Report on Memcrashed Vulnerability, Exploits & Solutions- CO4509
VerifiedAdded on 2023/04/06
|20
|3898
|455
Report
AI Summary
This report provides a comprehensive analysis of the memcrashed vulnerability, a significant security concern related to memcached servers. It begins by explaining the principles of key-value databases and illustrating their use in various applications. The report then delves into the details of the memcrashed exploit, describing how attackers leverage memcached's functionality to launch Distributed Denial of Service (DDoS) attacks. It outlines the mechanics of the attack, including reflection and amplification techniques, and discusses the impact of such attacks on targeted systems. Furthermore, the report explores potential solutions and preventative measures to mitigate the risks associated with memcrashed, offering insights into securing memcached deployments. Finally, it offers a perspective on the future implications and effectiveness of memcrashed exploits, considering the evolving landscape of cybersecurity threats. This document is available on Desklib, where students can find similar resources.

Running head: VULNERABILITY OF MEM-CRASHED
Vulnerability of mem-crashed
Name of the student:
Name of the university:
Author note:
Vulnerability of mem-crashed
Name of the student:
Name of the university:
Author note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1VULNERABILITY OF MEM-CRASHED
Executive Summary
The following report is prepared to focus on the vulnerabilities faced due to mem crashed
exploitation. Detailed study of mem cached server is done on this report and based on it the
probable attacks that are possible with the mem crashed tool is reflected and the process of
the exploitation is described. In the last part of the report a detailed study of the solutions that
can help in prevention of the mem crashed effect is focused. The future aspects and the
efficient mem crashed vulnerability are thus reflected in the last part of the report.
Executive Summary
The following report is prepared to focus on the vulnerabilities faced due to mem crashed
exploitation. Detailed study of mem cached server is done on this report and based on it the
probable attacks that are possible with the mem crashed tool is reflected and the process of
the exploitation is described. In the last part of the report a detailed study of the solutions that
can help in prevention of the mem crashed effect is focused. The future aspects and the
efficient mem crashed vulnerability are thus reflected in the last part of the report.

2VULNERABILITY OF MEM-CRASHED
Table of Contents
Introduction:...............................................................................................................................3
Discussion:.................................................................................................................................3
Principles of key databases:...................................................................................................3
Example of the use of database:.............................................................................................5
Description of the mem-crashed exploit:...............................................................................6
How does the mem-crash works?..........................................................................................6
Effect of the mem-crashed DDoS attack................................................................................7
Solution of the mem-crashed exploit:....................................................................................8
Future experience and effectiveness of mem-crashed:........................................................11
Conclusion:..............................................................................................................................11
References:...............................................................................................................................13
Table of Contents
Introduction:...............................................................................................................................3
Discussion:.................................................................................................................................3
Principles of key databases:...................................................................................................3
Example of the use of database:.............................................................................................5
Description of the mem-crashed exploit:...............................................................................6
How does the mem-crash works?..........................................................................................6
Effect of the mem-crashed DDoS attack................................................................................7
Solution of the mem-crashed exploit:....................................................................................8
Future experience and effectiveness of mem-crashed:........................................................11
Conclusion:..............................................................................................................................11
References:...............................................................................................................................13
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3VULNERABILITY OF MEM-CRASHED
Introduction:
According to Liu et al. (2015), Mem-cached is defined as a high quality performance
object caching system. It is generic in nature but is intended to speed up dynamic web
applications. This makes it usable with any languages like PHP, Perl, Python, Ruby and many
more. Mem-cash stores key value pairs in memory. It is not classified as the database or does
not persist data to disk by default. One of the most typical use of mem-cash is in PHP or My
Sql where data are required to be fetched from databases (Lavasani, Angepat and Chiou
2014). The fetched values are stored in the mem-cache to access them in a faster way. Mem-
cached is a general purpose distributed memory caching system which speeds up the dynamic
database driven websites. The process gets faster by caching data and objects in the RAM to
reduce the number of times the external data sources such as a database API can be read.
Mem-cashed is an open source software licensed. According to Shodan site, there are over
80,000 mem-cached servers present over worldwide which are using a default insecure
configurations in them (Zhang et al. 2014). They do not have any appropriate network access
policies implemented in them. Mem-cached servers are being abused to launch Distributed
Denial of Service attack. More specifically mem-cached servers can be used for reflection
and amplification of Distributed denial of service attack. As things are getting very real and
generally fast the threat of DDoS aatack is gradually increasing for future markets. Still there
are some vulnerabilities that exist with the memcashed attack which needs to be checked for.
