CO4512 Information Security Management: Cloud Risk Assessment
VerifiedAdded on 2023/06/12
|19
|3285
|104
Report
AI Summary
This report provides a comprehensive risk assessment of a cloud architecture, following the ISO 27001 framework. It identifies primary and secondary assets, along with potential threats such as third-party vulnerabilities, cybernetic server weaknesses, firewall limitations, intranet vulnerabilities, and firmware exploits. Vulnerabilities are analyzed using CVE references, and risk levels are computed using the Boston Grid. The report details the impact of each risk and provides a structured overview of potential security issues within the cloud infrastructure. This document is available on Desklib, a platform offering a wide range of study resources including past papers and solved assignments.

Running head: CLOUD ARCHITECTURE RISK ASSESSMENT
Cloud Architecture Risk
Name of the student
Name of the university
Author note
Cloud Architecture Risk
Name of the student
Name of the university
Author note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1CLOUD ARCHITECTURE RISK ASSESSMENT
Executive summary
The structure of the construction of cloud computing enrols the aspects that uses the
technology to utilize assets for the creation of the data base that acts to be the major source of
security issue for the cloud computing infrastructure. The aspect that the security of the cloud
competing system is acting as the asset oriented server domain for securing the cloud computing
database the database that are used for storing the data in the cloud computing of the
organization. the assets are divided in 2 categories that is the primary data and the secondary
data. The primary data is the main asset that uses the fact that the architecture of the cloud
computing fixes the fact that the secondary asset in the process. The architecture of the
secondary assets are set with the help of the primary data. This aspect ensures the fact that the
secondary assets are dependent n the primary assets in the higher priority over the secondary
assets ain case f tracking the database of the cloud com putting system. In case of the cloud
computing software acts as the primary asset of the cloud computing infrastructural framework.
In the conduction process, that is lead by the ISO 27001. ISO 27001 has been caring as the most
standardized cloud-computing framework of the organization. The major benefit of this system is
that the ISO 27001 can help in recognizing the data that is related to the threats of the cloud
computing system. This aspect that the ISO 27001 can be constructed due to the constitution if
the safeguarding are data base of the cloud computing system. This factor enables the aspect that
the security of the database is prevailed and the risks that are detected are prevented by taking
useful measures against the threats. The usage of the international standard security system
helps the cloud computing database updated with the fact that the robustness of the database is
maintained and during the process of the methodology of the checking the robustness of the
database provides support to the organization that has been using the data base of the
Executive summary
The structure of the construction of cloud computing enrols the aspects that uses the
technology to utilize assets for the creation of the data base that acts to be the major source of
security issue for the cloud computing infrastructure. The aspect that the security of the cloud
competing system is acting as the asset oriented server domain for securing the cloud computing
database the database that are used for storing the data in the cloud computing of the
organization. the assets are divided in 2 categories that is the primary data and the secondary
data. The primary data is the main asset that uses the fact that the architecture of the cloud
computing fixes the fact that the secondary asset in the process. The architecture of the
secondary assets are set with the help of the primary data. This aspect ensures the fact that the
secondary assets are dependent n the primary assets in the higher priority over the secondary
assets ain case f tracking the database of the cloud com putting system. In case of the cloud
computing software acts as the primary asset of the cloud computing infrastructural framework.
In the conduction process, that is lead by the ISO 27001. ISO 27001 has been caring as the most
standardized cloud-computing framework of the organization. The major benefit of this system is
that the ISO 27001 can help in recognizing the data that is related to the threats of the cloud
computing system. This aspect that the ISO 27001 can be constructed due to the constitution if
the safeguarding are data base of the cloud computing system. This factor enables the aspect that
the security of the database is prevailed and the risks that are detected are prevented by taking
useful measures against the threats. The usage of the international standard security system
helps the cloud computing database updated with the fact that the robustness of the database is
maintained and during the process of the methodology of the checking the robustness of the
database provides support to the organization that has been using the data base of the

2CLOUD ARCHITECTURE RISK ASSESSMENT
organization. Another fact that the organization that has been using the international cloud
computing security stature then the good will of the clients also increases as been acting as the
major reason for the supplementing of the security.
