Cloud Security Solutions: Benefits, Risks, and Implementation Analysis
VerifiedAdded on 2023/06/10
|9
|2034
|436
Report
AI Summary
This report provides a comprehensive overview of cloud-based security solutions, addressing concerns and risks associated with cloud applications and systems. It examines the need for cloud security, highlighting the roles of service providers and customers in ensuring data protection. The report discusses cloud-based managed security services, their working mechanisms, and essential security tools. It also outlines the advantages and disadvantages of cloud-based security solutions, emphasizing the importance of automated applications and real-time analytics for threat protection. Furthermore, the report touches on the challenges of implementing cloud-based security, including maintaining control and visibility across diverse areas, and concludes with a discussion on ICT systems and the steps required for enforcing cloud security services, including stakeholder collaboration, qualified service providers, and robust data security measures such as data encryption and Virtual Private Data Centers (VPDC).

Cloud Based Security Solution
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cloud-Based Security
In cloud system and applications, there exists security concerns and the cloud based
security providers have developed its security solutions. The main objective of the cloud based
security providers is to ensure customer’s data and information security. In cloud, only the
authorized person is provided access, for security reasons. The service provider and the
customers are responsible for securing cloud, where effective measures must be taken by the
customers for protecting their systems and applications, with passwords and by enforcing limited
access to the sensitive data. The service provider’s role is to make sure that the customer’s data
and information are always safe from unauthorized access.
Business and Cloud Applications
For business, the cloud applications increases convenience, data management and
provides easy access of data from anywhere. The cloud services provides information in real
time and builds a platform of interaction with the business owner (Kumar, 2018).
Security Concerns
As like any other system, the cloud comprises of security concerns, which could risk the
cloud applications, systems, and information. The risks related to security are listed below:
1) Data breaches
2) Account hijacking
3) Unauthorized access
4) Misusing sensitive information
Hence, the cloud based security services ensures to secure the database and manages the
risks. Moreover, there is increased demand for cloud based security, since the virtualized and
cloud networks have increased. The reason for this the high portability and distribution of data
and applications across wide range of networks. Thus, in cloud the security applications must
have software instead of hardware which can protect only a specific part of the network. Thus,
the cloud based security services utilize the Software as a Service (SAAS) model, to accomplish
their purpose ("What is Cloud Based Security?", 2018).
Why is there need of Cloud Security?
The key need of cloud security is to provide network security for one and all. The
Amazon Web Services or Microsoft Office 365 holds the responsibility of data security in a
cloud environments. However, the main point to be noted is that, similar protection cannot be
In cloud system and applications, there exists security concerns and the cloud based
security providers have developed its security solutions. The main objective of the cloud based
security providers is to ensure customer’s data and information security. In cloud, only the
authorized person is provided access, for security reasons. The service provider and the
customers are responsible for securing cloud, where effective measures must be taken by the
customers for protecting their systems and applications, with passwords and by enforcing limited
access to the sensitive data. The service provider’s role is to make sure that the customer’s data
and information are always safe from unauthorized access.
Business and Cloud Applications
For business, the cloud applications increases convenience, data management and
provides easy access of data from anywhere. The cloud services provides information in real
time and builds a platform of interaction with the business owner (Kumar, 2018).
Security Concerns
As like any other system, the cloud comprises of security concerns, which could risk the
cloud applications, systems, and information. The risks related to security are listed below:
1) Data breaches
2) Account hijacking
3) Unauthorized access
4) Misusing sensitive information
Hence, the cloud based security services ensures to secure the database and manages the
risks. Moreover, there is increased demand for cloud based security, since the virtualized and
cloud networks have increased. The reason for this the high portability and distribution of data
and applications across wide range of networks. Thus, in cloud the security applications must
have software instead of hardware which can protect only a specific part of the network. Thus,
the cloud based security services utilize the Software as a Service (SAAS) model, to accomplish
their purpose ("What is Cloud Based Security?", 2018).
Why is there need of Cloud Security?
The key need of cloud security is to provide network security for one and all. The
Amazon Web Services or Microsoft Office 365 holds the responsibility of data security in a
cloud environments. However, the main point to be noted is that, similar protection cannot be

provided by all the cloud providers. Thus, the users will required complete access control and
security for protection against risks. However, Cloud Application Security Broker (CASB) helps
to cut the risks that occur from various cloud applications, and it is utilized for creating access
policies. On the other hand, the cloud security platform can prevent data leakage with the help of
CASB, it fails to provide protection on its own, against the following ("Cloud Security Solutions
— Advantages & Benefits", 2018):
a) Security Breaches
b) Ransomware
c) Other type of internet threats.
