CMP71001 - Cybersecurity Risk Assessment of BYOD Policy at SCU
VerifiedAdded on 2023/06/03
|13
|2466
|317
Report
AI Summary
This report provides a risk assessment of Southern Cross University's information system, focusing on the Bring Your Own Device (BYOD) policy and its potential threats to critical information assets such as software tools, data governance, master data governance, and financial policies. It identifies vulnerabilities and assesses the level of risk associated with data theft, network breakdowns, and violations of financial policies. The report also compares certificate-based authentication with password-based authentication, highlighting the features and advantages of the former in enhancing security. Furthermore, it discusses the characteristics of spam and spamming acts, provides examples of different types of spam, and offers spam handling instructions. The conclusion emphasizes the need for robust security measures, such as certificate-based authentication and anti-spam guidelines, to protect the university's information system from cyber threats.

Running Head: CYBER SECURITY IN SOUTHERN CROSS UNIVERSITY
Risk Assessment of Southern Cross University
Name of the student:
Name of the university:
Author note:
Risk Assessment of Southern Cross University
Name of the student:
Name of the university:
Author note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1CYBER SECURITY IN SOUTHERN CROSS UNIVERSITY
Table of Contents
Introduction......................................................................................................................................2
Task 1...............................................................................................................................................2
Critical Components of the Southern Cross University’s Information System...........................2
BYOD Policy threats to critical information assets.....................................................................2
Potential vulnerabilities of each assets against the identified threats..........................................3
Vulnerability to data governance......................................................................................3
Vulnerability to master data governance..........................................................................3
Vulnerability to financial data and policy.........................................................................4
Vulnerability to software tools..........................................................................................4
Risk assessment of the university’s information system.............................................................4
Task 2...............................................................................................................................................5
Brief explanation of Certificate-based Authentication................................................................5
Comparison between certificate-based authentication and password-based authentication.......6
Features of certificate-based authentication................................................................................6
Task 3...............................................................................................................................................7
Characteristics of Spam and Spamming Act...............................................................................7
Three representative examples of Spams....................................................................................8
Spam handling instruction...........................................................................................................8
Conclusion.......................................................................................................................................9
Reference.......................................................................................................................................10
Table of Contents
Introduction......................................................................................................................................2
Task 1...............................................................................................................................................2
Critical Components of the Southern Cross University’s Information System...........................2
BYOD Policy threats to critical information assets.....................................................................2
Potential vulnerabilities of each assets against the identified threats..........................................3
Vulnerability to data governance......................................................................................3
Vulnerability to master data governance..........................................................................3
Vulnerability to financial data and policy.........................................................................4
Vulnerability to software tools..........................................................................................4
Risk assessment of the university’s information system.............................................................4
Task 2...............................................................................................................................................5
Brief explanation of Certificate-based Authentication................................................................5
Comparison between certificate-based authentication and password-based authentication.......6
Features of certificate-based authentication................................................................................6
Task 3...............................................................................................................................................7
Characteristics of Spam and Spamming Act...............................................................................7
Three representative examples of Spams....................................................................................8
Spam handling instruction...........................................................................................................8
Conclusion.......................................................................................................................................9
Reference.......................................................................................................................................10

2CYBER SECURITY IN SOUTHERN CROSS UNIVERSITY
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3CYBER SECURITY IN SOUTHERN CROSS UNIVERSITY
Introduction:
This assignment will enlighten on the risk assessment of Southern Cross University. The
common risks faced by the university in maintaining the information systems is discussed in the
assignment. To manage risks, the university is using a password based authentication system so
that the access to the university’s information system can be restricted and controlled. However,
the BYOD (Bring Your Own Device) policy is posing great threats to the university. The
following paragraphs will deal with risk assessment of the BYOD policy to the university’s
information system, the advantages of Certificate based authentication over password-based
authentication followed by providing a guideline for anti-spamming.
Task 1:
Critical Components of the Southern Cross University’s Information System:
The critical information assets of Southern Cross University are software tools, Data governance,
Master data governance and financial policies. The software tools are required to protect the data
assets of the university by facilitating data governance. The university has adopted various data
governance software tools and technology to keep the data confidential.
