Computer Forensics Case Study: Analyzing Illegal Clown Content Access
VerifiedAdded on 2023/06/04
|95
|5630
|353
Case Study
AI Summary
This case study delves into a computer forensics investigation concerning the alleged access and storage of illegal clown-related digital content in Western Australia. The investigation begins with a witness report and the subsequent seizure of a computer. A junior investigator's initial logical acquisition and unfortunate wiping of the original hard drive led to challenges, which were overcome by utilizing a forensically sound approach for the logical acquisition. The suspect denies accessing the content and claims potential malware infection. The analysis employs digital forensics tools to examine various forensic image files, identifying deleted files, email addresses, and other relevant data to determine the validity of the allegations. The report details the steps taken to extract and analyze the case files, including the use of 7-Zip and Autopsy forensic software, providing a comprehensive overview of the forensic investigation process and findings.

Computer Forensics
Unit Number:
Unit Name:
Student Name:
Student Number:
Unit Number:
Unit Name:
Student Name:
Student Number:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1 Summary of the Project...................................................................................................2
2 Presentation of content relating to offence.....................................................................2
3 Identification.....................................................................................................................9
4 Intent................................................................................................................................47
5 Quantity of Files..............................................................................................................69
6 Installed Software...........................................................................................................89
7 Appendix – A...................................................................................................................90
8 Appendix - B....................................................................................................................91
References...............................................................................................................................93
1
1 Summary of the Project...................................................................................................2
2 Presentation of content relating to offence.....................................................................2
3 Identification.....................................................................................................................9
4 Intent................................................................................................................................47
5 Quantity of Files..............................................................................................................69
6 Installed Software...........................................................................................................89
7 Appendix – A...................................................................................................................90
8 Appendix - B....................................................................................................................91
References...............................................................................................................................93
1

1 Summary of the Project
Essential focal point of this project is investigate the advanced propelled crime scene
examination images by utilizing sensible tool. Essentially, space of Western Australia does
not offer access to electronic substance identified with comedians since it is illegal access,
assurance and stream the impelled substance identified with clowns. The comedians'
modernized substance are gotten to by malware. In this manner, this examination is essentials
to investigate the impelled substance identified with the clowns. By and large, the charge was
make the law endorsement where by an witness professes to get to the comedians related
information inside a work put. Regardless, some humourist's substance are gotten to without
the work put. Shockingly, junior impelled pro got the modernized wrongdoing scene
examination photograph of the PC that is comedians substance played out a genuine mooring.
Thusly, this circumstance the lesser advanced progressed legitimate sciences examiner wiped
the primary hard drive from the PC. Since, the anticipated securing is finished by forensically
solid way. Along these lines, the lesser specialist effortlessly picked the legal picture. The
suspect, Clark demies the getting to the humourist content furthermore Clark does not affirm
that the PC has a place with him. The Clark says, he doesn't generally take the PC home or jar
it. In this manner, senior investigator needs to audit the legal photograph of the lap which was
seized with right warrants. In like manner, moreover Clark express the PC was debased with
malware that accomplished distinctive potential substance showing up on the PC. This
examination is finished by utilizing the after death examination propelled wrongdoing scene
examination instrument. The examination will be done and talked about in detail.
2 Presentation of content relating to offence
Here, user needs to give the introduction of substance identifying with the offense. The
gave appropriate examination imparted that the charge was make the law essential where by
an witness announces to get to the clowns related information inside a work put. Shockingly,
junior pushed excellent got the modernized offense scene examination photo of the PC that is
clowns substance played out a genuine anchoring. Consequently, this situation the Junior
analyst wiped the rule hard drive from the PC. Since, the foreseen secures is done by
forensically strong way. In this manner, the junior investigator effectively picked the
criminological picture. Along these lines, senior examiner needs to explore the quantifiable
2
Essential focal point of this project is investigate the advanced propelled crime scene
examination images by utilizing sensible tool. Essentially, space of Western Australia does
not offer access to electronic substance identified with comedians since it is illegal access,
assurance and stream the impelled substance identified with clowns. The comedians'
modernized substance are gotten to by malware. In this manner, this examination is essentials
to investigate the impelled substance identified with the clowns. By and large, the charge was
make the law endorsement where by an witness professes to get to the comedians related
information inside a work put. Regardless, some humourist's substance are gotten to without
the work put. Shockingly, junior impelled pro got the modernized wrongdoing scene
examination photograph of the PC that is comedians substance played out a genuine mooring.
Thusly, this circumstance the lesser advanced progressed legitimate sciences examiner wiped
the primary hard drive from the PC. Since, the anticipated securing is finished by forensically
solid way. Along these lines, the lesser specialist effortlessly picked the legal picture. The
suspect, Clark demies the getting to the humourist content furthermore Clark does not affirm
that the PC has a place with him. The Clark says, he doesn't generally take the PC home or jar
it. In this manner, senior investigator needs to audit the legal photograph of the lap which was
seized with right warrants. In like manner, moreover Clark express the PC was debased with
malware that accomplished distinctive potential substance showing up on the PC. This
examination is finished by utilizing the after death examination propelled wrongdoing scene
examination instrument. The examination will be done and talked about in detail.
