Cloud Computing Report: Security and Privacy for NGOs - [University]
VerifiedAdded on 2023/06/03
|14
|4292
|217
Report
AI Summary
This report provides an in-depth analysis of cloud computing, focusing on the specific needs and challenges of Non-Governmental Organizations (NGOs). It explores the ethical and practical implications of cloud adoption, particularly concerning data privacy and security. The report examines the potential benefits of cloud services like IaaS, SaaS, and PaaS, and discusses the importance of robust authentication systems and adherence to ethical codes of conduct. It also highlights the significance of various cloud providers such as Amazon Web Services, Microsoft Azure, and Google Cloud in providing essential services like data storage and application platforms. Furthermore, the report emphasizes the importance of mobile device security within the cloud context and offers recommendations for ensuring data integrity and confidentiality. Overall, the report offers a comprehensive overview of how NGOs can leverage cloud technologies effectively while mitigating associated risks.
Running Head: CLOUD COMPUTING 0
Cloud Computing
Individual Assignment
Student name
Cloud Computing
Individual Assignment
Student name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cloud Computing 1
Table of Contents
Introduction......................................................................................................................................2
Personal and Ethical implications for the privacy...........................................................................3
Personal and Ethical implications for the security..........................................................................6
Privacy and security recommendations...........................................................................................7
Conclusion.......................................................................................................................................9
References......................................................................................................................................11
Table of Contents
Introduction......................................................................................................................................2
Personal and Ethical implications for the privacy...........................................................................3
Personal and Ethical implications for the security..........................................................................6
Privacy and security recommendations...........................................................................................7
Conclusion.......................................................................................................................................9
References......................................................................................................................................11

Cloud Computing 2
Introduction
Cloud computing services are the future in upcoming time of computer field. It was start
for data storage and it provides data everywhere. One thing was required for accessing data is
Internet. There are various cloud services for providing different facility to organization. In this
report, I will discuss about security and privacy of a Non-Government Organisations (referred as
NGO). NGO have some money for distribution to different clients (Chen & Zhao, 2012). They
want an online system, in which clients access money and other things with the help of
MySupport approach. Some NGO helps to government for handling some functions in a process.
It is a very sensitive system because of their work process. They had clients, which are required
help form government, and it delivered through the NGO’s (Cuzzocrea, 2014).
For that architecture, they have to implement different services form cloud computing
services, such as Amazon Web Service, Microsoft Azure, and Google cloud. It was a pack of
different services as per requirement of an organization. Now days, cloud is used as a service
provider to different organization. They provide different services, such as servers, data storage,
application software, and platform for executing programs (Garg, Versteeg, & Buyya, 2013).
Cloud computing is a latest service for enhance the business of an organization. It has
new IT technologies for providing better services to clients with security and privacy, such as
Machine Learning, Artificial Intelligence, and deep learning. Hadoop and Big data are the best
technologies used in cloud computing. NGO’s are a self-governed body, which provide various
services in different fields. Government release funds for NGO have to help them in their work
for public services.
For implementation, a system to connect different clients of a NGO with a valid
identification of client requires a system in which many facilities should be there for help of
clients (Krutz & Vines, 2010). I want to suggest that, they should adopt an IaaS for managing all
the services for clients and NGO functions. There are many function of a NGO with lots of
responsibilities. I will discuss about services and code of ethics of NGO (Kshetri, 2013).
Introduction
Cloud computing services are the future in upcoming time of computer field. It was start
for data storage and it provides data everywhere. One thing was required for accessing data is
Internet. There are various cloud services for providing different facility to organization. In this
report, I will discuss about security and privacy of a Non-Government Organisations (referred as
NGO). NGO have some money for distribution to different clients (Chen & Zhao, 2012). They
want an online system, in which clients access money and other things with the help of
MySupport approach. Some NGO helps to government for handling some functions in a process.
It is a very sensitive system because of their work process. They had clients, which are required
help form government, and it delivered through the NGO’s (Cuzzocrea, 2014).
For that architecture, they have to implement different services form cloud computing
services, such as Amazon Web Service, Microsoft Azure, and Google cloud. It was a pack of
different services as per requirement of an organization. Now days, cloud is used as a service
provider to different organization. They provide different services, such as servers, data storage,
application software, and platform for executing programs (Garg, Versteeg, & Buyya, 2013).
