CO4512 Information Security Management Risk Assessment for CloudXYZ
VerifiedAdded on 2023/06/13
|15
|2929
|491
Report
AI Summary
This document presents a comprehensive risk assessment conducted for CloudXYZ, a UK-based cloud service provider, focusing on their IT network and security infrastructure. The assessment identifies potential threats and vulnerabilities across various assets, including cloud storage, virtual servers, authentication servers, customer databases, web servers, mail servers, and firewalls. It utilizes qualitative risk assessment methods, including Risk Assessment Matrix (RAM), Risk Probability and Impact Assessment, and ISO 27001 based tools, to evaluate likelihood and impact. The report details owner specifications, asset categorization, threat and vulnerability analysis (including CVE numbers), likelihood level computation, impact table specification, threat and vulnerability levels, risk identification, and overall risk levels. Key risks identified include coding errors, denial of service attacks, data breaches, web application security flaws, and hacking attempts. The assessment aims to provide insights and recommendations for improving CloudXYZ's security posture and mitigating potential business losses due to security incidents.

Information Security
Management
Management
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1. Introduction.....................................................................................................................................3
2. Risk Assessment............................................................................................................................3
2.1 Owner Specifications..................................................................................................................3
2.2 Assets..........................................................................................................................................4
2.3 Assets Table.................................................................................................................................4
2.4 Threats and Vulnerabilities for Asset.........................................................................................4
3. Likelihood Level Computation..................................................................................................7
4. Impact Table Specification........................................................................................................9
5. Threat Level..................................................................................................................................11
6. Vulnerability Level......................................................................................................................12
7. Risk Identification.......................................................................................................................13
8. Risk Level.......................................................................................................................................13
9. Summary and Recommendations.........................................................................................13
10. Conclusion.................................................................................................................................14
References............................................................................................................................................14
1. Introduction.....................................................................................................................................3
2. Risk Assessment............................................................................................................................3
2.1 Owner Specifications..................................................................................................................3
2.2 Assets..........................................................................................................................................4
2.3 Assets Table.................................................................................................................................4
2.4 Threats and Vulnerabilities for Asset.........................................................................................4
3. Likelihood Level Computation..................................................................................................7
4. Impact Table Specification........................................................................................................9
5. Threat Level..................................................................................................................................11
6. Vulnerability Level......................................................................................................................12
7. Risk Identification.......................................................................................................................13
8. Risk Level.......................................................................................................................................13
9. Summary and Recommendations.........................................................................................13
10. Conclusion.................................................................................................................................14
References............................................................................................................................................14

1. Introduction
In UK, a cloud service provider named CloudXYZ, provides IT network/ system for various
organizations. CloudXYZ ensures securing storage and virtual server services for both the individual
customers and for the organizations. Ultimately, they target on security system for preventing or
decreasing any business loss due to incidents like data modification, malfunction, data deletion and
information stealing. The task of this project includes to perform risk assessment for the provided
security network architecture. For performing risk assessment, there exists certain “open-source”
methods and some proprietary methods, which provides answer to the questions like- What must be
protected? What are the vulnerabilities and threats? What are its implications? What value it has to the
organization? and What could decrease the damages? Therefore, these are the advantages of risk
assessment methods. The utilized risk assessment methods are, Qualitative Risk Assessment Matrix
(RAM), Risk Probability and Impact Assessment, Combination of checklists and what-if analysis methods,
and Preliminary environment risk ranking method. The ISO 27001 based Risk Assessment Tool is
effective solution. The impact analysis and likelihood are the other tasks which will be performed during
the risk assessment on the given system. Because, it helps to determine the potential impacts resulting
from the critical business processes. Moreover, the risk assessment methods help to provide
suggestions of whether the system’s security, integrity, confidentiality must be increased or not?
2. Risk Assessment
2.1 Owner Specifications
For maintaining the database, security tool, website and other services which provides a
function for security vulnerability or exposure identification is known as capability. Here, the user
denotes the owner and the owner has the responsibility of maintaining the capability. The CVE
(Common Vulnerabilities and Exposures) compatibility provides the facility of sharing the data, only
when there is accurate capability mapping. Thus, it is required that CVE-compatible capabilities should
meet minimum accuracy requirements (Cve.mitre.org, 2018).
The owner specifications include the following (Cve.mitre.org, 2018):
1) The Owner should have valid phone number, email ID and address.
2) The capability should give additional information or value that is provided in the CVE
such as, name, references, description and related data.
3) The queries related to CVE functionality of the capability and mapping must be provided
by the technical point of contact which the owner has.
4) By using CVE names ("CVE-Searchable"), the capability show let the users to locate the
security elements.
5) The CVE names must be used for Security Service to mention the user which of the
security elements are tested or detected by the service ("CVE-Searchable").
6) The Service should enable the client to decide the related CVE names for those
elements ("CVE-Output"), for the report which recognizes the single security elements,
by completing at least one of these- letting the client directly incorporate CVE names in
In UK, a cloud service provider named CloudXYZ, provides IT network/ system for various
organizations. CloudXYZ ensures securing storage and virtual server services for both the individual
customers and for the organizations. Ultimately, they target on security system for preventing or
decreasing any business loss due to incidents like data modification, malfunction, data deletion and
information stealing. The task of this project includes to perform risk assessment for the provided
security network architecture. For performing risk assessment, there exists certain “open-source”
methods and some proprietary methods, which provides answer to the questions like- What must be
protected? What are the vulnerabilities and threats? What are its implications? What value it has to the
organization? and What could decrease the damages? Therefore, these are the advantages of risk
assessment methods. The utilized risk assessment methods are, Qualitative Risk Assessment Matrix
(RAM), Risk Probability and Impact Assessment, Combination of checklists and what-if analysis methods,
and Preliminary environment risk ranking method. The ISO 27001 based Risk Assessment Tool is
effective solution. The impact analysis and likelihood are the other tasks which will be performed during
the risk assessment on the given system. Because, it helps to determine the potential impacts resulting
from the critical business processes. Moreover, the risk assessment methods help to provide
suggestions of whether the system’s security, integrity, confidentiality must be increased or not?