2 Presentation of content relating to offence
Here, user needs to give the introduction of substance identifying with the offense. The
gave appropriate examination imparted that the charge was make the law essential where by
an witness announces to get to the clowns related information inside a work put. Shockingly,
junior pushed excellent got the modernized offense scene examination photo of the PC that is
clowns substance played out a genuine anchoring. Consequently, this situation the Junior
analyst wiped the rule hard drive from the PC. Since, the foreseen secures is done by
forensically strong way. In this manner, the junior investigator effectively picked the
criminological picture. Along these lines, senior examiner needs to explore the quantifiable
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
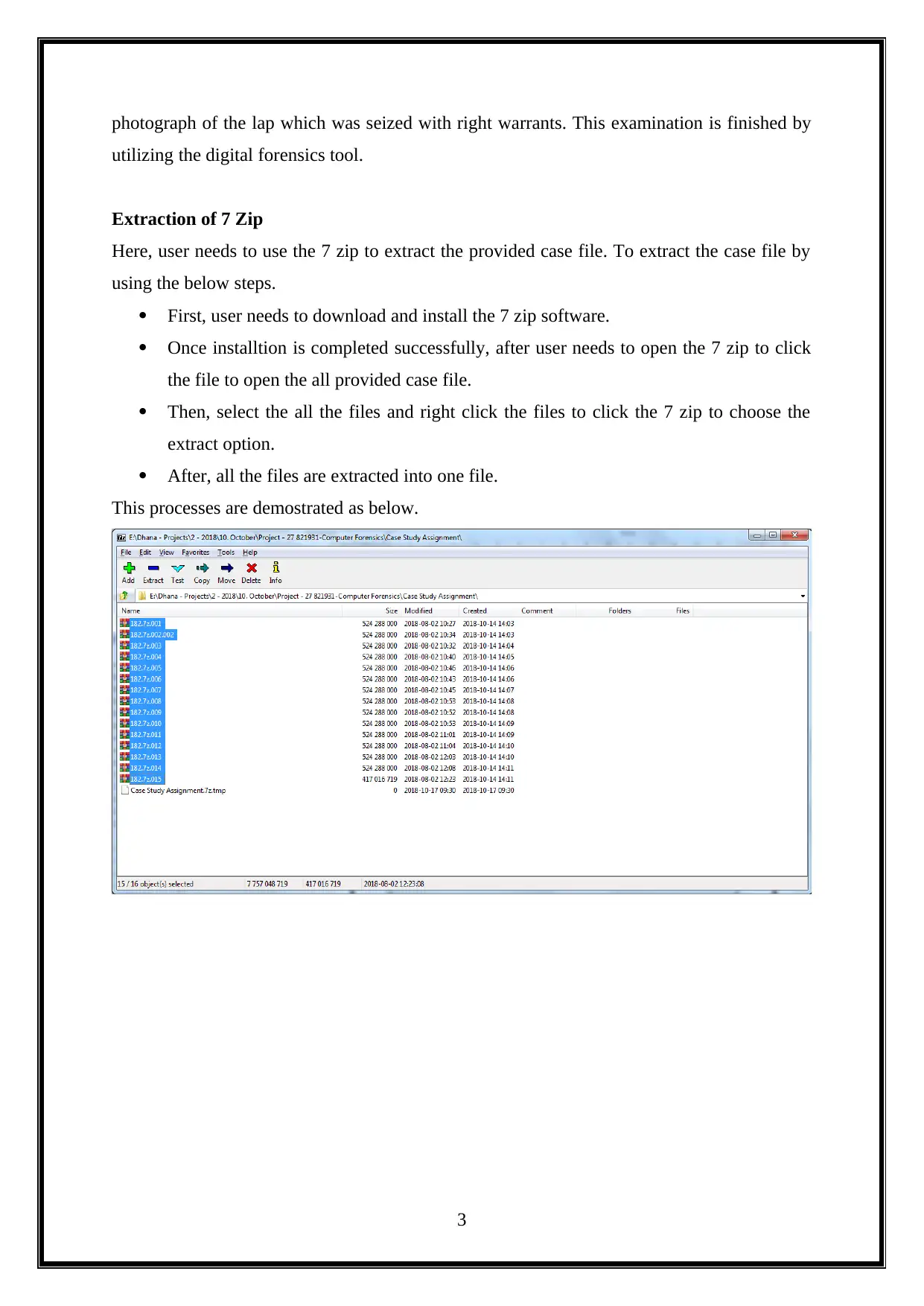
photograph of the lap which was seized with right warrants. This examination is finished by
utilizing the digital forensics tool.
Extraction of 7 Zip
Here, user needs to use the 7 zip to extract the provided case file. To extract the case file by
using the below steps.
First, user needs to download and install the 7 zip software.
Once installtion is completed successfully, after user needs to open the 7 zip to click
the file to open the all provided case file.
Then, select the all the files and right click the files to click the 7 zip to choose the
extract option.
After, all the files are extracted into one file.
