Cloud Security Research Project Proposal: Infrastructure Costs
VerifiedAdded on 2022/12/27
|8
|2375
|1
Project
AI Summary
This research project proposal examines the critical issue of cloud security and its potential impact on infrastructure costs. The proposal begins with an introduction to cloud computing, highlighting its benefits such as scalability and cost-effectiveness, while also acknowledging the associated security risks. The research background provides context, referencing existing literature on cloud security from various perspectives, including architecture and stakeholder viewpoints. The research problem focuses on how improper cloud security can lead to significant infrastructure costs, including data breaches, malicious insiders, and denial-of-service attacks. The methodology involves online research, keyword searches, and analysis of existing literature, with potential outreach to IT companies for insights. The significance of the research lies in its potential to help organizations mitigate risks and prevent financial losses related to cloud computing. The proposal outlines various security threats, including insecure APIs, malicious insiders, shared resources, and data breaches. The conclusion emphasizes the importance of client organizations investing in their operating system and software security and implementing mechanisms to mitigate cloud security risks. Finally, a research planning timeline is included to outline the project's activities and milestones.

Cloud Security Research Project Proposal1
Cloud Security Research Project Proposal
By Name
Course
Instructor
Institution
Location
Date
Cloud Security Research Project Proposal
By Name
Course
Instructor
Institution
Location
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cloud Security Research Project Proposal2
Table of Contents
1.0 Introduction................................................................................................................................3
1.1 Research Background................................................................................................................3
1.2 Research Problem......................................................................................................................4
1.3 Research Methodology..............................................................................................................4
1.4 Research Significance................................................................................................................4
1.5 Conclusion and Recommendation.............................................................................................6
1.6 Research Planning.....................................................................................................................7
Bibliography....................................................................................................................................8
Table of Contents
1.0 Introduction................................................................................................................................3
1.1 Research Background................................................................................................................3
1.2 Research Problem......................................................................................................................4
1.3 Research Methodology..............................................................................................................4
1.4 Research Significance................................................................................................................4
1.5 Conclusion and Recommendation.............................................................................................6
1.6 Research Planning.....................................................................................................................7
Bibliography....................................................................................................................................8

Cloud Security Research Project Proposal3
Improper Cloud Security Can Lead To Unnecessary Infrastructure Cost
1.0 Introduction
In the contemporary world, organizations are shifting from the on-premise computing model to a
cloud-based model. Cloud computing model involves using a network of remote servers that are
hosted on the internet to collect, manage, store and process data instead of using local servers or
a personal computer. The shift to cloud computing is attributed to its several benefits such as
improved flexibility and scalability, lower cost and on-demand provisioning, (Botta, De Donato,
W., Persico, and Pescapé, 2016, pp. 685). Cloud computing enables organizations to deliver
mission-critical applications without necessarily having to install expensive dedicated hardware
infrastructure behind the corporate firewall. Cloud computing also allows employees to work
from any location as long as they are connected to the internet and this has increased employee
flexibility and productivity. As much as cloud computing is associated with so many benefits, it
comes along with security risks that can bring down an organization. This research proposal is on
how improper cloud security can lead to infrastructure cost and the mechanisms that can be put
in place to minimize the risks.
1.1 Research Background
The security concern has raised a lot of uncertainty on the adoption of cloud computing. Several
researchers and scientists have made their contribution to the concept of cloud security.
According to Almorsy, Grundy, and Müller, 2016, cloud computing is a complex issue since this
model has introduced new dimensions and scopes due to the model architecture, its elasticity,
dependency stack as well as its multi-tenancy. The authors of this book provide a detailed
analysis of cloud computing security from various scopes such as cloud architecture,
stakeholder's perspectives as well as cloud service delivery perspective.
In "Cloud computing: implementation, management, and security," by Rittinghouse and
Ransome the background and evolution to cloud computing are discussed in details. In chapter
six of this book, the authors explicitly tackle the issue of cloud security and how to manage the
security threats that arise due to the cloud –computing models. The authors have used several
data collection methods including surveys and analysis to determine how improper cloud
security could lead to enormous infrastructure cost. The book also discusses the philosophical
and legal aspects of cloud computing as well as narrate the story of successful vendors who have
made a fortune in the cloud computing sector despite the security threat.
The research on cloud computing is significant since they provide the background data on which
further research can look into and improve on the cloud computing security concern. The
literature on improper cloud computing security helps people to have a deep understanding of
cloud computing hence promote the adoption of this technology in many modern organizations.
