Cloud Cryptography for Privacy: Technologies and Methodologies Report
VerifiedAdded on 2022/12/05
|14
|3660
|239
Report
AI Summary
This report provides an in-depth analysis of cloud cryptography, focusing on its role in ensuring data privacy and security within cloud computing environments. It explores various cryptographic techniques, including homomorphic encryption, secure multi-party computation, and verifiable computation, highlighting their applications in addressing threats and achieving security goals. The report examines different cloud deployment models, such as trusted, semi-trusted, and untrusted clouds, and discusses the challenges and solutions associated with each. It emphasizes the importance of confidentiality and integrity in cloud data storage and outlines the significance of multi-party computation in secure data processing. The findings highlight the practical implementations of multi-party computation in various sectors, such as auctions and data analysis. The report concludes with a discussion of the future of cloud cryptography and its reliance on collaboration between cryptography and data science. The report is contributed by a student and is available on Desklib, a platform providing AI-based study tools.

Running head: CLOUD CRYPTOGRAPHY FOR PRIVACY
CLOUD CRYPTOGRAPHY FOR PRIVACY
Name of the Student
Name of the University
Author Note:
CLOUD CRYPTOGRAPHY FOR PRIVACY
Name of the Student
Name of the University
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1CLOUD CRYPTOGRAPHY FOR PRIVACY
Abstract
Data Storage can be considered to be as one of the major usages of cloud computing. Cloud aims to
provide a huge amount of capacity for data storage for all the cloud users. It can be considered to be a
flexible and reliable method to a user for storing data and retrieving it at any time and location. With
every passing year, it is found to be as one of the growing technology. Most of the enterprises have
started using cloud storage as a result of various benefits. Cloud aims to gain a huge amount of popularity
as a result of usability and interaction. The major issue is with data security, data privacy and other kinds
of protection problems.
Abstract
Data Storage can be considered to be as one of the major usages of cloud computing. Cloud aims to
provide a huge amount of capacity for data storage for all the cloud users. It can be considered to be a
flexible and reliable method to a user for storing data and retrieving it at any time and location. With
every passing year, it is found to be as one of the growing technology. Most of the enterprises have
started using cloud storage as a result of various benefits. Cloud aims to gain a huge amount of popularity
as a result of usability and interaction. The major issue is with data security, data privacy and other kinds
of protection problems.

2CLOUD CRYPTOGRAPHY FOR PRIVACY
Table of Contents
Introduction....................................................................................................................................3
Main Body......................................................................................................................................3
Findings..........................................................................................................................................7
Conclusion......................................................................................................................................9
References....................................................................................................................................10
Table of Contents
Introduction....................................................................................................................................3
Main Body......................................................................................................................................3
Findings..........................................................................................................................................7
Conclusion......................................................................................................................................9
References....................................................................................................................................10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3CLOUD CRYPTOGRAPHY FOR PRIVACY
Introduction
The biggest method of securing data transmission mainly relies on the overall security of cloud
storage. Cloud aims to provide a huge amount of capacity which is required for storing data of different
cloud users. It is much more flexible and reliable method for storing and retrieving data at any place and
time (Choo, Domingo-Ferrer & Zhang, 2016). It is found to be a growing technology which is being used
by many enterprises that makes use of cloud storage. As cloud aims to gain popularity as a result of
usability and attraction. The major issues lie in the overall data security, privacy and data protection
issues. Both security and data privacy in the cloud aims to have a major setback in the domain of cloud
computing. In the domain of cloud computing, both security and privacy aim to play like a key issue.
Cloud computing is found to be next-generation architecture of IT enterprise architecture (Al Hamid et
al., 2017). This can be defined as one the best method for big data processing and analytics that allow the
user to store and analyze data by making use of shared computing resources.
In this report, an overview has been provided with respect to different cryptographic techniques.
It is mainly related to address different threats and security goals for analyzing the security of cloud
computing. Private semi-trusted cloud will allow different researchers to properly design cloud by making
use of cryptographic techniques. It is mainly needed for protecting the semi-trusted ones.
Main Body
Cloud computing mainly focus on service side where data security and trust is not taken to be
sufficient one. There are many techniques on the concept of cloud computing which has been analyzed
with respect to both academics and industries (Hong et al., 2016). Protection of data security and privacy
is becoming an important aspect for the development of cloud computing in various domain like
government, industries and business. There is a list of security risk for any sensitive data which is there in
cloud computing (Esposito et al., 2018). There is a need for entrusting the data protection for some of the
third party cloud provider which directs the protection provided by cryptography in the cloud. When a
Introduction
The biggest method of securing data transmission mainly relies on the overall security of cloud
storage. Cloud aims to provide a huge amount of capacity which is required for storing data of different
cloud users. It is much more flexible and reliable method for storing and retrieving data at any place and
time (Choo, Domingo-Ferrer & Zhang, 2016). It is found to be a growing technology which is being used
by many enterprises that makes use of cloud storage. As cloud aims to gain popularity as a result of
usability and attraction. The major issues lie in the overall data security, privacy and data protection
issues. Both security and data privacy in the cloud aims to have a major setback in the domain of cloud
computing. In the domain of cloud computing, both security and privacy aim to play like a key issue.
