Cloud Security Issues & Solutions in Big Data Management: A Review
VerifiedAdded on 2020/05/28
|16
|3287
|269
Literature Review
AI Summary
This document presents a literature review analyzing cloud security issues and solutions within the context of big data management. The review examines various cryptographic schemes, including Identity-Based Encryption (IBE) and Identity-Based Signature (IBS), to enhance data security. It includes a table summarizing multiple research papers, focusing on aspects such as cloud computing, Hadoop, data security, and data integrity. The analysis highlights current best solutions, such as a hierarchical framework for smart grids using Identity Based Cryptography, and their limitations, such as scalability issues. The proposed solution introduces the SA-EDS model, AD2 algorithm and SED2 algorithm to improve data efficiency and security in distributed cloud storage. The review also explores data encryption, network encryption, and access control methods to mitigate security challenges. The document provides equations and flowcharts to illustrate the working of the proposed solutions, emphasizing the need for robust security measures in cloud computing environments, and concludes by highlighting areas for improvement in securing distributed data storage.

Literature review Anaysis: CLOUD
SECURITY ISSUES & SOLUTIONS
IN BIG DATA MANAGEMENT
SECURITY ISSUES & SOLUTIONS
IN BIG DATA MANAGEMENT
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
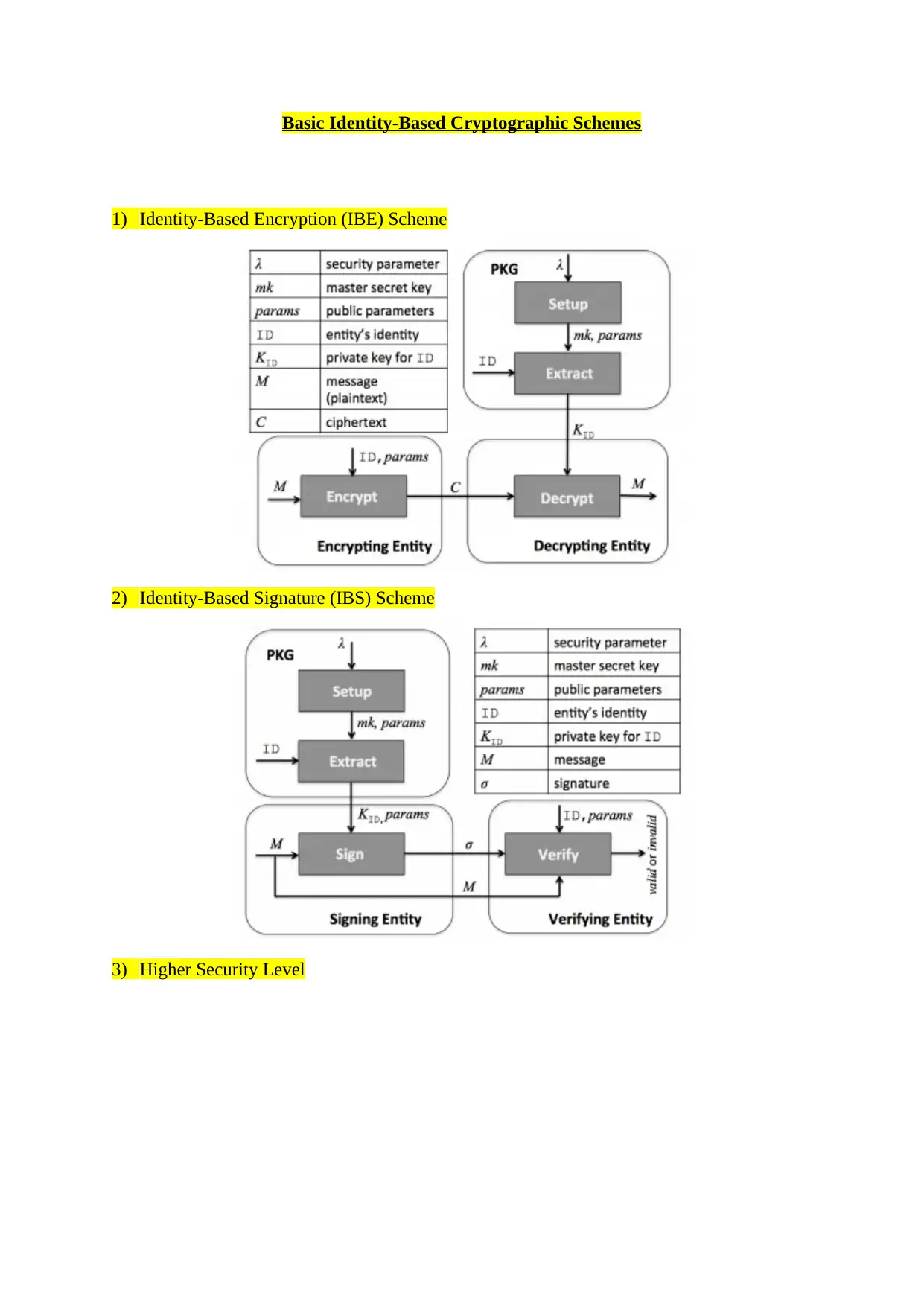
Basic Identity-Based Cryptographic Schemes
1) Identity-Based Encryption (IBE) Scheme
2) Identity-Based Signature (IBS) Scheme