Recently there are about more than thousands of memcashed servers that can cause
vulnerability to the mem cached attack. Shadow server foundation founded about 50000
running mem cache servers running on the public internet today. That means there are 50000
reflectors out there that can be pulled together and spoofed into sending traffic against a
single target. The scary part of this type of attack is that due to the raw capability of the
attacking vector, there is actual potential for even larger attacks to come in future. This report
Introduction:
According to Liu et al. (2015), Mem-cached is defined as a high quality performance
object caching system. It is generic in nature but is intended to speed up dynamic web
applications. This makes it usable with any languages like PHP, Perl, Python, Ruby and many
more. Mem-cash stores key value pairs in memory. It is not classified as the database or does
not persist data to disk by default. One of the most typical use of mem-cash is in PHP or My
Sql where data are required to be fetched from databases (Lavasani, Angepat and Chiou
2014). The fetched values are stored in the mem-cache to access them in a faster way. Mem-
cached is a general purpose distributed memory caching system which speeds up the dynamic
database driven websites. The process gets faster by caching data and objects in the RAM to
reduce the number of times the external data sources such as a database API can be read.
Mem-cashed is an open source software licensed. According to Shodan site, there are over
80,000 mem-cached servers present over worldwide which are using a default insecure
configurations in them (Zhang et al. 2014). They do not have any appropriate network access
policies implemented in them. Mem-cached servers are being abused to launch Distributed
Denial of Service attack. More specifically mem-cached servers can be used for reflection
and amplification of Distributed denial of service attack. As things are getting very real and
generally fast the threat of DDoS aatack is gradually increasing for future markets. Still there
are some vulnerabilities that exist with the memcashed attack which needs to be checked for.
Recently there are about more than thousands of memcashed servers that can cause
vulnerability to the mem cached attack. Shadow server foundation founded about 50000
running mem cache servers running on the public internet today. That means there are 50000
reflectors out there that can be pulled together and spoofed into sending traffic against a
single target. The scary part of this type of attack is that due to the raw capability of the
attacking vector, there is actual potential for even larger attacks to come in future. This report
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4VULNERABILITY OF MEM-CRASHED
focusses on the critically vulnerability that is faced in Mem-cached that is the mem-crashed
and based on it necessary solutions are recommended in the report.
Discussion:
Principles of key databases:
However, a database system is an assortment of data sets to store them for a long period of
time. A database system provides an interface between the stored information and retrieved
data.
A good and efficient database includes the following characteristics:
1. Concurrency: Concurrency of a database is measured when multiple users are able to use
the database safely and able to read and edit the contents of the entries at the same time.
2. Scalability: A database is said to be scalable when large tables can be read without facing
any issues.
3. Reliability: The reliability feature exists with the relational databases where it enforces the
concept of tidy data.
The term database is often related to the relational database systems where data are allowed
to manipulate with the help of structured query language (Bugiotti et al. 2014). Database
management provides users to comprehensively use the data present in the database system.
A key value database is defined as a database that stores data associated with array or hash
tables. A key value database works relatively better that the relational database system. It
consists of identifiers that are stored as key values (Lu, Shankar and Panda 2017). The values
focusses on the critically vulnerability that is faced in Mem-cached that is the mem-crashed
and based on it necessary solutions are recommended in the report.
Discussion:
Principles of key databases:
However, a database system is an assortment of data sets to store them for a long period of
time. A database system provides an interface between the stored information and retrieved
data.
A good and efficient database includes the following characteristics:
1. Concurrency: Concurrency of a database is measured when multiple users are able to use
the database safely and able to read and edit the contents of the entries at the same time.
2. Scalability: A database is said to be scalable when large tables can be read without facing
any issues.
3. Reliability: The reliability feature exists with the relational databases where it enforces the
concept of tidy data.
The term database is often related to the relational database systems where data are allowed
to manipulate with the help of structured query language (Bugiotti et al. 2014). Database
management provides users to comprehensively use the data present in the database system.
A key value database is defined as a database that stores data associated with array or hash
tables. A key value database works relatively better that the relational database system. It
consists of identifiers that are stored as key values (Lu, Shankar and Panda 2017). The values

5VULNERABILITY OF MEM-CRASHED
related to arrays, strings or any data structure, can be sorted out with the help of this
identifiers. As for example, Windows Explorer as well as Apple Finder are key value
database systems. A good key value data must include scalable data, cache management,
Block chain implementation and multimedia storage.
The principles of key-valued data base system include-
1. Simplicity: Key-value database system is quite simple to use as it contains the basic data
structure in it. It can store value including arrays, strings, integers followed by a key that
helps in referencing the value.
2. Flexibility: This principle of Document database system remains similar to that of the
Key-Data base system where it contains a set of key-value pairs inside a document.
