVE-2017-6062
The "OpenID Connect Relying Party and OAuth 2.0 Resource Server" also known as the
mod_auth_openidc is used for the HTTP authentication server maintained by Apache software
foundation. The server does not have the ability to skip the OIDC_CLAIM_ and OIDCAuthNHeader
headers in an "OIDCUnAuthAction pass" configuration. This enables the attackers in bypassing the
authentication request made through the HTTP traffic (Cve.mitre.org 2018).
CVE-2017-11693
The vulnerability is related with the MEDHOST, a document management system that is used for
creating customer database in the cloud infrastructure. The system uses hard-coded credentials that are
necessary to request access to the database. It is not impossible for the unauthorized users to access the
database. All it takes is the knowledge of those credentials. With the help of those hard coded
credentials, it is possible for the attackers to directly communicate with the database. It is even possible
for the attackers to create modifications in the database by accessing the sensitive information
contained in the database. The database is designed with the PostgreSQL. The Account name is dms and
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9CLOUD ARCHITECTURE RISK ASSESSMENT
the password is hard-coded which is same not only throughout the applications but also same across all
the installation process. The customer does not have any option to change the password either. The
dms account connected to the PostgreSQL can access the database schema used for the DMS
(Cve.mitre.org 2018).
CVE-2017-9457
The vulnerability is identified with the firmware that is used in the admin pc. The firmware is
made by the Compulabe. The main issue with the firmware is that it does not include the signature
checking for firmware updates. Due to this, it is possible for anyone to modify the firmware setting
during the system flash. The modification can be done using the Phoenix “UEFI update program”. It is
not hard to obtain the Phoenix utility program. The DOS or the Windows version of the program can be
easily downloaded online. With the help of the utility program, rootkit can be installed to the computer
at the firmware level, which has the ability to corrupt the entire system, leading to the denial of the
service, even by the admin profile (Cve.mitre.org 2018).
The installation does not require the permission of the admin and the process can be completed
at the background without the knowledge of the user. Once the installation is done, it is not easily
detectable by the utilities provided by the operating service.
CVE-2017-8514
The vulnerability is related to the intranetwork that is used for the internal device connections
in the network. The intra network used is the architecture is the Microsoft SharePoint technology. The
issue that is identified in this context is that network is not strong enough to prevent unauthorized users
to access the data that is meant to be kept private and secure. Once the hackers get access to the
network, they can use the victim’s identity and perform action on behalf of the user, like changing
security setting, deleting content and it is even possible to steal important data like browser cookies and
inject malicious codes in the browser of the user (Cve.mitre.org 2018).
CVE-2017-9450
The vulnerability is the identified with the web and mail service provider Amazon Web
Services ,also known as AWS. The bootstrap tools packed called CloudFormation permits the users in
executing codes arbitrarily with root access. It helps the users in creating local files in the directory, not
specified in the system (Cve.mitre.org 2018).
the password is hard-coded which is same not only throughout the applications but also same across all
the installation process. The customer does not have any option to change the password either. The
dms account connected to the PostgreSQL can access the database schema used for the DMS
(Cve.mitre.org 2018).
CVE-2017-9457
The vulnerability is identified with the firmware that is used in the admin pc. The firmware is
made by the Compulabe. The main issue with the firmware is that it does not include the signature
checking for firmware updates. Due to this, it is possible for anyone to modify the firmware setting
during the system flash. The modification can be done using the Phoenix “UEFI update program”. It is
not hard to obtain the Phoenix utility program. The DOS or the Windows version of the program can be
easily downloaded online. With the help of the utility program, rootkit can be installed to the computer
at the firmware level, which has the ability to corrupt the entire system, leading to the denial of the
service, even by the admin profile (Cve.mitre.org 2018).
The installation does not require the permission of the admin and the process can be completed
at the background without the knowledge of the user. Once the installation is done, it is not easily
detectable by the utilities provided by the operating service.
CVE-2017-8514
The vulnerability is related to the intranetwork that is used for the internal device connections
in the network. The intra network used is the architecture is the Microsoft SharePoint technology. The
issue that is identified in this context is that network is not strong enough to prevent unauthorized users
to access the data that is meant to be kept private and secure. Once the hackers get access to the
network, they can use the victim’s identity and perform action on behalf of the user, like changing
security setting, deleting content and it is even possible to steal important data like browser cookies and
inject malicious codes in the browser of the user (Cve.mitre.org 2018).