The main objective of this research is to understand the cloud computing security risks and
Improper Cloud Security Can Lead To Unnecessary Infrastructure Cost
1.0 Introduction
In the contemporary world, organizations are shifting from the on-premise computing model to a
cloud-based model. Cloud computing model involves using a network of remote servers that are
hosted on the internet to collect, manage, store and process data instead of using local servers or
a personal computer. The shift to cloud computing is attributed to its several benefits such as
improved flexibility and scalability, lower cost and on-demand provisioning, (Botta, De Donato,
W., Persico, and Pescapé, 2016, pp. 685). Cloud computing enables organizations to deliver
mission-critical applications without necessarily having to install expensive dedicated hardware
infrastructure behind the corporate firewall. Cloud computing also allows employees to work
from any location as long as they are connected to the internet and this has increased employee
flexibility and productivity. As much as cloud computing is associated with so many benefits, it
comes along with security risks that can bring down an organization. This research proposal is on
how improper cloud security can lead to infrastructure cost and the mechanisms that can be put
in place to minimize the risks.
1.1 Research Background
The security concern has raised a lot of uncertainty on the adoption of cloud computing. Several
researchers and scientists have made their contribution to the concept of cloud security.
According to Almorsy, Grundy, and Müller, 2016, cloud computing is a complex issue since this
model has introduced new dimensions and scopes due to the model architecture, its elasticity,
dependency stack as well as its multi-tenancy. The authors of this book provide a detailed
analysis of cloud computing security from various scopes such as cloud architecture,
stakeholder's perspectives as well as cloud service delivery perspective.
In "Cloud computing: implementation, management, and security," by Rittinghouse and
Ransome the background and evolution to cloud computing are discussed in details. In chapter
six of this book, the authors explicitly tackle the issue of cloud security and how to manage the
security threats that arise due to the cloud –computing models. The authors have used several
data collection methods including surveys and analysis to determine how improper cloud
security could lead to enormous infrastructure cost. The book also discusses the philosophical
and legal aspects of cloud computing as well as narrate the story of successful vendors who have
made a fortune in the cloud computing sector despite the security threat.
The research on cloud computing is significant since they provide the background data on which
further research can look into and improve on the cloud computing security concern. The
literature on improper cloud computing security helps people to have a deep understanding of
cloud computing hence promote the adoption of this technology in many modern organizations.
The main objective of this research is to understand the cloud computing security risks and
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Cloud Security Research Project Proposal4
determine the most appropriate mechanisms that can be used to prevent an organization from
incurring substantial infrastructure costs.
1.2 Research Problem
So many new organizations would like to embrace cloud computing, but the security risks are a
threat to this ambition. Cloud computing can lead to leaking of very crucial client information as
well as strategic information that helps an organization to sustain the competitive advantage they
have over their competitors. In this contemporary world, clients are very much concerned about
the privacy of their data, and it is upon any business organization to ensure that they protect
client data. With the linking of various personal data in cloud computing, a breach in security can
lead to lawsuits that may see an organization incur huge losses. Also, there are individuals with
malicious intentions that may take advantage of the security loopholes to interfere with hardware
and software assets of an organization leading to infrastructure loss.
1.3 Research Methodology
The research is going to be conducted online with information collected over the internet. Cloud
security is a topic of concern, and there is a lot of available information published and reviewed
for enlightening people on cloud computing. The search for keywords such as cloud computing,
security risks, infrastructure costs in cloud computing will help in gathering a lot of information
on the topic. There a lot of articles and journals written specifically to address cloud security and
ways on how to mitigate the threats. Furthermore, several IT companies are willing to assist
students in understanding the topic; hence we can identify such organizations and visit them to
get assistance. We can plan to survey the organizations which have already adopted the cloud
computing model and see how they are benefiting from the model. We can look at the security
challenges they are facing and the mechanism put in place to handle the problems.
1.4 Research Significance
This research is fundamental since it can help organizations prevent the loss of millions of
dollars involved in the installation and maintenance of a local corporate network. Cloud
computing is a large area that includes platform –as- service (PaaS), infrastructure-as-a-service
(IaaS) and software-as-a-service (SaaS) but in this research, will concentrate on the
Infrastructure-as-a-service platform. This platform is where the cloud provider handles the IT
infrastructure, and the clients are virtually allowed to access them on demand. In this model, the
client organization does not have to purchase and manage hardware and data centers since this is
the responsibility of the cloud providers, (Martinez and Pulier, ServiceMesh Inc, 2015). This
means that a lot of sensitive organization data and information get into the hands of a third party;
hence the security concerns arise.
determine the most appropriate mechanisms that can be used to prevent an organization from
incurring substantial infrastructure costs.
