CO4512 Information Security Management: CloudXYZ Risk Assessment
VerifiedAdded on 2023/06/08
|15
|3591
|117
Report
AI Summary
This report provides a detailed risk assessment for CloudXYZ, focusing on information security management. It begins with an abstract outlining the purpose of the assessment, which is to identify and mitigate potential risks to data security and privacy. The introduction provides background on ISO standards, specifically ISO/IEC 27001, and explains how these standards are applied to CloudXYZ's cloud-based information system. The report then outlines the risk assessment methodology, including the stages involved in identifying, evaluating, and managing risks. It defines system owners, assets (primary and secondary), and potential threats, categorizing them based on their severity. The report also identifies vulnerabilities associated with each asset, providing CVE codes where applicable. The assessment covers various assets, including mail servers, web servers, authentication servers, customer databases, and user PCs, along with the threats they face, such as system hacking, viruses, and spoofing attacks. The report concludes with a comprehensive analysis of the identified risks, providing a basis for developing security measures to protect CloudXYZ's information systems and data.

CO4512
INFORMATION SECURITY MANAGEMENT
INFORMATION SECURITY MANAGEMENT
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ABSTRACT
The report will contain a deep understanding of the CloudXYZ Company which have a procedure for the
calculation of the risk which uses and follow some rules of ISO. The reason behind performing the risk
assessment is to handle the issues of improving the security and management. The potential risk is being
calculated for the risk assessment depending on its quality and the quantity of the known threat. The
calculation of risk is the main purpose for which any system failure can be avoided. The scenario that
has been given over here has a risk assessment that is being conducted for reducing the investment that
is being done to improve the system for security for which work could be done for the system in which
data could be loss, fraud data could be provided or any privacy statment could be steal.
INTRODUCTION
ISO is an International Organization for Standardization which consist of a non-dependent, international
body that is private and it consist of bodies with 161 national level of standardization. In the year 1947
for the month of February it was founded as the result of having two of the renowned organizations in
combination with each other are:
1. United Nations Standard Coordinating Committee (UNSCC)
2. International Federation of National Standardizing Associations
The organization aim at easing the industrial standards unifications and the international coordination.
The standards of the ISO are as follow:
ISO 50001 Energy Management
ISO/IEC 27001 Management of Information Security
ISO/IEC 17025 calibration and testing laboratory
ISO 9001 Quality Management
In this assessment we have decided to use ISO/IEC 27001 Management of Information System
for the CloudXYZ Company. There are some standards that have a set for ISO/IEC 27001
Management of Information System whose help is there for any organization through which
the organization could keep the resources of the organization secure (Hart et al. 2016).
With the use of CloudXYZ standardization, the information system could be securely managed
as it consists of information for the user data that are stored in the cloud. The CloudXYZ has an
authentication server that is accountable to approve the clients’ permits (username/account
and password). During the performance of the task authorization, it may happen that there
may be interaction between the client database and the authorization server in which the
customer data is content. When the verification is done, the right will be provided to the
customer so that the can use the data that is stored in the cloud or else log in to the virtual
server.
The enterprise of CloudXYZ Company will be able to identify the use of ISO/IEC 27001
Management of Information Security for the assessment of the risk that potentially can cause
risks of the security threat for the privacy of the user and the data and according to it plan
The report will contain a deep understanding of the CloudXYZ Company which have a procedure for the
calculation of the risk which uses and follow some rules of ISO. The reason behind performing the risk
assessment is to handle the issues of improving the security and management. The potential risk is being
calculated for the risk assessment depending on its quality and the quantity of the known threat. The
calculation of risk is the main purpose for which any system failure can be avoided. The scenario that
has been given over here has a risk assessment that is being conducted for reducing the investment that
is being done to improve the system for security for which work could be done for the system in which
data could be loss, fraud data could be provided or any privacy statment could be steal.
INTRODUCTION
ISO is an International Organization for Standardization which consist of a non-dependent, international
body that is private and it consist of bodies with 161 national level of standardization. In the year 1947
for the month of February it was founded as the result of having two of the renowned organizations in
combination with each other are:
1. United Nations Standard Coordinating Committee (UNSCC)
2. International Federation of National Standardizing Associations
The organization aim at easing the industrial standards unifications and the international coordination.
The standards of the ISO are as follow:
ISO 50001 Energy Management
ISO/IEC 27001 Management of Information Security
ISO/IEC 17025 calibration and testing laboratory
ISO 9001 Quality Management
In this assessment we have decided to use ISO/IEC 27001 Management of Information System
for the CloudXYZ Company. There are some standards that have a set for ISO/IEC 27001
Management of Information System whose help is there for any organization through which
the organization could keep the resources of the organization secure (Hart et al. 2016).
With the use of CloudXYZ standardization, the information system could be securely managed
as it consists of information for the user data that are stored in the cloud. The CloudXYZ has an
authentication server that is accountable to approve the clients’ permits (username/account
and password). During the performance of the task authorization, it may happen that there
may be interaction between the client database and the authorization server in which the
customer data is content. When the verification is done, the right will be provided to the
customer so that the can use the data that is stored in the cloud or else log in to the virtual
server.
The enterprise of CloudXYZ Company will be able to identify the use of ISO/IEC 27001
Management of Information Security for the assessment of the risk that potentially can cause
risks of the security threat for the privacy of the user and the data and according to it plan
about the risk where the risk could be eliminated properly and the Company of CloudXYZ meet
the security of the information with international standards.
