Cloud Computing Implementation: Regional Gardens Ltd Analysis
VerifiedAdded on 2023/06/14
|14
|2270
|122
Report
AI Summary
This report presents an analysis of cloud computing implementation for Regional Gardens Ltd, considering the company's existing IT infrastructure. It evaluates different approaches to office automation, including centralized database and office portal approaches, highlighting their benefits and issues. The report further differentiates between Infrastructure as a Service (IaaS) and Platform as a Service (PaaS) in a public cloud environment, recommending PaaS as the most suitable model for Regional Gardens Ltd. It addresses potential problems such as availability, data confidentiality, and virtual machine risks, proposing solutions to mitigate these issues. The conclusion emphasizes the beneficial aspects of adopting cloud services despite the associated risks, positioning it as a trending technology across various industries. Desklib offers solved assignments and past papers for students.

Running head: CLOUD COMPUTING
CLOUD COMPUTING
Name of the Student
Name of the University
Author Note
CLOUD COMPUTING
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2CLOUD COMPUTING
Table of Contents
1. Presentation:...........................................................................................................................3
2. Introduction............................................................................................................................7
3. 1 Different Approaches of Office automation.......................................................................7
3.2 Benefit of Automation system approach..........................................................................8
3.3 Issues in Automation system approach............................................................................8
3.4 Benefit in Office portal approach.....................................................................................8
3.5 Issues in Office portal approach.......................................................................................8
3.6 Recommendation..............................................................................................................8
4.1 Difference between IaaS and PaaS in public cloud.............................................................9
4.2 Differences.......................................................................................................................9
5.1 Recommendation of model............................................................................................10
5.2 Problem 1: Availability..................................................................................................11
5.2.1 Problem 2: Data confidentiality..................................................................................11
5.2.2 Problem 3: Virtual machine........................................................................................11
5.2.3 Dealing with the Issue.................................................................................................11
6.0 Conclusion..........................................................................................................................12
7.0 Bibliography.......................................................................................................................13
Table of Contents
1. Presentation:...........................................................................................................................3
2. Introduction............................................................................................................................7
3. 1 Different Approaches of Office automation.......................................................................7
