CO4509 Computer Security: A Detailed System Security Evaluation Report
VerifiedAdded on 2023/06/11
|34
|4045
|114
Report
AI Summary
This report details a system security evaluation performed on a virtual machine image, as per the CO4509 Computer Security assignment. It outlines the investigation process, including tools and techniques used to discover vulnerabilities, such as password recovery methods and file access permissions. The report then discusses the security issues identified, their implications, and a proposal for securing the system, addressing each vulnerability found. It covers aspects like account security, file access permissions, data verification, encrypted storage, secure remote access using OpenSSH, software management, host integrity testing, system recovery, resource allocation controls, monitoring and audit features, firewall configuration, and application isolation. The proposal includes methods to limit user account resources, implement storage quotas, utilize monitoring and audit facilities, configure firewalls, and isolate applications to minimize potential damage. The report concludes with a comprehensive strategy to enhance the overall security posture of the system.
COMPUTER SCIENCE
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Introduction......................................................................................................................................3
Investigation....................................................................................................................................3
System Security Aspects............................................................................................................3
Password Recovery....................................................................................................................7
Implications.....................................................................................................................................9
Security Issues and Implications..............................................................................................9
Securing.........................................................................................................................................11
How to exploit and secure a problem?...................................................................................11
Conclusion.....................................................................................................................................32
References......................................................................................................................................33
2
Introduction......................................................................................................................................3
Investigation....................................................................................................................................3
System Security Aspects............................................................................................................3
Password Recovery....................................................................................................................7
Implications.....................................................................................................................................9
Security Issues and Implications..............................................................................................9
Securing.........................................................................................................................................11
How to exploit and secure a problem?...................................................................................11
Conclusion.....................................................................................................................................32
References......................................................................................................................................33
2

Introduction
This project refers to investigating the security of the system. The WidgetsInc Company
contracted the Benny Vandergast Inc. for developing a new web based store for them. Because,
the Benny Vandergast Inc. facilitated testing using the VMware virtual machine. So, the
WidgetsInc took decision of providing you a job, related to system security evaluation. In this
project, we will perform security evaluation on the provided virtual machine image. All this will
be investigated and analyzed in detail.
Investigation
System Security Aspects
Accounts for All users
All types of Linux system, have a root account. All the administrative functionalities can
be carried out directly in this account. But, other accounts are not having rights to access the
system. It represents that not all the user accounts are permissible to access the files and are able
to publish the network services. The users who have authorized can only access these files. To
access the root account, the user needs to be logged in with appropriate credentials. For our
convenience, the user account can be created for individuals or group of people. If a group of
people are assigned to do the same resource, then they are allowed to access the files
automatically (Stuartellis.name, 2018).
File Access Permissions
To access all types of directory and file system in the Linux based system, there are three
types of file access permissions based on the person who have accessed.
The special account accessibility for the owner.
The accessibility for the group.
Permission to access for all the other accounts.
The following permissions will be applied on the files.
They can read.
They can write.
3
This project refers to investigating the security of the system. The WidgetsInc Company
contracted the Benny Vandergast Inc. for developing a new web based store for them. Because,
the Benny Vandergast Inc. facilitated testing using the VMware virtual machine. So, the
WidgetsInc took decision of providing you a job, related to system security evaluation. In this
project, we will perform security evaluation on the provided virtual machine image. All this will
be investigated and analyzed in detail.
Investigation
System Security Aspects
Accounts for All users
All types of Linux system, have a root account. All the administrative functionalities can
be carried out directly in this account. But, other accounts are not having rights to access the
system. It represents that not all the user accounts are permissible to access the files and are able
to publish the network services. The users who have authorized can only access these files. To
access the root account, the user needs to be logged in with appropriate credentials. For our
convenience, the user account can be created for individuals or group of people. If a group of
people are assigned to do the same resource, then they are allowed to access the files
automatically (Stuartellis.name, 2018).
File Access Permissions
To access all types of directory and file system in the Linux based system, there are three
types of file access permissions based on the person who have accessed.
The special account accessibility for the owner.
The accessibility for the group.
Permission to access for all the other accounts.
The following permissions will be applied on the files.
They can read.
They can write.
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

They can execute the file.
The user can only run the program but they can't change the file content. The files in the
root account, can be accessed by all the authorized users.
Verification of Data
The checksum is created for a file or it is tested against the checksum by using the utility
of sha1sum. In Linux based system, to encrypt the files and signing the documents digitally,
GNU Privacy Guard (GnuPG) system is enabled. The files that we encrypted and signed digitally
are compatible with OpenPGP standard.
As the evolution of email application, it supports both encryption technique and digital
signing process along with GnuPG.
If we want to apply the GnuPG features in GNOME PC environment, we need to do
installation process by the standardized software management tool.
Encrypted storage process
We can protect our sensitive files in a deeper encrypted way. We can enclose the
encrypted data in another directory, wherever required. The decryption password is essential to
access the encrypted file. If the user enters valid password, then they can manage the file
otherwise it could not be accessed.