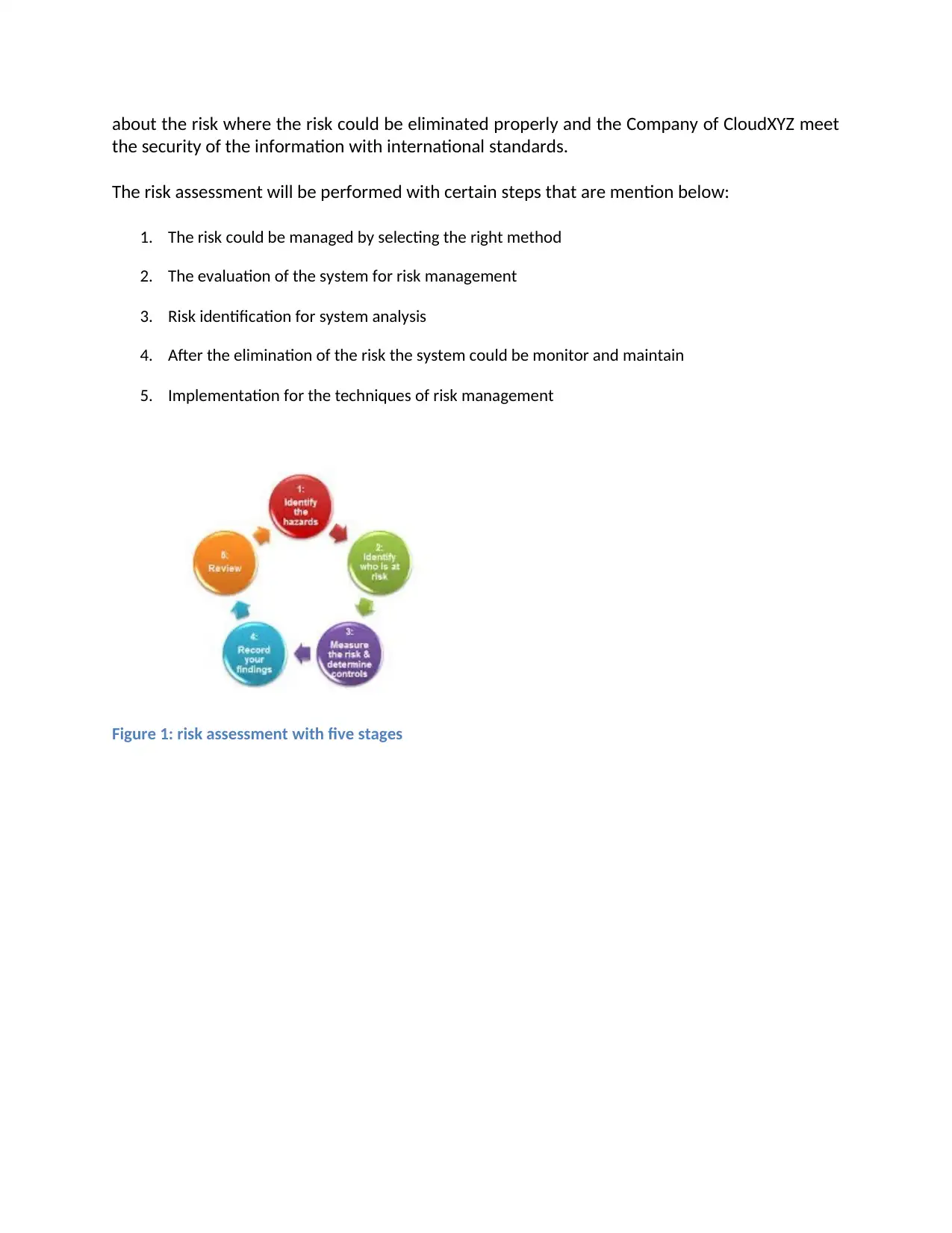
The risk assessment will be performed with certain steps that are mention below:
1. The risk could be managed by selecting the right method
2. The evaluation of the system for risk management
3. Risk identification for system analysis
4. After the elimination of the risk the system could be monitor and maintain
5. Implementation for the techniques of risk management
Figure 1: risk assessment with five stages
the security of the information with international standards.
The risk assessment will be performed with certain steps that are mention below:
1. The risk could be managed by selecting the right method
2. The evaluation of the system for risk management
3. Risk identification for system analysis
4. After the elimination of the risk the system could be monitor and maintain
5. Implementation for the techniques of risk management
Figure 1: risk assessment with five stages
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
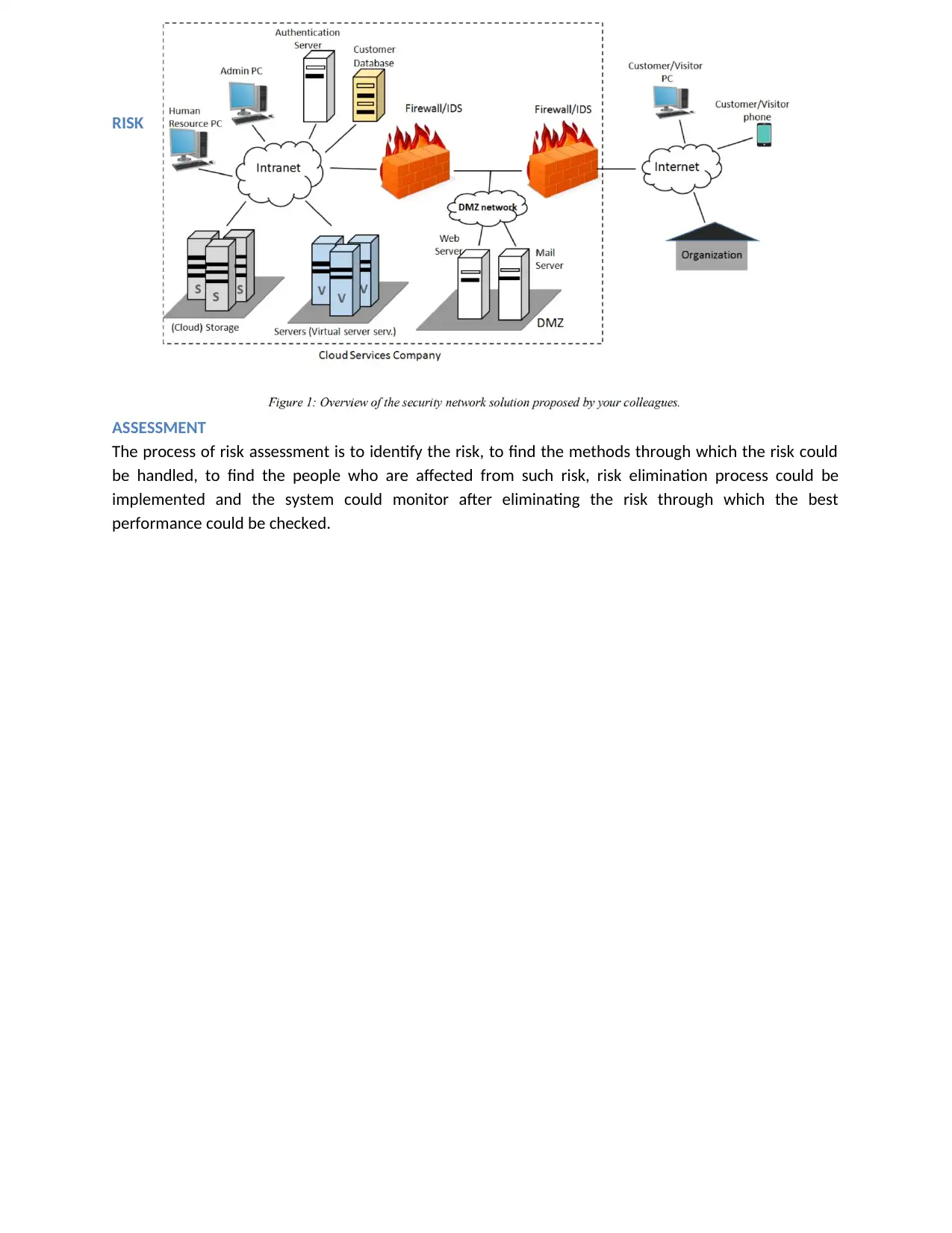
RISK
ASSESSMENT
The process of risk assessment is to identify the risk, to find the methods through which the risk could
be handled, to find the people who are affected from such risk, risk elimination process could be
implemented and the system could monitor after eliminating the risk through which the best
performance could be checked.
