Cloud Infrastructure Security: Vulnerability Assessment and Strategy
VerifiedAdded on 2022/12/26
|12
|2270
|83
Report
AI Summary
This report provides a detailed analysis of cloud infrastructure security, addressing key challenges and proposing effective mitigation strategies. The report begins with a literature review of cloud infrastructure security challenges, including DDoS attacks, data breaches, data loss, and insecure access points. It then delves into a comprehensive risk analysis, including asset assessments and a risk register, identifying potential threats such as hackers, viruses, phishing, botnets, and DoS attacks. The report assesses the impact and probability of these risks, recommending controls such as network segmentation, network address translation, and intrusion detection systems. The document emphasizes the importance of proper awareness and communication of security threats for ensuring a secure cloud environment, and includes a list of relevant references.

Running head: CLOUD INFRASTRUCTURE SECURITY
CLOUD INFRASTRUCTURE SECURITY
Name of student
Name of university
Author’s note:
CLOUD INFRASTRUCTURE SECURITY
Name of student
Name of university
Author’s note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
CLOUD INFRASTRUCTURE SECURITY
Table of Contents
4. VULNERABILITY ASSESSMENT AND RISK MITIGATION STRATEGY......2
4.2 Risk Analysis.......................................................................................................4
4.2.1 Asset Assessment..............................................................................................4
4.2.2 Risk Assessment................................................................................................5
Risk register...............................................................................................................6
4.2.3 Recommended controls.....................................................................................8
References......................................................................................................................9
CLOUD INFRASTRUCTURE SECURITY
Table of Contents
4. VULNERABILITY ASSESSMENT AND RISK MITIGATION STRATEGY......2
4.2 Risk Analysis.......................................................................................................4
4.2.1 Asset Assessment..............................................................................................4
4.2.2 Risk Assessment................................................................................................5
Risk register...............................................................................................................6
4.2.3 Recommended controls.....................................................................................8
References......................................................................................................................9

2
CLOUD INFRASTRUCTURE SECURITY
4. VULNERABILITY ASSESSMENT AND RISK MITIGATION
STRATEGY
4.1 Cloud infrastructure security challenges literature review
In the present business environment there is the major intention of the protection of
the data and the applications that could be accessible from any of the devices (Ibrahim,
Hamlyn-Harris and Grundy 2016). It is significantly probable with the cloud technology but
there are some challenges to the implementation of the cloud technology in the organisations.
In the world where there is the major intent of development using the technology, the security
in the cloud is the major issue that must be considered and discussed from board level to all
the way down to the new employees (Madni, Latiff and Coulibaly 2016). Some of the cloud
infrastructure challenges could be categorised as:
DDoS attacks: As increasingly the businesses and the operation are shifting to the
cloud, the cloud providers are increasingly becoming the bigger target for the malicious
attacks. The attacks of the distributed denial of services are increasingly becoming common
than before. There have been reported several attacks by the IT services, the SaaS and the
cloud are the most often targeted industry in the recent times (Puthal et al. 2015). Any DDoS
attack is specifically designed for the overwhelming of the website servers for damaging the
network and not respond to the requests of the legitimate users. If any DDoS attack is
successful, it could lead to the rendering of the website not useful for couple of hours or even
several days. It could lead to the loss of the revenue, trust of the customers along with the
authority of the brand (Taleb 2014). Complementing cloud services with the protection from
the DDoS attack is not considered just the best practice for the organisation, it has grown to
be the necessity for the organisation (Sultan 2014). The websites and the web-based
application are the core components of the recent business market and it requires the
enhanced security measures.
CLOUD INFRASTRUCTURE SECURITY
4. VULNERABILITY ASSESSMENT AND RISK MITIGATION
STRATEGY
4.1 Cloud infrastructure security challenges literature review
In the present business environment there is the major intention of the protection of
the data and the applications that could be accessible from any of the devices (Ibrahim,
Hamlyn-Harris and Grundy 2016). It is significantly probable with the cloud technology but
there are some challenges to the implementation of the cloud technology in the organisations.