organization. Another fact that the organization that has been using the international cloud
computing security stature then the good will of the clients also increases as been acting as the
major reason for the supplementing of the security.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3CLOUD ARCHITECTURE RISK ASSESSMENT
Table of Contents
Introduction:....................................................................................................................................5
Type of assets:.............................................................................................................................6
Owner specification:....................................................................................................................6
Threats for each asset:.................................................................................................................7
Threats with cloud storage:......................................................................................................7
Threats with cybernetic servers:......................................................................................................7
Threats with firewall:...............................................................................................................8
Threats with the intranet:.............................................................................................................8
Threats with web and mail servers:.........................................................................................8
Threats with the firmware and the admin and user pc:............................................................9
The firmware does have the option for the encryption process and is one of the easily hack
able thing. IT is possible for the hackers to easily penetrate to the internal hardware’s by
breaking the security of the firmware. The admin as well as the network comes to danger
because of this.(Singh, Jeong and Park 2016) ........................................................................9
Vulnerabilities for each asset:......................................................................................................9
Level computation, using Boston gird:......................................................................................11
Impact table specification:.........................................................................................................12
Risk credentials with the risk level, by Boston grid:.................................................................13
Reference.......................................................................................................................................14
Table of Contents
Introduction:....................................................................................................................................5
Type of assets:.............................................................................................................................6
Owner specification:....................................................................................................................6
Threats for each asset:.................................................................................................................7
Threats with cloud storage:......................................................................................................7
Threats with cybernetic servers:......................................................................................................7
Threats with firewall:...............................................................................................................8
Threats with the intranet:.............................................................................................................8
Threats with web and mail servers:.........................................................................................8
Threats with the firmware and the admin and user pc:............................................................9
The firmware does have the option for the encryption process and is one of the easily hack
able thing. IT is possible for the hackers to easily penetrate to the internal hardware’s by
breaking the security of the firmware. The admin as well as the network comes to danger
because of this.(Singh, Jeong and Park 2016) ........................................................................9
Vulnerabilities for each asset:......................................................................................................9
Level computation, using Boston gird:......................................................................................11
Impact table specification:.........................................................................................................12
Risk credentials with the risk level, by Boston grid:.................................................................13
Reference.......................................................................................................................................14
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4CLOUD ARCHITECTURE RISK ASSESSMENT

5CLOUD ARCHITECTURE RISK ASSESSMENT
Introduction:
After the identification of the risk in the architecture of the cloud the functioning of the
ISO 27001 performs computing. This report includes the factor that the architecture of the cloud
computing with the help of the infrastructural efficiency that causes the fact of the data being
protected from the threat that are approaching the data regarding the fat of the security. The
standard methodology also acts as the major reason of the robustness of the database of the
architecture of the cloud computing system. The efficiency of the architecture of the database of
the system causes the fact that database of the cloud computing has been acting as the major
reason for the analysis of the threats in the processing of the risk management of the architecture
of the cloud computing system. The cloud computing system architecture has been facing severe
threats of the imposters who deal with the fact of hacking the architecture of the cloud computing
of the organization. This fact ensures the terminology that are related to the robustness of the
architecture of the cloud computing of the database. The CVE of the infrastructure of the
framework ensures the fact that the cloud computing of the organization ensures that the data
stays protected from the threats that are approaching towards the organization. Another aspect of
detecting the threat with eth help of the ISO 27001 has been acting as the best process of
protecting the data that are stored in the framework of the cloud computing architecture. This
fact assures the methodology of the risk assessment factor of the cloud computing architecture.
