IT Cloud Security Risk Analysis Report: Risk Assessment Project
VerifiedAdded on 2023/06/07
|21
|5402
|335
Report
AI Summary
This report provides a comprehensive risk assessment of cloud security within IT projects. It covers various aspects of cloud computing, including its components (Platform as a Service, Software as a Service, and Infrastructure as a Service), risk assessment processes, and potential risks (organizational, technical, and legal). The report also discusses major cloud security threats and vulnerabilities, their effects on organizations, and proposes control measures. The literature review highlights protection mechanisms against risks, emphasizing the importance of control measures, encryption, and updated access control tools. The document concludes with a summary of key findings and recommendations for mitigating cloud security risks.

Running head: Cloud Security Risk Analysis Report 1
IT Cloud Security Risk Assessment Report
Professors Name
Affiliate Institution
Date
IT Cloud Security Risk Assessment Report
Professors Name
Affiliate Institution
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT Cloud Security Risk Analysis Report 2
Executive summary
Computing resources can be offered through the storage cloud. Cloud computing as a
technology advancenment provides service for storage of data and users may acquire these data
through the use of the internet. Resources which can be stored in the cloud includes programs
and applications, data and information. Examples include email management and software
storage.
The target groups upon the implementation of the cloud computing includes the
following; private users, public users, members of the community and the hybrid group. The
private group will have their services accessed from different location. Unlike the public where
bidding process is involved so that anyone will be able to give out the best proposal is given the
offer.
The main functional parts in the cloud include the following three models
Platform as a service- the software programs are installed in this cloud model
Software as a service- this is where software programs are downloaded and
uploaded
Infrastructure as a service- ensures that all network devices are connected through
the right protocol.
Executive summary
Computing resources can be offered through the storage cloud. Cloud computing as a
technology advancenment provides service for storage of data and users may acquire these data
through the use of the internet. Resources which can be stored in the cloud includes programs
and applications, data and information. Examples include email management and software
storage.
The target groups upon the implementation of the cloud computing includes the
following; private users, public users, members of the community and the hybrid group. The
private group will have their services accessed from different location. Unlike the public where
bidding process is involved so that anyone will be able to give out the best proposal is given the
offer.
The main functional parts in the cloud include the following three models
Platform as a service- the software programs are installed in this cloud model
Software as a service- this is where software programs are downloaded and
uploaded
Infrastructure as a service- ensures that all network devices are connected through
the right protocol.

IT Cloud Security Risk Analysis Report 3
Contents
ecutive summaryEx ........................................................................................................................................2
iterature reviewL .........................................................................................................................................4
ntroductionI ...................................................................................................................................................6
mportant cloud componentsI ..................................................................................................................8
Risk assessment process..............................................................................................................................9
Risks....................................................................................................................................................... 11
rganizational risksO ..................................................................................................................................12
echnical risksT ........................................................................................................................................13
egal risksL ..............................................................................................................................................14
Major cloud security threats and vulnerabilities.........................................................................................14
ff
ects of cloud security on the organizationsE ............................................................................................16
Control measures......................................................................................................................................17
Conclusion.................................................................................................................................................18
References.................................................................................................................................................20
Contents
ecutive summaryEx ........................................................................................................................................2
iterature reviewL .........................................................................................................................................4
ntroductionI ...................................................................................................................................................6
mportant cloud componentsI ..................................................................................................................8
Risk assessment process..............................................................................................................................9
Risks....................................................................................................................................................... 11
rganizational risksO ..................................................................................................................................12
echnical risksT ........................................................................................................................................13
egal risksL ..............................................................................................................................................14
Major cloud security threats and vulnerabilities.........................................................................................14
ff
ects of cloud security on the organizationsE ............................................................................................16
Control measures......................................................................................................................................17
Conclusion.................................................................................................................................................18
References.................................................................................................................................................20
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

IT Cloud Security Risk Analysis Report 4
Literature review
The organization should also make use of control measures concerning cloud security
issues and may stay away from them. Likewise, if there should arise an occurrence of an event,
the company will be prepared to control the harm and recover from the fiasco in negligible
reaction time (Mather, Kumaraswamy & Latif 2009).