ASSESSMENT
The process of risk assessment is to identify the risk, to find the methods through which the risk could
be handled, to find the people who are affected from such risk, risk elimination process could be
implemented and the system could monitor after eliminating the risk through which the best
performance could be checked.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The figure that is displayed above proposed a system for which the team provide some security for the
system of the CloudXYZ Company. The process of risk assessment produces a results that will have a
risks which can cause failure in the security system.
OWNER SPECIFICATION
In this section of the article the system owner will be specified. The system users are provided below:
Visitors that visits the bank
Departmant of maintainance
Employees
Bank Staff
Developers
Management team of the band
The cloud system wanted by the client
Team of the Administration
Human Resource
ASSETS
Resource/Asset – Poeple, information and properties. Clients and Representatives were incorporated by
the individuals alongside the other people who were welcomed, some of the example like, visitors or
contractual workers. There are resources that are both tangible and intangible and comprise of the
resources of the property of which an esteem could be relegated. There are exclusive data and notoriety
that has incorporated intangible resources. Incorporate the data or information for the database, data
for the basic organization, other intangible things that are numerous and programming codes (Smith et
al. 2014).
system of the CloudXYZ Company. The process of risk assessment produces a results that will have a
risks which can cause failure in the security system.
OWNER SPECIFICATION
In this section of the article the system owner will be specified. The system users are provided below:
Visitors that visits the bank
Departmant of maintainance
Employees
Bank Staff
Developers
Management team of the band
The cloud system wanted by the client
Team of the Administration
Human Resource
ASSETS
Resource/Asset – Poeple, information and properties. Clients and Representatives were incorporated by
the individuals alongside the other people who were welcomed, some of the example like, visitors or
contractual workers. There are resources that are both tangible and intangible and comprise of the
resources of the property of which an esteem could be relegated. There are exclusive data and notoriety
that has incorporated intangible resources. Incorporate the data or information for the database, data
for the basic organization, other intangible things that are numerous and programming codes (Smith et
al. 2014).
The aim could be achieve by using the asset of the helping object and the resources. This asset could be
anything that include people, cash, machines etc. The asset or the resource purpose is providing some
profit so that utilizer could get it.
There are two types of assets:
1. The Primary assets
2. The Secondary assets
There are certain advantages for the primary resources that are transported to import certain sort of
benefits. There are default extension of the primary resources that import the writes of other resource.
After the primary resources there are advantages transported to secondary resources. The super-
arrangement of the primary resources is constitute in the secondary resources.
The CloudXYZ Company has a system asset:
Asset id Asset Name Type Remark
S1. Mail server Primary Asset The mail server contain all the
information about the email
that the company receive and
send.
S2. Web server Primary Asset The website displays all the
details of the company.
S3. Authentication server Primary Asset The server is being used by
the CloudXYZ company were
the user is authorized or else
permit is given to log in to the
system.
S4. Customer database Primary Asset The customer details and the
related data are all saved
here.
S5. Firewall Secondary asset The users filtering is provided
over here. The system is
access by only those users
that are authorized.
S6. Virtual servers Secondary Asset The virtual server is added just
after the actual servers on
which the extra load could be
anything that include people, cash, machines etc. The asset or the resource purpose is providing some
profit so that utilizer could get it.
There are two types of assets:
1. The Primary assets
2. The Secondary assets
There are certain advantages for the primary resources that are transported to import certain sort of
benefits. There are default extension of the primary resources that import the writes of other resource.
After the primary resources there are advantages transported to secondary resources. The super-
arrangement of the primary resources is constitute in the secondary resources.
The CloudXYZ Company has a system asset:
Asset id Asset Name Type Remark
S1. Mail server Primary Asset The mail server contain all the
information about the email
that the company receive and
send.
S2. Web server Primary Asset The website displays all the
details of the company.
S3. Authentication server Primary Asset The server is being used by
the CloudXYZ company were
the user is authorized or else
permit is given to log in to the
system.
S4. Customer database Primary Asset The customer details and the
related data are all saved
here.
S5. Firewall Secondary asset The users filtering is provided
over here. The system is
access by only those users
that are authorized.
S6. Virtual servers Secondary Asset The virtual server is added just
after the actual servers on
which the extra load could be
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
handle.
S7. Cloud storage Primary Asset The CloudXYZ Company main
purpose is over the internet, it
could provide some storage.
The storage is provided to the
asset needed by the user.
S8. HR PC Primary Asset The PC of Human Resources
stored some other details of
the stuff and details of the
staff of CloudXYZ.
S9. Visitor PC Primary Asset This store the details that are
related to visitors.
S10. Admin PC Primary Asset The web server, mail server
and more details would be
stored on the admin PC.
S11. Staff PC Primary Asset The related data of the
technical work, the enterprise
development details and the
related information of the
staff
S12. Visitor phone Primary Asset There are details of the brand
and the visitors.
THREAT
The threat could be utilize by harasing the weakness, by intention or by fault, through which the
resource could be either find or defect or destroy. The work of any organization or asset could be fully
destroy through the organizational threat or it may happen that the enterprise could get collapse. The
evaluation of the treats could be either categories as high-level or medium-level or low-level. The
system has threat of low level that could basically cause problem in minimum amount. The system that
has threat of medium level could cause a little more defect but however both the type of threats could
be easily handled. However, the high-level threats cause destruction that are of very large amount for
which the organisation could be destroy.
The asset of the threats in the CloudXYZ organization:
Table 1: table of the assets of the threat
Asset name Threat Level SOURCE
S7. Cloud storage Primary Asset The CloudXYZ Company main
purpose is over the internet, it
could provide some storage.
