ICT373 Cloud Computing: Cloud Security Strategy for SmoothVideos Ltd
VerifiedAdded on 2022/08/17
|7
|810
|16
Report
AI Summary
This report provides a cloud computing security strategy for SmoothVideos Ltd, a video production company transitioning to the cloud. It discusses the importance of cloud security, highlighting benefits like reliability, reduced administration, centralized security, and cost reduction. The report explores the selection of the right cloud security solution, recommending a Standard Desktop Operating Environment (SDOE) for its cost-effectiveness and flexibility. It concludes that a cloud deployment model is essential for building cloud-based applications and analyzes various security measures to protect SmoothVideos Ltd's data and infrastructure. Desklib offers similar solved assignments and past papers for students.

Running head: CLOUD COMPUTING
CLOUD COMPUTING
Name of the Student
Name of the University
Author Note
CLOUD COMPUTING
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1CLOUD COMPUTING
Table of Contents
Deployment Model:...................................................................................................................2
Security:.....................................................................................................................................3
Introduction:...........................................................................................................................3
Discussion:.............................................................................................................................3
Conclusion:............................................................................................................................4
Reference:..................................................................................................................................5
Table of Contents
Deployment Model:...................................................................................................................2
Security:.....................................................................................................................................3
Introduction:...........................................................................................................................3
Discussion:.............................................................................................................................3
Conclusion:............................................................................................................................4
Reference:..................................................................................................................................5
2CLOUD COMPUTING
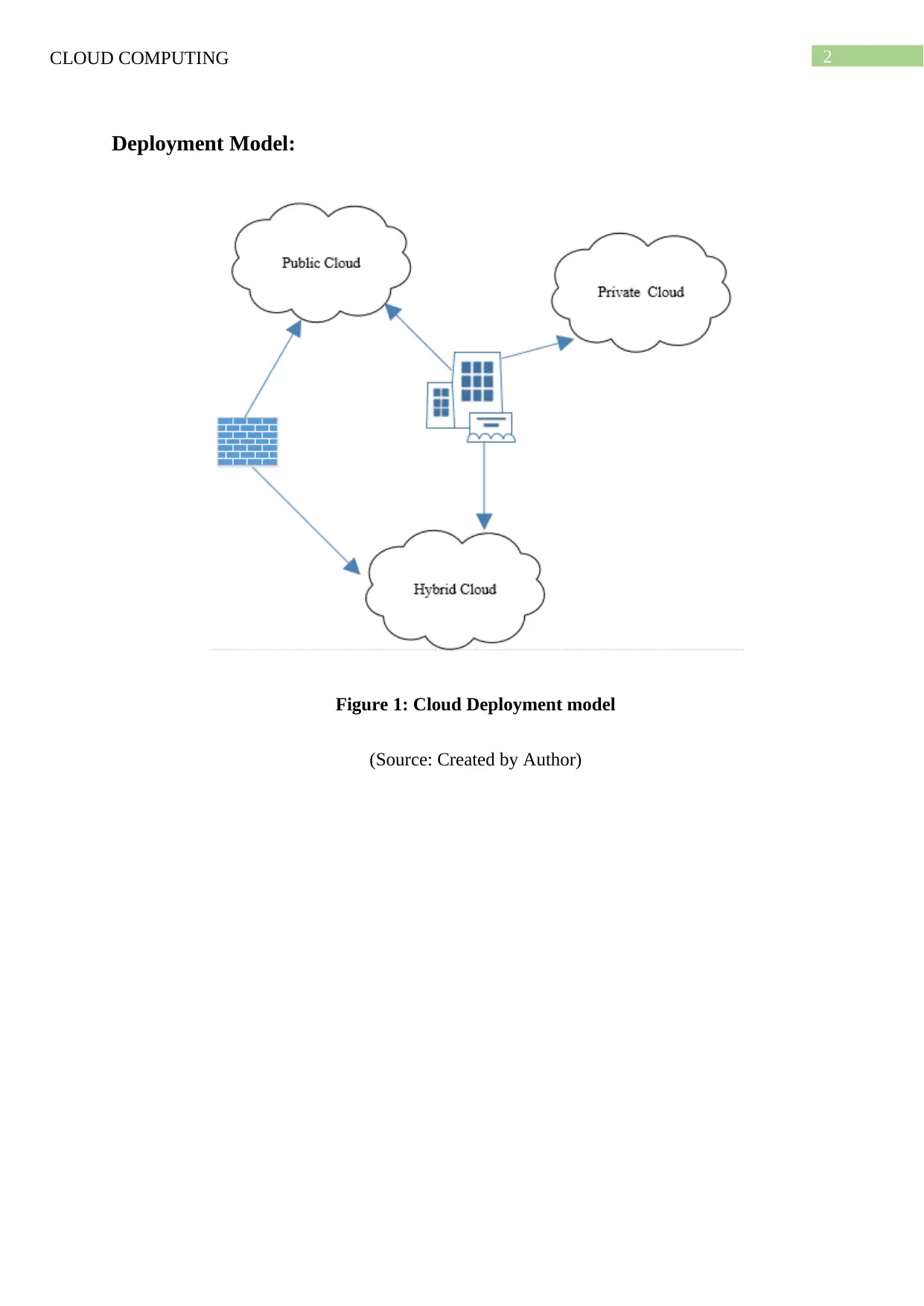
Deployment Model:
Figure 1: Cloud Deployment model
(Source: Created by Author)
Deployment Model:
Figure 1: Cloud Deployment model
(Source: Created by Author)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3CLOUD COMPUTING
Security:
Introduction:
Cloud security is an essential part of cloud computing. To protect the cloud from
various threats and maintain the different security controls, policies, and procedures need to
