COIT 20246 Assignment: IoT Cybersecurity in the Healthcare Sector
VerifiedAdded on 2020/05/16
|14
|4366
|167
Homework Assignment
AI Summary
This homework assignment for COIT 20246 covers several key topics related to information technology and its applications in various sectors. The assignment is divided into weekly tasks, each focusing on a different area. Week 1 explores mass storage technologies, comparing direct-attached storage (DAS) and network-attached storage (NAS). Week 2 examines real-time operating systems (RTOS) and their benefits within the healthcare sector. Week 3 delves into security and privacy issues related to mobile cloud computing in finance. Week 4 discusses common standards at the transport layer of the TCP/IP protocol suite. Finally, Week 5 addresses the cybersecurity challenges presented by the Internet of Things (IoT) within the healthcare industry. Each task requires students to research and summarize relevant resources, demonstrating their understanding of the topics and their ability to apply academic referencing standards.

COIT 20246 ASSIGNMENT SUBMISSION
Due date: Thursday Week 11 (2PM AEST)
Part: Written Assessment
Weighting: 30% of total assessment.
Submission: Electronic (see course website for details)
Instructions
It will be necessary to use literature/online resources to complete this
assignment, please ensure you cite and reference any such materials using
the Harvard format.
DO NOT copy content directly from either the text or Internet resources: this
assignment is to be in your own words. You will lose marks if you do not
use your own words!
Please complete your assignment using this submission template file,
inserting your responses where indicated.
DO NOT delete the marking criteria page – changes are permitted to the
formatting of other pages including the headers and footers.
Please fill in the following details:
Student Name
Student Number
Due date: Thursday Week 11 (2PM AEST)
Part: Written Assessment
Weighting: 30% of total assessment.
Submission: Electronic (see course website for details)
Instructions
It will be necessary to use literature/online resources to complete this
assignment, please ensure you cite and reference any such materials using
the Harvard format.
DO NOT copy content directly from either the text or Internet resources: this
assignment is to be in your own words. You will lose marks if you do not
use your own words!
Please complete your assignment using this submission template file,
inserting your responses where indicated.
DO NOT delete the marking criteria page – changes are permitted to the
formatting of other pages including the headers and footers.
Please fill in the following details:
Student Name
Student Number
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
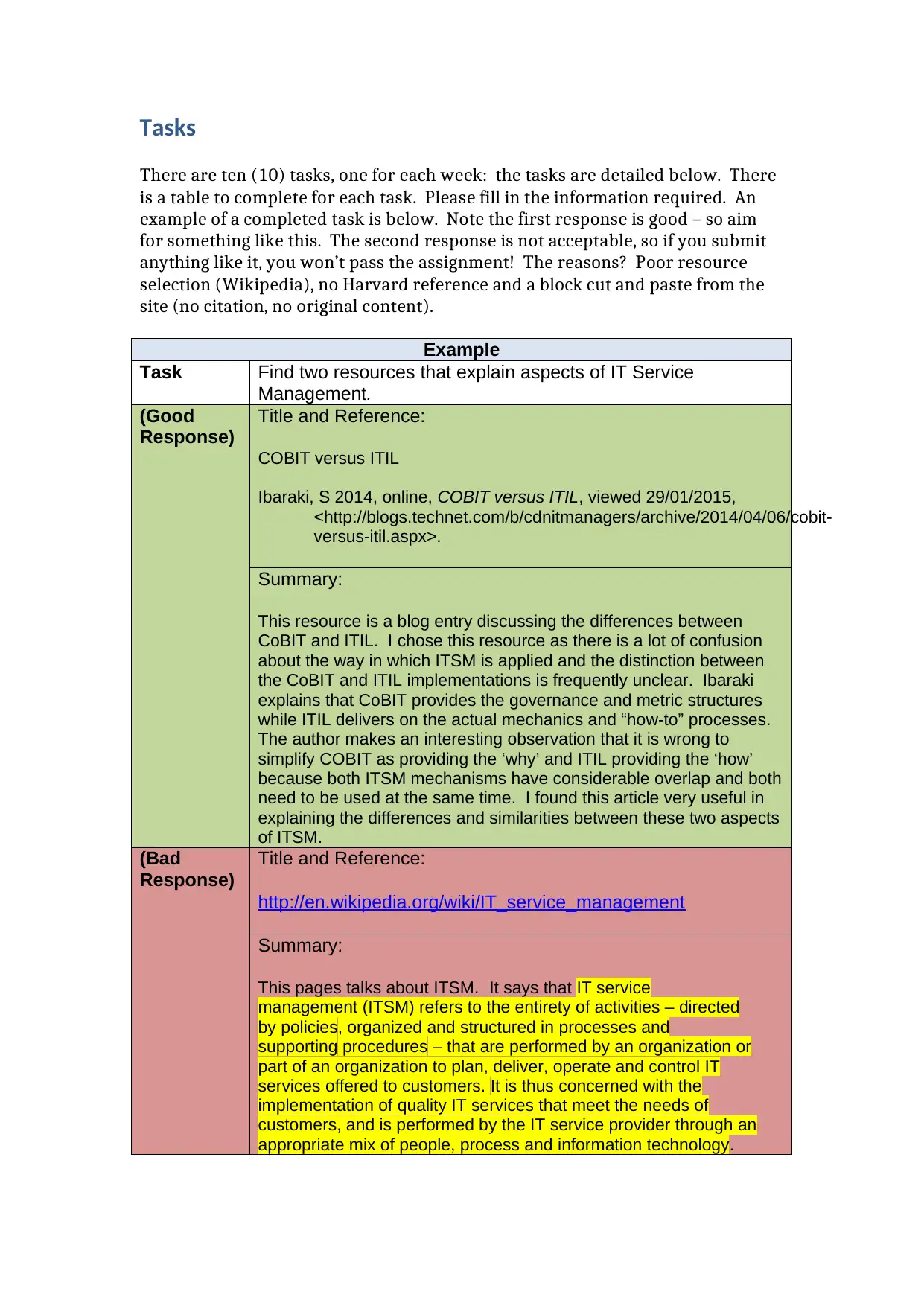
Tasks
There are ten (10) tasks, one for each week: the tasks are detailed below. There
is a table to complete for each task. Please fill in the information required. An
example of a completed task is below. Note the first response is good – so aim
for something like this. The second response is not acceptable, so if you submit
anything like it, you won’t pass the assignment! The reasons? Poor resource
selection (Wikipedia), no Harvard reference and a block cut and paste from the
site (no citation, no original content).
Example
Task Find two resources that explain aspects of IT Service
Management.
