CO4512 Information Security Management: Cloud Risk Assessment Report
VerifiedAdded on 2023/06/14
|13
|3442
|497
Report
AI Summary
This document presents a comprehensive risk assessment report for Cloud-Centum, a cloud service provider, analyzing its network system and identifying potential threats and vulnerabilities. The assessment utilizes a combination of checklist and security matrix methods, adhering to ISO standards and NIST guidelines. It categorizes assets, identifies threats such as web API hacks and malware, and details vulnerabilities related to web applications, virtual machines, and cryptography. The report also includes preventive measures and recommendations to enhance the security posture of the cloud infrastructure. The document is contributed by a student and available on Desklib, a platform offering a range of study tools and resources for students.

RISK ASSESSMENT
REPORT
REPORT
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
Introduction.................................................................................................................................................1
Risk assessment methods........................................................................................................................1
Proposed Model......................................................................................................................................2
Advantages of risk assessment................................................................................................................2
Risk Assessment..........................................................................................................................................2
Determining risk..........................................................................................................................................3
Owner specification.....................................................................................................................................4
Threats........................................................................................................................................................6
Vulnerabilities..............................................................................................................................................7
Risk Assessment..........................................................................................................................................9
Risk identification........................................................................................................................................9
Benefits:....................................................................................................................................................10
Preventive measures.................................................................................................................................10
Summary...................................................................................................................................................11
Recommendation......................................................................................................................................11
References.................................................................................................................................................11
Introduction
In recent years the cloud computing became an integral part of any organization, May it belongs to any
business field including manufacturing, banking, education system, hospitals or government sector. All
these organizations maintain a basic infrastructure which consists of hardware, software and networking
equipment. The objective of this document is to analyze the network system of a cloud service provider
organization named Cloud-Centum. The company provides various cloud services such as storage, virtual
services for individual clients and for other organizations as well. The main output of this assessment is a
detailed risk assessment report.
According to ENISA, to analyze the risk assessment in a cloud computing environment, a use case must
be used and the goal should be identify and represent all the risks is a structured presentable format in a
table which includes the likelihood of risks, impact level and the references all possible vulnerabilities.
Risk assessment methods
To assess the risk in a cloud computing environment, following methods can be used:
1
Introduction.................................................................................................................................................1
Risk assessment methods........................................................................................................................1
Proposed Model......................................................................................................................................2
Advantages of risk assessment................................................................................................................2
Risk Assessment..........................................................................................................................................2
Determining risk..........................................................................................................................................3
Owner specification.....................................................................................................................................4
Threats........................................................................................................................................................6
Vulnerabilities..............................................................................................................................................7
Risk Assessment..........................................................................................................................................9
Risk identification........................................................................................................................................9
Benefits:....................................................................................................................................................10
Preventive measures.................................................................................................................................10
Summary...................................................................................................................................................11
Recommendation......................................................................................................................................11
References.................................................................................................................................................11
Introduction
In recent years the cloud computing became an integral part of any organization, May it belongs to any
business field including manufacturing, banking, education system, hospitals or government sector. All
these organizations maintain a basic infrastructure which consists of hardware, software and networking
equipment. The objective of this document is to analyze the network system of a cloud service provider
organization named Cloud-Centum. The company provides various cloud services such as storage, virtual
services for individual clients and for other organizations as well. The main output of this assessment is a
detailed risk assessment report.
According to ENISA, to analyze the risk assessment in a cloud computing environment, a use case must
be used and the goal should be identify and represent all the risks is a structured presentable format in a
table which includes the likelihood of risks, impact level and the references all possible vulnerabilities.
Risk assessment methods
To assess the risk in a cloud computing environment, following methods can be used:
1

What-if analysis: It is a type of brainstorming technique, in which the probability of threats and
vulnerabilities are identified and what would go wrong, if it would happen should also be find
out.
Checklist: The known threats or problems must be listed and verified. In this method, the quality
assessment will depend on the checklist.
Combination of what-if and checklist: In this method above both methods can be used in a
suitable combination. This is the most creative approach of risk assessment.
Hazard and operability study (HAZOP): It is a more detailed process of risk assessment. It needed
a strong leadership. It is time consuming and costly also.
Failure mode and effect analysis (FMEA): In this method of risk assessment, we can start from
any selected system and then thoroughly analyze each part of the system.
Fault tree analysis: In this method, we can start from a potentially affected event and then
analyze every possible cause behind it.
To maintain the security goal of the company, this report is being used to analyze the whole existing
architecture which is provided by the team of the organization. The outcome of this document is the
detailed risk assessment report.
Proposed Model
To accomplish the task, we will use the combination of checklist and security matrix assessment method
in this report. We will focus on all the possible threats and vulnerability and represent it in form of
matrix.