In the world where there is the major intent of development using the technology, the security
in the cloud is the major issue that must be considered and discussed from board level to all
the way down to the new employees (Madni, Latiff and Coulibaly 2016). Some of the cloud
infrastructure challenges could be categorised as:
DDoS attacks: As increasingly the businesses and the operation are shifting to the
cloud, the cloud providers are increasingly becoming the bigger target for the malicious
attacks. The attacks of the distributed denial of services are increasingly becoming common
than before. There have been reported several attacks by the IT services, the SaaS and the
cloud are the most often targeted industry in the recent times (Puthal et al. 2015). Any DDoS
attack is specifically designed for the overwhelming of the website servers for damaging the
network and not respond to the requests of the legitimate users. If any DDoS attack is
successful, it could lead to the rendering of the website not useful for couple of hours or even
several days. It could lead to the loss of the revenue, trust of the customers along with the
authority of the brand (Taleb 2014). Complementing cloud services with the protection from
the DDoS attack is not considered just the best practice for the organisation, it has grown to
be the necessity for the organisation (Sultan 2014). The websites and the web-based
application are the core components of the recent business market and it requires the
enhanced security measures.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
CLOUD INFRASTRUCTURE SECURITY
Data breaches: The known data breaches are increasing in number in the present
business world (Sadiku, Musa and Momoh 2014). This is the most endangered statistic and it
solely emphasised on the growing challenge for securing the sensitive and the confidential
data. Conventionally the IT professionals have the improved control over physical hardware
and the network infrastructure that are implemented for securing the proprietary data (Ali,
Khan and Vasilakos 2015). Within the cloud, several controls are relinquished to the trusted
partner. The selection of the appropriate vendor, with the robust record of the security is
essential for overcoming this specific challenge (Battula 2014).
Data loss: When the critical information has been migrated within the cloud, it is
predictable to be significantly connected with the security. The loss of the data from cloud,
either using the accidental deletion, the malicious tampering or the act of the nature damages
the cloud service provider, can be significantly disastrous for any enterprise business. Often
any DDoS attack is the only attack that is intended to create any diversion for the greater
threat, and this attempt could be used for deletion or stealing of the data (Rao and Selvamani
2015).
Insecure access points: The major benefit of the cloud technology implementation in
the organisation is the enhanced accessibility that is gained by the employees. The
information stored in the cloud could be accessed from anywhere with the availability of the
internet. There is the significant threat to the interfaces and the APIs that is used by the users
for interacting the cloud might not be secure with the proper mechanisms (Fortino et al.
2014). The hackers could discover the various kinds of the vulnerabilities and then exploit the
vulnerabilities. The behavioural web application firewall performs the examination of the
HTTP requests to any website to ensuring whether it is the authentic traffic. The always on
device assists in the protecting the web application from facing the security breaches (Singh
and Chana 2016).
CLOUD INFRASTRUCTURE SECURITY
Data breaches: The known data breaches are increasing in number in the present
business world (Sadiku, Musa and Momoh 2014). This is the most endangered statistic and it
solely emphasised on the growing challenge for securing the sensitive and the confidential
data. Conventionally the IT professionals have the improved control over physical hardware
and the network infrastructure that are implemented for securing the proprietary data (Ali,
Khan and Vasilakos 2015). Within the cloud, several controls are relinquished to the trusted
partner. The selection of the appropriate vendor, with the robust record of the security is
essential for overcoming this specific challenge (Battula 2014).
Data loss: When the critical information has been migrated within the cloud, it is
predictable to be significantly connected with the security. The loss of the data from cloud,
either using the accidental deletion, the malicious tampering or the act of the nature damages
the cloud service provider, can be significantly disastrous for any enterprise business. Often
any DDoS attack is the only attack that is intended to create any diversion for the greater
threat, and this attempt could be used for deletion or stealing of the data (Rao and Selvamani
2015).
Insecure access points: The major benefit of the cloud technology implementation in
the organisation is the enhanced accessibility that is gained by the employees. The
information stored in the cloud could be accessed from anywhere with the availability of the
internet. There is the significant threat to the interfaces and the APIs that is used by the users
for interacting the cloud might not be secure with the proper mechanisms (Fortino et al.
2014). The hackers could discover the various kinds of the vulnerabilities and then exploit the
vulnerabilities. The behavioural web application firewall performs the examination of the
HTTP requests to any website to ensuring whether it is the authentic traffic. The always on
device assists in the protecting the web application from facing the security breaches (Singh
and Chana 2016).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
CLOUD INFRASTRUCTURE SECURITY
Notification along with alerts: The proper awareness and the suitable communication
of the security threats is the major issue of the network that must be followed extensively for
ensuring the proper security of the cloud infrastructure. Alerting the suitable website or the
application managers in the situation when the infrastructure is facing some threat and the
threat has been identified must be the section of the well planned security plan (Biswas and
Giaffreda 2014). The robust mitigation of the threat depends on the clear and the prompt
communication for allowing the undertaking of the steps by the proper entities and the
minimisation of the impact of the threat.
