Cloud Systems and Applications: Storage Options and System Security
VerifiedAdded on 2023/06/05
|18
|4727
|493
Report
AI Summary
This report evaluates storage options for enterprises, focusing on bandwidth and performance enhancements in cloud platforms. It discusses Amazon S3 as a viable solution, emphasizing service-oriented architecture and cloud governance. The report addresses scalability and storage issues, comparing AWS, Azure, and Google Cloud offerings, including object, block, and file storage. It also explores system security, covering authorization, privacy, authentication, and acceptable use policies. The integration of virtualization and grid computing is highlighted for improving cloud performance. The document concludes by stressing the importance of redundancy, fault tolerance, and data management in cloud environments.

Running head: CLOUD SYSTEMS AND APPLICATIONS
Cloud Systems and Applications: Report
Name of the Student
Name of the University
Author’s Note
Cloud Systems and Applications: Report
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
CLOUD SYSTEMS AND APPLICATIONS
Table of Contents
Introduction................................................................................................................................2
Answer to Question 1:................................................................................................................2
Answer to question 2:.................................................................................................................6
Answer to Question 2 (Learning outcomes 2, 5 and 6)..............................................................9
Application of System security in Cloud and distributed computing......................................10
a. Authorisation....................................................................................................................10
b. Privacy and mandatory access control policy..................................................................10
c. Authentication..................................................................................................................11
d. Acceptable Use.................................................................................................................11
Conclusion................................................................................................................................11
References................................................................................................................................13
CLOUD SYSTEMS AND APPLICATIONS
Table of Contents
Introduction................................................................................................................................2
Answer to Question 1:................................................................................................................2
Answer to question 2:.................................................................................................................6
Answer to Question 2 (Learning outcomes 2, 5 and 6)..............................................................9
Application of System security in Cloud and distributed computing......................................10
a. Authorisation....................................................................................................................10
b. Privacy and mandatory access control policy..................................................................10
c. Authentication..................................................................................................................11
d. Acceptable Use.................................................................................................................11
Conclusion................................................................................................................................11
References................................................................................................................................13

2
CLOUD SYSTEMS AND APPLICATIONS
Introduction
The report is prepared for the selection of the storage option for an enterprise and
analysing which storage option can provide highest total bandwidth and the design feature
used for increasing the performance of the cloud platform. The report also discusses the
security of the system that are used for managing access rights of the people and improve the
security of the cloud platform. The virtualization technology is used for physical
characteristic masking of the computer resources for eliminating the complexity of the
resources such as applications and systems that are interacted by the end user. For enabling
distributed computing Grid Computing is applied such that the data transport and computers
can be accessed by the users without any concern of operating system, account administration
and location. The virtualization and grid computing can be combined with each other for
further improvement since some of the properties of virtualization and grid computing is
inherited by the cloud computing with its own characteristics and risks.
Answer to Question 1:
Amazon Simple Storage Service (S3) would be the easiest options for the traditional
enterprises. This is because the traditional enterprise can contract with the cloud service
providers are needed sign the contract immediately after analysing the legal and regulatory
requirements. Transparency and trust is maintained between the service provider and the
client and visibility is also present that helps in improving the transparency. Moreover
Amazon Simple Storage Service (S3) uses a simple interface for web service that can be
utilized for storing and retrieving any amount of data from remote location at any time. With
the use of the service the traditional enterprise can gain maximum benefit and scale improve
their current business process. Service oriented architecture is used for supporting the service
orientation and used for the development of the enterprise cloud solution (Zhang et al. 2017).
CLOUD SYSTEMS AND APPLICATIONS
Introduction
The report is prepared for the selection of the storage option for an enterprise and
analysing which storage option can provide highest total bandwidth and the design feature
used for increasing the performance of the cloud platform. The report also discusses the
security of the system that are used for managing access rights of the people and improve the
security of the cloud platform. The virtualization technology is used for physical
characteristic masking of the computer resources for eliminating the complexity of the
resources such as applications and systems that are interacted by the end user. For enabling
distributed computing Grid Computing is applied such that the data transport and computers
can be accessed by the users without any concern of operating system, account administration
and location. The virtualization and grid computing can be combined with each other for
further improvement since some of the properties of virtualization and grid computing is
inherited by the cloud computing with its own characteristics and risks.