Recurrence of a problem is one of the security estimates that will be utilized to shield the
cloud applications from a range of related risks. The hackers won't have the capacity to stick to
the system if the recurrence is adjusted at normal cycles. The cloud APIs can prevent security
issues by just giving out an alert to the users and admins to alert them on the problem issue. The
admins will immediately block the intruder from further appearances. This a security concern to
all the users of the cloud storage model. The popup message can be link to the email to ensure
that a quick alert is passed to all the admins (Robinson, Vogt & Wagealla, 2006). The utilization
of encryption of the considerable number of informational indexes will be influenced obligatory
with the goal that the attackers will bomb in the abuse of the data sets.
The verification plans utilized in the cloud storage will likewise be improved to stay
away from information ruptures. Since cloud platforms are prone to various types of attacks such
as the brute force attacks, a confirmation, and multi-overlay verification plans are used to keep
away from those threats from infringing of access control (Robinson, Vogt & Wagealla, 2006).
Organizations must not limit to the well-established cloud access control measures. The
more up to date types of access control tools in the cloud will be utilized and incorporated in the
application (Robinson, Vogt & Wagealla, 2006).
Literature review
The organization should also make use of control measures concerning cloud security
issues and may stay away from them. Likewise, if there should arise an occurrence of an event,
the company will be prepared to control the harm and recover from the fiasco in negligible
reaction time (Mather, Kumaraswamy & Latif 2009).
Recurrence of a problem is one of the security estimates that will be utilized to shield the
cloud applications from a range of related risks. The hackers won't have the capacity to stick to
the system if the recurrence is adjusted at normal cycles. The cloud APIs can prevent security
issues by just giving out an alert to the users and admins to alert them on the problem issue. The
admins will immediately block the intruder from further appearances. This a security concern to
all the users of the cloud storage model. The popup message can be link to the email to ensure
that a quick alert is passed to all the admins (Robinson, Vogt & Wagealla, 2006). The utilization
of encryption of the considerable number of informational indexes will be influenced obligatory
with the goal that the attackers will bomb in the abuse of the data sets.
The verification plans utilized in the cloud storage will likewise be improved to stay
away from information ruptures. Since cloud platforms are prone to various types of attacks such
as the brute force attacks, a confirmation, and multi-overlay verification plans are used to keep
away from those threats from infringing of access control (Robinson, Vogt & Wagealla, 2006).
Organizations must not limit to the well-established cloud access control measures. The
more up to date types of access control tools in the cloud will be utilized and incorporated in the
application (Robinson, Vogt & Wagealla, 2006).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT Cloud Security Risk Analysis Report 5
Innovation is quickly progressing and the use of innovation in the field of security
controls has been noteworthy. The ascent of cyberattacks and other electronic attacks has
prompted the rise and improvement of specialized devices and controls for security. Malware
attacks on the cloud applications will be controlled and identified with the mix of the application
with the most recent attacker of malware devices (Takabi, 2010). Denial of service devices and
dispersed software of managing and controlling attacks will be identified and counteracted with
the denial of service devices.
The point of the association will not be limited towards the counteractive action and
recognition of the attacks. Be that as it may, the event of such issues will be maintained a
strategic distance from and the success must be done towards that path also. One of such
estimates that will be utilized will benefit reviewing of the service. The procedure will rattle off
every one of the administrations being done on the cloud server. Every one of the points of
interest related with the system ports and hubs and the cloud conventions will be presented by
this procedure. An ongoing introduction and investigation of the application administrations will
be made accessible. Another procedure that will be utilized in a similar way will be document
reviewing (Krutz & Vines, 2010).
Disaster recovery and risk control are also the instruments that will prompt the measure
of the data and informational collections. There must be a catastrophic recovery plan created for
the task with the goal that all types of security issues might be taken care of and handled. There
are computerized reinforcement and recovery instruments and plans that must be incorporated in
the cloud service providers. These instruments will keep a duplicate of the informational indexes
at a substitute area. The application will be taken back to the recovery state on account of the
service provider.