Advantages of risk assessment
The main benefits of risk assessment includes:
Minimized Cost
Enhanced scalability
Continuation plan in business
Collaboration
Flexible services
Timely automated updates
Risk Assessment
According to given infrastructure layout of company, the assessment of risk must be strongly adhere on
the ISO standards. Risk is unavoidable part for a cloud service provider organization as the data is
tremendously increasing day by day and it is important to identify the threats and vulnerabilities for any
company to maintain its goodwill in IT world (Vohradsky, 2017). According to ISO 31000, the risk
assessment must be based on governance policies, management reporting policies and planning of
analyzing mitigate risks. Risk assessment in a specific cloud service infrastructure is simple on one hand
but challenging on the other hand as, the security related business decisions are based on the
assessment of severity of business risk and the economical expenses which might be done to mitigate
2
vulnerabilities are identified and what would go wrong, if it would happen should also be find
out.
Checklist: The known threats or problems must be listed and verified. In this method, the quality
assessment will depend on the checklist.
Combination of what-if and checklist: In this method above both methods can be used in a
suitable combination. This is the most creative approach of risk assessment.
Hazard and operability study (HAZOP): It is a more detailed process of risk assessment. It needed
a strong leadership. It is time consuming and costly also.
Failure mode and effect analysis (FMEA): In this method of risk assessment, we can start from
any selected system and then thoroughly analyze each part of the system.
Fault tree analysis: In this method, we can start from a potentially affected event and then
analyze every possible cause behind it.
To maintain the security goal of the company, this report is being used to analyze the whole existing
architecture which is provided by the team of the organization. The outcome of this document is the
detailed risk assessment report.
Proposed Model
To accomplish the task, we will use the combination of checklist and security matrix assessment method
in this report. We will focus on all the possible threats and vulnerability and represent it in form of
matrix.
Advantages of risk assessment
The main benefits of risk assessment includes:
Minimized Cost
Enhanced scalability
Continuation plan in business
Collaboration
Flexible services
Timely automated updates
Risk Assessment
According to given infrastructure layout of company, the assessment of risk must be strongly adhere on
the ISO standards. Risk is unavoidable part for a cloud service provider organization as the data is
tremendously increasing day by day and it is important to identify the threats and vulnerabilities for any
company to maintain its goodwill in IT world (Vohradsky, 2017). According to ISO 31000, the risk
assessment must be based on governance policies, management reporting policies and planning of
