Analysis of Coca-Cola's Governance, CSR Policy, and Epsilon Case Study
VerifiedAdded on 2022/09/28
|5
|864
|30
Homework Assignment
AI Summary
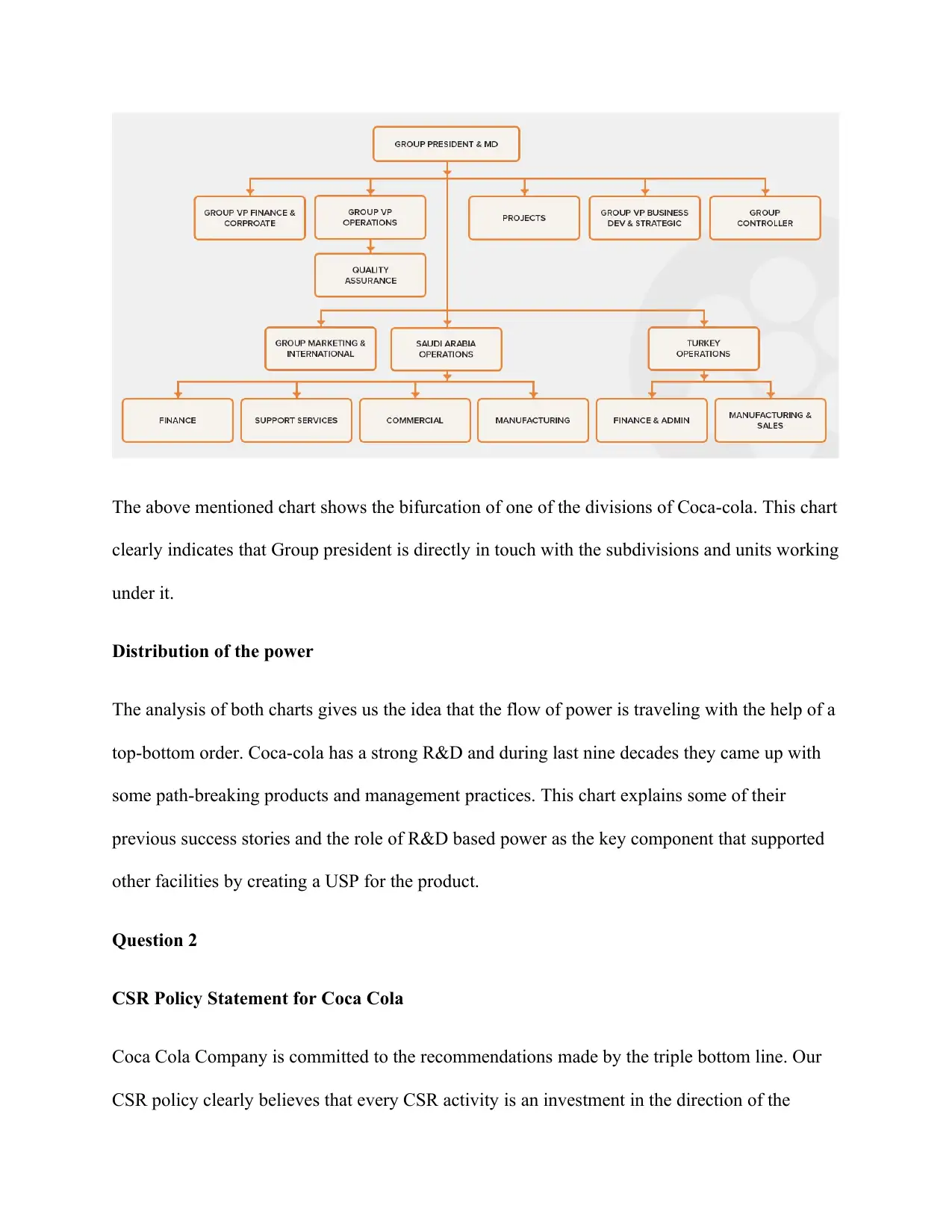
This assignment analyzes Coca-Cola's governance and management structure, presenting it through governance charts that illustrate power distribution across different divisions and geographical regions, emphasizing a top-down approach. It then develops a CSR policy statement for Coca-Cola, aligning with triple bottom line principles, focusing on local area welfare, ecological balance, and infrastructure development, with a commitment to water conservation and enhancement of human life quality. The assignment also addresses the Epsilon case study, where a marketing services company faced a data breach. It assesses Epsilon's fault, highlighting criminal negligence in data security and third-party misuse, and recommends damage control measures, including investigation, compensation claims, and leveraging the situation to demonstrate the company's strength. References to academic literature support the analysis.
1 out of 5




![[object Object]](/_next/static/media/star-bottom.7253800d.svg)