Innovation is quickly progressing and the use of innovation in the field of security
controls has been noteworthy. The ascent of cyberattacks and other electronic attacks has
prompted the rise and improvement of specialized devices and controls for security. Malware
attacks on the cloud applications will be controlled and identified with the mix of the application
with the most recent attacker of malware devices (Takabi, 2010). Denial of service devices and
dispersed software of managing and controlling attacks will be identified and counteracted with
the denial of service devices.
The point of the association will not be limited towards the counteractive action and
recognition of the attacks. Be that as it may, the event of such issues will be maintained a
strategic distance from and the success must be done towards that path also. One of such
estimates that will be utilized will benefit reviewing of the service. The procedure will rattle off
every one of the administrations being done on the cloud server. Every one of the points of
interest related with the system ports and hubs and the cloud conventions will be presented by
this procedure. An ongoing introduction and investigation of the application administrations will
be made accessible. Another procedure that will be utilized in a similar way will be document
reviewing (Krutz & Vines, 2010).
Disaster recovery and risk control are also the instruments that will prompt the measure
of the data and informational collections. There must be a catastrophic recovery plan created for
the task with the goal that all types of security issues might be taken care of and handled. There
are computerized reinforcement and recovery instruments and plans that must be incorporated in
the cloud service providers. These instruments will keep a duplicate of the informational indexes
at a substitute area. The application will be taken back to the recovery state on account of the
service provider.

IT Cloud Security Risk Analysis Report 6
Introduction
Cloud computing is proving a model that is utilize the opportunity to raise the ability of a
business to grow rapidly. Cloud computing utilize the internet as a resource to ensure its quick
delivery of service. There are some major components which must be there for the storage cloud
to exist. The following components materials are needed;
Hardware components which include the site servers, desktop computers, and the transfer
media. Without these components, one will not be able to access the cloud storage service.
Without hardware devices, cloud computing could not be inexistence and therefore security risks
concerning hardware devices have to be taken into account. Hardware devices must be well kept
in a save place where the security is of high priority. Cloud servers are hardware devices which
assist several customers to store their large amount of data in the storage cloud because they have
a lot of space to accommodate large amount of data. These kind of servers are of high speed and
they are capable of processing large data formats at a time (Krutz & Vines, 2010).
Software components. Software is one of the major item that is needed for both the cloud
management and its accessibility. Cloud infrastructure requires the APIs which assist during the
management. The interface of the cloud is the overall API which will help the users to actually
understand what they are supposed to do in the cloud.
Cloud computing consist of high level instant scalability of network resources e.g.
database, memory, and hardware. The cloud computing is also very flexible and can easily be
expanded. Management systems and abstracted materials and resources are also available in the
cloud. So for this case, cloud computing has really lead to an increase in reliability and the
productivity of various organization because it has made the work become easier for the
Introduction
Cloud computing is proving a model that is utilize the opportunity to raise the ability of a
business to grow rapidly. Cloud computing utilize the internet as a resource to ensure its quick
delivery of service. There are some major components which must be there for the storage cloud
to exist. The following components materials are needed;
Hardware components which include the site servers, desktop computers, and the transfer
media. Without these components, one will not be able to access the cloud storage service.
Without hardware devices, cloud computing could not be inexistence and therefore security risks
concerning hardware devices have to be taken into account. Hardware devices must be well kept
in a save place where the security is of high priority. Cloud servers are hardware devices which
assist several customers to store their large amount of data in the storage cloud because they have
a lot of space to accommodate large amount of data. These kind of servers are of high speed and
they are capable of processing large data formats at a time (Krutz & Vines, 2010).
Software components. Software is one of the major item that is needed for both the cloud
management and its accessibility. Cloud infrastructure requires the APIs which assist during the
management. The interface of the cloud is the overall API which will help the users to actually
understand what they are supposed to do in the cloud.