analyzing mitigate risks. Risk assessment in a specific cloud service infrastructure is simple on one hand
but challenging on the other hand as, the security related business decisions are based on the
assessment of severity of business risk and the economical expenses which might be done to mitigate
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
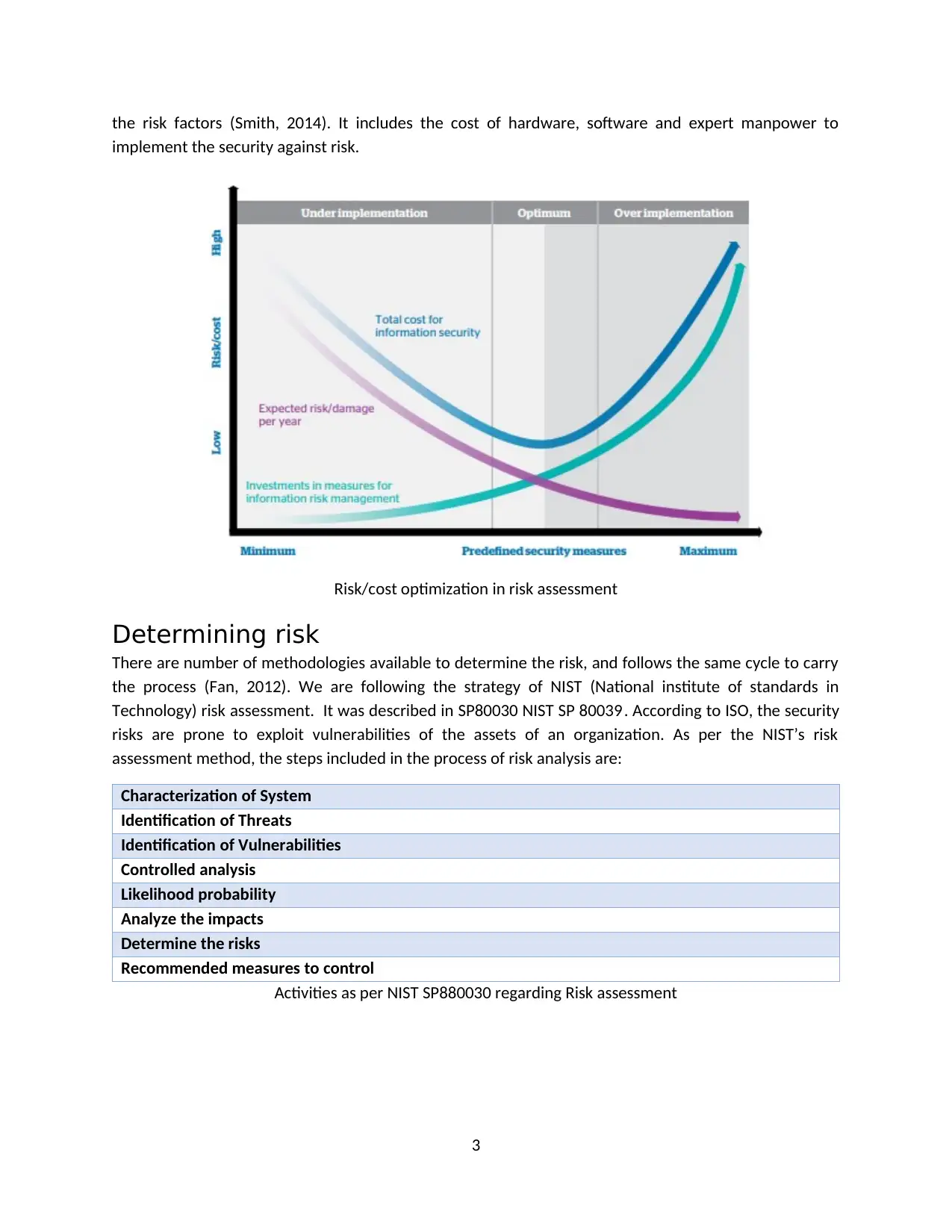
the risk factors (Smith, 2014). It includes the cost of hardware, software and expert manpower to
implement the security against risk.
Risk/cost optimization in risk assessment
Determining risk
There are number of methodologies available to determine the risk, and follows the same cycle to carry
the process (Fan, 2012). We are following the strategy of NIST (National institute of standards in
Technology) risk assessment. It was described in SP80030 NIST SP 80039. According to ISO, the security
risks are prone to exploit vulnerabilities of the assets of an organization. As per the NIST’s risk
assessment method, the steps included in the process of risk analysis are:
Characterization of System
Identification of Threats
Identification of Vulnerabilities
Controlled analysis
Likelihood probability
Analyze the impacts
Determine the risks
Recommended measures to control
Activities as per NIST SP880030 regarding Risk assessment
3
implement the security against risk.
Risk/cost optimization in risk assessment
Determining risk
There are number of methodologies available to determine the risk, and follows the same cycle to carry
the process (Fan, 2012). We are following the strategy of NIST (National institute of standards in
Technology) risk assessment. It was described in SP80030 NIST SP 80039. According to ISO, the security
risks are prone to exploit vulnerabilities of the assets of an organization. As per the NIST’s risk
assessment method, the steps included in the process of risk analysis are:
Characterization of System
Identification of Threats
Identification of Vulnerabilities
Controlled analysis
Likelihood probability
Analyze the impacts
Determine the risks
Recommended measures to control
Activities as per NIST SP880030 regarding Risk assessment
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
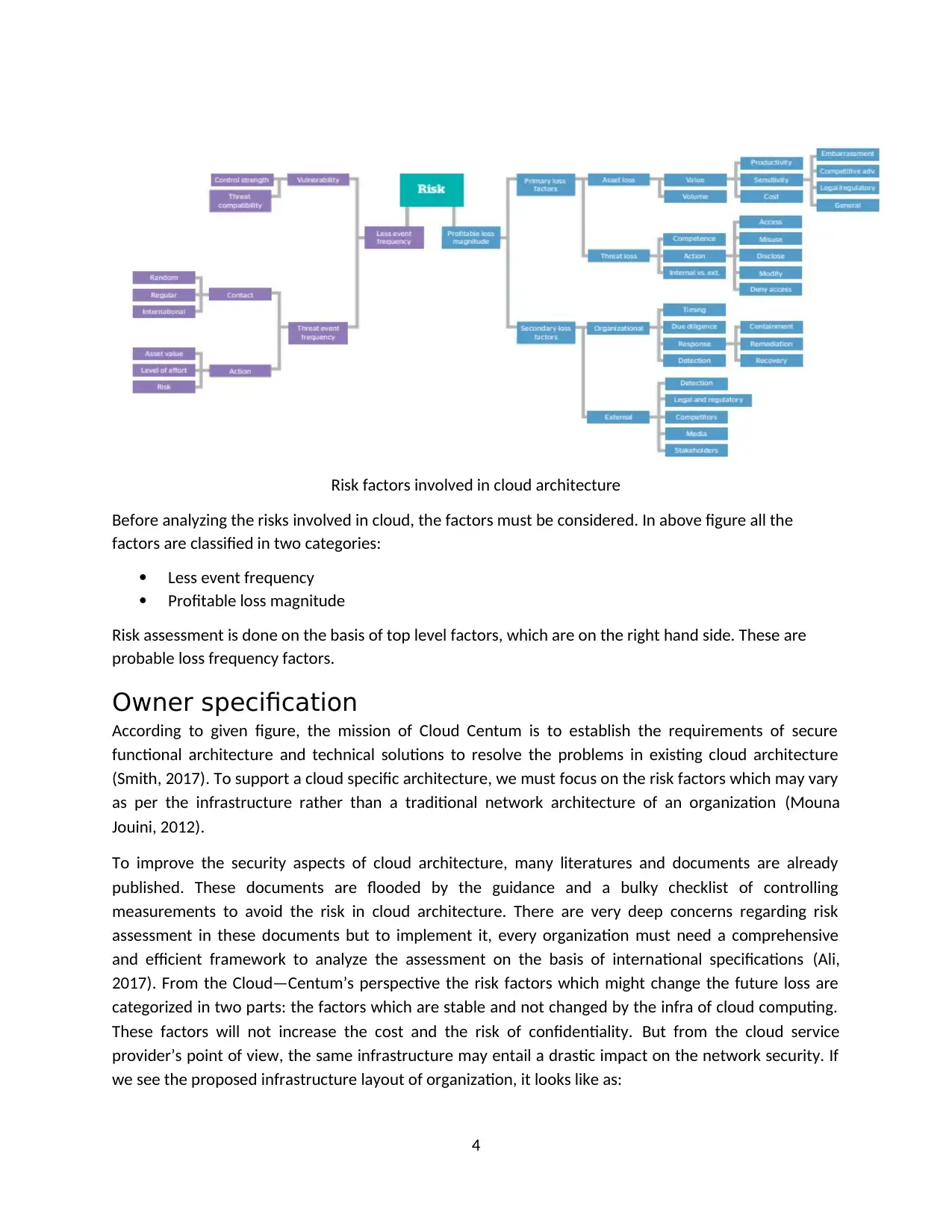
Risk factors involved in cloud architecture
Before analyzing the risks involved in cloud, the factors must be considered. In above figure all the
factors are classified in two categories:
Less event frequency
Profitable loss magnitude
Risk assessment is done on the basis of top level factors, which are on the right hand side. These are
probable loss frequency factors.
Owner specification
According to given figure, the mission of Cloud Centum is to establish the requirements of secure
functional architecture and technical solutions to resolve the problems in existing cloud architecture
(Smith, 2017). To support a cloud specific architecture, we must focus on the risk factors which may vary