Answer to Question 1:
Amazon Simple Storage Service (S3) would be the easiest options for the traditional
enterprises. This is because the traditional enterprise can contract with the cloud service
providers are needed sign the contract immediately after analysing the legal and regulatory
requirements. Transparency and trust is maintained between the service provider and the
client and visibility is also present that helps in improving the transparency. Moreover
Amazon Simple Storage Service (S3) uses a simple interface for web service that can be
utilized for storing and retrieving any amount of data from remote location at any time. With
the use of the service the traditional enterprise can gain maximum benefit and scale improve
their current business process. Service oriented architecture is used for supporting the service
orientation and used for the development of the enterprise cloud solution (Zhang et al. 2017).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
CLOUD SYSTEMS AND APPLICATIONS
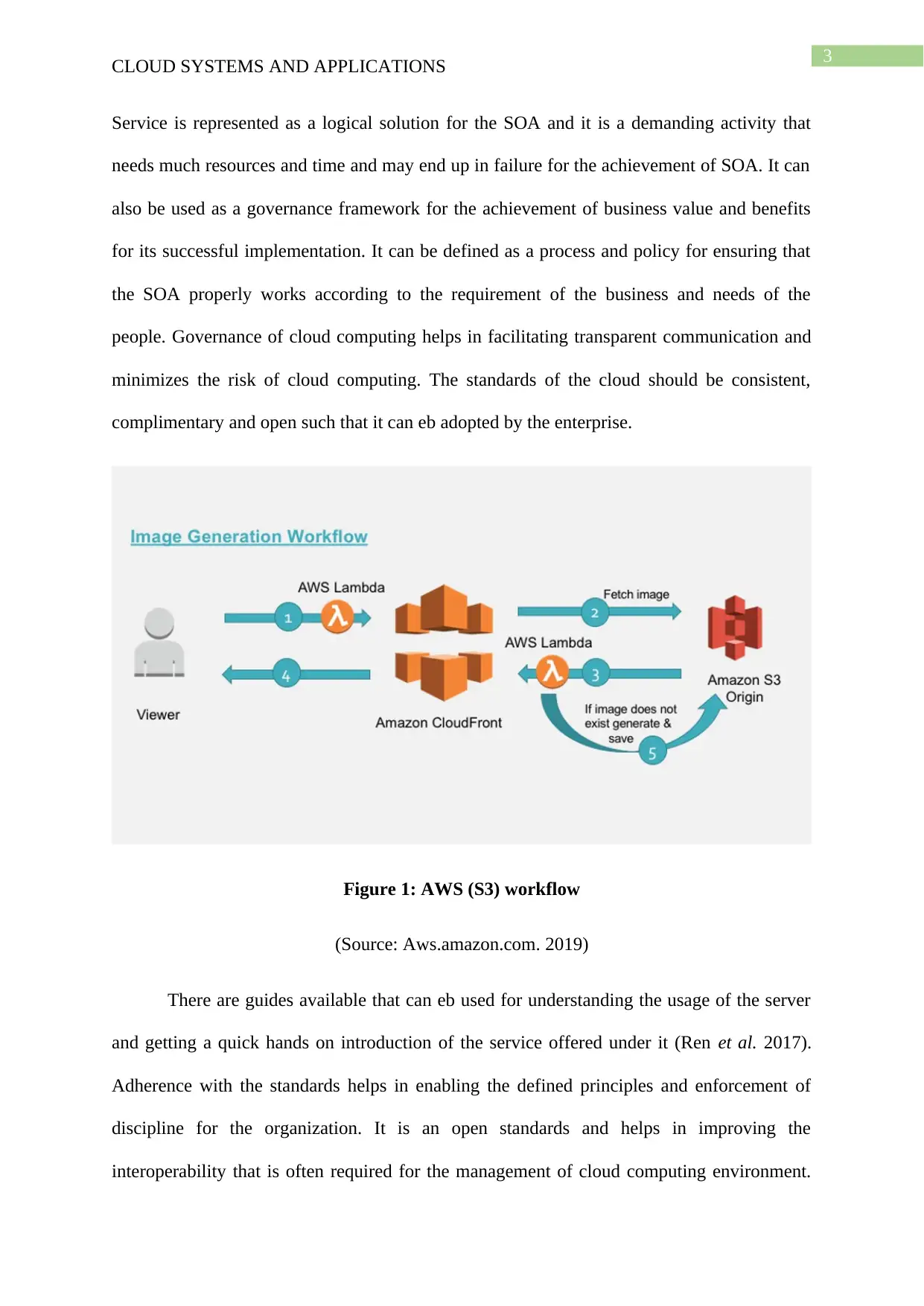
Service is represented as a logical solution for the SOA and it is a demanding activity that
needs much resources and time and may end up in failure for the achievement of SOA. It can
also be used as a governance framework for the achievement of business value and benefits
for its successful implementation. It can be defined as a process and policy for ensuring that
the SOA properly works according to the requirement of the business and needs of the
people. Governance of cloud computing helps in facilitating transparent communication and
minimizes the risk of cloud computing. The standards of the cloud should be consistent,
complimentary and open such that it can eb adopted by the enterprise.