3) Higher Security Level
1) Identity-Based Encryption (IBE) Scheme
2) Identity-Based Signature (IBS) Scheme
3) Higher Security Level
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
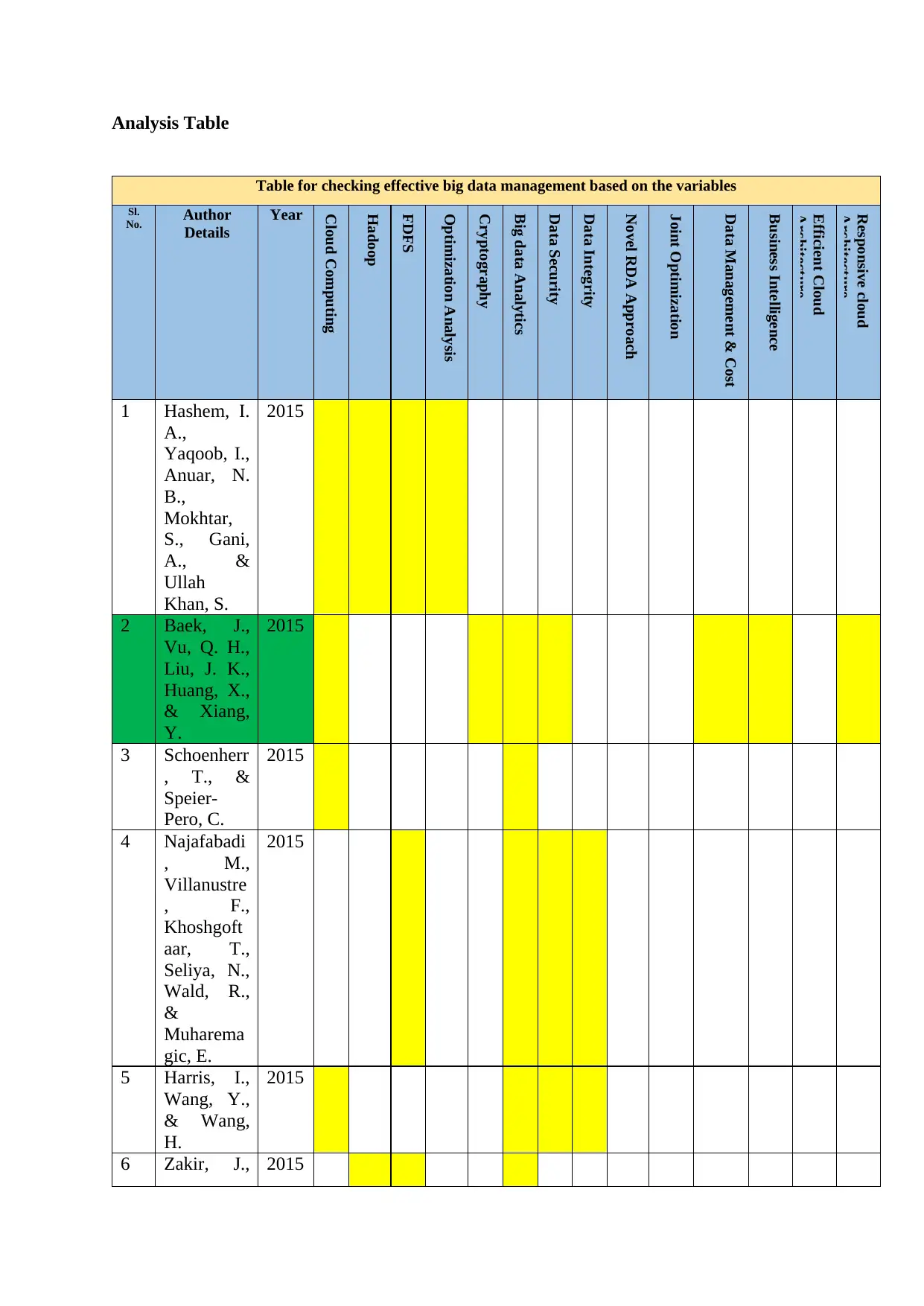
Analysis Table
Table for checking effective big data management based on the variables
Sl.
No. Author
Details
Year
Cloud Computing
Hadoop
FDFS
Optimization Analysis
Cryptography
Big data Analytics
Data Security
Data Integrity
Novel RDA Approach
Joint Optimization
Data Management & Cost
Business Intelligence
Efficient Cloud
Architecture
Responsive cloud
Architecture
1 Hashem, I.
A.,
Yaqoob, I.,
Anuar, N.
B.,
Mokhtar,
S., Gani,
A., &
Ullah
Khan, S.
2015
2 Baek, J.,
Vu, Q. H.,
Liu, J. K.,
Huang, X.,
& Xiang,
Y.
2015
3 Schoenherr
, T., &
Speier-
Pero, C.
2015
4 Najafabadi
, M.,
Villanustre
, F.,
Khoshgoft
aar, T.,
Seliya, N.,
Wald, R.,
&
Muharema
gic, E.
2015
5 Harris, I.,
Wang, Y.,
& Wang,
H.
2015
6 Zakir, J., 2015
Table for checking effective big data management based on the variables
Sl.
No. Author
Details
Year
Cloud Computing
Hadoop
FDFS
Optimization Analysis
Cryptography
Big data Analytics
Data Security
Data Integrity
Novel RDA Approach
Joint Optimization
Data Management & Cost
Business Intelligence
Efficient Cloud
Architecture
Responsive cloud
Architecture
1 Hashem, I.
A.,
Yaqoob, I.,
Anuar, N.
B.,
Mokhtar,
S., Gani,
A., &
Ullah
Khan, S.
2015
2 Baek, J.,
Vu, Q. H.,
Liu, J. K.,
Huang, X.,
& Xiang,
Y.
2015
3 Schoenherr
, T., &
Speier-
Pero, C.
2015
4 Najafabadi
, M.,
Villanustre
, F.,
Khoshgoft
aar, T.,
Seliya, N.,
Wald, R.,
&
Muharema
gic, E.
2015
5 Harris, I.,
Wang, Y.,
& Wang,
H.