CVE-2017-9450
The vulnerability is the identified with the web and mail service provider Amazon Web
Services ,also known as AWS. The bootstrap tools packed called CloudFormation permits the users in
executing codes arbitrarily with root access. It helps the users in creating local files in the directory, not
specified in the system (Cve.mitre.org 2018).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10CLOUD ARCHITECTURE RISK ASSESSMENT
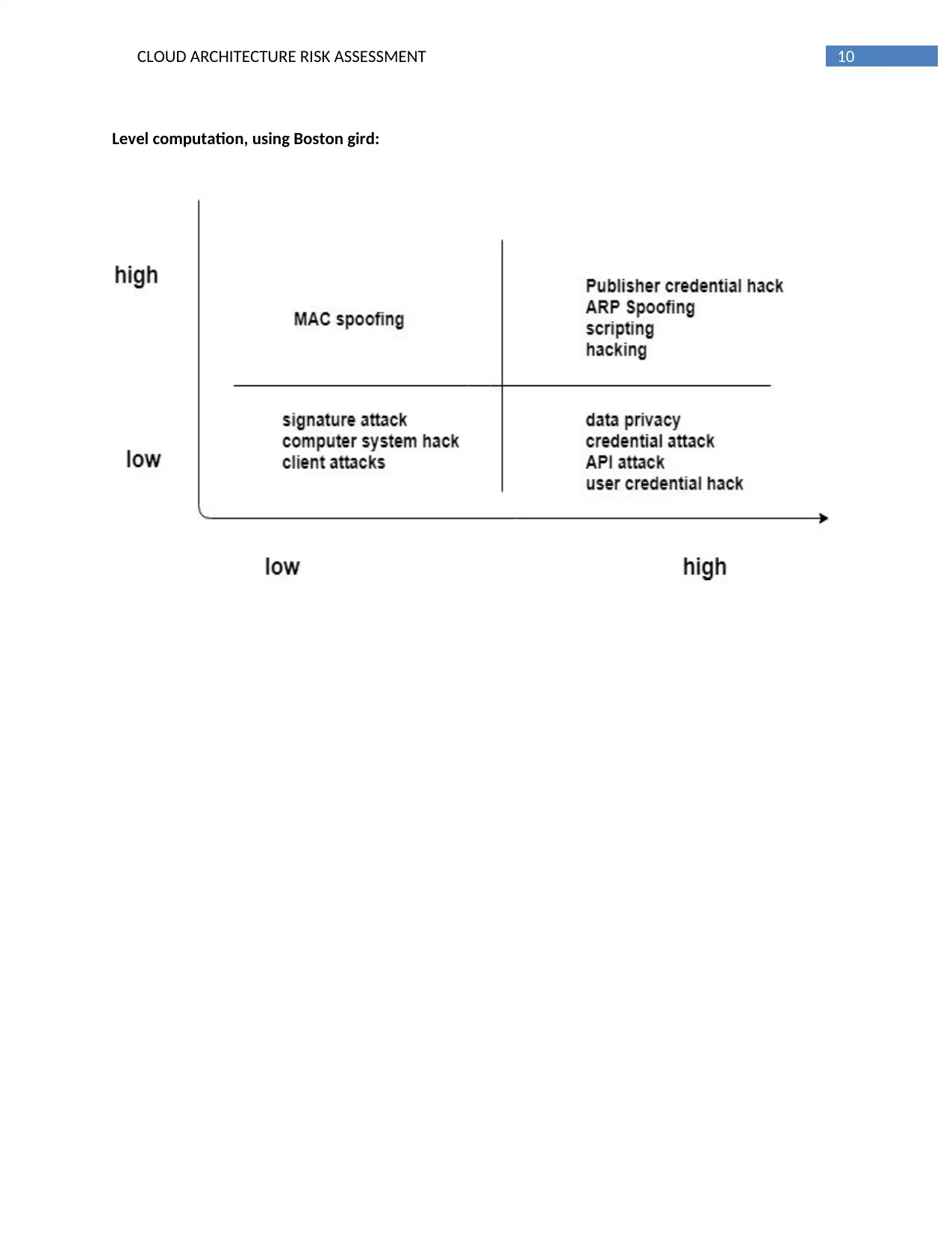
Level computation, using Boston gird:
Level computation, using Boston gird:
11CLOUD ARCHITECTURE RISK ASSESSMENT