(Good
Response)
Title and Reference:
COBIT versus ITIL
Ibaraki, S 2014, online, COBIT versus ITIL, viewed 29/01/2015,
<http://blogs.technet.com/b/cdnitmanagers/archive/2014/04/06/cobit-
versus-itil.aspx>.
Summary:
This resource is a blog entry discussing the differences between
CoBIT and ITIL. I chose this resource as there is a lot of confusion
about the way in which ITSM is applied and the distinction between
the CoBIT and ITIL implementations is frequently unclear. Ibaraki
explains that CoBIT provides the governance and metric structures
while ITIL delivers on the actual mechanics and “how-to” processes.
The author makes an interesting observation that it is wrong to
simplify COBIT as providing the ‘why’ and ITIL providing the ‘how’
because both ITSM mechanisms have considerable overlap and both
need to be used at the same time. I found this article very useful in
explaining the differences and similarities between these two aspects
of ITSM.
(Bad
Response)
Title and Reference:
http://en.wikipedia.org/wiki/IT_service_management
Summary:
This pages talks about ITSM. It says that IT service
management (ITSM) refers to the entirety of activities – directed
by policies, organized and structured in processes and
supporting procedures – that are performed by an organization or
part of an organization to plan, deliver, operate and control IT
services offered to customers. It is thus concerned with the
implementation of quality IT services that meet the needs of
customers, and is performed by the IT service provider through an
appropriate mix of people, process and information technology.
There are ten (10) tasks, one for each week: the tasks are detailed below. There
is a table to complete for each task. Please fill in the information required. An
example of a completed task is below. Note the first response is good – so aim
for something like this. The second response is not acceptable, so if you submit
anything like it, you won’t pass the assignment! The reasons? Poor resource
selection (Wikipedia), no Harvard reference and a block cut and paste from the
site (no citation, no original content).
Example
Task Find two resources that explain aspects of IT Service
Management.
(Good
Response)
Title and Reference:
COBIT versus ITIL
Ibaraki, S 2014, online, COBIT versus ITIL, viewed 29/01/2015,
<http://blogs.technet.com/b/cdnitmanagers/archive/2014/04/06/cobit-
versus-itil.aspx>.
Summary:
This resource is a blog entry discussing the differences between
CoBIT and ITIL. I chose this resource as there is a lot of confusion
about the way in which ITSM is applied and the distinction between
the CoBIT and ITIL implementations is frequently unclear. Ibaraki
explains that CoBIT provides the governance and metric structures
while ITIL delivers on the actual mechanics and “how-to” processes.
The author makes an interesting observation that it is wrong to
simplify COBIT as providing the ‘why’ and ITIL providing the ‘how’
because both ITSM mechanisms have considerable overlap and both
need to be used at the same time. I found this article very useful in
explaining the differences and similarities between these two aspects
of ITSM.
(Bad
Response)
Title and Reference:
http://en.wikipedia.org/wiki/IT_service_management
Summary:
This pages talks about ITSM. It says that IT service
management (ITSM) refers to the entirety of activities – directed
by policies, organized and structured in processes and
supporting procedures – that are performed by an organization or
part of an organization to plan, deliver, operate and control IT
services offered to customers. It is thus concerned with the
implementation of quality IT services that meet the needs of
customers, and is performed by the IT service provider through an
appropriate mix of people, process and information technology.

Note: Each resource summary should be a maximum of 300 words.
Week 1
Task The past decade has witnessed tremendous advances in
computing, wired and wireless communication, and storage
technologies. Discuss the main features and applications of
two mass storage technologies namely: direct-attached
storage and network-attached storage.
Summary Title and Reference:
Getting started with storage. Understanding SAN vs. NAS
vs. DAS
Olson, C 2014, online, Getting started with storage.
Understanding SAN vs. NAS vs. DAS, viewed 23/01/2018,
<https://vanillavideo.com/blog/2014/started-storage-
understanding-san-nas-das>.
Summary:
This resource is a blog entry which discusses the features
and applications of direct-attached storage and network-
attached storage. I chose this resource because it gives a
brief description of these two attached storage technologies.
This resource explains that in directly- attached storage the
storage devices are directly attached to the computer without
any network. While in the Network-attached storage the files
are shared over the network and hence it works as a
computer.
It also explains that directly-attached storage is used in
external hard drive which is connected through a USB cable
and the network-attached storage is used in computer
across a network for example, Ethernet. At a particular time
the network- attached storage can transfer the data to
multiple users but in direct-attached storage only one user
can connect at a time.
The features of DAS device are they are cheaper and it’s
easy to setup and configure. There is no need of any sort of
IP address and hence the transfer of data is fast. At the
same time, NAS devices do not depend on the number of
disks and their size. It also provides an easy way to provide
RAID redundancy to multiple users and hence provides
highest utilization of storage sources.
Disadvantages of DAS devices includes that it requires a
special hardware connection while the disadvantages of
NAS devices includes that it provide slow latency and require
an IP address.
I found this article because it explained the advantages and
disadvantages of both direct-attached storage devices and
network-attached storage devices.
Week 1
Task The past decade has witnessed tremendous advances in
computing, wired and wireless communication, and storage
technologies. Discuss the main features and applications of
two mass storage technologies namely: direct-attached
storage and network-attached storage.
Summary Title and Reference:
Getting started with storage. Understanding SAN vs. NAS
vs. DAS
Olson, C 2014, online, Getting started with storage.
Understanding SAN vs. NAS vs. DAS, viewed 23/01/2018,
<https://vanillavideo.com/blog/2014/started-storage-
understanding-san-nas-das>.
Summary:
This resource is a blog entry which discusses the features
and applications of direct-attached storage and network-
attached storage. I chose this resource because it gives a
brief description of these two attached storage technologies.
This resource explains that in directly- attached storage the
storage devices are directly attached to the computer without
any network. While in the Network-attached storage the files
are shared over the network and hence it works as a
computer.
It also explains that directly-attached storage is used in
external hard drive which is connected through a USB cable
and the network-attached storage is used in computer
across a network for example, Ethernet. At a particular time
the network- attached storage can transfer the data to
multiple users but in direct-attached storage only one user
can connect at a time.
The features of DAS device are they are cheaper and it’s
easy to setup and configure. There is no need of any sort of
IP address and hence the transfer of data is fast. At the
same time, NAS devices do not depend on the number of
disks and their size. It also provides an easy way to provide
RAID redundancy to multiple users and hence provides
highest utilization of storage sources.
Disadvantages of DAS devices includes that it requires a
special hardware connection while the disadvantages of
NAS devices includes that it provide slow latency and require
an IP address.
