COIT 20246 Assignment: Exploring Networking Technologies and Trends
VerifiedAdded on 2019/11/20
|10
|3670
|421
Homework Assignment
AI Summary
This assignment, submitted for COIT 20246, delves into various aspects of computer and networking technologies. The assignment comprises ten weekly tasks, each requiring a summary of a resource related to the week's topic. The topics covered include the contributions of individuals like John von Neumann and Bill Gates to computer architecture and operating systems respectively. It explores the evolution of the internet, focusing on networks like BITNET, and examines Layer 2 protocols such as ARP. Furthermore, the assignment investigates the impact of hackers, exemplified by Kevin Mitnick, and forecasts future networking technologies like quantum networking. The assignment also touches upon the history of social media platforms like Facebook. Each summary is approximately 200-300 words, and the assignment emphasizes the use of literature and online resources, requiring proper citation in Harvard format. The goal is to analyze and synthesize information on these key areas, fostering a comprehensive understanding of the field.
COIT 20246 ASSIGNMENT SUBMISSION
Due date: Thursday Week 11 (2PM AEST)
Part: Written Assessment
Weighting: 30% of total assessment.
Submission: Electronic (see course website for details)
Instructions
It will be necessary to use literature/online resources to complete this
assignment, please ensure you cite and reference any such materials using
the Harvard format.
DO NOT copy content directly from either the text or Internet resources: this
assignment is to be in your own words. You will lose marks if you do not
use your own words!
Please complete your assignment using this submission template file,
inserting your responses where indicated.
DO NOT delete the marking criteria page – changes are permitted to the
formatting of other pages including the headers and footers.
Please fill in the following details:
Student Name
Student Number
Due date: Thursday Week 11 (2PM AEST)
Part: Written Assessment
Weighting: 30% of total assessment.
Submission: Electronic (see course website for details)
Instructions
It will be necessary to use literature/online resources to complete this
assignment, please ensure you cite and reference any such materials using
the Harvard format.
DO NOT copy content directly from either the text or Internet resources: this
assignment is to be in your own words. You will lose marks if you do not
use your own words!
Please complete your assignment using this submission template file,
inserting your responses where indicated.
DO NOT delete the marking criteria page – changes are permitted to the
formatting of other pages including the headers and footers.
Please fill in the following details:
Student Name
Student Number
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Tasks
There are ten (10) tasks, one for each week: the tasks are detailed below. There is a
table to complete for each task. Please fill in the information required.
Note: Each resource summary should be around 200-300 words.
Week 1
The text discusses the elements of modern computing architecture however is largely silent
on the individuals who played a role in its development. Find and summarise a resource that
describes ONE such individual. The individual should have had a significant influence on the
development of computers and/or components of modern computing architecture.
Title: Mordern computer Architecture
Reference: History, T. 2017. John von Neumann - Computing History. [online]
Computinghistory.org.uk. Available at: http://www.computinghistory.org.uk/det/3665/john-von-
neumann
URL : http://www.computinghistory.org.uk/det/3665/john-von-neumann/
Summary: John von Neumann one of the famous mathematician in the field of architecture
related to modern computers of the architecture. The article in the context is related to the
overview of the architecture related to the modern computer which would be very much
incomplete without the authors contribution in the field. It is directly stated in the article that
due to the authors contribution in the indicated field the modern computer which was
relatively very fast was invented. He suggested that the modern computer main architecture
can be fixed which can be very much affective in the same period of time. The sequential flow
of control which is controlled by the conditional flow, at any time initialization and interruption
in the flow of control can be done. Mainly by utilizing the processing unit of the system, a
model was proposed which had the same memory allocation in order to make it more
affective. This concept which is related to the system is known as turning machine, which
mainly consist of architecture which is sequential which is based on the concept of non
veumann concept of architecture.
Week 2
The text discusses the components and activities of operating systems however is largely
silent on the individuals who played a role in their development. Find and summarise a
resource that describes ONE such individual. The individual should have had a significant
influence on the writing or development of operating systems.