3.2 Benefit of Automation system approach..........................................................................8
3.3 Issues in Automation system approach............................................................................8
3.4 Benefit in Office portal approach.....................................................................................8
3.5 Issues in Office portal approach.......................................................................................8
3.6 Recommendation..............................................................................................................8
4.1 Difference between IaaS and PaaS in public cloud.............................................................9
4.2 Differences.......................................................................................................................9
5.1 Recommendation of model............................................................................................10
5.2 Problem 1: Availability..................................................................................................11
5.2.1 Problem 2: Data confidentiality..................................................................................11
5.2.2 Problem 3: Virtual machine........................................................................................11
5.2.3 Dealing with the Issue.................................................................................................11
6.0 Conclusion..........................................................................................................................12
7.0 Bibliography.......................................................................................................................13
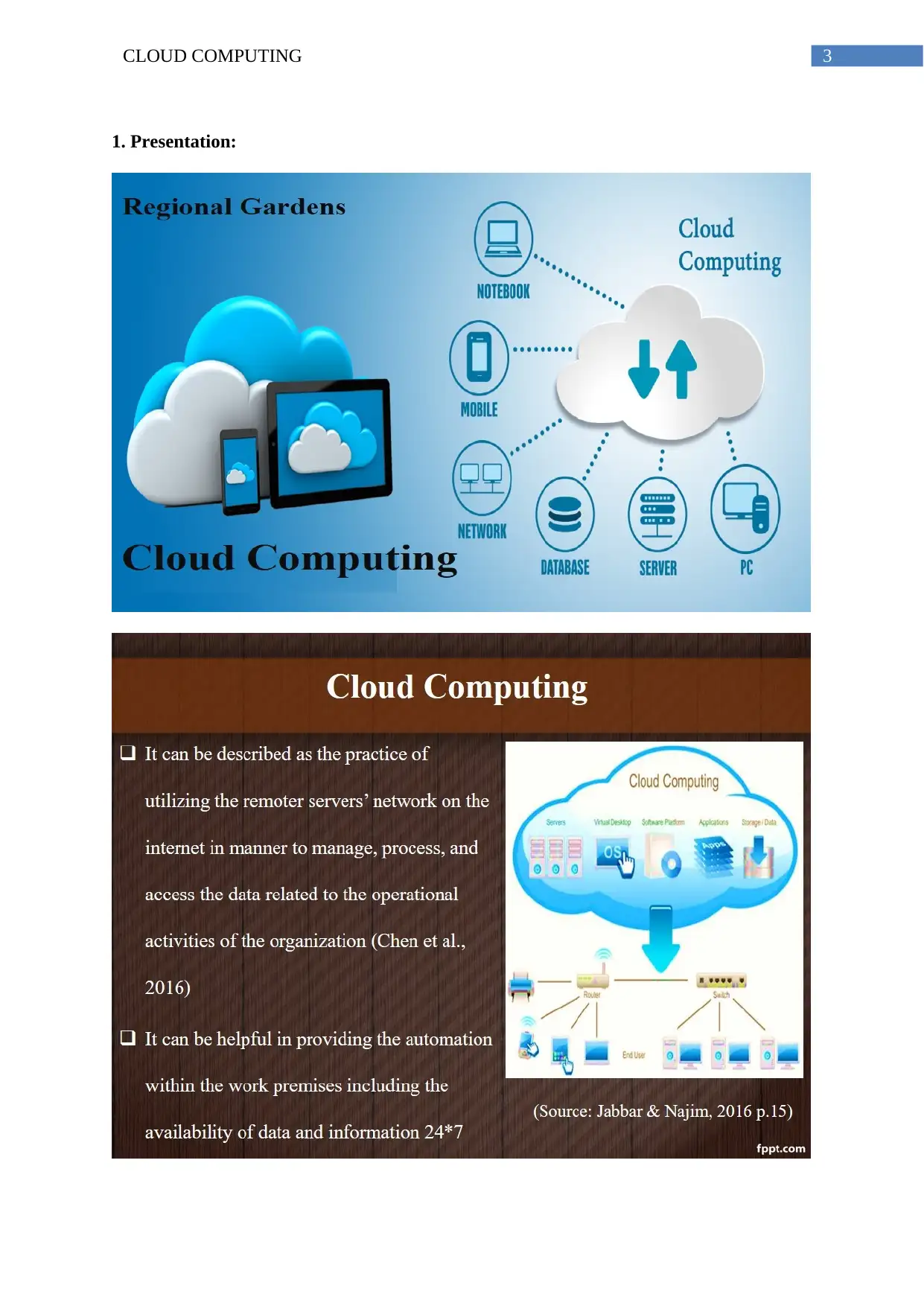
3CLOUD COMPUTING
1. Presentation:
1. Presentation:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
4CLOUD COMPUTING
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5CLOUD COMPUTING
6CLOUD COMPUTING
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

7CLOUD COMPUTING
2. Introduction
Technology has been continuously expanding with the passage of time and cloud
computing has become one of the trending technology among almost every industry. The aim
of this report is to present the aspects related to the implementation of the cloud services
within the existing system of the Regional garden’s and express al the available options
including the advantages and the disadvantages on these applications. Following report
presents the two approaches that can best suited for the regional gardens considering the
existing IT infrastructure and operational activities. Followed by this description and
classifications of the on demand services have been expressed in this report.
recommendations ad problems associated with the recommendation have also been proposed
in this report n the last section.
3. 1 Different Approaches of Office automation
Reviewing the functioning and size of the organizational network, centralized
database approach and office portal approach can be recommended. These approaches are
capable of providing effective office automation to the staffs of the Regional gardens.
Automation system: It is one of the best approach for the Regional garden system as it
can be implemented within the existing IT infrastructure of the Regional Gardens and can be
easily comply with the business’s framework. It can be helpful in the effective and efficient
wireless communication within the office premises and can be an effective solution for the
enhancement of the individual contribution within the organization. It can be utilized for
bearing some if the loads from the employees or staffs.
