CMIT 350: WAN and SOHO Skills Implementation: Router and Switch Setup
VerifiedAdded on 2019/10/16
|6
|1107
|171
Practical Assignment
AI Summary
This assignment solution for CMIT 350, focusing on WAN and SOHO skills implementation, details network configurations across Sacramento and Los Angeles sites. The Sacramento site configuration includes VLAN setup using switchport mode access and port security, along with the implementation of a Router on a Stick (ROS) setup for multiple VLANs, and DHCP server configuration for dynamic IP address assignment. The Los Angeles site management section covers remote IOS storage and management of switches, including ACL implementation and Network Time Protocol (NTP) configuration. Finally, the assignment addresses the xACME WAN implementation using leased lines, including the configuration of Point-to-Point Protocol (PPP) with PAP and CHAP authentication on Cisco routers. The solution provides detailed configuration steps and relevant bibliography for reference.

CMIT 350 WAN and SOHO Skills
Implementation
Course: CMIT 350 Interconnecting Cisco Devices (Part 3)
Professor: Rodolfo Solis
Created by: Chris Reagan
Date: 7/1/2016
Summary:
I. Sacramento Site VLAN, ROS, DHCP Implementation, Los Angeles Site Management,
xACME WAN – WAN Implementation and Secure Communications
II. Bibliography
Sacramento
VLANs: We need to use switchport mode “access” for setting port security.
The steps for implementing port security to allow maximum two MAC addresses and shutdowns
for violations are:
a) interface ga0/1
b) switchport mode access
c) switchport port-security
d) switchport port-security maximum 2
e) switchport port-security violation shutdown
f) show port-security address will display the ports with matching switchport modes
security settings .
ROS: The configuration will be simplified as
a) faculty VLAN: 10.50.0.0 /28
b) The administrative: 10.50.0.64 /28
c) instructional - 10.50.0.122 /28
d) server : 10.50.0.193 /28
Which is as follows;
SacramentoRouter (config)#int fastEthernet 0/0.1
SacramentoRouter(config-subif)#encapsulation isl 1
Implementation
Course: CMIT 350 Interconnecting Cisco Devices (Part 3)
Professor: Rodolfo Solis
Created by: Chris Reagan
Date: 7/1/2016
Summary:
I. Sacramento Site VLAN, ROS, DHCP Implementation, Los Angeles Site Management,
xACME WAN – WAN Implementation and Secure Communications
II. Bibliography
Sacramento
VLANs: We need to use switchport mode “access” for setting port security.
The steps for implementing port security to allow maximum two MAC addresses and shutdowns
for violations are:
a) interface ga0/1
b) switchport mode access
c) switchport port-security
d) switchport port-security maximum 2
e) switchport port-security violation shutdown
f) show port-security address will display the ports with matching switchport modes
security settings .
ROS: The configuration will be simplified as
a) faculty VLAN: 10.50.0.0 /28
b) The administrative: 10.50.0.64 /28
c) instructional - 10.50.0.122 /28
d) server : 10.50.0.193 /28
Which is as follows;
SacramentoRouter (config)#int fastEthernet 0/0.1
SacramentoRouter(config-subif)#encapsulation isl 1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
SacramentoRouter(config-subif)#encapsulation dot1Q 1
SacramentoRouter(config-subif)#encapsulation dot1Q 1 native
SacramentoRouter(config-subif)#ip address 10.50.0.0 255.255.255.192
SacramentoRouter(config-subif)#exit
SacramentoRouter(config)#int fastEthernet 0/0.2
SacramentoRouter(config-subif)#encapsulation isl 2
SacramentoRouter(config-subif)#encapsulation dot1Q 2
SacramentoRouter(config-subif)#ip address 10.50.0.64 255.255.255.192
SacramentoRouter(config-subif)#exit
SacramentoRouter(config)#int fastEthernet 0/0.2
SacramentoRouter(config-subif)#encapsulation isl 2
SacramentoRouter(config-subif)#encapsulation dot1Q 2
SacramentoRouter(config-subif)#ip address 10.50.0.128 255.255.255.192
SacramentoRouter(config-subif)#exit
SacramentoRouter(config)#int fastEthernet 0/0.2
SacramentoRouter(config-subif)#encapsulation isl 2
SacramentoRouter(config-subif)#encapsulation dot1Q 2
SacramentoRouter(config-subif)#ip address 10.50.0.192 255.255.255.192
SacramentoRouter(config-subif)#exit
DHCP - is used to dynamically assign ip address to the hosts on the VLAN.