Cloud computing is found to be next-generation architecture of IT enterprise architecture (Al Hamid et
al., 2017). This can be defined as one the best method for big data processing and analytics that allow the
user to store and analyze data by making use of shared computing resources.
In this report, an overview has been provided with respect to different cryptographic techniques.
It is mainly related to address different threats and security goals for analyzing the security of cloud
computing. Private semi-trusted cloud will allow different researchers to properly design cloud by making
use of cryptographic techniques. It is mainly needed for protecting the semi-trusted ones.
Main Body
Cloud computing mainly focus on service side where data security and trust is not taken to be
sufficient one. There are many techniques on the concept of cloud computing which has been analyzed
with respect to both academics and industries (Hong et al., 2016). Protection of data security and privacy
is becoming an important aspect for the development of cloud computing in various domain like
government, industries and business. There is a list of security risk for any sensitive data which is there in
cloud computing (Esposito et al., 2018). There is a need for entrusting the data protection for some of the
third party cloud provider which directs the protection provided by cryptography in the cloud. When a
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4CLOUD CRYPTOGRAPHY FOR PRIVACY
user releases data in the cloud environment and leaves the protection of owners then the overall data
protection becomes one of the serious concern. Both cryptographic solution and secure communication
are considered to be the best method for a user for ensuring the overall security on a cloud platform. It is
merely inclusive of confidentiality and integrity issue (Yu et al., 2016). Confidentiality aims to highlight
various kind of sensitive data, which is to be accessed by some specific user. This is mainly done so that
information can be secured from any untrusted entities. Integrity focus on any kind of unauthorized
modification for any sensitive data which is detectable. The overall output of computation of sensitive
data requires to be consistent with input data.
Cloud deployment method and current trust methods have entities which are needed for achieving
overall confidentiality and integrity. There are mainly three concepts for cloud data storage that is trusted
the cloud, semi-trusted cloud and lastly untrusted cloud (Kolhar, Abu-Alhaj & El-atty, 2017). Both
untrusted and trusted cloud generally corresponds to private and public cloud model of deployment.
Semi-trusted cloud generally corresponds to a hybrid, private and public cloud. Untrusted cloud along
with cloud provider that is not trusted on cloud nodes so that its confidentiality and data integrity needs to
be maintained. Some of the trusted cloud users aims to occur on cloud which is employed on the isolated
environment from outside. In this kind of environment, similar kind of nodes can be easily corrupted as a
result of malicious insider that leads to data violation and integrity (Hörandner et al., 2016). Semi-trusted
cloud with consistent data owner focuses on maintaining the overall security of cloud resources. In some
of the parts, cloud can be controlled by some untrusted parties. In this scenario, it ultimately leads to
violation of confidentiality and data integrity or computation. The corrupted parties are considered to be a
major threat for collecting the required information by a combination of observation.
Let us consider an agency which is responsible for creating datasets along with maintaining a
reference database. The datasets come up with metadata that is computed by a cloud which is achieved by
using an effective algorithm (Ulybyshev et al., 2017). This particular agency is not fully trustable as a
cloud is completely free of wishes and adversaries semi-trusted cloud focus on ignoring risk for some
user releases data in the cloud environment and leaves the protection of owners then the overall data
protection becomes one of the serious concern. Both cryptographic solution and secure communication
are considered to be the best method for a user for ensuring the overall security on a cloud platform. It is
merely inclusive of confidentiality and integrity issue (Yu et al., 2016). Confidentiality aims to highlight
various kind of sensitive data, which is to be accessed by some specific user. This is mainly done so that
information can be secured from any untrusted entities. Integrity focus on any kind of unauthorized
modification for any sensitive data which is detectable. The overall output of computation of sensitive
data requires to be consistent with input data.
Cloud deployment method and current trust methods have entities which are needed for achieving
overall confidentiality and integrity. There are mainly three concepts for cloud data storage that is trusted
the cloud, semi-trusted cloud and lastly untrusted cloud (Kolhar, Abu-Alhaj & El-atty, 2017). Both
untrusted and trusted cloud generally corresponds to private and public cloud model of deployment.