Title: Bill gates influencing windows operating system
Reference: Influentialleadership.com. 2017. Bill Gates — Influential Leadership. [online]
URL : http://influentialleadership.com/bill-gates/
Summary: the main focus point of the article which is taken above is the influencing factor
which is elated to Bill Gates related to the field of modern architecture relating to the
operating system. The main aspect due to which the article is chosen is that the author plays
a very vital role in the pre-existent field of the concerned area. Bill gates is considered one of
the pioneers in the field of modern computer tis is mainly due to the factor that the windows
were first introduced by him. With the linking of the windows concept with the modern
computer architecture the name Bill Gates became very much famous and very much
renounced. Due to the implementation the overall concept with the field became very much
There are ten (10) tasks, one for each week: the tasks are detailed below. There is a
table to complete for each task. Please fill in the information required.
Note: Each resource summary should be around 200-300 words.
Week 1
The text discusses the elements of modern computing architecture however is largely silent
on the individuals who played a role in its development. Find and summarise a resource that
describes ONE such individual. The individual should have had a significant influence on the
development of computers and/or components of modern computing architecture.
Title: Mordern computer Architecture
Reference: History, T. 2017. John von Neumann - Computing History. [online]
Computinghistory.org.uk. Available at: http://www.computinghistory.org.uk/det/3665/john-von-
neumann
URL : http://www.computinghistory.org.uk/det/3665/john-von-neumann/
Summary: John von Neumann one of the famous mathematician in the field of architecture
related to modern computers of the architecture. The article in the context is related to the
overview of the architecture related to the modern computer which would be very much
incomplete without the authors contribution in the field. It is directly stated in the article that
due to the authors contribution in the indicated field the modern computer which was
relatively very fast was invented. He suggested that the modern computer main architecture
can be fixed which can be very much affective in the same period of time. The sequential flow
of control which is controlled by the conditional flow, at any time initialization and interruption
in the flow of control can be done. Mainly by utilizing the processing unit of the system, a
model was proposed which had the same memory allocation in order to make it more
affective. This concept which is related to the system is known as turning machine, which
mainly consist of architecture which is sequential which is based on the concept of non
veumann concept of architecture.
Week 2
The text discusses the components and activities of operating systems however is largely
silent on the individuals who played a role in their development. Find and summarise a
resource that describes ONE such individual. The individual should have had a significant
influence on the writing or development of operating systems.
Title: Bill gates influencing windows operating system
Reference: Influentialleadership.com. 2017. Bill Gates — Influential Leadership. [online]
URL : http://influentialleadership.com/bill-gates/
Summary: the main focus point of the article which is taken above is the influencing factor
which is elated to Bill Gates related to the field of modern architecture relating to the
operating system. The main aspect due to which the article is chosen is that the author plays
a very vital role in the pre-existent field of the concerned area. Bill gates is considered one of
the pioneers in the field of modern computer tis is mainly due to the factor that the windows
were first introduced by him. With the linking of the windows concept with the modern
computer architecture the name Bill Gates became very much famous and very much
renounced. Due to the implementation the overall concept with the field became very much

famous and it became a pre dominant player in the field of computer. Bill gates was
considered one of the wealthiest person in the field due to his innovations and expertise with
the knowledge of computers. He started his own organisation which was known as Microsoft.
He graduated in the year 1973 and enrolled into Harvard university. The maximum he used to
spend was with his team in the research unit rather than putting emphasis on the study
syllabus.
considered one of the wealthiest person in the field due to his innovations and expertise with
the knowledge of computers. He started his own organisation which was known as Microsoft.
He graduated in the year 1973 and enrolled into Harvard university. The maximum he used to
spend was with his team in the research unit rather than putting emphasis on the study
syllabus.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Week 3
The Internet didn’t just appear – it was an evolution from earlier networks. Find and
summarise a resource that describes ONE of the networks that led to the development of the
modern Internet.