Router(config)# ip name-server 10.50.0.1
Router(config)# ip dhcp excluded-address 10.50.0.54/26 – 10.50.0.63/26
Router(config)# ip dhcp pool dpool1
Router(config-dhcp)#
Router(config-dhcp)#network 10.50.0.0 255.255.255.192
Router(config-dhcp)#default-router 10.50.0.1
Router(config-dhcp)# dns-server 10.50.0.1
Los Angeles Site Management
Faculty VLAN = 21 devices
SacramentoRouter(config-subif)#encapsulation dot1Q 1 native
SacramentoRouter(config-subif)#ip address 10.50.0.0 255.255.255.192
SacramentoRouter(config-subif)#exit
SacramentoRouter(config)#int fastEthernet 0/0.2
SacramentoRouter(config-subif)#encapsulation isl 2
SacramentoRouter(config-subif)#encapsulation dot1Q 2
SacramentoRouter(config-subif)#ip address 10.50.0.64 255.255.255.192
SacramentoRouter(config-subif)#exit
SacramentoRouter(config)#int fastEthernet 0/0.2
SacramentoRouter(config-subif)#encapsulation isl 2
SacramentoRouter(config-subif)#encapsulation dot1Q 2
SacramentoRouter(config-subif)#ip address 10.50.0.128 255.255.255.192
SacramentoRouter(config-subif)#exit
SacramentoRouter(config)#int fastEthernet 0/0.2
SacramentoRouter(config-subif)#encapsulation isl 2
SacramentoRouter(config-subif)#encapsulation dot1Q 2
SacramentoRouter(config-subif)#ip address 10.50.0.192 255.255.255.192
SacramentoRouter(config-subif)#exit
DHCP - is used to dynamically assign ip address to the hosts on the VLAN.
Router(config)# ip name-server 10.50.0.1
Router(config)# ip dhcp excluded-address 10.50.0.54/26 – 10.50.0.63/26
Router(config)# ip dhcp pool dpool1
Router(config-dhcp)#
Router(config-dhcp)#network 10.50.0.0 255.255.255.192
Router(config-dhcp)#default-router 10.50.0.1
Router(config-dhcp)# dns-server 10.50.0.1
Los Angeles Site Management
Faculty VLAN = 21 devices

Administrative VLAN = 44 devices
Instructional VLAN = 120 devices
Server VLAN = 21 devices
Remote IOS Storage: Console> (enable) copy config tftp
IP address or name of remote host []? 10.40.6.10/23
Name of file to copy to []? Cat6500_config.cfg
Upload configuration to tftp:cat6500_config.cfg, (y/n) [n]? y
/
Configuration has been copied successfully.
Console> (enable)
Remote Management of Switches Solutions:
LosAngelesSw1(config)# catalyst6500-system remote-mgmt primary ip 10.40.6.10/23 username
admin password *************
LosAngelesSw1(config)# show running-config
ACL Implementation:
LosAngelesSw3(config)# access-list 1 permit VLAN 1
LosAngelesSw3 (config)# access-list 2 deny VLAN 2
LosAngelesSw3 (config)# access-list 3 deny VLAN 3
LosAngelesSw3 (config)# access-list 4 deny VLAN 4
Network Time Protocol:
LosAngelesRouter(config)# ip nameserver 10.40.6.10/23
LosAngelesRouter (config)# ntp server 1.gr.pool.ntp.org
LosAngelesRouter # show ntp associations
LosAngelesRouter # show ntp status
LosAngelesRouter# ntp logging
SacramentoRouter(config)# ip nameserver 10.40.6.10/23
SacramentoRouter (config)# ntp server 1.gr.pool.ntp.org
SacramentoRouter # show ntp associations
SacramentoRouter # show ntp status
SacramentoRouter # ntp logging
Instructional VLAN = 120 devices
Server VLAN = 21 devices
Remote IOS Storage: Console> (enable) copy config tftp
IP address or name of remote host []? 10.40.6.10/23
Name of file to copy to []? Cat6500_config.cfg
Upload configuration to tftp:cat6500_config.cfg, (y/n) [n]? y
/
Configuration has been copied successfully.