2015
6 Zakir, J., 2015
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
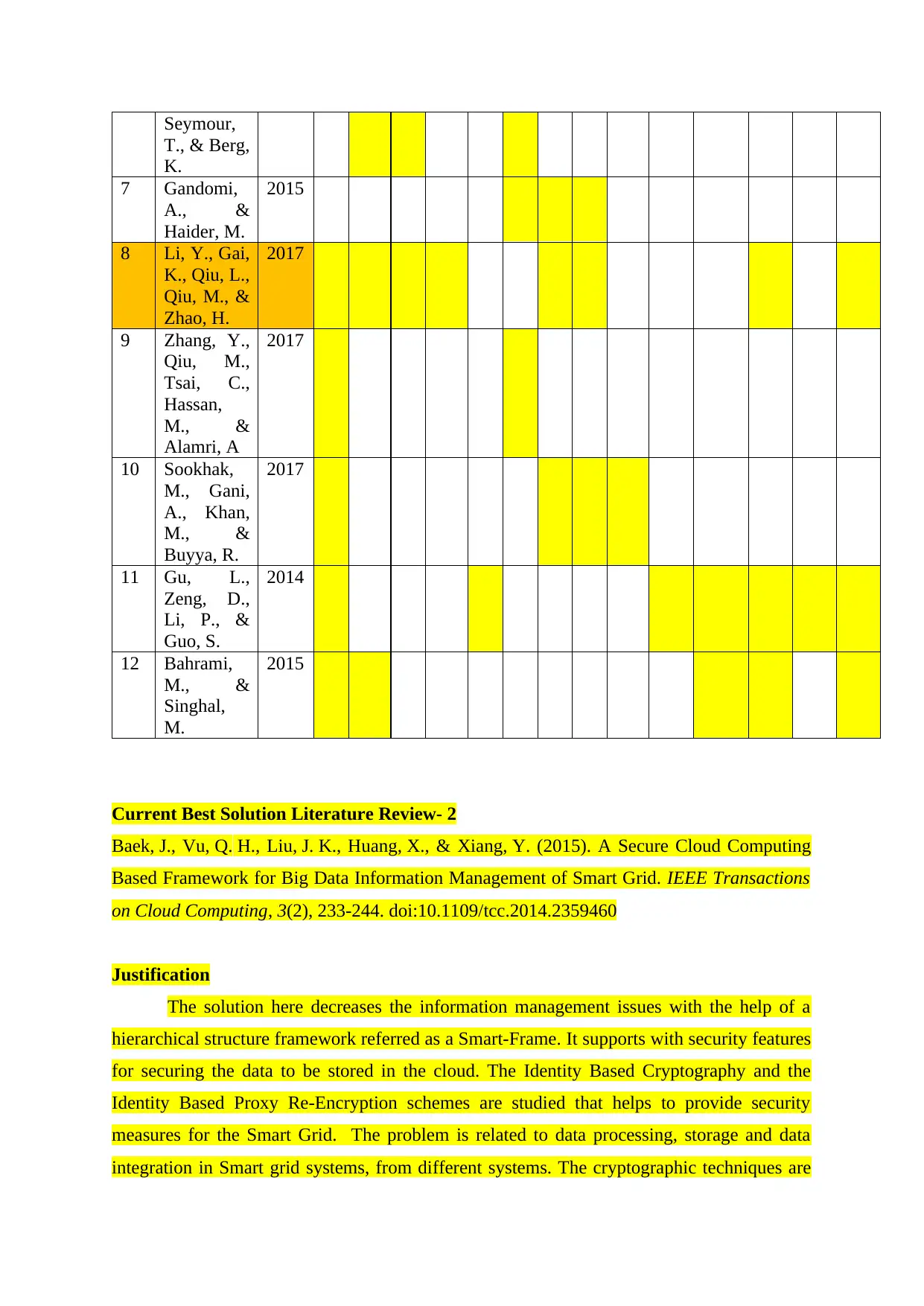
Seymour,
T., & Berg,
K.
7 Gandomi,
A., &
Haider, M.
2015
8 Li, Y., Gai,
K., Qiu, L.,
Qiu, M., &
Zhao, H.
2017
9 Zhang, Y.,
Qiu, M.,
Tsai, C.,
Hassan,
M., &
Alamri, A
2017
10 Sookhak,
M., Gani,
A., Khan,
M., &
Buyya, R.
2017
11 Gu, L.,
Zeng, D.,
Li, P., &
Guo, S.
2014
12 Bahrami,
M., &
Singhal,
M.
2015
Current Best Solution Literature Review- 2
Baek, J., Vu, Q. H., Liu, J. K., Huang, X., & Xiang, Y. (2015). A Secure Cloud Computing
Based Framework for Big Data Information Management of Smart Grid. IEEE Transactions
on Cloud Computing, 3(2), 233-244. doi:10.1109/tcc.2014.2359460
Justification
The solution here decreases the information management issues with the help of a
hierarchical structure framework referred as a Smart-Frame. It supports with security features
for securing the data to be stored in the cloud. The Identity Based Cryptography and the
Identity Based Proxy Re-Encryption schemes are studied that helps to provide security
measures for the Smart Grid. The problem is related to data processing, storage and data
integration in Smart grid systems, from different systems. The cryptographic techniques are
T., & Berg,
K.
7 Gandomi,
A., &
Haider, M.
2015
8 Li, Y., Gai,
K., Qiu, L.,
Qiu, M., &
Zhao, H.
2017
9 Zhang, Y.,
Qiu, M.,
Tsai, C.,
Hassan,
M., &
Alamri, A
2017
10 Sookhak,
M., Gani,
A., Khan,
M., &
Buyya, R.
2017
11 Gu, L.,
Zeng, D.,
Li, P., &
Guo, S.
2014
12 Bahrami,
M., &
Singhal,
M.