1.2 Research Problem
So many new organizations would like to embrace cloud computing, but the security risks are a
threat to this ambition. Cloud computing can lead to leaking of very crucial client information as
well as strategic information that helps an organization to sustain the competitive advantage they
have over their competitors. In this contemporary world, clients are very much concerned about
the privacy of their data, and it is upon any business organization to ensure that they protect
client data. With the linking of various personal data in cloud computing, a breach in security can
lead to lawsuits that may see an organization incur huge losses. Also, there are individuals with
malicious intentions that may take advantage of the security loopholes to interfere with hardware
and software assets of an organization leading to infrastructure loss.
1.3 Research Methodology
The research is going to be conducted online with information collected over the internet. Cloud
security is a topic of concern, and there is a lot of available information published and reviewed
for enlightening people on cloud computing. The search for keywords such as cloud computing,
security risks, infrastructure costs in cloud computing will help in gathering a lot of information
on the topic. There a lot of articles and journals written specifically to address cloud security and
ways on how to mitigate the threats. Furthermore, several IT companies are willing to assist
students in understanding the topic; hence we can identify such organizations and visit them to
get assistance. We can plan to survey the organizations which have already adopted the cloud
computing model and see how they are benefiting from the model. We can look at the security
challenges they are facing and the mechanism put in place to handle the problems.
1.4 Research Significance
This research is fundamental since it can help organizations prevent the loss of millions of
dollars involved in the installation and maintenance of a local corporate network. Cloud
computing is a large area that includes platform –as- service (PaaS), infrastructure-as-a-service
(IaaS) and software-as-a-service (SaaS) but in this research, will concentrate on the
Infrastructure-as-a-service platform. This platform is where the cloud provider handles the IT
infrastructure, and the clients are virtually allowed to access them on demand. In this model, the
client organization does not have to purchase and manage hardware and data centers since this is
the responsibility of the cloud providers, (Martinez and Pulier, ServiceMesh Inc, 2015). This
means that a lot of sensitive organization data and information get into the hands of a third party;
hence the security concerns arise.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cloud Security Research Project Proposal5
The software environment and the operating system is under the control of the client
organization. The organization having understood the security risks of cloud computing can
invest in securing its software and operating system through updates and patches. Having
control over the operating system and the software environment also enables the organization to
upgrade its operations in the event special applications and demands are required.
The research will determine the various scenarios of security threats involve in cloud computing
as opposed to traditional computing. These include insecure APIs, malicious insiders, shared
resources, data breach/loss, stolen credentials and denial of service. For an organization to
access the services of a cloud provider, they must be provided with APIs by the provider,
(Hussein and Khalid, 2016, pp. 150). Poorly implemented APIs have caused security issues, and
the cloud providers must continuously improve the APIs so that the client does not have to worry
about this. API bugs must be patched at the right time, and the users should be notified in
advance to prepare for any compatibility upgrade of their operating system.
As with an IT environment, there will always be the threat of malicious insiders in the system
and this threat has to be neutralized to safeguard sensitive data. Research shows that roughly
eight percent of data breaches are as a result of inside work, (Singh, Jeong, and Park, 2016, pp.
218). A malicious insider security threat involves internal administrators from the cloud provider
side to access client data, and they can steal it or manipulate maliciously. Full encryption of
cloud services may not be possible depending on the features of the cloud network; thus rogue
employees from the service provider could access sensitive client data.
Cloud computing environment usually involves sharing of resources among the many clients of
a service provider. RAM, GPUs, CPU cache, hard disks, and other shared hardware appliances
were designed without multitenant privacy considerations. Therefore, sharing of these resources
by multiple users expose them to the risk of data leakage. The entire cloud computing
infrastructure can be compromised due to the security vulnerability of core components in the
system such as the hypervisor. Denial of service may occur in the cloud computing if a client
uses all the offered cloud resources making others in the same section to get poor quality services
or no service at all, (Ali, Khan, and Vasilakos, 2015, pp. 380). Attackers can take advantage of
this and launch distributed denial-of-service (DDoS) attacks thus denying clients from accessing
crucial services, and this can bring losses to an organization.