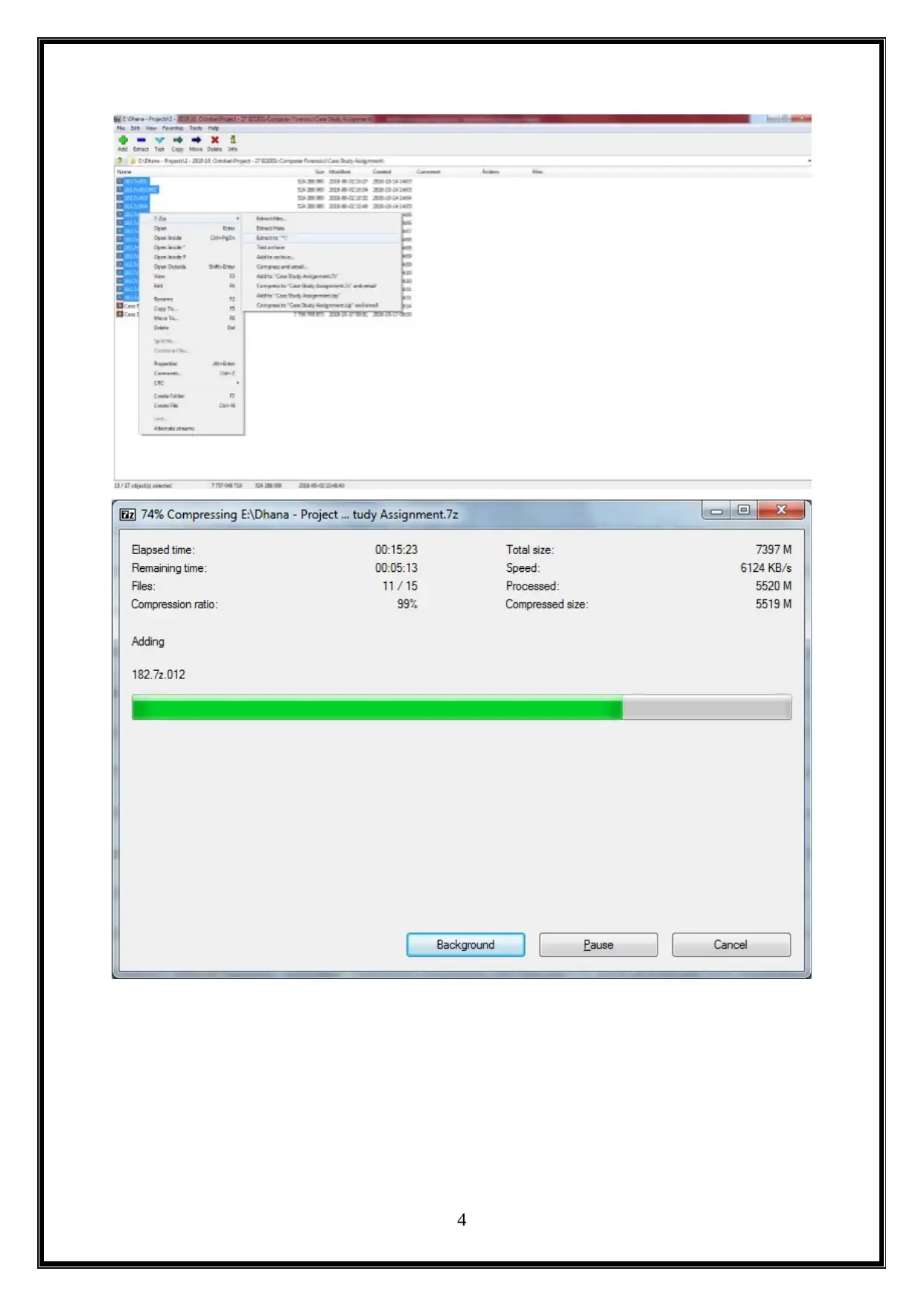
This processes are demostrated as below.
3
utilizing the digital forensics tool.
Extraction of 7 Zip
Here, user needs to use the 7 zip to extract the provided case file. To extract the case file by
using the below steps.
First, user needs to download and install the 7 zip software.
Once installtion is completed successfully, after user needs to open the 7 zip to click
the file to open the all provided case file.
Then, select the all the files and right click the files to click the 7 zip to choose the
extract option.
After, all the files are extracted into one file.