Cloud computing consist of high level instant scalability of network resources e.g.
database, memory, and hardware. The cloud computing is also very flexible and can easily be
expanded. Management systems and abstracted materials and resources are also available in the
cloud. So for this case, cloud computing has really lead to an increase in reliability and the
productivity of various organization because it has made the work become easier for the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
IT Cloud Security Risk Analysis Report 7
customers to access resources and information at their own comfort. Also in case of any serious
damage like fire outbreak, cloud storage can allow us to access the information even if the
storage physical servers got burnt down. It is the best when it comes to the recovery of the data
loss after the disaster (Mather, Kumaraswamy & Latif 2009).
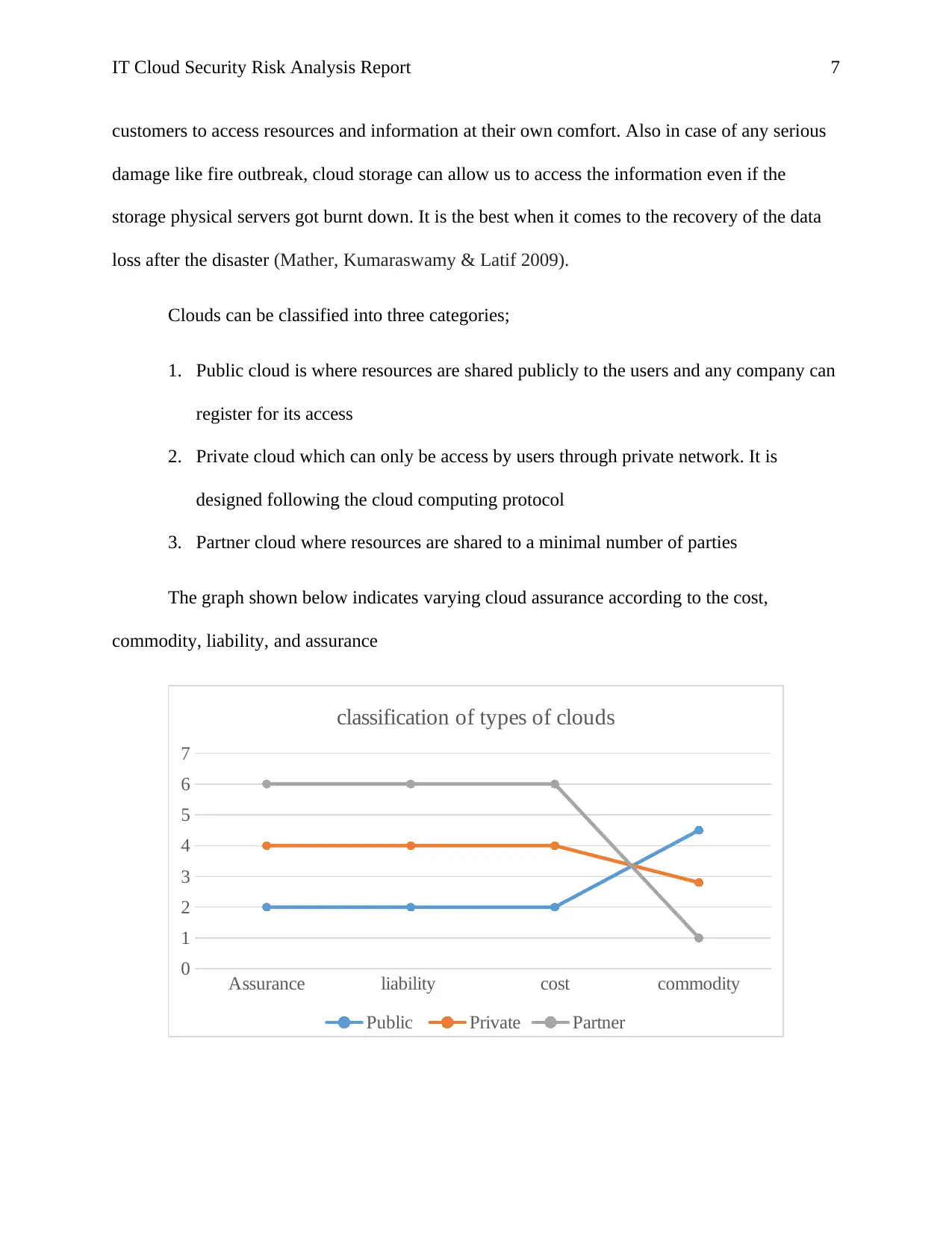
Clouds can be classified into three categories;
1. Public cloud is where resources are shared publicly to the users and any company can
register for its access
2. Private cloud which can only be access by users through private network. It is
designed following the cloud computing protocol
3. Partner cloud where resources are shared to a minimal number of parties
The graph shown below indicates varying cloud assurance according to the cost,
commodity, liability, and assurance
Assurance liability cost commodity
0
1
2
3
4
5
6
7
classification of types of clouds
Public Private Partner
customers to access resources and information at their own comfort. Also in case of any serious
damage like fire outbreak, cloud storage can allow us to access the information even if the
storage physical servers got burnt down. It is the best when it comes to the recovery of the data
loss after the disaster (Mather, Kumaraswamy & Latif 2009).
Clouds can be classified into three categories;
1. Public cloud is where resources are shared publicly to the users and any company can
register for its access
2. Private cloud which can only be access by users through private network. It is
designed following the cloud computing protocol
3. Partner cloud where resources are shared to a minimal number of parties
The graph shown below indicates varying cloud assurance according to the cost,
commodity, liability, and assurance
Assurance liability cost commodity
0
1
2
3
4
5
6
7
classification of types of clouds
Public Private Partner
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT Cloud Security Risk Analysis Report 8
Important cloud components
Cloud computing can be categorized in three major components which includes;
Platform as a service, this provide a platform in which the hardware and software
products are provide by the third party user. This makes it possible for all the on demand tools
and software available at any given time over the cloud. The application can be run without