Cloud computing is a latest service for enhance the business of an organization. It has
new IT technologies for providing better services to clients with security and privacy, such as
Machine Learning, Artificial Intelligence, and deep learning. Hadoop and Big data are the best
technologies used in cloud computing. NGO’s are a self-governed body, which provide various
services in different fields. Government release funds for NGO have to help them in their work
for public services.
For implementation, a system to connect different clients of a NGO with a valid
identification of client requires a system in which many facilities should be there for help of
clients (Krutz & Vines, 2010). I want to suggest that, they should adopt an IaaS for managing all
the services for clients and NGO functions. There are many function of a NGO with lots of
responsibilities. I will discuss about services and code of ethics of NGO (Kshetri, 2013).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Cloud Computing 3
Personal and Ethical implications for the privacy
In this scenario, a valid authentication system will provided to NGO for managing
different functions with their clients. There are some issues in starting but if it is implement for
fully managed system then it will beneficial for all the department related to NGO. I will discuss
about ethical issues of implementation of cloud services, and discuss about privacy and security
on cloud system with the help of some cloud computing services (King & Raja, 2012).
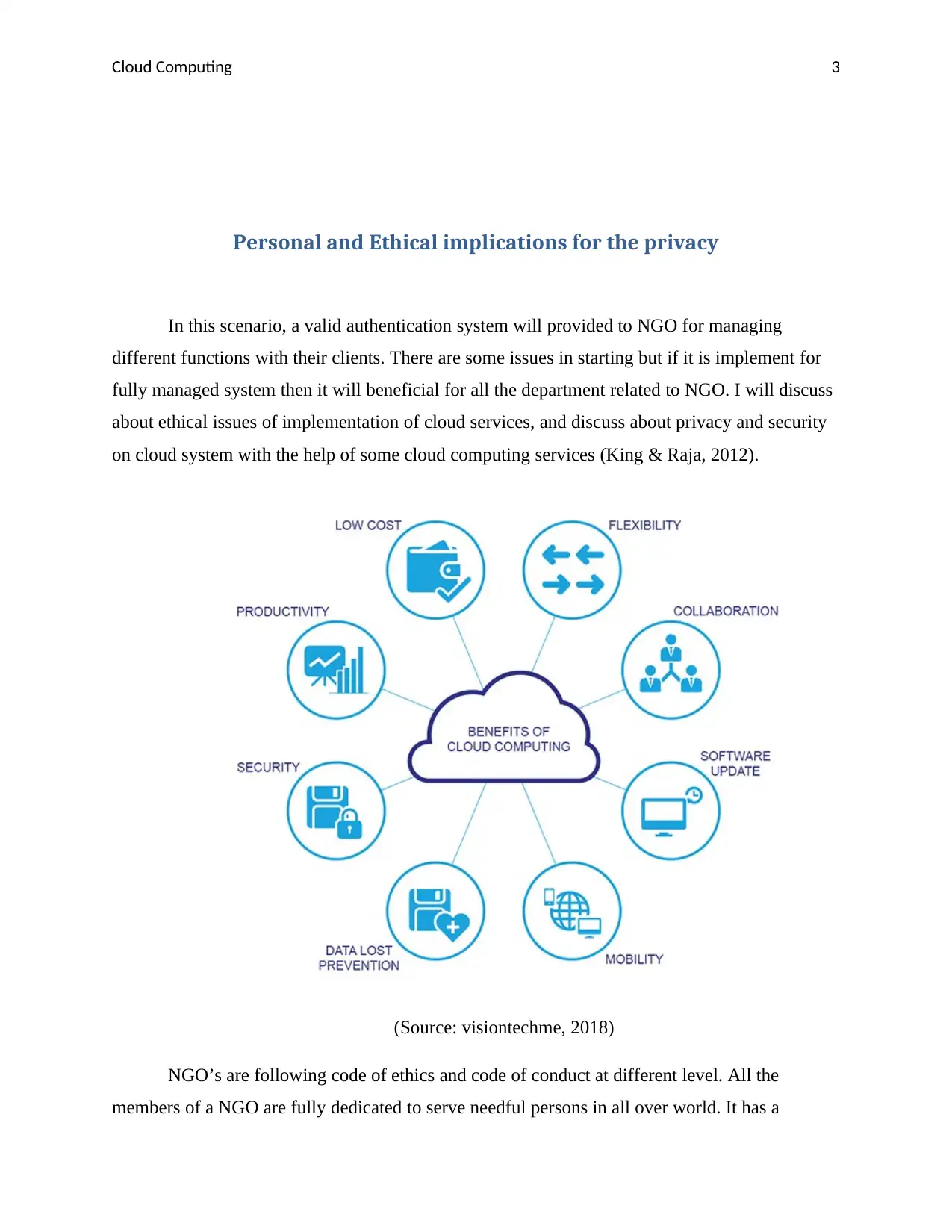
(Source: visiontechme, 2018)
NGO’s are following code of ethics and code of conduct at different level. All the
members of a NGO are fully dedicated to serve needful persons in all over world. It has a
Personal and Ethical implications for the privacy
In this scenario, a valid authentication system will provided to NGO for managing
different functions with their clients. There are some issues in starting but if it is implement for
fully managed system then it will beneficial for all the department related to NGO. I will discuss
about ethical issues of implementation of cloud services, and discuss about privacy and security
on cloud system with the help of some cloud computing services (King & Raja, 2012).
