CO4515 Trends in Cybercrime: Crypto Malware and Vulnerabilities
VerifiedAdded on 2023/05/29
|14
|919
|105
Report
AI Summary
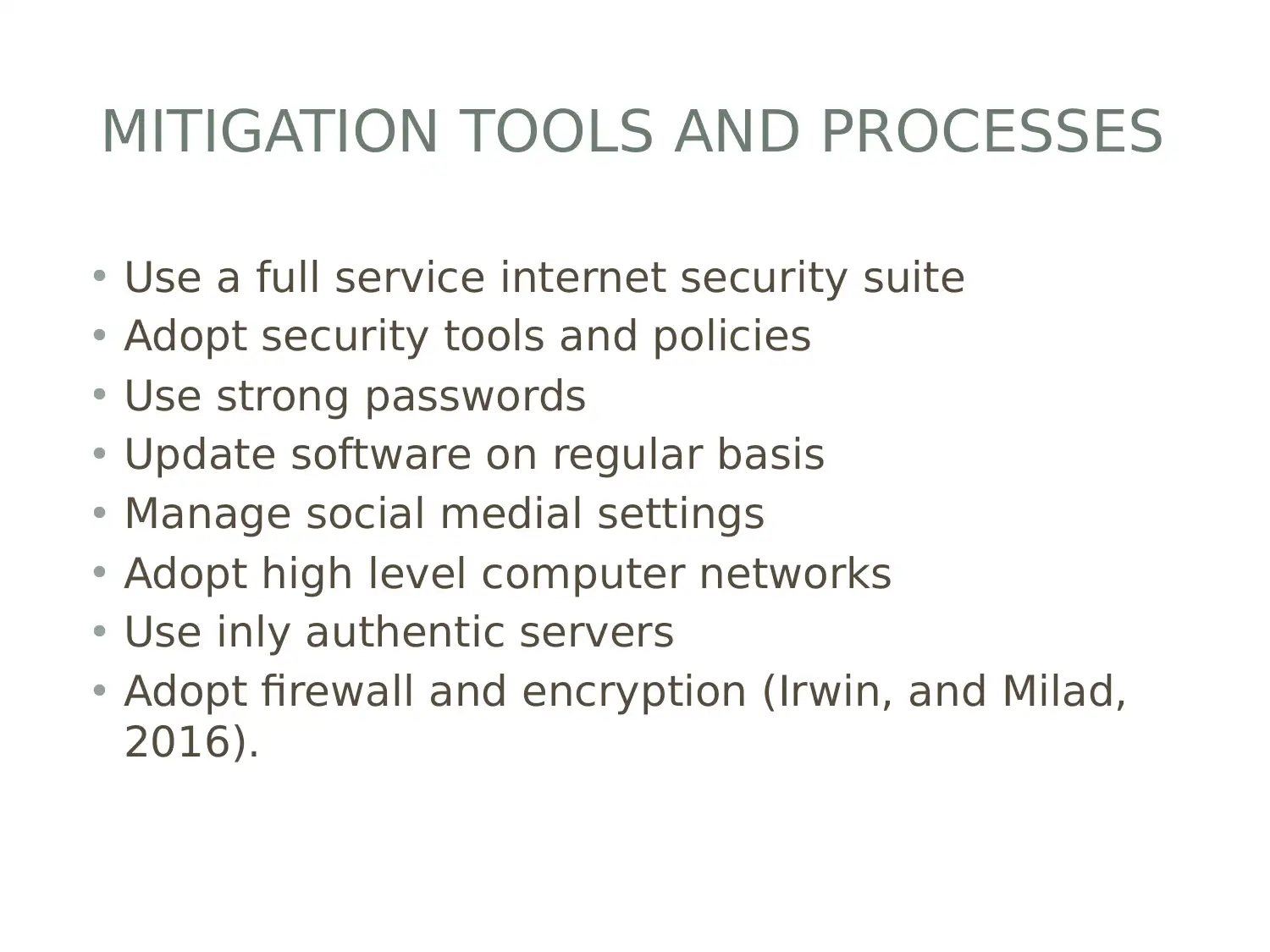
This report investigates the connection between cryptocurrency and cybercrime, focusing on the types of malware used by cybercriminals to target cryptocurrencies. It identifies specific malware such as Crypto lockers, Crypto jacking, and WannaCry, and examines the vulnerabilities they exploit. The report also discusses mitigation tools and processes, including authentication, firewall technology, and the importance of strong passwords and regular software updates. It addresses the drawbacks of these mitigation strategies and proposes solutions to overcome them, such as using high-level passwords and employing antivirus and cryptography technologies. The conclusion emphasizes the significance of understanding cryptocurrency-related cybercrime and the importance of cybersecurity skills. Desklib provides access to similar reports and study tools for students.
1 out of 14


















![[object Object]](/_next/static/media/star-bottom.7253800d.svg)