as per the infrastructure rather than a traditional network architecture of an organization (Mouna
Jouini, 2012).
To improve the security aspects of cloud architecture, many literatures and documents are already
published. These documents are flooded by the guidance and a bulky checklist of controlling
measurements to avoid the risk in cloud architecture. There are very deep concerns regarding risk
assessment in these documents but to implement it, every organization must need a comprehensive
and efficient framework to analyze the assessment on the basis of international specifications (Ali,
2017). From the Cloud—Centum’s perspective the risk factors which might change the future loss are
categorized in two parts: the factors which are stable and not changed by the infra of cloud computing.
These factors will not increase the cost and the risk of confidentiality. But from the cloud service
provider’s point of view, the same infrastructure may entail a drastic impact on the network security. If
we see the proposed infrastructure layout of organization, it looks like as:
4
Before analyzing the risks involved in cloud, the factors must be considered. In above figure all the
factors are classified in two categories:
Less event frequency
Profitable loss magnitude
Risk assessment is done on the basis of top level factors, which are on the right hand side. These are
probable loss frequency factors.
Owner specification
According to given figure, the mission of Cloud Centum is to establish the requirements of secure
functional architecture and technical solutions to resolve the problems in existing cloud architecture
(Smith, 2017). To support a cloud specific architecture, we must focus on the risk factors which may vary
as per the infrastructure rather than a traditional network architecture of an organization (Mouna
Jouini, 2012).
To improve the security aspects of cloud architecture, many literatures and documents are already
published. These documents are flooded by the guidance and a bulky checklist of controlling
measurements to avoid the risk in cloud architecture. There are very deep concerns regarding risk
assessment in these documents but to implement it, every organization must need a comprehensive
and efficient framework to analyze the assessment on the basis of international specifications (Ali,
2017). From the Cloud—Centum’s perspective the risk factors which might change the future loss are
categorized in two parts: the factors which are stable and not changed by the infra of cloud computing.
These factors will not increase the cost and the risk of confidentiality. But from the cloud service
provider’s point of view, the same infrastructure may entail a drastic impact on the network security. If
we see the proposed infrastructure layout of organization, it looks like as:
4

We can see the architecture of company is broadly divided in two parts: the Internet and the Intranet.
The client can access the cloud services of organization through company premises or individual devices.