be implemented. These security methods are organized to save the data and it is able to
protect customers' privacy as well as (Erl, Puttini & Mahmood, 2013). This report produces
several security options that are helpful for SmoothVideos Ltd to maintain its security.
Discussion:
By using the cloud, business is changing day by day. Robust cloud security is
necessary. With increasing the demand for cloud, several threats becoming sophisticated.
Robust cloud security has many benefits. Few cloud securities are providing below:
Reliability:
A complete cloud computing service offers dependability. By using proper cloud security,
every user is able to access every application and data safely (de Bruin & Floridi, 2017).
SmoothVideos Ltd wants to increase its production, and its old server takes time for video
processing. By using a cloud database, they are able to reduce processing time (Liu et al.,
2016). Cloud allows every organization to reduce production costs, and it uses the agile
systems that are good advantages for the organizations. Every cloud model is a vulnerable
threat. IT experts must be careful while they are transforming server to cloud.
Reduced Administration:
When SmoothVideos Ltd chooses a reputed cloud service provider, they can easily
remove their manual server security configuration and it can reduce the administration cost.
Security:
Introduction:
Cloud security is an essential part of cloud computing. To protect the cloud from
various threats and maintain the different security controls, policies, and procedures need to
be implemented. These security methods are organized to save the data and it is able to
protect customers' privacy as well as (Erl, Puttini & Mahmood, 2013). This report produces
several security options that are helpful for SmoothVideos Ltd to maintain its security.
Discussion:
By using the cloud, business is changing day by day. Robust cloud security is
necessary. With increasing the demand for cloud, several threats becoming sophisticated.
Robust cloud security has many benefits. Few cloud securities are providing below:
Reliability:
A complete cloud computing service offers dependability. By using proper cloud security,
every user is able to access every application and data safely (de Bruin & Floridi, 2017).
SmoothVideos Ltd wants to increase its production, and its old server takes time for video
processing. By using a cloud database, they are able to reduce processing time (Liu et al.,
2016). Cloud allows every organization to reduce production costs, and it uses the agile
systems that are good advantages for the organizations. Every cloud model is a vulnerable
threat. IT experts must be careful while they are transforming server to cloud.
Reduced Administration:
When SmoothVideos Ltd chooses a reputed cloud service provider, they can easily
remove their manual server security configuration and it can reduce the administration cost.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4CLOUD COMPUTING
While changing the server platform, essential information can be lost but after completing the
transformation, they can access every possible administration configuration.