Console> (enable)
Remote Management of Switches Solutions:
LosAngelesSw1(config)# catalyst6500-system remote-mgmt primary ip 10.40.6.10/23 username
admin password *************
LosAngelesSw1(config)# show running-config
ACL Implementation:
LosAngelesSw3(config)# access-list 1 permit VLAN 1
LosAngelesSw3 (config)# access-list 2 deny VLAN 2
LosAngelesSw3 (config)# access-list 3 deny VLAN 3
LosAngelesSw3 (config)# access-list 4 deny VLAN 4
Network Time Protocol:
LosAngelesRouter(config)# ip nameserver 10.40.6.10/23
LosAngelesRouter (config)# ntp server 1.gr.pool.ntp.org
LosAngelesRouter # show ntp associations
LosAngelesRouter # show ntp status
LosAngelesRouter# ntp logging
SacramentoRouter(config)# ip nameserver 10.40.6.10/23
SacramentoRouter (config)# ntp server 1.gr.pool.ntp.org
SacramentoRouter # show ntp associations
SacramentoRouter # show ntp status
SacramentoRouter # ntp logging
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

BostonRouter(config)# ip nameserver 10.40.6.10/23
BostonRouter (config)# ntp server 1.gr.pool.ntp.org
BostonRouter # show ntp associations
BostonRouter # show ntp status
BostonRouter # ntp logging
WorchesterRouter(config)# ip nameserver 10.40.6.10/23
WorchesterRouter (config)# ntp server 1.gr.pool.ntp.org
WorchesterRouter # show ntp associations
WorchesterRouter # show ntp status
WorchesterRouter # ntp logging
SpringfieldRouter(config)# ip nameserver 10.40.6.10/23
SpringfieldRouter (config)# ntp server 1.gr.pool.ntp.org
SpringfieldRouter # show ntp associations
SpringfieldRouter # show ntp status
SpringfieldRouter # ntp logging
xACME
Leased Line is a dedicated point-to-point connection where a permanent communication path
exists between the two sites’ Customer Premise Equipment (CPE) through a Data
Communicating Equipment (DCE). The protocols used are most often HDLC (High-Level
Data Link Control) and PPP (Point-to-Point Protocol).
Point-to-Point Protocol (PPP) is used on serial connections between dissimilar routers, for
example a Cisco router and a non-Cisco router. PPP is designed to allow the simultaneous
use of multiple network layer protocols and also supports two types of hostname
authentications CHAP Challenge Handshake Authentication Protocol and PAP password
Authentication Protocol. Network Control Protocol (NCP) provides the means for
encapsulating multiple network layer protocols across the PPP data link.
Sacramento Router
SacramentoRouter#config t
SacramentoRouter (config)#username RO password orbit
BostonRouter (config)# ntp server 1.gr.pool.ntp.org
BostonRouter # show ntp associations
BostonRouter # show ntp status
BostonRouter # ntp logging
WorchesterRouter(config)# ip nameserver 10.40.6.10/23
WorchesterRouter (config)# ntp server 1.gr.pool.ntp.org
WorchesterRouter # show ntp associations
WorchesterRouter # show ntp status
WorchesterRouter # ntp logging
SpringfieldRouter(config)# ip nameserver 10.40.6.10/23
SpringfieldRouter (config)# ntp server 1.gr.pool.ntp.org
SpringfieldRouter # show ntp associations
SpringfieldRouter # show ntp status
SpringfieldRouter # ntp logging
xACME
Leased Line is a dedicated point-to-point connection where a permanent communication path
exists between the two sites’ Customer Premise Equipment (CPE) through a Data
Communicating Equipment (DCE). The protocols used are most often HDLC (High-Level
Data Link Control) and PPP (Point-to-Point Protocol).