To access the encrypted files in all the operating systems, we need to work with cross
platform. Sometimes, an entire part of the disk partition need to be encrypted when it caches the
data. In such case, the contents can be accessed by the unauthorized users.
Secured remote access along with OpenSSH
Generally, the Linux based system has the OpenSSH version. SSH standard is
implemented to provide a secured remote access. In default, SSH has a strong encryption and it
gives the following features:
Providing accessibility for command execution.
Providing File transfer.
Providing remote accessibility for graphical software.
4
The user can only run the program but they can't change the file content. The files in the
root account, can be accessed by all the authorized users.
Verification of Data
The checksum is created for a file or it is tested against the checksum by using the utility
of sha1sum. In Linux based system, to encrypt the files and signing the documents digitally,
GNU Privacy Guard (GnuPG) system is enabled. The files that we encrypted and signed digitally
are compatible with OpenPGP standard.
As the evolution of email application, it supports both encryption technique and digital
signing process along with GnuPG.
If we want to apply the GnuPG features in GNOME PC environment, we need to do
installation process by the standardized software management tool.
Encrypted storage process
We can protect our sensitive files in a deeper encrypted way. We can enclose the
encrypted data in another directory, wherever required. The decryption password is essential to
access the encrypted file. If the user enters valid password, then they can manage the file
otherwise it could not be accessed.
To access the encrypted files in all the operating systems, we need to work with cross
platform. Sometimes, an entire part of the disk partition need to be encrypted when it caches the
data. In such case, the contents can be accessed by the unauthorized users.
Secured remote access along with OpenSSH
Generally, the Linux based system has the OpenSSH version. SSH standard is
implemented to provide a secured remote access. In default, SSH has a strong encryption and it
gives the following features:
Providing accessibility for command execution.
Providing File transfer.
Providing remote accessibility for graphical software.
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Providing accessibility through command line.
The SSH helps the user to access the tunnel connection to some other services by SSH.
This tunneling service provides various benefits such as security and data compression options as
in-built functionalities of SSH. This feature provides protection option for the entire
communication among Linux systems as the traffic passes through pubic network.
Software Management
Most of the Linux environment distribution has the facility to manage the software
according to the package files. Because, it has a set of pre-defined websites and it is known as
channels. The software management facility helps to build and update working copies of the
package to execute other tasks that are required by the software package. This software package
management tool helps to determine the installed software that is outdated on the system. It
represents that the supported software in system could not be affected in the repositories.
Testing the host integrity
The execution of the system will be verified by its integrity and all the host integrity will
be tested by the checksum process. So that, the FreeBSD and Solaris distributions has these
integrity testing usages and the integrity monitoring system of cross platform like Osiris and
Samhain. These two centralized supporting system auditing processes handles many systems.
The system configuration process will be varied with the integrity tester to exclude
specific files and directories, which need to be modified in the system before they are generating
the initial checksum database of the system. It compares the obtained checksum of files in the
database and report.
System Recovery
User can easily restore the software program files which is added along with the
distribution of software management tools. The user even contains the access to the copies of log
files, configuration as well as data. These aspects need separate back up mechanism. The backup
system is used to providing the capacity of restoring the versions of the user files from several
earlier facts. It discovers that, the current system has compromised, then it can get damaged any
5
The SSH helps the user to access the tunnel connection to some other services by SSH.
This tunneling service provides various benefits such as security and data compression options as
in-built functionalities of SSH. This feature provides protection option for the entire
communication among Linux systems as the traffic passes through pubic network.
Software Management
Most of the Linux environment distribution has the facility to manage the software
according to the package files. Because, it has a set of pre-defined websites and it is known as
channels. The software management facility helps to build and update working copies of the
package to execute other tasks that are required by the software package. This software package
management tool helps to determine the installed software that is outdated on the system. It
represents that the supported software in system could not be affected in the repositories.
Testing the host integrity
The execution of the system will be verified by its integrity and all the host integrity will
be tested by the checksum process. So that, the FreeBSD and Solaris distributions has these
integrity testing usages and the integrity monitoring system of cross platform like Osiris and
Samhain. These two centralized supporting system auditing processes handles many systems.
The system configuration process will be varied with the integrity tester to exclude
specific files and directories, which need to be modified in the system before they are generating
the initial checksum database of the system. It compares the obtained checksum of files in the
database and report.
System Recovery
User can easily restore the software program files which is added along with the
distribution of software management tools. The user even contains the access to the copies of log
files, configuration as well as data. These aspects need separate back up mechanism. The backup
system is used to providing the capacity of restoring the versions of the user files from several
earlier facts. It discovers that, the current system has compromised, then it can get damaged any
5

time and it needs reverting to the previous version of the key files. Hence, it should not be
considered as an adequate backup. It provides the wide range of backup tools and gives a
suitable backup arrangement for their systems (Stuartellis.name, 2018).
Resource Allocation Controls
To limit the user account and user application resources, configure various mechanisms.