4.2 Risk Analysis
4.2.1 Asset Assessment
The information assets of the organisation could be identified as the body of the
information that consists of significant financial value to the organisation. Some of the
information assets of the organisation are:
Content server
Authentication server
Web server
Database server
Application server
Mail server
4.2.2 Risk Assessment
Sl. no. Assets Impact Probability
CLOUD INFRASTRUCTURE SECURITY
Notification along with alerts: The proper awareness and the suitable communication
of the security threats is the major issue of the network that must be followed extensively for
ensuring the proper security of the cloud infrastructure. Alerting the suitable website or the
application managers in the situation when the infrastructure is facing some threat and the
threat has been identified must be the section of the well planned security plan (Biswas and
Giaffreda 2014). The robust mitigation of the threat depends on the clear and the prompt
communication for allowing the undertaking of the steps by the proper entities and the
minimisation of the impact of the threat.
4.2 Risk Analysis
4.2.1 Asset Assessment
The information assets of the organisation could be identified as the body of the
information that consists of significant financial value to the organisation. Some of the
information assets of the organisation are:
Content server
Authentication server
Web server
Database server
Application server
Mail server
4.2.2 Risk Assessment
Sl. no. Assets Impact Probability
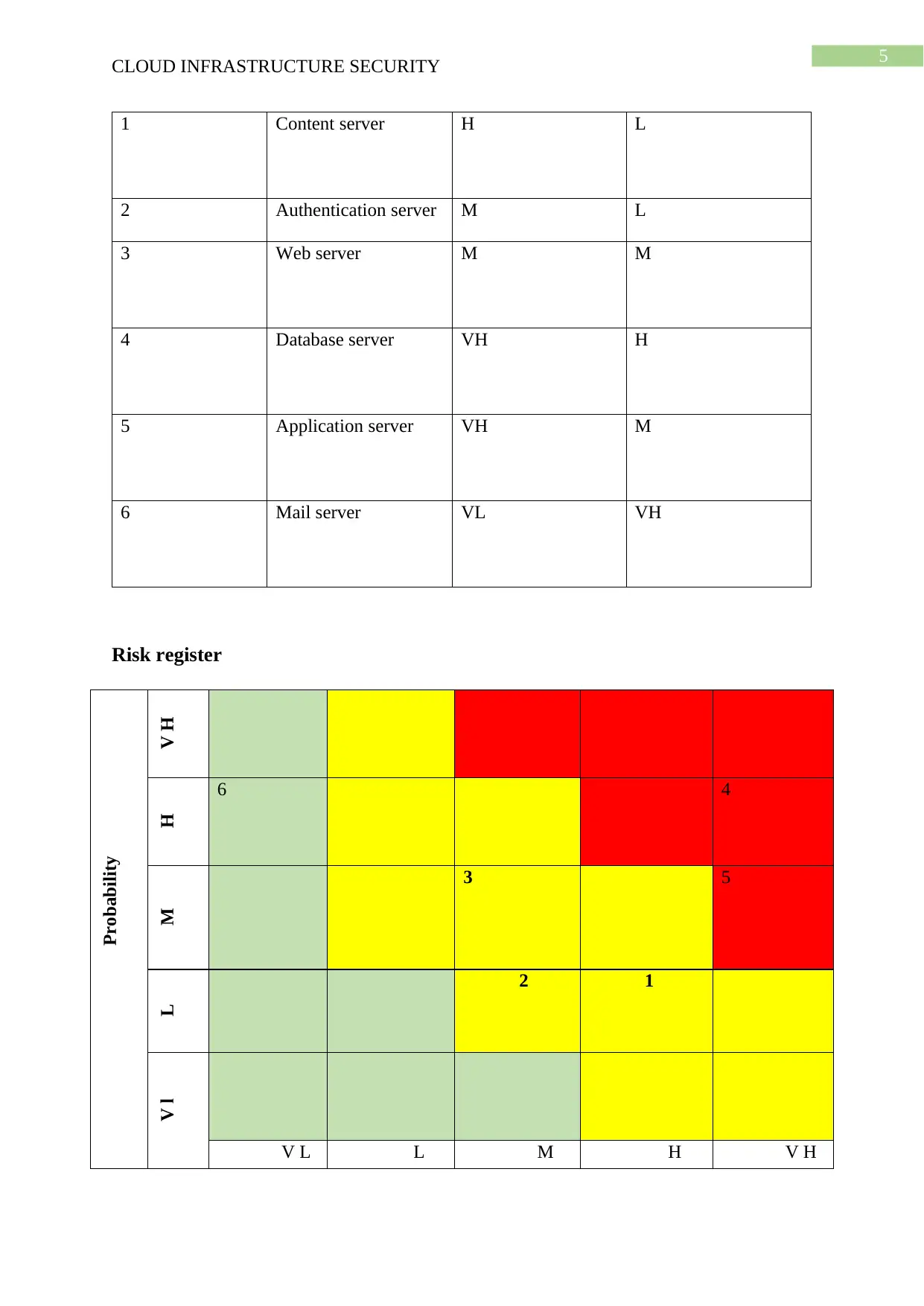
5
CLOUD INFRASTRUCTURE SECURITY
1 Content server H L
2 Authentication server M L
3 Web server M M
4 Database server VH H
5 Application server VH M
6 Mail server VL VH
Risk register
Probability
V HH
6 4
M
3 5
L 2 1
V l
V L L M H V H
CLOUD INFRASTRUCTURE SECURITY
1 Content server H L
2 Authentication server M L
3 Web server M M
4 Database server VH H
5 Application server VH M
6 Mail server VL VH
Risk register
Probability
V HH
6 4
M
3 5
L 2 1
V l
V L L M H V H
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
CLOUD INFRASTRUCTURE SECURITY
Impact
Some of the threats that could damage the assets of the organisation are:
Hackers: These are major threats to the assets of the organisation who could damage
the infrastructure as well as the assets of the organisation. majorly the businesses are being
targeted by the hackers for the financial gain. These particular predators majorly seek out the
opportunities for capitalising the vulnerabilities and they are the sole reason for the alerting
the organisational assets.
Viruses: The viruses could be significantly dangerous as they are significantly costly
and it could be executed in the organisational data whenever wished. Any virus is the piece of
the software that is created for damaging the computer and the assets of the organisation. This
program replicates then executes itself and interfering with manner by which the computer