Semi-trusted cloud generally corresponds to a hybrid, private and public cloud. Untrusted cloud along
with cloud provider that is not trusted on cloud nodes so that its confidentiality and data integrity needs to
be maintained. Some of the trusted cloud users aims to occur on cloud which is employed on the isolated
environment from outside. In this kind of environment, similar kind of nodes can be easily corrupted as a
result of malicious insider that leads to data violation and integrity (Hörandner et al., 2016). Semi-trusted
cloud with consistent data owner focuses on maintaining the overall security of cloud resources. In some
of the parts, cloud can be controlled by some untrusted parties. In this scenario, it ultimately leads to
violation of confidentiality and data integrity or computation. The corrupted parties are considered to be a
major threat for collecting the required information by a combination of observation.
Let us consider an agency which is responsible for creating datasets along with maintaining a
reference database. The datasets come up with metadata that is computed by a cloud which is achieved by
using an effective algorithm (Ulybyshev et al., 2017). This particular agency is not fully trustable as a
cloud is completely free of wishes and adversaries semi-trusted cloud focus on ignoring risk for some
5CLOUD CRYPTOGRAPHY FOR PRIVACY
malicious insider by controlling cloud nodes. Cryptographic technique is generally applied for securing
big data analytics on the cloud platform. It will merely become an important aspect in the whole
ecosystem of big data (Yan, Deng & Varadharajan, 2017). The overall future of big data processing is
completely depended on collaboration between cryptography and data science.
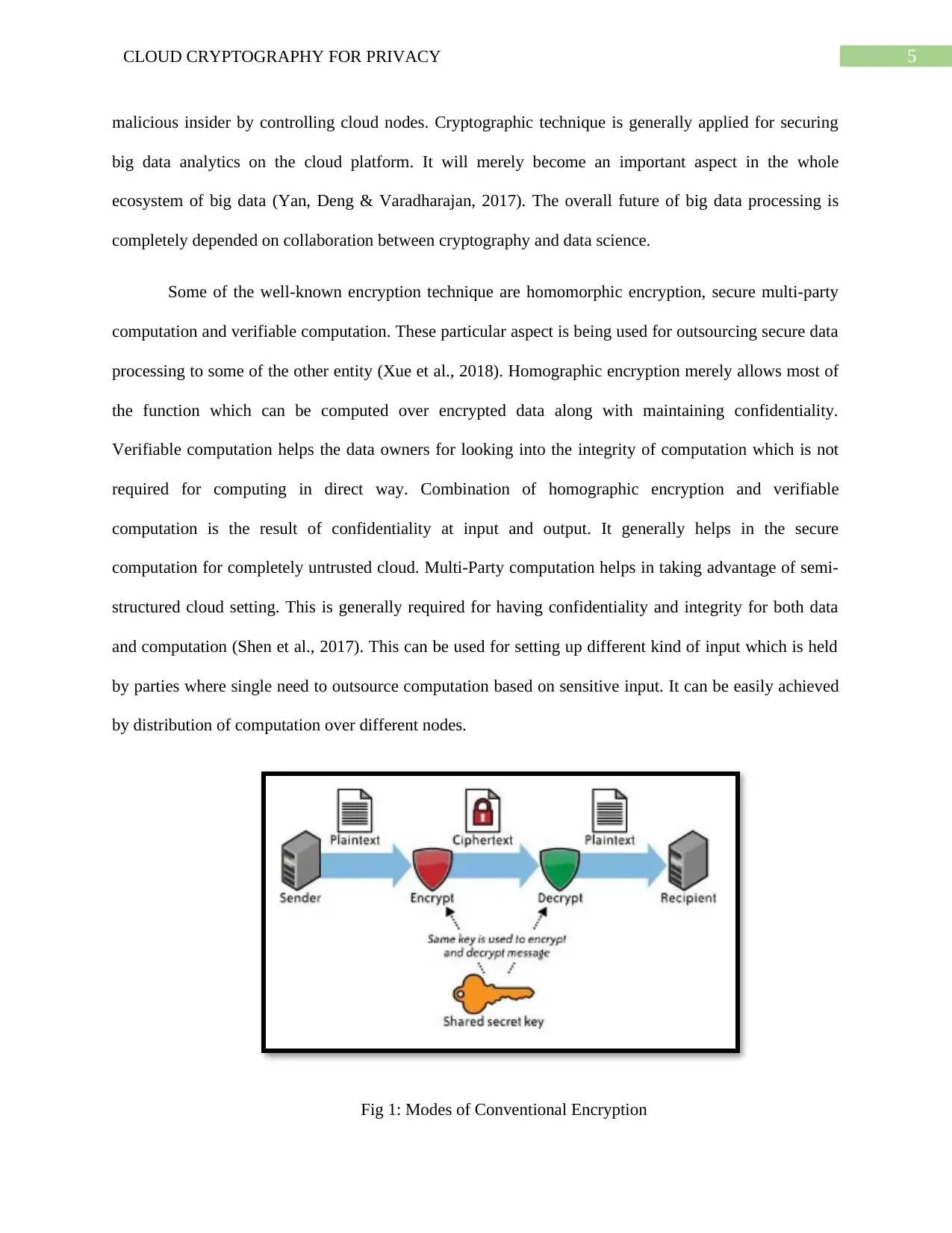
Some of the well-known encryption technique are homomorphic encryption, secure multi-party
computation and verifiable computation. These particular aspect is being used for outsourcing secure data
processing to some of the other entity (Xue et al., 2018). Homographic encryption merely allows most of
the function which can be computed over encrypted data along with maintaining confidentiality.