I found this article because it explained the advantages and
disadvantages of both direct-attached storage devices and
network-attached storage devices.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
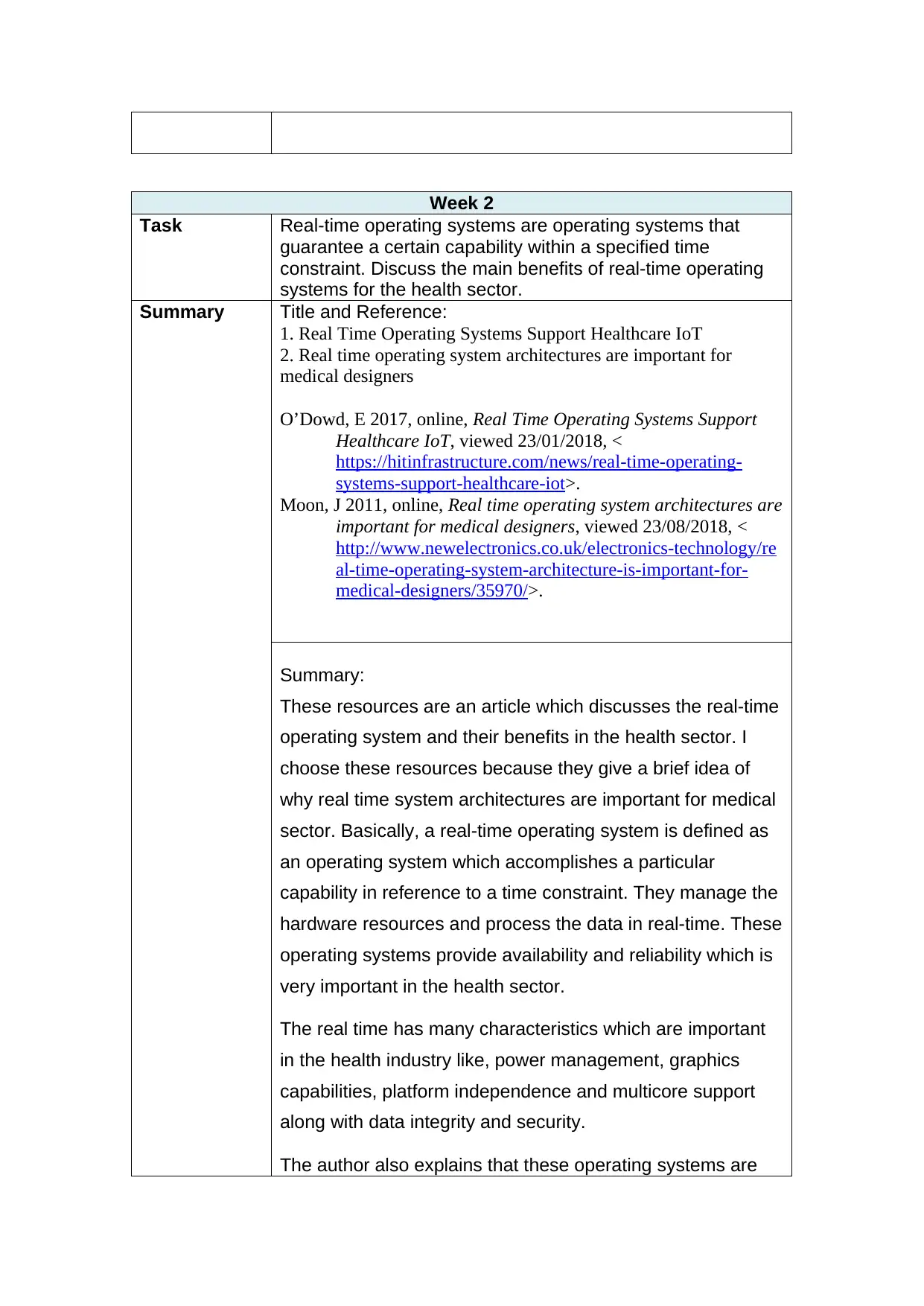
Week 2
Task Real-time operating systems are operating systems that
guarantee a certain capability within a specified time
constraint. Discuss the main benefits of real-time operating
systems for the health sector.
Summary Title and Reference:
1. Real Time Operating Systems Support Healthcare IoT
2. Real time operating system architectures are important for
medical designers
O’Dowd, E 2017, online, Real Time Operating Systems Support
Healthcare IoT, viewed 23/01/2018, <
https://hitinfrastructure.com/news/real-time-operating-
systems-support-healthcare-iot>.
Moon, J 2011, online, Real time operating system architectures are
important for medical designers, viewed 23/08/2018, <
http://www.newelectronics.co.uk/electronics-technology/re
al-time-operating-system-architecture-is-important-for-
medical-designers/35970/>.
Summary:
These resources are an article which discusses the real-time
operating system and their benefits in the health sector. I
choose these resources because they give a brief idea of
why real time system architectures are important for medical
sector. Basically, a real-time operating system is defined as
an operating system which accomplishes a particular
capability in reference to a time constraint. They manage the
hardware resources and process the data in real-time. These
operating systems provide availability and reliability which is
very important in the health sector.
The real time has many characteristics which are important
in the health industry like, power management, graphics
capabilities, platform independence and multicore support
along with data integrity and security.
The author also explains that these operating systems are
Task Real-time operating systems are operating systems that
guarantee a certain capability within a specified time
constraint. Discuss the main benefits of real-time operating
systems for the health sector.
Summary Title and Reference:
1. Real Time Operating Systems Support Healthcare IoT
2. Real time operating system architectures are important for
medical designers
O’Dowd, E 2017, online, Real Time Operating Systems Support
Healthcare IoT, viewed 23/01/2018, <
https://hitinfrastructure.com/news/real-time-operating-
systems-support-healthcare-iot>.
Moon, J 2011, online, Real time operating system architectures are
important for medical designers, viewed 23/08/2018, <
http://www.newelectronics.co.uk/electronics-technology/re
al-time-operating-system-architecture-is-important-for-
medical-designers/35970/>.
Summary:
These resources are an article which discusses the real-time
operating system and their benefits in the health sector. I
choose these resources because they give a brief idea of
why real time system architectures are important for medical
sector. Basically, a real-time operating system is defined as
an operating system which accomplishes a particular
capability in reference to a time constraint. They manage the
hardware resources and process the data in real-time. These
operating systems provide availability and reliability which is
very important in the health sector.
The real time has many characteristics which are important
in the health industry like, power management, graphics
capabilities, platform independence and multicore support
along with data integrity and security.