3. Comparison features: Key-value database system stores the set of key-value pairs
together within a single name space in a relational schema. Key-value pairs having similar
IDs consists of dissimilar type of values in them.
Example of the use of database:
Key-value database can be applied to many cases such as:
It can be used it general computers where it can be used to store information like-
Session information: session information includes interchange of information between
communicating devices such as HTTP sessions or login sessions.
Profile details of users: This data sets includes information related to passwords and number
of access to the profile of a particular user.
related to arrays, strings or any data structure, can be sorted out with the help of this
identifiers. As for example, Windows Explorer as well as Apple Finder are key value
database systems. A good key value data must include scalable data, cache management,
Block chain implementation and multimedia storage.
The principles of key-valued data base system include-
1. Simplicity: Key-value database system is quite simple to use as it contains the basic data
structure in it. It can store value including arrays, strings, integers followed by a key that
helps in referencing the value.
2. Flexibility: This principle of Document database system remains similar to that of the
Key-Data base system where it contains a set of key-value pairs inside a document.
3. Comparison features: Key-value database system stores the set of key-value pairs
together within a single name space in a relational schema. Key-value pairs having similar
IDs consists of dissimilar type of values in them.
Example of the use of database:
Key-value database can be applied to many cases such as:
It can be used it general computers where it can be used to store information like-
Session information: session information includes interchange of information between
communicating devices such as HTTP sessions or login sessions.
Profile details of users: This data sets includes information related to passwords and number
of access to the profile of a particular user.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6VULNERABILITY OF MEM-CRASHED
Comments related to blog or any article that is published: Storing information related to
comments dine in different blog articles.
Message status: Database are designed to store messages and their status related to chat
query.
Emails: It also allows storing of emails in the database system.
Another example to where key-value database systems can be used is in the maintenance of
data in the networking areas. The database systems store values related to-
1. Telecom directories
2. Forwarding tables of Internet Protocols
3. DE duplicated data
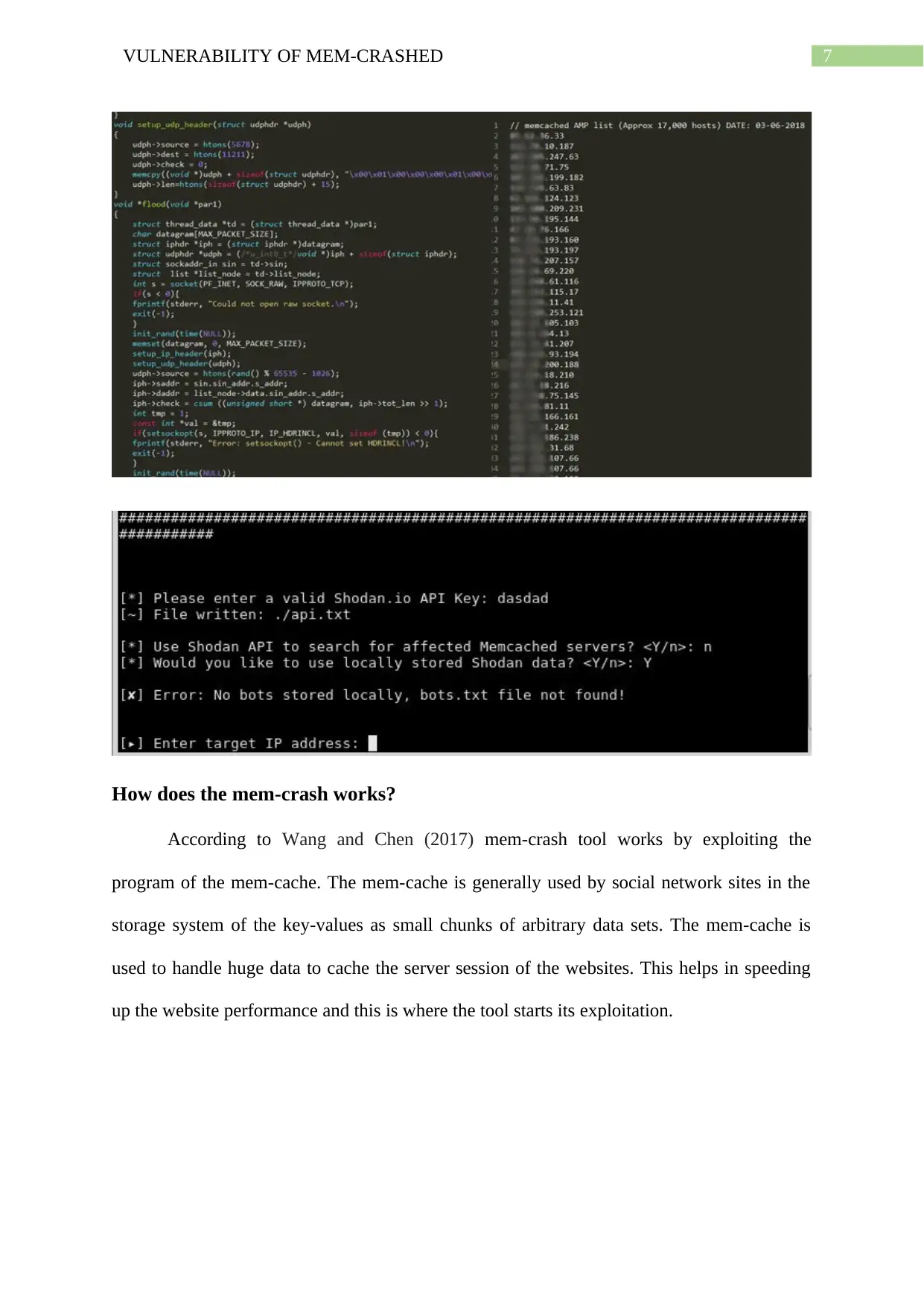
Description of the mem-crashed exploit:
Mem-crashed is a tool that is used to exploit the Distributed Denial of Service of the
Mem-cache. The entire tool is written in Python which allows to transfer the UDP packets to
a list of servers of the Mem-cached obtained from the Shodan site.
Comments related to blog or any article that is published: Storing information related to
comments dine in different blog articles.
Message status: Database are designed to store messages and their status related to chat
query.
Emails: It also allows storing of emails in the database system.
Another example to where key-value database systems can be used is in the maintenance of