Figure 1: AWS (S3) workflow
(Source: Aws.amazon.com. 2019)
There are guides available that can eb used for understanding the usage of the server
and getting a quick hands on introduction of the service offered under it (Ren et al. 2017).
Adherence with the standards helps in enabling the defined principles and enforcement of
discipline for the organization. It is an open standards and helps in improving the
interoperability that is often required for the management of cloud computing environment.
CLOUD SYSTEMS AND APPLICATIONS
Service is represented as a logical solution for the SOA and it is a demanding activity that
needs much resources and time and may end up in failure for the achievement of SOA. It can
also be used as a governance framework for the achievement of business value and benefits
for its successful implementation. It can be defined as a process and policy for ensuring that
the SOA properly works according to the requirement of the business and needs of the
people. Governance of cloud computing helps in facilitating transparent communication and
minimizes the risk of cloud computing. The standards of the cloud should be consistent,
complimentary and open such that it can eb adopted by the enterprise.
Figure 1: AWS (S3) workflow
(Source: Aws.amazon.com. 2019)
There are guides available that can eb used for understanding the usage of the server
and getting a quick hands on introduction of the service offered under it (Ren et al. 2017).
Adherence with the standards helps in enabling the defined principles and enforcement of
discipline for the organization. It is an open standards and helps in improving the
interoperability that is often required for the management of cloud computing environment.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
CLOUD SYSTEMS AND APPLICATIONS
For the implication of the compliance policy and standards existing standards of the
enterprise is needed to be evaluated. The standards exists with different domains such as
government, region and industry and a research is needed to be conducted for determining the
application of compliance with policy standards in the enterprise (Wang et al. 2017). The
standards of cloud is needed to be established and agreed in the early stage of adoption of
cloud platform. The policies should be applied to all the stakeholders in the cloud ecosystem
and a viable exception appeal procedure is needed to be addressed depending on special
circumstances. A reference architecture is needed to be placed for the cloud environment for
facilitating effective communication across the layers.
Figure 2: Cloud deployment models
(Source: Vold, N. 2012)
There are several components that are needed for the successful deployment of cloud
computing such as understanding the responsibility clearly, definition of IaaS, health of the
network and best practices and prepared staffs. For successfully migrating to the cloud
CLOUD SYSTEMS AND APPLICATIONS
For the implication of the compliance policy and standards existing standards of the
enterprise is needed to be evaluated. The standards exists with different domains such as
government, region and industry and a research is needed to be conducted for determining the
application of compliance with policy standards in the enterprise (Wang et al. 2017). The
standards of cloud is needed to be established and agreed in the early stage of adoption of
cloud platform. The policies should be applied to all the stakeholders in the cloud ecosystem
and a viable exception appeal procedure is needed to be addressed depending on special
circumstances. A reference architecture is needed to be placed for the cloud environment for
facilitating effective communication across the layers.