Because, the system has multiple users and they enforces with the resource limitation for making
sure that there must not be any deliberate and accidental reason which could fail the facilities,
when the available resources are used by the user. It enables storage quota on each partition,
because the quotas are used to prevent the users from the backup facilities and from storage
overloading.
Monitoring and audit features
In Linux, the klogd and syslog services are record activities and they are reported
according to various system parts. Linux kernel basically reports to klogd, whereas system
facilities and other services send log messages to the syslog service. Read and analyze the system
log files by using several tools provided by the distributions. The monitoring and audit facilities
also provide the central logging facility for the user network by configuring the syslog services
on the other system to forward the information that they receive to the syslog services, on the log
host. It maintains the record of all the processes that are run on that system (Stuartellis.name,
2018).
The Firewall of the System
In Linux system, netfilter framework is installed in its kernel to provide restriction for
both incoming and outgoing connection in network. This is based on the rules defined by the
system administrator. In most of the Linux system, the firewall rules are set as default. Some of
the simple firewall configurations are set into the simple firewall configuration. So that, we can
manage the rules of firewall in any Linux System along with appropriate command line utilities.
These Linux distributions help the user to utilize the blocked connections from other systems and
services. So that, the port is managed from irrelevant port.
6
considered as an adequate backup. It provides the wide range of backup tools and gives a
suitable backup arrangement for their systems (Stuartellis.name, 2018).
Resource Allocation Controls
To limit the user account and user application resources, configure various mechanisms.
Because, the system has multiple users and they enforces with the resource limitation for making
sure that there must not be any deliberate and accidental reason which could fail the facilities,
when the available resources are used by the user. It enables storage quota on each partition,
because the quotas are used to prevent the users from the backup facilities and from storage
overloading.
Monitoring and audit features
In Linux, the klogd and syslog services are record activities and they are reported
according to various system parts. Linux kernel basically reports to klogd, whereas system
facilities and other services send log messages to the syslog service. Read and analyze the system
log files by using several tools provided by the distributions. The monitoring and audit facilities