Cloud-based Managed Security Services
At present, the digital world faces serious issues related to cyber security and there are
various organizations that are still struggling to cope with these threats. For this cloud-
based managed security services are the solution.
The following factors led to the rise of cloud-based Managed Security Services (Saha,
2016):
1) In all the fields, the implementation of cloud started increasing irrespective of size
of the organization.
2) The growing interest in managed security services.
3) Poor budgets and limitation of cost, for the models of traditional in-house based
security.
4) Increased regulatory pressures and rigid laws for information security.
5) Shortage of security staff who are qualified enough.
Working of Cloud Based Security
a) Secure the Server from threats, using cloud web security helps the traffic to get to the
cloud rather than being directly routed to the servers. The cloud investigates traffic and
just enables the authorized users to obtain the access. Any kind of traffic which is not
supported by the cloud, will be blocked from getting to the server (Kumar, 2018).
b) Inspecting and filtering data takes place. Where, the traditional systems contain
applications which can filter the data prior to reaching the server, these applications are
security for protection against risks. However, Cloud Application Security Broker (CASB) helps
to cut the risks that occur from various cloud applications, and it is utilized for creating access
policies. On the other hand, the cloud security platform can prevent data leakage with the help of
CASB, it fails to provide protection on its own, against the following ("Cloud Security Solutions
— Advantages & Benefits", 2018):
a) Security Breaches
b) Ransomware
c) Other type of internet threats.
Cloud-based Managed Security Services
At present, the digital world faces serious issues related to cyber security and there are
various organizations that are still struggling to cope with these threats. For this cloud-
based managed security services are the solution.
The following factors led to the rise of cloud-based Managed Security Services (Saha,
2016):
1) In all the fields, the implementation of cloud started increasing irrespective of size
of the organization.
2) The growing interest in managed security services.
3) Poor budgets and limitation of cost, for the models of traditional in-house based
security.
4) Increased regulatory pressures and rigid laws for information security.
5) Shortage of security staff who are qualified enough.
Working of Cloud Based Security
a) Secure the Server from threats, using cloud web security helps the traffic to get to the
cloud rather than being directly routed to the servers. The cloud investigates traffic and
just enables the authorized users to obtain the access. Any kind of traffic which is not
supported by the cloud, will be blocked from getting to the server (Kumar, 2018).
b) Inspecting and filtering data takes place. Where, the traditional systems contain
applications which can filter the data prior to reaching the server, these applications are
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

highly expensive and even its maintenance is difficult. As it reaches the network, they
filter the traffic. At times the machines might shut down, for blocking good as well as the
bad traffic, and it will not be possible to meet the desired functions. But, first the club
web security services help to redirect the traffic to the security cloud. Prior to reaching
the application system, filtration takes place.
c) The option of private club is provided by the cloud based security solutions which
segregates the unwanted traffic access of the client applications. This option makes sure
that the shared resource issue never exists, by providing protection.
d) By enforcing data management with secured encryption, to limit the authorized access.
e) Set compliance rules for enforcing strict security of data base.
Cloud Bases Security Tools
The following are the highly effective tools for cloud based security (Kelly, 2014):
1) Qualys
2) Okta
3) White Hat Security
4) Proofpoint
5) Zscaler
6) DocTrackr
7) CipherCloud
8) Centrify
9) Vaultive
10) SilverSky
Advantages and Disadvantages of Cloud Based Security Solutions
Advantages:
a) When the cloud provider uses specialized staff, it improvises the patch management
and deployment.
b) Improved approach for human-relations.
c) It provides system redundancy.
d) It improves incident response.
filter the traffic. At times the machines might shut down, for blocking good as well as the
bad traffic, and it will not be possible to meet the desired functions. But, first the club
web security services help to redirect the traffic to the security cloud. Prior to reaching
the application system, filtration takes place.
c) The option of private club is provided by the cloud based security solutions which
segregates the unwanted traffic access of the client applications. This option makes sure
that the shared resource issue never exists, by providing protection.
d) By enforcing data management with secured encryption, to limit the authorized access.
e) Set compliance rules for enforcing strict security of data base.