(Source: visiontechme, 2018)
NGO’s are following code of ethics and code of conduct at different level. All the
members of a NGO are fully dedicated to serve needful persons in all over world. It has a
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cloud Computing 4
sustainable process in which all organization contributes money or anything else to the common
good (Mather, Kumaraswamy, & Latif, 2009). That money will be used for progress, peace, and
justice to needful people, such as Rohingya people, and many more. NGO should integrate many
things for providing public services. NGO’s are responsible for providing services to particular
people or large amount of the public ( Maziliauskaite, 2018). It is public money for use of good
purpose by the government, so that money not used for personal purposes. Also, make as public
trust on NGO by everyone. NGO can be conduct different activities for betterment of
environment (Pearson, 2013). There should be cooperation beyond boundaries, such as inter-
religious, intercultural. An NGO should be willing to work for people in different fields beyond
borders of ethnicity, politics, culture, and religious matter. NGO’s always follow human rights
and dignity of every person from all over the world. They are religious free and help every
religion, when they require help (Rittinghouse & Ransome, 2016).
Source: ( Fu, 2017)
There are three types of services provided by a cloud vendor, which are Infrastructure as
a Service (referred as IaaS), Software as a Service (SaaS), and Platform as a service (PaaS). It is
a simple process in which cloud service provider charge according to your usages of services. If
anyone required only data storage then they provides only infrastructure for data storage, such as
servers and storage in terabytes (Heiser J. N., 2008). These services are so costly so not everyone
can implement all these services for personal use. Servers are too costly for implementations, as
well as other services are also too complex. NGO’s are also having lot of data and important
sustainable process in which all organization contributes money or anything else to the common
good (Mather, Kumaraswamy, & Latif, 2009). That money will be used for progress, peace, and
justice to needful people, such as Rohingya people, and many more. NGO should integrate many
things for providing public services. NGO’s are responsible for providing services to particular
people or large amount of the public ( Maziliauskaite, 2018). It is public money for use of good
purpose by the government, so that money not used for personal purposes. Also, make as public
trust on NGO by everyone. NGO can be conduct different activities for betterment of
environment (Pearson, 2013). There should be cooperation beyond boundaries, such as inter-
religious, intercultural. An NGO should be willing to work for people in different fields beyond
borders of ethnicity, politics, culture, and religious matter. NGO’s always follow human rights
and dignity of every person from all over the world. They are religious free and help every
religion, when they require help (Rittinghouse & Ransome, 2016).
Source: ( Fu, 2017)
There are three types of services provided by a cloud vendor, which are Infrastructure as
a Service (referred as IaaS), Software as a Service (SaaS), and Platform as a service (PaaS). It is
a simple process in which cloud service provider charge according to your usages of services. If
anyone required only data storage then they provides only infrastructure for data storage, such as
servers and storage in terabytes (Heiser J. N., 2008). These services are so costly so not everyone
can implement all these services for personal use. Servers are too costly for implementations, as
well as other services are also too complex. NGO’s are also having lot of data and important

Cloud Computing 5
things to serve public with the help of governments of country and other outside agencies
(Jansen, 2011).
NGO’s should be truthful for their working and dealing with the clients, staff members,
and government. NGO is a integrate project of many things, such as nonprofit, non-
governmental, organized, independent and self-governing. There are some mission and activities
of NGO, according to their field. There are some activities in NGO for accomplishes mission of
NGO. Activities should effective and efficient for achieving mission. Feedback should be there
for satisfaction of beneficiaries and stakeholders ( Schouten, 2014). Elevation is also necessary
for every activity by which some good changes should change in the activities by members.