also provide the central logging facility for the user network by configuring the syslog services
on the other system to forward the information that they receive to the syslog services, on the log
host. It maintains the record of all the processes that are run on that system (Stuartellis.name,
2018).
The Firewall of the System
In Linux system, netfilter framework is installed in its kernel to provide restriction for
both incoming and outgoing connection in network. This is based on the rules defined by the
system administrator. In most of the Linux system, the firewall rules are set as default. Some of
the simple firewall configurations are set into the simple firewall configuration. So that, we can
manage the rules of firewall in any Linux System along with appropriate command line utilities.
These Linux distributions help the user to utilize the blocked connections from other systems and
services. So that, the port is managed from irrelevant port.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Isolating the Application
The Linux based system environment provides various methodologies to reduce the
capability of system program to damage both host systems as well as the running program itself.
MAC (Mandatory Access Control) provides the usual security features of LINUX and it limits to
any type of account and program.
Virtualization process helps assigning the hardware resources’ limited set, in the virtual
machine. It will be monitored and the data can be backed up by the host system's separate
process,
Linux container which helps to generate the new file system and separates this from an usual
host system process.
The chroot utility runs the software programs along with the particular working directory
and it helps to prevent the file directory from some other infected file directories.
Password Recovery
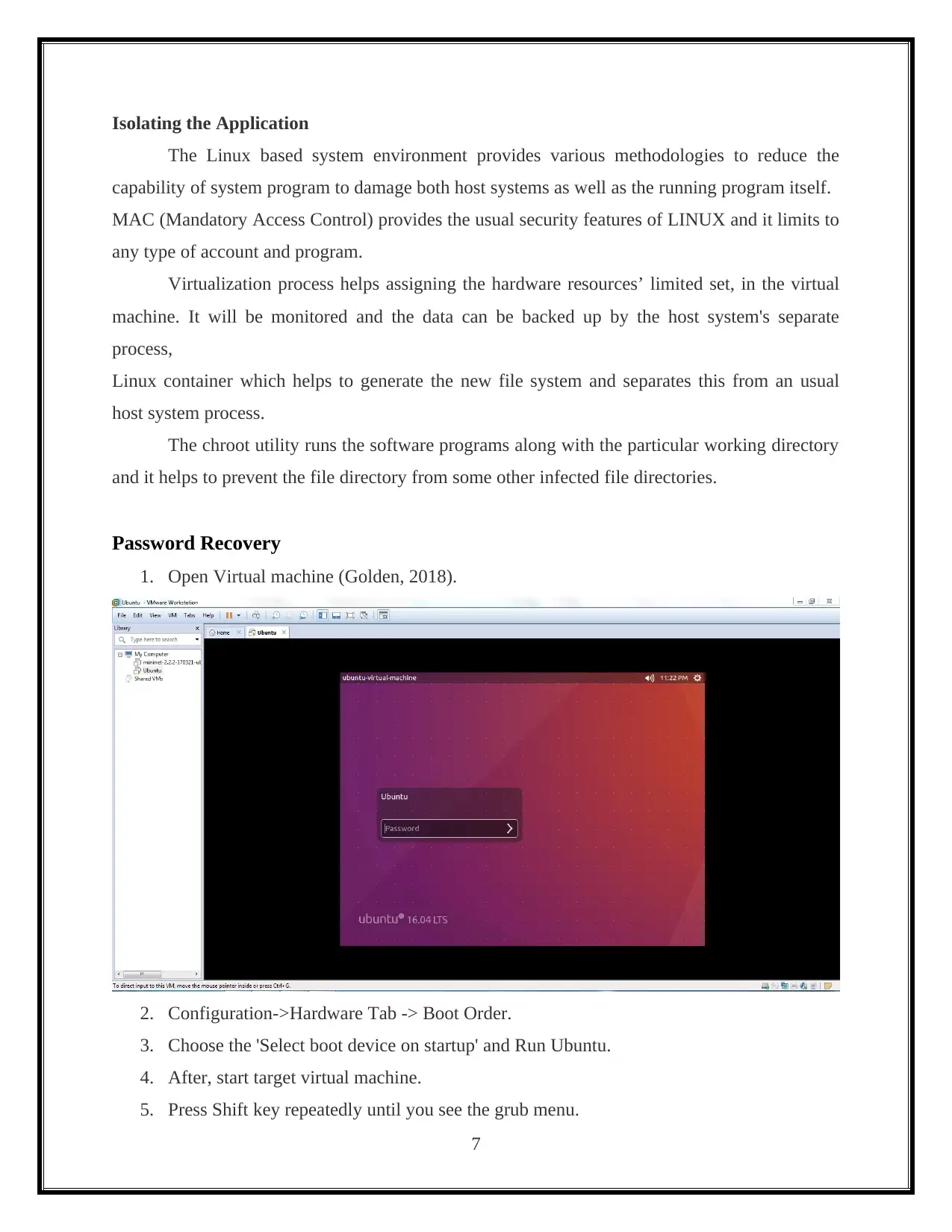
1. Open Virtual machine (Golden, 2018).
2. Configuration->Hardware Tab -> Boot Order.
3. Choose the 'Select boot device on startup' and Run Ubuntu.
4. After, start target virtual machine.
5. Press Shift key repeatedly until you see the grub menu.
7
The Linux based system environment provides various methodologies to reduce the
capability of system program to damage both host systems as well as the running program itself.
MAC (Mandatory Access Control) provides the usual security features of LINUX and it limits to
any type of account and program.
Virtualization process helps assigning the hardware resources’ limited set, in the virtual
machine. It will be monitored and the data can be backed up by the host system's separate
process,
Linux container which helps to generate the new file system and separates this from an usual
host system process.
The chroot utility runs the software programs along with the particular working directory