Although cloud providers are continuously improving on their infrastructure, there is still a
possibility of data loss or breach. Data loss or leakage of information at the service provider side
can occur due to external attacks, hardware failure or unfortunate error handling procedures by
the service providers. This can cause organizations and their clients to lose vital data and
information that they entrusted the service provider to protect, (Chang, and Ramachandran, 2016,
pp. 150). Therefore, service providers must continuously assess their cloud computing
infrastructure to identify any loopholes in the system and rectify it before attackers realize the
gap.
The software environment and the operating system is under the control of the client
organization. The organization having understood the security risks of cloud computing can
invest in securing its software and operating system through updates and patches. Having
control over the operating system and the software environment also enables the organization to
upgrade its operations in the event special applications and demands are required.
The research will determine the various scenarios of security threats involve in cloud computing
as opposed to traditional computing. These include insecure APIs, malicious insiders, shared
resources, data breach/loss, stolen credentials and denial of service. For an organization to
access the services of a cloud provider, they must be provided with APIs by the provider,
(Hussein and Khalid, 2016, pp. 150). Poorly implemented APIs have caused security issues, and
the cloud providers must continuously improve the APIs so that the client does not have to worry
about this. API bugs must be patched at the right time, and the users should be notified in
advance to prepare for any compatibility upgrade of their operating system.
As with an IT environment, there will always be the threat of malicious insiders in the system
and this threat has to be neutralized to safeguard sensitive data. Research shows that roughly
eight percent of data breaches are as a result of inside work, (Singh, Jeong, and Park, 2016, pp.
218). A malicious insider security threat involves internal administrators from the cloud provider
side to access client data, and they can steal it or manipulate maliciously. Full encryption of
cloud services may not be possible depending on the features of the cloud network; thus rogue
employees from the service provider could access sensitive client data.
Cloud computing environment usually involves sharing of resources among the many clients of
a service provider. RAM, GPUs, CPU cache, hard disks, and other shared hardware appliances
were designed without multitenant privacy considerations. Therefore, sharing of these resources
by multiple users expose them to the risk of data leakage. The entire cloud computing
infrastructure can be compromised due to the security vulnerability of core components in the
system such as the hypervisor. Denial of service may occur in the cloud computing if a client
uses all the offered cloud resources making others in the same section to get poor quality services
or no service at all, (Ali, Khan, and Vasilakos, 2015, pp. 380). Attackers can take advantage of
this and launch distributed denial-of-service (DDoS) attacks thus denying clients from accessing
crucial services, and this can bring losses to an organization.
Although cloud providers are continuously improving on their infrastructure, there is still a
possibility of data loss or breach. Data loss or leakage of information at the service provider side
can occur due to external attacks, hardware failure or unfortunate error handling procedures by
the service providers. This can cause organizations and their clients to lose vital data and
information that they entrusted the service provider to protect, (Chang, and Ramachandran, 2016,
pp. 150). Therefore, service providers must continuously assess their cloud computing
infrastructure to identify any loopholes in the system and rectify it before attackers realize the
gap.

Cloud Security Research Project Proposal6
1.5 Conclusion and Recommendation
Cloud computing security risk is a significant issue that can cause considerable losses in an
organization. Apart from the technical security challenges, this has raised legal concerns among
stakeholders in this sector. The cloud computing network can make some clients use the resource
without knowing exactly where their information is stored and the country regulation of the host
service provider. Some countries have strict rules than others, and these regulations may have an
impact on the organizations utilizing the cloud resources located in these particular countries
with strict regulations.
Since the client resources have no or very little control over the provider infrastructure we
recommend that client organizations should invest on their operating system and software
environment security, a secure cloud experience starts at the client connection; thus
organizations should ensure they have put in place mechanisms that mitigate cloud security risks.
An organization must invest in systems that will ensure that their sensitive information reaches
the service providers safely. There are contract agreements before settling for any cloud
provider, and the organization should provide that the service provider proof complete protection
of the information sent to them through the cloud resources. They have to ensure that there is no
external attackers who can intercept of deviate the information submitted to the service provider.
Unsecured networks such as Wi-Fi can pose a threat to secure connection; thus organizations
should procure operating system with this security concern at the back of their minds.
Secondly, data security trumps infrastructure security. Instead of investing in the infrastructure
involved in cloud networking, organizations should focus on protecting the data itself. They can
spend in encryption technologies that will ensure that the data sent is not readable from the
service provider end or any other third party that may intercept the data during its transmission.