Cloud computing is an emerging technology for providing cloud computing services to
various organizations for betterment of their business and other things (Sen, 2014). Cloud
computing depends on different things, such as Web services, virtualization, and internet. It
provides scalable and inexpensive infrastructures as per the client demand. They are helpful for
saving cost of implementation and provide new opportunities for business. Cloud computing is a
group of services, such as platform, webbing hosting, services, data storage, and softwares. It is a
group of services in which user can acquire different services according to their needs for a
particular time (So, 2011).
Many NGO’s acquire cloud-computing services for taking advantage of new
technologies. NGO’s are spreading there activities through cloud computing services. It is a
platform where they start their activities for public help. There are many advantages of cloud
computing, but some are so important feature of cloud computing, such as availability, Elasticity,
reliability, and quality of services (Subashini & Kavitha, 2011). It provides extend service in
which any organization change their requirement as per their need, such as data storage. It
provides scaling in different services, according to client’s needs. It is also reliable to all
organizations. It is capable to ensure about security and privacy of client data and services. It is
main feature of a cloud computing service (Svantesson & Clarke, 2010). It provides good quality
of services to every client as per their requirement.
It provides best services as per the agreement between client and vendor. Clients are free
to change their demand according to need (Takabi, Joshi, & Ahn, 2010). Sometimes
things to serve public with the help of governments of country and other outside agencies
(Jansen, 2011).
NGO’s should be truthful for their working and dealing with the clients, staff members,
and government. NGO is a integrate project of many things, such as nonprofit, non-
governmental, organized, independent and self-governing. There are some mission and activities
of NGO, according to their field. There are some activities in NGO for accomplishes mission of
NGO. Activities should effective and efficient for achieving mission. Feedback should be there
for satisfaction of beneficiaries and stakeholders ( Schouten, 2014). Elevation is also necessary
for every activity by which some good changes should change in the activities by members.
Cloud computing is an emerging technology for providing cloud computing services to
various organizations for betterment of their business and other things (Sen, 2014). Cloud
computing depends on different things, such as Web services, virtualization, and internet. It
provides scalable and inexpensive infrastructures as per the client demand. They are helpful for
saving cost of implementation and provide new opportunities for business. Cloud computing is a
group of services, such as platform, webbing hosting, services, data storage, and softwares. It is a
group of services in which user can acquire different services according to their needs for a
particular time (So, 2011).
Many NGO’s acquire cloud-computing services for taking advantage of new
technologies. NGO’s are spreading there activities through cloud computing services. It is a
platform where they start their activities for public help. There are many advantages of cloud
computing, but some are so important feature of cloud computing, such as availability, Elasticity,
reliability, and quality of services (Subashini & Kavitha, 2011). It provides extend service in
which any organization change their requirement as per their need, such as data storage. It
provides scaling in different services, according to client’s needs. It is also reliable to all
organizations. It is capable to ensure about security and privacy of client data and services. It is
main feature of a cloud computing service (Svantesson & Clarke, 2010). It provides good quality
of services to every client as per their requirement.
It provides best services as per the agreement between client and vendor. Clients are free
to change their demand according to need (Takabi, Joshi, & Ahn, 2010). Sometimes
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Cloud Computing 6
requirements are change for data storage and softwares. However, cloud computing enhance
their service and provide better service to client. There are so many services for client and all of
these are available for the client. If there is any problem in the system, then a team is always
there for your help (Wu, Casey, Hazen, & Hall, 2013).
Cloud computing is also cost effective, if any organization have their own infrastructure
then they should pay for many things for maintenance and acquisition. However, cloud provides
all those service in lower cost with the better maintenance and acquisition. It is also charge
according to uses of services. They take charge for actual use of services. Many organizations
are not from computer background so it is not their core competency. So less focus on
implementation of these types of services and hire these services from any cloud service
provider. It is also environment friendly system and save many things (Zhang, Wuwong, Li, &
Zhang, 2010).
Personal and Ethical implications for the security
Using cloud computing any organization can reduce complexity of system including
management and configuration of infrastructure. It has a great advantage that is no restriction of
physical location on working. Anyone can work from anywhere. Using cloud computing
Resources Company develops their business instead of developing infrastructure for data
management.
Cloud computing service providers are providing services but there are some risk for
security of personal data and processes of different modules. It provides access control to related
client but there are same space for data storage and same platform for development of
application, so it was an issue of privacy sometimes. Your data is secure on the cloud. However,
when you access your own data using Internet then make sure you access your data using a
secure channel.