2. Risk Assessment
2.1 Owner Specifications
For maintaining the database, security tool, website and other services which provides a
function for security vulnerability or exposure identification is known as capability. Here, the user
denotes the owner and the owner has the responsibility of maintaining the capability. The CVE
(Common Vulnerabilities and Exposures) compatibility provides the facility of sharing the data, only
when there is accurate capability mapping. Thus, it is required that CVE-compatible capabilities should
meet minimum accuracy requirements (Cve.mitre.org, 2018).
The owner specifications include the following (Cve.mitre.org, 2018):
1) The Owner should have valid phone number, email ID and address.
2) The capability should give additional information or value that is provided in the CVE
such as, name, references, description and related data.
3) The queries related to CVE functionality of the capability and mapping must be provided
by the technical point of contact which the owner has.
4) By using CVE names ("CVE-Searchable"), the capability show let the users to locate the
security elements.
5) The CVE names must be used for Security Service to mention the user which of the
security elements are tested or detected by the service ("CVE-Searchable").
6) The Service should enable the client to decide the related CVE names for those
elements ("CVE-Output"), for the report which recognizes the single security elements,
by completing at least one of these- letting the client directly incorporate CVE names in
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
the report, by furnishing the client with a mapping between the security elements and
CVE names, or by utilizing any other system.
7) Any desired reports or mappings which are given by the Service should fulfill the
requirements of media.
8) The product must be CVE-compatible, when the Service provides direct access to the
users.
2.2 Assets
The assets are considered as either primary or secondary, to recognize the assets that are
imported. For instance, the assets that should be imported first when compared to the other assets are
referred as primary assets and the assets which will be imported after the primary assets are referred as
the secondary assets (Support.symantec.com, 2011).
The primary assets contains super-set of the secondary assets. For instance, when a Control
Compliance Suite is considered, it is required to first import the Windows Domain prior to importing the
Windows Machines. Thus, here the primary asset is denoted as Windows Domain and the secondary
asset is denoted as Windows Machine. On the other hand, in the asset system, the Windows Domain is
called as the default scope for the Windows Machines. On the other hand, default scope refers to
importing the primary assets prior to the secondary assets.
2.3 Assets Table
ID Asset Primary or Secondary Asset
CS Cloud storage Primary Asset
VS Virtual server Secondary Asset
AS Authentication Server Secondary Asset
CD Customer Database Secondary Asset
WS Web server Secondary Asset
MS Mail Server Secondary Asset
FW Firewall/IDS Secondary Asset
I Internet Primary Asset
2.4 Threats and Vulnerabilities for Asset
The CloudXYZ organization’s assets their threats and vulnerabilities are as follows:
1) Cloud Storage
Threats
a) Data Breaches
The security breaches comprises of healthcare data, revenue details and
financial data (Networkmagazineindia.com, 2002).
b) Data Loss
There are possibilities of heavy loss of data and it could be highly expensive
for the organization.
c) Malicious Insiders
CVE names, or by utilizing any other system.
7) Any desired reports or mappings which are given by the Service should fulfill the
requirements of media.
8) The product must be CVE-compatible, when the Service provides direct access to the
users.
2.2 Assets
The assets are considered as either primary or secondary, to recognize the assets that are
imported. For instance, the assets that should be imported first when compared to the other assets are
referred as primary assets and the assets which will be imported after the primary assets are referred as
the secondary assets (Support.symantec.com, 2011).
The primary assets contains super-set of the secondary assets. For instance, when a Control
Compliance Suite is considered, it is required to first import the Windows Domain prior to importing the
Windows Machines. Thus, here the primary asset is denoted as Windows Domain and the secondary
asset is denoted as Windows Machine. On the other hand, in the asset system, the Windows Domain is
called as the default scope for the Windows Machines. On the other hand, default scope refers to
importing the primary assets prior to the secondary assets.
2.3 Assets Table
ID Asset Primary or Secondary Asset
CS Cloud storage Primary Asset
VS Virtual server Secondary Asset
AS Authentication Server Secondary Asset
CD Customer Database Secondary Asset
WS Web server Secondary Asset
MS Mail Server Secondary Asset
FW Firewall/IDS Secondary Asset
I Internet Primary Asset
2.4 Threats and Vulnerabilities for Asset
The CloudXYZ organization’s assets their threats and vulnerabilities are as follows:
1) Cloud Storage
Threats
a) Data Breaches
The security breaches comprises of healthcare data, revenue details and
financial data (Networkmagazineindia.com, 2002).
b) Data Loss
There are possibilities of heavy loss of data and it could be highly expensive
for the organization.
c) Malicious Insiders
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The threats of IT and network security could harm the organizational
infrastructure.
Vulnerabilities
a) The CVE number of the vulnerability is CVE-2017-1375. This vulnerability
refers to the IBM System Storage Storwize V7000 Unified (V7000U) where
1.5 and 1.6 utilizes cryptographic algorithms that are weaker and this might
help the attacker in decrypting the extremely sensitive information. IBM X-
Force ID: 126868. (High)
b) The CVE number is CVE-2017-1304. This vulnerability could result in using
incorrect memory address and can lead to DoS or undetected data
corruption (Nvd.nist.gov, 2018). (Medium).
2) Virtual Server
Threats
a) Traffic control (US EPA, 2018).
b) Lack of visibility.
c) DoS.
Vulnerabilities
a) The CVE number is CVE-2017-6160. The remote attacker could easily
makes HTTP request that are crafted maliciously, so that the Traffic
Management Microkernel (TMM) will restart then it will fail to process the
traffic temporarily. (Medium).
b) The CVE number is CVE-2017-6159. The following are vulnerable to DoS
attack, in F5 BIG-IP LTM, AAM, AFM, Analytics, APM, ASM, DNS, GTM, Link
Controller, PEM, Websafe software version 12.0.0 to 12.1.2, 11.6.0 to
11.6.1. The attacker could harm the services so that the Traffic
Management Microkernel (TMM) will restart then it will fail to process the
traffic temporarily. (Medium).