BYOD Policy threats to critical information assets:
The potential threats that arises from Bring your own device policy to information assets of
universities are as follows:
The personal devices like smart phones laptops and tablets that are brought inside the
campus of the university are connected to the network of the university through LANs or
VLANs. If the devices contain viruses in it, then the viruses would contaminate the
Introduction:
This assignment will enlighten on the risk assessment of Southern Cross University. The
common risks faced by the university in maintaining the information systems is discussed in the
assignment. To manage risks, the university is using a password based authentication system so
that the access to the university’s information system can be restricted and controlled. However,
the BYOD (Bring Your Own Device) policy is posing great threats to the university. The
following paragraphs will deal with risk assessment of the BYOD policy to the university’s
information system, the advantages of Certificate based authentication over password-based
authentication followed by providing a guideline for anti-spamming.
Task 1:
Critical Components of the Southern Cross University’s Information System:
The critical information assets of Southern Cross University are software tools, Data governance,
Master data governance and financial policies. The software tools are required to protect the data
assets of the university by facilitating data governance. The university has adopted various data
governance software tools and technology to keep the data confidential.
BYOD Policy threats to critical information assets:
The potential threats that arises from Bring your own device policy to information assets of
universities are as follows:
The personal devices like smart phones laptops and tablets that are brought inside the
campus of the university are connected to the network of the university through LANs or
VLANs. If the devices contain viruses in it, then the viruses would contaminate the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4CYBER SECURITY IN SOUTHERN CROSS UNIVERSITY
network and the internal campus resources of Southern Cross University would be
infected.
According to BYOD policy, regular monitoring of personal devices are not done by the
university and therefore, some students might intentionally introduce malicious codes to
the network that would result in breakdown of the network. Software tools is one of the
critical information assets that is used by the university. Introduction of malware might
crash the software that would lead to shutdown of the whole information system of the
university.
The staffs of the university are given responsibility of protecting data as per BYOD
policy. However, staffs of Southern Cross University might not be efficient in checking
all the devices and registering each of them in the university’s record. Therefore, threats
prevail in the attack of the information assets.
Potential vulnerabilities of each assets against the identified threats: As discussed the
critical information assets that are used by Southern Cross University are Software tools, Data
governance, Master data governance and financial policies. The vulnerabilities of each assets are
as follows:
Vulnerability to data governance: The data that are stored in the information systems of
the university are vulnerable to attack by malicious codes introduced in the network of
the university.
Vulnerability to master data governance: The master data are also vulnerable to attack
by the malwares. This might lead to data theft. The data of the students studying in
Southern Cross University would be lost that would result in great trouble while
retrieving them.
network and the internal campus resources of Southern Cross University would be
infected.
According to BYOD policy, regular monitoring of personal devices are not done by the
university and therefore, some students might intentionally introduce malicious codes to
the network that would result in breakdown of the network. Software tools is one of the
critical information assets that is used by the university. Introduction of malware might
crash the software that would lead to shutdown of the whole information system of the
university.
The staffs of the university are given responsibility of protecting data as per BYOD
policy. However, staffs of Southern Cross University might not be efficient in checking
all the devices and registering each of them in the university’s record. Therefore, threats
prevail in the attack of the information assets.
Potential vulnerabilities of each assets against the identified threats: As discussed the
critical information assets that are used by Southern Cross University are Software tools, Data
governance, Master data governance and financial policies. The vulnerabilities of each assets are
as follows:
Vulnerability to data governance: The data that are stored in the information systems of
the university are vulnerable to attack by malicious codes introduced in the network of
the university.
Vulnerability to master data governance: The master data are also vulnerable to attack
by the malwares. This might lead to data theft. The data of the students studying in
Southern Cross University would be lost that would result in great trouble while
retrieving them.