data in the networking areas. The database systems store values related to-
1. Telecom directories
2. Forwarding tables of Internet Protocols
3. DE duplicated data
Description of the mem-crashed exploit:
Mem-crashed is a tool that is used to exploit the Distributed Denial of Service of the
Mem-cache. The entire tool is written in Python which allows to transfer the UDP packets to
a list of servers of the Mem-cached obtained from the Shodan site.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7VULNERABILITY OF MEM-CRASHED
How does the mem-crash works?
According to Wang and Chen (2017) mem-crash tool works by exploiting the
program of the mem-cache. The mem-cache is generally used by social network sites in the
storage system of the key-values as small chunks of arbitrary data sets. The mem-cache is
used to handle huge data to cache the server session of the websites. This helps in speeding
up the website performance and this is where the tool starts its exploitation.
How does the mem-crash works?
According to Wang and Chen (2017) mem-crash tool works by exploiting the
program of the mem-cache. The mem-cache is generally used by social network sites in the
storage system of the key-values as small chunks of arbitrary data sets. The mem-cache is
used to handle huge data to cache the server session of the websites. This helps in speeding
up the website performance and this is where the tool starts its exploitation.

8VULNERABILITY OF MEM-CRASHED
The exploit of mem-crashed was first discovered in the year 2018. The exploit
executes powerful Distributed Denial of Service attack in amplification. According to report,
the exploitation is reported to be noticeable in IoT devices with low bandwidth (Duro et al.
2016). The mem-cached servers remain connected to higher bandwidth networks and as a
result of increased amplification factor, the delivered data slides to crippling effect. As per
Ghiëtte and Doerr (2018), exploited mem-crashed servers are vulnerable to the bluffed UDP
packets that are sent to the port 11211. The misconfigured servers cause the denial of service
attack by the method of reflection and amplification. Whenever a get requests of the mem-
cached is received by the server, the requested values get collected in the form of a response
from the memory. The value then gets transferred over the internet in the form of stream of
uninterrupted multiple UDP packets. Each of the UDP packets that is sent, measures with a
length of up to 1400 bytes. The tool does not stop its exploitation over here only. There is
more to go. The attacker using the mem-crashed tool injects records in the open servers of the
mem-cached. As a result, the mem-cached uses a stored value up to the limit of 1 MB per
storage. As there is no authentication factor present with the mem-cached servers hence
attackers can demand a multiple number of duplicate keys with a single request. As result of
this, attackers can load huge valued data into the data base store and use these data in their
further attacks. According to report, the web performance of the Cloud Fare company found
to trigger 15 bytes of request responding to about 134 KB. This is known as the amplification
The exploit of mem-crashed was first discovered in the year 2018. The exploit
executes powerful Distributed Denial of Service attack in amplification. According to report,
the exploitation is reported to be noticeable in IoT devices with low bandwidth (Duro et al.