operates. It could steal the data, corrupt the files and also delete the files that could be the
damaging threat for the businesses.
Phishing: The phishing scam tricks any internal user into offering the information like
the authentication credentials that could be later utilised for breaching the system of the
organisation. This particular information could be solicited from the employees using the
email and it could be disguised as the legitimate requests. As soon as the recipient provides
the sensitive information to the malicious user, the hacker gains access to the materials that
are required by them for seizing, stealing or even compromising the critical data of the
company. several phishing methods utilise the keyloggers in the combination with the
sophisticated tracking the components for targeting the particular information and the specific
organisation. There are several spear phishing emails that leads to the tiny piece of the
CLOUD INFRASTRUCTURE SECURITY
Impact
Some of the threats that could damage the assets of the organisation are:
Hackers: These are major threats to the assets of the organisation who could damage
the infrastructure as well as the assets of the organisation. majorly the businesses are being
targeted by the hackers for the financial gain. These particular predators majorly seek out the
opportunities for capitalising the vulnerabilities and they are the sole reason for the alerting
the organisational assets.
Viruses: The viruses could be significantly dangerous as they are significantly costly
and it could be executed in the organisational data whenever wished. Any virus is the piece of
the software that is created for damaging the computer and the assets of the organisation. This
program replicates then executes itself and interfering with manner by which the computer
operates. It could steal the data, corrupt the files and also delete the files that could be the
damaging threat for the businesses.
Phishing: The phishing scam tricks any internal user into offering the information like
the authentication credentials that could be later utilised for breaching the system of the
organisation. This particular information could be solicited from the employees using the
email and it could be disguised as the legitimate requests. As soon as the recipient provides
the sensitive information to the malicious user, the hacker gains access to the materials that
are required by them for seizing, stealing or even compromising the critical data of the
company. several phishing methods utilise the keyloggers in the combination with the
sophisticated tracking the components for targeting the particular information and the specific
organisation. There are several spear phishing emails that leads to the tiny piece of the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
CLOUD INFRASTRUCTURE SECURITY
malware that might be downloaded in the computer of the user without the proper knowledge
and it then unleashes the network breach that might go undetected for the long time period.