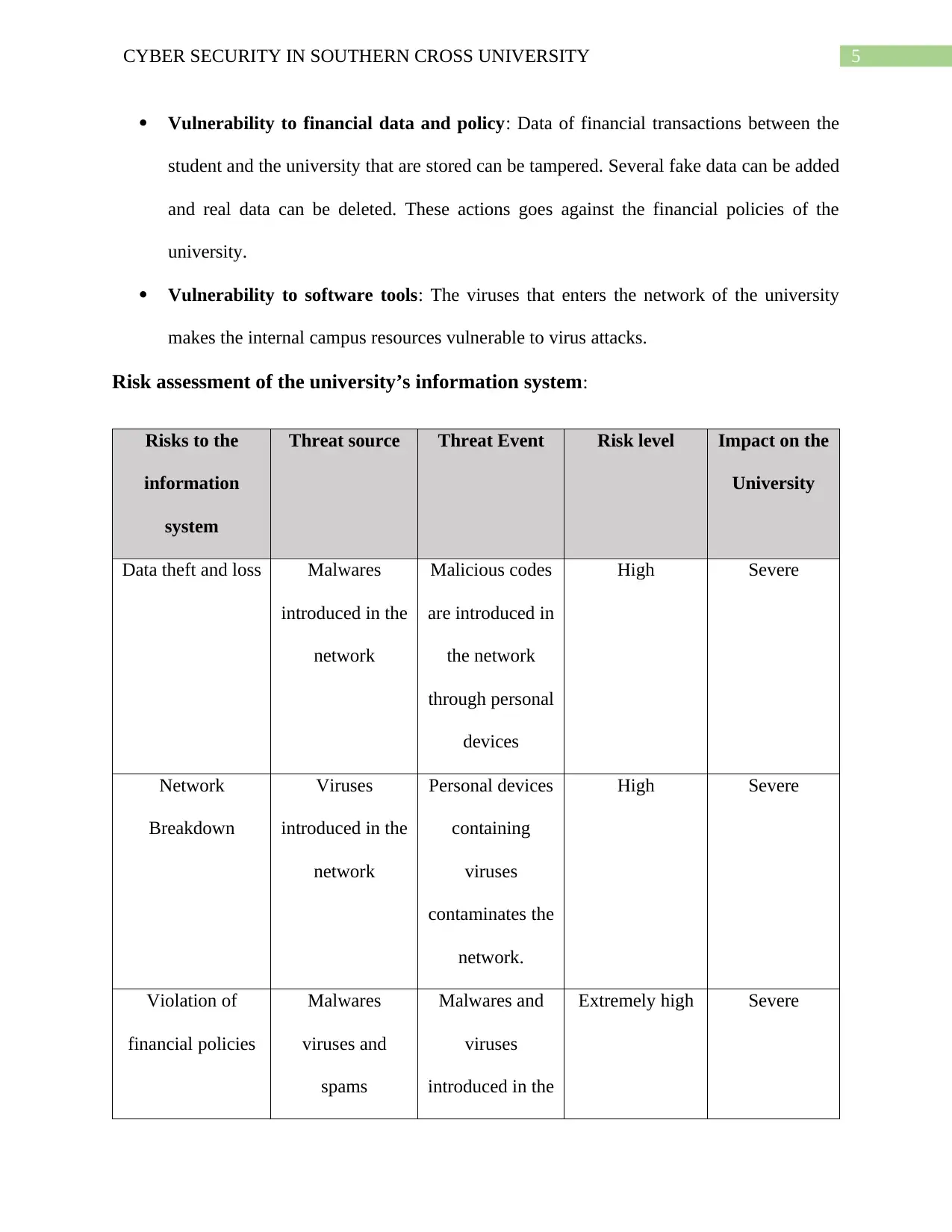
5CYBER SECURITY IN SOUTHERN CROSS UNIVERSITY
Vulnerability to financial data and policy: Data of financial transactions between the
student and the university that are stored can be tampered. Several fake data can be added
and real data can be deleted. These actions goes against the financial policies of the
university.
Vulnerability to software tools: The viruses that enters the network of the university
makes the internal campus resources vulnerable to virus attacks.
Risk assessment of the university’s information system:
Risks to the
information
system
Threat source Threat Event Risk level Impact on the
University
Data theft and loss Malwares
introduced in the
network
Malicious codes
are introduced in
the network
through personal
devices
High Severe
Network
Breakdown
Viruses
introduced in the
network
Personal devices
containing
viruses
contaminates the
network.
High Severe
Violation of
financial policies
Malwares
viruses and
spams
Malwares and
viruses
introduced in the
Extremely high Severe
Vulnerability to financial data and policy: Data of financial transactions between the
student and the university that are stored can be tampered. Several fake data can be added
and real data can be deleted. These actions goes against the financial policies of the
university.
Vulnerability to software tools: The viruses that enters the network of the university
makes the internal campus resources vulnerable to virus attacks.
Risk assessment of the university’s information system:
Risks to the
information
system
Threat source Threat Event Risk level Impact on the
University
Data theft and loss Malwares
introduced in the
network
Malicious codes
are introduced in
the network
through personal
devices
High Severe
Network
Breakdown
Viruses
introduced in the
network
Personal devices
containing
viruses
contaminates the
network.