Risk Analysis
Risk analysis of the architecture of the cloud computing system has been ac ting as the,
major reason that has been acting from the main reason for the processing of the risks that are
due to the fact of the cloud computing of the data base of the organization. This ensures the fact
Introduction:
After the identification of the risk in the architecture of the cloud the functioning of the
ISO 27001 performs computing. This report includes the factor that the architecture of the cloud
computing with the help of the infrastructural efficiency that causes the fact of the data being
protected from the threat that are approaching the data regarding the fat of the security. The
standard methodology also acts as the major reason of the robustness of the database of the
architecture of the cloud computing system. The efficiency of the architecture of the database of
the system causes the fact that database of the cloud computing has been acting as the major
reason for the analysis of the threats in the processing of the risk management of the architecture
of the cloud computing system. The cloud computing system architecture has been facing severe
threats of the imposters who deal with the fact of hacking the architecture of the cloud computing
of the organization. This fact ensures the terminology that are related to the robustness of the
architecture of the cloud computing of the database. The CVE of the infrastructure of the
framework ensures the fact that the cloud computing of the organization ensures that the data
stays protected from the threats that are approaching towards the organization. Another aspect of
detecting the threat with eth help of the ISO 27001 has been acting as the best process of
protecting the data that are stored in the framework of the cloud computing architecture. This
fact assures the methodology of the risk assessment factor of the cloud computing architecture.
Risk Analysis
Risk analysis of the architecture of the cloud computing system has been ac ting as the,
major reason that has been acting from the main reason for the processing of the risks that are
due to the fact of the cloud computing of the data base of the organization. This ensures the fact
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6CLOUD ARCHITECTURE RISK ASSESSMENT
that the updation of the model of the IISO 287001 has been acting as the main aspect for the
protection of the data that are present in the architecture of the data base. The database of the
cloud computing system of the organization ensures the fact that the data are safe from the
intruders only when the fact are ISO 27001 is updated to the latest version of the cloud
computing database system. This fact has been acting as the major source of support for the data
that are stored in the database of the architecture of the cloud computing structure of the
organization.
Type of assets:
The assets are differentiated in two integral parts namely the primary asset and the
secondary asset. The fact that the data system of the cloud computing system has been
differentiated as the asset that is primary in nature has been acting as a platform that is
supporting the infrastructure of the cloud computing system. In case of the usage of the
secondary asst the usage of the primary asset has been acting to the fact of the performance pf
teh secondary asset. The performance of the secondary assets are completely dependent on the
function in goof the primary assets. The fact proves that the efficiency of the secondary asset is
completely dependent on the structure of the architecture of the cloud computing of the
organization. the fact that the aspiration of the data that is stored in the architecture of the cloud
computing of the organization is aspired with the facts that the betterment of the security system
pf the architecture of the cloud computing system has been acting as the major reason for the
Owner specification:
that the updation of the model of the IISO 287001 has been acting as the main aspect for the
protection of the data that are present in the architecture of the data base. The database of the
cloud computing system of the organization ensures the fact that the data are safe from the
intruders only when the fact are ISO 27001 is updated to the latest version of the cloud
computing database system. This fact has been acting as the major source of support for the data
that are stored in the database of the architecture of the cloud computing structure of the
organization.