Verifiable computation helps the data owners for looking into the integrity of computation which is not
required for computing in direct way. Combination of homographic encryption and verifiable
computation is the result of confidentiality at input and output. It generally helps in the secure
computation for completely untrusted cloud. Multi-Party computation helps in taking advantage of semi-
structured cloud setting. This is generally required for having confidentiality and integrity for both data
and computation (Shen et al., 2017). This can be used for setting up different kind of input which is held
by parties where single need to outsource computation based on sensitive input. It can be easily achieved
by distribution of computation over different nodes.
Fig 1: Modes of Conventional Encryption
malicious insider by controlling cloud nodes. Cryptographic technique is generally applied for securing
big data analytics on the cloud platform. It will merely become an important aspect in the whole
ecosystem of big data (Yan, Deng & Varadharajan, 2017). The overall future of big data processing is
completely depended on collaboration between cryptography and data science.
Some of the well-known encryption technique are homomorphic encryption, secure multi-party
computation and verifiable computation. These particular aspect is being used for outsourcing secure data
processing to some of the other entity (Xue et al., 2018). Homographic encryption merely allows most of
the function which can be computed over encrypted data along with maintaining confidentiality.
Verifiable computation helps the data owners for looking into the integrity of computation which is not
required for computing in direct way. Combination of homographic encryption and verifiable
computation is the result of confidentiality at input and output. It generally helps in the secure
computation for completely untrusted cloud. Multi-Party computation helps in taking advantage of semi-
structured cloud setting. This is generally required for having confidentiality and integrity for both data
and computation (Shen et al., 2017). This can be used for setting up different kind of input which is held
by parties where single need to outsource computation based on sensitive input. It can be easily achieved
by distribution of computation over different nodes.
Fig 1: Modes of Conventional Encryption
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6CLOUD CRYPTOGRAPHY FOR PRIVACY
(Source: Ulybyshev et al., 2017)
In some of the cases, data owners aim to jointly compute with some of the function that is
required for collecting sensitive data. Most of the organization predict cyber threats by conducting an
analysis of information from other firms. Even if the hospital wants to have a result of the computation of
data collected by parties without any data sharing of sensitive information (Wang et al., 2017). Securing
multi-party computation can be defined as a group of efficient approach which helps the client to easily
outsource computation to any third party. It generally assures that client information is completely
prevented from any kind of misuse even if some parties are completely corrupted and cannot even be
trusted. Securing multi-party computation is the best domain for cryptography which addressed this
particular issue. The protocol will help the parties for carrying distributed computation for private data
with the need of the third party. It generally exists for various computation function which provides
private data without making use of the third party (Xia et al., 2015). It merely exists for any of the
computation function which provides privacy for different application where parties aim to share data.
There is a party for everyone who trusts their input and trusted party will carry out distributed
computation. The mere focus is multi-party computation which is powerful cryptographic notion required
for solving any kind of cryptographic issue.
Cryptographic protocol aims to provide the best kind of security for any behaviour change like
semi-honest adversary and malicious adversary. The given adversary will be done by making use of
different efforts so that it can interfere with overall computation. semi-honest adversary aims to follow
protocol description for any kind of unauthorized messages to be received (Sahin & El Abbadi, 2018). In
general, malicious derivates from protocol so that they can have private information or even disrupt
protocol.
MPC stands for multi-party computation has generally two kind of adversaries that is semi-honest
and malicious. Single adversary can easily corrupt the different subset parties which can control behavior
along with input and output. There is huge number of differences in between computational security and
(Source: Ulybyshev et al., 2017)
In some of the cases, data owners aim to jointly compute with some of the function that is
required for collecting sensitive data. Most of the organization predict cyber threats by conducting an
analysis of information from other firms. Even if the hospital wants to have a result of the computation of
data collected by parties without any data sharing of sensitive information (Wang et al., 2017). Securing
multi-party computation can be defined as a group of efficient approach which helps the client to easily
outsource computation to any third party. It generally assures that client information is completely
prevented from any kind of misuse even if some parties are completely corrupted and cannot even be
trusted. Securing multi-party computation is the best domain for cryptography which addressed this
particular issue. The protocol will help the parties for carrying distributed computation for private data
with the need of the third party. It generally exists for various computation function which provides
private data without making use of the third party (Xia et al., 2015). It merely exists for any of the
computation function which provides privacy for different application where parties aim to share data.