High Severe
Violation of
financial policies
Malwares
viruses and
spams
Malwares and
viruses
introduced in the
Extremely high Severe
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
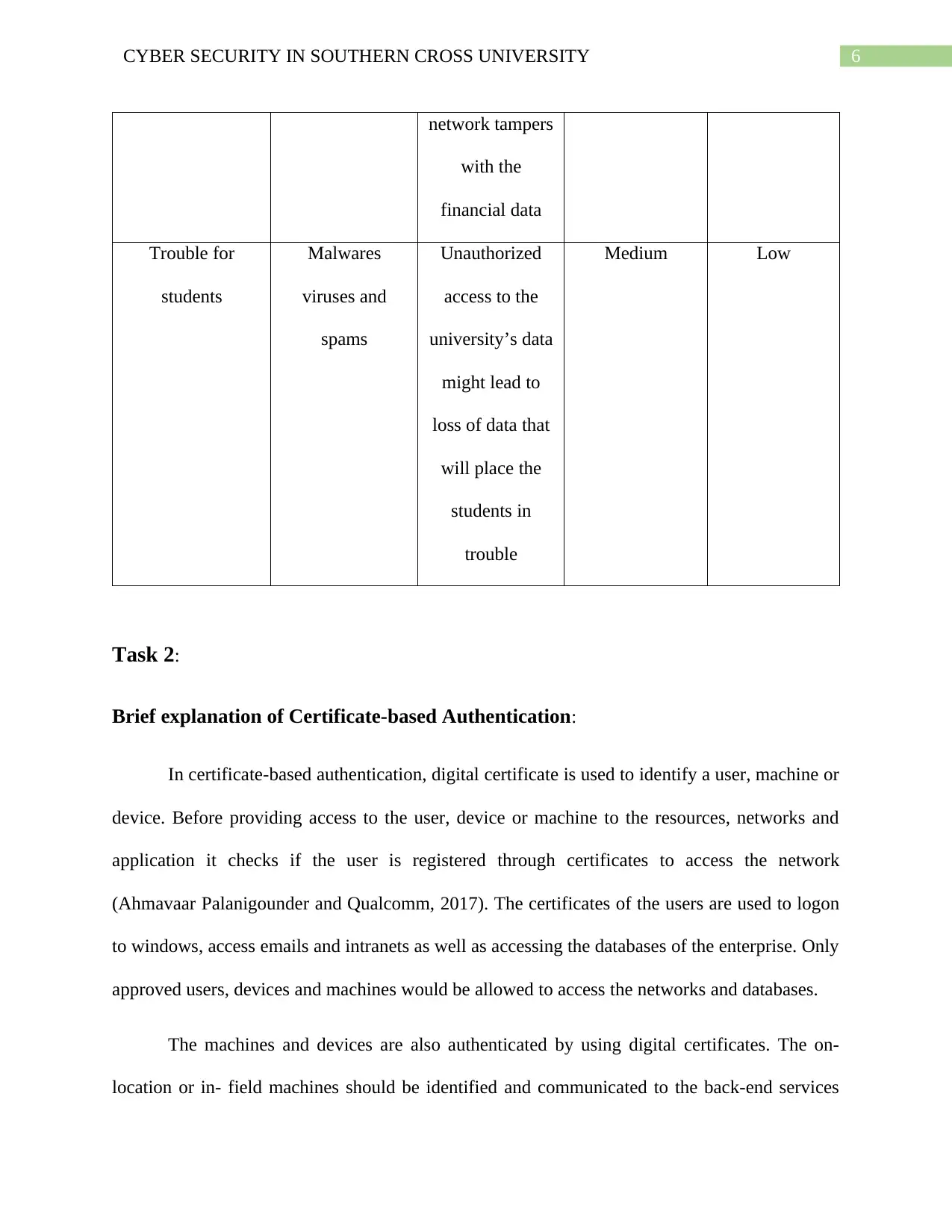
6CYBER SECURITY IN SOUTHERN CROSS UNIVERSITY
network tampers
with the
financial data
Trouble for
students
Malwares
viruses and
spams
Unauthorized
access to the
university’s data
might lead to
loss of data that
will place the
students in
trouble
Medium Low
Task 2:
Brief explanation of Certificate-based Authentication:
In certificate-based authentication, digital certificate is used to identify a user, machine or
device. Before providing access to the user, device or machine to the resources, networks and
application it checks if the user is registered through certificates to access the network
(Ahmavaar Palanigounder and Qualcomm, 2017). The certificates of the users are used to logon
to windows, access emails and intranets as well as accessing the databases of the enterprise. Only
approved users, devices and machines would be allowed to access the networks and databases.