Type of assets:
The assets are differentiated in two integral parts namely the primary asset and the
secondary asset. The fact that the data system of the cloud computing system has been
differentiated as the asset that is primary in nature has been acting as a platform that is
supporting the infrastructure of the cloud computing system. In case of the usage of the
secondary asst the usage of the primary asset has been acting to the fact of the performance pf
teh secondary asset. The performance of the secondary assets are completely dependent on the
function in goof the primary assets. The fact proves that the efficiency of the secondary asset is
completely dependent on the structure of the architecture of the cloud computing of the
organization. the fact that the aspiration of the data that is stored in the architecture of the cloud
computing of the organization is aspired with the facts that the betterment of the security system
pf the architecture of the cloud computing system has been acting as the major reason for the
Owner specification:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7CLOUD ARCHITECTURE RISK ASSESSMENT
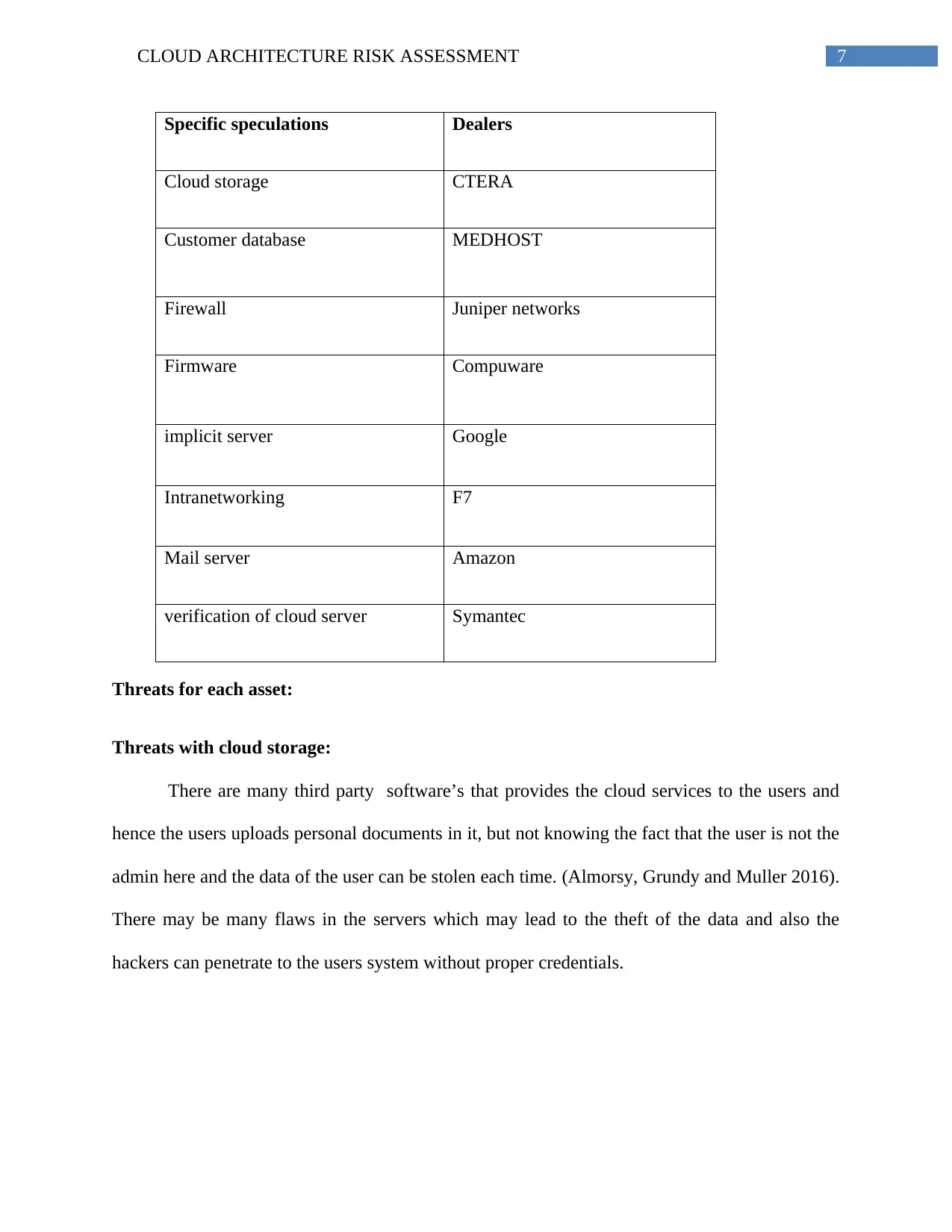
Specific speculations Dealers
Cloud storage CTERA
Customer database MEDHOST
Firewall Juniper networks
Firmware Compuware
implicit server Google
Intranetworking F7
Mail server Amazon
verification of cloud server Symantec
Threats for each asset:
Threats with cloud storage:
There are many third party software’s that provides the cloud services to the users and
hence the users uploads personal documents in it, but not knowing the fact that the user is not the
admin here and the data of the user can be stolen each time. (Almorsy, Grundy and Muller 2016).
There may be many flaws in the servers which may lead to the theft of the data and also the
hackers can penetrate to the users system without proper credentials.