There is a party for everyone who trusts their input and trusted party will carry out distributed
computation. The mere focus is multi-party computation which is powerful cryptographic notion required
for solving any kind of cryptographic issue.
Cryptographic protocol aims to provide the best kind of security for any behaviour change like
semi-honest adversary and malicious adversary. The given adversary will be done by making use of
different efforts so that it can interfere with overall computation. semi-honest adversary aims to follow
protocol description for any kind of unauthorized messages to be received (Sahin & El Abbadi, 2018). In
general, malicious derivates from protocol so that they can have private information or even disrupt
protocol.
MPC stands for multi-party computation has generally two kind of adversaries that is semi-honest
and malicious. Single adversary can easily corrupt the different subset parties which can control behavior
along with input and output. There is huge number of differences in between computational security and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7CLOUD CRYPTOGRAPHY FOR PRIVACY
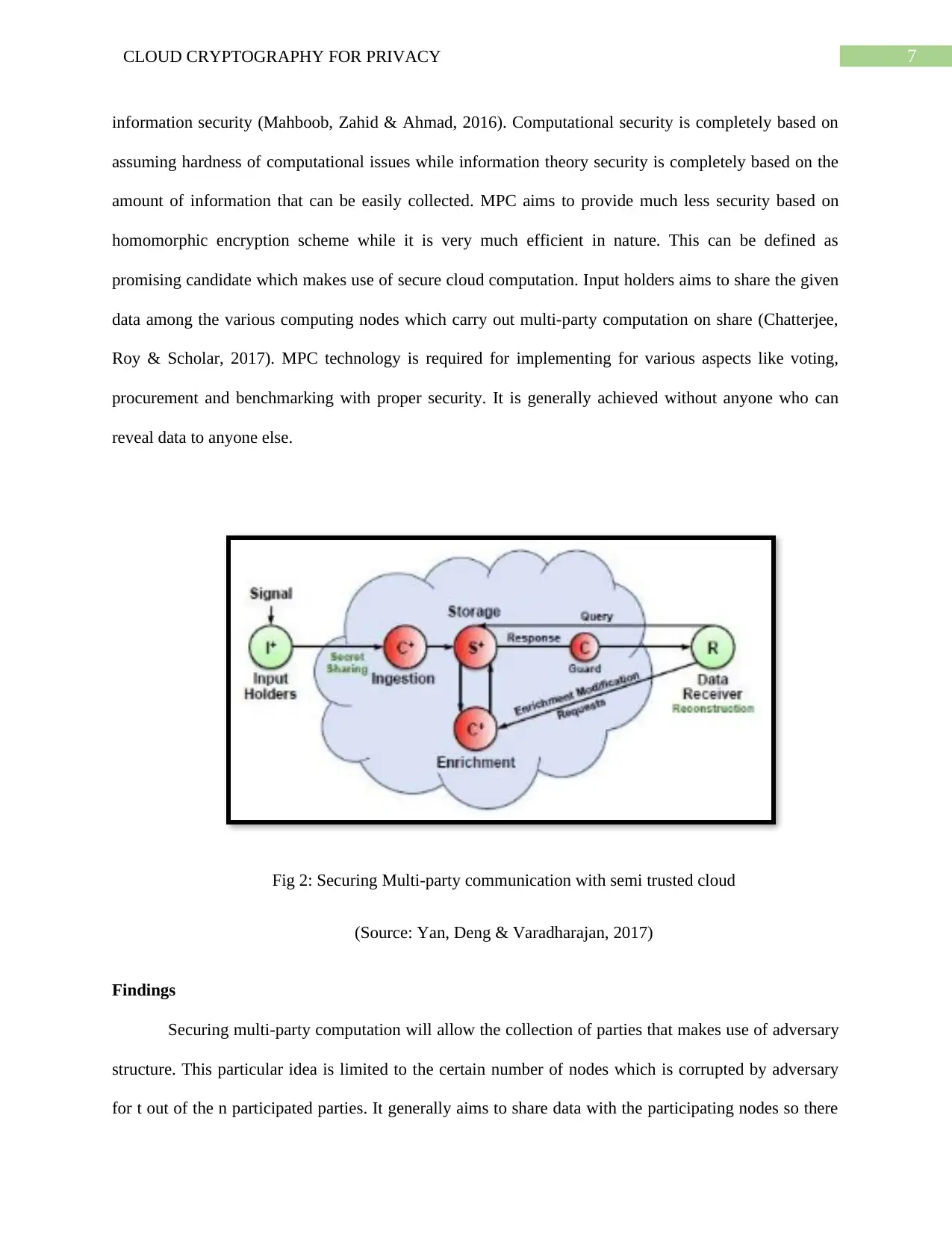
information security (Mahboob, Zahid & Ahmad, 2016). Computational security is completely based on
assuming hardness of computational issues while information theory security is completely based on the
amount of information that can be easily collected. MPC aims to provide much less security based on
homomorphic encryption scheme while it is very much efficient in nature. This can be defined as
promising candidate which makes use of secure cloud computation. Input holders aims to share the given
data among the various computing nodes which carry out multi-party computation on share (Chatterjee,
Roy & Scholar, 2017). MPC technology is required for implementing for various aspects like voting,
procurement and benchmarking with proper security. It is generally achieved without anyone who can
reveal data to anyone else.