3) Authentication Server
Threats
a) Sniffing and Spoofing
b) Data leakage
c) Denial of Service (DoS)
Vulnerabilities
a) The CVE number CVE-2017-16025 refers to a DoS vulnerability through
invalid Cookie header. (Medium)
b) The CVE number CVE-2018-7942 refers to the vulnerability that leads to
improper authentication design, exploitation and leakage of information.
(High)
infrastructure.
Vulnerabilities
a) The CVE number of the vulnerability is CVE-2017-1375. This vulnerability
refers to the IBM System Storage Storwize V7000 Unified (V7000U) where
1.5 and 1.6 utilizes cryptographic algorithms that are weaker and this might
help the attacker in decrypting the extremely sensitive information. IBM X-
Force ID: 126868. (High)
b) The CVE number is CVE-2017-1304. This vulnerability could result in using
incorrect memory address and can lead to DoS or undetected data
corruption (Nvd.nist.gov, 2018). (Medium).
2) Virtual Server
Threats
a) Traffic control (US EPA, 2018).
b) Lack of visibility.
c) DoS.
Vulnerabilities
a) The CVE number is CVE-2017-6160. The remote attacker could easily
makes HTTP request that are crafted maliciously, so that the Traffic
Management Microkernel (TMM) will restart then it will fail to process the
traffic temporarily. (Medium).
b) The CVE number is CVE-2017-6159. The following are vulnerable to DoS
attack, in F5 BIG-IP LTM, AAM, AFM, Analytics, APM, ASM, DNS, GTM, Link
Controller, PEM, Websafe software version 12.0.0 to 12.1.2, 11.6.0 to
11.6.1. The attacker could harm the services so that the Traffic
Management Microkernel (TMM) will restart then it will fail to process the
traffic temporarily. (Medium).
3) Authentication Server
Threats
a) Sniffing and Spoofing
b) Data leakage
c) Denial of Service (DoS)
Vulnerabilities
a) The CVE number CVE-2017-16025 refers to a DoS vulnerability through
invalid Cookie header. (Medium)
b) The CVE number CVE-2018-7942 refers to the vulnerability that leads to
improper authentication design, exploitation and leakage of information.
(High)

4) Customer Database
Threats
a) Privilege Abuse, which is a threat in the database security.
b) Web application Security which is not enough.
c) Storage media which is not secure enough (Securitycommunity.tcs.com,
2017).
Vulnerabilities
a) The CVE number CVE-2008-6761 refers to the vulnerability that lets the
attackers to inject a static code injection in admin/install.php. (High)
b) The CVE number CVE-2005-4515 refers to DISPUTED SQL injection
vulnerability in the WebDB 1.1. (High)
5) Web Server
Threats
a) Coding errors
b) Security holes
c) Sensitive file
Vulnerabilities
a) The CVE number CVE-2018-2893 refers to the vulnerability of exploitation.
(critical).
b) The CVE number CVE-2018-0340 refers to the vulnerability in the web
framework. The attacker can exploit the vulnerability. (medium).
6) Mail Server
Threats
a) Spam
b) Hoaxes
c) Fake emails
Vulnerabilities
a) The CVE number CVE-2017-14077 refers to the vulnerability that allows the
attackers inject the arbitrary HTML into the body of the e-mail message.
(medium).
b) The CVE number CVE-2016-9127 refers to the vulnerability that sends a
large number of password recovery/ bug recovery emails to the registered
users. (High).
7) Firewall/IDS
Threats
a) Insider Attacks
b) Missed Security Patches
c) Distributed Denial of Service (DDoS) attacks
Threats
a) Privilege Abuse, which is a threat in the database security.
b) Web application Security which is not enough.
c) Storage media which is not secure enough (Securitycommunity.tcs.com,
2017).
Vulnerabilities
a) The CVE number CVE-2008-6761 refers to the vulnerability that lets the
attackers to inject a static code injection in admin/install.php. (High)
b) The CVE number CVE-2005-4515 refers to DISPUTED SQL injection
vulnerability in the WebDB 1.1. (High)
5) Web Server
Threats
a) Coding errors
b) Security holes
c) Sensitive file
Vulnerabilities
a) The CVE number CVE-2018-2893 refers to the vulnerability of exploitation.
(critical).
b) The CVE number CVE-2018-0340 refers to the vulnerability in the web
framework. The attacker can exploit the vulnerability. (medium).
6) Mail Server
Threats
a) Spam
b) Hoaxes
c) Fake emails
Vulnerabilities
a) The CVE number CVE-2017-14077 refers to the vulnerability that allows the
attackers inject the arbitrary HTML into the body of the e-mail message.
(medium).
b) The CVE number CVE-2016-9127 refers to the vulnerability that sends a
large number of password recovery/ bug recovery emails to the registered
users. (High).
7) Firewall/IDS
Threats
a) Insider Attacks
b) Missed Security Patches
c) Distributed Denial of Service (DDoS) attacks
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Vulnerabilities
a) The CVE number CVE- 2018-0227 refers to the vulnerability present in the
Secure Sockets Layer (SSL), the Virtual Private Network (VPN) Client
Certificate Authentication because of incorrect SSL Client Certificate
verification. (High).
b) The CVE number CVE-2018-8873 refers to the vulnerability of denial of
service (High).
8) Internet
Threats
a) Hacking
This is a serious threat, where unauthorized user can easily access other
person’s confidential information, for performing malicious activities and
harming them.
b) Viruses
The computer programs are sent through email which are refers are virus
and has the capacity to harm the computer and its working (Roussey,
2017).
c) Data leakage
Vulnerabilities
a) The CVE number CVE-2018-0978 refers to remote code execution
vulnerability. (High)
b) The CVE number CVE-2018-1025 refers to information disclosure
vulnerability. (Medium).