Botnets: The botnets could be utilised by the hackers for executing the several attacks
ranging from the targeting attacks to the servers to the running of email campaigns. As the
botnets commonly includes the several computers, several businesses discover it as
significantly difficult in stopping the botnet attacks. Commonly the computer security threat
might be deployed by any botmaster, who is the sole person of commanding the numerous
bots or the compromised computers for executing the malicious activities on the internet
connection. The combination of the infected malicious are frequently referred as the zombie
army that executes the ill intent of botmaster.
DoS attacks: In any DoS attack, the website or the web service of the company could
be rendered as significantly unusable and unavailable for the users. Frequently, the attacks of
the DoS are utilised against the businesses for the blackmail or the ransom purposes. This
method of the attack is then developed into the DDoS attacks that renders the network of the
organisation as useless for significant amount of time. With the successful execution of the
DoS attack, the network of the organisation could be rendered useless and it allows the
hackers to easily penetrate into the network of the organisation and steal the data.
4.2.3 Recommended controls
Implementation of the network segmentation and the deploying of the firewalls: The
network segmentation consists of the classification and the categorisation of the IT assets,
personnel and the data in the particular groups and then limiting the access to the specific
groups. By the implementation of the resources in the various areas of the network, the
comprising of the data or any sector could not translate into the exploitation of the complete
system.
CLOUD INFRASTRUCTURE SECURITY
malware that might be downloaded in the computer of the user without the proper knowledge
and it then unleashes the network breach that might go undetected for the long time period.
Botnets: The botnets could be utilised by the hackers for executing the several attacks
ranging from the targeting attacks to the servers to the running of email campaigns. As the
botnets commonly includes the several computers, several businesses discover it as
significantly difficult in stopping the botnet attacks. Commonly the computer security threat
might be deployed by any botmaster, who is the sole person of commanding the numerous
bots or the compromised computers for executing the malicious activities on the internet
connection. The combination of the infected malicious are frequently referred as the zombie
army that executes the ill intent of botmaster.
DoS attacks: In any DoS attack, the website or the web service of the company could
be rendered as significantly unusable and unavailable for the users. Frequently, the attacks of
the DoS are utilised against the businesses for the blackmail or the ransom purposes. This
method of the attack is then developed into the DDoS attacks that renders the network of the
organisation as useless for significant amount of time. With the successful execution of the
DoS attack, the network of the organisation could be rendered useless and it allows the
hackers to easily penetrate into the network of the organisation and steal the data.
4.2.3 Recommended controls
Implementation of the network segmentation and the deploying of the firewalls: The
network segmentation consists of the classification and the categorisation of the IT assets,
personnel and the data in the particular groups and then limiting the access to the specific
groups. By the implementation of the resources in the various areas of the network, the
comprising of the data or any sector could not translate into the exploitation of the complete
system.

8
CLOUD INFRASTRUCTURE SECURITY
Network address translation: This method is also known as the NAT that is the
technique of the remapping of one of the IP address space within any other by the
modification of the information of the network address in IP header of the packers while
these are in the transit all across the traffic routing device. This specific technique could
become the essential tool in the prevention of the hackers threat and the it would help in the
saving of the space in the network.
IDS or intrusion detection system: The Intrusion detection system could be
extensively utilised for the prevention of any kind of attack on the organisational network. It
is the device or any software application which helps in the monitoring of the network or the
systems for the malicious activity or the policy violations.
CLOUD INFRASTRUCTURE SECURITY
Network address translation: This method is also known as the NAT that is the
technique of the remapping of one of the IP address space within any other by the
modification of the information of the network address in IP header of the packers while
these are in the transit all across the traffic routing device. This specific technique could
become the essential tool in the prevention of the hackers threat and the it would help in the
saving of the space in the network.
IDS or intrusion detection system: The Intrusion detection system could be
extensively utilised for the prevention of any kind of attack on the organisational network. It
is the device or any software application which helps in the monitoring of the network or the
systems for the malicious activity or the policy violations.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
CLOUD INFRASTRUCTURE SECURITY
References
Ali, M., Khan, S.U. and Vasilakos, A.V., 2015. Security in cloud computing: Opportunities
and challenges. Information sciences, 305, pp.357-383.
Battula, L.R., 2014, September. Network security function virtualization (nsfv) towards cloud
computing with nfv over openflow infrastructure: Challenges and novel approaches. In 2014
International Conference on Advances in Computing, Communications and Informatics
(ICACCI) (pp. 1622-1628). IEEE.
Biswas, A.R. and Giaffreda, R., 2014, March. IoT and cloud convergence: Opportunities and
challenges. In 2014 IEEE World Forum on Internet of Things (WF-IoT) (pp. 375-376). IEEE.