The author also explains that these operating systems are
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
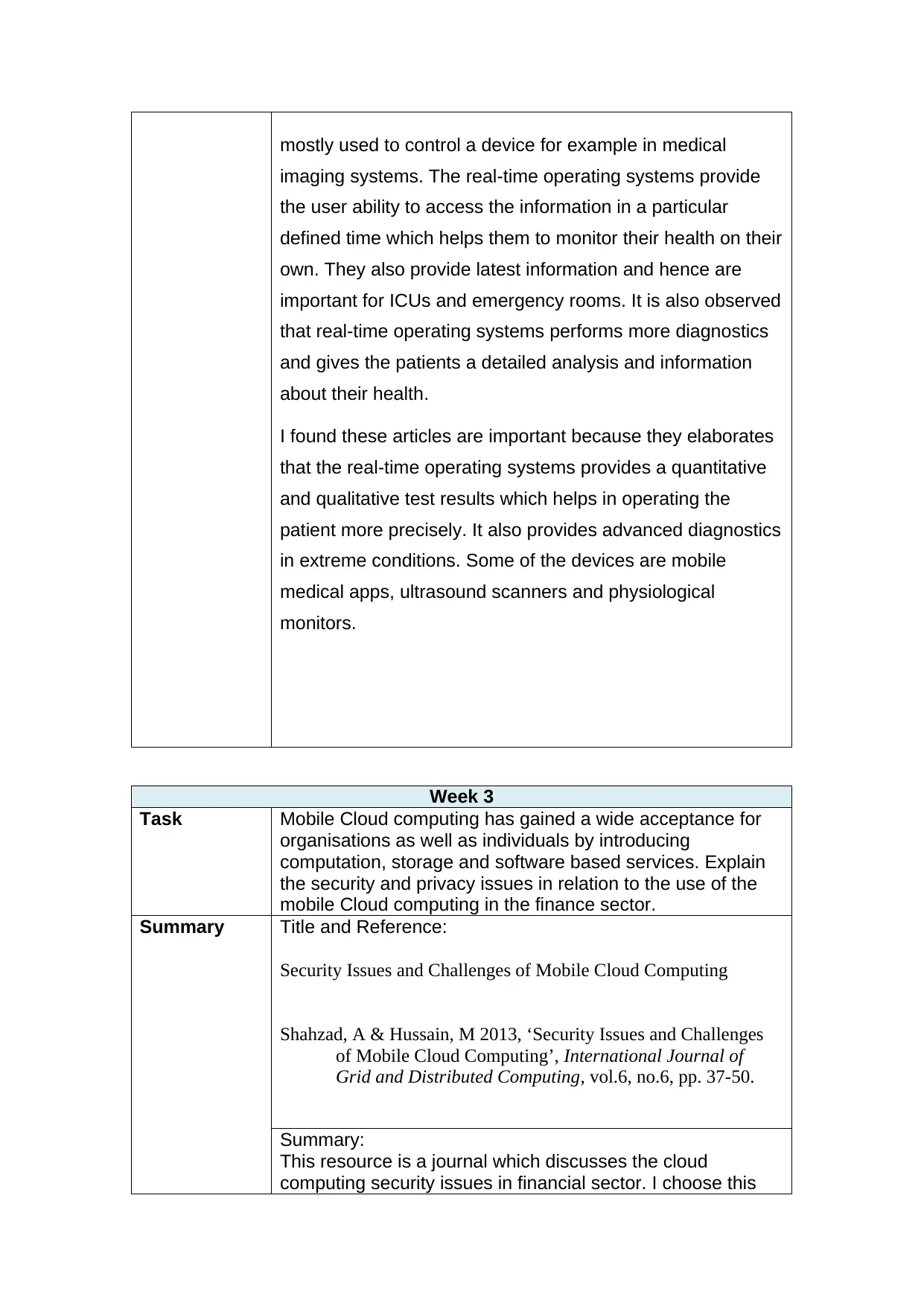
mostly used to control a device for example in medical
imaging systems. The real-time operating systems provide
the user ability to access the information in a particular
defined time which helps them to monitor their health on their
own. They also provide latest information and hence are
important for ICUs and emergency rooms. It is also observed
that real-time operating systems performs more diagnostics
and gives the patients a detailed analysis and information
about their health.
I found these articles are important because they elaborates
that the real-time operating systems provides a quantitative
and qualitative test results which helps in operating the
patient more precisely. It also provides advanced diagnostics
in extreme conditions. Some of the devices are mobile
medical apps, ultrasound scanners and physiological
monitors.
Week 3
Task Mobile Cloud computing has gained a wide acceptance for
organisations as well as individuals by introducing
computation, storage and software based services. Explain
the security and privacy issues in relation to the use of the
mobile Cloud computing in the finance sector.
Summary Title and Reference:
Security Issues and Challenges of Mobile Cloud Computing
Shahzad, A & Hussain, M 2013, ‘Security Issues and Challenges
of Mobile Cloud Computing’, International Journal of
Grid and Distributed Computing, vol.6, no.6, pp. 37-50.
Summary:
This resource is a journal which discusses the cloud
computing security issues in financial sector. I choose this
imaging systems. The real-time operating systems provide
the user ability to access the information in a particular
defined time which helps them to monitor their health on their
own. They also provide latest information and hence are
important for ICUs and emergency rooms. It is also observed
that real-time operating systems performs more diagnostics
and gives the patients a detailed analysis and information
about their health.
I found these articles are important because they elaborates
that the real-time operating systems provides a quantitative
and qualitative test results which helps in operating the
patient more precisely. It also provides advanced diagnostics
in extreme conditions. Some of the devices are mobile
medical apps, ultrasound scanners and physiological
monitors.
Week 3
Task Mobile Cloud computing has gained a wide acceptance for
organisations as well as individuals by introducing
computation, storage and software based services. Explain
the security and privacy issues in relation to the use of the
mobile Cloud computing in the finance sector.
Summary Title and Reference:
Security Issues and Challenges of Mobile Cloud Computing
Shahzad, A & Hussain, M 2013, ‘Security Issues and Challenges
of Mobile Cloud Computing’, International Journal of
Grid and Distributed Computing, vol.6, no.6, pp. 37-50.