The storage is provided to the
asset needed by the user.
S8. HR PC Primary Asset The PC of Human Resources
stored some other details of
the stuff and details of the
staff of CloudXYZ.
S9. Visitor PC Primary Asset This store the details that are
related to visitors.
S10. Admin PC Primary Asset The web server, mail server
and more details would be
stored on the admin PC.
S11. Staff PC Primary Asset The related data of the
technical work, the enterprise
development details and the
related information of the
staff
S12. Visitor phone Primary Asset There are details of the brand
and the visitors.
THREAT
The threat could be utilize by harasing the weakness, by intention or by fault, through which the
resource could be either find or defect or destroy. The work of any organization or asset could be fully
destroy through the organizational threat or it may happen that the enterprise could get collapse. The
evaluation of the treats could be either categories as high-level or medium-level or low-level. The
system has threat of low level that could basically cause problem in minimum amount. The system that
has threat of medium level could cause a little more defect but however both the type of threats could
be easily handled. However, the high-level threats cause destruction that are of very large amount for
which the organisation could be destroy.
The asset of the threats in the CloudXYZ organization:
Table 1: table of the assets of the threat
Asset name Threat Level SOURCE
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
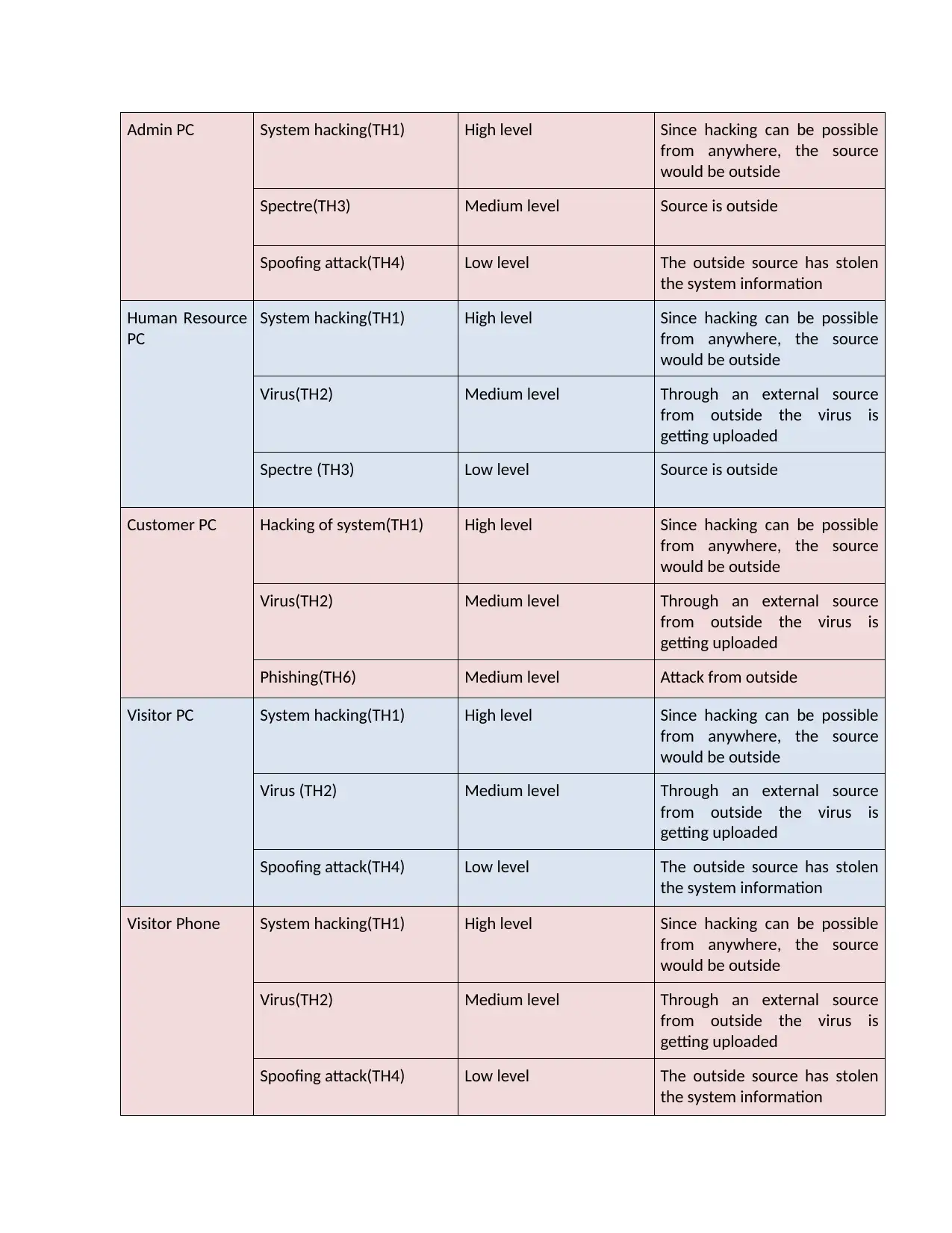
Admin PC System hacking(TH1) High level Since hacking can be possible
from anywhere, the source
would be outside
Spectre(TH3) Medium level Source is outside
Spoofing attack(TH4) Low level The outside source has stolen
the system information
Human Resource
PC
System hacking(TH1) High level Since hacking can be possible
from anywhere, the source
would be outside
Virus(TH2) Medium level Through an external source
from outside the virus is
getting uploaded
Spectre (TH3) Low level Source is outside
Customer PC Hacking of system(TH1) High level Since hacking can be possible
from anywhere, the source
would be outside
Virus(TH2) Medium level Through an external source
from outside the virus is
getting uploaded
Phishing(TH6) Medium level Attack from outside
Visitor PC System hacking(TH1) High level Since hacking can be possible
from anywhere, the source
would be outside
Virus (TH2) Medium level Through an external source
from outside the virus is
getting uploaded
Spoofing attack(TH4) Low level The outside source has stolen
the system information
Visitor Phone System hacking(TH1) High level Since hacking can be possible
from anywhere, the source
would be outside
Virus(TH2) Medium level Through an external source
from outside the virus is
getting uploaded
Spoofing attack(TH4) Low level The outside source has stolen
the system information
from anywhere, the source
would be outside
Spectre(TH3) Medium level Source is outside
Spoofing attack(TH4) Low level The outside source has stolen