Title: Influence of BITNET in the advancement of modern Internet
Reference : Livinginternet.com. 2017. BITNET History - Ira Fuchs, Greydon Freeman, Mailing
Lists, Usenet. [online] Available at: https://www.livinginternet.com/u/ui_bitnet.htm
URL : https://www.livinginternet.com/u/ui_bitnet.htm
Summary: The article directly puts emphasis on the concept of BITNET. The BITNET concept
and the modern internet go hand in hand. The reason of choosing the article is that BITMAP
is considered as one of the most important factors when relating to the modern computer
architecture. It can be stated that the BITMAP is a primary factor when relating to the concept
of the internet. The main working aspect of the technology is that it can forward and store
network which is quite similar to the technology of UseNet. When relating to the full form of
the BITMAP it is because of the internet. It is basically based on the concept of the IBM’s
concept of VNET email system and the sub system which is related to the remote spooling
communication. Later on the emulation of the technology of the RSCS was done into other
operating system’s which are DEC VMS and a portion of UNIX which was an extended
portion which is related to the BITMAP. The BITMAP concept introduced many concepts
which can be actively used in the participation. The concept can be varied into many fields,
and it included more than one service which was attached to it. The overall concept created a
backbone to the concept of TCP/IP protocol of the computer system.
Week 4
Ethernet is an example of a Layer Two (L2) data link protocol that is discussed in the text.
Find and summarise a resource that describes the features and uses of ONE other L2
protocol that is not discussed in the text (i.e. NOT Ethernet).
Title : Address Resolution Protocol (ARP)
Reference: Lifewire. 2017. What Address Resolution Protocol (ARP) does for your computer
network. [online] Available at: https://www.lifewire.com/address-resolution-protocol-817941
URL: https://www.lifewire.com/address-resolution-protocol-817941
Summary: This article which is selected above puts direct emphasis on the concept of the
most important and common layer 2 protocol which is termed as the address Resolution
Protocol (ARP). The article is mainly chosen because the address Resolution Protocol (ARP)
is considered as the most primary and useful protocol. The address Resolution Protocol
(ARP) is considered as the integral part in the running of the of the IP network which are
mainly used in the Ethernet and also can be related to the concept of Wi-Fi. Taking into
account the history of the technology it was developed in the year 1980 mainly with the main
point of creating an address resolution protocol. The address Resolution Protocol (ARP) main
function is to convert the internet protocol address to the physical network. The technology is
mainly implemented in the ATM, which are mainly physical type and the token ring.
Considering the advantage related to the implantation is that it manages the overall
connection of the system irrespective of the physical device in particular which are connected
with each other. The address Resolution Protocol (ARP) performs its main activity in the layer
two protocol of the OSI model. When the address Resolution Protocol (ARP) is maintained in
every device it helps in mapping of the Internet protocol to the MAC address mapping. Based
on the overall concept of the address Resolution Protocol (ARP) an inverse of the address
Resolution Protocol (ARP) and a reverse of address Resolution Protocol (ARP)is also
developed.
The Internet didn’t just appear – it was an evolution from earlier networks. Find and
summarise a resource that describes ONE of the networks that led to the development of the
modern Internet.
Title: Influence of BITNET in the advancement of modern Internet
Reference : Livinginternet.com. 2017. BITNET History - Ira Fuchs, Greydon Freeman, Mailing
Lists, Usenet. [online] Available at: https://www.livinginternet.com/u/ui_bitnet.htm
URL : https://www.livinginternet.com/u/ui_bitnet.htm
Summary: The article directly puts emphasis on the concept of BITNET. The BITNET concept
and the modern internet go hand in hand. The reason of choosing the article is that BITMAP
is considered as one of the most important factors when relating to the modern computer
architecture. It can be stated that the BITMAP is a primary factor when relating to the concept
of the internet. The main working aspect of the technology is that it can forward and store
network which is quite similar to the technology of UseNet. When relating to the full form of
the BITMAP it is because of the internet. It is basically based on the concept of the IBM’s
concept of VNET email system and the sub system which is related to the remote spooling
communication. Later on the emulation of the technology of the RSCS was done into other
operating system’s which are DEC VMS and a portion of UNIX which was an extended
portion which is related to the BITMAP. The BITMAP concept introduced many concepts
which can be actively used in the participation. The concept can be varied into many fields,
and it included more than one service which was attached to it. The overall concept created a
backbone to the concept of TCP/IP protocol of the computer system.