3. Likelihood Level Computation
The likelihood is calculated using the following formula,
Likelihood= Threat * Vulnerability
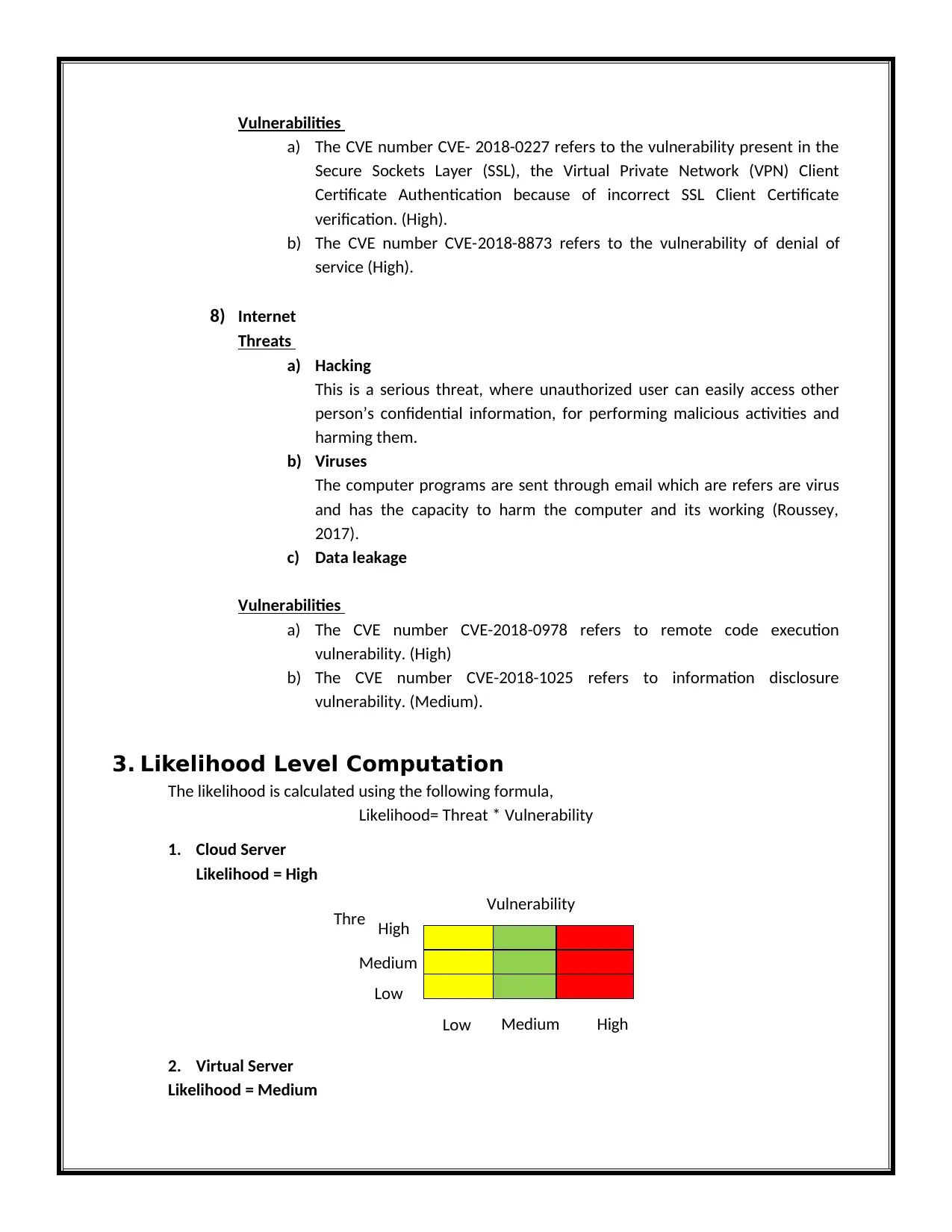
1. Cloud Server
Likelihood = High
2. Virtual Server
Likelihood = Medium
Threat Vulnerability
Low Medium High
Low
Medium
High
a) The CVE number CVE- 2018-0227 refers to the vulnerability present in the
Secure Sockets Layer (SSL), the Virtual Private Network (VPN) Client
Certificate Authentication because of incorrect SSL Client Certificate
verification. (High).
b) The CVE number CVE-2018-8873 refers to the vulnerability of denial of
service (High).
8) Internet
Threats
a) Hacking
This is a serious threat, where unauthorized user can easily access other
person’s confidential information, for performing malicious activities and
harming them.
b) Viruses
The computer programs are sent through email which are refers are virus
and has the capacity to harm the computer and its working (Roussey,
2017).
c) Data leakage
Vulnerabilities
a) The CVE number CVE-2018-0978 refers to remote code execution
vulnerability. (High)
b) The CVE number CVE-2018-1025 refers to information disclosure
vulnerability. (Medium).