Office portal approach: It can be described as one of the secured approach for
providing automation in the office through ensuring that the user always logged in the system
to access the files and information.
2. Introduction
Technology has been continuously expanding with the passage of time and cloud
computing has become one of the trending technology among almost every industry. The aim
of this report is to present the aspects related to the implementation of the cloud services
within the existing system of the Regional garden’s and express al the available options
including the advantages and the disadvantages on these applications. Following report
presents the two approaches that can best suited for the regional gardens considering the
existing IT infrastructure and operational activities. Followed by this description and
classifications of the on demand services have been expressed in this report.
recommendations ad problems associated with the recommendation have also been proposed
in this report n the last section.
3. 1 Different Approaches of Office automation
Reviewing the functioning and size of the organizational network, centralized
database approach and office portal approach can be recommended. These approaches are
capable of providing effective office automation to the staffs of the Regional gardens.
Automation system: It is one of the best approach for the Regional garden system as it
can be implemented within the existing IT infrastructure of the Regional Gardens and can be
easily comply with the business’s framework. It can be helpful in the effective and efficient
wireless communication within the office premises and can be an effective solution for the
enhancement of the individual contribution within the organization. It can be utilized for
bearing some if the loads from the employees or staffs.
Office portal approach: It can be described as one of the secured approach for
providing automation in the office through ensuring that the user always logged in the system
to access the files and information.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8CLOUD COMPUTING
3.2 Benefit of Automation system approach
It will be helpful in providing the automation system that is capable of bearing the work load
rom the staffs and reducing through contributing in the various operational activities that
consumes lot of time. It has been best suited for the accomplishment of thee multi tasks
involved in the project or within the organization.
3.3 Issues in Automation system approach
The cost is comparatively high than rest of approaches to providing the automation. It
is a big transformational in the traditional system and might not be accepted by most of the
individuals. It cannot be operated manually and requires training for effectively flow of work.
3.4 Benefit in Office portal approach
The major benefit of this approach is the secured data and information access and
storage. It provides unique credentials for entering the network and different level of access
for the categorized data or information.
3.5 Issues in Office portal approach
It can be a risk for the organization considering the financial and reputation aspects.
An intruder or unauthorized individual cn enter the network and access to the sensitive ata or
information.
3.6 Recommendation
The most effective and efficient approach would be the office automation approach
that could established and accessed within the existing infrastructure and regional garden will
have to pay less price.
3.2 Benefit of Automation system approach
It will be helpful in providing the automation system that is capable of bearing the work load
rom the staffs and reducing through contributing in the various operational activities that
consumes lot of time. It has been best suited for the accomplishment of thee multi tasks
involved in the project or within the organization.
3.3 Issues in Automation system approach
The cost is comparatively high than rest of approaches to providing the automation. It
is a big transformational in the traditional system and might not be accepted by most of the
individuals. It cannot be operated manually and requires training for effectively flow of work.
3.4 Benefit in Office portal approach
The major benefit of this approach is the secured data and information access and
storage. It provides unique credentials for entering the network and different level of access
for the categorized data or information.
3.5 Issues in Office portal approach
It can be a risk for the organization considering the financial and reputation aspects.
An intruder or unauthorized individual cn enter the network and access to the sensitive ata or
information.
3.6 Recommendation
The most effective and efficient approach would be the office automation approach
that could established and accessed within the existing infrastructure and regional garden will
have to pay less price.

9CLOUD COMPUTING
4.1 Difference between IaaS and PaaS in public cloud
IaaS: Infrastructure as a Service is an on-demand service that can be used for highly
and scalable automated resources that can be utilized as self-provisioned and metered. Many
service providers in the market are providing the IaaS services such as Softlayer, Exoscale,
and many more.
Advantages: provides complete manual access to the VM and flexible in nature. There
are many applications without any complicated setup and could be utilized effectively and
efficiently. Third Party Management of the virtual setup and provide effective infrastructure.