The machines and devices are also authenticated by using digital certificates. The on-
location or in- field machines should be identified and communicated to the back-end services
network tampers
with the
financial data
Trouble for
students
Malwares
viruses and
spams
Unauthorized
access to the
university’s data
might lead to
loss of data that
will place the
students in
trouble
Medium Low
Task 2:
Brief explanation of Certificate-based Authentication:
In certificate-based authentication, digital certificate is used to identify a user, machine or
device. Before providing access to the user, device or machine to the resources, networks and
application it checks if the user is registered through certificates to access the network
(Ahmavaar Palanigounder and Qualcomm, 2017). The certificates of the users are used to logon
to windows, access emails and intranets as well as accessing the databases of the enterprise. Only
approved users, devices and machines would be allowed to access the networks and databases.
The machines and devices are also authenticated by using digital certificates. The on-
location or in- field machines should be identified and communicated to the back-end services
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7CYBER SECURITY IN SOUTHERN CROSS UNIVERSITY
(Hummen et al., 2013). The personal devices like smart phones, laptops and tablets should be
identified before access is allowed to Wi-Fi networks. Mutual certificate-based authentication
between various servers of the enterprise is enabled (Xue et al., 2013).
Comparison between certificate-based authentication and password-based
authentication:
Certificate-based authentication is better than password-based authentication due to some
differences between them. The differences between them are as follows:
The security provided by certificate-based authentication is much more than password-
based application. This is because the users create passwords themselves that can be
easily identified (Farash and Attari, 2016). Whereas, certificate-based authentication
uses asymmetric cryptography. A certification authority with unique information for
each individual issues certificates. Therefore, it cannot be guessed and provides better
security to users.
Passwords are mostly simple consisting of strings, numbers and special characters
whereas, certificates are complex consisting of detailed information of the user
(Turkanovic and Holbl, 2013). Therefore, passwords of the user can be guessed easily
however, it is not possible in case of certificates.
Certificate-based authentication allows separation of roles that is not allowed by
password-based applications.
Certificate-based authentication is expensive than that of password-based authentication.
Features of certificate-based authentication:
Some features of certificate-based authentication are mentioned below:
(Hummen et al., 2013). The personal devices like smart phones, laptops and tablets should be
identified before access is allowed to Wi-Fi networks. Mutual certificate-based authentication
between various servers of the enterprise is enabled (Xue et al., 2013).
Comparison between certificate-based authentication and password-based
authentication:
Certificate-based authentication is better than password-based authentication due to some
differences between them. The differences between them are as follows:
The security provided by certificate-based authentication is much more than password-
based application. This is because the users create passwords themselves that can be
easily identified (Farash and Attari, 2016). Whereas, certificate-based authentication
uses asymmetric cryptography. A certification authority with unique information for
each individual issues certificates. Therefore, it cannot be guessed and provides better
security to users.
Passwords are mostly simple consisting of strings, numbers and special characters
whereas, certificates are complex consisting of detailed information of the user
(Turkanovic and Holbl, 2013). Therefore, passwords of the user can be guessed easily
however, it is not possible in case of certificates.
Certificate-based authentication allows separation of roles that is not allowed by
password-based applications.
Certificate-based authentication is expensive than that of password-based authentication.
Features of certificate-based authentication:
Some features of certificate-based authentication are mentioned below:

8CYBER SECURITY IN SOUTHERN CROSS UNIVERSITY
No additional hardware needed: Unlike authentication methods such as biometrics and
OTP tokens, certificate-based authentication does not require additional hardware (He
and Wang, 2015). The certificates are stored in a machine that reduces pain of
distributing and replacing tokens.
User-friendly: The use of certificates for validating users easy for the end-users. This is
because after certificates are used, no such additional information about the users are
there that can be used.
Mutual Authentication: Another advantage of certificate-based authentication is that it
allows mutual authentication between users or user to machine or machine to machine.