Cloud Bases Security Tools
The following are the highly effective tools for cloud based security (Kelly, 2014):
1) Qualys
2) Okta
3) White Hat Security
4) Proofpoint
5) Zscaler
6) DocTrackr
7) CipherCloud
8) Centrify
9) Vaultive
10) SilverSky
Advantages and Disadvantages of Cloud Based Security Solutions
Advantages:
a) When the cloud provider uses specialized staff, it improvises the patch management
and deployment.
b) Improved approach for human-relations.
c) It provides system redundancy.
d) It improves incident response.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Disadvantages:
a) Insufficient clarity on the impact of physical location of the data.
b) Concerns of multitenant, with respect to exposing the customer’s private data.
c) Contract lock-ins.
d) Malicious insiders.
e) Failure of vendor.
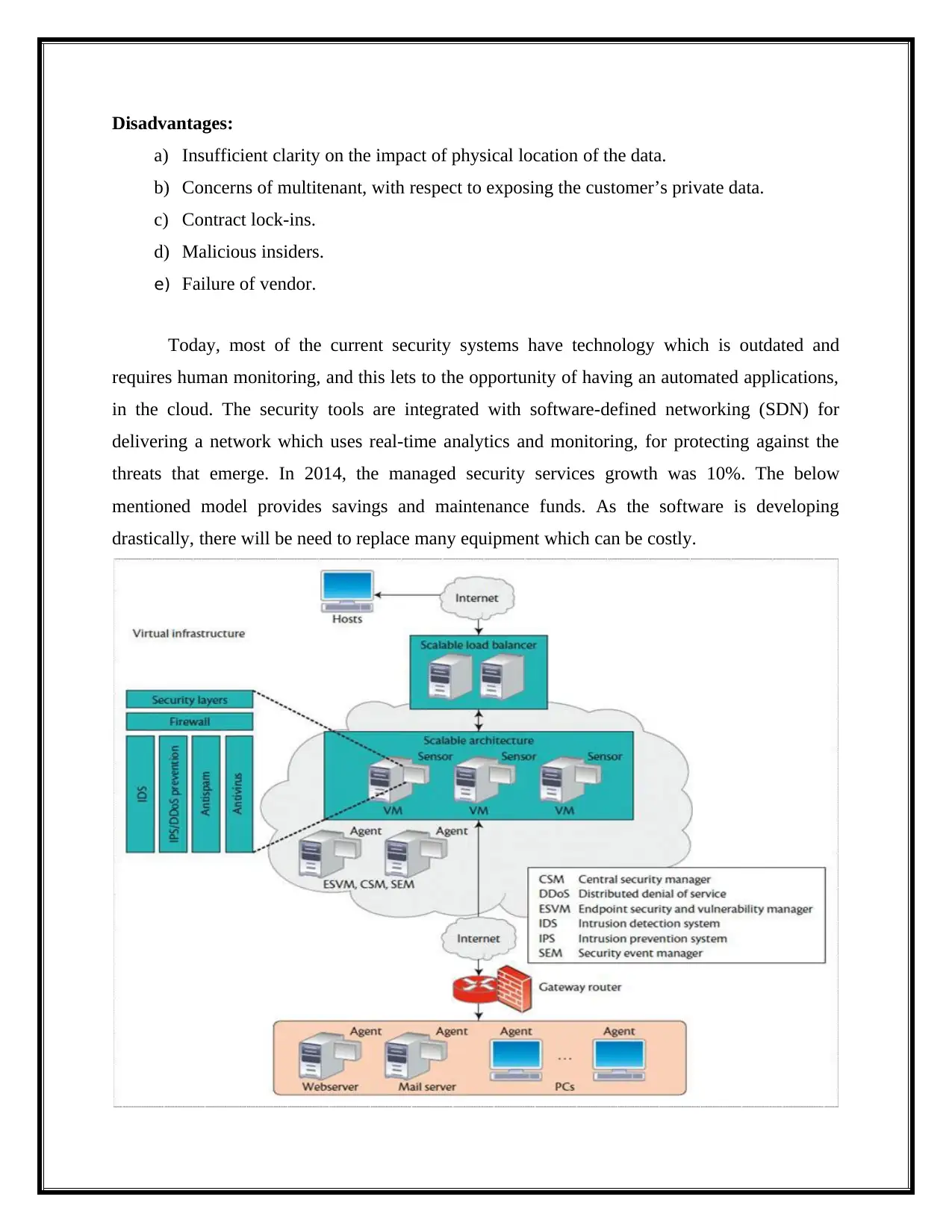
Today, most of the current security systems have technology which is outdated and
requires human monitoring, and this lets to the opportunity of having an automated applications,
in the cloud. The security tools are integrated with software-defined networking (SDN) for
delivering a network which uses real-time analytics and monitoring, for protecting against the
threats that emerge. In 2014, the managed security services growth was 10%. The below
mentioned model provides savings and maintenance funds. As the software is developing
drastically, there will be need to replace many equipment which can be costly.
a) Insufficient clarity on the impact of physical location of the data.
b) Concerns of multitenant, with respect to exposing the customer’s private data.
c) Contract lock-ins.
d) Malicious insiders.
e) Failure of vendor.