and it helps to prevent the file directory from some other infected file directories.
Password Recovery
1. Open Virtual machine (Golden, 2018).
2. Configuration->Hardware Tab -> Boot Order.
3. Choose the 'Select boot device on startup' and Run Ubuntu.
4. After, start target virtual machine.
5. Press Shift key repeatedly until you see the grub menu.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
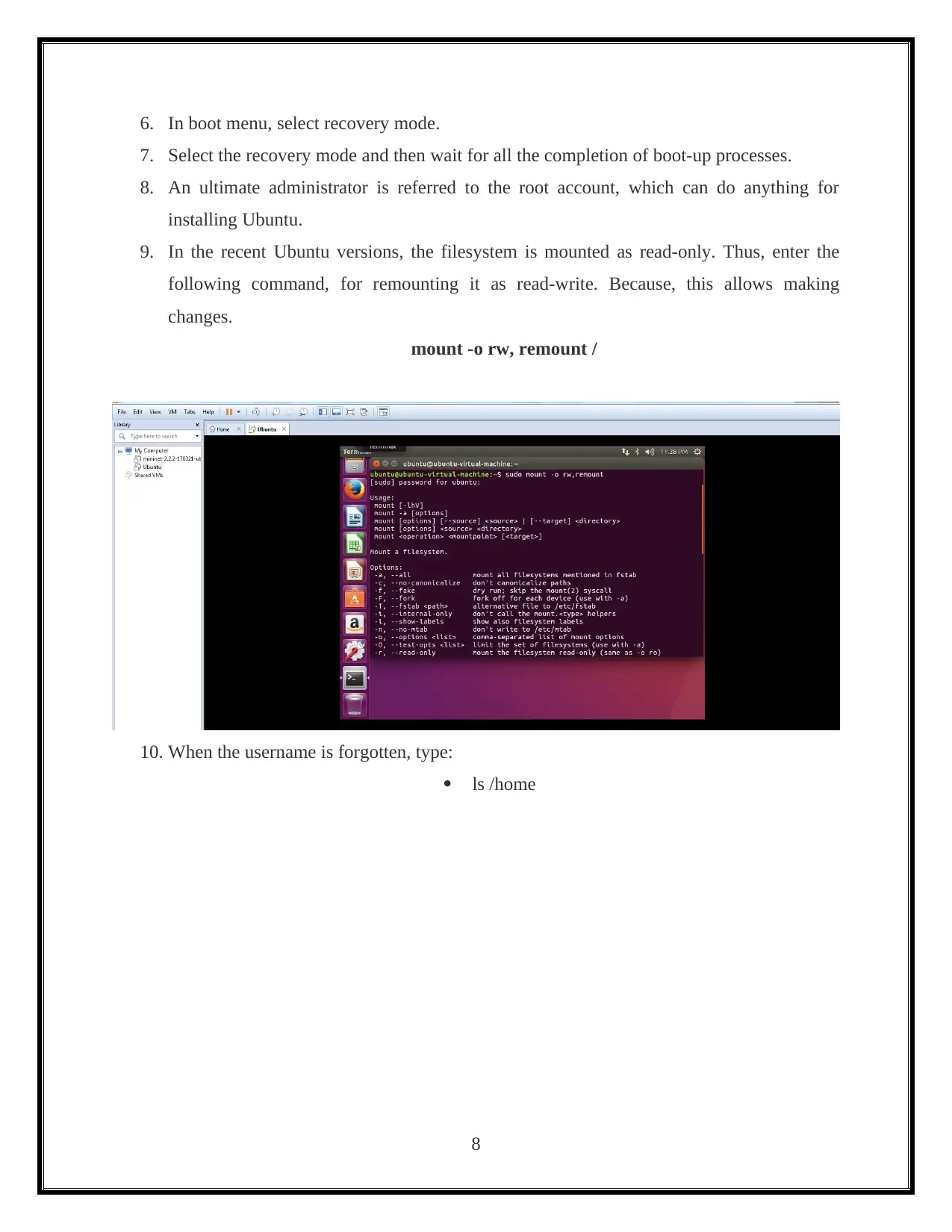
6. In boot menu, select recovery mode.
7. Select the recovery mode and then wait for all the completion of boot-up processes.
8. An ultimate administrator is referred to the root account, which can do anything for
installing Ubuntu.
9. In the recent Ubuntu versions, the filesystem is mounted as read-only. Thus, enter the
following command, for remounting it as read-write. Because, this allows making
changes.
mount -o rw, remount /
10. When the username is forgotten, type:
ls /home
8
7. Select the recovery mode and then wait for all the completion of boot-up processes.
8. An ultimate administrator is referred to the root account, which can do anything for
installing Ubuntu.
9. In the recent Ubuntu versions, the filesystem is mounted as read-only. Thus, enter the
following command, for remounting it as read-write. Because, this allows making
changes.
mount -o rw, remount /
10. When the username is forgotten, type:
ls /home
8
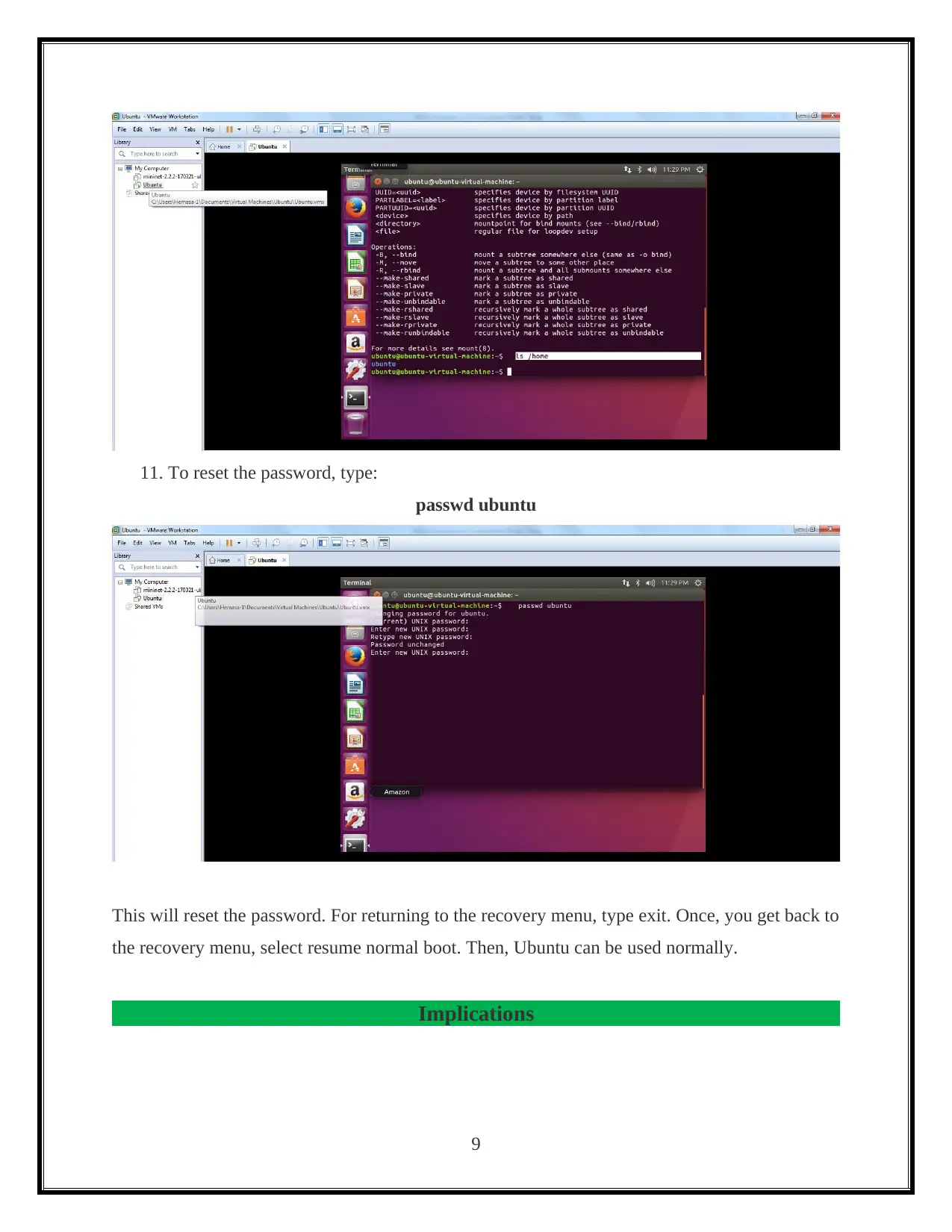
11. To reset the password, type:
passwd ubuntu
This will reset the password. For returning to the recovery menu, type exit. Once, you get back to
the recovery menu, select resume normal boot. Then, Ubuntu can be used normally.
Implications
9
passwd ubuntu
This will reset the password. For returning to the recovery menu, type exit. Once, you get back to
the recovery menu, select resume normal boot. Then, Ubuntu can be used normally.
Implications
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Security Issues and Implications
By dismissing the dependence of working frameworks on a framework's physical state,
framework virtualization enables numerous working frameworks to be introduced on a VMM,
and in this way different working framework VMs can be introduced on each physical
framework. Permitting various VMs on a similar equipment offers numerous points of interest.
Near-complete isolation between visitor working frameworks on a similar equipment ensures
against OSs being a self-contained purpose of dissatisfaction. It likewise permits OS
combination from various machines as it is important to reduce framework underutilization and
keep up effectiveness of task. This conversation from the equipment state permits not just
numerous working frameworks to exist together on a similar equipment, yet for one VMM to
keep running on various diverse organized physical frameworks simultaneously. By using a