Week 4
Ethernet is an example of a Layer Two (L2) data link protocol that is discussed in the text.
Find and summarise a resource that describes the features and uses of ONE other L2
protocol that is not discussed in the text (i.e. NOT Ethernet).
Title : Address Resolution Protocol (ARP)
Reference: Lifewire. 2017. What Address Resolution Protocol (ARP) does for your computer
network. [online] Available at: https://www.lifewire.com/address-resolution-protocol-817941
URL: https://www.lifewire.com/address-resolution-protocol-817941
Summary: This article which is selected above puts direct emphasis on the concept of the
most important and common layer 2 protocol which is termed as the address Resolution
Protocol (ARP). The article is mainly chosen because the address Resolution Protocol (ARP)
is considered as the most primary and useful protocol. The address Resolution Protocol
(ARP) is considered as the integral part in the running of the of the IP network which are
mainly used in the Ethernet and also can be related to the concept of Wi-Fi. Taking into
account the history of the technology it was developed in the year 1980 mainly with the main
point of creating an address resolution protocol. The address Resolution Protocol (ARP) main
function is to convert the internet protocol address to the physical network. The technology is
mainly implemented in the ATM, which are mainly physical type and the token ring.
Considering the advantage related to the implantation is that it manages the overall
connection of the system irrespective of the physical device in particular which are connected
with each other. The address Resolution Protocol (ARP) performs its main activity in the layer
two protocol of the OSI model. When the address Resolution Protocol (ARP) is maintained in
every device it helps in mapping of the Internet protocol to the MAC address mapping. Based
on the overall concept of the address Resolution Protocol (ARP) an inverse of the address
Resolution Protocol (ARP) and a reverse of address Resolution Protocol (ARP)is also
developed.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Week 5
The text mentions the role of hackers in attacks on networked infrastructure. Find and
summarise a resource that describes ONE famous or well-known hacker.
Title: Famous hacker Kevin Mitnick
Reference: Knowbe4.com. 2017. Kevin Mitnick | KnowBe4. [online] Available at:
https://www.knowbe4.com/products/who-is-kevin-mitnick/
URL : https://www.knowbe4.com/products/who-is-kevin-mitnick/
Summary: The role of the hacker is the main point of focus in the above stated article. When
hackers term is taken into consideration the first name which comes to the mind is Kevin
Mitnick. The article on the other hand puts direct emphasis on the characteristics of the
hackers. Kevin Mitnick was considered as the most renounced name in the world of the
hacking. He has been involved in many activities which mainly comprised of bypassing the
security of a computer system. The role of the hacker can be subdivided into two parts one
being an active hacker and on the other hand it is passive hacker. The active hacker’s role is
to get the message and modify the overall message and the passive hacker just gets the
message and does not involve any modification into the aspect. Due to this factor the active
hackers can be detected very easily and the passive hackers are very much difficult to detect.
Where kevin is concern, he was involved in both type of hacking activity. From the above
discussion it can be conducted that kevin is one of the biggest hackers of all times who was
involved in various type of hacking activity and because of the activity he was also punished
by law.
The text mentions the role of hackers in attacks on networked infrastructure. Find and
summarise a resource that describes ONE famous or well-known hacker.
Title: Famous hacker Kevin Mitnick
Reference: Knowbe4.com. 2017. Kevin Mitnick | KnowBe4. [online] Available at:
https://www.knowbe4.com/products/who-is-kevin-mitnick/
URL : https://www.knowbe4.com/products/who-is-kevin-mitnick/
Summary: The role of the hacker is the main point of focus in the above stated article. When
hackers term is taken into consideration the first name which comes to the mind is Kevin
Mitnick. The article on the other hand puts direct emphasis on the characteristics of the
hackers. Kevin Mitnick was considered as the most renounced name in the world of the
hacking. He has been involved in many activities which mainly comprised of bypassing the
security of a computer system. The role of the hacker can be subdivided into two parts one
being an active hacker and on the other hand it is passive hacker. The active hacker’s role is
to get the message and modify the overall message and the passive hacker just gets the
message and does not involve any modification into the aspect. Due to this factor the active
hackers can be detected very easily and the passive hackers are very much difficult to detect.