2016). The mem-cached servers remain connected to higher bandwidth networks and as a
result of increased amplification factor, the delivered data slides to crippling effect. As per
Ghiëtte and Doerr (2018), exploited mem-crashed servers are vulnerable to the bluffed UDP
packets that are sent to the port 11211. The misconfigured servers cause the denial of service
attack by the method of reflection and amplification. Whenever a get requests of the mem-
cached is received by the server, the requested values get collected in the form of a response
from the memory. The value then gets transferred over the internet in the form of stream of
uninterrupted multiple UDP packets. Each of the UDP packets that is sent, measures with a
length of up to 1400 bytes. The tool does not stop its exploitation over here only. There is
more to go. The attacker using the mem-crashed tool injects records in the open servers of the
mem-cached. As a result, the mem-cached uses a stored value up to the limit of 1 MB per
storage. As there is no authentication factor present with the mem-cached servers hence
attackers can demand a multiple number of duplicate keys with a single request. As result of
this, attackers can load huge valued data into the data base store and use these data in their
further attacks. According to report, the web performance of the Cloud Fare company found
to trigger 15 bytes of request responding to about 134 KB. This is known as the amplification
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9VULNERABILITY OF MEM-CRASHED
factor. The UDP reflection initiates the amplification attack by taking advantage of UDP
traffic as both the senders and the recipients do not need to commit to the network bi-
directionally. This allows weaponing about thousands of services in the internet by allowing
request along with a spoofed address source. This spoofed address is the intended target for
those attacks which the services flood with bunch of responses to those requests that were
never made.
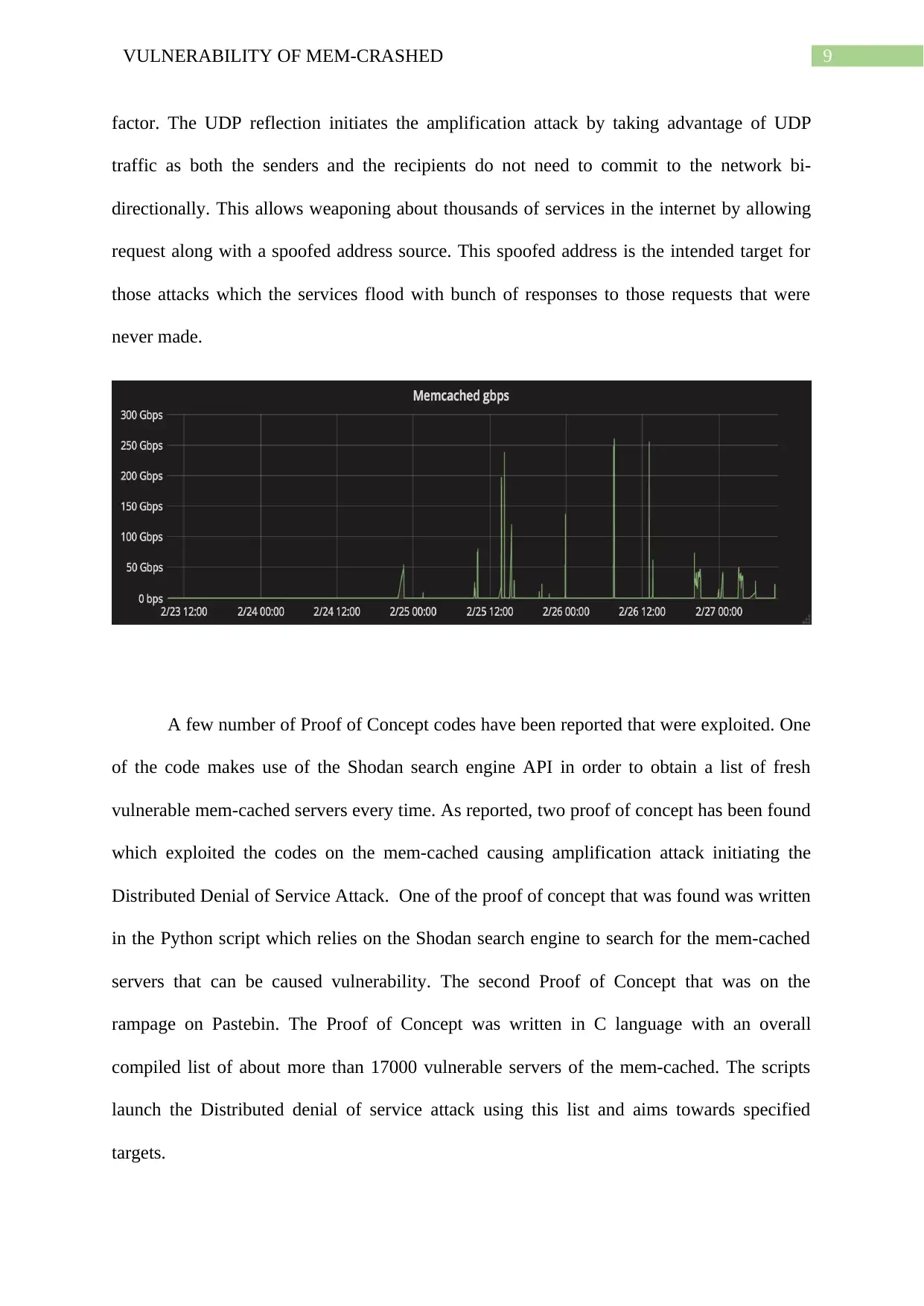
A few number of Proof of Concept codes have been reported that were exploited. One
of the code makes use of the Shodan search engine API in order to obtain a list of fresh
vulnerable mem-cached servers every time. As reported, two proof of concept has been found