Today, most of the current security systems have technology which is outdated and
requires human monitoring, and this lets to the opportunity of having an automated applications,
in the cloud. The security tools are integrated with software-defined networking (SDN) for
delivering a network which uses real-time analytics and monitoring, for protecting against the
threats that emerge. In 2014, the managed security services growth was 10%. The below
mentioned model provides savings and maintenance funds. As the software is developing
drastically, there will be need to replace many equipment which can be costly.
Practicing cloud-based security demonstrates challenges. With a specific end goal to
convey protection, it is required that the architecture has security. There are additionally an
extensive variety of security needs, where all need diverse applications and requirements.
Moreover, moving to cloud-based applications has its own dangers. For business, web security,
mail security and, identity and access management are the serious cloud issues. Then, in the
organization the trend for employees to Bring your own device (BYOD), lead to Distributed
Denial of Service (DDoS) attacks, and improved threats. This is becoming difficult for the IT
managers and they are approaching multi-faceted method, for security. The biggest difficulties of
executing cloud-based security includes maintaining control and perceivability over the diverse
areas. A mix of public and private cloud-based services makes the joining of security services, to
undertake a major task.
ICT System
ICT comprises of internet-enabled sphere circle and the mobile devices which works
based on the wireless networks. It likewise incorporates outdated advances. For example, radio,
landline phones and television, which even today are utilized as master piece of ICT, like
robotics. ICT refers to a broad representation of components such as computer and digital
technologies (Pratt, 2018).
Figure: ICT components
convey protection, it is required that the architecture has security. There are additionally an
extensive variety of security needs, where all need diverse applications and requirements.
Moreover, moving to cloud-based applications has its own dangers. For business, web security,
mail security and, identity and access management are the serious cloud issues. Then, in the
organization the trend for employees to Bring your own device (BYOD), lead to Distributed
Denial of Service (DDoS) attacks, and improved threats. This is becoming difficult for the IT
managers and they are approaching multi-faceted method, for security. The biggest difficulties of
executing cloud-based security includes maintaining control and perceivability over the diverse
areas. A mix of public and private cloud-based services makes the joining of security services, to
undertake a major task.
ICT System
ICT comprises of internet-enabled sphere circle and the mobile devices which works
based on the wireless networks. It likewise incorporates outdated advances. For example, radio,
landline phones and television, which even today are utilized as master piece of ICT, like
robotics. ICT refers to a broad representation of components such as computer and digital
technologies (Pratt, 2018).
Figure: ICT components
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

For enforcing Cloud bases security service the following steps are required (Chen, 2018):
1) Take help of the stakeholders, as collaboration and coordination with them can
help to protect the cloud platform.
2) Choose a qualified Cloud service provider.
3) The Cloud service providers or vendors ensure sharing of security products and
services.
4) For governance and managing risk, Cloud security services management is
implemented and it plays a significant role in security.
Data Security
In cloud computing, data security is risky, as the internet is the medium to access the
data, there are chances of easily getting monitored or spoofed. Data encryption that is at its high
level of performance and safe for accessing. There are high chances that the service providers
and their partners can read and edit the customer’s data. At last, as internet is required for
communication of all types, there are no chances to exclude the ruled interception and the
blocking attacks. However, the customers must rely on the IT Service Providers, because the
customer’s data, applications and projects are stored in a remote cloud data center, for which
internet with high speed is required.
Example:
In U.S, the data stored in the clouds are accessed with the help of local offices, like the
FBI, CIA and the public cloud providers (i.e., Amazon, Google and iCloud) which helps in
distribution of data inside an organization, where the client has the likelihood of controlling and
influencing the storage areas. For such as issue, Virtual Private Data Center (VPDC) is set up for
benefiting the cloud’s advantages. Here, the VPDC empowers the client to completely utilize and
take advantage of cloud technologies, however there is restriction that it can enjoy the benefits
inside a gated community and the access is restricted only for one user.
Cloud-based Project Management solutions
The cloud-based Project Management solutions helps in tracking the time spent on
project’s specific elements. This helps the team members to check the duration of completing the
task. This helps to provide realistic projections. Moreover, the team members who are away can
also be connected through online, and this way they are kept informed about the project.
1) Take help of the stakeholders, as collaboration and coordination with them can
help to protect the cloud platform.
