Cloud Computing Security Solution: Emerging Technologies & Innovation
VerifiedAdded on 2023/06/04
|14
|694
|187
Report
AI Summary
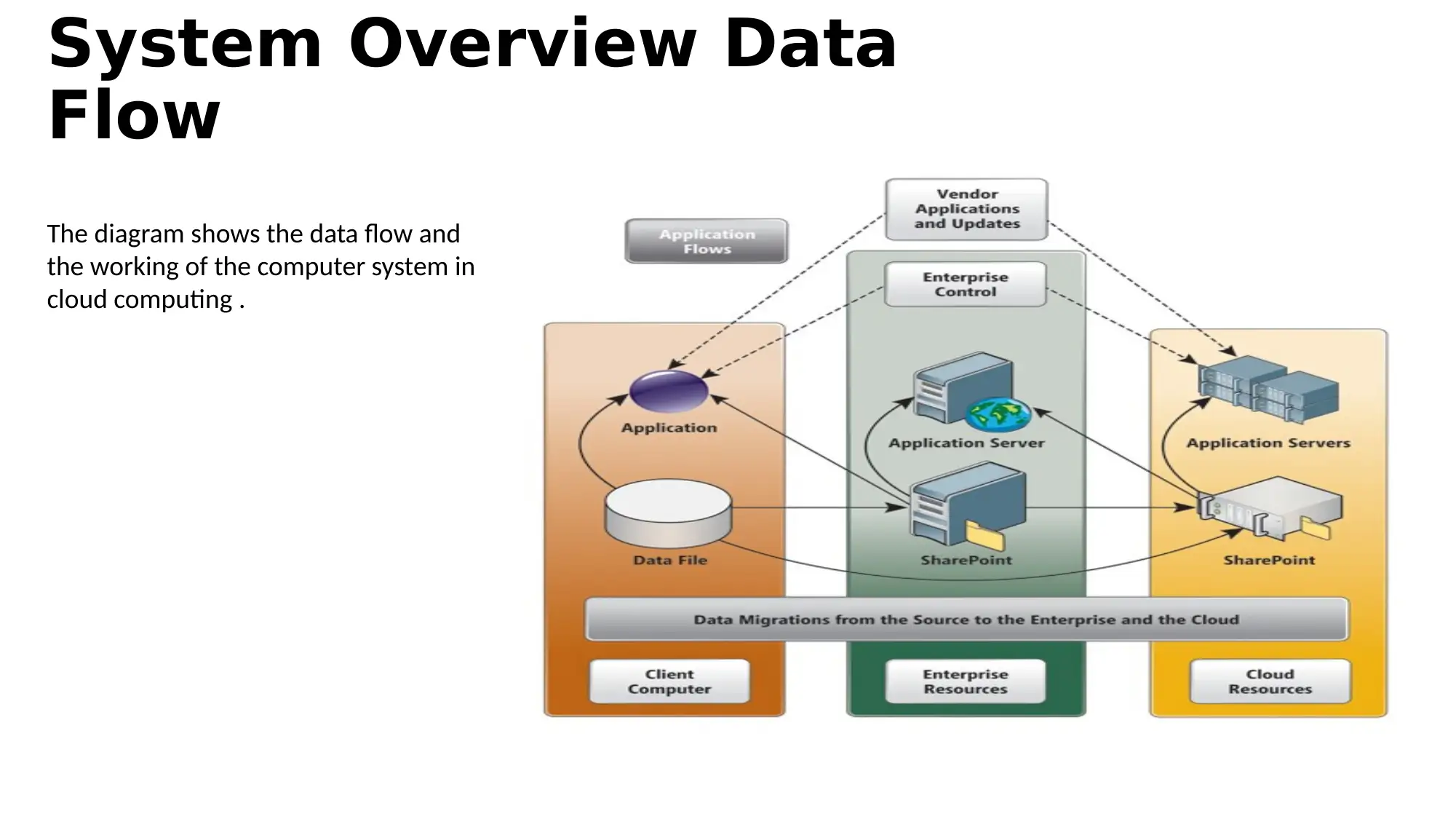
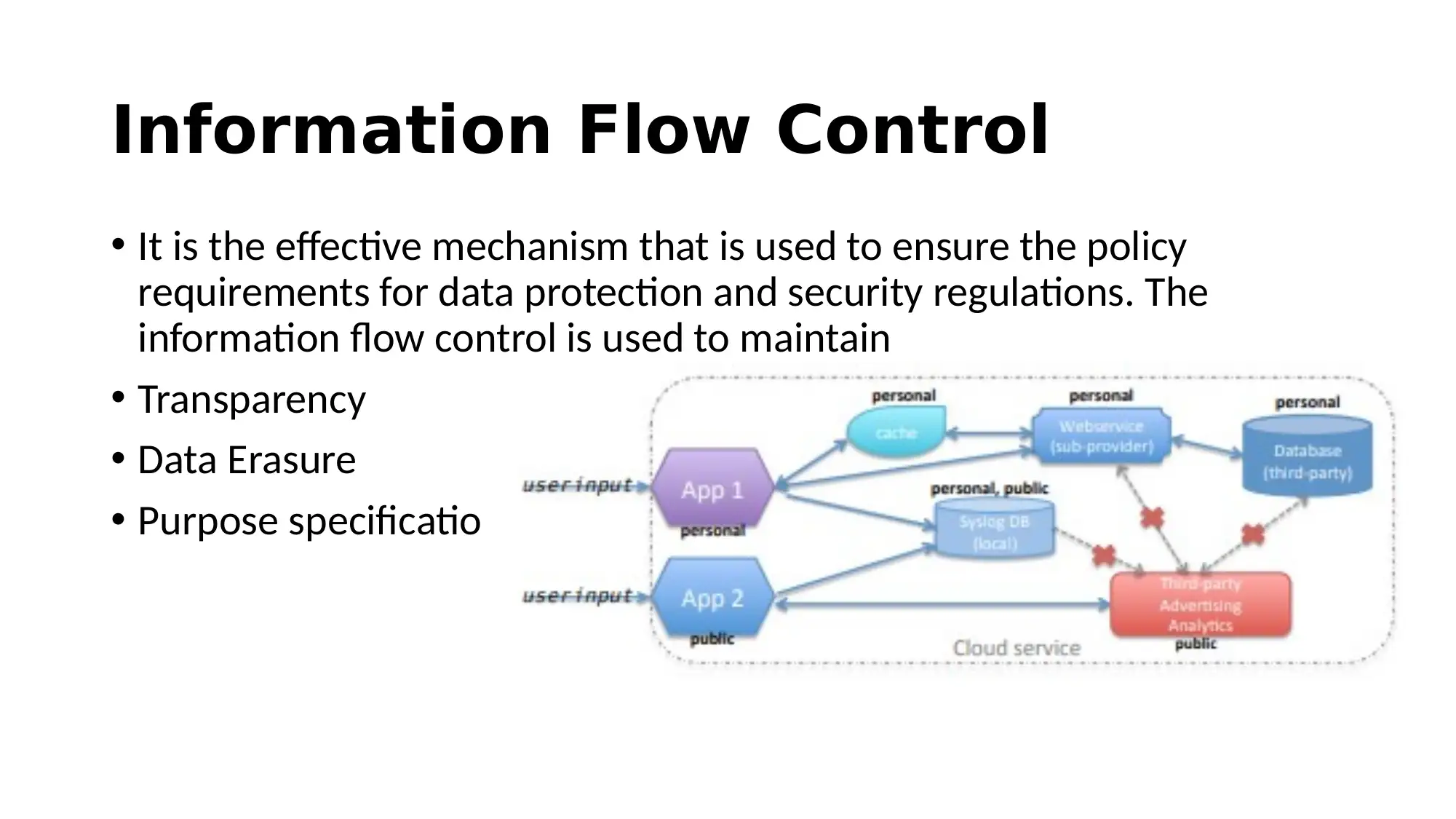
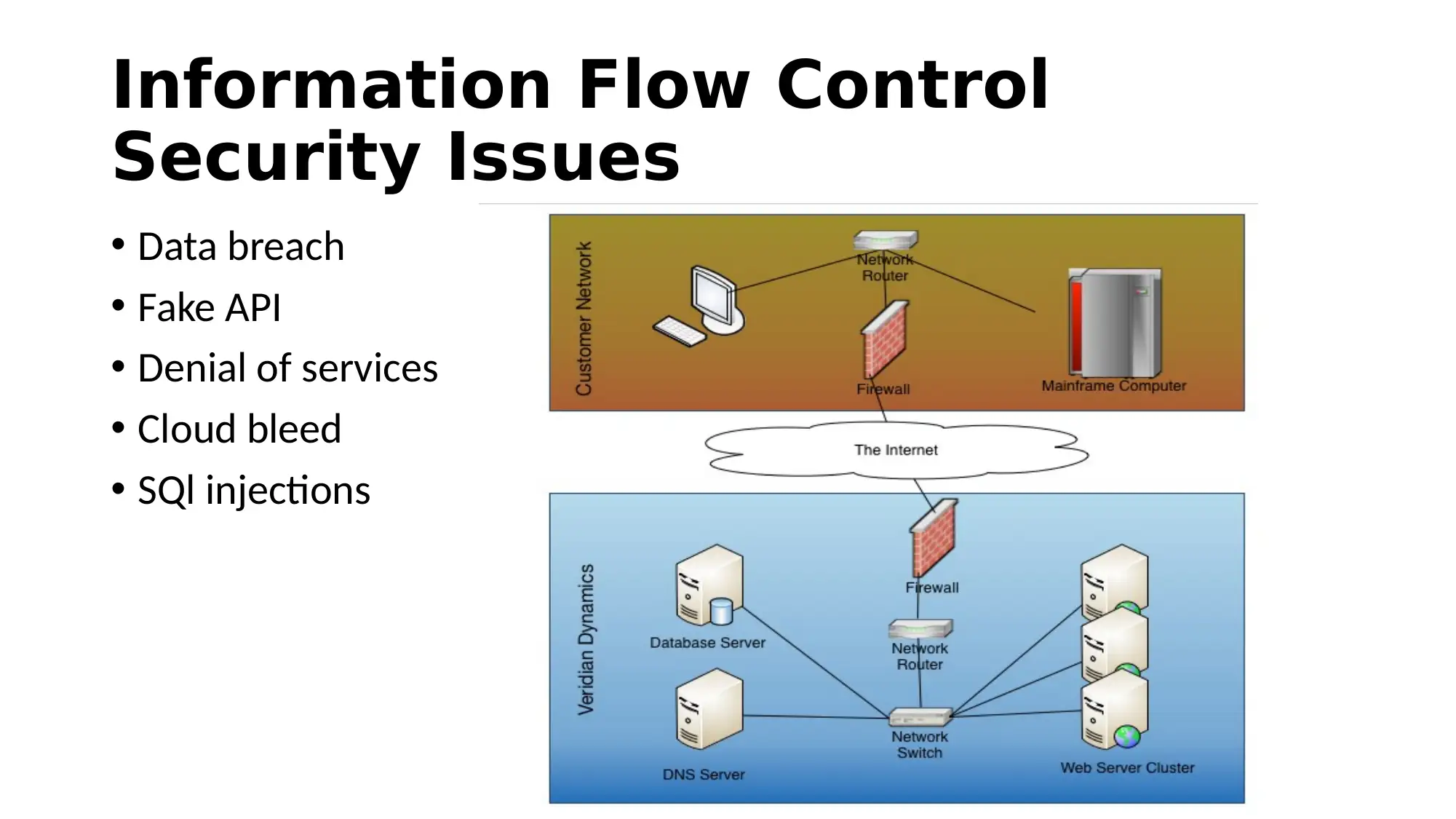