They also used three level security systems for dynamic group in cloud. Cloud is a way to
store and share the information by clients in an efficient way with the high security and privacy.
It is helpful for organizations to avoid burden of data storage and ensure data integrity. There are
requirements are change for data storage and softwares. However, cloud computing enhance
their service and provide better service to client. There are so many services for client and all of
these are available for the client. If there is any problem in the system, then a team is always
there for your help (Wu, Casey, Hazen, & Hall, 2013).
Cloud computing is also cost effective, if any organization have their own infrastructure
then they should pay for many things for maintenance and acquisition. However, cloud provides
all those service in lower cost with the better maintenance and acquisition. It is also charge
according to uses of services. They take charge for actual use of services. Many organizations
are not from computer background so it is not their core competency. So less focus on
implementation of these types of services and hire these services from any cloud service
provider. It is also environment friendly system and save many things (Zhang, Wuwong, Li, &
Zhang, 2010).
Personal and Ethical implications for the security
Using cloud computing any organization can reduce complexity of system including
management and configuration of infrastructure. It has a great advantage that is no restriction of
physical location on working. Anyone can work from anywhere. Using cloud computing
Resources Company develops their business instead of developing infrastructure for data
management.
Cloud computing service providers are providing services but there are some risk for
security of personal data and processes of different modules. It provides access control to related
client but there are same space for data storage and same platform for development of
application, so it was an issue of privacy sometimes. Your data is secure on the cloud. However,
when you access your own data using Internet then make sure you access your data using a
secure channel.
They also used three level security systems for dynamic group in cloud. Cloud is a way to
store and share the information by clients in an efficient way with the high security and privacy.
It is helpful for organizations to avoid burden of data storage and ensure data integrity. There are
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cloud Computing 7
still research going on the security and privacy of clouds data storage and services. Virtualization
makes it better day by day based on client’s needs. Every client needs services for security and
privacy of their data. Cloud computing makes feasible all things in a single place with security
and privacy. Amazon was the first Cloud computing service provider and now various cloud
service providers in market (Yan, Deng, & Varadharajan, 2017).
Cloud services are more secure than other ways, because there is a big team for
researching on the security and privacy. Day by day cloud computing is the only way to use data
storage for future use. It is also providing data sharing with a high security of your personal data.
It is beneficial for NGO has to store information of all previous data on the cloud and using data
mining tools, they can analyses actual figures for processing. There are lot of softwares and
services of cloud computing to manage security and privacy of organizations.
According survey, cloud computing provides a better platform for NGO to provide
money to their clients form any place of world. It is fruitful for NGO’s as well as for clients also.
They need only an access key for getting that fund for betterment of their future. Cloud
computing provides better services to all their clients in low cost. As an example, AWS provides
services to Netflix for their data storage and infrastructure. There are many more examples,
which can use cloud, as an infrastructure. NGO’s should provide their service by helping of
cloud services, which can more beneficial for the clients. It is a better way to provide services to
needful persons (Jansen, 2011). Cloud computing is also providing backups, if in any case your
servers are fail then you can get your data from different backup servers.
In the cloud computing services, all things are legal and ethical, according to rules and
regulation of the country. NGO’s are world level organizations, so it is useful for their use and
provide different services to public. It is a better way to use the latest technology for betterment
of new generation. So many good things in the cloud service for managing so many works with
effective and more secure to NGO’s.
Privacy and security recommendations
still research going on the security and privacy of clouds data storage and services. Virtualization
makes it better day by day based on client’s needs. Every client needs services for security and
privacy of their data. Cloud computing makes feasible all things in a single place with security
and privacy. Amazon was the first Cloud computing service provider and now various cloud
service providers in market (Yan, Deng, & Varadharajan, 2017).
Cloud services are more secure than other ways, because there is a big team for
researching on the security and privacy. Day by day cloud computing is the only way to use data
storage for future use. It is also providing data sharing with a high security of your personal data.
It is beneficial for NGO has to store information of all previous data on the cloud and using data
mining tools, they can analyses actual figures for processing. There are lot of softwares and
services of cloud computing to manage security and privacy of organizations.
According survey, cloud computing provides a better platform for NGO to provide
money to their clients form any place of world. It is fruitful for NGO’s as well as for clients also.