Figure 2: Cloud deployment models
(Source: Vold, N. 2012)
There are several components that are needed for the successful deployment of cloud
computing such as understanding the responsibility clearly, definition of IaaS, health of the
network and best practices and prepared staffs. For successfully migrating to the cloud

5
CLOUD SYSTEMS AND APPLICATIONS
platform a planning is needed to be done similar with the other projects and the stakeholders
involved in the migration is needed to understand the roles and responsibility for addressing
the problem in the early stage of development of the project and completing the migration in
the estimated cost and schedule. The infrastructure of the datacentre and its reliability is
important for the development of virtual infrastructure, upgrades, accessibility, uptimes and
security (Qu et al. 2016). Core routing and connectivity of the network is also important for
the deployment of distributed data and application. Network health and best practice is
needed to be followed such as internal cabling, battery backup, stable power and cooling
facility is needed to be available. It is also important to manage the connectivity of the
network devices and reduce the loss of packet in the network implementation of QoS policy
for increasing the efficiency of the network. The server and firewall guidelines are also
needed to be followed and the capacity of the cloud solution is need to be verified for
documentation of the scope of migration. A network monitoring system is also needed to be
deployed the WAN and LAN solution is needed to be tested for the configuration of Netflow
(Calheiros et al. 2015). For getting the maximum benefit from the cloud environment the
current requirement of the business is needed to be analysed. Multi criteria decision making
model can eb implemented for selection and agreeing on the set of attributes that the chosen
cloud platform fulfils. The selection is needed to be made based on experience and the result
of the goals. The types and classification of the clouds is also needed to be analysed for the
adoption of the cloud platform. The selection of the platform is dependent on the amount and
data size that the application supports and the number of concurrent users. The capability of
ensuring constant operation and ensuring that no data is loss should also be analysed for
increasing the reliability of cloud service (Liu et al. 2018). Quality of service is also needed
to be maintained such that it is ensured that the resource requirement are meet. The cloud
platform should also help in on time reaction and adapting the changes in need for the
CLOUD SYSTEMS AND APPLICATIONS
platform a planning is needed to be done similar with the other projects and the stakeholders
involved in the migration is needed to understand the roles and responsibility for addressing
the problem in the early stage of development of the project and completing the migration in
the estimated cost and schedule. The infrastructure of the datacentre and its reliability is
important for the development of virtual infrastructure, upgrades, accessibility, uptimes and
security (Qu et al. 2016). Core routing and connectivity of the network is also important for
the deployment of distributed data and application. Network health and best practice is
needed to be followed such as internal cabling, battery backup, stable power and cooling
facility is needed to be available. It is also important to manage the connectivity of the
network devices and reduce the loss of packet in the network implementation of QoS policy
for increasing the efficiency of the network. The server and firewall guidelines are also
needed to be followed and the capacity of the cloud solution is need to be verified for
documentation of the scope of migration. A network monitoring system is also needed to be
deployed the WAN and LAN solution is needed to be tested for the configuration of Netflow
(Calheiros et al. 2015). For getting the maximum benefit from the cloud environment the
current requirement of the business is needed to be analysed. Multi criteria decision making
model can eb implemented for selection and agreeing on the set of attributes that the chosen
cloud platform fulfils. The selection is needed to be made based on experience and the result
of the goals. The types and classification of the clouds is also needed to be analysed for the
adoption of the cloud platform. The selection of the platform is dependent on the amount and
data size that the application supports and the number of concurrent users. The capability of
ensuring constant operation and ensuring that no data is loss should also be analysed for
increasing the reliability of cloud service (Liu et al. 2018). Quality of service is also needed
to be maintained such that it is ensured that the resource requirement are meet. The cloud
platform should also help in on time reaction and adapting the changes in need for the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
CLOUD SYSTEMS AND APPLICATIONS
management of the resources. Redundancy of the data and service is needed to be introduced
such that the failure can be masked. Fault tolerance and achievement of replication and
distribution of data and service is also important for increasing the availability of data. The
return of investment for the adoption is needed to be calculated and data management is also
necessary for increasing the flexibility and distribution of the resources (Li et al. 2017).
Consistency and awareness of the data location and latencies are needed to be eliminated for
the distribution of the workload and assuring that security, privacy and compliance is
maintained.
Answer to question 2:
The scalability and the storage issues with cloud computing is needed to be evaluated
before the selection of the cloud service an vendor. The size of the object that is needed to be
stored is needed to be identified for requesting the bandwidth rate. The utilization of access
pattern and the workload of the application is also dependent for meeting the requirement
performance. The scale limit of the standard storage account is 2PB for Europe and US and
500 TB for the rest of the region including UK. The default limit is 250 storage account per
subscription per region including the premium and the standard accounts. There re no limits
for the number of blob containers, fie shares, tables, message per account storage and blobs.