the system information
Human Resource
PC
System hacking(TH1) High level Since hacking can be possible
from anywhere, the source
would be outside
Virus(TH2) Medium level Through an external source
from outside the virus is
getting uploaded
Spectre (TH3) Low level Source is outside
Customer PC Hacking of system(TH1) High level Since hacking can be possible
from anywhere, the source
would be outside
Virus(TH2) Medium level Through an external source
from outside the virus is
getting uploaded
Phishing(TH6) Medium level Attack from outside
Visitor PC System hacking(TH1) High level Since hacking can be possible
from anywhere, the source
would be outside
Virus (TH2) Medium level Through an external source
from outside the virus is
getting uploaded
Spoofing attack(TH4) Low level The outside source has stolen
the system information
Visitor Phone System hacking(TH1) High level Since hacking can be possible
from anywhere, the source
would be outside
Virus(TH2) Medium level Through an external source
from outside the virus is
getting uploaded
Spoofing attack(TH4) Low level The outside source has stolen
the system information
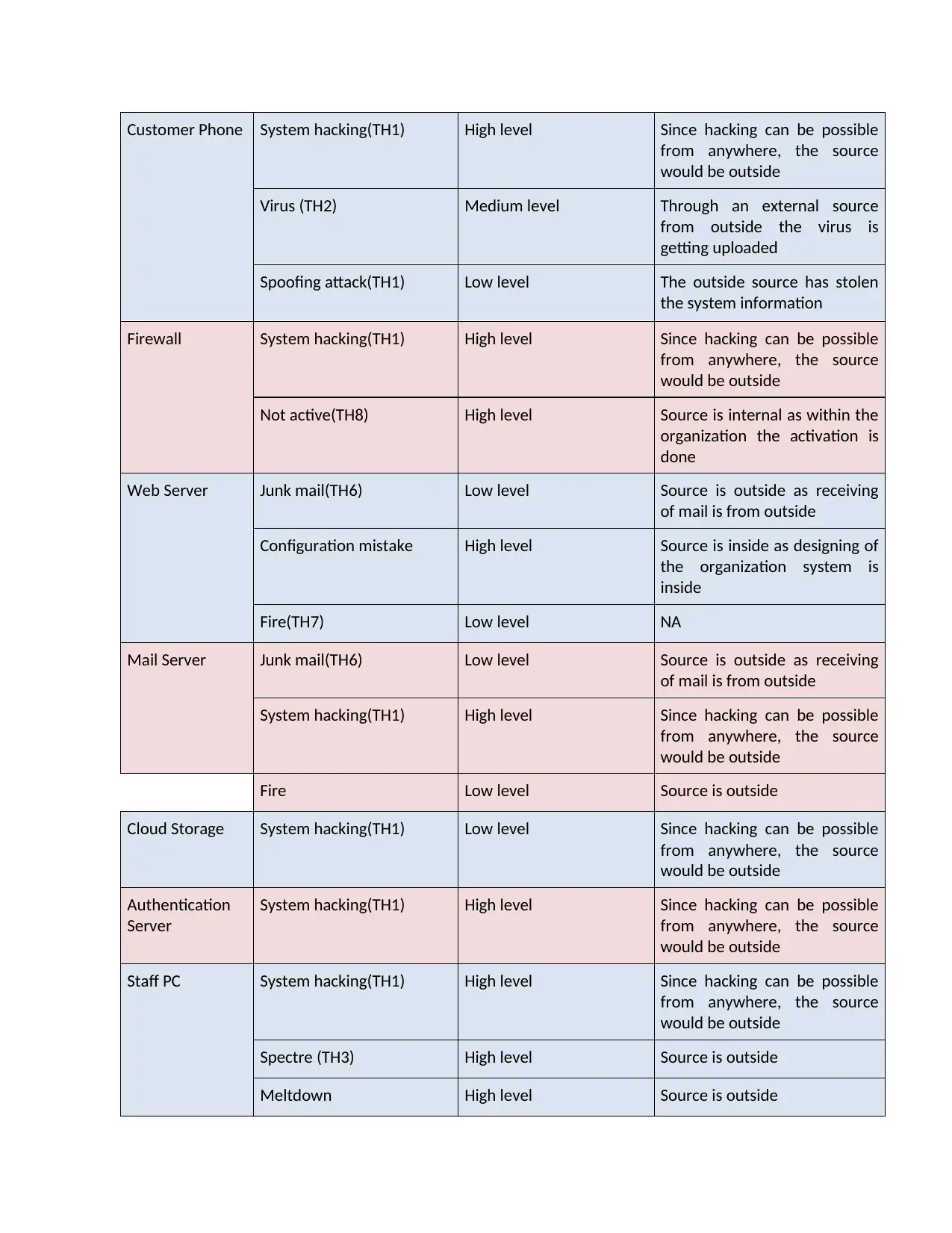
Customer Phone System hacking(TH1) High level Since hacking can be possible
from anywhere, the source
would be outside
Virus (TH2) Medium level Through an external source
from outside the virus is
getting uploaded
Spoofing attack(TH1) Low level The outside source has stolen
the system information
Firewall System hacking(TH1) High level Since hacking can be possible
from anywhere, the source
would be outside
Not active(TH8) High level Source is internal as within the
organization the activation is
done
Web Server Junk mail(TH6) Low level Source is outside as receiving
of mail is from outside
Configuration mistake High level Source is inside as designing of
the organization system is
inside
Fire(TH7) Low level NA
Mail Server Junk mail(TH6) Low level Source is outside as receiving
of mail is from outside
System hacking(TH1) High level Since hacking can be possible
from anywhere, the source
would be outside
Fire Low level Source is outside
Cloud Storage System hacking(TH1) Low level Since hacking can be possible
from anywhere, the source
would be outside
Authentication
Server
System hacking(TH1) High level Since hacking can be possible
from anywhere, the source
would be outside
Staff PC System hacking(TH1) High level Since hacking can be possible
from anywhere, the source
would be outside
Spectre (TH3) High level Source is outside
Meltdown High level Source is outside
from anywhere, the source
would be outside
Virus (TH2) Medium level Through an external source
from outside the virus is
getting uploaded
Spoofing attack(TH1) Low level The outside source has stolen
the system information
Firewall System hacking(TH1) High level Since hacking can be possible
from anywhere, the source
would be outside
Not active(TH8) High level Source is internal as within the
organization the activation is
done
Web Server Junk mail(TH6) Low level Source is outside as receiving