Summary:
This resource is a journal which discusses the cloud
computing security issues in financial sector. I choose this
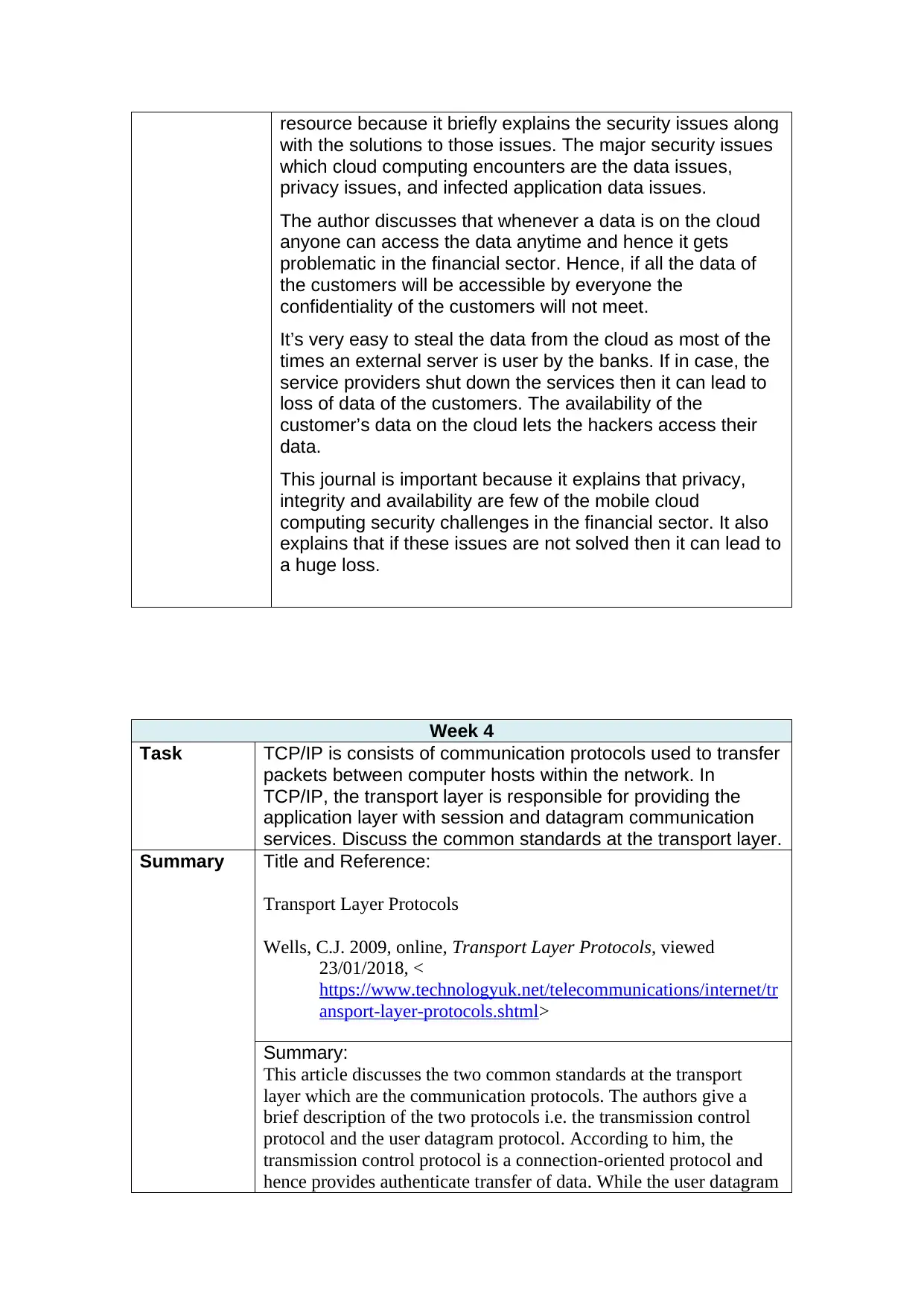
resource because it briefly explains the security issues along
with the solutions to those issues. The major security issues
which cloud computing encounters are the data issues,
privacy issues, and infected application data issues.
The author discusses that whenever a data is on the cloud
anyone can access the data anytime and hence it gets
problematic in the financial sector. Hence, if all the data of
the customers will be accessible by everyone the
confidentiality of the customers will not meet.
It’s very easy to steal the data from the cloud as most of the
times an external server is user by the banks. If in case, the
service providers shut down the services then it can lead to
loss of data of the customers. The availability of the
customer’s data on the cloud lets the hackers access their
data.
This journal is important because it explains that privacy,
integrity and availability are few of the mobile cloud
computing security challenges in the financial sector. It also
explains that if these issues are not solved then it can lead to
a huge loss.
Week 4
Task TCP/IP is consists of communication protocols used to transfer
packets between computer hosts within the network. In
TCP/IP, the transport layer is responsible for providing the
application layer with session and datagram communication
services. Discuss the common standards at the transport layer.
Summary Title and Reference:
Transport Layer Protocols
Wells, C.J. 2009, online, Transport Layer Protocols, viewed
23/01/2018, <
https://www.technologyuk.net/telecommunications/internet/tr
ansport-layer-protocols.shtml>
Summary:
This article discusses the two common standards at the transport
layer which are the communication protocols. The authors give a
brief description of the two protocols i.e. the transmission control
protocol and the user datagram protocol. According to him, the
transmission control protocol is a connection-oriented protocol and
hence provides authenticate transfer of data. While the user datagram
with the solutions to those issues. The major security issues
which cloud computing encounters are the data issues,
privacy issues, and infected application data issues.
The author discusses that whenever a data is on the cloud
anyone can access the data anytime and hence it gets
problematic in the financial sector. Hence, if all the data of
the customers will be accessible by everyone the
confidentiality of the customers will not meet.
It’s very easy to steal the data from the cloud as most of the
times an external server is user by the banks. If in case, the
service providers shut down the services then it can lead to
loss of data of the customers. The availability of the
customer’s data on the cloud lets the hackers access their
data.
This journal is important because it explains that privacy,
integrity and availability are few of the mobile cloud
computing security challenges in the financial sector. It also
explains that if these issues are not solved then it can lead to
a huge loss.
Week 4
Task TCP/IP is consists of communication protocols used to transfer
packets between computer hosts within the network. In
TCP/IP, the transport layer is responsible for providing the
application layer with session and datagram communication
services. Discuss the common standards at the transport layer.
Summary Title and Reference:
Transport Layer Protocols
Wells, C.J. 2009, online, Transport Layer Protocols, viewed
23/01/2018, <
https://www.technologyuk.net/telecommunications/internet/tr
ansport-layer-protocols.shtml>
Summary:
This article discusses the two common standards at the transport
layer which are the communication protocols. The authors give a
brief description of the two protocols i.e. the transmission control
protocol and the user datagram protocol. According to him, the
transmission control protocol is a connection-oriented protocol and
hence provides authenticate transfer of data. While the user datagram
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
protocol is a connectionless protocol which is an unreliable but it
adds minimum header.
The TCP adds header which comprises of the checksum and the
sequence number. It also makes use of a sliding window mechanism
and lets multiple segments to be transmitted, in short hands the flow
control.
The article also depicts that TCP uses a three-way handshake to make
up a connection. The basic features of TCP are: full duplex
communication, sequencing, flow control, timing and error handling.