maintaining any premise within your company. (Pearson, 2013).The main purpose of this cloud
model is to provide an environment through which we can install programs and device drivers.
Platform as a service provides a computing and editing platforms where we can test different
kind of software.
Software as a service- this is the cloud storage where all the applications and programs
are stored over the internet. This cloud model gives a platform in which software application are
shared and customers can access them through the internet. Every application required by the
clients can be downloaded from this model at any given time once needed. These resources are
accessed by users through the web browsers. Software that are on demand for commercial use
can be accessed from this model cloud(Mather et al, 2009). The software which can be located in
this platform include the on-demand software, hosted systems and web based applications.
Infrastructure as a service- this is a cloud storage which is managed over the internet.
The high demand will be accommodated because this service is highly scalable and supports as
many clients as possible. Infrastructure as a service enables one to reduce the expenses of buying
your own servers and installing your own datacenter which is so costly. In terms of security
storage, this kind of service is more secure than when you have your own data centers (Pearson,
2013).This is because your employees has the only role of entering the data into the cloud.
Important cloud components
Cloud computing can be categorized in three major components which includes;
Platform as a service, this provide a platform in which the hardware and software
products are provide by the third party user. This makes it possible for all the on demand tools
and software available at any given time over the cloud. The application can be run without
maintaining any premise within your company. (Pearson, 2013).The main purpose of this cloud
model is to provide an environment through which we can install programs and device drivers.
Platform as a service provides a computing and editing platforms where we can test different
kind of software.
Software as a service- this is the cloud storage where all the applications and programs
are stored over the internet. This cloud model gives a platform in which software application are
shared and customers can access them through the internet. Every application required by the
clients can be downloaded from this model at any given time once needed. These resources are
accessed by users through the web browsers. Software that are on demand for commercial use
can be accessed from this model cloud(Mather et al, 2009). The software which can be located in
this platform include the on-demand software, hosted systems and web based applications.
Infrastructure as a service- this is a cloud storage which is managed over the internet.