which exploited the codes on the mem-cached causing amplification attack initiating the
Distributed Denial of Service Attack. One of the proof of concept that was found was written
in the Python script which relies on the Shodan search engine to search for the mem-cached
servers that can be caused vulnerability. The second Proof of Concept that was on the
rampage on Pastebin. The Proof of Concept was written in C language with an overall
compiled list of about more than 17000 vulnerable servers of the mem-cached. The scripts
launch the Distributed denial of service attack using this list and aims towards specified
targets.
factor. The UDP reflection initiates the amplification attack by taking advantage of UDP
traffic as both the senders and the recipients do not need to commit to the network bi-
directionally. This allows weaponing about thousands of services in the internet by allowing
request along with a spoofed address source. This spoofed address is the intended target for
those attacks which the services flood with bunch of responses to those requests that were
never made.
A few number of Proof of Concept codes have been reported that were exploited. One
of the code makes use of the Shodan search engine API in order to obtain a list of fresh
vulnerable mem-cached servers every time. As reported, two proof of concept has been found
which exploited the codes on the mem-cached causing amplification attack initiating the
Distributed Denial of Service Attack. One of the proof of concept that was found was written
in the Python script which relies on the Shodan search engine to search for the mem-cached
servers that can be caused vulnerability. The second Proof of Concept that was on the
rampage on Pastebin. The Proof of Concept was written in C language with an overall
compiled list of about more than 17000 vulnerable servers of the mem-cached. The scripts
launch the Distributed denial of service attack using this list and aims towards specified
targets.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10VULNERABILITY OF MEM-CRASHED
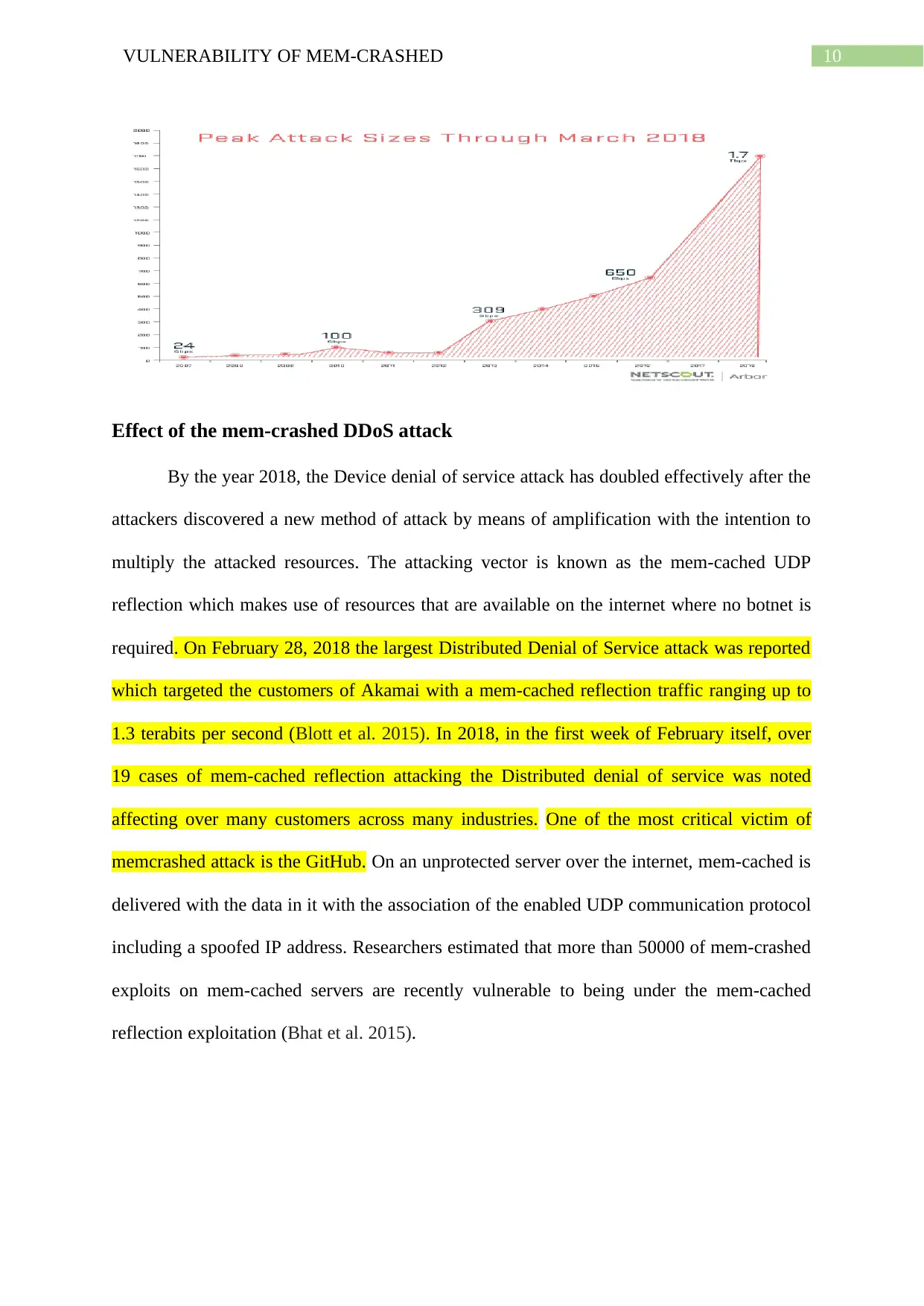
Effect of the mem-crashed DDoS attack
By the year 2018, the Device denial of service attack has doubled effectively after the
attackers discovered a new method of attack by means of amplification with the intention to