VMM to interfere between the OS and the equipment, virtualization changes the coordinated
mapping of OSs to equipment to, many-to-many (Guthrie and Lowe, 2013).
Although some open frameworks actualize this model just freely, as a VM does not, as a
rule keep running on different frameworks simultaneously, permitting one VMM to be moved
over numerous physical frameworks perfectly while running has enhanced the contributions for
elite and high-accessibility frameworks and distributed computing. Additionally for the
commoditization of handling power. While we center in this article around framework
virtualization, there are numerous other virtualization advances that cover with what we talk
about, for example, storing virtualization and system virtualization.
The properties of virtualization are not only favorable for the security, they can be
unfavorable. Because, virtualization is huge and extremely a dynamic research field, with new
research and threats turning out daily, any scope can never be comprehensive. As expressed in
the Introduction, this work is expected as an introduction for the concerns of security,
contemplations, and for coming up with suggestions, by using the virtualized frameworks. Thus,
such a work proposes a general scope of security related problems, which contain virtualization.
We are worried about threats that influences the accompanying operators like, VMM, VMs, OSs
in VMs, programming running on OSs, and are in operational condition. For instance, system.
Since we are attempted an extremely broad approach, there are circumstances where a particular
illustration will be secured quickly. For more data we need per user to suggest to the suitable
references. Security, with regards to this work, refers the revelation and modification of
10
By dismissing the dependence of working frameworks on a framework's physical state,
framework virtualization enables numerous working frameworks to be introduced on a VMM,
and in this way different working framework VMs can be introduced on each physical
framework. Permitting various VMs on a similar equipment offers numerous points of interest.
Near-complete isolation between visitor working frameworks on a similar equipment ensures
against OSs being a self-contained purpose of dissatisfaction. It likewise permits OS
combination from various machines as it is important to reduce framework underutilization and
keep up effectiveness of task. This conversation from the equipment state permits not just
numerous working frameworks to exist together on a similar equipment, yet for one VMM to
keep running on various diverse organized physical frameworks simultaneously. By using a
VMM to interfere between the OS and the equipment, virtualization changes the coordinated
mapping of OSs to equipment to, many-to-many (Guthrie and Lowe, 2013).