On the contrary, UDP do not provide error recovery and flow control
and hence it does not assures the delivery of the packets. The
application layer protocols which use UDP connection are Simple
Network Management Protocol (SNMP), Routing Information
Protocol (RIP), Dynamic Host Configuration Protocol (DHCP) and
the Domain Name System (DNS).
It was found in this article that TCP is more reliable as compared to
UDP but for host-to-host delivery of small packets UDP is used in
place of TCP.
Week 5
Task The Internet of Things (IoT) is a system of interrelated
computing devices that are provided with unique identifiers
and the ability to transfer data over a network without
requiring human-to-human or human-to-computer
interaction. Discuss the cyber security challenges faced by
the health sector in this IoT era.
Summary Title and Reference:
Security of the Internet Of Things(IoT) in healthcare
Lewis, M 2017, online, Security of the Internet Of Things (IoT) in
healthcare, viewed 23/01/2018, <
https://www.nccgroup.trust/uk/about-us/newsroom-and-
events/blogs/2017/february/security-of-the-internet-of-
things-iot-in-healthcare/>.
Summary:
This resource is an article which discusses the cyber security issues
which are faced by the health sector in IoT era. The internet of
things provides the ability to transfer data over the network without
any human interaction. IoT is evolving in the health sector as it has
many benefits.
The various cyber security challenges discussed by the author
include big data and privacy. As the IoT comprises of the health
data of the patients which are collected from different types of
devices therefore it gets easy for the attacker to access the data
easily. This can put huge amount of patient’s confidentiality at risk.
The latest technology devices like the electronic health implants
adds minimum header.
The TCP adds header which comprises of the checksum and the
sequence number. It also makes use of a sliding window mechanism
and lets multiple segments to be transmitted, in short hands the flow
control.
The article also depicts that TCP uses a three-way handshake to make
up a connection. The basic features of TCP are: full duplex
communication, sequencing, flow control, timing and error handling.
On the contrary, UDP do not provide error recovery and flow control
and hence it does not assures the delivery of the packets. The
application layer protocols which use UDP connection are Simple
Network Management Protocol (SNMP), Routing Information
Protocol (RIP), Dynamic Host Configuration Protocol (DHCP) and
the Domain Name System (DNS).
It was found in this article that TCP is more reliable as compared to
UDP but for host-to-host delivery of small packets UDP is used in
place of TCP.
Week 5
Task The Internet of Things (IoT) is a system of interrelated
computing devices that are provided with unique identifiers
and the ability to transfer data over a network without
requiring human-to-human or human-to-computer
interaction. Discuss the cyber security challenges faced by
the health sector in this IoT era.
Summary Title and Reference:
Security of the Internet Of Things(IoT) in healthcare
Lewis, M 2017, online, Security of the Internet Of Things (IoT) in
healthcare, viewed 23/01/2018, <
https://www.nccgroup.trust/uk/about-us/newsroom-and-
events/blogs/2017/february/security-of-the-internet-of-
things-iot-in-healthcare/>.
Summary:
This resource is an article which discusses the cyber security issues
which are faced by the health sector in IoT era. The internet of
things provides the ability to transfer data over the network without
any human interaction. IoT is evolving in the health sector as it has
many benefits.
The various cyber security challenges discussed by the author
include big data and privacy. As the IoT comprises of the health
data of the patients which are collected from different types of
devices therefore it gets easy for the attacker to access the data
easily. This can put huge amount of patient’s confidentiality at risk.
The latest technology devices like the electronic health implants
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
and the fitness track records essential data of the patient’s body.
Electronic health implants allows wireless monitoring and
diagnosis of the data hence it gets very easy for the attacker to
connect to the internet and disrupt the operation of the health
implants. This way the financial health of the manufactures is also
at risk because they produce devices which have security flaws.
It has been concluded that the applications of the internet of things
like the patient monitoring and communication provides many
benefits but ef the attacker disrupts the monitoring and
communication signals then it will have very serious implications
on the health of the patient.
This article helped in understanding that although there are many
benefits of IoT in the health industry but at the same time there are
many cyber security challenges.
Week 6
Task Internet of Things (IoT) Cloud is a model designed to
facilitate the information society, enabling advanced services
by interconnecting physical and virtual things based on,
existing and evolving, interoperable information and
communication technologies through ennoblement of
ubiquitous, convenient, on-demand network access to a
shared pool of configurable computing resources. Explain
the importance of real time data capture capability, data
visualisation, data analytics, and API protocols in the
application of IoT Cloud.
Summary Title and Reference:
A survey of IoT platforms
Ray, P 206, A survey of IoT platforms, Future Computing and
Informatics Journal, vol.1, no.2,pp.35-46.
Summary:
This resource is a journal which describes the importance of real
time data capture capability, data visualization, data analytics and
API protocols in the application of IoT cloud.
The author describes that Internet of Things Cloud is a model
which is designed to facilitate on- demand network access to a
shared pool of configurable computing resources.
Along with this, the author that as the data is stored on the cloud
therefore it is important to have real time data capture capability. A
lot of data is stored at a particular place on a network so precise
data visualization is very essential.
As the data which is collected from the IoT devices is in different
Electronic health implants allows wireless monitoring and
diagnosis of the data hence it gets very easy for the attacker to
connect to the internet and disrupt the operation of the health
implants. This way the financial health of the manufactures is also
at risk because they produce devices which have security flaws.
It has been concluded that the applications of the internet of things
like the patient monitoring and communication provides many
benefits but ef the attacker disrupts the monitoring and
communication signals then it will have very serious implications
on the health of the patient.
This article helped in understanding that although there are many
benefits of IoT in the health industry but at the same time there are
many cyber security challenges.
Week 6
Task Internet of Things (IoT) Cloud is a model designed to
facilitate the information society, enabling advanced services
by interconnecting physical and virtual things based on,
existing and evolving, interoperable information and
communication technologies through ennoblement of
ubiquitous, convenient, on-demand network access to a
shared pool of configurable computing resources. Explain
the importance of real time data capture capability, data
visualisation, data analytics, and API protocols in the
application of IoT Cloud.
Summary Title and Reference:
A survey of IoT platforms
Ray, P 206, A survey of IoT platforms, Future Computing and
Informatics Journal, vol.1, no.2,pp.35-46.
Summary:
This resource is a journal which describes the importance of real
time data capture capability, data visualization, data analytics and
API protocols in the application of IoT cloud.
The author describes that Internet of Things Cloud is a model
which is designed to facilitate on- demand network access to a
shared pool of configurable computing resources.
Along with this, the author that as the data is stored on the cloud
therefore it is important to have real time data capture capability. A
lot of data is stored at a particular place on a network so precise
data visualization is very essential.
As the data which is collected from the IoT devices is in different
formats it is very difficult to order this data in a particular format.