This processes are demostrated as below.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
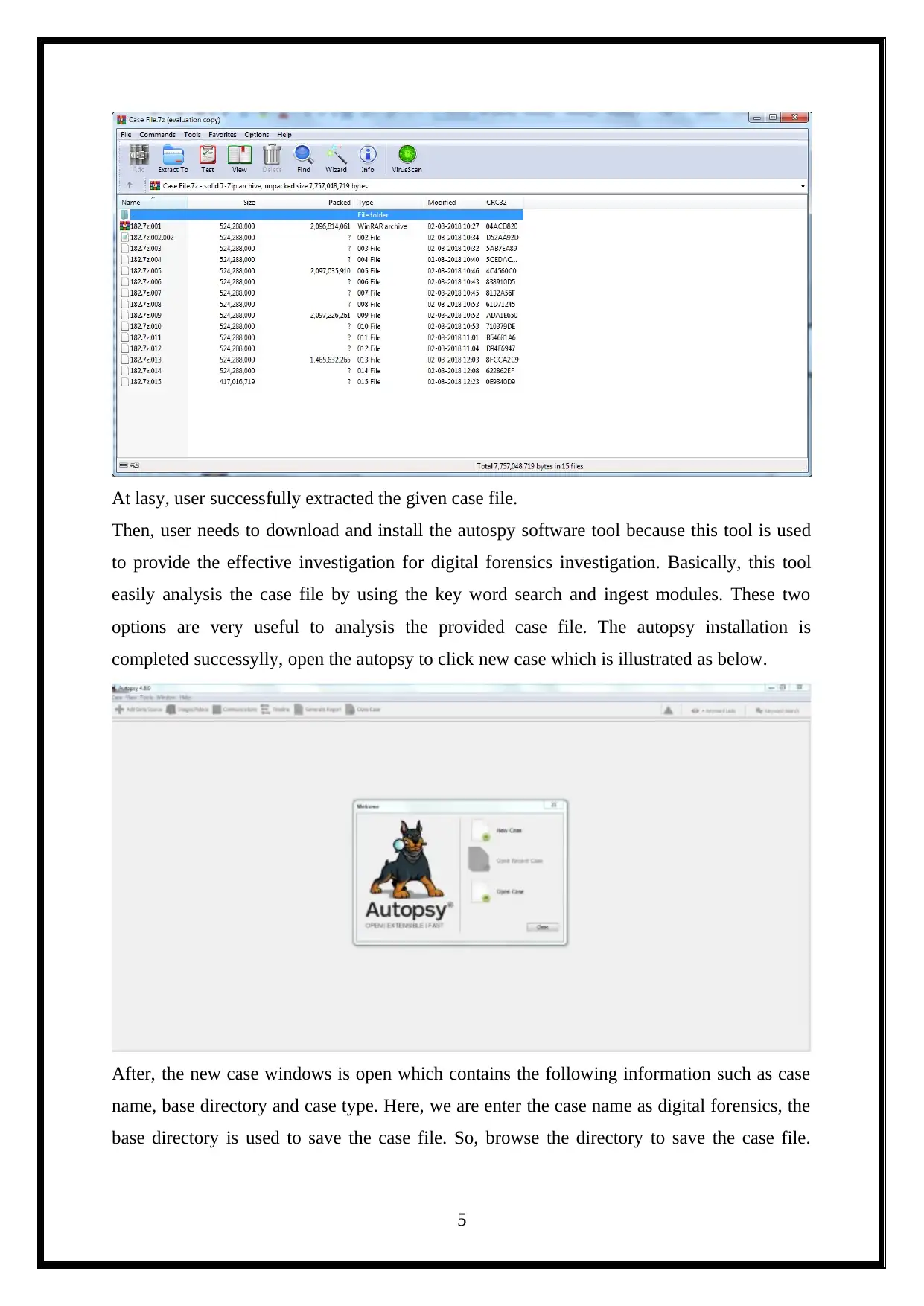
At lasy, user successfully extracted the given case file.
Then, user needs to download and install the autospy software tool because this tool is used
to provide the effective investigation for digital forensics investigation. Basically, this tool
easily analysis the case file by using the key word search and ingest modules. These two
options are very useful to analysis the provided case file. The autopsy installation is
completed successylly, open the autopsy to click new case which is illustrated as below.
After, the new case windows is open which contains the following information such as case
name, base directory and case type. Here, we are enter the case name as digital forensics, the
base directory is used to save the case file. So, browse the directory to save the case file.
5
Then, user needs to download and install the autospy software tool because this tool is used
to provide the effective investigation for digital forensics investigation. Basically, this tool
easily analysis the case file by using the key word search and ingest modules. These two
options are very useful to analysis the provided case file. The autopsy installation is
completed successylly, open the autopsy to click new case which is illustrated as below.
After, the new case windows is open which contains the following information such as case
name, base directory and case type. Here, we are enter the case name as digital forensics, the
base directory is used to save the case file. So, browse the directory to save the case file.