2015
Current Best Solution Literature Review- 2
Baek, J., Vu, Q. H., Liu, J. K., Huang, X., & Xiang, Y. (2015). A Secure Cloud Computing
Based Framework for Big Data Information Management of Smart Grid. IEEE Transactions
on Cloud Computing, 3(2), 233-244. doi:10.1109/tcc.2014.2359460
Justification
The solution here decreases the information management issues with the help of a
hierarchical structure framework referred as a Smart-Frame. It supports with security features
for securing the data to be stored in the cloud. The Identity Based Cryptography and the
Identity Based Proxy Re-Encryption schemes are studied that helps to provide security
measures for the Smart Grid. The problem is related to data processing, storage and data
integration in Smart grid systems, from different systems. The cryptographic techniques are
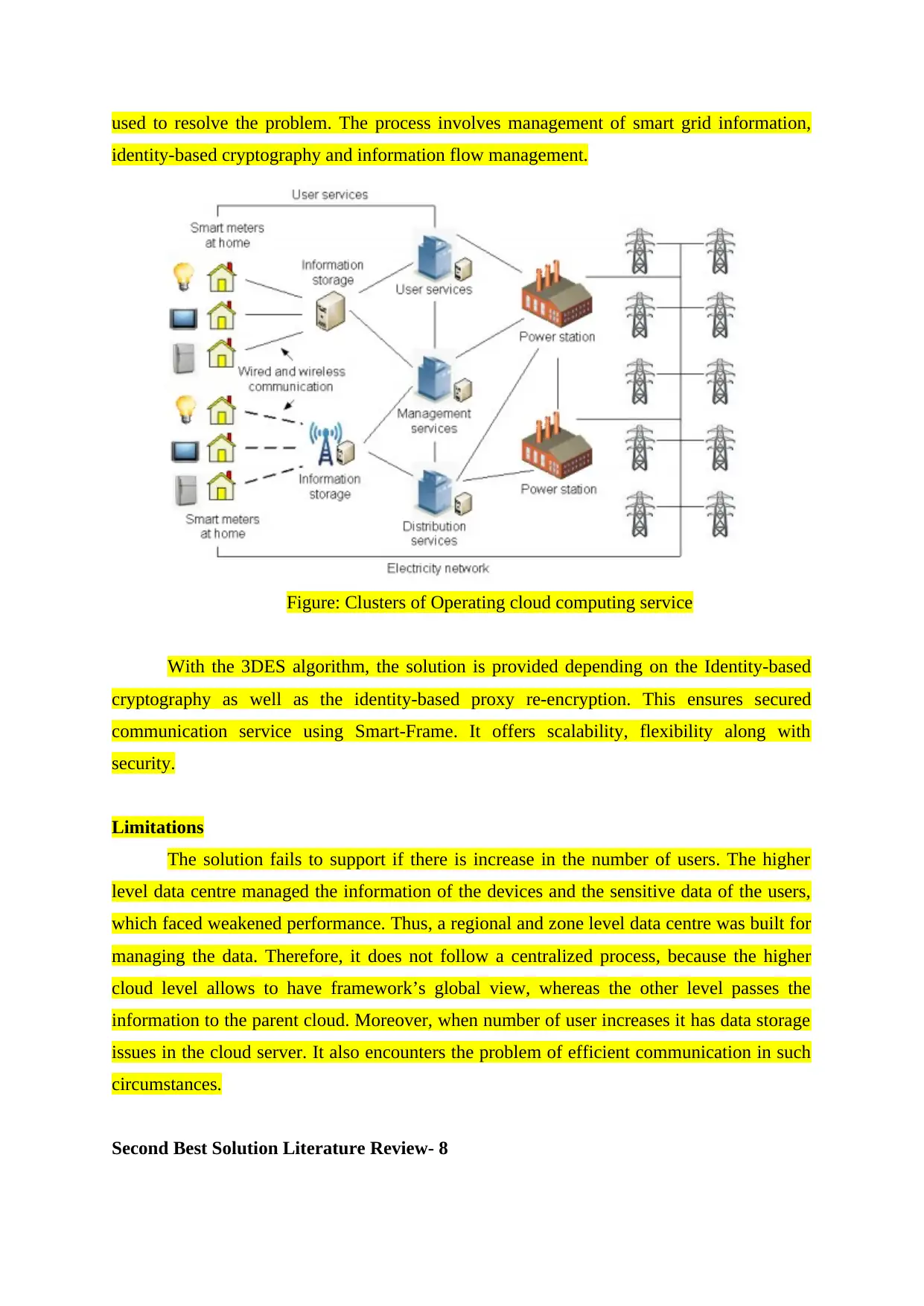
used to resolve the problem. The process involves management of smart grid information,
identity-based cryptography and information flow management.
Figure: Clusters of Operating cloud computing service
With the 3DES algorithm, the solution is provided depending on the Identity-based
cryptography as well as the identity-based proxy re-encryption. This ensures secured
communication service using Smart-Frame. It offers scalability, flexibility along with
security.
Limitations
The solution fails to support if there is increase in the number of users. The higher
level data centre managed the information of the devices and the sensitive data of the users,
which faced weakened performance. Thus, a regional and zone level data centre was built for
managing the data. Therefore, it does not follow a centralized process, because the higher
cloud level allows to have framework’s global view, whereas the other level passes the
information to the parent cloud. Moreover, when number of user increases it has data storage
issues in the cloud server. It also encounters the problem of efficient communication in such
circumstances.
Second Best Solution Literature Review- 8
identity-based cryptography and information flow management.
Figure: Clusters of Operating cloud computing service
With the 3DES algorithm, the solution is provided depending on the Identity-based
cryptography as well as the identity-based proxy re-encryption. This ensures secured
communication service using Smart-Frame. It offers scalability, flexibility along with
security.
Limitations
The solution fails to support if there is increase in the number of users. The higher
level data centre managed the information of the devices and the sensitive data of the users,
which faced weakened performance. Thus, a regional and zone level data centre was built for
managing the data. Therefore, it does not follow a centralized process, because the higher
cloud level allows to have framework’s global view, whereas the other level passes the
information to the parent cloud. Moreover, when number of user increases it has data storage
issues in the cloud server. It also encounters the problem of efficient communication in such
circumstances.
Second Best Solution Literature Review- 8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Li, Y., Gai, K., Qiu, L., Qiu, M., & Zhao, H. (2017). Intelligent cryptography approach for
secure distributed big data storage in cloud computing. Information Sciences, 387, 103-115.
http://dx.doi.org/10.1016/j.ins.2016.09.005
Justification
This solution uses intelligent cryptography method. In this method the files are split
into two parts such as normal data and sensitive data and they are stored in a distributed cloud
servers. Hence it increases the security of cloud services and the data cannot be accessed by
the service providers. Cloud computing is one of the significant technology which uses STaas
model to enable the huge remote data storage. In big data, cloud based technology is mainly
used for the development of networks and web services. However this cloud technology has
critical issues in the privacy and security of the data. Because the sensitive data can be
accessed by the cloud operators. Hence this issue is solved by the intelligent cryptography
method. Hence, the sensitive data cannot accessed by the cloud operators directly. The Key
process of this method is the files are split into two parts and stored in different distributed
cloud servers. It also has alternative approach to reduce the process time by determining
whether the data packets needs to split.