Disadvantages: staffs cannot operate it manually and can be much costly comparing
to others. It is not flexible towards integrating with other services. Data is always exposed
and controlled by the third party.
PaaS: Platform as a Service that can be helpful in offering a platform that can lead to
the deployment and development of the software being used by the regional gardens.
Advantages: much cost effective than others, and allows full access and control over
the software. integration is easy and does not require high management skill for performing
the objectives.
Disadvantages: VM cannot be controlled, share platform will be used within the
office premises, and management can be complicated and time taking.
4.2 Differences
PaaS can be helpful in providing an operating system that will be boosting the
application services and enables an operating system. There is no need of the high-level
software as an operating system for the Infrastructure as a Service that consists of mainly pre-
configured hardware through interface or hypervisor unlike the PaaS. Paas enables the access
4.1 Difference between IaaS and PaaS in public cloud
IaaS: Infrastructure as a Service is an on-demand service that can be used for highly
and scalable automated resources that can be utilized as self-provisioned and metered. Many
service providers in the market are providing the IaaS services such as Softlayer, Exoscale,
and many more.
Advantages: provides complete manual access to the VM and flexible in nature. There
are many applications without any complicated setup and could be utilized effectively and
efficiently. Third Party Management of the virtual setup and provide effective infrastructure.
Disadvantages: staffs cannot operate it manually and can be much costly comparing
to others. It is not flexible towards integrating with other services. Data is always exposed
and controlled by the third party.
PaaS: Platform as a Service that can be helpful in offering a platform that can lead to
the deployment and development of the software being used by the regional gardens.
Advantages: much cost effective than others, and allows full access and control over
the software. integration is easy and does not require high management skill for performing
the objectives.
Disadvantages: VM cannot be controlled, share platform will be used within the
office premises, and management can be complicated and time taking.
4.2 Differences
PaaS can be helpful in providing an operating system that will be boosting the
application services and enables an operating system. There is no need of the high-level
software as an operating system for the Infrastructure as a Service that consists of mainly pre-
configured hardware through interface or hypervisor unlike the PaaS. Paas enables the access
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

10CLOUD COMPUTING
of the security through providing external security however; IaaS needs another third party
for the implementation of the security over the purchased infrastructure. There is not much
wide range to the PaaS for the flexibility in the security and it is available with the IaaS as a
variety of options can be selected as per the security of the document.
5.1 Recommendation of model
PaaS can be recommended as the best approach for the regional garden ltd.
considering the efficiency and output of the implementation. Very low skill is required for
operating the technology, and can be helpful in providing an effective automation to the
operational activities.
Supports DR, BC and high availability: For the unwanted accidents or disasters, tthere
is always maximum chances of losing the data or information saved in the system and IaaS
do provide a manageable and cost effective solution for recovering the lost information or
data. It also provides accessibility to the stored data or information from anywhere via
connecting to the internet.
Monitoring: Both the SaaS and PaaS needs to be properly audited and monitored in
manner to identify if there is any flaws or glitch within the system. However, IaaS
management does not requires any monitoring or evaluation.
Focus on Growth of the Business: Automation of the office through the
implementation of the cloud can be helpful in accomplishing the operational activities within
the organization. it can also allow the user to accomplish the activities through minimum
extra effort and present a precise solution. Thus, business growth can be managed as the
increase in the competitive market.
of the security through providing external security however; IaaS needs another third party
for the implementation of the security over the purchased infrastructure. There is not much
wide range to the PaaS for the flexibility in the security and it is available with the IaaS as a
variety of options can be selected as per the security of the document.
5.1 Recommendation of model
PaaS can be recommended as the best approach for the regional garden ltd.
considering the efficiency and output of the implementation. Very low skill is required for
operating the technology, and can be helpful in providing an effective automation to the
operational activities.