Point-to-Point Protocol (PPP) is used on serial connections between dissimilar routers, for
example a Cisco router and a non-Cisco router. PPP is designed to allow the simultaneous
use of multiple network layer protocols and also supports two types of hostname
authentications CHAP Challenge Handshake Authentication Protocol and PAP password
Authentication Protocol. Network Control Protocol (NCP) provides the means for
encapsulating multiple network layer protocols across the PPP data link.
Sacramento Router
SacramentoRouter#config t
SacramentoRouter (config)#username RO password orbit
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
SacramentoRouter (config)#interface se0/0/0
SacramentoRouter (config-if)#encapsulation ppp
SacramentoRouter (config-if)#ppp authentication PAP
SacramentoRouter (config-if)#ppp pap sent-username HQ password orbit
SacramentoRouter (config-if)#end
Los Angeles router
LosAngelesRouter#Config t
LosAngelesRouter (config)#username HQ password orbit
LosAngelesRouter (config)#interface se0/0/0
LosAngelesRouter (config-if)#encapsulation ppp
LosAngelesRouter (config-if)#ppp authentication PAP
LosAngelesRouter (config-if)#ppp pap sent-username RO password orbit
LosAngelesRouter (config-if)#end
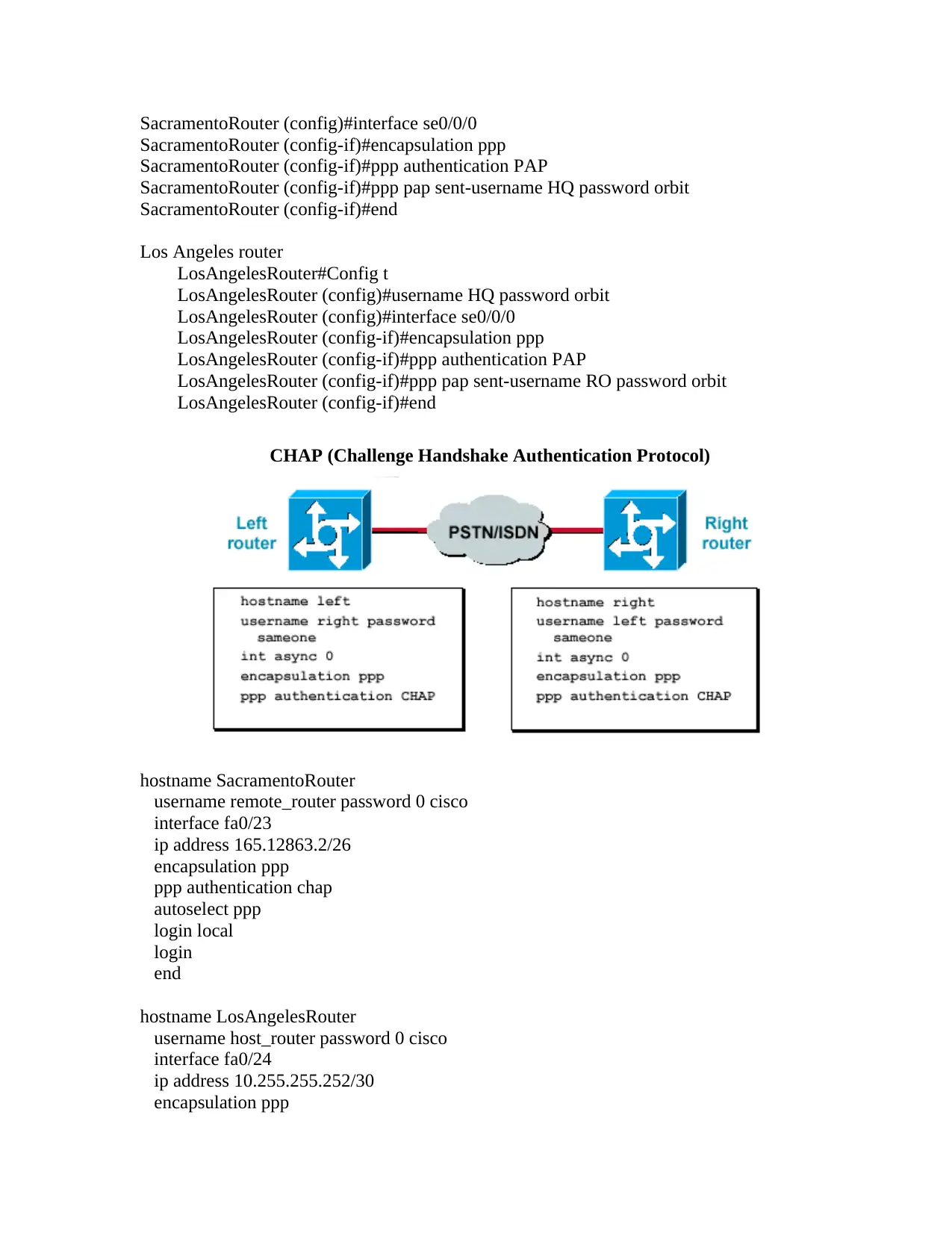
CHAP (Challenge Handshake Authentication Protocol)
hostname SacramentoRouter
username remote_router password 0 cisco
interface fa0/23
ip address 165.12863.2/26
encapsulation ppp
ppp authentication chap
autoselect ppp
login local
login
end
hostname LosAngelesRouter
username host_router password 0 cisco
interface fa0/24
ip address 10.255.255.252/30
encapsulation ppp
SacramentoRouter (config-if)#encapsulation ppp
SacramentoRouter (config-if)#ppp authentication PAP
SacramentoRouter (config-if)#ppp pap sent-username HQ password orbit
SacramentoRouter (config-if)#end
Los Angeles router
LosAngelesRouter#Config t
LosAngelesRouter (config)#username HQ password orbit
LosAngelesRouter (config)#interface se0/0/0
LosAngelesRouter (config-if)#encapsulation ppp
LosAngelesRouter (config-if)#ppp authentication PAP