The request raised by the client firstly pass through the Firewall implemented in the network of cloud
service provider (Kaefer, 2010). The intranet plays very prominent role in given figure, which is the
private network of company. The DMZ server is the web and mail server which is responsible to store
and forward the Emails send by the clients and it also handles the sending and receiving of request
within the network or outside the private network of company (Ferkoun, 2014). It is recommended that
on both network there must be a strong intrusion detection system in form of Firewall to filter the
reliable and authenticated requests (Rouse, 2015). The proposed system also signifies the database
servers. After reviewing the above figure we can categorize the assets of organization in two forms:
Primary Assets: The assets which must be first implemented to perform certain kind of operations
(Jones, 2011). These assets work as the default assets. It create the super set of all the secondary assets.
a. The Site (The web applications and web services)
b. The cloud Database
c. The Virtual Server
d. The authentication server
e. The DMZ
f. The NOS (Network operating system)
g. The Firewall
Secondary Assets
a. The Firewall connected with internet
b. Other software
5
The client can access the cloud services of organization through company premises or individual devices.
The request raised by the client firstly pass through the Firewall implemented in the network of cloud
service provider (Kaefer, 2010). The intranet plays very prominent role in given figure, which is the
private network of company. The DMZ server is the web and mail server which is responsible to store
and forward the Emails send by the clients and it also handles the sending and receiving of request
within the network or outside the private network of company (Ferkoun, 2014). It is recommended that
on both network there must be a strong intrusion detection system in form of Firewall to filter the
reliable and authenticated requests (Rouse, 2015). The proposed system also signifies the database
servers. After reviewing the above figure we can categorize the assets of organization in two forms:
Primary Assets: The assets which must be first implemented to perform certain kind of operations
(Jones, 2011). These assets work as the default assets. It create the super set of all the secondary assets.
a. The Site (The web applications and web services)
b. The cloud Database
c. The Virtual Server
d. The authentication server
e. The DMZ
f. The NOS (Network operating system)
g. The Firewall
Secondary Assets
a. The Firewall connected with internet
b. Other software
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Threats
Most of the cloud services are easily prone to security issues. According to a report published in 2017 by
Cloud security spotlight, near about 30% of the organizations want a managed cloud service provider for
their cloud services (Anderson, 2018). 20% organizations are looking for security as a service providers,
so that their cloud must be on high monitoring all the time. Some of the most common threats which
might occur in proposed cloud architecture are:
Asset Threat Description
Site Web API Hacks
Malware
User awareness
While session handling is done
with the help of cookies in site,
the name of the user can steal.
In this situation an attacker can
also use the CSRF method for
hacking.
Users must aware about the
attachments, which might
produce the security threats in
their environment.
Database Data loss
Data breach
In this type of threat, the
database might affected by
unauthorized users and the
data can be breached.
To secure the database on
cloud, the most important way
is to provide password for strict
validation before connecting
with cloud database.
Virtual server DoS (Denial of services)
Virtual machine escape
In virtual environment,
hypervisors and the virtual
machines are the most common
resources. In this type of threat
the attacker can hack the virtual
machine from the remote
location. These threats are
mostly rare.
Authentication server Reliability and availability of
services
Secure data transmission
Malicious insiders
Account hijacking
The server used in the intranet
of company is called
authentication server. Attacker
may attack on this server, to get
the list of authenticated server.
NOS Ransomware This threat was recently found,
in which due to problem with
updates in OS, many systems
were affected. The effect of
threat was in form of money
demand.
DMZ Trojan Horse DMZ server is responsible for
6
Most of the cloud services are easily prone to security issues. According to a report published in 2017 by
Cloud security spotlight, near about 30% of the organizations want a managed cloud service provider for
their cloud services (Anderson, 2018). 20% organizations are looking for security as a service providers,
so that their cloud must be on high monitoring all the time. Some of the most common threats which
might occur in proposed cloud architecture are:
Asset Threat Description
Site Web API Hacks
Malware
User awareness
While session handling is done
with the help of cookies in site,
the name of the user can steal.
In this situation an attacker can
also use the CSRF method for
hacking.
Users must aware about the
attachments, which might
produce the security threats in
their environment.
Database Data loss
Data breach
In this type of threat, the
database might affected by
unauthorized users and the
data can be breached.
To secure the database on
cloud, the most important way
is to provide password for strict
validation before connecting
with cloud database.
Virtual server DoS (Denial of services)
Virtual machine escape
In virtual environment,
hypervisors and the virtual
machines are the most common
resources. In this type of threat
the attacker can hack the virtual
machine from the remote
location. These threats are
mostly rare.
Authentication server Reliability and availability of
services
Secure data transmission
Malicious insiders
Account hijacking
The server used in the intranet
of company is called
authentication server. Attacker
may attack on this server, to get
the list of authenticated server.
NOS Ransomware This threat was recently found,
in which due to problem with
updates in OS, many systems
were affected. The effect of
threat was in form of money
demand.