3. Likelihood Level Computation
The likelihood is calculated using the following formula,
Likelihood= Threat * Vulnerability
1. Cloud Server
Likelihood = High
2. Virtual Server
Likelihood = Medium
Threat Vulnerability
Low Medium High
Low
Medium
High
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
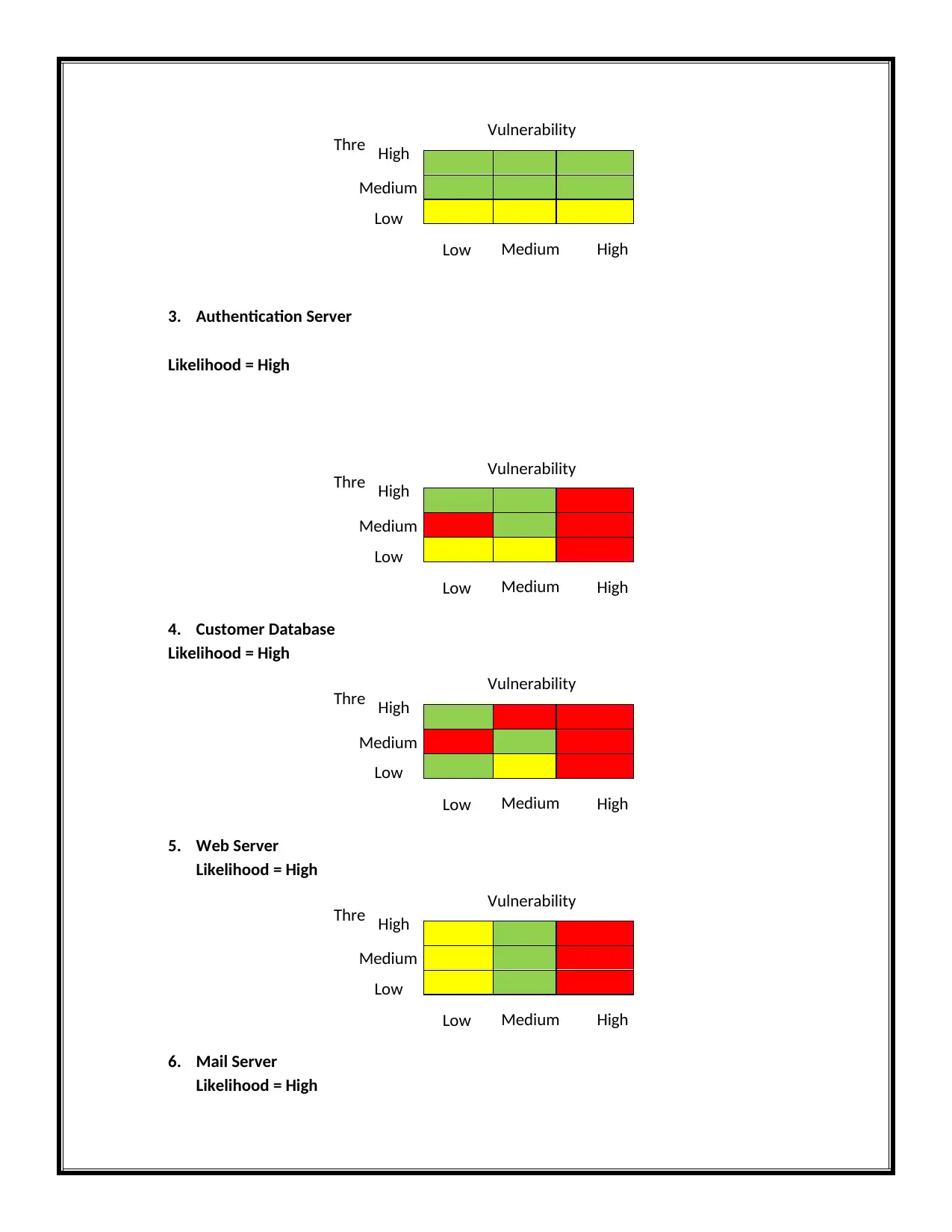
3. Authentication Server
Likelihood = High
4. Customer Database
Likelihood = High
5. Web Server
Likelihood = High
6. Mail Server
Likelihood = High
Threat Vulnerability
Low Medium High
Low
Medium
High
Threat Vulnerability
Low Medium High
Low
Medium
High
Threat Vulnerability
Low Medium High
Low
Medium
High
Threat Vulnerability
Low Medium High
Low
Medium
High
Likelihood = High
4. Customer Database
Likelihood = High
5. Web Server
Likelihood = High
6. Mail Server
Likelihood = High
Threat Vulnerability
Low Medium High
Low
Medium
High
Threat Vulnerability
Low Medium High
Low
Medium
High
Threat Vulnerability
Low Medium High
Low
Medium
High
Threat Vulnerability
Low Medium High
Low
Medium
High
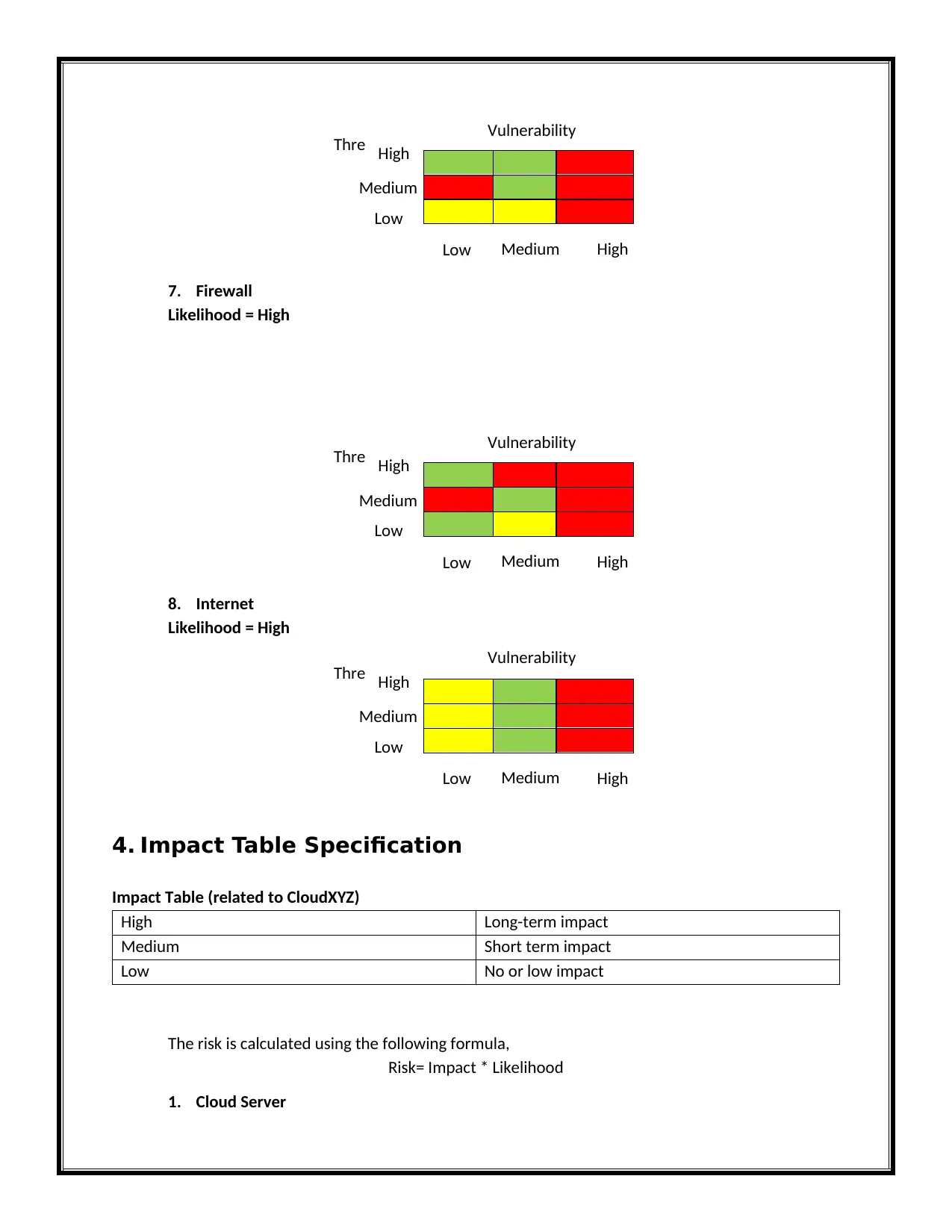
7. Firewall
Likelihood = High
8. Internet
Likelihood = High
4. Impact Table Specification
Impact Table (related to CloudXYZ)
High Long-term impact
Medium Short term impact
Low No or low impact
The risk is calculated using the following formula,
Risk= Impact * Likelihood
1. Cloud Server
Threat Vulnerability
Low Medium High
Low
Medium
High
Threat Vulnerability
Low Medium High
Low
Medium
High
Threat Vulnerability
Low Medium High
Low
Medium
High
Likelihood = High
8. Internet
Likelihood = High