of mail is from outside
Configuration mistake High level Source is inside as designing of
the organization system is
inside
Fire(TH7) Low level NA
Mail Server Junk mail(TH6) Low level Source is outside as receiving
of mail is from outside
System hacking(TH1) High level Since hacking can be possible
from anywhere, the source
would be outside
Fire Low level Source is outside
Cloud Storage System hacking(TH1) Low level Since hacking can be possible
from anywhere, the source
would be outside
Authentication
Server
System hacking(TH1) High level Since hacking can be possible
from anywhere, the source
would be outside
Staff PC System hacking(TH1) High level Since hacking can be possible
from anywhere, the source
would be outside
Spectre (TH3) High level Source is outside
Meltdown High level Source is outside
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
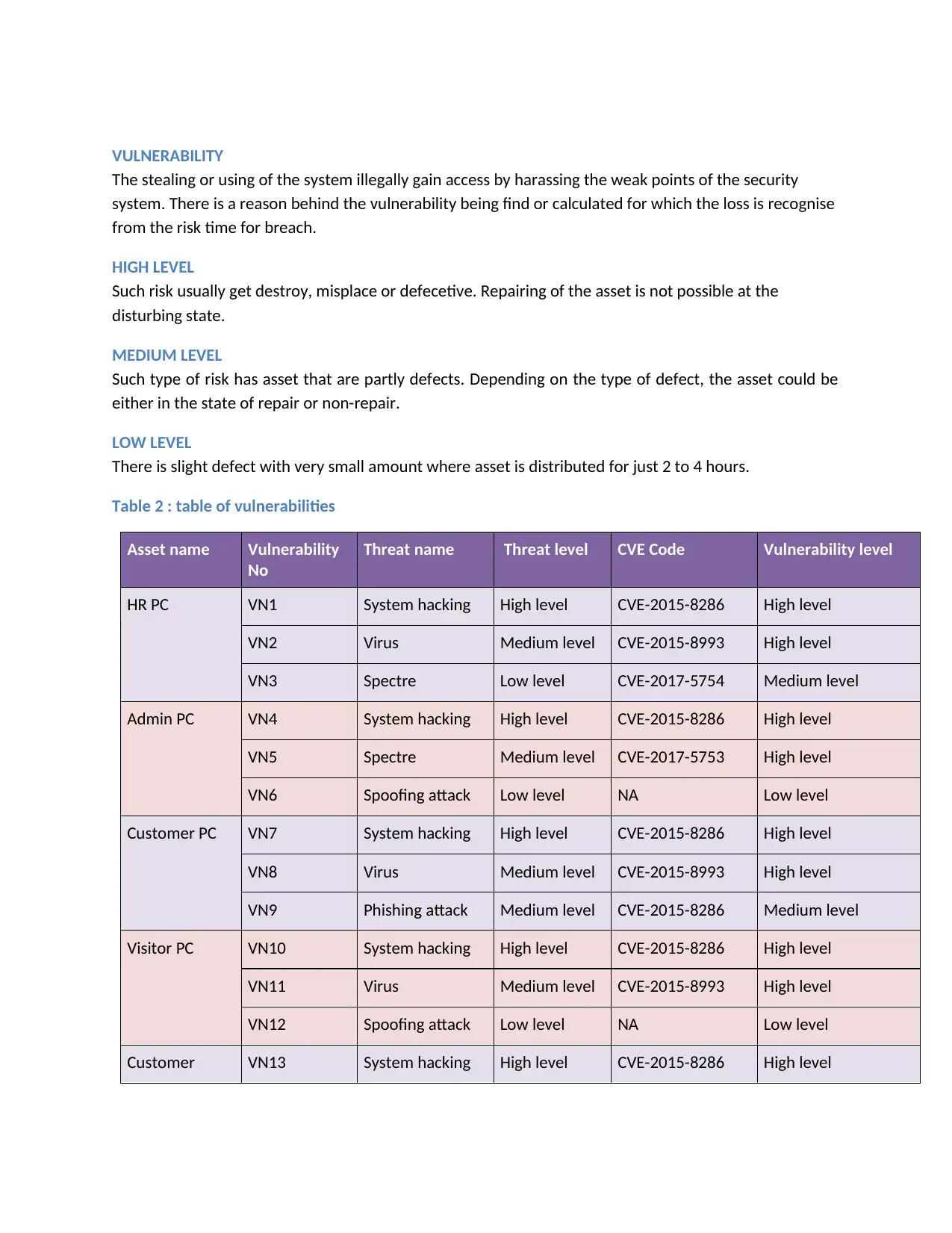
VULNERABILITY
The stealing or using of the system illegally gain access by harassing the weak points of the security
system. There is a reason behind the vulnerability being find or calculated for which the loss is recognise
from the risk time for breach.
HIGH LEVEL
Such risk usually get destroy, misplace or defecetive. Repairing of the asset is not possible at the
disturbing state.
MEDIUM LEVEL
Such type of risk has asset that are partly defects. Depending on the type of defect, the asset could be
either in the state of repair or non-repair.
LOW LEVEL
There is slight defect with very small amount where asset is distributed for just 2 to 4 hours.
Table 2 : table of vulnerabilities
Asset name Vulnerability
No
Threat name Threat level CVE Code Vulnerability level
HR PC VN1 System hacking High level CVE-2015-8286 High level
VN2 Virus Medium level CVE-2015-8993 High level
VN3 Spectre Low level CVE-2017-5754 Medium level
Admin PC VN4 System hacking High level CVE-2015-8286 High level
VN5 Spectre Medium level CVE-2017-5753 High level
VN6 Spoofing attack Low level NA Low level
Customer PC VN7 System hacking High level CVE-2015-8286 High level
VN8 Virus Medium level CVE-2015-8993 High level
VN9 Phishing attack Medium level CVE-2015-8286 Medium level
Visitor PC VN10 System hacking High level CVE-2015-8286 High level
VN11 Virus Medium level CVE-2015-8993 High level
VN12 Spoofing attack Low level NA Low level
Customer VN13 System hacking High level CVE-2015-8286 High level
The stealing or using of the system illegally gain access by harassing the weak points of the security
system. There is a reason behind the vulnerability being find or calculated for which the loss is recognise
from the risk time for breach.
HIGH LEVEL
Such risk usually get destroy, misplace or defecetive. Repairing of the asset is not possible at the
disturbing state.
MEDIUM LEVEL
Such type of risk has asset that are partly defects. Depending on the type of defect, the asset could be
either in the state of repair or non-repair.
LOW LEVEL
There is slight defect with very small amount where asset is distributed for just 2 to 4 hours.