Proposed Solution
The proposed solution mainly addresses the data efficiency performance to its cloud
providers, with the help of SA-EDS. The problem is addressed as Security Improvement
Problem in Distributed Storage (SIPDS). With the help of the given input data and distributed
cloud servers, the cloud security problem finds appropriate solution for effectively storing the
data in the cloud servers. It also ensures that the data reaches the cloud client irrespective any
increase in the execution time. The data conversion requires less execution time, for hiding
the sensitive data i.e., the newly generated data packets. This helps to secure the data from the
cloud operators. Thus, this proposed solution uses SA-EDS model, AD2 algorithm to
evaluate the efficiency and security of the results. The working of the SA-EDS model is
given in the below flow chart.
secure distributed big data storage in cloud computing. Information Sciences, 387, 103-115.
http://dx.doi.org/10.1016/j.ins.2016.09.005
Justification
This solution uses intelligent cryptography method. In this method the files are split
into two parts such as normal data and sensitive data and they are stored in a distributed cloud
servers. Hence it increases the security of cloud services and the data cannot be accessed by
the service providers. Cloud computing is one of the significant technology which uses STaas
model to enable the huge remote data storage. In big data, cloud based technology is mainly
used for the development of networks and web services. However this cloud technology has
critical issues in the privacy and security of the data. Because the sensitive data can be
accessed by the cloud operators. Hence this issue is solved by the intelligent cryptography
method. Hence, the sensitive data cannot accessed by the cloud operators directly. The Key
process of this method is the files are split into two parts and stored in different distributed
cloud servers. It also has alternative approach to reduce the process time by determining
whether the data packets needs to split.
Proposed Solution
The proposed solution mainly addresses the data efficiency performance to its cloud
providers, with the help of SA-EDS. The problem is addressed as Security Improvement
Problem in Distributed Storage (SIPDS). With the help of the given input data and distributed
cloud servers, the cloud security problem finds appropriate solution for effectively storing the
data in the cloud servers. It also ensures that the data reaches the cloud client irrespective any
increase in the execution time. The data conversion requires less execution time, for hiding
the sensitive data i.e., the newly generated data packets. This helps to secure the data from the
cloud operators. Thus, this proposed solution uses SA-EDS model, AD2 algorithm to
evaluate the efficiency and security of the results. The working of the SA-EDS model is
given in the below flow chart.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
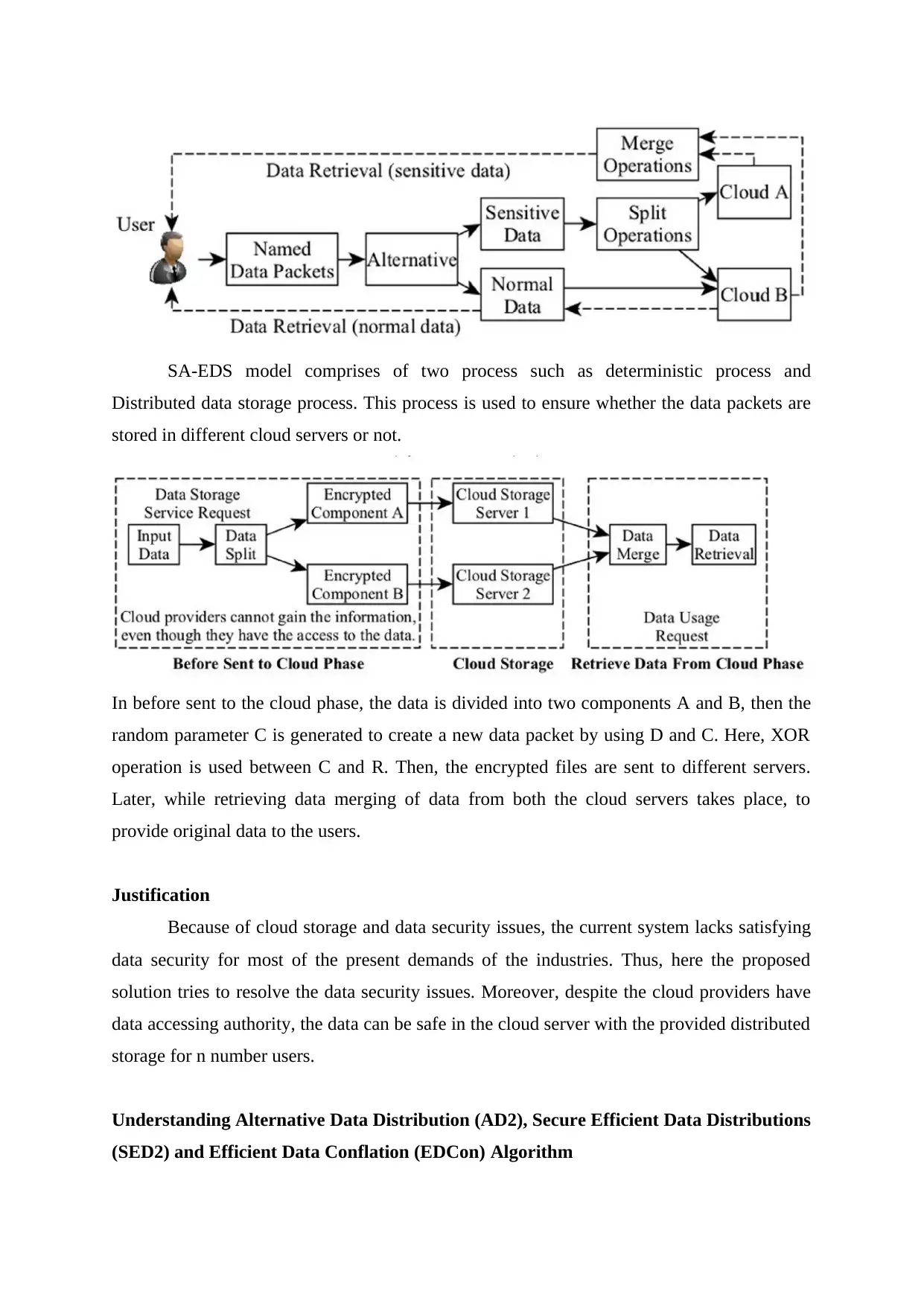
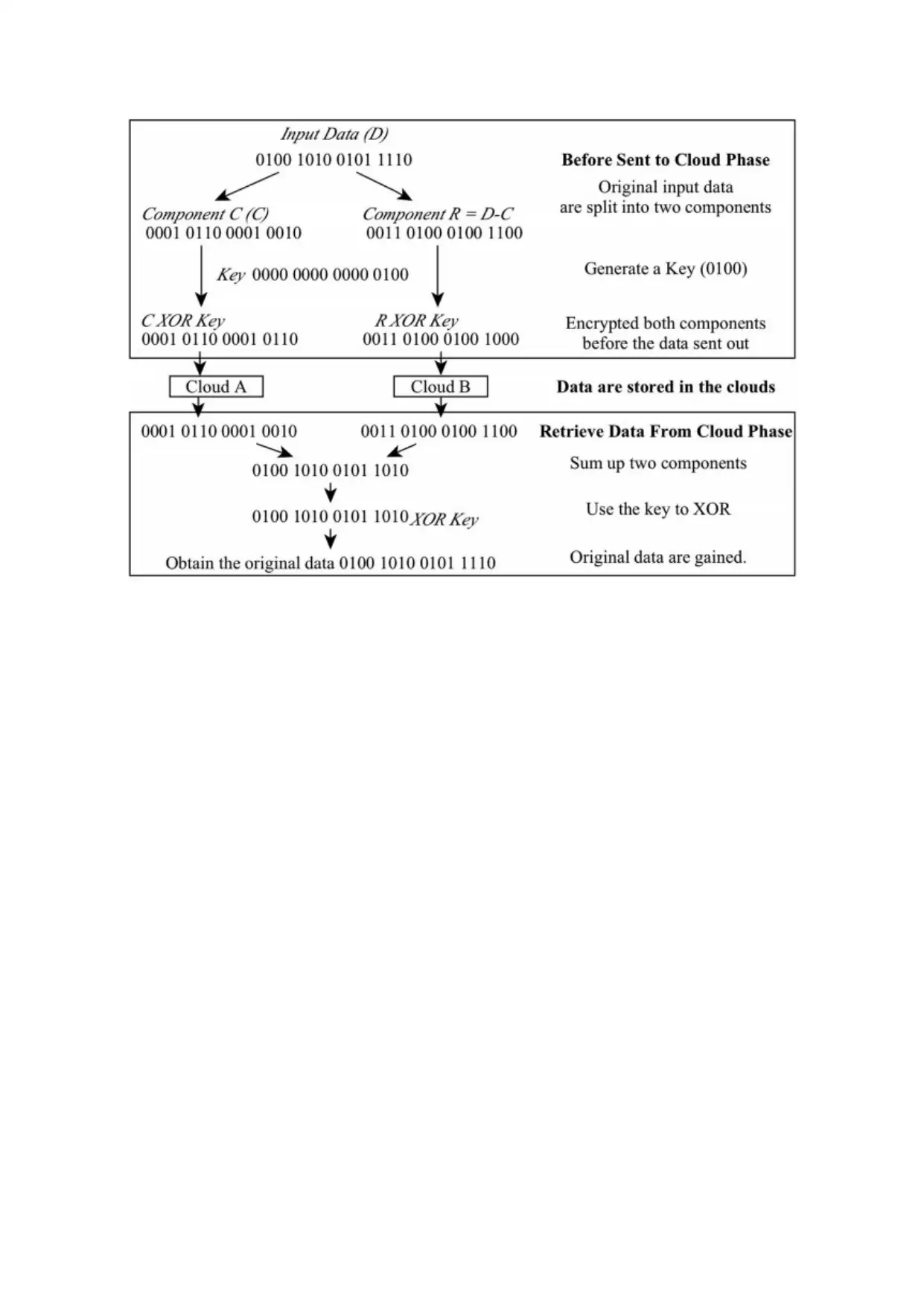
SA-EDS model comprises of two process such as deterministic process and
Distributed data storage process. This process is used to ensure whether the data packets are