They need only an access key for getting that fund for betterment of their future. Cloud
computing provides better services to all their clients in low cost. As an example, AWS provides
services to Netflix for their data storage and infrastructure. There are many more examples,
which can use cloud, as an infrastructure. NGO’s should provide their service by helping of
cloud services, which can more beneficial for the clients. It is a better way to provide services to
needful persons (Jansen, 2011). Cloud computing is also providing backups, if in any case your
servers are fail then you can get your data from different backup servers.
In the cloud computing services, all things are legal and ethical, according to rules and
regulation of the country. NGO’s are world level organizations, so it is useful for their use and
provide different services to public. It is a better way to use the latest technology for betterment
of new generation. So many good things in the cloud service for managing so many works with
effective and more secure to NGO’s.
Privacy and security recommendations

Cloud Computing 8
According to my opinion, Mobile devices will secure by two things, first is security
provided by mobile operating system, and second is from antivirus of third party software.
Mobile devices are used by most of the person in current scenario. Mobile devices have many
capabilities for access sensitive data. They are helpful for the user but sometimes they are a way
to enter unauthorized threads by other mobile device using mobile network. There are lot of
personal data, such as personal information, medical history, online transaction details, and
business data. Mobile devices are very sensitive, because they used cellular network. Malware is
a program, which access mobile device to exfiltration user personal data. It breaks their privacy
and security. Mobile security is an issue for current generation, and research is going on at large
level in industry, as well as academia for improving privacy and security of mobile devices. Now
a days research is continue on novel techniques for proving privacy and security to mobile
devices (Choo, Rokach, & Bettini, 2016).
Risk management issues are also raise in implementation an environment for personal
data storage. First thing is cost, because software and hardware are so costly for managing virtual
machines. It requires few months for implementation as well as maintenance cost will also high.
All these are risk for implementation of persona infrastructure for getting privacy and security,
but it will cost so much high then hire a cloud service form a vendor. There is a service legal
agreement (referred as SLA) for providing services with security and privacy. It is mandatory for
taking benefits of current scenario rather than implementing own virtual machine stations.
Encryption techniques are so helpful for managing security features (Garg, Versteeg, &
Buyya, 2013). NGO’s must use MySupport for managing different functions of NGO. The
MySupport approach will helpful for clients and it is cloud based approach so it provides so
many benefits to the all clients. It also provides different function to all clients to creating
activities for different people, which really need the help of NGO. There are some key features
of mobile computing, which makes it better than other services, such as scalability, reliability,
and lower cost. NGO’s are having different activities simultaneously, so they need data at
different place, which can only possible by the cloud service. NGO’s are providing services to all
their clients, so using cloud computing, we can provide access control of the system to the client
on the basis of high security, such as biometric and user ID, password concept ( Maziliauskaite,
2018).
According to my opinion, Mobile devices will secure by two things, first is security
provided by mobile operating system, and second is from antivirus of third party software.
Mobile devices are used by most of the person in current scenario. Mobile devices have many
capabilities for access sensitive data. They are helpful for the user but sometimes they are a way
to enter unauthorized threads by other mobile device using mobile network. There are lot of
personal data, such as personal information, medical history, online transaction details, and
business data. Mobile devices are very sensitive, because they used cellular network. Malware is
a program, which access mobile device to exfiltration user personal data. It breaks their privacy
and security. Mobile security is an issue for current generation, and research is going on at large
level in industry, as well as academia for improving privacy and security of mobile devices. Now
a days research is continue on novel techniques for proving privacy and security to mobile
devices (Choo, Rokach, & Bettini, 2016).
Risk management issues are also raise in implementation an environment for personal
data storage. First thing is cost, because software and hardware are so costly for managing virtual
machines. It requires few months for implementation as well as maintenance cost will also high.
All these are risk for implementation of persona infrastructure for getting privacy and security,
but it will cost so much high then hire a cloud service form a vendor. There is a service legal
agreement (referred as SLA) for providing services with security and privacy. It is mandatory for
taking benefits of current scenario rather than implementing own virtual machine stations.
Encryption techniques are so helpful for managing security features (Garg, Versteeg, &
Buyya, 2013). NGO’s must use MySupport for managing different functions of NGO. The
MySupport approach will helpful for clients and it is cloud based approach so it provides so
many benefits to the all clients. It also provides different function to all clients to creating
activities for different people, which really need the help of NGO. There are some key features
of mobile computing, which makes it better than other services, such as scalability, reliability,
and lower cost. NGO’s are having different activities simultaneously, so they need data at
different place, which can only possible by the cloud service. NGO’s are providing services to all
their clients, so using cloud computing, we can provide access control of the system to the client
on the basis of high security, such as biometric and user ID, password concept ( Maziliauskaite,
2018).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Cloud Computing 9
For privacy, public key based holomorphic linear authentication system will used by
cloud. There are so many ways in cryptography, such as hash functions, MD5, SHA1, and IDEA.