Fortino, G., Di Fatta, G., Pathan, M. and Vasilakos, A.V., 2014. Cloud-assisted body area
networks: state-of-the-art and future challenges. Wireless Networks, 20(7), pp.1925-1938.
Ibrahim, A.S., Hamlyn-Harris, J. and Grundy, J., 2016. Emerging security challenges of
cloud virtual infrastructure. arXiv preprint arXiv:1612.09059.
Madni, S.H.H., Latiff, M.S.A. and Coulibaly, Y., 2016. Resource scheduling for
infrastructure as a service (IaaS) in cloud computing: Challenges and opportunities. Journal
of Network and Computer Applications, 68, pp.173-200.
Puthal, D., Sahoo, B.P.S., Mishra, S. and Swain, S., 2015, January. Cloud computing
features, issues, and challenges: a big picture. In 2015 International Conference on
Computational Intelligence and Networks (pp. 116-123). IEEE.
Rao, R.V. and Selvamani, K., 2015. Data security challenges and its solutions in cloud
computing. Procedia Computer Science, 48, pp.204-209.
CLOUD INFRASTRUCTURE SECURITY
References
Ali, M., Khan, S.U. and Vasilakos, A.V., 2015. Security in cloud computing: Opportunities
and challenges. Information sciences, 305, pp.357-383.
Battula, L.R., 2014, September. Network security function virtualization (nsfv) towards cloud
computing with nfv over openflow infrastructure: Challenges and novel approaches. In 2014
International Conference on Advances in Computing, Communications and Informatics
(ICACCI) (pp. 1622-1628). IEEE.
Biswas, A.R. and Giaffreda, R., 2014, March. IoT and cloud convergence: Opportunities and
challenges. In 2014 IEEE World Forum on Internet of Things (WF-IoT) (pp. 375-376). IEEE.
Fortino, G., Di Fatta, G., Pathan, M. and Vasilakos, A.V., 2014. Cloud-assisted body area
networks: state-of-the-art and future challenges. Wireless Networks, 20(7), pp.1925-1938.
Ibrahim, A.S., Hamlyn-Harris, J. and Grundy, J., 2016. Emerging security challenges of
cloud virtual infrastructure. arXiv preprint arXiv:1612.09059.
Madni, S.H.H., Latiff, M.S.A. and Coulibaly, Y., 2016. Resource scheduling for
infrastructure as a service (IaaS) in cloud computing: Challenges and opportunities. Journal
of Network and Computer Applications, 68, pp.173-200.
Puthal, D., Sahoo, B.P.S., Mishra, S. and Swain, S., 2015, January. Cloud computing
features, issues, and challenges: a big picture. In 2015 International Conference on
Computational Intelligence and Networks (pp. 116-123). IEEE.
Rao, R.V. and Selvamani, K., 2015. Data security challenges and its solutions in cloud
computing. Procedia Computer Science, 48, pp.204-209.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
CLOUD INFRASTRUCTURE SECURITY
Sadiku, M.N., Musa, S.M. and Momoh, O.D., 2014. Cloud computing: opportunities and
challenges. IEEE potentials, 33(1), pp.34-36.
Singh, S. and Chana, I., 2016. A survey on resource scheduling in cloud computing: Issues
and challenges. Journal of grid computing, 14(2), pp.217-264.
Sultan, N., 2014. Making use of cloud computing for healthcare provision: Opportunities and
challenges. International Journal of Information Management, 34(2), pp.177-184.
Taleb, T., 2014. Toward carrier cloud: Potential, challenges, and solutions. IEEE Wireless
Communications, 21(3), pp.80-91.
CLOUD INFRASTRUCTURE SECURITY
Sadiku, M.N., Musa, S.M. and Momoh, O.D., 2014. Cloud computing: opportunities and
challenges. IEEE potentials, 33(1), pp.34-36.
Singh, S. and Chana, I., 2016. A survey on resource scheduling in cloud computing: Issues
and challenges. Journal of grid computing, 14(2), pp.217-264.
Sultan, N., 2014. Making use of cloud computing for healthcare provision: Opportunities and
challenges. International Journal of Information Management, 34(2), pp.177-184.
Taleb, T., 2014. Toward carrier cloud: Potential, challenges, and solutions. IEEE Wireless
Communications, 21(3), pp.80-91.

11
CLOUD INFRASTRUCTURE SECURITY
CLOUD INFRASTRUCTURE SECURITY
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