Specific speculations Dealers
Cloud storage CTERA
Customer database MEDHOST
Firewall Juniper networks
Firmware Compuware
implicit server Google
Intranetworking F7
Mail server Amazon
verification of cloud server Symantec
Threats for each asset:
Threats with cloud storage:
There are many third party software’s that provides the cloud services to the users and
hence the users uploads personal documents in it, but not knowing the fact that the user is not the
admin here and the data of the user can be stolen each time. (Almorsy, Grundy and Muller 2016).
There may be many flaws in the servers which may lead to the theft of the data and also the
hackers can penetrate to the users system without proper credentials.

8CLOUD ARCHITECTURE RISK ASSESSMENT
Threats with cybernetic servers:
The cybernetic servers are the servers that stores massive amount of the data and requires
a very strong knowledge for the administration process. In case, of the administrator does not
have the proper knowledge of the administration can lead to devastating network faults. The
servers needs regular security patches otherwise can have a chance to become some of the basic
target of the hackers. (Jokar, Arianpoo and Leung 2016).
Threats with firewall:
Firewall protects the internal network from the external threats like malicious attacks
which are carried out with the help of the external internet. However, it is not appropriate for
defending the network from the threats that is due to the flaws in the internal security.
In case external communication like receiving emails from the outside sources is allowed
by the system, it is not possible for the firewall to prevent the communication by analyzing the
flaws and nature of the communication (Singh, Jeong and Park 2016).
Threats with the intranet:
The concept of the intranet is used for the purpose of the connection of the networks in a
particular institute or office. Due to this many people think that it is not possible for other outside
the network to access the intranet and uses weak or no passwords for saving the personal
security’s, and hence becomes some of the major targets of the hackers and the crackers. (Wang,
Wei and Vagary 2014).
Threats with web and mail servers:
There are too many flaws and vulnerability that the hacker may exploit that belongs to
the firewall used. Also it has one stop solutions for the protection of the web servers. IF the
Threats with cybernetic servers:
The cybernetic servers are the servers that stores massive amount of the data and requires
a very strong knowledge for the administration process. In case, of the administrator does not
have the proper knowledge of the administration can lead to devastating network faults. The
servers needs regular security patches otherwise can have a chance to become some of the basic
target of the hackers. (Jokar, Arianpoo and Leung 2016).
Threats with firewall:
Firewall protects the internal network from the external threats like malicious attacks
which are carried out with the help of the external internet. However, it is not appropriate for
defending the network from the threats that is due to the flaws in the internal security.
In case external communication like receiving emails from the outside sources is allowed
by the system, it is not possible for the firewall to prevent the communication by analyzing the
flaws and nature of the communication (Singh, Jeong and Park 2016).
Threats with the intranet:
The concept of the intranet is used for the purpose of the connection of the networks in a
particular institute or office. Due to this many people think that it is not possible for other outside
the network to access the intranet and uses weak or no passwords for saving the personal
security’s, and hence becomes some of the major targets of the hackers and the crackers. (Wang,
Wei and Vagary 2014).
Threats with web and mail servers:
There are too many flaws and vulnerability that the hacker may exploit that belongs to
the firewall used. Also it has one stop solutions for the protection of the web servers. IF the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9CLOUD ARCHITECTURE RISK ASSESSMENT
hacker gets into the web mails then can access the personal information of the users as well as
the data of the network. (Wang, Wei and Vangury 2014).
Threats with the firmware and the admin and user pc:
The firmware does have the option for the encryption process and is one of the easily
hack able thing. IT is possible for the hackers to easily penetrate to the internal hardware’s by
breaking the security of the firmware. The admin as well as the network comes to danger
because of this.(Singh, Jeong and Park 2016) .