There are many security protocols for securing data on Internet, such as Internet Protocol
Security (referred as IP Sec). IP sec provide security of your data, when your data is travelling in
the network. Some cloud-computing vendor assures that you use your data only, after that, they
will dispose of your data and all information related to your portal. For more secure data transfer
you can use virtual private networks. There are lot of ways for securing data and information on
cloud but cryptography is a single way to secure your data from unethical persons. They also
provide antivirus and highly secured firewalls for data security and privacy. Many organizations
have their business data on cloud that was so important for their business. Therefore, it must be
secure and reliable thing to process all data on cloud (Zhou, Cao, Dong, & Vasilakos, 2017).
There are so many kinds of application, they take permission through user for providing
some free services, but actually, they are taking personal information of the users. It is also
happed due to unsecured Wi-Fi connection, in which many unauthorized users working, and they
harm your devices. Network spoofing is an example of hacking username and password of a
user. There are so many unwanted mails are coming on the mobiles device, some important
mails are missing due to that type of phishing attacks. Spam facility is available in the email
portal, but they are not safe. I had facing many issues in mobile device. Finally decide to install a
solid antivirus for stooping malwares.
Conclusion
It is concluded from previous parts of this report that, cloud computing is helpful for
implementation of an infrastructure for any organization. In case of NGO’s cloud, computing
provides many series and resources for completing their need for betterment of their purpose.
Cloud computing provides services as per requirement of clients, as I discussed in previous part.
Cloud service is available at lower cost for managing data and services of different
organizations. NGO’s are providing help in different areas, such as urban, and rural. Most of
them are helping needful people’s, which are in trouble because of some natural disaster or
genocide.
For privacy, public key based holomorphic linear authentication system will used by
cloud. There are so many ways in cryptography, such as hash functions, MD5, SHA1, and IDEA.
There are many security protocols for securing data on Internet, such as Internet Protocol
Security (referred as IP Sec). IP sec provide security of your data, when your data is travelling in
the network. Some cloud-computing vendor assures that you use your data only, after that, they
will dispose of your data and all information related to your portal. For more secure data transfer
you can use virtual private networks. There are lot of ways for securing data and information on
cloud but cryptography is a single way to secure your data from unethical persons. They also
provide antivirus and highly secured firewalls for data security and privacy. Many organizations
have their business data on cloud that was so important for their business. Therefore, it must be
secure and reliable thing to process all data on cloud (Zhou, Cao, Dong, & Vasilakos, 2017).
There are so many kinds of application, they take permission through user for providing
some free services, but actually, they are taking personal information of the users. It is also
happed due to unsecured Wi-Fi connection, in which many unauthorized users working, and they
harm your devices. Network spoofing is an example of hacking username and password of a
user. There are so many unwanted mails are coming on the mobiles device, some important
mails are missing due to that type of phishing attacks. Spam facility is available in the email
portal, but they are not safe. I had facing many issues in mobile device. Finally decide to install a
solid antivirus for stooping malwares.
Conclusion
It is concluded from previous parts of this report that, cloud computing is helpful for
implementation of an infrastructure for any organization. In case of NGO’s cloud, computing
provides many series and resources for completing their need for betterment of their purpose.
Cloud computing provides services as per requirement of clients, as I discussed in previous part.
Cloud service is available at lower cost for managing data and services of different
organizations. NGO’s are providing help in different areas, such as urban, and rural. Most of
them are helping needful people’s, which are in trouble because of some natural disaster or
genocide.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cloud Computing 10
It is concluded that, if cloud service will used for identification for clients of NGO then it
will be best for the security purpose of NGO as well as it maintain privacy also. There are many
ways to provide security to clients, such as authentication system. Every client will have a user
Id and password for his or her portal, such as education portal of a NGO. Few NGO’s are
providing education in rural areas for development. They can use cloud services for spreading
education in each part. It provides a better platform for development of softwares and application
according to clients and organization requirements.
Cloud computing is a basic need of this era for every person. Every person has their
personal data in terabytes and they need that data at different place so cloud is the best things for
this thing.