DMZ Trojan Horse DMZ server is responsible for
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Email and web server. The mails
of clients are stored and
processed on this server. There
may be chances of Trojan horse
virus, which may enter in the
intranet of company through
attachments.
Firewall Insecurity
Worms
Spear phishing
Firewall is responsible for
filtration of data packets. Due to
problem in security the worms
may enter in the network of
organization and slowly attack
on all the systems of
organization.
Spear phishing is a threat, in
which an attempt is made to
capture the private information
of some users. It may be done
through emails or other mode
of communication. This kind of
threat is deceiving someone.
Vulnerabilities
The vulnerabilities of cloud architecture are related with the web applications, virtual machines and
cryptography (Piplode, 2012). According to CVE the vulnerability is defined as the weakness in hardware,
software component or the computational logic. Due to which the negative impacts like integrity,
confidentiality and availability might occur. Vulnerabilities can be explained as:
Asset Vulnerability Description CVE number Severity/
Likelihood/
Site Session Riding
Session hijacking
Vulnerability
related with
sessions are very
common in web
technologies. It
occurs because of
the HTTP
protocol, as this
protocol is
stateless protocol
and to maintain
the state, other
techniques can be
used, such as:
session handling,
cookies, URL
CVE-2017-11398 High/ Frequent
7
of clients are stored and
processed on this server. There
may be chances of Trojan horse
virus, which may enter in the
intranet of company through
attachments.
Firewall Insecurity
Worms
Spear phishing
Firewall is responsible for
filtration of data packets. Due to
problem in security the worms
may enter in the network of
organization and slowly attack
on all the systems of
organization.
Spear phishing is a threat, in
which an attempt is made to
capture the private information
of some users. It may be done
through emails or other mode
of communication. This kind of
threat is deceiving someone.
Vulnerabilities
The vulnerabilities of cloud architecture are related with the web applications, virtual machines and
cryptography (Piplode, 2012). According to CVE the vulnerability is defined as the weakness in hardware,
software component or the computational logic. Due to which the negative impacts like integrity,
confidentiality and availability might occur. Vulnerabilities can be explained as:
Asset Vulnerability Description CVE number Severity/
Likelihood/
Site Session Riding
Session hijacking
Vulnerability
related with
sessions are very
common in web
technologies. It
occurs because of
the HTTP
protocol, as this
protocol is
stateless protocol
and to maintain
the state, other
techniques can be
used, such as:
session handling,
cookies, URL
CVE-2017-11398 High/ Frequent
7

rewriting etc.
Cloud Database Data Recovery
Data Breach
Cloud database is
an important
asset of cloud
service provider.
It is mainly a
resource of SaaS
(Lukan, 2014).
Clients can save
their information
on cloud
database, in case
of data loss,
efficient data
recovery must be
used to maintain
the reliability.
CVE-2015-3456 Serious/Occasional
Virtual Server Memory
management
implementation
in VM
Virtual servers
were not able to
restrict the guest
users to access
the VMM work
area
CVE-2010-1225 Medium/ Remote
Authentication
Server
User Account
breaches
In this
vulnerability the
DS3 server was
not able to stop
attackers to inject
the error pages in
text format
through message
parameters.
CVE-2013-4098 Medium/
Occasional
DMZ SQL injections Through SQL
injections
attackers may
access the
confidential
information of
users
CVE-2015-6195 High/ probable
NOS Improper
handling of
requests
It was related with
stack based buffer
overflow and the
downloader
manager will not
be able to install
the downloaded
files.
CVE-2008-5364
119
Serious/
Occasional
8
Cloud Database Data Recovery
Data Breach
Cloud database is
an important
asset of cloud
service provider.
It is mainly a
resource of SaaS
(Lukan, 2014).
Clients can save
their information
on cloud
database, in case
of data loss,
efficient data
recovery must be
used to maintain
the reliability.
CVE-2015-3456 Serious/Occasional
Virtual Server Memory
management
implementation
in VM
Virtual servers
were not able to
restrict the guest
users to access
the VMM work
area
CVE-2010-1225 Medium/ Remote
Authentication
Server
User Account
breaches
In this
vulnerability the
DS3 server was
not able to stop
attackers to inject
the error pages in
text format
through message
parameters.
CVE-2013-4098 Medium/
Occasional
DMZ SQL injections Through SQL
injections
attackers may
access the
confidential
information of
users
CVE-2015-6195 High/ probable
NOS Improper
handling of
requests
It was related with
stack based buffer
overflow and the
downloader
manager will not
be able to install
the downloaded
files.
CVE-2008-5364
119
Serious/
Occasional
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Firewall in
intranet
Unauthorized
access
The attackers are
able to access the
arbitrary files
through fake
encode URL
CVE-2006-3885 Medium/
Improbable
Firewall in
internet
Fake IKE (Internet
key exchange)
By sending a fake
IKE, the attackers
are able to access
sensitive
information of
cloud users.