Existing access control policies can be leveraged: Existing group’s policy and
permissions can be leveraged to control the access of users and machines.
Task 3:
Characteristics of Spam and Spamming Act:
Unsolicited messages are regarded as spams. Commercial electronic messages that are
unsolicited cannot be sent. The electronic messages should contain information of the
organization or individual who is authorized for sending the message (Kigerl, 2015). Otherwise,
the message will be marked as spam. The various forms of spam that are email spams, web
search engine spam, online classified ads spam, UseNet newsgroup spam, social spam, mobile
apps spam and so on.
Spamming is the use of messaging systems to send spams (unsolicited messages).
Repeated messages sent to a site is also referred to as spamming. The characteristics of
spamming are explained in the following paragraphs:
No additional hardware needed: Unlike authentication methods such as biometrics and
OTP tokens, certificate-based authentication does not require additional hardware (He
and Wang, 2015). The certificates are stored in a machine that reduces pain of
distributing and replacing tokens.
User-friendly: The use of certificates for validating users easy for the end-users. This is
because after certificates are used, no such additional information about the users are
there that can be used.
Mutual Authentication: Another advantage of certificate-based authentication is that it
allows mutual authentication between users or user to machine or machine to machine.
Existing access control policies can be leveraged: Existing group’s policy and
permissions can be leveraged to control the access of users and machines.
Task 3:
Characteristics of Spam and Spamming Act:
Unsolicited messages are regarded as spams. Commercial electronic messages that are
unsolicited cannot be sent. The electronic messages should contain information of the
organization or individual who is authorized for sending the message (Kigerl, 2015). Otherwise,
the message will be marked as spam. The various forms of spam that are email spams, web
search engine spam, online classified ads spam, UseNet newsgroup spam, social spam, mobile
apps spam and so on.
Spamming is the use of messaging systems to send spams (unsolicited messages).
Repeated messages sent to a site is also referred to as spamming. The characteristics of
spamming are explained in the following paragraphs:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9CYBER SECURITY IN SOUTHERN CROSS UNIVERSITY
Spamming asks for sensitive information
Uses scare tactics
Asks for money in advance
Seems too good to be true
Three representative examples of Spams:
Email spam: It is also known as unsolicited bulk email or junk mail (Idris et al., 2015).
Huge number of messages are sent that are unwanted and it consists of large quantity of
commercial contents.
Instant messaging spam: Instant messaging spams uses instant messaging systems to
that leads to shut down of the network (Youn and Cho, 2015).
Social networking spam: Spam links are sent to account holders in social media like
Facebook and Twitter (Cao and Caverlee, 2015). Once the user opens the link, all data of
the user is collected by unauthorized access.
Spam handling instruction:
Spam is a growing problem in today’s world and needs a solution. Therefore, the
following guidelines will help to reduce spam risks:
Developing strong technical measures.
Effective and strong legislation should be followed.
Best anti-spam practices should be adopted (Rothwell et al., 2015).
By spreading awareness for spams
The internet service providers (ISPs) should use latest anti-spam technology to filter
spams from transferring in a network (Phokeer and Aina, 2016).
Spamming asks for sensitive information
Uses scare tactics
Asks for money in advance
Seems too good to be true
Three representative examples of Spams:
Email spam: It is also known as unsolicited bulk email or junk mail (Idris et al., 2015).
Huge number of messages are sent that are unwanted and it consists of large quantity of
commercial contents.
Instant messaging spam: Instant messaging spams uses instant messaging systems to
that leads to shut down of the network (Youn and Cho, 2015).
Social networking spam: Spam links are sent to account holders in social media like
Facebook and Twitter (Cao and Caverlee, 2015). Once the user opens the link, all data of
the user is collected by unauthorized access.
Spam handling instruction:
Spam is a growing problem in today’s world and needs a solution. Therefore, the
following guidelines will help to reduce spam risks:
Developing strong technical measures.
Effective and strong legislation should be followed.
Best anti-spam practices should be adopted (Rothwell et al., 2015).
By spreading awareness for spams
The internet service providers (ISPs) should use latest anti-spam technology to filter
spams from transferring in a network (Phokeer and Aina, 2016).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10CYBER SECURITY IN SOUTHERN CROSS UNIVERSITY
Conclusion:
From the above discussions, it can be concluded that Southern Cross University’s
information system is facing threats from malwares, viruses and spam that might occur from
‘bring your own device’ policy. However, if certificate-based authentication is used in the
university, then unauthorized access to the network can be controlled. Spams are bulk messages
that are sent through either emails or social media. However, anti-spam guidelines will help to
reduce the threats.