2) Choose a qualified Cloud service provider.
3) The Cloud service providers or vendors ensure sharing of security products and
services.
4) For governance and managing risk, Cloud security services management is
implemented and it plays a significant role in security.
Data Security
In cloud computing, data security is risky, as the internet is the medium to access the
data, there are chances of easily getting monitored or spoofed. Data encryption that is at its high
level of performance and safe for accessing. There are high chances that the service providers
and their partners can read and edit the customer’s data. At last, as internet is required for
communication of all types, there are no chances to exclude the ruled interception and the
blocking attacks. However, the customers must rely on the IT Service Providers, because the
customer’s data, applications and projects are stored in a remote cloud data center, for which
internet with high speed is required.
Example:
In U.S, the data stored in the clouds are accessed with the help of local offices, like the
FBI, CIA and the public cloud providers (i.e., Amazon, Google and iCloud) which helps in
distribution of data inside an organization, where the client has the likelihood of controlling and
influencing the storage areas. For such as issue, Virtual Private Data Center (VPDC) is set up for
benefiting the cloud’s advantages. Here, the VPDC empowers the client to completely utilize and
take advantage of cloud technologies, however there is restriction that it can enjoy the benefits
inside a gated community and the access is restricted only for one user.
Cloud-based Project Management solutions
The cloud-based Project Management solutions helps in tracking the time spent on
project’s specific elements. This helps the team members to check the duration of completing the
task. This helps to provide realistic projections. Moreover, the team members who are away can
also be connected through online, and this way they are kept informed about the project.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

In an organization, for effectively managing and controlling cloud technology, the
business decision makers must assess the impacts which has potential of competitive edge. Next,
the critical security related queries and cloud technology implementation must be evaluated.
For an effective cloud computing, the organization must ensure to monitor their cloud
governance, cloud transparency and impacts of cloud computing security. The SLA helps to
form effective cloud transparency in the cloud computing.
business decision makers must assess the impacts which has potential of competitive edge. Next,
the critical security related queries and cloud technology implementation must be evaluated.
For an effective cloud computing, the organization must ensure to monitor their cloud
governance, cloud transparency and impacts of cloud computing security. The SLA helps to
form effective cloud transparency in the cloud computing.

References
Chen, D. (2018). Cloud Security Services Management. Retrieved from
https://cloudsecurityalliance.org/group/cloud-security-services-management/#_overview
Cloud Security Solutions — Advantages & Benefits. (2018). Retrieved from
https://www.zscaler.com/solutions/cloud-security
Kelly, M. (2014). The top 10 cloud-based security tools to protect your network in a hurry.
Retrieved from https://venturebeat.com/2014/01/30/top-ten-saas-security-tools/
Kumar, A. (2018). How Does Cloud-Based Security Work. Retrieved from
https://jktech.com/insight/blogs/how-does-cloud-based-security-work/
Pratt, M. (2018). ICT (information and communications technology, or technologies). Retrieved
from https://searchcio.techtarget.com/definition/ICT-information-and-communications-
technology-or-technologies
Saha, P. (2016). The Rise of Cloud-based Managed Security Services. Retrieved from
https://www.happiestminds.com/blogs/the-rise-of-cloud-based-managed-security-services/
What is Cloud Based Security?. (2018). Retrieved from
https://www.sdxcentral.com/security/definitions/what-is-cloud-based-security/
Chen, D. (2018). Cloud Security Services Management. Retrieved from
https://cloudsecurityalliance.org/group/cloud-security-services-management/#_overview
Cloud Security Solutions — Advantages & Benefits. (2018). Retrieved from
https://www.zscaler.com/solutions/cloud-security
Kelly, M. (2014). The top 10 cloud-based security tools to protect your network in a hurry.
Retrieved from https://venturebeat.com/2014/01/30/top-ten-saas-security-tools/
Kumar, A. (2018). How Does Cloud-Based Security Work. Retrieved from
https://jktech.com/insight/blogs/how-does-cloud-based-security-work/
Pratt, M. (2018). ICT (information and communications technology, or technologies). Retrieved
from https://searchcio.techtarget.com/definition/ICT-information-and-communications-
technology-or-technologies
Saha, P. (2016). The Rise of Cloud-based Managed Security Services. Retrieved from
https://www.happiestminds.com/blogs/the-rise-of-cloud-based-managed-security-services/
What is Cloud Based Security?. (2018). Retrieved from
https://www.sdxcentral.com/security/definitions/what-is-cloud-based-security/
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