CVE-2004-2679 Medium/
Frequent
Risk Assessment
The risk is calculated on the basis of probability of the incidence and the negative impact it will impose
on the business (Shackleford, 2017). The likelihood or probability depends on the model or architecture
of cloud. The risk assessment can be shown as below having scaling factor in between 0 to 8. It is
measured against the risk acceptance criteria.
Here we are representing the risk factor as:
Low risk: 0-2
Medium risk: 3-5
High risk: 6-8
Likelihood
of scenario
Very Low
(very rare)
Low (Rare) Medium
(possible)
High
(Likely)
Very High
(Frequent)
Impact on
business
Very low 0 1 2 3 4
Low 1 2 3 4 5
Medium 2 3 4 5 6
High 3 4 5 6 7
Very High 4 5 6 7
Risk identification
The representation of risk assessment can be shown using Boston grid. To perform the risk analysis of
not achieving target, the core reasons behind that and priority of the issues where the necessary actions
can be taken, the matrix representation is the best tool (lewis, 2016). It is important tool from the
management point of view:
9
intranet
Unauthorized
access
The attackers are
able to access the
arbitrary files
through fake
encode URL
CVE-2006-3885 Medium/
Improbable
Firewall in
internet
Fake IKE (Internet
key exchange)
By sending a fake
IKE, the attackers
are able to access
sensitive
information of
cloud users.
CVE-2004-2679 Medium/
Frequent
Risk Assessment
The risk is calculated on the basis of probability of the incidence and the negative impact it will impose
on the business (Shackleford, 2017). The likelihood or probability depends on the model or architecture
of cloud. The risk assessment can be shown as below having scaling factor in between 0 to 8. It is
measured against the risk acceptance criteria.
Here we are representing the risk factor as:
Low risk: 0-2
Medium risk: 3-5
High risk: 6-8
Likelihood
of scenario
Very Low
(very rare)
Low (Rare) Medium
(possible)
High
(Likely)
Very High
(Frequent)
Impact on
business
Very low 0 1 2 3 4
Low 1 2 3 4 5
Medium 2 3 4 5 6
High 3 4 5 6 7
Very High 4 5 6 7
Risk identification
The representation of risk assessment can be shown using Boston grid. To perform the risk analysis of
not achieving target, the core reasons behind that and priority of the issues where the necessary actions
can be taken, the matrix representation is the best tool (lewis, 2016). It is important tool from the
management point of view:
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Benefits:
1. It enforces the major risks where the support allocation is preferred to resolve the limitation of
resources.
2. It highlights the major areas where the urgent steps are needed to resolve potential threats and
appropriate management actions.
3. Concerned environmental points can be identified.
4. Easily finding the gaps which are critical and required fast actions.
Preventive measures
To prevent the chances of security concerns, some of the important approaches which can be beneficial
in cloud services are:
Support in investigations: Such type of tools are provided to the customers, so that they can ensure the
security and privacy of their data. The investigation of illegal activities is quite tough due to huge
amount of data dispersed geographically.
Secured the network: In accessing the web services, user can deny by using the IP spoofing, which is not
recommended as per the security concern. To resolve this problem we can recommend the digital
signature technique. For secured communication either HTTPS of SSL protocols are recommended
(Ravera, 2018).
Encryption algorithm: It is recommended that the information of users must be saved in form of
encrypted data. Sometimes the encryption makes complicated data which is totally unusable and cannot
be easily available. It is recommended that the encryption algorithm must be designed by experienced
programmers.
Data backup: The security of data is the most important factor to achieve the customer’s satisfaction.
Natural disaster may occur any time so, a proper stand by secondary devices to maintain the backup of
data is recommended.
Satisfaction of customers: To satisfy the customers, the cloud service providers must maintain some
standards and provide timely facilities to the customers as per the government rules, so that customers
10
1. It enforces the major risks where the support allocation is preferred to resolve the limitation of
resources.
2. It highlights the major areas where the urgent steps are needed to resolve potential threats and
appropriate management actions.
3. Concerned environmental points can be identified.
4. Easily finding the gaps which are critical and required fast actions.
Preventive measures
To prevent the chances of security concerns, some of the important approaches which can be beneficial
in cloud services are:
Support in investigations: Such type of tools are provided to the customers, so that they can ensure the
security and privacy of their data. The investigation of illegal activities is quite tough due to huge
amount of data dispersed geographically.
Secured the network: In accessing the web services, user can deny by using the IP spoofing, which is not
recommended as per the security concern. To resolve this problem we can recommend the digital
signature technique. For secured communication either HTTPS of SSL protocols are recommended
(Ravera, 2018).