Although some open frameworks actualize this model just freely, as a VM does not, as a
rule keep running on different frameworks simultaneously, permitting one VMM to be moved
over numerous physical frameworks perfectly while running has enhanced the contributions for
elite and high-accessibility frameworks and distributed computing. Additionally for the
commoditization of handling power. While we center in this article around framework
virtualization, there are numerous other virtualization advances that cover with what we talk
about, for example, storing virtualization and system virtualization.
The properties of virtualization are not only favorable for the security, they can be
unfavorable. Because, virtualization is huge and extremely a dynamic research field, with new
research and threats turning out daily, any scope can never be comprehensive. As expressed in
the Introduction, this work is expected as an introduction for the concerns of security,
contemplations, and for coming up with suggestions, by using the virtualized frameworks. Thus,
such a work proposes a general scope of security related problems, which contain virtualization.
We are worried about threats that influences the accompanying operators like, VMM, VMs, OSs
in VMs, programming running on OSs, and are in operational condition. For instance, system.
Since we are attempted an extremely broad approach, there are circumstances where a particular
illustration will be secured quickly. For more data we need per user to suggest to the suitable
references. Security, with regards to this work, refers the revelation and modification of
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

information and tasks that might be viewed as touchy. Associated threats includes, two ruptures
of expected benefit and breaks of different controls which are allowed frequently and certainly. It
might be connected on a case-by-case premise, for suiting the situation.
To begin with virtualization, it includes extra layers of framework complexity. This refers
to checking for the extraordinary events and oddities which similarly turns out to be more
difficult when compared to the current situation, for recognizing the security related problems.
For instance, advanced constant risks.
Next, by configuration the virtualized situations are dynamic, which instantly changes
every time. In few minutes, not all the physical situations, can the virtual machines be turned up.
It can be anything but hard to forget what is on the web, disconnected and subsequently what
potential security openings are uncovered. This is recognized based on a phenomenon called
virtual extension. It refers to when the quantity of virtual machines present inside a situation
achieves a point where they can never again be overseen, adequately. For instance, making all
the security fixes connected correctly. In similar situation, the security of all the virtual machine
can never be ensured again. The attackers have used the disconnected virtual machines as a
portal, for accessing the framework of an organization, as it is guaranteed in the Browser Stack
break.
At last, although the dynamic idea of virtual machines and workloads can be instantly
moved. This represents a security hazard. For instance, a specific workload may require an
abnormal state of security, and the underlying virtual machine the workload is allocated to give
that security. Yet, when looked with the preparation need for more mission-basic workloads,
without setting up appropriate governing rules, it could be moved undoubtedly to the other
virtual machine, by bringing down the level of security, where a potential gap is opened.
Securing
How to exploit and secure a problem?
To secure a virtual machine by using the osquery. The osquery refers to an open source
security tool to provide secure operating system and it transforms as a giant database, which
contains tables that you can query, with the help of SQL-like statements. This tool is used to
monitor the system security including monitoring the file integrity, checking on the status,
11
of expected benefit and breaks of different controls which are allowed frequently and certainly. It
might be connected on a case-by-case premise, for suiting the situation.
To begin with virtualization, it includes extra layers of framework complexity. This refers
to checking for the extraordinary events and oddities which similarly turns out to be more
difficult when compared to the current situation, for recognizing the security related problems.
For instance, advanced constant risks.
Next, by configuration the virtualized situations are dynamic, which instantly changes
every time. In few minutes, not all the physical situations, can the virtual machines be turned up.
It can be anything but hard to forget what is on the web, disconnected and subsequently what
potential security openings are uncovered. This is recognized based on a phenomenon called
virtual extension. It refers to when the quantity of virtual machines present inside a situation
achieves a point where they can never again be overseen, adequately. For instance, making all
the security fixes connected correctly. In similar situation, the security of all the virtual machine
can never be ensured again. The attackers have used the disconnected virtual machines as a
portal, for accessing the framework of an organization, as it is guaranteed in the Browser Stack
break.
At last, although the dynamic idea of virtual machines and workloads can be instantly
moved. This represents a security hazard. For instance, a specific workload may require an
abnormal state of security, and the underlying virtual machine the workload is allocated to give
that security. Yet, when looked with the preparation need for more mission-basic workloads,
without setting up appropriate governing rules, it could be moved undoubtedly to the other
virtual machine, by bringing down the level of security, where a potential gap is opened.
Securing
How to exploit and secure a problem?
To secure a virtual machine by using the osquery. The osquery refers to an open source
security tool to provide secure operating system and it transforms as a giant database, which
contains tables that you can query, with the help of SQL-like statements. This tool is used to
monitor the system security including monitoring the file integrity, checking on the status,
11
performing security audits of the target server and firewall configuration. The osquery is a cross
platform application supporting various operating systems. It is described as SQL powered
operating system analytics, instrumentation and monitoring framework. The osquery has three
components like, osqueryi, osqueryd and osqueryctl. The osqueryi is used to interact with the
osquery shell for performing the ad hoc queries. The osqueryd is daemon for running and
scheduling the queries in the background. The osqueryctl is a helper script for testing osquery
configuration and deployment (Digitalocean.com, 2018). It is also used instead of operating
system service manager to start, stop and restart the osqueryd. These components are
independent tools. So, these do not communicate with others.