Each of the storage account can handle a maximum request rate of 20,000 request in each
second (Abawajy and Hassan 2017). The storage comes in standard and SSD options and
selection of the SSD would improve the performance and response from the cloud servers but
they are costly when compared with standard options available in the market. The version
available with Azure is known as Managed Disks while the Google’s version is known as
Persistent Disk. The size of the volumes varies with the service provider for example the
AWS volume size varies from 1 Gb to 16 Tb, 4 Gb to 16 Tb for the PIOPs. The block size of
Azure varies from 1 to 1 TB and the Google varies from 1 Gb to 64 Tb. For purchasing the
CLOUD SYSTEMS AND APPLICATIONS
management of the resources. Redundancy of the data and service is needed to be introduced
such that the failure can be masked. Fault tolerance and achievement of replication and
distribution of data and service is also important for increasing the availability of data. The
return of investment for the adoption is needed to be calculated and data management is also
necessary for increasing the flexibility and distribution of the resources (Li et al. 2017).
Consistency and awareness of the data location and latencies are needed to be eliminated for
the distribution of the workload and assuring that security, privacy and compliance is
maintained.
Answer to question 2:
The scalability and the storage issues with cloud computing is needed to be evaluated
before the selection of the cloud service an vendor. The size of the object that is needed to be
stored is needed to be identified for requesting the bandwidth rate. The utilization of access
pattern and the workload of the application is also dependent for meeting the requirement
performance. The scale limit of the standard storage account is 2PB for Europe and US and
500 TB for the rest of the region including UK. The default limit is 250 storage account per
subscription per region including the premium and the standard accounts. There re no limits
for the number of blob containers, fie shares, tables, message per account storage and blobs.
Each of the storage account can handle a maximum request rate of 20,000 request in each
second (Abawajy and Hassan 2017). The storage comes in standard and SSD options and
selection of the SSD would improve the performance and response from the cloud servers but
they are costly when compared with standard options available in the market. The version
available with Azure is known as Managed Disks while the Google’s version is known as
Persistent Disk. The size of the volumes varies with the service provider for example the
AWS volume size varies from 1 Gb to 16 Tb, 4 Gb to 16 Tb for the PIOPs. The block size of
Azure varies from 1 to 1 TB and the Google varies from 1 Gb to 64 Tb. For purchasing the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
CLOUD SYSTEMS AND APPLICATIONS
block the faster speed needed for accessing the data residing in SSD is needed to be
considered and here Google leads for offering 400,000 IOPs for read and 30,000 IOPs for