LosAngelesRouter (config-if)#ppp pap sent-username RO password orbit
LosAngelesRouter (config-if)#end
CHAP (Challenge Handshake Authentication Protocol)
hostname SacramentoRouter
username remote_router password 0 cisco
interface fa0/23
ip address 165.12863.2/26
encapsulation ppp
ppp authentication chap
autoselect ppp
login local
login
end
hostname LosAngelesRouter
username host_router password 0 cisco
interface fa0/24
ip address 10.255.255.252/30
encapsulation ppp

ppp authentication chap
autoselect ppp
login local
login
end
Bibliography
[1]"Understanding and Configuring PPP CHAP Authentication", Cisco, 2016. [Online].
Available: http://www.cisco.com/c/en/us/support/docs/wan/point-to-point-protocol-ppp/25647-
understanding-ppp-chap.html. [Accessed: 01- Jul- 2016].
[2]P. Support, C. Firewall, T. Alerts and T. TechNotes, "Configuring IP Access Lists", Cisco,
2016. [Online]. Available:
http://www.cisco.com/c/en/us/support/docs/security/ios-firewall/23602-confaccesslists.html.
[Accessed: 01- Jul- 2016].
[3]"How To Configure Router On A Stick - 802.1q Trunk To Cisco Router", Firewall.cx, 2016.
[Online]. Available: http://www.firewall.cx/cisco-technical-knowledgebase/cisco-routers/336-
cisco-router-8021q-router-stick.html. [Accessed: 01- Jul- 2016].
autoselect ppp
login local
login
end
Bibliography
[1]"Understanding and Configuring PPP CHAP Authentication", Cisco, 2016. [Online].
Available: http://www.cisco.com/c/en/us/support/docs/wan/point-to-point-protocol-ppp/25647-
understanding-ppp-chap.html. [Accessed: 01- Jul- 2016].
[2]P. Support, C. Firewall, T. Alerts and T. TechNotes, "Configuring IP Access Lists", Cisco,
2016. [Online]. Available:
http://www.cisco.com/c/en/us/support/docs/security/ios-firewall/23602-confaccesslists.html.
[Accessed: 01- Jul- 2016].
[3]"How To Configure Router On A Stick - 802.1q Trunk To Cisco Router", Firewall.cx, 2016.
[Online]. Available: http://www.firewall.cx/cisco-technical-knowledgebase/cisco-routers/336-
cisco-router-8021q-router-stick.html. [Accessed: 01- Jul- 2016].
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 6
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