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
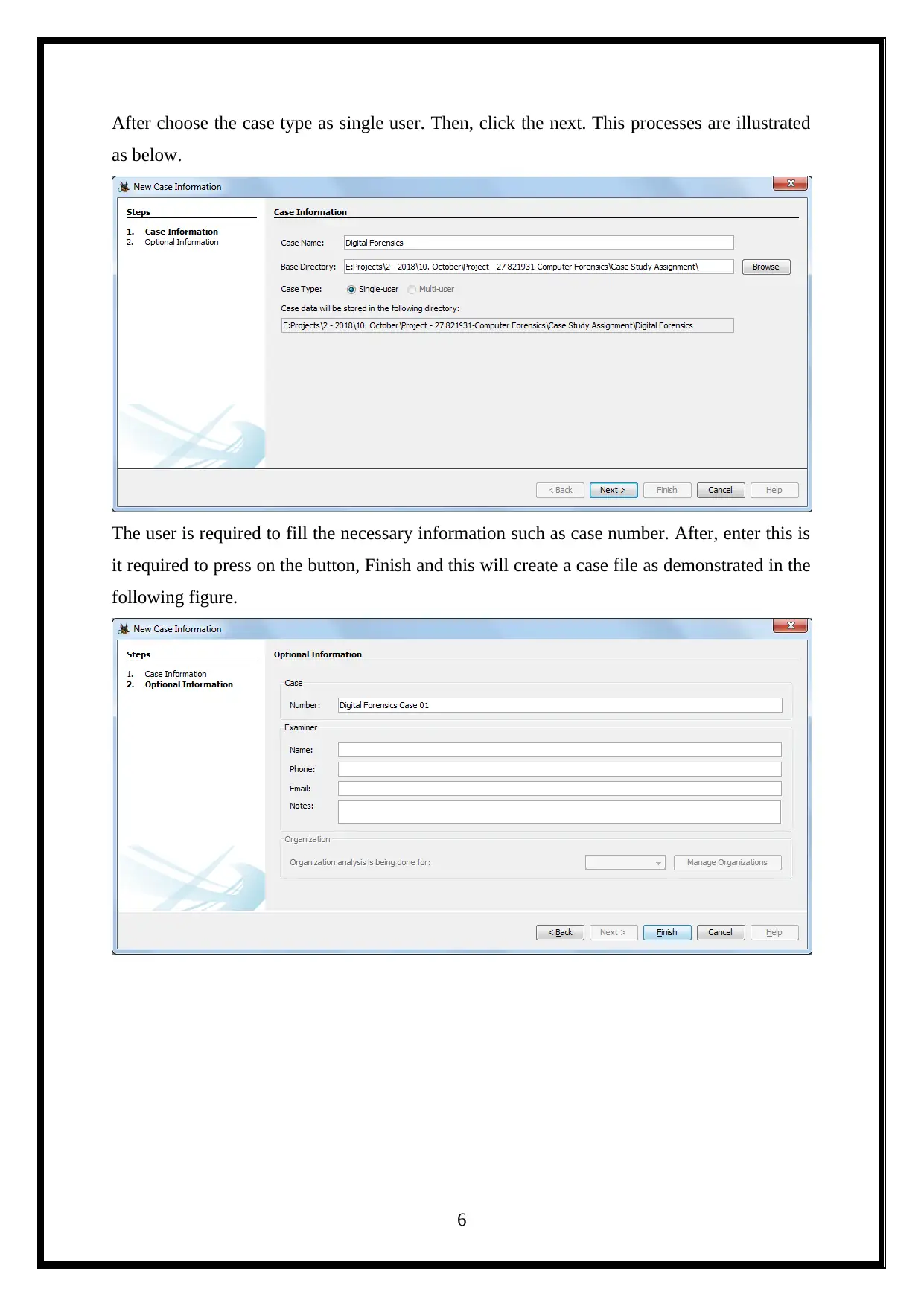
After choose the case type as single user. Then, click the next. This processes are illustrated
as below.
The user is required to fill the necessary information such as case number. After, enter this is
it required to press on the button, Finish and this will create a case file as demonstrated in the
following figure.
6
as below.
The user is required to fill the necessary information such as case number. After, enter this is
it required to press on the button, Finish and this will create a case file as demonstrated in the
following figure.
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
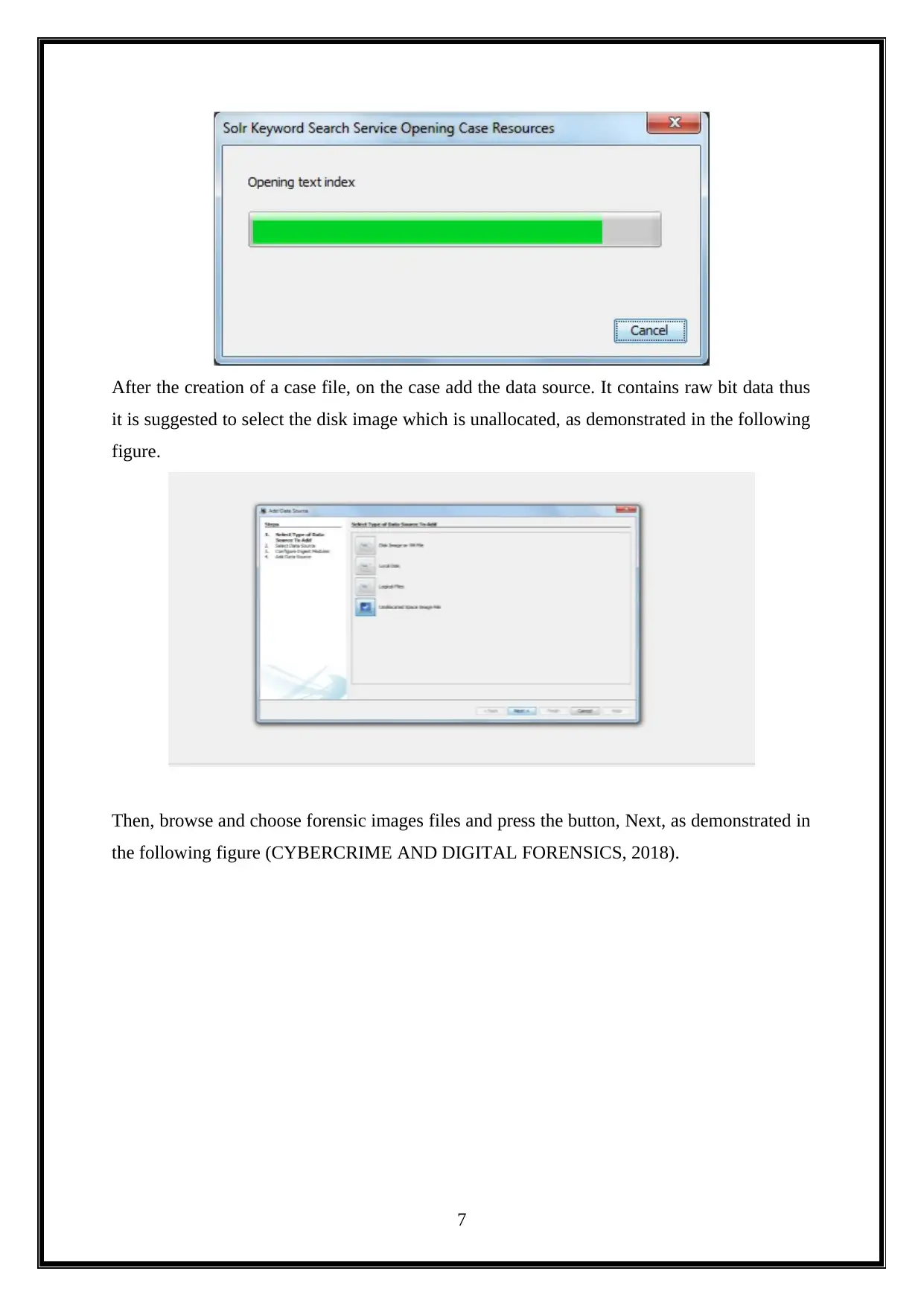