Table 2 : table of vulnerabilities
Asset name Vulnerability
No
Threat name Threat level CVE Code Vulnerability level
HR PC VN1 System hacking High level CVE-2015-8286 High level
VN2 Virus Medium level CVE-2015-8993 High level
VN3 Spectre Low level CVE-2017-5754 Medium level
Admin PC VN4 System hacking High level CVE-2015-8286 High level
VN5 Spectre Medium level CVE-2017-5753 High level
VN6 Spoofing attack Low level NA Low level
Customer PC VN7 System hacking High level CVE-2015-8286 High level
VN8 Virus Medium level CVE-2015-8993 High level
VN9 Phishing attack Medium level CVE-2015-8286 Medium level
Visitor PC VN10 System hacking High level CVE-2015-8286 High level
VN11 Virus Medium level CVE-2015-8993 High level
VN12 Spoofing attack Low level NA Low level
Customer VN13 System hacking High level CVE-2015-8286 High level
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
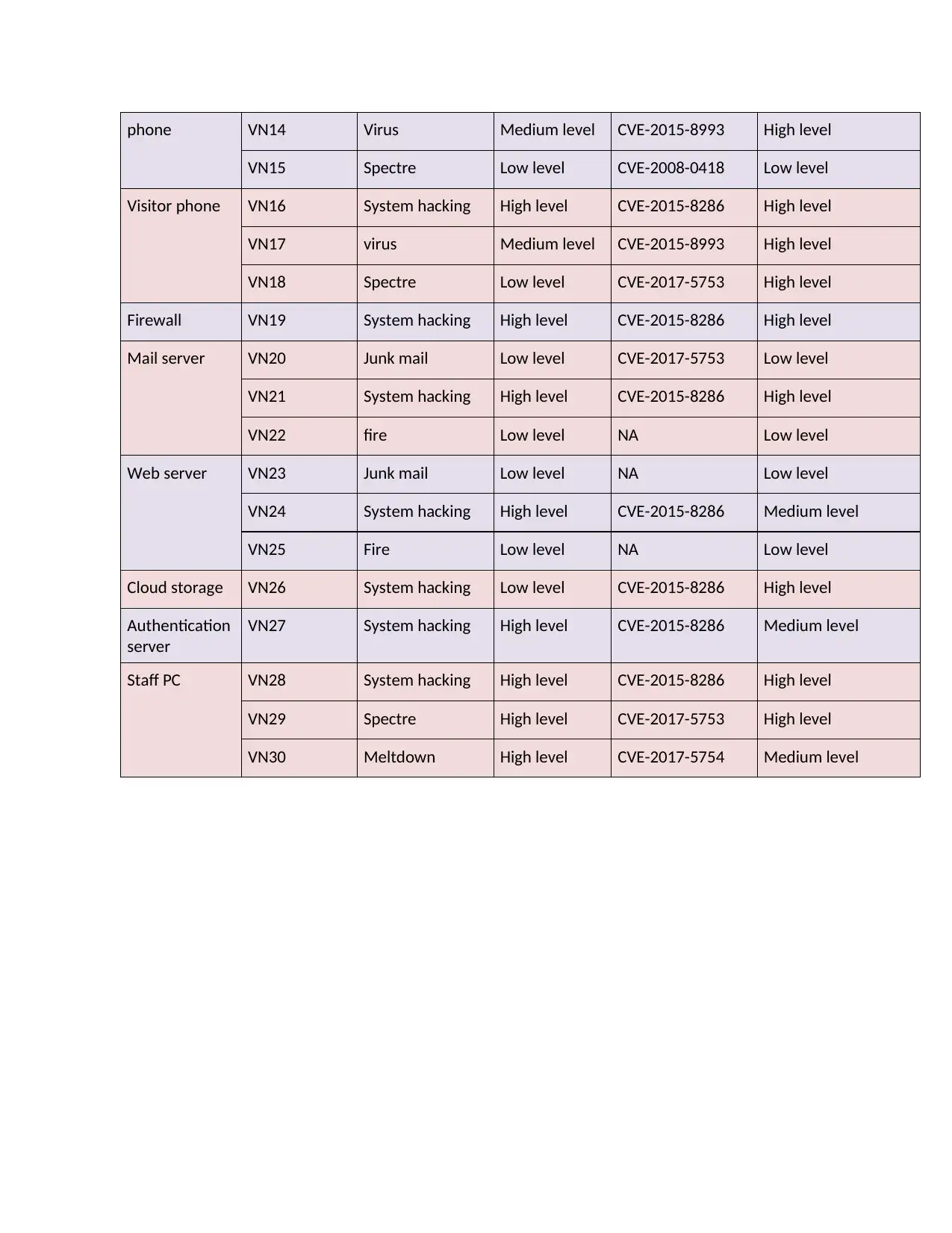
phone VN14 Virus Medium level CVE-2015-8993 High level
VN15 Spectre Low level CVE-2008-0418 Low level
Visitor phone VN16 System hacking High level CVE-2015-8286 High level
VN17 virus Medium level CVE-2015-8993 High level
VN18 Spectre Low level CVE-2017-5753 High level
Firewall VN19 System hacking High level CVE-2015-8286 High level
Mail server VN20 Junk mail Low level CVE-2017-5753 Low level
VN21 System hacking High level CVE-2015-8286 High level
VN22 fire Low level NA Low level
Web server VN23 Junk mail Low level NA Low level
VN24 System hacking High level CVE-2015-8286 Medium level
VN25 Fire Low level NA Low level
Cloud storage VN26 System hacking Low level CVE-2015-8286 High level
Authentication
server
VN27 System hacking High level CVE-2015-8286 Medium level
Staff PC VN28 System hacking High level CVE-2015-8286 High level
VN29 Spectre High level CVE-2017-5753 High level
VN30 Meltdown High level CVE-2017-5754 Medium level
VN15 Spectre Low level CVE-2008-0418 Low level
Visitor phone VN16 System hacking High level CVE-2015-8286 High level
VN17 virus Medium level CVE-2015-8993 High level
VN18 Spectre Low level CVE-2017-5753 High level
Firewall VN19 System hacking High level CVE-2015-8286 High level
Mail server VN20 Junk mail Low level CVE-2017-5753 Low level
VN21 System hacking High level CVE-2015-8286 High level
VN22 fire Low level NA Low level
Web server VN23 Junk mail Low level NA Low level
VN24 System hacking High level CVE-2015-8286 Medium level
VN25 Fire Low level NA Low level
Cloud storage VN26 System hacking Low level CVE-2015-8286 High level
Authentication
server
VN27 System hacking High level CVE-2015-8286 Medium level
Staff PC VN28 System hacking High level CVE-2015-8286 High level
VN29 Spectre High level CVE-2017-5753 High level
VN30 Meltdown High level CVE-2017-5754 Medium level
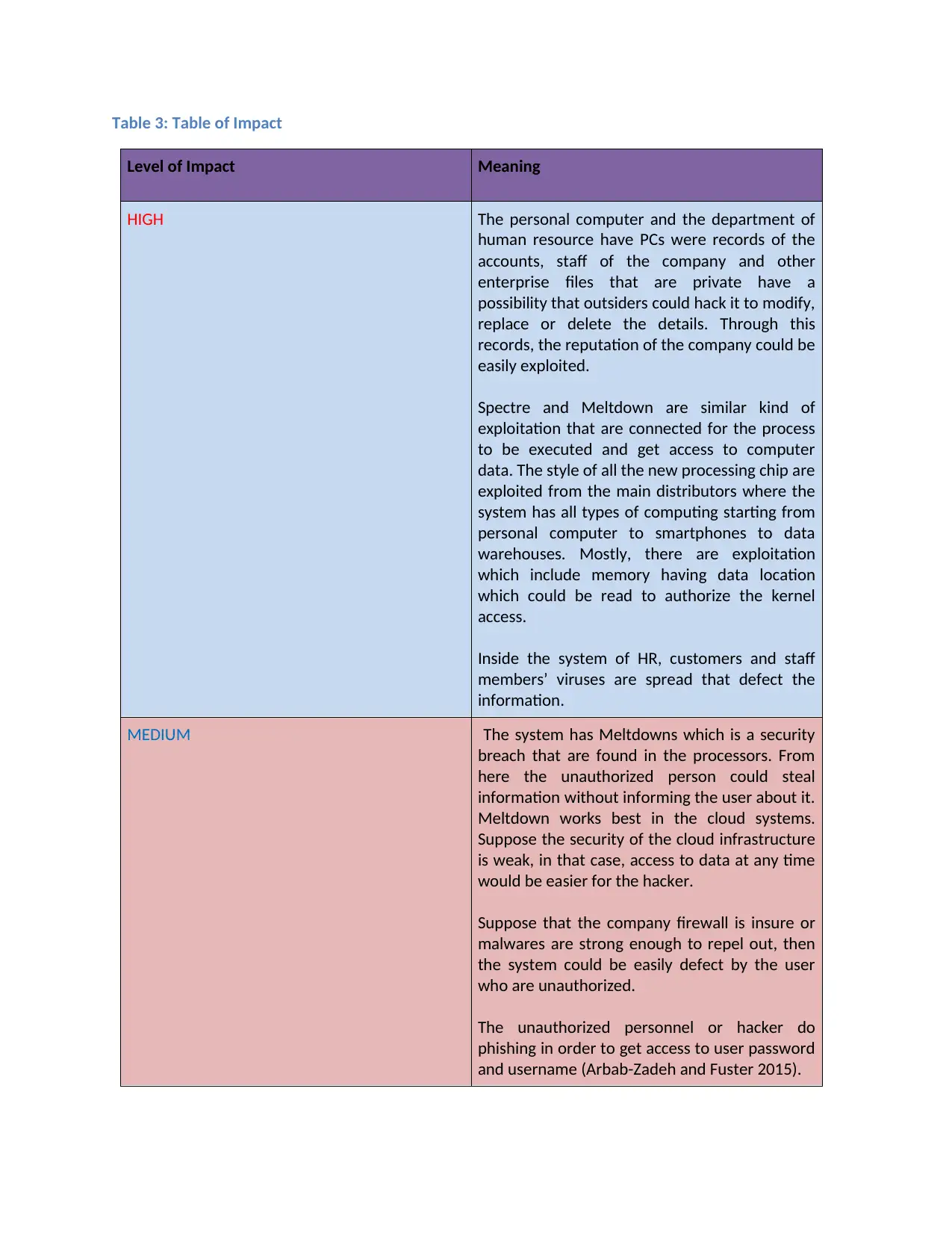
Table 3: Table of Impact
Level of Impact Meaning
HIGH The personal computer and the department of
human resource have PCs were records of the
accounts, staff of the company and other
enterprise files that are private have a