Finally, it is concluded that, NGO’s should use cloud computing for providing better
services to needful persons. They are also used different tools for analysis and details of different
activities. So cloud computing is the best way to enhance business as well as services of NGO’s.
MySupport approach will be beneficial for the NGO’s services.
It is concluded that, if cloud service will used for identification for clients of NGO then it
will be best for the security purpose of NGO as well as it maintain privacy also. There are many
ways to provide security to clients, such as authentication system. Every client will have a user
Id and password for his or her portal, such as education portal of a NGO. Few NGO’s are
providing education in rural areas for development. They can use cloud services for spreading
education in each part. It provides a better platform for development of softwares and application
according to clients and organization requirements.
Cloud computing is a basic need of this era for every person. Every person has their
personal data in terabytes and they need that data at different place so cloud is the best things for
this thing.
Finally, it is concluded that, NGO’s should use cloud computing for providing better
services to needful persons. They are also used different tools for analysis and details of different
activities. So cloud computing is the best way to enhance business as well as services of NGO’s.
MySupport approach will be beneficial for the NGO’s services.

Cloud Computing 11
References
Maziliauskaite, K. (2018). Logistics in the Cloud. Retrieved september 11, 2018, from
https://longitudes.ups.com/supply-chain-cloud/
Schouten, E. (2014). Cloud computing defined: Characteristics & service levels. Retrieved
September 11, 2018, from
https://www.ibm.com/blogs/cloud-computing/2014/01/31/cloud-computing-defined-
characteristics-service-levels/
Chen, D., & Zhao, H. (2012). Data security and privacy protection issues in cloud computing.
International Conference on Computer Science and Electronics Engineering, 1(1), 647-
651.
Cuzzocrea, A. (2014). Privacy and security of big data: current challenges and future research
perspectives. In Proceedings of the First International Workshop on Privacy and Secuirty
of Big Data (pp. 45-47). Shanghai: ACM.
Garg, S. K., Versteeg, S., & Buyya, R. (2013). A framework for ranking of cloud computing
services. Future Generation Computer Systems, 29(4), 1012-1023.
Heiser, J., & Nicolett, M. (2008). Assessing the security risks of cloud computing. Gartner
Report, 27(1), 29-52.
Heiser, J., & Nicolett, M. (2008). Assessing the security risks of cloud computing. Gartner
Report, 27(1), 29-52.
https://o7planning.org. (2018). Introducing Netflix and their cloud computing technology .
Retrieved 09 01, 2018, from https://o7planning.org/en/11717/introducing-netflix-and-
their-cloud-computing-technology
Jansen, W. (2011). Cloud hooks: Security and privacy issues in cloud computing. In 2011 44th
Hawaii International Conference on System Sciences (pp. 1-10). Hawaii: IEEE.
References
Maziliauskaite, K. (2018). Logistics in the Cloud. Retrieved september 11, 2018, from
https://longitudes.ups.com/supply-chain-cloud/
Schouten, E. (2014). Cloud computing defined: Characteristics & service levels. Retrieved
September 11, 2018, from
https://www.ibm.com/blogs/cloud-computing/2014/01/31/cloud-computing-defined-
characteristics-service-levels/
Chen, D., & Zhao, H. (2012). Data security and privacy protection issues in cloud computing.
International Conference on Computer Science and Electronics Engineering, 1(1), 647-
651.
Cuzzocrea, A. (2014). Privacy and security of big data: current challenges and future research
perspectives. In Proceedings of the First International Workshop on Privacy and Secuirty
of Big Data (pp. 45-47). Shanghai: ACM.
Garg, S. K., Versteeg, S., & Buyya, R. (2013). A framework for ranking of cloud computing
services. Future Generation Computer Systems, 29(4), 1012-1023.
Heiser, J., & Nicolett, M. (2008). Assessing the security risks of cloud computing. Gartner
Report, 27(1), 29-52.
Heiser, J., & Nicolett, M. (2008). Assessing the security risks of cloud computing. Gartner
Report, 27(1), 29-52.
https://o7planning.org. (2018). Introducing Netflix and their cloud computing technology .
Retrieved 09 01, 2018, from https://o7planning.org/en/11717/introducing-netflix-and-
their-cloud-computing-technology
Jansen, W. (2011). Cloud hooks: Security and privacy issues in cloud computing. In 2011 44th
Hawaii International Conference on System Sciences (pp. 1-10). Hawaii: IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