There are several additional security services such as tokenization which automatically generate
substitute values for sensitive data preventing it from leaving the provider servers. If an
organization ultimately secures its data, it will not be worried about any security threats arising
from the cloud provider end. A lot of research and inventions on securing data in cloud
computing are going on with the aim of improving the cloud experience.
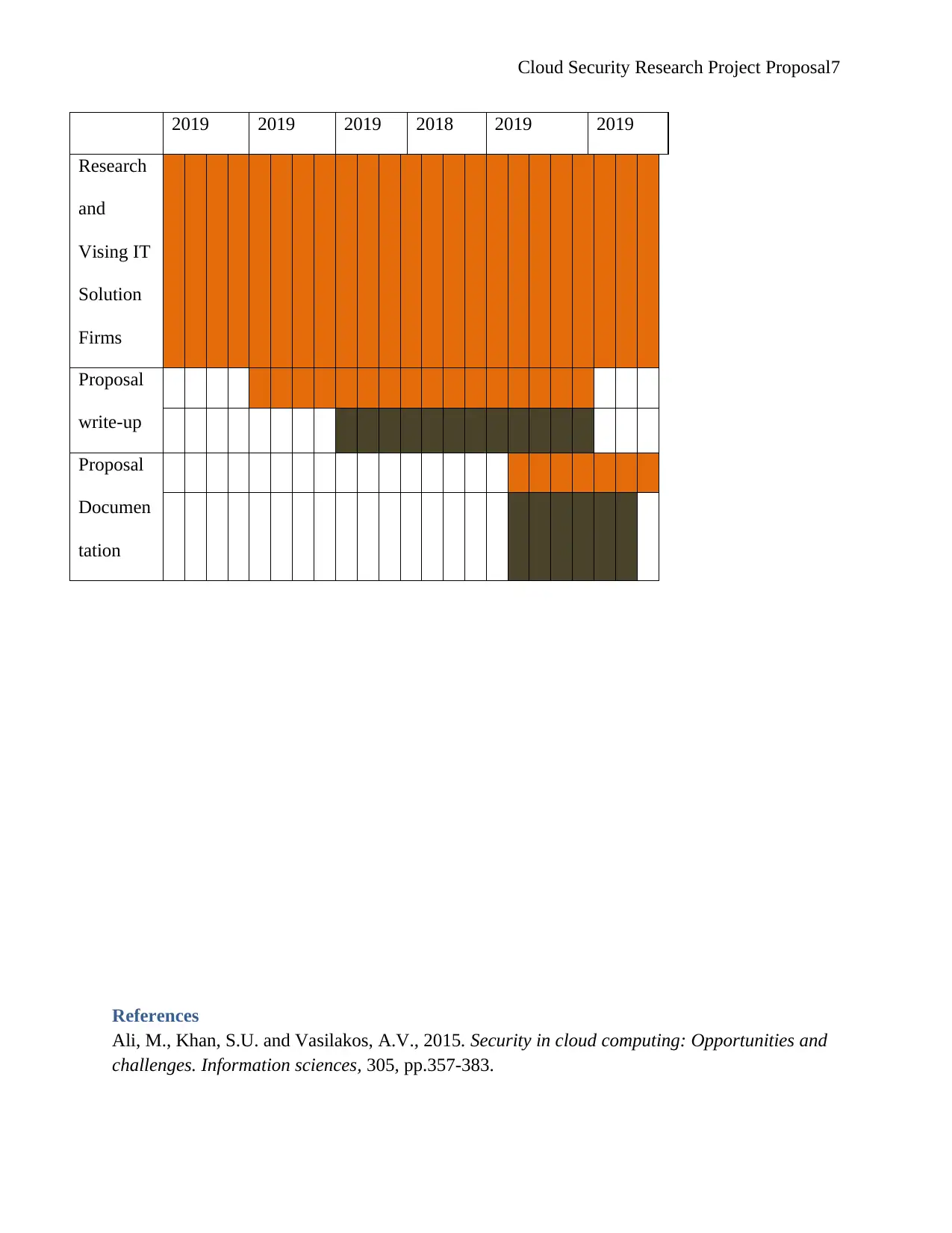
1.6 Research Planning
Activity May June July August September October
1.5 Conclusion and Recommendation
Cloud computing security risk is a significant issue that can cause considerable losses in an
organization. Apart from the technical security challenges, this has raised legal concerns among
stakeholders in this sector. The cloud computing network can make some clients use the resource
without knowing exactly where their information is stored and the country regulation of the host
service provider. Some countries have strict rules than others, and these regulations may have an
impact on the organizations utilizing the cloud resources located in these particular countries
with strict regulations.