Osquery Installation
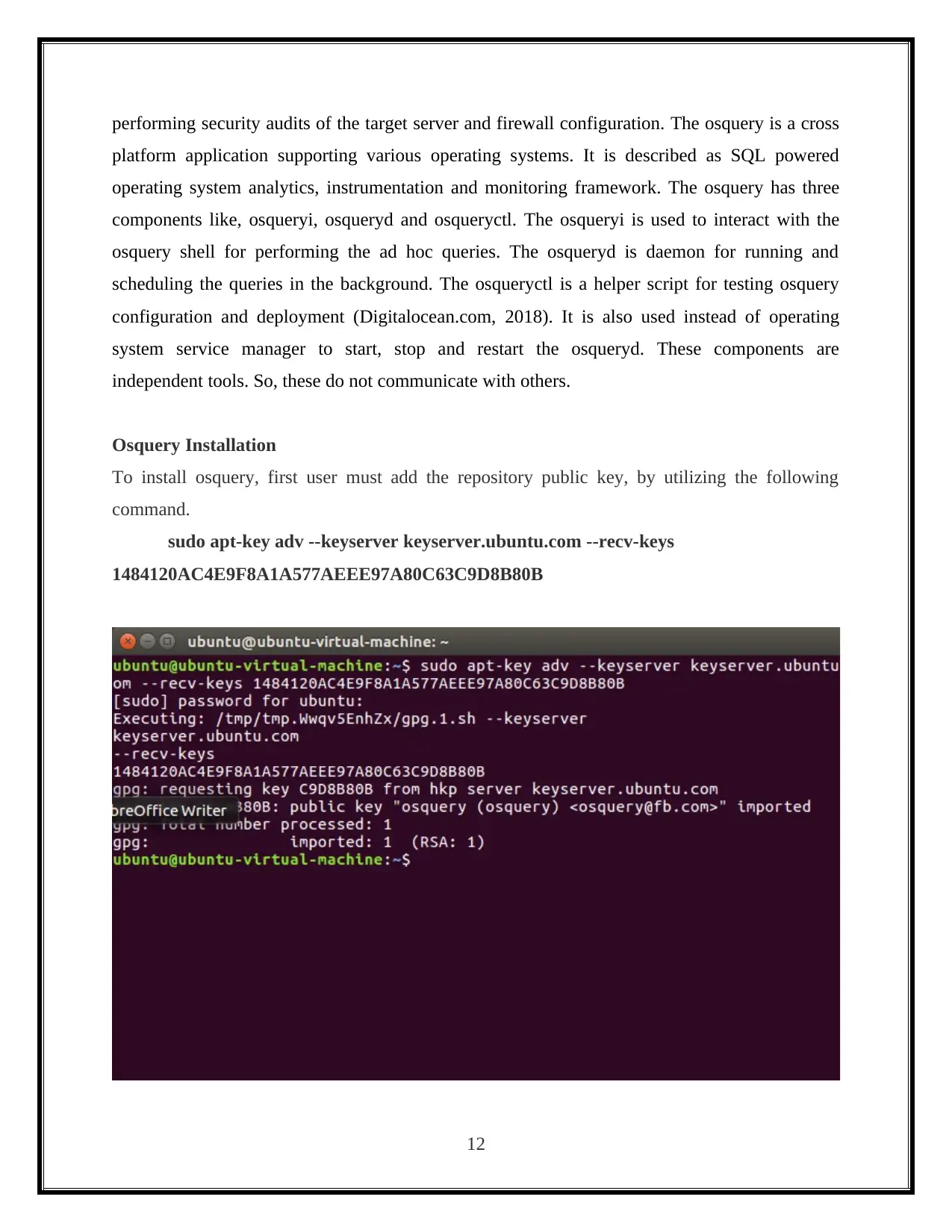
To install osquery, first user must add the repository public key, by utilizing the following
command.
sudo apt-key adv --keyserver keyserver.ubuntu.com --recv-keys
1484120AC4E9F8A1A577AEEE97A80C63C9D8B80B
12
platform application supporting various operating systems. It is described as SQL powered
operating system analytics, instrumentation and monitoring framework. The osquery has three
components like, osqueryi, osqueryd and osqueryctl. The osqueryi is used to interact with the
osquery shell for performing the ad hoc queries. The osqueryd is daemon for running and
scheduling the queries in the background. The osqueryctl is a helper script for testing osquery
configuration and deployment (Digitalocean.com, 2018). It is also used instead of operating
system service manager to start, stop and restart the osqueryd. These components are
independent tools. So, these do not communicate with others.
Osquery Installation
To install osquery, first user must add the repository public key, by utilizing the following
command.
sudo apt-key adv --keyserver keyserver.ubuntu.com --recv-keys
1484120AC4E9F8A1A577AEEE97A80C63C9D8B80B
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 34
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