Where kevin is concern, he was involved in both type of hacking activity. From the above
discussion it can be conducted that kevin is one of the biggest hackers of all times who was
involved in various type of hacking activity and because of the activity he was also punished
by law.
Week 6
Society is increasingly reliant on networks and network technologies but they are evolving at
a rapid pace. Find and summarise a resource that describes ONE example of a future
networking technology or trend that will impact society.
Title : Quantum networking system
Reference: Ieeexplore.ieee.org. 2017. Quantum networking and internetworking - IEEE
Journals & Magazine. [online] Available at: http://ieeexplore.ieee.org/document/6246754/
URL : http://ieeexplore.ieee.org/document/6246754/
Summary: The article puts direct limelight on the prospective of the quantum network
computing phenomenon and its direct implementation of the quantum technology which can
be applied to the future which related to network system. It can be stated that the future of the
networking system is directly dependent on the implementation of the quantum technology.
There are mainly three advantages that can be related to the topic. One of the most important
advantage that can be related to the implementation of the technology is directly making te
system more secured. In any system the security of the system plays a very vital role in every
aspect. The main theory of the quantum lies on the concept of qubits. The quantum physical
is mainly used as method in order to detect the eavesdropping. It can make the system more
and more advanced with making the system well isochronized with the technology of the
quantum. It also helps in creating a distributed data system which can be used in order to
make the numerical quantum computation possible which can achieve a much faster
response in the networking system. The teleportation method which is involved in the process
can create a revolution with regards to the communication system. From the above
discussion it can be concluded that the quantum technology can be a successful
implementation in the future related to the network system.
Week 7
The text mentions social business and the impact of the use of social networking platforms.
Find and summarise a resource that describes the history of the development of ONE such
social media platform.
Title : Brief history of Facebook
Reference: Phillips, S. 2017. A brief history of Facebook. [online] the Guardian. Available at:
https://www.theguardian.com/technology/2007/jul/25/media.newmedia
URL: https://www.theguardian.com/technology/2007/jul/25/media.newmedia
Summary: In this article the social networking site which has renovated the world, is taken
into account. Facebook comes among the biggest name in the field of social media. This
article is chosen due to the fact that the Facebook have altered the life of the people in many
aspects. Mark Zuckerberg is the founder and the owner of the Facebook, and he initiated the
social media site from a dormitory of the Harvard university. There are many expansion
technique that are related the Facebook history from its origin in the year 2004.it is one of the
fastest growing social networking site that exist in the recent times. Mark first created a social
networking site with the help of the website of the Harvard university and created a fashmash
of the site and later on the site was named as Facebook. In the recent update Facebook have
implemented many new technological aspect into it which includes haring of video, pictures
post or text. People with the text and the post can revert with their liking and comment on
them if they have any option regarding it. People can also chat and share their current
location with the aspect. Zuckerberg refuses to sell his company to google and to other giants
in the initial stage of the development of the company and on the other hand he refused to
post any advertisement in this regard.
Society is increasingly reliant on networks and network technologies but they are evolving at
a rapid pace. Find and summarise a resource that describes ONE example of a future
networking technology or trend that will impact society.
Title : Quantum networking system
Reference: Ieeexplore.ieee.org. 2017. Quantum networking and internetworking - IEEE
Journals & Magazine. [online] Available at: http://ieeexplore.ieee.org/document/6246754/
URL : http://ieeexplore.ieee.org/document/6246754/
Summary: The article puts direct limelight on the prospective of the quantum network
computing phenomenon and its direct implementation of the quantum technology which can
be applied to the future which related to network system. It can be stated that the future of the
networking system is directly dependent on the implementation of the quantum technology.