stored in different cloud servers or not.
In before sent to the cloud phase, the data is divided into two components A and B, then the
random parameter C is generated to create a new data packet by using D and C. Here, XOR
operation is used between C and R. Then, the encrypted files are sent to different servers.
Later, while retrieving data merging of data from both the cloud servers takes place, to
provide original data to the users.
Justification
Because of cloud storage and data security issues, the current system lacks satisfying
data security for most of the present demands of the industries. Thus, here the proposed
solution tries to resolve the data security issues. Moreover, despite the cloud providers have
data accessing authority, the data can be safe in the cloud server with the provided distributed
storage for n number users.
Understanding Alternative Data Distribution (AD2), Secure Efficient Data Distributions
(SED2) and Efficient Data Conflation (EDCon) Algorithm
Distributed data storage process. This process is used to ensure whether the data packets are
stored in different cloud servers or not.
In before sent to the cloud phase, the data is divided into two components A and B, then the
random parameter C is generated to create a new data packet by using D and C. Here, XOR
operation is used between C and R. Then, the encrypted files are sent to different servers.
Later, while retrieving data merging of data from both the cloud servers takes place, to
provide original data to the users.
Justification
Because of cloud storage and data security issues, the current system lacks satisfying
data security for most of the present demands of the industries. Thus, here the proposed
solution tries to resolve the data security issues. Moreover, despite the cloud providers have
data accessing authority, the data can be safe in the cloud server with the provided distributed
storage for n number users.
Understanding Alternative Data Distribution (AD2), Secure Efficient Data Distributions
(SED2) and Efficient Data Conflation (EDCon) Algorithm

AD2 Algorithm
This algorithm helps in successfully determining the requirements like the data packet
must be split or it has be to safely stored in the distributed cloud servers. It has compatibility
with the framework of big data like the Hadoop MapReduce. This algorithm ensure to split
the data, which groups the named-data-packets. It requires Named-Data-Packets (NDP),
{D(N)}, and Pre-stored Name List (PNL) as its inputs. The data packet’s configured list is
defined by PBL. This algorithm mainly insists on securing the sensitive data. Data
segregation takes place for generating the outcome of this algorithm.
SED2 Algorithm
This SED2 algorithm is mainly used process the data before it is sent to the cloud
server. Hence it is placed prior to the" before sent to cloud phase". The execution of this
algorithm defends the threat model.
EDCon Algorithm
To converge the data from two distributed servers, EDCon algorithm is used. It
retrieves the data from cloud phase. The main advantage of this solution is, it provides
schematic architecture of the data to ensure high level security and privacy in cloud server.