Centralized Security:
By using the cloud, every information and application can found in one place and it is
secure by using centralize protection technology. Every business uses many devices and
manually manages every device is not possible. Recovery plans must be implemented to
reduce the risks of data loss. SmoothVideos Ltd can access every data and application from
one place.
Reduce Costs:
By using cloud security and cloud storage SmoothVideos Ltd is able to reduce its
costs. They can eliminate the hardware cost and invest that money in their business. It also
helps to reduce administrative costs. Cloud protection can provide 24/7 security that is not
possible for a person.
Right cloud security solution:
Selecting the right security in business can eliminate the risk of unauthorized access
and other vulnerable threats (Singh, Jeong & Park, 2016). SmoothVideos wants to facilitate
with Standard Desktop Operating Environment to use these services in their platform. This is
an operating system that is associated with the hardware component and applications. Along
with SmoothVideos Ltd, much big organization is using this platform. This platform cost-
effective, and an organization can change its configuration if required.
Conclusion:
Hence, from the above discussion, it can be stated that the cloud deployment model is
one of an essential model for building the cloud-based application. This model is helpful in
While changing the server platform, essential information can be lost but after completing the
transformation, they can access every possible administration configuration.
Centralized Security:
By using the cloud, every information and application can found in one place and it is
secure by using centralize protection technology. Every business uses many devices and
manually manages every device is not possible. Recovery plans must be implemented to
reduce the risks of data loss. SmoothVideos Ltd can access every data and application from
one place.
Reduce Costs:
By using cloud security and cloud storage SmoothVideos Ltd is able to reduce its
costs. They can eliminate the hardware cost and invest that money in their business. It also
helps to reduce administrative costs. Cloud protection can provide 24/7 security that is not
possible for a person.
Right cloud security solution:
Selecting the right security in business can eliminate the risk of unauthorized access
and other vulnerable threats (Singh, Jeong & Park, 2016). SmoothVideos wants to facilitate
with Standard Desktop Operating Environment to use these services in their platform. This is
an operating system that is associated with the hardware component and applications. Along
with SmoothVideos Ltd, much big organization is using this platform. This platform cost-
effective, and an organization can change its configuration if required.
Conclusion:
Hence, from the above discussion, it can be stated that the cloud deployment model is
one of an essential model for building the cloud-based application. This model is helpful in

5CLOUD COMPUTING
analyzing cloud securities. In this report, various types of securities are discussed.
SmoothVideos Ltd has chosen SDOE to increase video processing speed.
analyzing cloud securities. In this report, various types of securities are discussed.
SmoothVideos Ltd has chosen SDOE to increase video processing speed.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6CLOUD COMPUTING
Reference:
Erl, T., Puttini, R., & Mahmood, Z. (2013). Cloud computing: concepts, technology &
architecture. Pearson Education.
de Bruin, B., & Floridi, L. (2017). The ethics of cloud computing. Science and engineering
ethics, 23(1), 21-39.
Liu, D., Zhang, H., Zhou, J., Shen, W., Cao, M., Chen, S., ... & Dai, D. (2016, July). Video
processing using GPU-Accelerator under desktop virtualization environment. In 2016
International Conference on Audio, Language and Image Processing (ICALIP) (pp.
766-770). IEEE.
Singh, S., Jeong, Y. S., & Park, J. H. (2016). A survey on cloud computing security: Issues,
threats, and solutions. Journal of Network and Computer Applications, 75, 200-222.
Reference:
Erl, T., Puttini, R., & Mahmood, Z. (2013). Cloud computing: concepts, technology &
architecture. Pearson Education.
de Bruin, B., & Floridi, L. (2017). The ethics of cloud computing. Science and engineering
ethics, 23(1), 21-39.
Liu, D., Zhang, H., Zhou, J., Shen, W., Cao, M., Chen, S., ... & Dai, D. (2016, July). Video
processing using GPU-Accelerator under desktop virtualization environment. In 2016
International Conference on Audio, Language and Image Processing (ICALIP) (pp.
766-770). IEEE.
Singh, S., Jeong, Y. S., & Park, J. H. (2016). A survey on cloud computing security: Issues,
threats, and solutions. Journal of Network and Computer Applications, 75, 200-222.
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