4. Impact Table Specification
Impact Table (related to CloudXYZ)
High Long-term impact
Medium Short term impact
Low No or low impact
The risk is calculated using the following formula,
Risk= Impact * Likelihood
1. Cloud Server
Threat Vulnerability
Low Medium High
Low
Medium
High
Threat Vulnerability
Low Medium High
Low
Medium
High
Threat Vulnerability
Low Medium High
Low
Medium
High
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
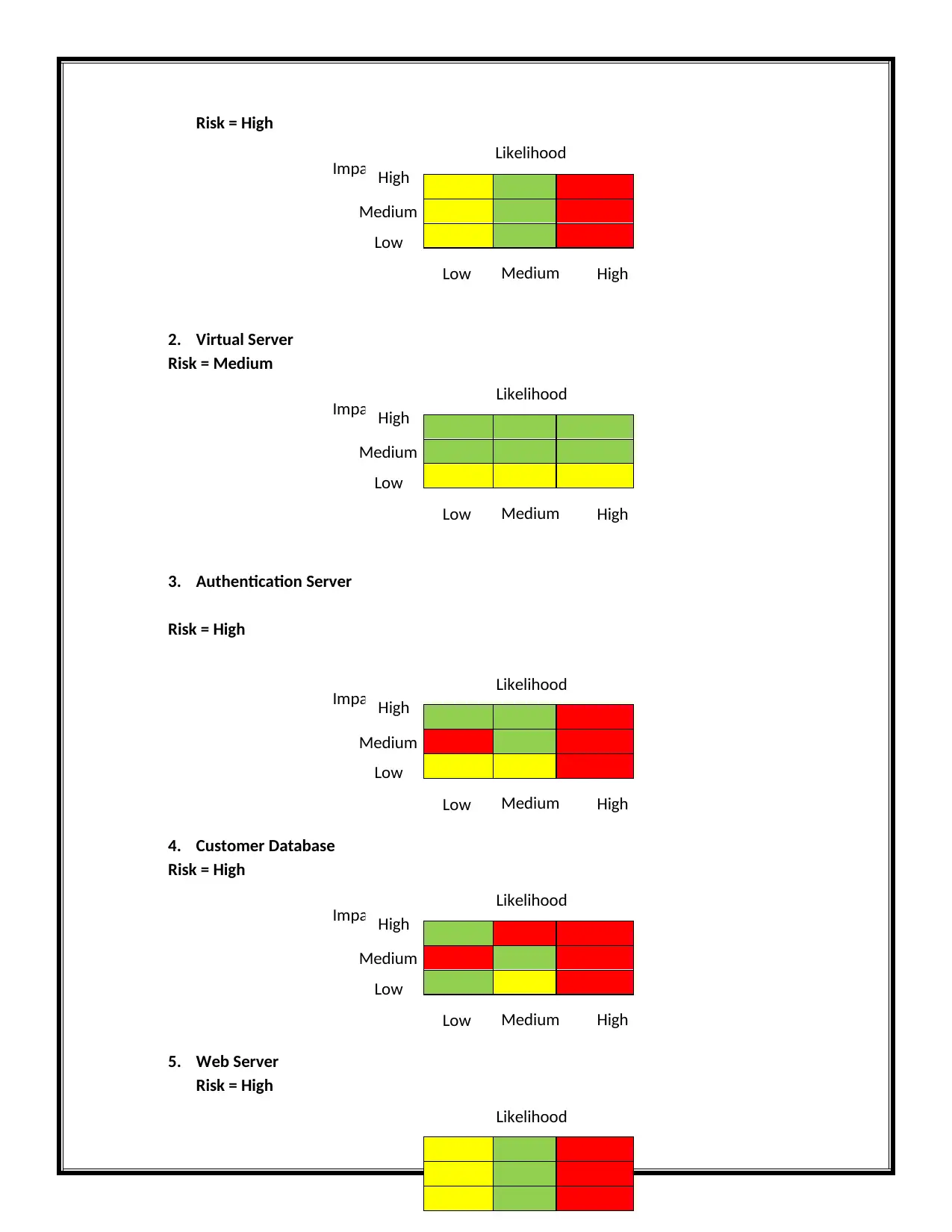
Risk = High
2. Virtual Server
Risk = Medium
3. Authentication Server
Risk = High
4. Customer Database
Risk = High
5. Web Server
Risk = High
Impact Likelihood
Low Medium High
Low
Medium
High
Impact Likelihood
Low Medium High
Low
Medium
High
Impact Likelihood
Low Medium High
Low
Medium
High
Impact Likelihood
Low Medium High
Low
Medium
High
Likelihood
2. Virtual Server
Risk = Medium
3. Authentication Server
Risk = High
4. Customer Database
Risk = High
5. Web Server
Risk = High
Impact Likelihood
Low Medium High
Low
Medium
High
Impact Likelihood
Low Medium High
Low
Medium
High
Impact Likelihood
Low Medium High
Low
Medium
High
Impact Likelihood
Low Medium High
Low
Medium
High
Likelihood
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
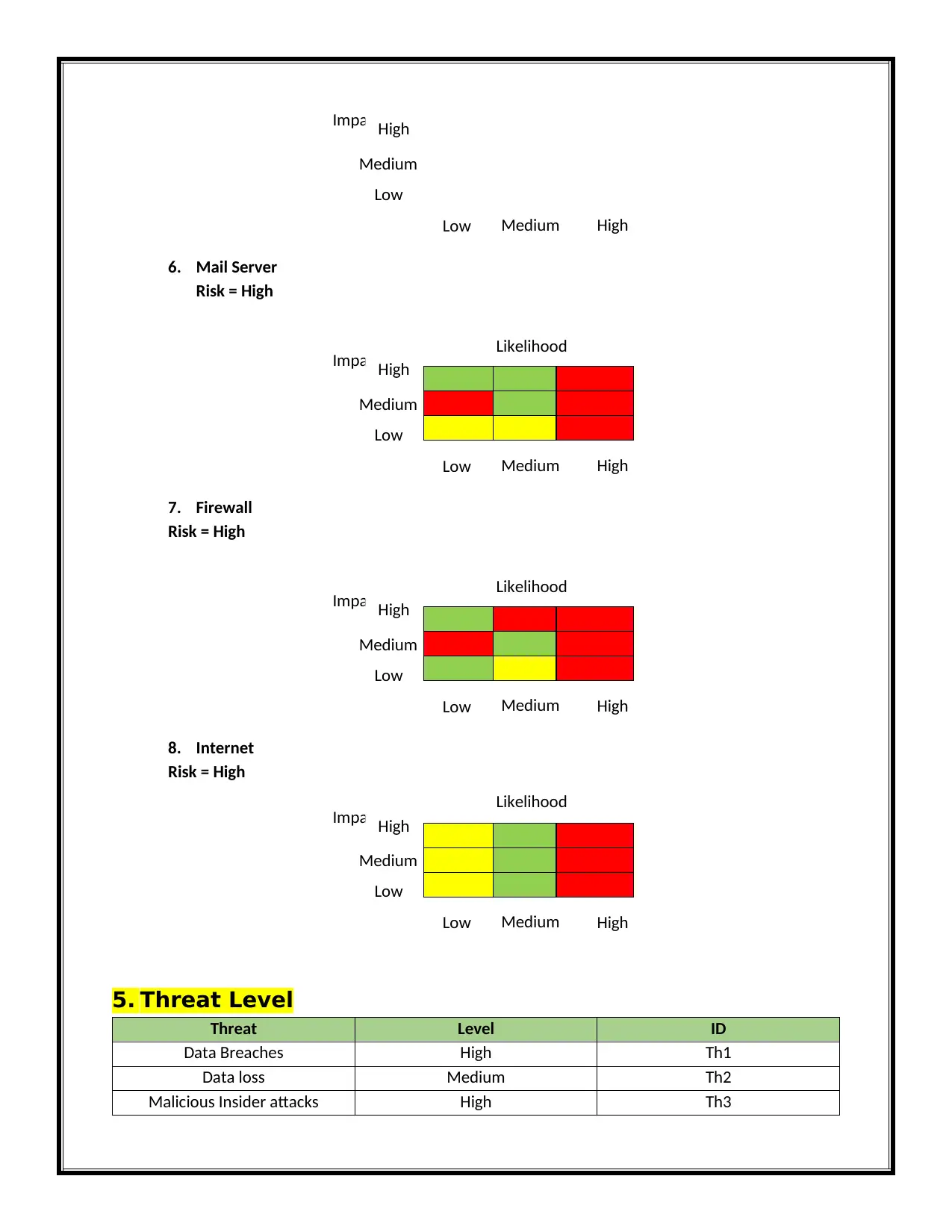
6. Mail Server
Risk = High
7. Firewall
Risk = High
8. Internet
Risk = High
5. Threat Level
Threat Level ID
Data Breaches High Th1
Data loss Medium Th2
Malicious Insider attacks High Th3
Impact
Low Medium High
Low
Medium
High
Impact Likelihood
Low Medium High
Low
Medium
High
Impact Likelihood
Low Medium High
Low
Medium