possibility that outsiders could hack it to modify,
replace or delete the details. Through this
records, the reputation of the company could be
easily exploited.
Spectre and Meltdown are similar kind of
exploitation that are connected for the process
to be executed and get access to computer
data. The style of all the new processing chip are
exploited from the main distributors where the
system has all types of computing starting from
personal computer to smartphones to data
warehouses. Mostly, there are exploitation
which include memory having data location
which could be read to authorize the kernel
access.
Inside the system of HR, customers and staff
members’ viruses are spread that defect the
information.
MEDIUM The system has Meltdowns which is a security
breach that are found in the processors. From
here the unauthorized person could steal
information without informing the user about it.
Meltdown works best in the cloud systems.
Suppose the security of the cloud infrastructure
is weak, in that case, access to data at any time
would be easier for the hacker.
Suppose that the company firewall is insure or
malwares are strong enough to repel out, then
the system could be easily defect by the user
who are unauthorized.
The unauthorized personnel or hacker do
phishing in order to get access to user password
and username (Arbab-Zadeh and Fuster 2015).
Level of Impact Meaning
HIGH The personal computer and the department of
human resource have PCs were records of the
accounts, staff of the company and other
enterprise files that are private have a
possibility that outsiders could hack it to modify,
replace or delete the details. Through this
records, the reputation of the company could be
easily exploited.
Spectre and Meltdown are similar kind of
exploitation that are connected for the process
to be executed and get access to computer
data. The style of all the new processing chip are
exploited from the main distributors where the
system has all types of computing starting from
personal computer to smartphones to data
warehouses. Mostly, there are exploitation
which include memory having data location
which could be read to authorize the kernel
access.
Inside the system of HR, customers and staff
members’ viruses are spread that defect the
information.
MEDIUM The system has Meltdowns which is a security
breach that are found in the processors. From
here the unauthorized person could steal
information without informing the user about it.
Meltdown works best in the cloud systems.
Suppose the security of the cloud infrastructure
is weak, in that case, access to data at any time
would be easier for the hacker.
Suppose that the company firewall is insure or
malwares are strong enough to repel out, then
the system could be easily defect by the user
who are unauthorized.
The unauthorized personnel or hacker do
phishing in order to get access to user password
and username (Arbab-Zadeh and Fuster 2015).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