This new approach mainly focuses on the privacy and security of the data by making it hard
to access the data by the service providers.
Area of Improvement
The proposed solution works on improving the issues related to data storage in cloud.
The security stage is improved, where it improves the data security, from the cloud providers.
This article ensures to decrease the changes of security threats from the cloud providers that
generally occur during the retrieving or requesting the sensitive information from the cloud.
The results of the proposed solution can help in discarding serious threats in the cloud. On the
other hand, the computation time is relatively short when compared to the actively present
methods. The proposed solution enhances efficiency, security and data storage from the cloud
service providers. However, this requires improvement in securing the distributed data
storage, as this brings the possibilities of threat from various sides.
Symbols Used:
α, β, γ , γ’ - Dataset
Dxor - Encrypted Data Packet
This algorithm helps in successfully determining the requirements like the data packet
must be split or it has be to safely stored in the distributed cloud servers. It has compatibility
with the framework of big data like the Hadoop MapReduce. This algorithm ensure to split
the data, which groups the named-data-packets. It requires Named-Data-Packets (NDP),
{D(N)}, and Pre-stored Name List (PNL) as its inputs. The data packet’s configured list is
defined by PBL. This algorithm mainly insists on securing the sensitive data. Data
segregation takes place for generating the outcome of this algorithm.
SED2 Algorithm
This SED2 algorithm is mainly used process the data before it is sent to the cloud
server. Hence it is placed prior to the" before sent to cloud phase". The execution of this
algorithm defends the threat model.
EDCon Algorithm
To converge the data from two distributed servers, EDCon algorithm is used. It
retrieves the data from cloud phase. The main advantage of this solution is, it provides
schematic architecture of the data to ensure high level security and privacy in cloud server.
This new approach mainly focuses on the privacy and security of the data by making it hard
to access the data by the service providers.
Area of Improvement
The proposed solution works on improving the issues related to data storage in cloud.
The security stage is improved, where it improves the data security, from the cloud providers.
This article ensures to decrease the changes of security threats from the cloud providers that
generally occur during the retrieving or requesting the sensitive information from the cloud.
The results of the proposed solution can help in discarding serious threats in the cloud. On the
other hand, the computation time is relatively short when compared to the actively present
methods. The proposed solution enhances efficiency, security and data storage from the cloud
service providers. However, this requires improvement in securing the distributed data
storage, as this brings the possibilities of threat from various sides.
Symbols Used:
α, β, γ , γ’ - Dataset
Dxor - Encrypted Data Packet
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

R, C - Data Packets/ Split two components
K - Key Value
XOR - EXOR operation
D - Original input data
Proposed Equation
D → (C, R)
D-C
D = C + R
α=C XOR key and β = R XOR Key.
Justification
Cloud computing has many security issues, because it is used in many technologies
like database, networking, operating systems, memory management, transaction
management, resource scheduling, concurrency control, load balancing and virtualization.
The Explosion of the data leads to difficulty for many industries. Hence, the data mining
techniques are used in clouds to detect the malwares. The security challenges in cloud
computing can be categorized into different levels such as network, authentication, data and
generic types.
Different security solutions can be given to improve the cloud security. This solution
has multiple technologies, to mitigate the security problems.
File Encryption
In machines the data is present in the cluster form. Hence the hacker can steal the
sensitive data easily. So the file encryption method can be used to encrypt the data. Different
types of encryption keys can be used in different machines and the key information can be
stored in the firewalls. Hence the user data can be stored securely in a encrypted format.
Network Encryption
In this security method, all the communication networks needs to be encrypted based
on the industry standard. SSL should be used for the RPC procedure calls. Hence the hacker
cannot tap the data packets.
Node Maintenance and Software Format
The nodes which are used to run the software’s must be formatted frequently to avoid
the virus. The software’s should be updated regularly to avoid the malwares and to increase
the data security in the system.
Authentication of Nodes
K - Key Value
XOR - EXOR operation
D - Original input data
Proposed Equation
D → (C, R)
D-C
D = C + R
α=C XOR key and β = R XOR Key.
Justification
Cloud computing has many security issues, because it is used in many technologies
like database, networking, operating systems, memory management, transaction
management, resource scheduling, concurrency control, load balancing and virtualization.
The Explosion of the data leads to difficulty for many industries. Hence, the data mining
techniques are used in clouds to detect the malwares. The security challenges in cloud
computing can be categorized into different levels such as network, authentication, data and
generic types.
Different security solutions can be given to improve the cloud security. This solution
has multiple technologies, to mitigate the security problems.
File Encryption
In machines the data is present in the cluster form. Hence the hacker can steal the
sensitive data easily. So the file encryption method can be used to encrypt the data. Different
types of encryption keys can be used in different machines and the key information can be
stored in the firewalls. Hence the user data can be stored securely in a encrypted format.
Network Encryption
In this security method, all the communication networks needs to be encrypted based
on the industry standard. SSL should be used for the RPC procedure calls. Hence the hacker
cannot tap the data packets.
Node Maintenance and Software Format
The nodes which are used to run the software’s must be formatted frequently to avoid
the virus. The software’s should be updated regularly to avoid the malwares and to increase
the data security in the system.
Authentication of Nodes
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

When a new node joins to the cluster, it should be authenticated to avoid the
malicious nodes. To validate the nodes Kerberos technique can be used.
Map Reducing and System Testing
Once the developer finishes the map reduce work, it should be tested in the distributed
environment to ensure the stability of the work.
Layered Frame Work
This layered frame work is used to assure the cloud computing. It has different layers
like virtual machine, secure cloud storage, virtual network monitor and secure cloud data
layer.
Access Control
It is a good security measure to integrate the different privacy and access controls.
Hence the data providers can control the security policy for the sensitive data.
Current Equation for Data Security Proposed Equation for Data
Security
KTC(= κ = g1 s0 )
Evaluate
g1 = H1(TC) ∈ G1 and gM = H1(TC, M) ∈ G1.
Select r ∈ Zq
σ1 = κ grM and σ2= gr0.
σ = (σ1, σ2)
e(g0, σ1) = e(g0, κ grM)=e(g0, κ) e(g0, gr M )= e(g0, g0, g1
s0) e(g0r, gM) = e(u, g1)e(σ2, gM).