Hence, data analytics is very important in the applications of IoT
devices. It provides visibility of operational factors an assist in
decision making process. Data virtualization is required to surface
the insights to the ends users because the available tolls are large in
number. This also allows the end users to explore more data from
the data warehouse.
The author mentioned that API tools are required in the
applications of IoT devices because they connect many
applications and devices with each other. It is very difficult to
deploy the APIs and proper skills are needed for its
implementation.
This journal concludes the importance of real time data capture
capability, data visualization, data analytics, and API protocols in
the application of IoT Cloud.
Week 7
Task A Social Network Service (SNS) is a kind of web service for
establishing a virtual connection between people with similar
interests, backgrounds, and activities. However, there are
different security and privacy threats that target every user of
social networking sites. Provide five solutions to deal with
these security threats.
Summary Title and Reference:
5 Social Media Security Risks and How to Avoid Them
Russell, J 2017, online, 5 Social Media Security Risks and How to
Avoid Them, viewed 23/01/2018, <
https://blog.hootsuite.com/social-media-security-for-
business/>.
Summary:
This resource is a blog entry which discusses the different security
and privacy threats of social networking sites along with the
solutions to deal with these problems. I choose this resource
because a brief description of the security threats is provided and a
precise solution to all the problems is concluded.
The author describes the different types of social media risks which
include human error, malicious apps and attacks, the phishing
scams and disrupted privacy settings. To avoid these security risks
he described many way for example,
1. Update your passwords- After a span of time keep updating
your passwords. Along with this use different password
management tools like two-factor authentication tool to
Hence, data analytics is very important in the applications of IoT
devices. It provides visibility of operational factors an assist in
decision making process. Data virtualization is required to surface
the insights to the ends users because the available tolls are large in
number. This also allows the end users to explore more data from
the data warehouse.
The author mentioned that API tools are required in the
applications of IoT devices because they connect many
applications and devices with each other. It is very difficult to
deploy the APIs and proper skills are needed for its
implementation.
This journal concludes the importance of real time data capture
capability, data visualization, data analytics, and API protocols in
the application of IoT Cloud.
Week 7
Task A Social Network Service (SNS) is a kind of web service for
establishing a virtual connection between people with similar
interests, backgrounds, and activities. However, there are
different security and privacy threats that target every user of
social networking sites. Provide five solutions to deal with
these security threats.
Summary Title and Reference:
5 Social Media Security Risks and How to Avoid Them
Russell, J 2017, online, 5 Social Media Security Risks and How to
Avoid Them, viewed 23/01/2018, <
https://blog.hootsuite.com/social-media-security-for-
business/>.
Summary:
This resource is a blog entry which discusses the different security
and privacy threats of social networking sites along with the
solutions to deal with these problems. I choose this resource
because a brief description of the security threats is provided and a
precise solution to all the problems is concluded.
The author describes the different types of social media risks which
include human error, malicious apps and attacks, the phishing
scams and disrupted privacy settings. To avoid these security risks
he described many way for example,
1. Update your passwords- After a span of time keep updating
your passwords. Along with this use different password
management tools like two-factor authentication tool to
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
authenticate your account.
2. Scan for any sort of threats- Make use of different types of
security software’s which can scan for threats. This
software’s makes easy for a user to detect the threats as it
sends continuous updates whenever it detects any sort of
scam, malware, virus or different security risks.
3. Regularly monitoring the accounts- Monitor your account
on a regular basis manually to check if there is any unusual
activity going on or not. A user can also make use of the
monitoring tools to check your accounts.
4. Keep updating the privacy settings- Regularly update the
privacy settings of your account. Keep a check on who
visited your profile and what activities are going on in your
account.
5. Use a firewall to secure the network- By using a firewall to
secure the network the unwanted traffic can be blocked
from entering the network for example viruses through
email. A personal firewall should be used to protect the
network.
This article provides the solutions to the security risks which are
encountered at different social networking sites.
Week 8
Task Big data has been considered to be a breakthrough
technological development over recent years. Big data is
based on large volumes of extensively varied data that are
generated, captured, and processed at high velocity. Discuss
the main challenges as well as the social and economic
values for organisations in adopting big data.
Summary Title and Reference:
Big Data: New Challenges and the Change of Organizational
Culture
Tuziak, R 2016, Big Data: New Challenges and the Change of
Organizational Culture, Opuscula Sociologica, vol.2,
pp.35-47.
Summary:
This resource is a journal which discusses the main challenges
which the organizations face in adopting the big data and the social
and economic values required in the organization to adopt big data.
The author has discussed that the main challenges which an
organization faces is in managing hadoop i.e. because it is very
difficult to implement hadoop. It requires many resources to
2. Scan for any sort of threats- Make use of different types of
security software’s which can scan for threats. This
software’s makes easy for a user to detect the threats as it
sends continuous updates whenever it detects any sort of
scam, malware, virus or different security risks.
3. Regularly monitoring the accounts- Monitor your account
on a regular basis manually to check if there is any unusual
activity going on or not. A user can also make use of the
monitoring tools to check your accounts.
4. Keep updating the privacy settings- Regularly update the
privacy settings of your account. Keep a check on who
visited your profile and what activities are going on in your
account.
5. Use a firewall to secure the network- By using a firewall to
secure the network the unwanted traffic can be blocked
from entering the network for example viruses through
email. A personal firewall should be used to protect the
network.
This article provides the solutions to the security risks which are
encountered at different social networking sites.
Week 8
Task Big data has been considered to be a breakthrough
technological development over recent years. Big data is
based on large volumes of extensively varied data that are
generated, captured, and processed at high velocity. Discuss
the main challenges as well as the social and economic
values for organisations in adopting big data.
Summary Title and Reference:
Big Data: New Challenges and the Change of Organizational
Culture
Tuziak, R 2016, Big Data: New Challenges and the Change of
Organizational Culture, Opuscula Sociologica, vol.2,
pp.35-47.
Summary:
This resource is a journal which discusses the main challenges
which the organizations face in adopting the big data and the social
and economic values required in the organization to adopt big data.
The author has discussed that the main challenges which an
organization faces is in managing hadoop i.e. because it is very
difficult to implement hadoop. It requires many resources to
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
implement it and manage it. The training of this technology is also
difficult because it’s a very vast area to study.
Another challenge is the scalability challenge because mostly the
organizations are not able to scale up and down the demands. As
big data works on servers and ultimately results in scalability
problems and the storage limitations. The addition of new servers
is quite expensive and time consuming and hence lets to the
disruption of the organization. Apart from this, the biggest
challenge is the data talent shortage because it is difficult to find
right people who have right skills to use this technology.