Vulnerabilities for each asset:
CVE-2016-9245
The exposure is connected with the F5 BIG-IP systems. This platform uses the virtual
servers for the working procedures. IN this vulnerability all that the attackers needs to do is to
request HTTP profile for restarting the TMM of the servers. This can expose all the big-IP A Pm
profiles, despite of the HTTPS servers. This helps in disrupting the traffic and trough the
injection of malicious software’s (Cve.mitre.org 2018). The systems make the use of the hard
code that is implemented for accessing the databases. With the proper knowledge of the hard
codes it is possible for any hacker to directly access the databases without the admin checking
and change any file in the data base. The DMS account can be connected with the Postgre SQL
which enables the hackers to access to the database DMS.AS a result while the system flash
anyone can get into the systems and can effortlessly make alteration in the firmware settings. It is
very easy to be done also all the user needs is the Phoenix “UEFI update program”. This
malware is easily available in the internet and can be used by any one. With the help of this the
hacker can easily corrupt the system and make a DDOS attack on the servers.
hacker gets into the web mails then can access the personal information of the users as well as
the data of the network. (Wang, Wei and Vangury 2014).
Threats with the firmware and the admin and user pc:
The firmware does have the option for the encryption process and is one of the easily
hack able thing. IT is possible for the hackers to easily penetrate to the internal hardware’s by
breaking the security of the firmware. The admin as well as the network comes to danger
because of this.(Singh, Jeong and Park 2016) .
Vulnerabilities for each asset:
CVE-2016-9245
The exposure is connected with the F5 BIG-IP systems. This platform uses the virtual
servers for the working procedures. IN this vulnerability all that the attackers needs to do is to
request HTTP profile for restarting the TMM of the servers. This can expose all the big-IP A Pm
profiles, despite of the HTTPS servers. This helps in disrupting the traffic and trough the
injection of malicious software’s (Cve.mitre.org 2018). The systems make the use of the hard
code that is implemented for accessing the databases. With the proper knowledge of the hard
codes it is possible for any hacker to directly access the databases without the admin checking
and change any file in the data base. The DMS account can be connected with the Postgre SQL
which enables the hackers to access to the database DMS.AS a result while the system flash
anyone can get into the systems and can effortlessly make alteration in the firmware settings. It is
very easy to be done also all the user needs is the Phoenix “UEFI update program”. This
malware is easily available in the internet and can be used by any one. With the help of this the
hacker can easily corrupt the system and make a DDOS attack on the servers.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10CLOUD ARCHITECTURE RISK ASSESSMENT
CVE-2017-8514
This type of the exposure is linked through intranet network which is used for the
connections of the internal device. The Microsoft SharePoint is one of the major example of this.
One of the major issue that is associated with the MS SharePoint is, the security standards are not
robust adequately for protection of the network. Therefore it can be said that the privacy policy
of the data can be compromised hence the data can be accessed by the unauthorized users. One
of the major risk in this is the fact once the hackers are in the network can user the identity of the
user for getting access to the entire system (Cve.mitre.org 2018).
This exposure is also applicable to the Amazon Web Services also known as the AWS
which provides web and mail facility(Cve.mitre.org 2018). . The bootstrap implement bundle
called Cloud Formation that enables the users to execute codes in arbitrary fashion with root
access while the same exposure cards the foul players to generate local files in the system. This
exposure was initially discovered by the CTERA cloud storage, associated with the cross site
scripting or the XSS. This vulnerability helps in the injection of the arbitrary web scripts.
CVE-2017-8514
This type of the exposure is linked through intranet network which is used for the
connections of the internal device. The Microsoft SharePoint is one of the major example of this.
One of the major issue that is associated with the MS SharePoint is, the security standards are not
robust adequately for protection of the network. Therefore it can be said that the privacy policy
of the data can be compromised hence the data can be accessed by the unauthorized users. One
of the major risk in this is the fact once the hackers are in the network can user the identity of the
user for getting access to the entire system (Cve.mitre.org 2018).
This exposure is also applicable to the Amazon Web Services also known as the AWS
which provides web and mail facility(Cve.mitre.org 2018). . The bootstrap implement bundle
called Cloud Formation that enables the users to execute codes in arbitrary fashion with root
access while the same exposure cards the foul players to generate local files in the system. This
exposure was initially discovered by the CTERA cloud storage, associated with the cross site
scripting or the XSS. This vulnerability helps in the injection of the arbitrary web scripts.