The high demand will be accommodated because this service is highly scalable and supports as
many clients as possible. Infrastructure as a service enables one to reduce the expenses of buying
your own servers and installing your own datacenter which is so costly. In terms of security
storage, this kind of service is more secure than when you have your own data centers (Pearson,
2013).This is because your employees has the only role of entering the data into the cloud.

IT Cloud Security Risk Analysis Report 9
Infrastructure as a service gives services like hosting of websites, testing and development,
storage and recovery backups and big data analysis
Despite all these important features of cloud computing, the fact remains that cloud
storage service is a target to attackers. Therefore it brings the issue of being a serious security
threat to the organizations who use these services to run and manage their businesses. As it is
known that because of the invention of high speed network, security risks has rampantly
increased. This has brought up the fear of how information are kept secured over this cloud
service.
Risk assessment process
During the risk analysis about cloud computing, a process flow was used. This process
allowed the project team to document the report after conducting some research about this cloud
security service. Water fall process flow was used to gather and analyzed the results collected
during the research (Pearson, 2013).The research which was done gathers all the importance and
the threats that may be caused by cloud computing to the users.
Risk
evaluation
Problem
identificati
on
Reporting
and
monitoring
Risk
controls
Risk
analysis
Infrastructure as a service gives services like hosting of websites, testing and development,
storage and recovery backups and big data analysis
Despite all these important features of cloud computing, the fact remains that cloud
storage service is a target to attackers. Therefore it brings the issue of being a serious security
threat to the organizations who use these services to run and manage their businesses. As it is
known that because of the invention of high speed network, security risks has rampantly
increased. This has brought up the fear of how information are kept secured over this cloud
service.
Risk assessment process
During the risk analysis about cloud computing, a process flow was used. This process
allowed the project team to document the report after conducting some research about this cloud
security service. Water fall process flow was used to gather and analyzed the results collected
during the research (Pearson, 2013).The research which was done gathers all the importance and
the threats that may be caused by cloud computing to the users.
Risk
evaluation
Problem
identificati
on
Reporting
and
monitoring
Risk
controls
Risk
analysis
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

IT Cloud Security Risk Analysis Report 10
During the research, the above process was followed where the problem was
identified and was brought to the discussion by the project team. After the problem had been
identified the possible risk are analyzed and grouped together. After grouping, they are
documented for future reference. Risks are then evaluated and the control measures were placed
on board for the discussion. The full report is now documented and the project is supposed to be
monitored during implementation (Pearson, 2013).
During the risk assessment process, the risk level is to be estimated according to
the likelihood of the concern scenario located against the possible negative result. The possibility
of the incident problem is given by the issue exploiting the weakness with the likelihood.
Therefore the possibility of each scenario was examined by the experts and was documented on
this report (Jansen, 2011). Drawing was made and it experienced. For the impossible cases, it
was assume not applicable during the documentation and while carrying out data analysis.