Establishing a team of skilled employees is an expensive process
and difficult.
The author also describes that the organizations have to change
their social and economic values to adapt big data. The employees
should be skilled then only they can make use of this technology. It
gets very important to adapt with the changing culture fo the
companies. The cost of implementing and maintain this technology
is very high and hence the organizations have to make a use of
budget. Adoption of big data requires change management,
coordination, communication and the organizational alignment
towards the new technology.
This journal describes all the challenges the organizations face and
the business change process they need to implement to adapt big
data.
Week 9
Task There has been a growing interest in the application of agile
and lean practices for software development. Discuss the
benefits of agile and lean practices and their impacts on
project constraints.
Summary Title and Reference:
The impacts of agile and lean practices on project constraints: A
tertiary study
Nurdiani, I., Börstler, J. and Fricker, S 2016, The impacts of agile
and lean practices on project constraints: A tertiary
study, Journal of Systems and Software, vol.119, pp.162-
183.
Summary:
The authors describes that agile practices provides a flexible and
interactive model and hence all the requirements of the
stakeholders and the customers is met easily. The lean approaches
eliminate waste and are used at the early stages of the project. The
agile practises reduce the project constraints because they mainly
focus on the people and the processes along with the tools. Lean
practices help in documenting the project plan at early stages and
hence reduces the chances of failures.
difficult because it’s a very vast area to study.
Another challenge is the scalability challenge because mostly the
organizations are not able to scale up and down the demands. As
big data works on servers and ultimately results in scalability
problems and the storage limitations. The addition of new servers
is quite expensive and time consuming and hence lets to the
disruption of the organization. Apart from this, the biggest
challenge is the data talent shortage because it is difficult to find
right people who have right skills to use this technology.
Establishing a team of skilled employees is an expensive process
and difficult.
The author also describes that the organizations have to change
their social and economic values to adapt big data. The employees
should be skilled then only they can make use of this technology. It
gets very important to adapt with the changing culture fo the
companies. The cost of implementing and maintain this technology
is very high and hence the organizations have to make a use of
budget. Adoption of big data requires change management,
coordination, communication and the organizational alignment
towards the new technology.
This journal describes all the challenges the organizations face and
the business change process they need to implement to adapt big
data.
Week 9
Task There has been a growing interest in the application of agile
and lean practices for software development. Discuss the
benefits of agile and lean practices and their impacts on
project constraints.
Summary Title and Reference:
The impacts of agile and lean practices on project constraints: A
tertiary study
Nurdiani, I., Börstler, J. and Fricker, S 2016, The impacts of agile
and lean practices on project constraints: A tertiary
study, Journal of Systems and Software, vol.119, pp.162-
183.
Summary:
The authors describes that agile practices provides a flexible and
interactive model and hence all the requirements of the
stakeholders and the customers is met easily. The lean approaches
eliminate waste and are used at the early stages of the project. The
agile practises reduce the project constraints because they mainly
focus on the people and the processes along with the tools. Lean
practices help in documenting the project plan at early stages and
hence reduces the chances of failures.
The various benefits of agile and lean practises described by the
author are that they respond to the change easily as it focuses on
incremental changes. The customers get the solution to their
problems on highest priority. Agile practises also accepts
uncertainty easily because more and more information is
discovered as the project goes on, this also helps in experimenting
new things on the project. The review cycle of agile projects is fast
as compared to traditional models because it is ensured timely that
the work is getting complete on time. If the work get completes
before time it gets easy to review it and make changes.
Another benefits of these practises is that the work is delivered to
the end users iteratively i.e. from time to time rather than
delivering the project as a whole. This helps in providing sufficient
functionality of the project. This methodology also leads to the
development of skilled employees as they work effectively and
take risks. These practices increase the chances of success because
the work is completed in the most effective way.
This journal completely defines the benefits of agile and lean
practises and how they increase the chances of success and solves
the project constraints.
Week 10
Task The availability and implementation of information and
communication technologies (ICT) is increasingly vital to all
dimensions of a nation’s inclusive, equitable and sustainable
economic development and growth strategies. Discuss how
ICT is fundamentally changing the nature of economic,
environmental, and social relationships globally.
Summary Title and Reference:
ICT and the environment in developing countries: opportunities
and developments
Houghton, J 2009, online, ICT and the environment in developing
countries: opportunities and developments, viewed
23/01/2018, < http://www.oecd.org/ict/4d/43631894.pdf>.
Summary:
This resource is an article which discusses the increasingly
implementation of information and communication technologies.
The author has discussed how ICT is fundamentally changing the
nature of economic, environmental and social relationships
globally.
The ICT is changing the social relationships globally as now the
citizens can connect to each other easily. The citizens can also
bypass the legal constraints an access the information easily.
Economically, different countries connect with each other and can
communicate easily. They can also import and export goods on a
large scale. The small business is able to use the technology easily
and in an effective manner. The ICT sector is contributing to the
author are that they respond to the change easily as it focuses on
incremental changes. The customers get the solution to their
problems on highest priority. Agile practises also accepts
uncertainty easily because more and more information is
discovered as the project goes on, this also helps in experimenting
new things on the project. The review cycle of agile projects is fast
as compared to traditional models because it is ensured timely that
the work is getting complete on time. If the work get completes
before time it gets easy to review it and make changes.
Another benefits of these practises is that the work is delivered to
the end users iteratively i.e. from time to time rather than
delivering the project as a whole. This helps in providing sufficient
functionality of the project. This methodology also leads to the
development of skilled employees as they work effectively and
take risks. These practices increase the chances of success because
the work is completed in the most effective way.
This journal completely defines the benefits of agile and lean
practises and how they increase the chances of success and solves
the project constraints.
Week 10
Task The availability and implementation of information and
communication technologies (ICT) is increasingly vital to all
dimensions of a nation’s inclusive, equitable and sustainable
economic development and growth strategies. Discuss how
ICT is fundamentally changing the nature of economic,
environmental, and social relationships globally.
Summary Title and Reference:
ICT and the environment in developing countries: opportunities
and developments
Houghton, J 2009, online, ICT and the environment in developing
countries: opportunities and developments, viewed
23/01/2018, < http://www.oecd.org/ict/4d/43631894.pdf>.
Summary:
This resource is an article which discusses the increasingly
implementation of information and communication technologies.
The author has discussed how ICT is fundamentally changing the
nature of economic, environmental and social relationships
globally.
The ICT is changing the social relationships globally as now the
citizens can connect to each other easily. The citizens can also
bypass the legal constraints an access the information easily.
Economically, different countries connect with each other and can
communicate easily. They can also import and export goods on a
large scale. The small business is able to use the technology easily
and in an effective manner. The ICT sector is contributing to the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