High
Impact Likelihood
Low Medium High
Low
Medium
High
Risk = High
7. Firewall
Risk = High
8. Internet
Risk = High
5. Threat Level
Threat Level ID
Data Breaches High Th1
Data loss Medium Th2
Malicious Insider attacks High Th3
Impact
Low Medium High
Low
Medium
High
Impact Likelihood
Low Medium High
Low
Medium
High
Impact Likelihood
Low Medium High
Low
Medium
High
Impact Likelihood
Low Medium High
Low
Medium
High
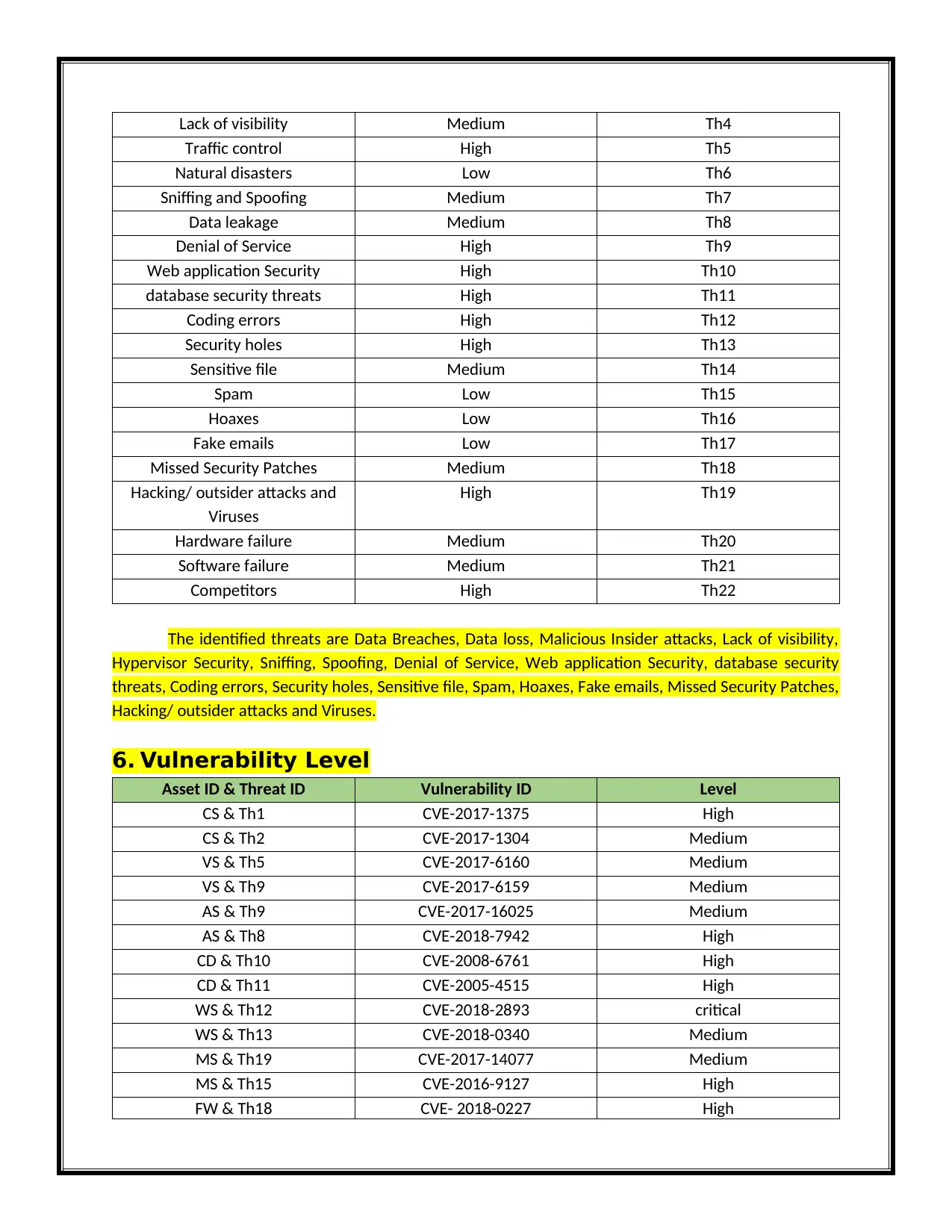
Lack of visibility Medium Th4
Traffic control High Th5
Natural disasters Low Th6
Sniffing and Spoofing Medium Th7
Data leakage Medium Th8
Denial of Service High Th9
Web application Security High Th10
database security threats High Th11
Coding errors High Th12
Security holes High Th13
Sensitive file Medium Th14
Spam Low Th15
Hoaxes Low Th16
Fake emails Low Th17
Missed Security Patches Medium Th18
Hacking/ outsider attacks and
Viruses
High Th19
Hardware failure Medium Th20
Software failure Medium Th21
Competitors High Th22
The identified threats are Data Breaches, Data loss, Malicious Insider attacks, Lack of visibility,
Hypervisor Security, Sniffing, Spoofing, Denial of Service, Web application Security, database security
threats, Coding errors, Security holes, Sensitive file, Spam, Hoaxes, Fake emails, Missed Security Patches,
Hacking/ outsider attacks and Viruses.
6. Vulnerability Level
Asset ID & Threat ID Vulnerability ID Level
CS & Th1 CVE-2017-1375 High
CS & Th2 CVE-2017-1304 Medium
VS & Th5 CVE-2017-6160 Medium
VS & Th9 CVE-2017-6159 Medium
AS & Th9 CVE-2017-16025 Medium
AS & Th8 CVE-2018-7942 High