writing (Thota et al. 2018). Google also leads by providing customer more choice in
providing size of block storage.
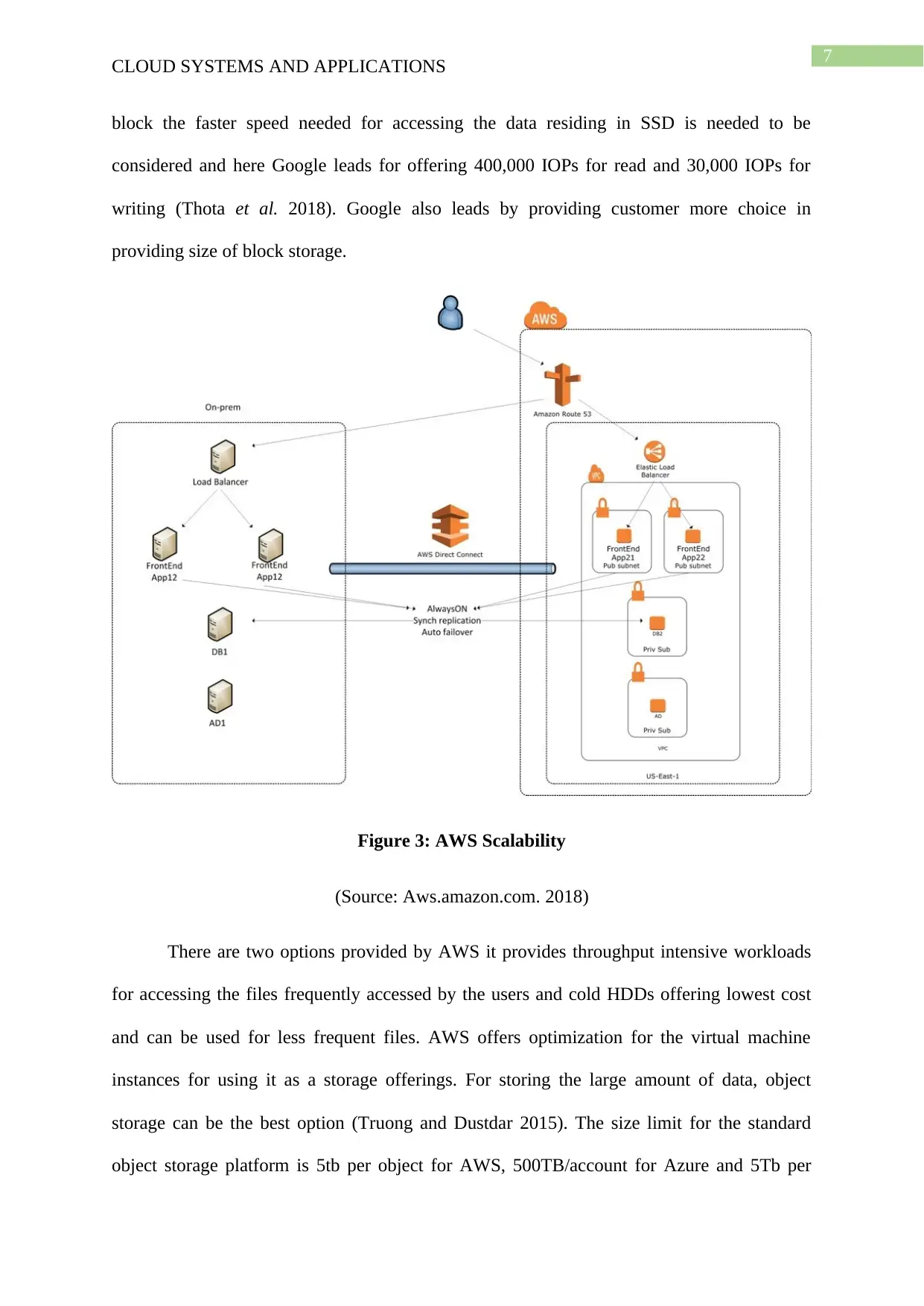
Figure 3: AWS Scalability
(Source: Aws.amazon.com. 2018)
There are two options provided by AWS it provides throughput intensive workloads
for accessing the files frequently accessed by the users and cold HDDs offering lowest cost
and can be used for less frequent files. AWS offers optimization for the virtual machine
instances for using it as a storage offerings. For storing the large amount of data, object
storage can be the best option (Truong and Dustdar 2015). The size limit for the standard
object storage platform is 5tb per object for AWS, 500TB/account for Azure and 5Tb per
CLOUD SYSTEMS AND APPLICATIONS
block the faster speed needed for accessing the data residing in SSD is needed to be
considered and here Google leads for offering 400,000 IOPs for read and 30,000 IOPs for
writing (Thota et al. 2018). Google also leads by providing customer more choice in
providing size of block storage.
Figure 3: AWS Scalability
(Source: Aws.amazon.com. 2018)
There are two options provided by AWS it provides throughput intensive workloads
for accessing the files frequently accessed by the users and cold HDDs offering lowest cost
and can be used for less frequent files. AWS offers optimization for the virtual machine
instances for using it as a storage offerings. For storing the large amount of data, object
storage can be the best option (Truong and Dustdar 2015). The size limit for the standard
object storage platform is 5tb per object for AWS, 500TB/account for Azure and 5Tb per

8
CLOUD SYSTEMS AND APPLICATIONS
object for Google. The design of the object storage are designed such that the data residing in
the servers are durable but in case of Azure there are no availability of service level
agreement based on durability.
The file storage option is an emerging use case and it is similar with the network file
system where the user can mount the files in system using any device or VM and retrieve or
read the file. The offering of the file storage are not fully features when it is compared with
object storage and block storage. AWS offers this category of storage option and is names as
Elastic File system and it allows the users to mount the files from AWS EC2 virtual machine
within virtual private cloud or on premises services using AWS direct connector or VPC
(Virtual Private Connector) (Suciu et al. 2015). It has no size limits and the scalability can be
increased based on the needs of the user. It also has the offering of 50mbps throughput for
each TB storage. The throughput can be increased on payment and it can maximum reach to
100mbps at the rate starting from $0.30/GB per month (Puthal et al. 2015). The primary
object storage platform is Simple Storage Service, a standard infrequent access for Glaciers
and cool storage is offered by it. Google also have two type of storage options i.e Google
Cloud Storage Nearline and Google Cloud Storage Coldline primarily designed for archival.