After the creation of a case file, on the case add the data source. It contains raw bit data thus
it is suggested to select the disk image which is unallocated, as demonstrated in the following
figure.
Then, browse and choose forensic images files and press the button, Next, as demonstrated in
the following figure (CYBERCRIME AND DIGITAL FORENSICS, 2018).
7
it is suggested to select the disk image which is unallocated, as demonstrated in the following
figure.
Then, browse and choose forensic images files and press the button, Next, as demonstrated in
the following figure (CYBERCRIME AND DIGITAL FORENSICS, 2018).
7
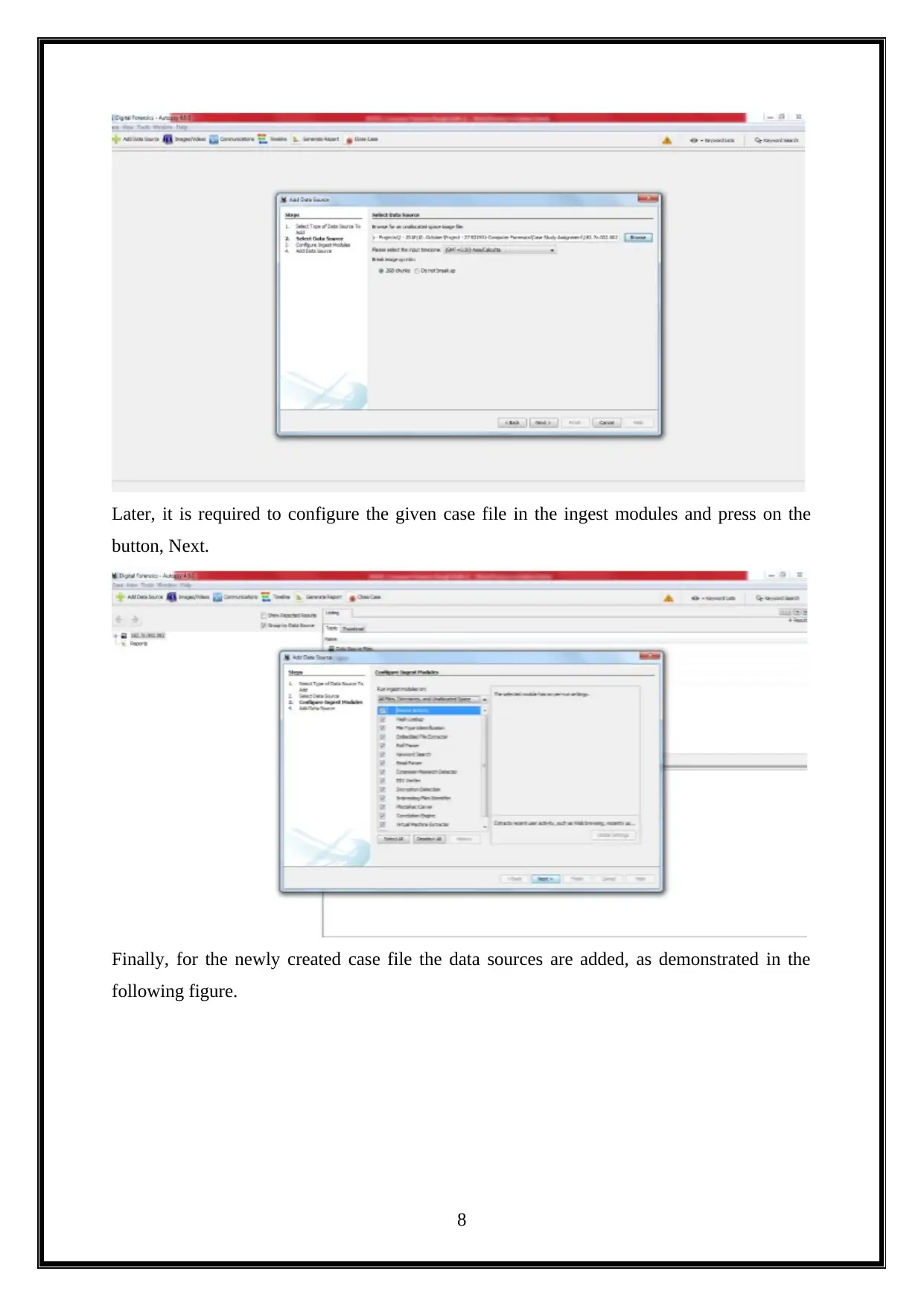
Later, it is required to configure the given case file in the ingest modules and press on the
button, Next.