Fig 2: Securing Multi-party communication with semi trusted cloud
(Source: Yan, Deng & Varadharajan, 2017)
Findings
Securing multi-party computation will allow the collection of parties that makes use of adversary
structure. This particular idea is limited to the certain number of nodes which is corrupted by adversary
for t out of the n participated parties. It generally aims to share data with the participating nodes so there
information security (Mahboob, Zahid & Ahmad, 2016). Computational security is completely based on
assuming hardness of computational issues while information theory security is completely based on the
amount of information that can be easily collected. MPC aims to provide much less security based on
homomorphic encryption scheme while it is very much efficient in nature. This can be defined as
promising candidate which makes use of secure cloud computation. Input holders aims to share the given
data among the various computing nodes which carry out multi-party computation on share (Chatterjee,
Roy & Scholar, 2017). MPC technology is required for implementing for various aspects like voting,
procurement and benchmarking with proper security. It is generally achieved without anyone who can
reveal data to anyone else.
Fig 2: Securing Multi-party communication with semi trusted cloud
(Source: Yan, Deng & Varadharajan, 2017)
Findings
Securing multi-party computation will allow the collection of parties that makes use of adversary
structure. This particular idea is limited to the certain number of nodes which is corrupted by adversary
for t out of the n participated parties. It generally aims to share data with the participating nodes so there

8CLOUD CRYPTOGRAPHY FOR PRIVACY
are no few nodes for t reveals for any input data (Tari et al., 2015). As the cloud node does have any
distinct idea of shares where they do not learn about computation input. Multi-party computation is
completely based on secret sharing which is generally used in most production system. In this particular
standard, many kinds of protocol depend of sharing input like computation which require other parties (Al
Hamid et al., 2017). For securing MPC most of the party process some of kind of private data while secret
sharing aims to provide a method to one party for spreading information.
For solving the secure multi-party computation issues, the adversary is generally specified by
single kind of corruption type. A threshold t for authorized number will lead to corrupted parties.
Considering the information-theoretic model, there is the mutual secure channel between every pair of
assumed parties (Hong et al., 2016). MPC can be easily used for setting up various kind of sensitive
inputs which are held by various parties or even setting up a single client. It is all about the outsourcing of
computation for various sensitive information by computation distribution over various computing nodes.
MPC has been studied for building various kind of solution which is practical with respect to computation
and communication cost. There is large number of practical implementation of MPC. Danish farmers
generally make it use for auction so that they can agree on price of sugar beets. Considering the specific
function of interest for securing multi-party computation (Kolhar, Abu-Alhaj & El-atty, 2017). Private set
interaction is one of the most preferred practice. PSI will merely allow n parties to carry out intersection
for the given datasets without providing any additional information.
Various kind of encryption algorithm is being used in information security. The given algorithm
can be used for categorizing various kind of classical encryption. This kind of encryption is completely
based on two kind of general principles which is known as a substitution cypher (Esposito et al., 2018). In
this each of the element provided in plaintext is completely mapped into other element and transposition
cypher where elements in plain text are completely re-arranged. Out of the range of encryption algorithm,
some of them are described below:
are no few nodes for t reveals for any input data (Tari et al., 2015). As the cloud node does have any
distinct idea of shares where they do not learn about computation input. Multi-party computation is
completely based on secret sharing which is generally used in most production system. In this particular
standard, many kinds of protocol depend of sharing input like computation which require other parties (Al
Hamid et al., 2017). For securing MPC most of the party process some of kind of private data while secret
sharing aims to provide a method to one party for spreading information.