11CLOUD ARCHITECTURE RISK ASSESSMENT
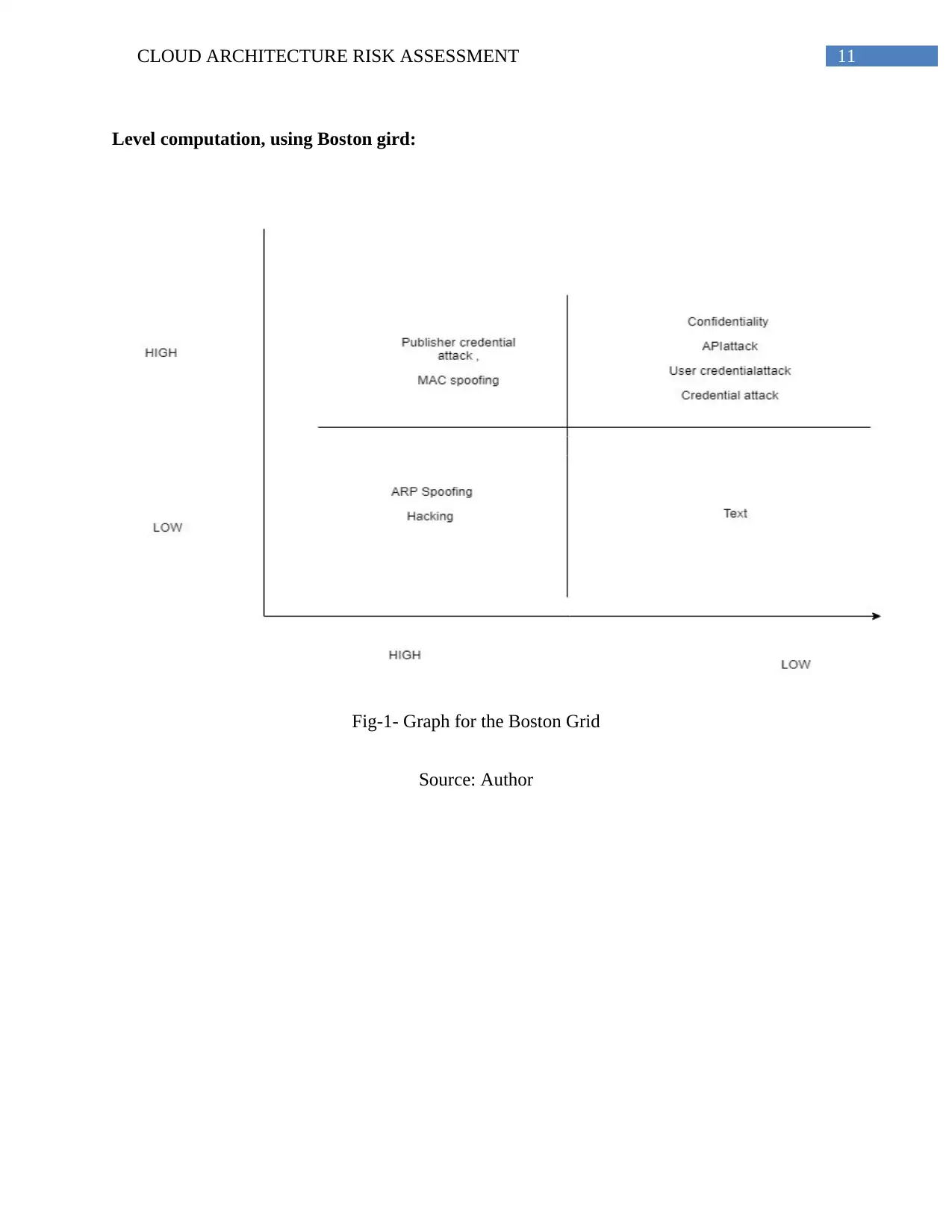
Level computation, using Boston gird:
Fig-1- Graph for the Boston Grid
Source: Author
Level computation, using Boston gird:
Fig-1- Graph for the Boston Grid
Source: Author
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