Finally, for the newly created case file the data sources are added, as demonstrated in the
following figure.
8
button, Next.
Finally, for the newly created case file the data sources are added, as demonstrated in the
following figure.
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
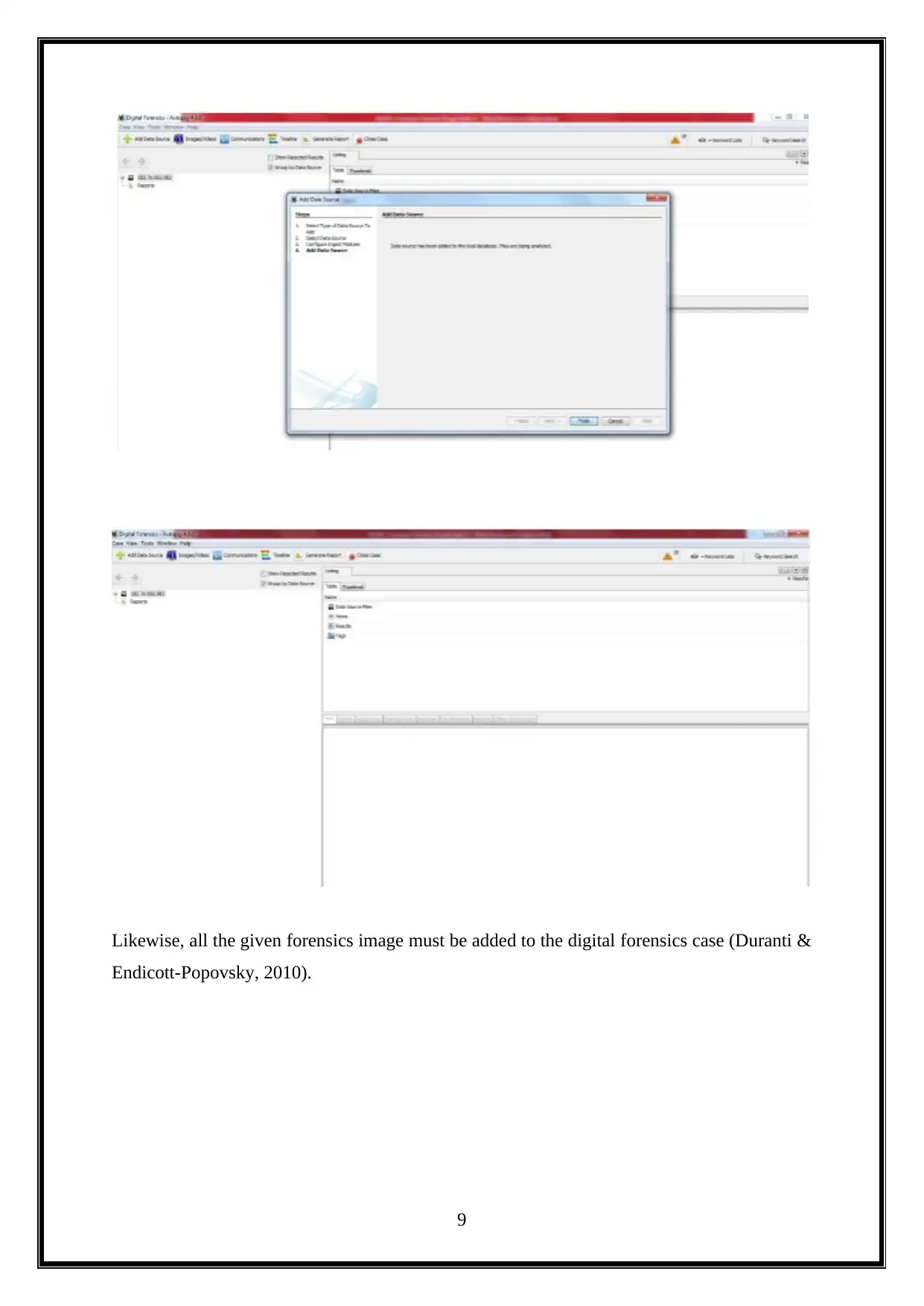
Likewise, all the given forensics image must be added to the digital forensics case (Duranti &
Endicott-Popovsky, 2010).