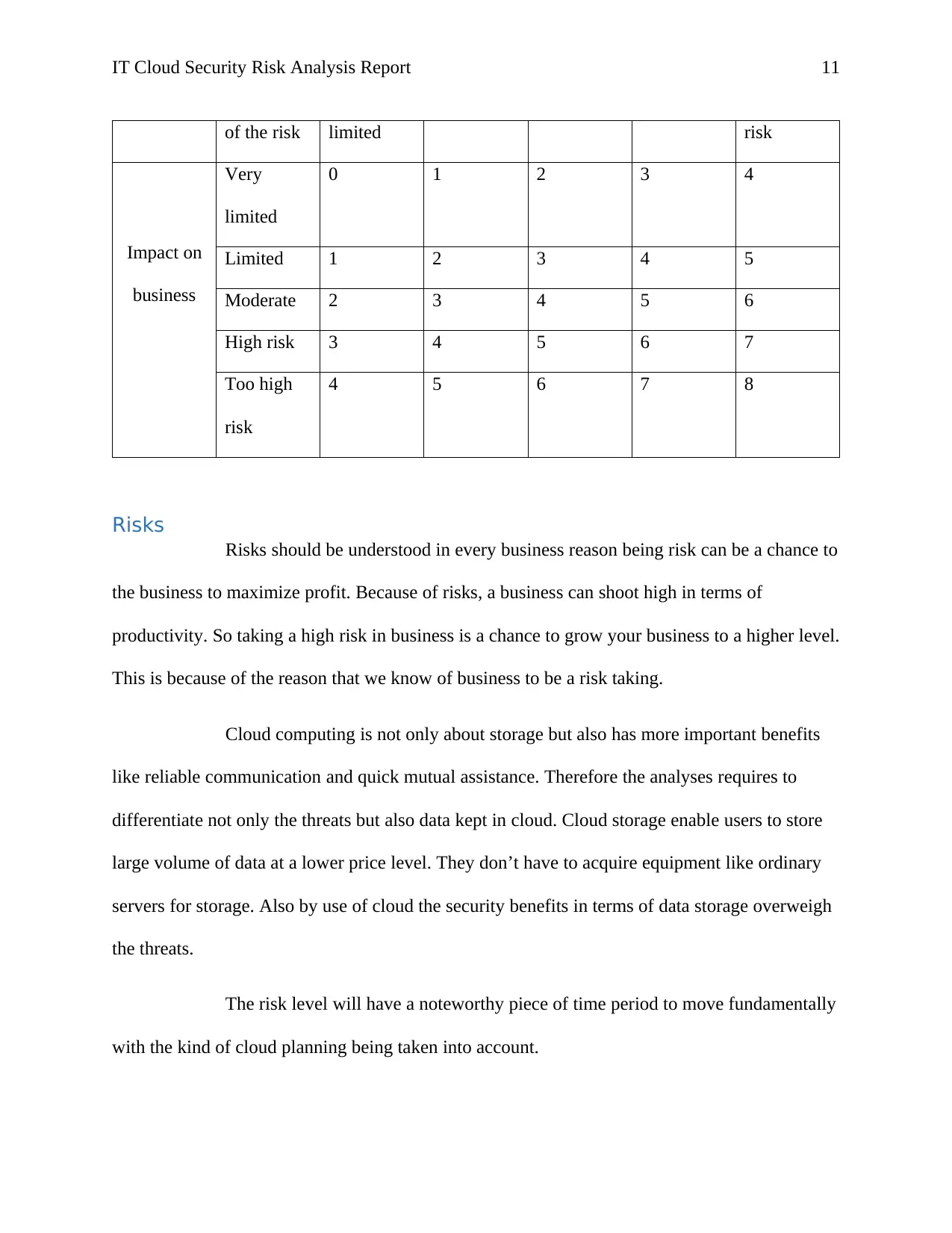
The level of risks was drawn as show in the below diagram with figures;
1. To show that the risk is low: 0-2
2. To show the risk is moderate: 3-5
3. To show that the risk is very high 6-8
Possibility Very limited Moderate High risk Too high
During the research, the above process was followed where the problem was
identified and was brought to the discussion by the project team. After the problem had been
identified the possible risk are analyzed and grouped together. After grouping, they are
documented for future reference. Risks are then evaluated and the control measures were placed
on board for the discussion. The full report is now documented and the project is supposed to be
monitored during implementation (Pearson, 2013).
During the risk assessment process, the risk level is to be estimated according to
the likelihood of the concern scenario located against the possible negative result. The possibility
of the incident problem is given by the issue exploiting the weakness with the likelihood.
Therefore the possibility of each scenario was examined by the experts and was documented on
this report (Jansen, 2011). Drawing was made and it experienced. For the impossible cases, it
was assume not applicable during the documentation and while carrying out data analysis.