There are mainly three advantages that can be related to the topic. One of the most important
advantage that can be related to the implementation of the technology is directly making te
system more secured. In any system the security of the system plays a very vital role in every
aspect. The main theory of the quantum lies on the concept of qubits. The quantum physical
is mainly used as method in order to detect the eavesdropping. It can make the system more
and more advanced with making the system well isochronized with the technology of the
quantum. It also helps in creating a distributed data system which can be used in order to
make the numerical quantum computation possible which can achieve a much faster
response in the networking system. The teleportation method which is involved in the process
can create a revolution with regards to the communication system. From the above
discussion it can be concluded that the quantum technology can be a successful
implementation in the future related to the network system.
Week 7
The text mentions social business and the impact of the use of social networking platforms.
Find and summarise a resource that describes the history of the development of ONE such
social media platform.
Title : Brief history of Facebook
Reference: Phillips, S. 2017. A brief history of Facebook. [online] the Guardian. Available at:
https://www.theguardian.com/technology/2007/jul/25/media.newmedia
URL: https://www.theguardian.com/technology/2007/jul/25/media.newmedia
Summary: In this article the social networking site which has renovated the world, is taken
into account. Facebook comes among the biggest name in the field of social media. This
article is chosen due to the fact that the Facebook have altered the life of the people in many
aspects. Mark Zuckerberg is the founder and the owner of the Facebook, and he initiated the
social media site from a dormitory of the Harvard university. There are many expansion
technique that are related the Facebook history from its origin in the year 2004.it is one of the
fastest growing social networking site that exist in the recent times. Mark first created a social
networking site with the help of the website of the Harvard university and created a fashmash
of the site and later on the site was named as Facebook. In the recent update Facebook have
implemented many new technological aspect into it which includes haring of video, pictures
post or text. People with the text and the post can revert with their liking and comment on
them if they have any option regarding it. People can also chat and share their current
location with the aspect. Zuckerberg refuses to sell his company to google and to other giants
in the initial stage of the development of the company and on the other hand he refused to
post any advertisement in this regard.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Week 8
With the advent of mass data collection and storage has come data mining. Find and
summarise a resource that describes ONE example where data mining has been used
successfully by a business. You should not use any examples covered in the textbook.
Title: Implementation of data mining in retailing business
Reference: Saravanan, G. 2017. [online] Available at:
http://www.coolavenues.com/marketing-zone/role-of-data-mining-in-retail-sector
URL: http://www.coolavenues.com/marketing-zone/role-of-data-mining-in-retail-sector
Summary: The article puts direct emphasis on the aspect of the role of the data mining in the
field of business related to mining. There are many advantages that can be related to the
topic. Data mining can be considered as a method which is related to the information system,
by this mean the processor can take action regarding a particular style or type of useful data
from a database or large amount of data. Data mining can be implemented in order to detect
the requirement of the user from the previously stored data ij the database. It can also act as
a mean of detecting the behaviour of the customer, trends that the customer are following and
the customer satisfaction level or different ways of improving the standard of the work that is
expected from the user. The information which is extracted from the process can be used to
strategically implement different processes related to the concept. It is very much important to
take into account the different production techniques which is related to the company. The
best implementation of the data mining concept is in the CR as CRM deals with the customer
relationship management. It can directly help in improving the loyalty which is related to the
customer, gaining the very important aspect which is the customer insight, retaining the
customer and also in implementing focused strategies which is related to the customer.
With the advent of mass data collection and storage has come data mining. Find and
summarise a resource that describes ONE example where data mining has been used
successfully by a business. You should not use any examples covered in the textbook.