There is also hot and cool option present in Azure and the cool storage is used for storing
achieved data and each of Google and AWS have object limit of 5 TB for the size of the
object while Azure offers an account limit of 500TB for storing data (Jararweh et al. 2016).
The cloud storage definition can be used for hosting and installing the client application in
the computer of the user. The program is used for transmitting files that is chosen by the user
via the internet such that the cloud service provider can able to share and access them on
different devices owned by them. It is the role of the cloud service provider or synchronizing
the files and make them available for the person intended to share the file or the group
(Khanna and Anand 2016). The sharing can be done with the help of private and public link
CLOUD SYSTEMS AND APPLICATIONS
object for Google. The design of the object storage are designed such that the data residing in
the servers are durable but in case of Azure there are no availability of service level
agreement based on durability.
The file storage option is an emerging use case and it is similar with the network file
system where the user can mount the files in system using any device or VM and retrieve or
read the file. The offering of the file storage are not fully features when it is compared with
object storage and block storage. AWS offers this category of storage option and is names as
Elastic File system and it allows the users to mount the files from AWS EC2 virtual machine
within virtual private cloud or on premises services using AWS direct connector or VPC
(Virtual Private Connector) (Suciu et al. 2015). It has no size limits and the scalability can be
increased based on the needs of the user. It also has the offering of 50mbps throughput for
each TB storage. The throughput can be increased on payment and it can maximum reach to
100mbps at the rate starting from $0.30/GB per month (Puthal et al. 2015). The primary
object storage platform is Simple Storage Service, a standard infrequent access for Glaciers
and cool storage is offered by it. Google also have two type of storage options i.e Google
Cloud Storage Nearline and Google Cloud Storage Coldline primarily designed for archival.
There is also hot and cool option present in Azure and the cool storage is used for storing
achieved data and each of Google and AWS have object limit of 5 TB for the size of the
object while Azure offers an account limit of 500TB for storing data (Jararweh et al. 2016).
The cloud storage definition can be used for hosting and installing the client application in
the computer of the user. The program is used for transmitting files that is chosen by the user
via the internet such that the cloud service provider can able to share and access them on
different devices owned by them. It is the role of the cloud service provider or synchronizing
the files and make them available for the person intended to share the file or the group
(Khanna and Anand 2016). The sharing can be done with the help of private and public link
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
CLOUD SYSTEMS AND APPLICATIONS
and if the file is intended to share with any person a public link is selected and the through
put of the link can affect the performance of the cloud service.
Answer to Question 2 (Learning outcomes 2, 5 and 6)
For analysing the weakness for the existing cloud management an analysis is
performed and it helps in evaluation of capability of the organisation along with the possible
threats and opportunities (Villari et al. 2016). It is improves the flexibility for sharing data
between the different users from remote location. The storage space of the cloud platform can
be expanded and it helps in enhancing the data and service availability. It can be used for the
development of operating system depending application and improve service and
performance (Bitam, Mellouk and Zeadally 2015). The reliability of data and service can be
improved while reducing the cost, workload on the server. It also improves the management
of power and improves the level of security by enabling centralized monitoring and software
maintenance. It helps in enhancing the business agility and maintains IT security and controls
as it have transparency in pricing (Tan et al. 2019). It is flexible and resilient for data
recovery and the enforcement of SLA guarantees the service form cloud service providers to
client.
CLOUD SYSTEMS AND APPLICATIONS
and if the file is intended to share with any person a public link is selected and the through
put of the link can affect the performance of the cloud service.
Answer to Question 2 (Learning outcomes 2, 5 and 6)
For analysing the weakness for the existing cloud management an analysis is
performed and it helps in evaluation of capability of the organisation along with the possible
threats and opportunities (Villari et al. 2016). It is improves the flexibility for sharing data
between the different users from remote location. The storage space of the cloud platform can
be expanded and it helps in enhancing the data and service availability. It can be used for the
development of operating system depending application and improve service and
performance (Bitam, Mellouk and Zeadally 2015). The reliability of data and service can be
improved while reducing the cost, workload on the server. It also improves the management
of power and improves the level of security by enabling centralized monitoring and software
maintenance. It helps in enhancing the business agility and maintains IT security and controls
as it have transparency in pricing (Tan et al. 2019). It is flexible and resilient for data
recovery and the enforcement of SLA guarantees the service form cloud service providers to
client.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
CLOUD SYSTEMS AND APPLICATIONS
Figure 4: Efficiency of cloud computing
(Source: Matthewb.id.au. 2019)
It can be used for removal of limitation of latency and improving the utilization of
bandwidth. The implementation of the cloud in the current business can help in monitoring
the network dynamically and resolve the different technical issues in the network. It also
provides opportunity for the new application for deploying their product and service with a
nominal cost (Chen et al. 2017). It is also adaptive with the future needs and can be used as a
back end for different types of applications. It speeds up the deployment and preserves the
dynamic flexibility and has the ability to relocate the security resources for creating a defence
for the system.