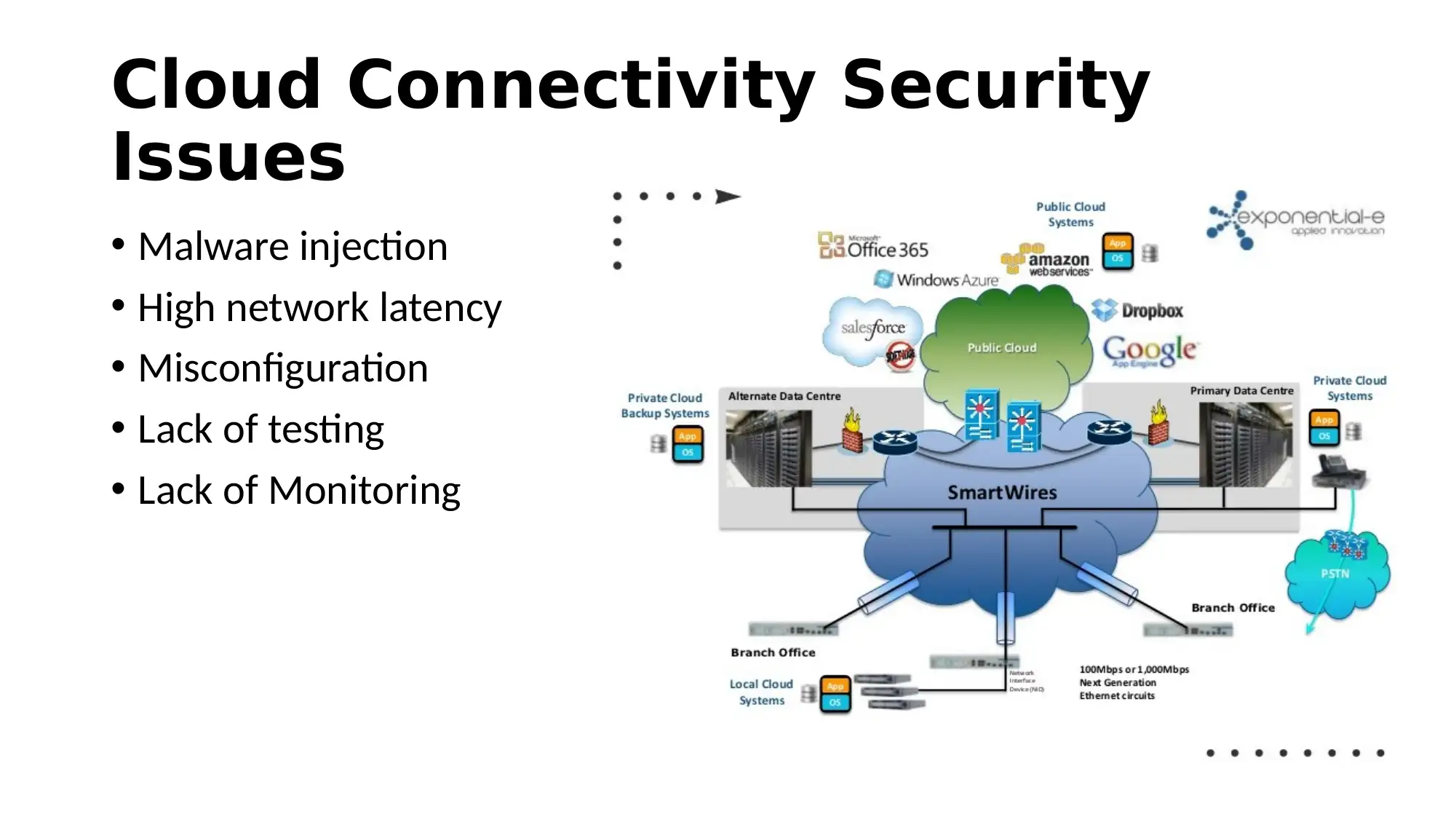
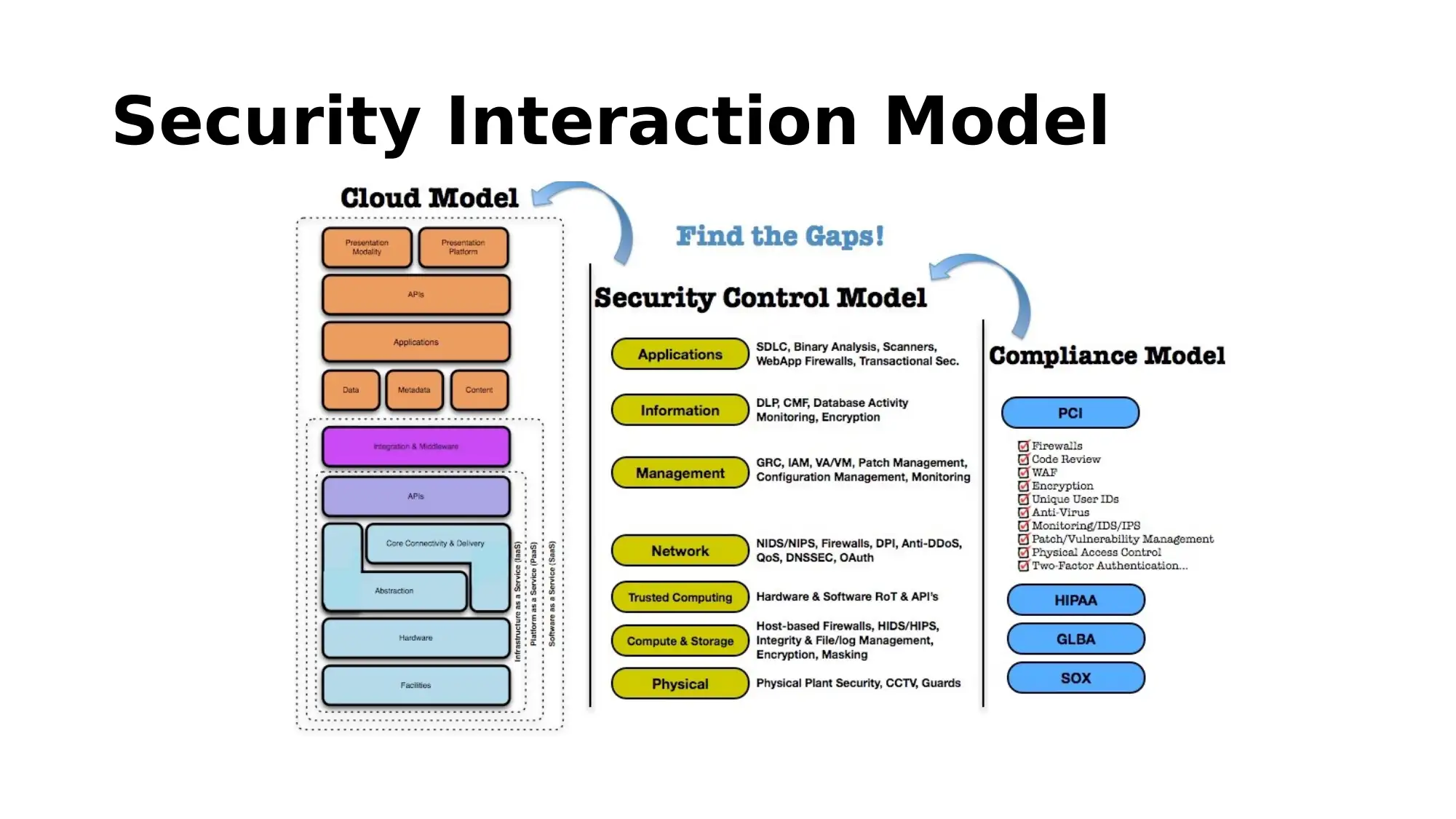
This report provides an overview of cloud-based security solutions, analyzing security issues in cloud computing derived from recent research. It highlights the basic services cloud computing offers, the threats it faces, and proposed solutions to minimize these issues. The report emphasizes the importance of information control and connectivity, discussing security issues such as data breaches, fake APIs, and malware injection. Proposed solutions include operational and organizational security measures, data security strategies, threat evasion techniques, safe access protocols, and privacy enhancements, exemplified by Google's security practices. The conclusion underscores the significance of the overall analysis in addressing security challenges in cloud computing.
1 out of 14











![[object Object]](/_next/static/media/star-bottom.7253800d.svg)