D → (C, R)
D-C
D = C + R
α=C XOR key and β = R XOR
Key.
The signature (σ) for the (message) M is verified with
the params and the top cloud’s Identity (TC). Where,
it requires confirmation from
e(g0, σ1) = e(u, g1)e(σ2, gM).
This method helps to effectively
secure the sensitive data, of n
number of users.
Security is comparatively low. High security is increased.
malicious nodes. To validate the nodes Kerberos technique can be used.
Map Reducing and System Testing
Once the developer finishes the map reduce work, it should be tested in the distributed
environment to ensure the stability of the work.
Layered Frame Work
This layered frame work is used to assure the cloud computing. It has different layers
like virtual machine, secure cloud storage, virtual network monitor and secure cloud data
layer.
Access Control
It is a good security measure to integrate the different privacy and access controls.
Hence the data providers can control the security policy for the sensitive data.
Current Equation for Data Security Proposed Equation for Data
Security
KTC(= κ = g1 s0 )
Evaluate
g1 = H1(TC) ∈ G1 and gM = H1(TC, M) ∈ G1.
Select r ∈ Zq
σ1 = κ grM and σ2= gr0.
σ = (σ1, σ2)
e(g0, σ1) = e(g0, κ grM)=e(g0, κ) e(g0, gr M )= e(g0, g0, g1
s0) e(g0r, gM) = e(u, g1)e(σ2, gM).
D → (C, R)
D-C
D = C + R
α=C XOR key and β = R XOR
Key.
The signature (σ) for the (message) M is verified with
the params and the top cloud’s Identity (TC). Where,
it requires confirmation from
e(g0, σ1) = e(u, g1)e(σ2, gM).
This method helps to effectively
secure the sensitive data, of n
number of users.
Security is comparatively low. High security is increased.
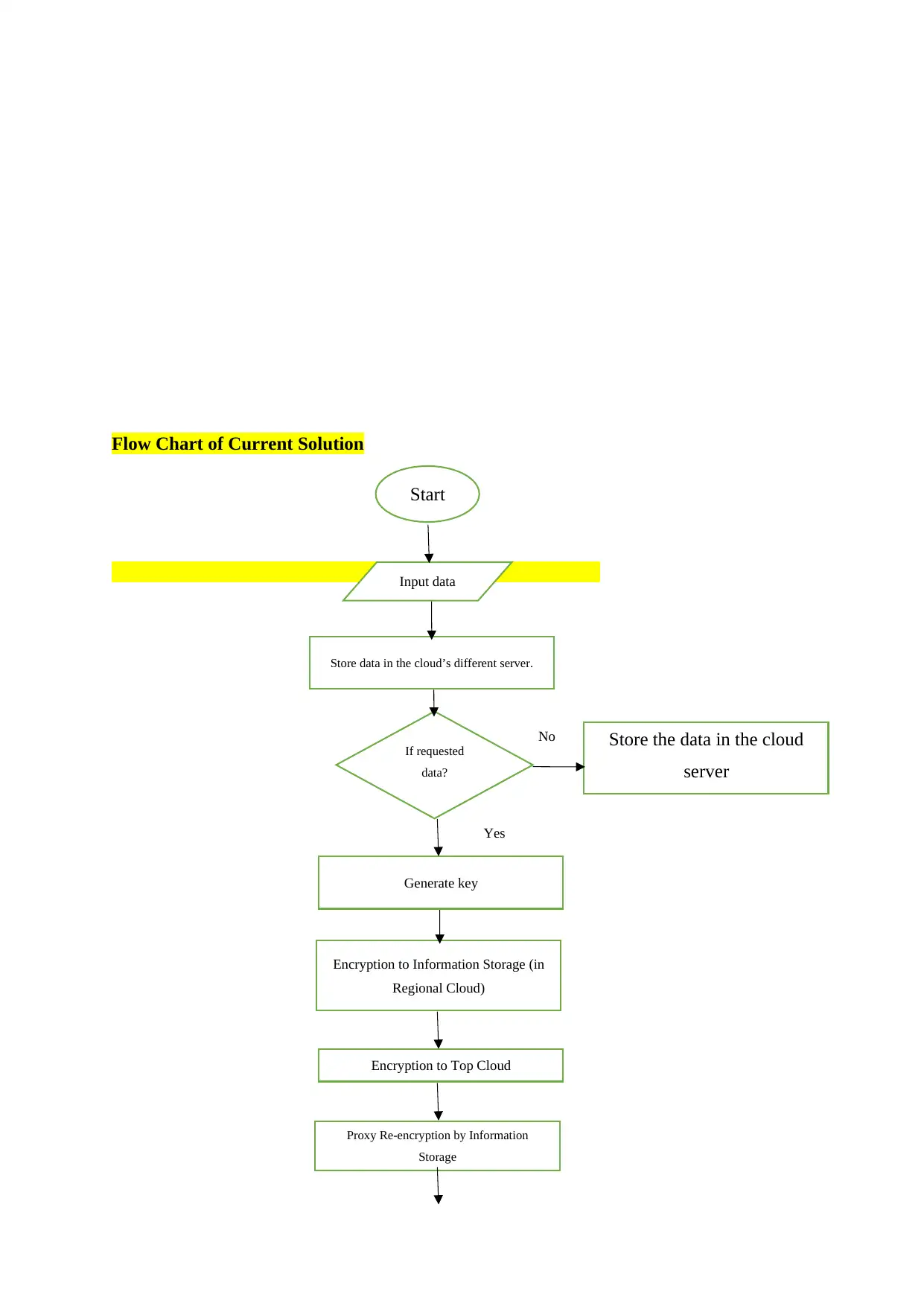
Flow Chart of Current Solution
Start
Input data
Store data in the cloud’s different server.
If requested
data?
yes
No
Generate key
Store the data in the cloud
server
Encryption to Information Storage (in
Regional Cloud)
Encryption to Top Cloud
Proxy Re-encryption by Information
Storage
Yes
Start
Input data
Store data in the cloud’s different server.
If requested
data?
yes
No
Generate key
Store the data in the cloud
server
Encryption to Information Storage (in
Regional Cloud)
Encryption to Top Cloud
Proxy Re-encryption by Information
Storage
Yes
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