Supports DR, BC and high availability: For the unwanted accidents or disasters, tthere
is always maximum chances of losing the data or information saved in the system and IaaS
do provide a manageable and cost effective solution for recovering the lost information or
data. It also provides accessibility to the stored data or information from anywhere via
connecting to the internet.
Monitoring: Both the SaaS and PaaS needs to be properly audited and monitored in
manner to identify if there is any flaws or glitch within the system. However, IaaS
management does not requires any monitoring or evaluation.
Focus on Growth of the Business: Automation of the office through the
implementation of the cloud can be helpful in accomplishing the operational activities within
the organization. it can also allow the user to accomplish the activities through minimum
extra effort and present a precise solution. Thus, business growth can be managed as the
increase in the competitive market.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

11CLOUD COMPUTING
5.2 Problem 1: Availability
There is no availability of the direct control over the data access and storage system. It
can result in less reliable for the organization as it could possibly affect the security of the
data and information being stored or shared via the clouds. It is one of the greatest concerns
for the organization enjoying the application of the cloud computing.
5.2.1 Problem 2: Data confidentiality
It can be represented as the restricting the access to the data or information by an
unauthorized user and thus, protecting information to b exposed as it could effectively affect
the privacy and security of the individuals associated with the organization.
5.2.2 Problem 3: Virtual machine
Virtualization has transformed the traditional life of the organizations that has been
much more effective and time saving approach for these organizations. There are high risks
associated with this phase of the cloud computing. There are many issues associated with the
application of the hypervisor and the virtual machine.
5.2.3 Dealing with the Issue
For the users using the SaaS on demand services, there are many problems associated
with the frequent updates and the user is the only, who is responsible for testing the SaaS
application base.
Application of encryption algorithm directly in the framework of the application to
involve more security into the concept
“Segregation of the area of the concern would be directly be beneficial in a way of
minimizing the chances of the performance getting affected and on the other hand need of
testing can also be established ().”
5.2 Problem 1: Availability
There is no availability of the direct control over the data access and storage system. It
can result in less reliable for the organization as it could possibly affect the security of the
data and information being stored or shared via the clouds. It is one of the greatest concerns
for the organization enjoying the application of the cloud computing.
5.2.1 Problem 2: Data confidentiality
It can be represented as the restricting the access to the data or information by an
unauthorized user and thus, protecting information to b exposed as it could effectively affect
the privacy and security of the individuals associated with the organization.
5.2.2 Problem 3: Virtual machine
Virtualization has transformed the traditional life of the organizations that has been
much more effective and time saving approach for these organizations. There are high risks
associated with this phase of the cloud computing. There are many issues associated with the
application of the hypervisor and the virtual machine.
5.2.3 Dealing with the Issue
For the users using the SaaS on demand services, there are many problems associated
with the frequent updates and the user is the only, who is responsible for testing the SaaS
application base.
Application of encryption algorithm directly in the framework of the application to
involve more security into the concept
“Segregation of the area of the concern would be directly be beneficial in a way of
minimizing the chances of the performance getting affected and on the other hand need of
testing can also be established ().”

12CLOUD COMPUTING
6.0 Conclusion
The information provided in the above report can be helpful; in concluding that there
are many beneficial aspects related to the application of cloud services. The above report
presented a thorough research on the adoption and application of the cloud computing for the
accomplishment of the operational activities on regular basis. This report also focuses on the
issues and disadvantages, associated with the application of this technology. The above case
study was helpful in understanding the practical implementations and implications of the
cloud services. It can stated that despite of having certain issues in this adoption, the
advantages hide the risks and being trending technology among almost every industry.
6.0 Conclusion
The information provided in the above report can be helpful; in concluding that there
are many beneficial aspects related to the application of cloud services. The above report
presented a thorough research on the adoption and application of the cloud computing for the
accomplishment of the operational activities on regular basis. This report also focuses on the
issues and disadvantages, associated with the application of this technology. The above case
study was helpful in understanding the practical implementations and implications of the
cloud services. It can stated that despite of having certain issues in this adoption, the
advantages hide the risks and being trending technology among almost every industry.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