9
Endicott-Popovsky, 2010).
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

After all the data sources are included in the created case, the user must identify the evidence
which is related to the investigation of digital forensic.
3 Identification
In this section, the forensics image file information will be identified, for proceeding
the analysis of digital forensics.
182.7z.002 Case File Identification
Choose appropriate data file for identifying the information of the case file, as
demonstrated in the following figure (Flory, 2016).
10
which is related to the investigation of digital forensic.
3 Identification
In this section, the forensics image file information will be identified, for proceeding
the analysis of digital forensics.
182.7z.002 Case File Identification
Choose appropriate data file for identifying the information of the case file, as
demonstrated in the following figure (Flory, 2016).
10
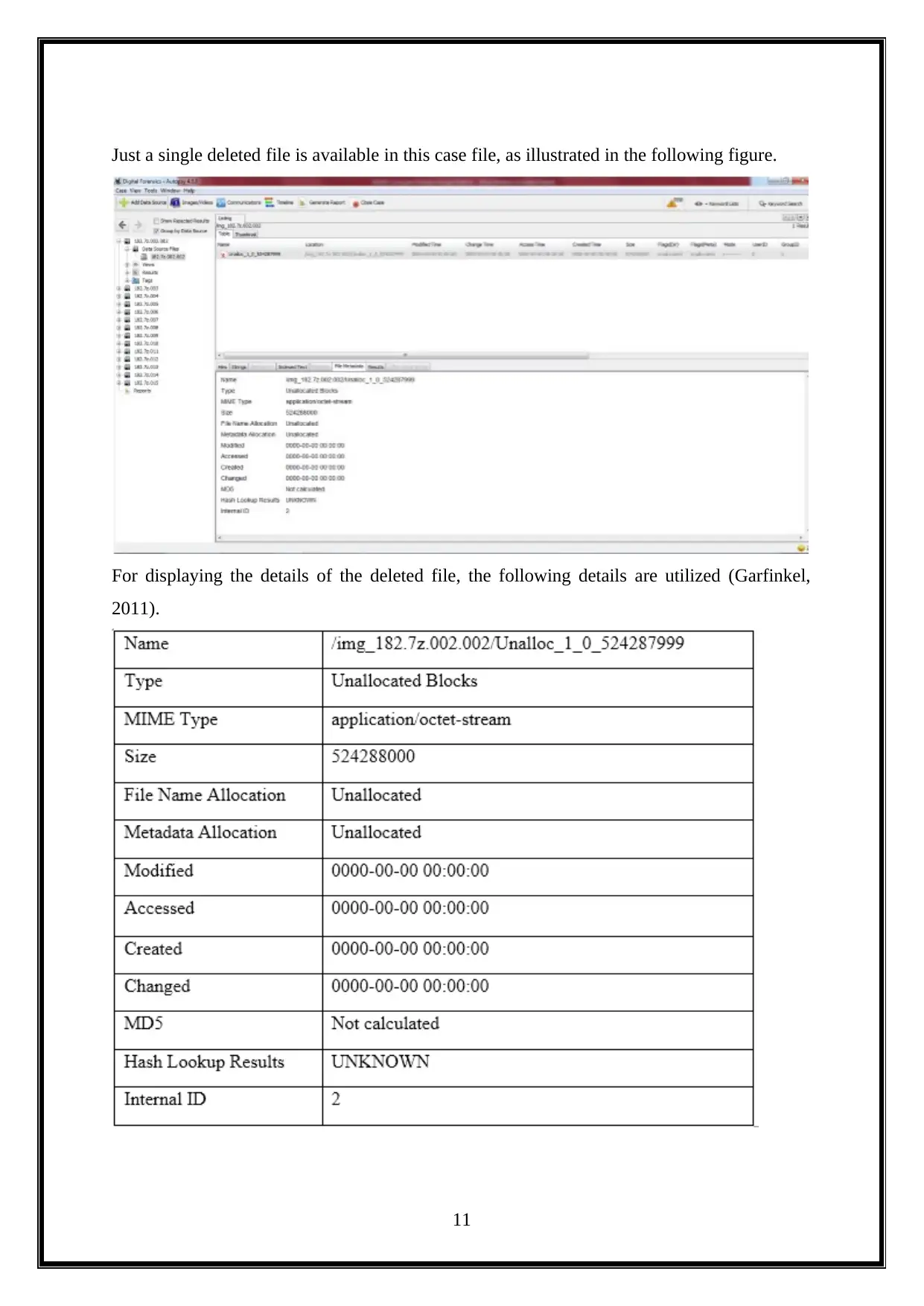
Just a single deleted file is available in this case file, as illustrated in the following figure.
For displaying the details of the deleted file, the following details are utilized (Garfinkel,
2011).
11
For displaying the details of the deleted file, the following details are utilized (Garfinkel,
2011).
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 95
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