Application of System security in Cloud and distributed computing
It is important to manage the identity and access management with the four main
component such as authorization, authentication, user management and credential
CLOUD SYSTEMS AND APPLICATIONS
Figure 4: Efficiency of cloud computing
(Source: Matthewb.id.au. 2019)
It can be used for removal of limitation of latency and improving the utilization of
bandwidth. The implementation of the cloud in the current business can help in monitoring
the network dynamically and resolve the different technical issues in the network. It also
provides opportunity for the new application for deploying their product and service with a
nominal cost (Chen et al. 2017). It is also adaptive with the future needs and can be used as a
back end for different types of applications. It speeds up the deployment and preserves the
dynamic flexibility and has the ability to relocate the security resources for creating a defence
for the system.
Application of System security in Cloud and distributed computing
It is important to manage the identity and access management with the four main
component such as authorization, authentication, user management and credential

11
CLOUD SYSTEMS AND APPLICATIONS
management (Wang, Li and Wang 2017). The cloud platform should not be available to all
the users, identity and access management is needed to be implemented for improving the
security of the cloud platform. Different policies are necessary to be integrated such that the
identity of the user and access privilege is needed to be maintained (Luo and Ren 2016). The
user should be able to access the resources by authenticating using username and password
and it can eb supported by the digital signature, registered IP address and MAC and digital
certificates. The access control should also be enforced and the relationship between access
control rights, resource availability and identities is also needed to be defined.
a. Authorisation
It can be defined as a security mechanism that is able to handle the security
mechanism for determining the client or user privileged and access related rights allocate to
the user for accessing the resources of the system, services, data, files and features of the
application. For the authorization authentication is necessary and it helps in maintaining the
identity and verification of the user (Cito et al. 2015). The administrator is assigned with
different permission for covering all the user and system resources. For the authorization the
authentication of the user is verified in the basis of access rules for granting or refusing the
system resources.
b. Privacy and mandatory access control policy
The use of public key infrastructure is used for the management of asymmetric key
issuance dependent on the public key infrastructure mechanism. It exists as a data format,
practice, rules and protocols which enables the large scale system for using the public key
cryptography securely (Luo et al. 2016). The public key infrastructure is used for the
association of public keys with corresponding key for enabling verification of validity of the
key. It is reliable on the digital certificate use and binds the certificate with the public key.
CLOUD SYSTEMS AND APPLICATIONS
management (Wang, Li and Wang 2017). The cloud platform should not be available to all
the users, identity and access management is needed to be implemented for improving the
security of the cloud platform. Different policies are necessary to be integrated such that the
identity of the user and access privilege is needed to be maintained (Luo and Ren 2016). The
user should be able to access the resources by authenticating using username and password
and it can eb supported by the digital signature, registered IP address and MAC and digital
certificates. The access control should also be enforced and the relationship between access
control rights, resource availability and identities is also needed to be defined.
a. Authorisation
It can be defined as a security mechanism that is able to handle the security
mechanism for determining the client or user privileged and access related rights allocate to
the user for accessing the resources of the system, services, data, files and features of the
application. For the authorization authentication is necessary and it helps in maintaining the
identity and verification of the user (Cito et al. 2015). The administrator is assigned with
different permission for covering all the user and system resources. For the authorization the
authentication of the user is verified in the basis of access rules for granting or refusing the
system resources.
b. Privacy and mandatory access control policy
The use of public key infrastructure is used for the management of asymmetric key
issuance dependent on the public key infrastructure mechanism. It exists as a data format,
practice, rules and protocols which enables the large scale system for using the public key
cryptography securely (Luo et al. 2016). The public key infrastructure is used for the
association of public keys with corresponding key for enabling verification of validity of the
key. It is reliable on the digital certificate use and binds the certificate with the public key.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