multiply the attacked resources. The attacking vector is known as the mem-cached UDP
reflection which makes use of resources that are available on the internet where no botnet is
required. On February 28, 2018 the largest Distributed Denial of Service attack was reported
which targeted the customers of Akamai with a mem-cached reflection traffic ranging up to
1.3 terabits per second (Blott et al. 2015). In 2018, in the first week of February itself, over
19 cases of mem-cached reflection attacking the Distributed denial of service was noted
affecting over many customers across many industries. One of the most critical victim of
memcrashed attack is the GitHub. On an unprotected server over the internet, mem-cached is
delivered with the data in it with the association of the enabled UDP communication protocol
including a spoofed IP address. Researchers estimated that more than 50000 of mem-crashed
exploits on mem-cached servers are recently vulnerable to being under the mem-cached
reflection exploitation (Bhat et al. 2015).
Effect of the mem-crashed DDoS attack
By the year 2018, the Device denial of service attack has doubled effectively after the
attackers discovered a new method of attack by means of amplification with the intention to
multiply the attacked resources. The attacking vector is known as the mem-cached UDP
reflection which makes use of resources that are available on the internet where no botnet is
required. On February 28, 2018 the largest Distributed Denial of Service attack was reported
which targeted the customers of Akamai with a mem-cached reflection traffic ranging up to
1.3 terabits per second (Blott et al. 2015). In 2018, in the first week of February itself, over
19 cases of mem-cached reflection attacking the Distributed denial of service was noted
affecting over many customers across many industries. One of the most critical victim of
memcrashed attack is the GitHub. On an unprotected server over the internet, mem-cached is
delivered with the data in it with the association of the enabled UDP communication protocol
including a spoofed IP address. Researchers estimated that more than 50000 of mem-crashed
exploits on mem-cached servers are recently vulnerable to being under the mem-cached
reflection exploitation (Bhat et al. 2015).