For solving the secure multi-party computation issues, the adversary is generally specified by
single kind of corruption type. A threshold t for authorized number will lead to corrupted parties.
Considering the information-theoretic model, there is the mutual secure channel between every pair of
assumed parties (Hong et al., 2016). MPC can be easily used for setting up various kind of sensitive
inputs which are held by various parties or even setting up a single client. It is all about the outsourcing of
computation for various sensitive information by computation distribution over various computing nodes.
MPC has been studied for building various kind of solution which is practical with respect to computation
and communication cost. There is large number of practical implementation of MPC. Danish farmers
generally make it use for auction so that they can agree on price of sugar beets. Considering the specific
function of interest for securing multi-party computation (Kolhar, Abu-Alhaj & El-atty, 2017). Private set
interaction is one of the most preferred practice. PSI will merely allow n parties to carry out intersection
for the given datasets without providing any additional information.
Various kind of encryption algorithm is being used in information security. The given algorithm
can be used for categorizing various kind of classical encryption. This kind of encryption is completely
based on two kind of general principles which is known as a substitution cypher (Esposito et al., 2018). In
this each of the element provided in plaintext is completely mapped into other element and transposition
cypher where elements in plain text are completely re-arranged. Out of the range of encryption algorithm,
some of them are described below:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9CLOUD CRYPTOGRAPHY FOR PRIVACY
Caesar Cipher: It is the most suitable example of substitution of cipher and is the simplest
example of substitution cypher. It generally replaces the alphabets of letter in the plain text with letter 3
placed ahead (Yu et al., 2016). This particular cipher can be broken by using brute force attack as there
are only 25 option for key.
Playfair Cipher: The concept of Playfair cipher can be defined as a symmetric encryption that
follows a manual format. In case of Playfair Cipher, pairs of letters that are known as digraphs are taken
into account for the purpose of encryption, unlike other substitution cyphers (Caesar Cipher for example)
that works with single letter encryption. As there can be almost 600 different pairs of letters, the concept
of frequency analysis is comparatively much more complicated in Playfair Cipher (Hörandner et al.,
2016). That is why, it is often considered to be one of the most secured substitution ciphers. The first step
of the playfair cipher involves the creation of a key table with a dimension of 5*5. This plays a vital role
in plain text encryption.
Conclusion
The above pages help in concluding the fact that report is all about secure multi-party techniques
for addressing cloud computing security goals. Cryptographic techniques and secure communication issue
help in enhancing user concern over security of cloud data storage. The solution helps in creating a
suitable event for secure cloud computing in real world. MPC is the most efficient for securely creating
cryptographic challenges. It can be also highlighted cryptographic challenges which are enough to rely on
MPC based protocols. It is needed for providing security against semi-honest adversaries. This is
achieved by honest behavior as soon as the challenge has been solved. It highlights how the combination
of FHE and MPC is there for getting something better and practical. In addition, research is required for
optimizing private cloud that leads to a practical solution for data security on cloud platform. Both
security and privacy for stored data on cloud platform is one of the major area that has challenges and is
of huge importance. Most of the research issues of this domain is still required to be identified.
Cryptographic techniques are required for providing secure communication in between user and cloud.
Caesar Cipher: It is the most suitable example of substitution of cipher and is the simplest
example of substitution cypher. It generally replaces the alphabets of letter in the plain text with letter 3
placed ahead (Yu et al., 2016). This particular cipher can be broken by using brute force attack as there
are only 25 option for key.
Playfair Cipher: The concept of Playfair cipher can be defined as a symmetric encryption that
follows a manual format. In case of Playfair Cipher, pairs of letters that are known as digraphs are taken
into account for the purpose of encryption, unlike other substitution cyphers (Caesar Cipher for example)
that works with single letter encryption. As there can be almost 600 different pairs of letters, the concept
of frequency analysis is comparatively much more complicated in Playfair Cipher (Hörandner et al.,
2016). That is why, it is often considered to be one of the most secured substitution ciphers. The first step
of the playfair cipher involves the creation of a key table with a dimension of 5*5. This plays a vital role
in plain text encryption.
Conclusion
The above pages help in concluding the fact that report is all about secure multi-party techniques
for addressing cloud computing security goals. Cryptographic techniques and secure communication issue
help in enhancing user concern over security of cloud data storage. The solution helps in creating a
suitable event for secure cloud computing in real world. MPC is the most efficient for securely creating
cryptographic challenges. It can be also highlighted cryptographic challenges which are enough to rely on
MPC based protocols. It is needed for providing security against semi-honest adversaries. This is
achieved by honest behavior as soon as the challenge has been solved. It highlights how the combination
of FHE and MPC is there for getting something better and practical. In addition, research is required for
optimizing private cloud that leads to a practical solution for data security on cloud platform. Both
security and privacy for stored data on cloud platform is one of the major area that has challenges and is
of huge importance. Most of the research issues of this domain is still required to be identified.