Encryption algorithm: It is recommended that the information of users must be saved in form of
encrypted data. Sometimes the encryption makes complicated data which is totally unusable and cannot
be easily available. It is recommended that the encryption algorithm must be designed by experienced
programmers.
Data backup: The security of data is the most important factor to achieve the customer’s satisfaction.
Natural disaster may occur any time so, a proper stand by secondary devices to maintain the backup of
data is recommended.
Satisfaction of customers: To satisfy the customers, the cloud service providers must maintain some
standards and provide timely facilities to the customers as per the government rules, so that customers
10

can ensure the security and reliability of their data. Maintaining the standards will create the goodwill of
company and it ensures the operational efficiency of the organization.
Summary
The cloud computing is the necessity of organizations in present scenario. This report is the conclusion
of risk assessment of cloud service provider. It will help to the organization to uncover the main risk
factors, which might occur in the network. It will support in maintaining the list of threats and
vulnerabilities according to their severity level so that a proper plan can be taken to resolve them. Risk
assessment report is to help in avoiding the issues and thus minimizing the cost of resolving them later
on in any organization.
Recommendation
As per the study of various considering factors of cloud architecture of organization, it is concluded that
the growing usage of cloud computing is the only way of fulfilling the requirements of various individuals
and organizations. Earlier the cloud adoption was not an easy decision for companies, but as the data
security and the reliability is the main concern for the cloud service providers nowadays, it has changed
the scenario. Now customers are more satisfied for their data security and services availability. It is
recommended for Cloud Centum that strong system administration must collaborate with service
delivery and audit trails.
References
Ali, F., 2017. Supercloud” to the Rescue? New Architecture Could Make Cloud Computing More Secure.
[Online]
Available at: http://ieeexplore-spotlight.ieee.org/article/multi-cloud-architecture-supercloud-u-cloud/
[Accessed 22 April 2018].
Anderson, B., 2018. cloud security threats. [Online]
Available at: https://www.tierpoint.com/top-5-cloud-data-security-threats-in-2018/
[Accessed 22 april 2018].
Fan, C. K., 2012. Risk management strategy, Taiwan: Department of Risk Management and Insurance.
Ferkoun, M., 2014. common usages of cloud computing. [Online]
Available at: https://www.ibm.com/blogs/cloud-computing/2014/02/06/top-7-most-common-uses-of-
cloud-computing/
[Accessed 22 April 2018].
Jones, M., 2011. Primary and secondary assets. [Online]
Available at: https://support.symantec.com/en_US/article.HOWTO40975.html
[Accessed 22 april 2018].
Kaefer, G., 2010. Cloud architecture. [Online]
Available at: https://resources.sei.cmu.edu/library/asset-view.cfm?assetid=20298
[Accessed 22 April 2018].
11
company and it ensures the operational efficiency of the organization.
Summary
The cloud computing is the necessity of organizations in present scenario. This report is the conclusion
of risk assessment of cloud service provider. It will help to the organization to uncover the main risk
factors, which might occur in the network. It will support in maintaining the list of threats and
vulnerabilities according to their severity level so that a proper plan can be taken to resolve them. Risk
assessment report is to help in avoiding the issues and thus minimizing the cost of resolving them later
on in any organization.
Recommendation
As per the study of various considering factors of cloud architecture of organization, it is concluded that
the growing usage of cloud computing is the only way of fulfilling the requirements of various individuals
and organizations. Earlier the cloud adoption was not an easy decision for companies, but as the data
security and the reliability is the main concern for the cloud service providers nowadays, it has changed
the scenario. Now customers are more satisfied for their data security and services availability. It is
recommended for Cloud Centum that strong system administration must collaborate with service
delivery and audit trails.
References
Ali, F., 2017. Supercloud” to the Rescue? New Architecture Could Make Cloud Computing More Secure.
[Online]
Available at: http://ieeexplore-spotlight.ieee.org/article/multi-cloud-architecture-supercloud-u-cloud/
[Accessed 22 April 2018].
Anderson, B., 2018. cloud security threats. [Online]
Available at: https://www.tierpoint.com/top-5-cloud-data-security-threats-in-2018/
[Accessed 22 april 2018].
Fan, C. K., 2012. Risk management strategy, Taiwan: Department of Risk Management and Insurance.
Ferkoun, M., 2014. common usages of cloud computing. [Online]
Available at: https://www.ibm.com/blogs/cloud-computing/2014/02/06/top-7-most-common-uses-of-
cloud-computing/
[Accessed 22 April 2018].
Jones, M., 2011. Primary and secondary assets. [Online]
Available at: https://support.symantec.com/en_US/article.HOWTO40975.html
[Accessed 22 april 2018].
Kaefer, G., 2010. Cloud architecture. [Online]
Available at: https://resources.sei.cmu.edu/library/asset-view.cfm?assetid=20298
[Accessed 22 April 2018].
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