Since the client resources have no or very little control over the provider infrastructure we
recommend that client organizations should invest on their operating system and software
environment security, a secure cloud experience starts at the client connection; thus
organizations should ensure they have put in place mechanisms that mitigate cloud security risks.
An organization must invest in systems that will ensure that their sensitive information reaches
the service providers safely. There are contract agreements before settling for any cloud
provider, and the organization should provide that the service provider proof complete protection
of the information sent to them through the cloud resources. They have to ensure that there is no
external attackers who can intercept of deviate the information submitted to the service provider.
Unsecured networks such as Wi-Fi can pose a threat to secure connection; thus organizations
should procure operating system with this security concern at the back of their minds.
Secondly, data security trumps infrastructure security. Instead of investing in the infrastructure
involved in cloud networking, organizations should focus on protecting the data itself. They can
spend in encryption technologies that will ensure that the data sent is not readable from the
service provider end or any other third party that may intercept the data during its transmission.
There are several additional security services such as tokenization which automatically generate
substitute values for sensitive data preventing it from leaving the provider servers. If an
organization ultimately secures its data, it will not be worried about any security threats arising
from the cloud provider end. A lot of research and inventions on securing data in cloud
computing are going on with the aim of improving the cloud experience.
1.6 Research Planning
Activity May June July August September October
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Cloud Security Research Project Proposal7
2019 2019 2019 2018 2019 2019
Research
and
Vising IT
Solution
Firms
Proposal
write-up
Proposal
Documen
tation
References
Ali, M., Khan, S.U. and Vasilakos, A.V., 2015. Security in cloud computing: Opportunities and
challenges. Information sciences, 305, pp.357-383.
2019 2019 2019 2018 2019 2019
Research
and
Vising IT
Solution
Firms
Proposal
write-up
Proposal
Documen
tation
References
Ali, M., Khan, S.U. and Vasilakos, A.V., 2015. Security in cloud computing: Opportunities and
challenges. Information sciences, 305, pp.357-383.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cloud Security Research Project Proposal8
Almorsy, M., Grundy, J. and Müller, I., 2016. An analysis of the cloud computing security
problem.1609.01107.
Botta, A., De Donato, W., Persico, V. and Pescapé, A., 2016. Integration of cloud computing and
internet of things: a survey. Future generation computer systems, 56, pp.684-700.
Chang, V. and Ramachandran, M., 2016. Towards achieving data security with the cloud
computing adoption framework. IEEE Transactions on Services Computing, 9(1), pp.138-151.
Hussein, N.H. and Khalid, A., 2016. A survey of cloud computing security challenges and
solutions. International Journal of Computer Science and Information Security, 14(1), p.52.
Martinez, F.R. and Pulier, E., ServiceMesh Inc, 2015. System and method for a cloud computing
abstraction layer with security zone facilities. U.S. Patent 9,069,599.
Rittinghouse, J.W. and Ransome, J.F., 2017. Cloud computing: implementation, management,
and security. CRC press.
Singh, S., Jeong, Y.S. and Park, J.H., 2016. A survey on cloud computing security: Issues,
threats, and solutions. Journal of Network and Computer Applications
Almorsy, M., Grundy, J. and Müller, I., 2016. An analysis of the cloud computing security
problem.1609.01107.
Botta, A., De Donato, W., Persico, V. and Pescapé, A., 2016. Integration of cloud computing and
internet of things: a survey. Future generation computer systems, 56, pp.684-700.
Chang, V. and Ramachandran, M., 2016. Towards achieving data security with the cloud
computing adoption framework. IEEE Transactions on Services Computing, 9(1), pp.138-151.
Hussein, N.H. and Khalid, A., 2016. A survey of cloud computing security challenges and
solutions. International Journal of Computer Science and Information Security, 14(1), p.52.
Martinez, F.R. and Pulier, E., ServiceMesh Inc, 2015. System and method for a cloud computing
abstraction layer with security zone facilities. U.S. Patent 9,069,599.
Rittinghouse, J.W. and Ransome, J.F., 2017. Cloud computing: implementation, management,
and security. CRC press.
Singh, S., Jeong, Y.S. and Park, J.H., 2016. A survey on cloud computing security: Issues,
threats, and solutions. Journal of Network and Computer Applications
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