11VULNERABILITY OF MEM-CRASHED
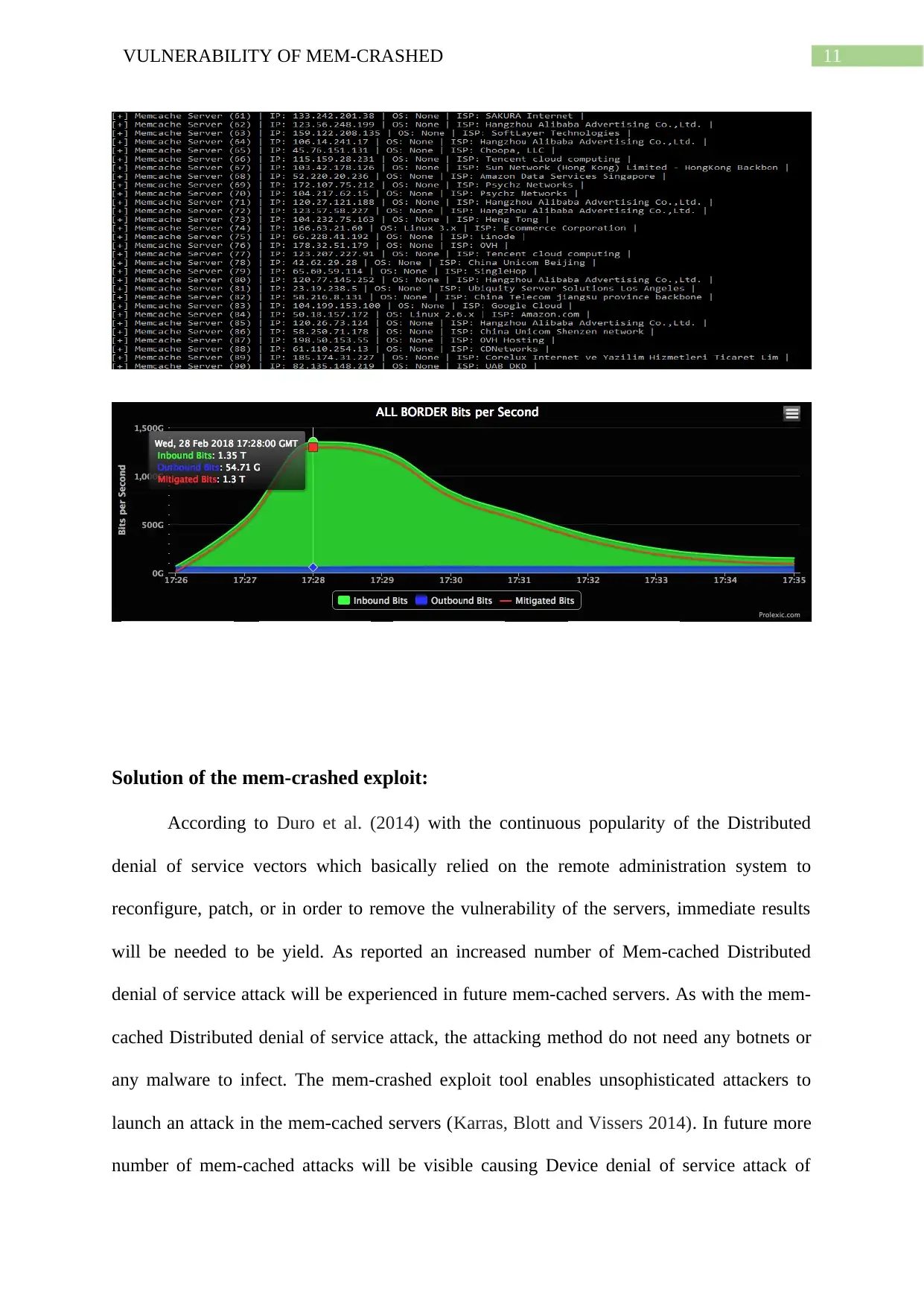
Solution of the mem-crashed exploit:
According to Duro et al. (2014) with the continuous popularity of the Distributed
denial of service vectors which basically relied on the remote administration system to
reconfigure, patch, or in order to remove the vulnerability of the servers, immediate results
will be needed to be yield. As reported an increased number of Mem-cached Distributed
denial of service attack will be experienced in future mem-cached servers. As with the mem-
cached Distributed denial of service attack, the attacking method do not need any botnets or
any malware to infect. The mem-crashed exploit tool enables unsophisticated attackers to
launch an attack in the mem-cached servers (Karras, Blott and Vissers 2014). In future more
number of mem-cached attacks will be visible causing Device denial of service attack of
Solution of the mem-crashed exploit:
According to Duro et al. (2014) with the continuous popularity of the Distributed
denial of service vectors which basically relied on the remote administration system to
reconfigure, patch, or in order to remove the vulnerability of the servers, immediate results
will be needed to be yield. As reported an increased number of Mem-cached Distributed
denial of service attack will be experienced in future mem-cached servers. As with the mem-
cached Distributed denial of service attack, the attacking method do not need any botnets or
any malware to infect. The mem-crashed exploit tool enables unsophisticated attackers to
launch an attack in the mem-cached servers (Karras, Blott and Vissers 2014). In future more
number of mem-cached attacks will be visible causing Device denial of service attack of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