The level of risks was drawn as show in the below diagram with figures;
1. To show that the risk is low: 0-2
2. To show the risk is moderate: 3-5
3. To show that the risk is very high 6-8
Possibility Very limited Moderate High risk Too high
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
IT Cloud Security Risk Analysis Report 11
of the risk limited risk
Impact on
business
Very
limited
0 1 2 3 4
Limited 1 2 3 4 5
Moderate 2 3 4 5 6
High risk 3 4 5 6 7
Too high
risk
4 5 6 7 8
Risks
Risks should be understood in every business reason being risk can be a chance to
the business to maximize profit. Because of risks, a business can shoot high in terms of
productivity. So taking a high risk in business is a chance to grow your business to a higher level.
This is because of the reason that we know of business to be a risk taking.
Cloud computing is not only about storage but also has more important benefits
like reliable communication and quick mutual assistance. Therefore the analyses requires to
differentiate not only the threats but also data kept in cloud. Cloud storage enable users to store
large volume of data at a lower price level. They don’t have to acquire equipment like ordinary
servers for storage. Also by use of cloud the security benefits in terms of data storage overweigh
the threats.
The risk level will have a noteworthy piece of time period to move fundamentally
with the kind of cloud planning being taken into account.
of the risk limited risk
Impact on
business
Very
limited
0 1 2 3 4
Limited 1 2 3 4 5
Moderate 2 3 4 5 6
High risk 3 4 5 6 7
Too high
risk
4 5 6 7 8
Risks
Risks should be understood in every business reason being risk can be a chance to
the business to maximize profit. Because of risks, a business can shoot high in terms of
productivity. So taking a high risk in business is a chance to grow your business to a higher level.
This is because of the reason that we know of business to be a risk taking.
Cloud computing is not only about storage but also has more important benefits
like reliable communication and quick mutual assistance. Therefore the analyses requires to
differentiate not only the threats but also data kept in cloud. Cloud storage enable users to store
large volume of data at a lower price level. They don’t have to acquire equipment like ordinary
servers for storage. Also by use of cloud the security benefits in terms of data storage overweigh
the threats.
The risk level will have a noteworthy piece of time period to move fundamentally
with the kind of cloud planning being taken into account.

IT Cloud Security Risk Analysis Report 12
The risk research applies to cloud improvement in this report. It doesn't have any
huge consideration to a specific distribution, registering, giving or association. This report isn't
organized to supplement an endeavor specific types of leveled risks researches.
Consequently, risks of using disseminated registration should have appeared
differently in relation to the threats of staying with traditional plans, for instance, work area
based models.
Dangers in this investigation were gathered into different classifications which
incorporate the following:
Organizational
Technical
Legal
Organizational risks
Risks on the concern of the organization are redirected to application exposure to the
attackers. The applications are not save this is because they are uploaded to the cloud leading to
its exposure giving an opportunity to the hackers and may get interested in damaging these
organizational application (Jansen, 2011). Many hackers do normally hack applications over the
cloud, this is because of the IoT technology where the high speed internet connection is the
crucial and resourceful tool for hacking.
Also, organizational network connectivity will get exposed. And it will be so easier for
the intruders to get into the organizational system whenever they are exposed to a network. This
will become a sure way for them to attack the company resources and steal from it.
The risk research applies to cloud improvement in this report. It doesn't have any
huge consideration to a specific distribution, registering, giving or association. This report isn't
organized to supplement an endeavor specific types of leveled risks researches.
Consequently, risks of using disseminated registration should have appeared
differently in relation to the threats of staying with traditional plans, for instance, work area
based models.
Dangers in this investigation were gathered into different classifications which
incorporate the following:
Organizational
Technical
Legal
Organizational risks
Risks on the concern of the organization are redirected to application exposure to the
attackers. The applications are not save this is because they are uploaded to the cloud leading to
its exposure giving an opportunity to the hackers and may get interested in damaging these
organizational application (Jansen, 2011). Many hackers do normally hack applications over the
cloud, this is because of the IoT technology where the high speed internet connection is the
crucial and resourceful tool for hacking.
Also, organizational network connectivity will get exposed. And it will be so easier for
the intruders to get into the organizational system whenever they are exposed to a network. This
will become a sure way for them to attack the company resources and steal from it.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 21
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