CD & Th10 CVE-2008-6761 High
CD & Th11 CVE-2005-4515 High
WS & Th12 CVE-2018-2893 critical
WS & Th13 CVE-2018-0340 Medium
MS & Th19 CVE-2017-14077 Medium
MS & Th15 CVE-2016-9127 High
FW & Th18 CVE- 2018-0227 High
Traffic control High Th5
Natural disasters Low Th6
Sniffing and Spoofing Medium Th7
Data leakage Medium Th8
Denial of Service High Th9
Web application Security High Th10
database security threats High Th11
Coding errors High Th12
Security holes High Th13
Sensitive file Medium Th14
Spam Low Th15
Hoaxes Low Th16
Fake emails Low Th17
Missed Security Patches Medium Th18
Hacking/ outsider attacks and
Viruses
High Th19
Hardware failure Medium Th20
Software failure Medium Th21
Competitors High Th22
The identified threats are Data Breaches, Data loss, Malicious Insider attacks, Lack of visibility,
Hypervisor Security, Sniffing, Spoofing, Denial of Service, Web application Security, database security
threats, Coding errors, Security holes, Sensitive file, Spam, Hoaxes, Fake emails, Missed Security Patches,
Hacking/ outsider attacks and Viruses.
6. Vulnerability Level
Asset ID & Threat ID Vulnerability ID Level
CS & Th1 CVE-2017-1375 High
CS & Th2 CVE-2017-1304 Medium
VS & Th5 CVE-2017-6160 Medium
VS & Th9 CVE-2017-6159 Medium
AS & Th9 CVE-2017-16025 Medium
AS & Th8 CVE-2018-7942 High
CD & Th10 CVE-2008-6761 High
CD & Th11 CVE-2005-4515 High
WS & Th12 CVE-2018-2893 critical
WS & Th13 CVE-2018-0340 Medium
MS & Th19 CVE-2017-14077 Medium
MS & Th15 CVE-2016-9127 High
FW & Th18 CVE- 2018-0227 High
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