Cryptographic techniques are required for providing secure communication in between user and cloud.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10CLOUD CRYPTOGRAPHY FOR PRIVACY

11CLOUD CRYPTOGRAPHY FOR PRIVACY
References
Al Hamid, H. A., Rahman, S. M. M., Hossain, M. S., Almogren, A., & Alamri, A. (2017). A security
model for preserving the privacy of medical big data in a healthcare cloud using a fog computing
facility with pairing-based cryptography. IEEE Access, 5, 22313-22328.
Chatterjee, R., Roy, S., & Scholar, U. G. (2017). Cryptography in cloud computing: a basic approach to
ensure security in cloud. International Journal of Engineering Science, 11818.
Choo, K. K. R., Domingo-Ferrer, J., & Zhang, L. (2016). Cloud Cryptography: Theory, Practice and
Future Research Directions. Future Generation Comp. Syst., 62, 51-53.
Esposito, C., De Santis, A., Tortora, G., Chang, H., & Choo, K. K. R. (2018). Blockchain: A panacea for
healthcare cloud-based data security and privacy?. IEEE Cloud Computing, 5(1), 31-37.
Hong, M. Q., Wang, P. Y., & Zhao, W. B. (2016, April). Homomorphic encryption scheme based on
elliptic curve cryptography for privacy protection of cloud computing. In 2016 IEEE 2nd
International Conference on Big Data Security on Cloud (BigDataSecurity), IEEE International
Conference on High Performance and Smart Computing (HPSC), and IEEE International
Conference on Intelligent Data and Security (IDS) (pp. 152-157). IEEE.
Hörandner, F., Krenn, S., Migliavacca, A., Thiemer, F., & Zwattendorfer, B. (2016, August).
CREDENTIAL: a framework for privacy-preserving cloud-based data sharing. In 2016 11th
International Conference on Availability, Reliability and Security (ARES) (pp. 742-749). IEEE.
Kolhar, M., Abu-Alhaj, M. M., & El-atty, S. M. A. (2017). Cloud data auditing techniques with a focus
on privacy and security. IEEE Security & Privacy, 15(1), 42-51.
Mahboob, T., Zahid, M., & Ahmad, G. (2016, August). Adopting information security techniques for
cloud computing—a survey. In 2016 1st International Conference on Information Technology,
Information Systems and Electrical Engineering (ICITISEE) (pp. 7-11). IEEE.
References
Al Hamid, H. A., Rahman, S. M. M., Hossain, M. S., Almogren, A., & Alamri, A. (2017). A security
model for preserving the privacy of medical big data in a healthcare cloud using a fog computing
facility with pairing-based cryptography. IEEE Access, 5, 22313-22328.
Chatterjee, R., Roy, S., & Scholar, U. G. (2017). Cryptography in cloud computing: a basic approach to
ensure security in cloud. International Journal of Engineering Science, 11818.
Choo, K. K. R., Domingo-Ferrer, J., & Zhang, L. (2016). Cloud Cryptography: Theory, Practice and
Future Research Directions. Future Generation Comp. Syst., 62, 51-53.
Esposito, C., De Santis, A., Tortora, G., Chang, H., & Choo, K. K. R. (2018). Blockchain: A panacea for
healthcare cloud-based data security and privacy?. IEEE Cloud Computing, 5(1), 31-37.
Hong, M. Q., Wang, P. Y., & Zhao, W. B. (2016, April). Homomorphic encryption scheme based on
elliptic curve cryptography for privacy protection of cloud computing. In 2016 IEEE 2nd
International Conference on Big Data Security on Cloud (BigDataSecurity), IEEE International
Conference on High Performance and Smart Computing (HPSC), and IEEE International
Conference on Intelligent Data and Security (IDS) (pp. 152-157). IEEE.
Hörandner, F., Krenn, S., Migliavacca, A., Thiemer, F., & Zwattendorfer, B. (2016, August).
CREDENTIAL: a framework for privacy-preserving cloud-based data sharing. In 2016 11th
International Conference on Availability, Reliability and Security (ARES) (pp. 742-749). IEEE.
Kolhar, M., Abu-Alhaj, M. M., & El-atty, S. M. A. (2017). Cloud data auditing techniques with a focus
on privacy and security. IEEE Security & Privacy, 15(1), 42-51.
Mahboob, T., Zahid, M., & Ahmad, G. (2016, August). Adopting information security techniques for
cloud computing—a survey. In 2016 1st International Conference on Information Technology,
Information Systems and Electrical Engineering (ICITISEE) (pp. 7-11). IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





