DAS Cloud Computing: Privacy and Data Protection Analysis
VerifiedAdded on 2022/09/18
|34
|2951
|30
Report
AI Summary
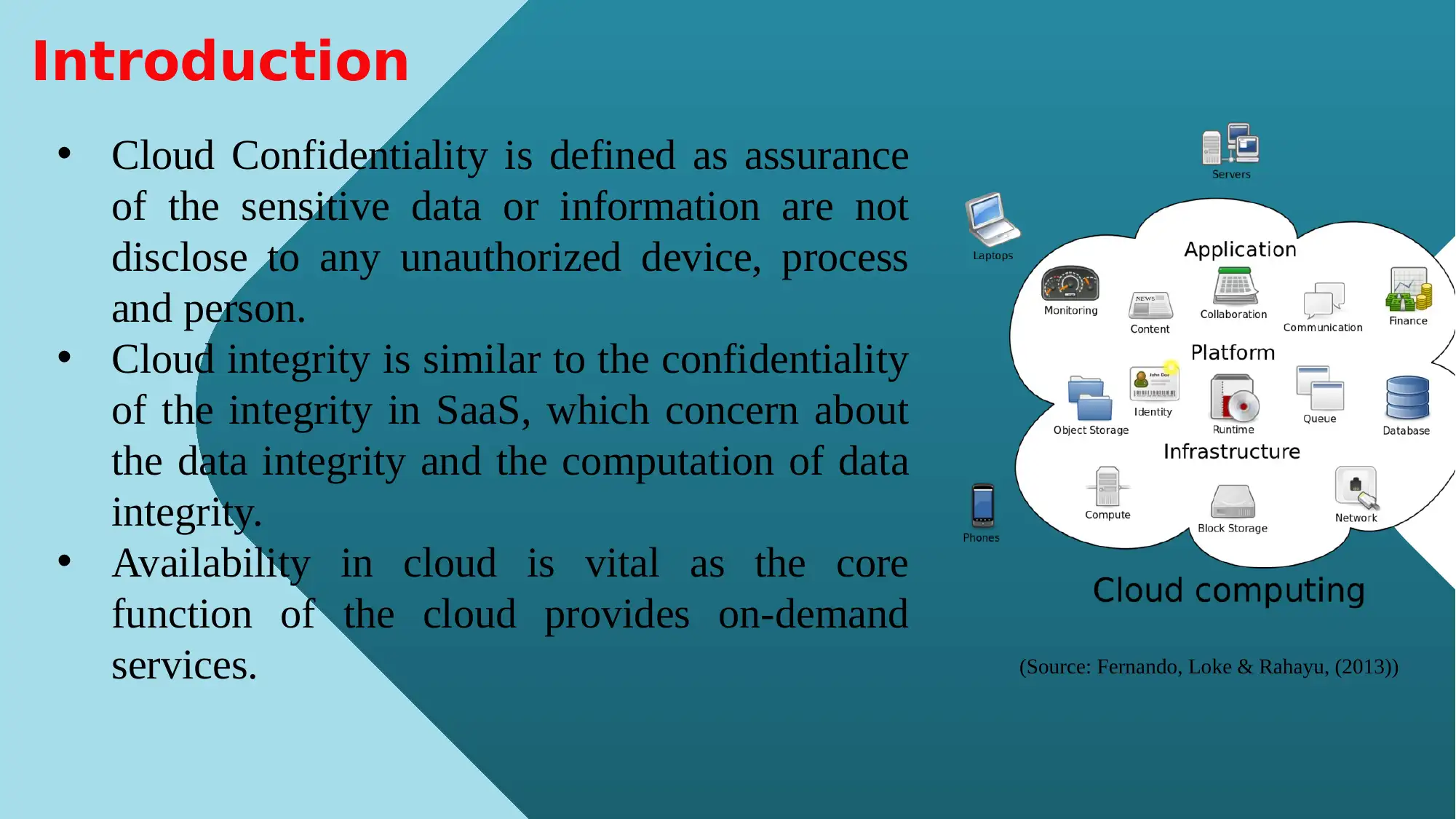
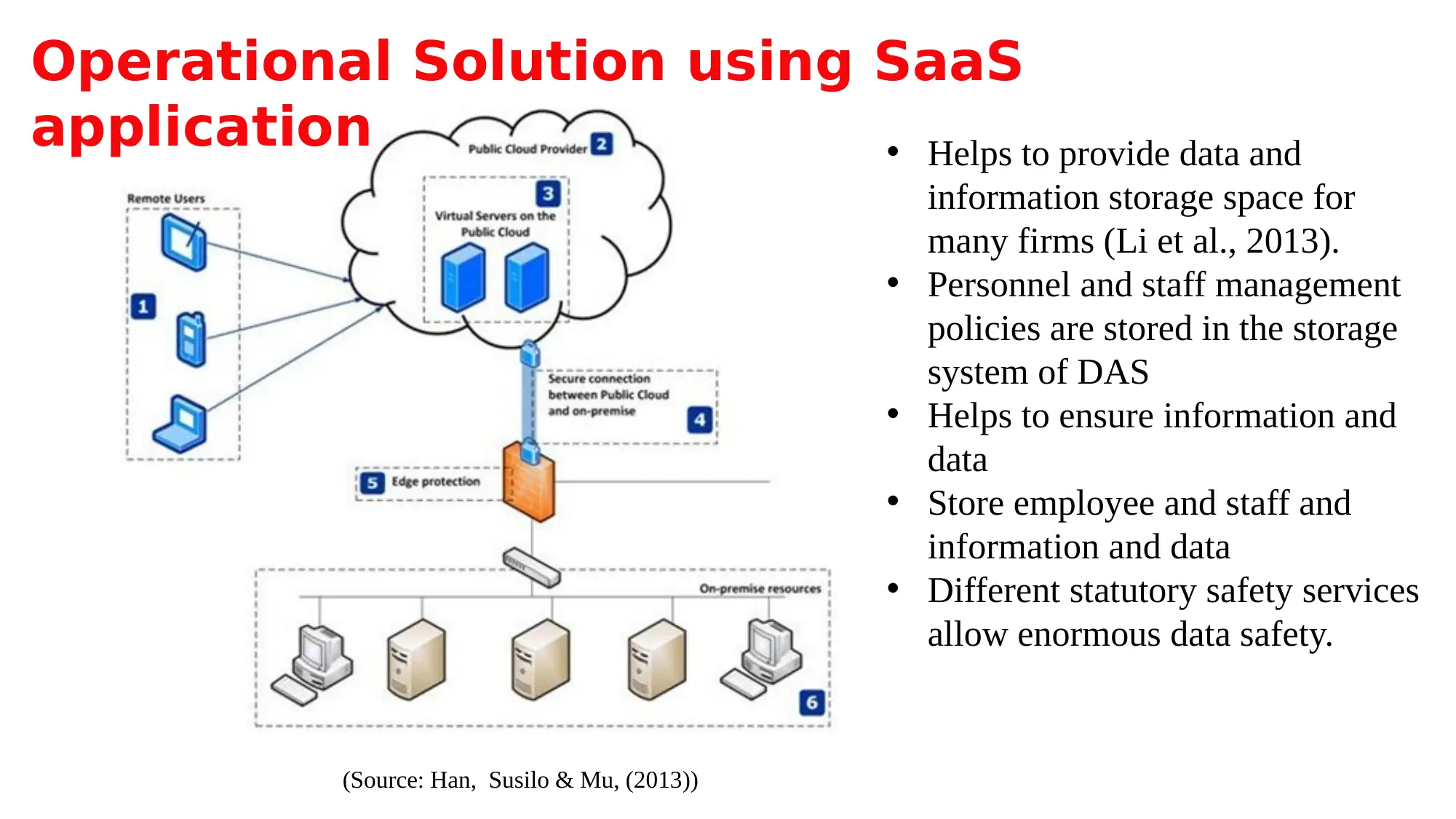
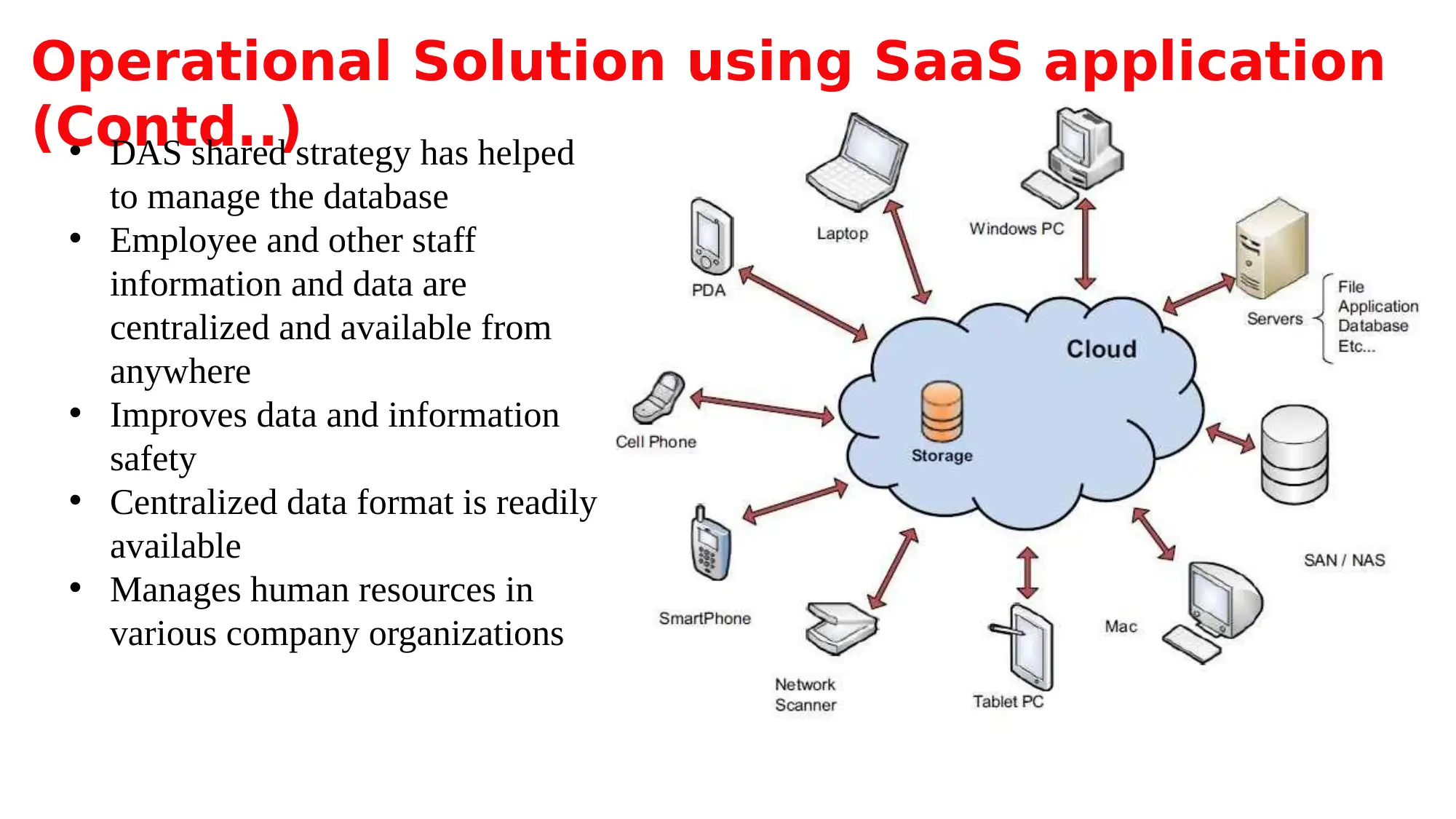
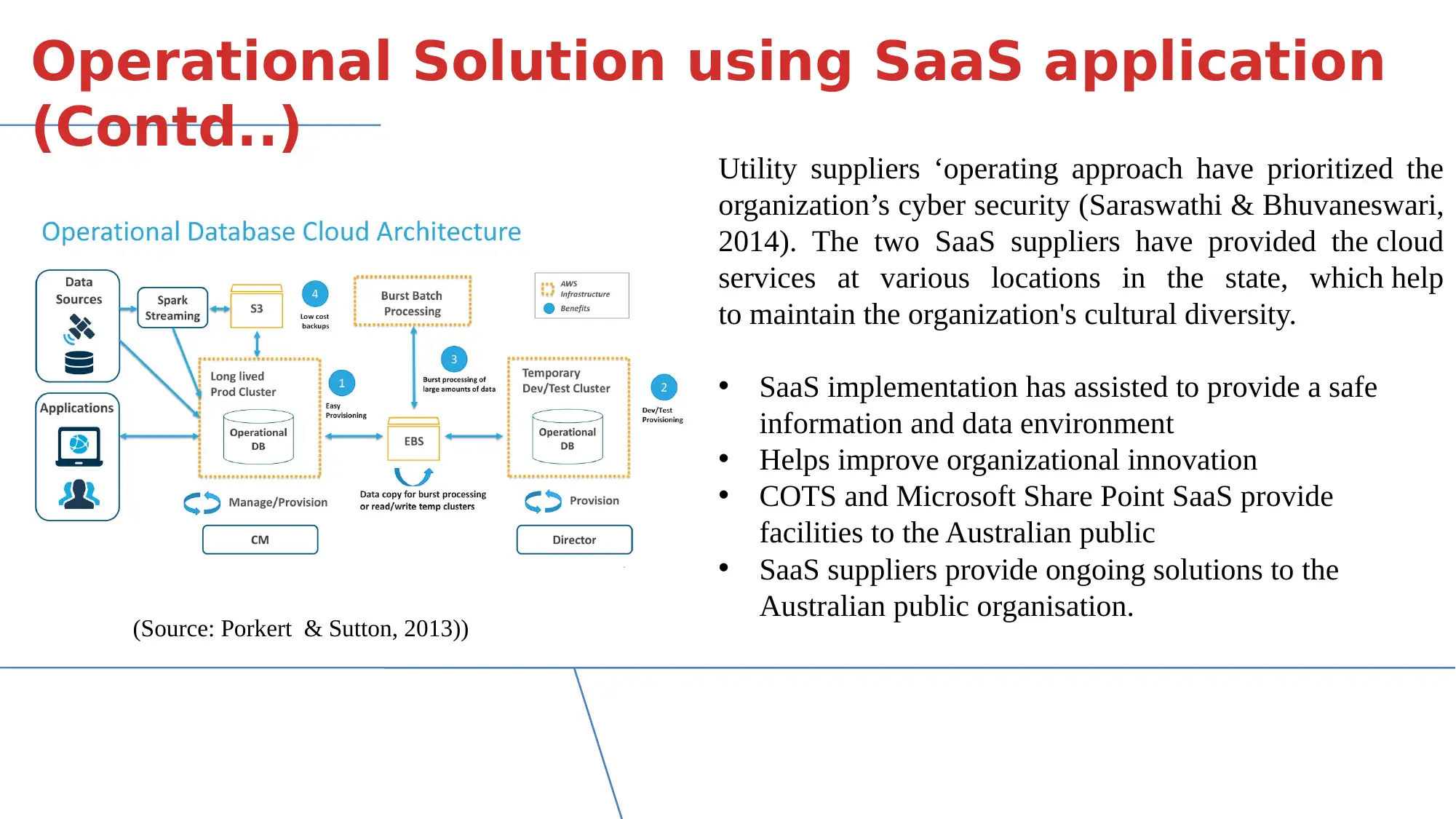
This report analyzes the privacy and data protection challenges associated with the Department of Administrative Services (DAS) migration to a cloud-based SaaS HR and personnel management system. It examines the concepts of cloud confidentiality, integrity, and availability, highlighting how SaaS solutions can provide data and information storage. The report details operational solutions using SaaS applications, including personnel management and data centralization. It identifies security risks, such as privilege abuse, malware, and input injection, and explores the implications of these threats on employee data. The document also discusses operational solutions for security and privacy, including digital identity, data sensitivity, and security implications for DAS, such as identity management and encryption. Furthermore, it addresses data sovereignty and the issues of data sensitivity, providing recommendations for SaaS providers to ensure data security and client guarantees. The report concludes by emphasizing the importance of risk and threat management in cloud environments, particularly within the context of SaaS applications and government services.
1 out of 34












![[object Object]](/_next/static/media/star-bottom.7253800d.svg)