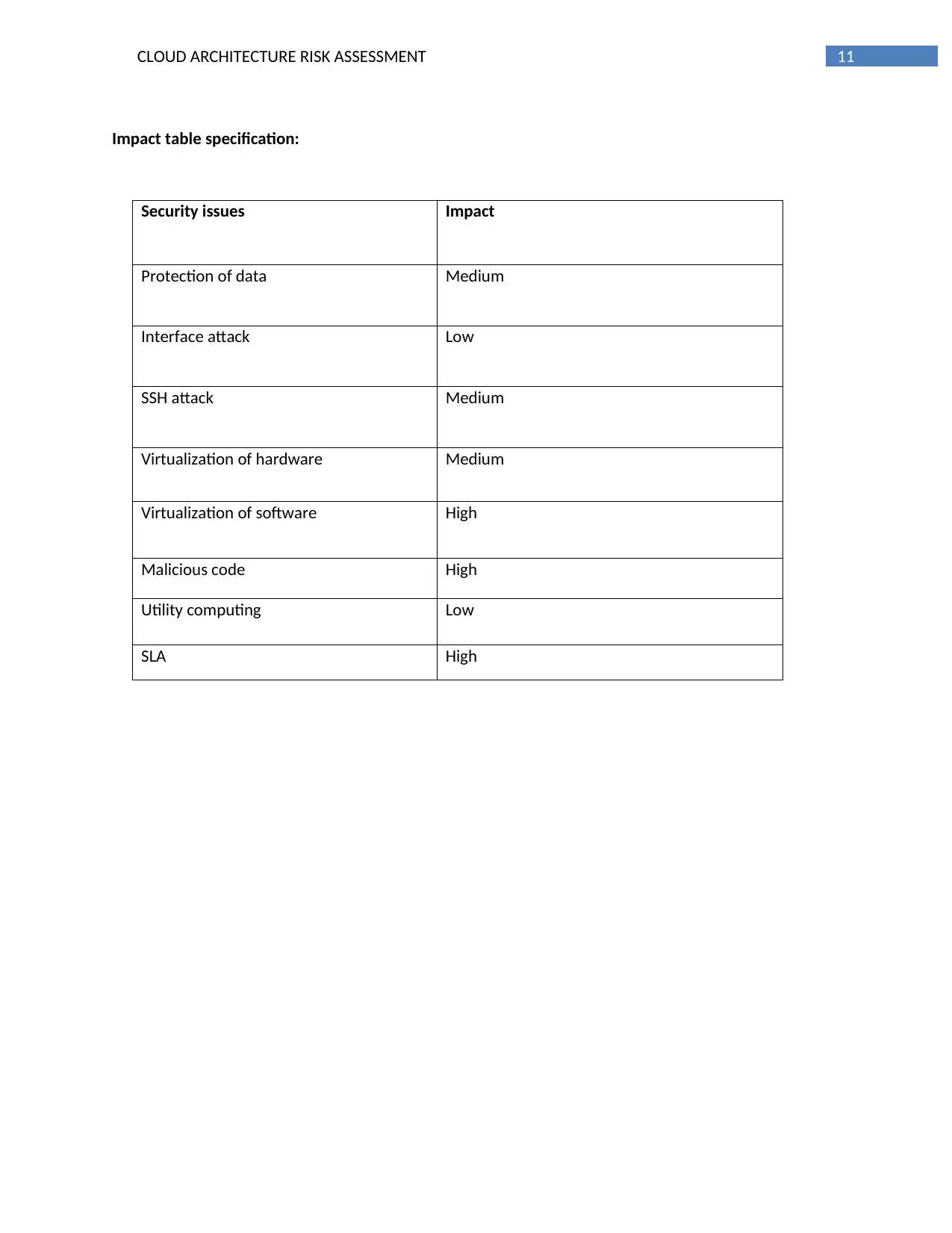
Impact table specification:
Security issues Impact
Protection of data Medium
Interface attack Low
SSH attack Medium
Virtualization of hardware Medium
Virtualization of software High
Malicious code High
Utility computing Low
SLA High
Impact table specification:
Security issues Impact
Protection of data Medium
Interface attack Low
SSH attack Medium
Virtualization of hardware Medium
Virtualization of software High
Malicious code High
Utility computing Low
SLA High
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