Conclusion:
From the above discussions, it can be concluded that Southern Cross University’s
information system is facing threats from malwares, viruses and spam that might occur from
‘bring your own device’ policy. However, if certificate-based authentication is used in the
university, then unauthorized access to the network can be controlled. Spams are bulk messages
that are sent through either emails or social media. However, anti-spam guidelines will help to
reduce the threats.

11CYBER SECURITY IN SOUTHERN CROSS UNIVERSITY
Reference:
Cao, C. and Caverlee, J., 2015, March. Detecting spam urls in social media via behavioral
analysis. In European Conference on Information Retrieval (pp. 703-714). Springer, Cham.
Farash, M.S. and Attari, M.A., 2016. An anonymous and untraceable password‐based
authentication scheme for session initiation protocol using smart cards. International Journal of
Communication Systems, 29(13), pp.1956-1967.
He, D. and Wang, D., 2015. Robust biometrics-based authentication scheme for multiserver
environment. IEEE Systems Journal, 9(3), pp.816-823.
Hummen, R., Ziegeldorf, J.H., Shafagh, H., Raza, S. and Wehrle, K., 2013, April. Towards
viable certificate-based authentication for the internet of things. In Proceedings of the 2nd ACM
workshop on Hot topics on wireless network security and privacy (pp. 37-42). ACM.
Idris, I., Selamat, A., Nguyen, N.T., Omatu, S., Krejcar, O., Kuca, K. and Penhaker, M., 2015. A
combined negative selection algorithm–particle swarm optimization for an email spam detection
system. Engineering Applications of Artificial Intelligence, 39, pp.33-44.
Kigerl, A.C., 2015. Evaluation of the CAN SPAM ACT: Testing deterrence and other influences
of e-mail spammer legal compliance over time. Social Science Computer Review, 33(4), pp.440-
458.
Phokeer, A. and Aina, A., 2016, May. A survey of anti-spam mechanisms and their usage from a
Regional Internet Registry's perspective. In IST-Africa Week Conference, 2016 (pp. 1-11). IEEE.
Rothwell, S., Elshenawy, A., Carter, S., Braga, D., Romani, F., Kennewick, M. and Kennewick,
B., 2015. Controlling quality and handling fraud in large scale crowdsourcing speech data
Reference:
Cao, C. and Caverlee, J., 2015, March. Detecting spam urls in social media via behavioral
analysis. In European Conference on Information Retrieval (pp. 703-714). Springer, Cham.
Farash, M.S. and Attari, M.A., 2016. An anonymous and untraceable password‐based
authentication scheme for session initiation protocol using smart cards. International Journal of
Communication Systems, 29(13), pp.1956-1967.
He, D. and Wang, D., 2015. Robust biometrics-based authentication scheme for multiserver
environment. IEEE Systems Journal, 9(3), pp.816-823.
Hummen, R., Ziegeldorf, J.H., Shafagh, H., Raza, S. and Wehrle, K., 2013, April. Towards
viable certificate-based authentication for the internet of things. In Proceedings of the 2nd ACM
workshop on Hot topics on wireless network security and privacy (pp. 37-42). ACM.
Idris, I., Selamat, A., Nguyen, N.T., Omatu, S., Krejcar, O., Kuca, K. and Penhaker, M., 2015. A
combined negative selection algorithm–particle swarm optimization for an email spam detection
system. Engineering Applications of Artificial Intelligence, 39, pp.33-44.
Kigerl, A.C., 2015. Evaluation of the CAN SPAM ACT: Testing deterrence and other influences
of e-mail spammer legal compliance over time. Social Science Computer Review, 33(4), pp.440-
458.
Phokeer, A. and Aina, A., 2016, May. A survey of anti-spam mechanisms and their usage from a
Regional Internet Registry's perspective. In IST-Africa Week Conference, 2016 (pp. 1-11). IEEE.
Rothwell, S., Elshenawy, A., Carter, S., Braga, D., Romani, F., Kennewick, M. and Kennewick,
B., 2015. Controlling quality and handling fraud in large scale crowdsourcing speech data
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