Title: Implementation of data mining in retailing business
Reference: Saravanan, G. 2017. [online] Available at:
http://www.coolavenues.com/marketing-zone/role-of-data-mining-in-retail-sector
URL: http://www.coolavenues.com/marketing-zone/role-of-data-mining-in-retail-sector
Summary: The article puts direct emphasis on the aspect of the role of the data mining in the
field of business related to mining. There are many advantages that can be related to the
topic. Data mining can be considered as a method which is related to the information system,
by this mean the processor can take action regarding a particular style or type of useful data
from a database or large amount of data. Data mining can be implemented in order to detect
the requirement of the user from the previously stored data ij the database. It can also act as
a mean of detecting the behaviour of the customer, trends that the customer are following and
the customer satisfaction level or different ways of improving the standard of the work that is
expected from the user. The information which is extracted from the process can be used to
strategically implement different processes related to the concept. It is very much important to
take into account the different production techniques which is related to the company. The
best implementation of the data mining concept is in the CR as CRM deals with the customer
relationship management. It can directly help in improving the loyalty which is related to the
customer, gaining the very important aspect which is the customer insight, retaining the
customer and also in implementing focused strategies which is related to the customer.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Week 9
One of the greatest success stories in application development in recent times has been the
popularity of mobile apps. Find and summarise a resource that describes the story of ONE
successful mobile app developer.
Title: Successful young app developer Robert Nay
Reference: Sutter, J. 2017. 14-year-old creates 'Bubble Ball,' iTunes' most popular free app.
[online] Edition.cnn.com. Available at:
http://edition.cnn.com/2011/TECH/mobile/01/21/bubble.ball.app/
URL : http://edition.cnn.com/2011/TECH/mobile/01/21/bubble.ball.app/
Summary: The main topic which is emphasized is the development of successful application.
This article mainly draws a point on the young and famous developer of application Robert
Nay, he has developed the most important free application ITunes. This article is mainly
chosen due to the factor of the person’s brilliant innovative ideas and its direct implementation
which would make the application field cross a certain level of boundary. On the other and the
developer also developed a famous app named bubble ball which was selected as the most
commonly used free application in the iTunes store and this application was invented by him
at the age of 14 only. This game was considered to be very much simple yet it was very much
attractive for the small kids. In the game there was series of puzzle that the player had to
guide the ball through in order to reach the goal of the game. Then most important aspect
which is very much needed for a game developer is that the person should have immense
knowledge of the programming language which is being used for the game and must have
creative thinking ideas in order to make the game look more realistic. On the other hand the
market need should be taken into account and the choice of the customers. From the above
discussion it can be concluded that the field of the development of a new application is
increasing on a day to day basis and knowledge and the creativity are very much required for
the development of the application.
Week 10
While information systems and technology deliver many benefits to society, they can also
result in (sometimes inadvertent) negative effects and outcomes. Find and summarise a
resource that describes ONE example of where the use of an information system or
technology has led to negative consequences for humans.
Title: Negative consequences of data warehousing
Reference: Burnside, K. 2017. The Disadvantages of a Data Warehouse. [online]
Smallbusiness.chron.com. Available at: http://smallbusiness.chron.com/disadvantages-data-
warehouse-73584.html
URL : http://smallbusiness.chron.com/disadvantages-data-warehouse-73584.html
Summary: the article puts direct emphasis on the concept of data warehousing with iot
bringing into account its negative impact. This article is mainly chosen due to the factor that
the warehouse technique is considered as the most important aspect in the information
system. This conceit is implemented in several information system and businesses. Data
warehousing is mainly used in order to find out in particular, the types of useful data from a
huge amount of data. Taking into account the practical aspect of the implementation there are
many disadvantages that can be taken in regards to the implementation. Data warehouse can
be considered as a technique which can be used to extract information which is mainly
collected from different department which can be directly be implemented for the betterment
of the different services that can improve the productivity of the organisation. The bad effect
of the data warehouse is the risk associated with the extra work which need to be done with
the aspect. As the data warehouse can be directly be related to the data collection from a
wide range of customers in some cases it is seen that the organisations database have the
same time of data or content thus as a result of which the data can be copied. Data
One of the greatest success stories in application development in recent times has been the
popularity of mobile apps. Find and summarise a resource that describes the story of ONE
successful mobile app developer.
Title: Successful young app developer Robert Nay
Reference: Sutter, J. 2017. 14-year-old creates 'Bubble Ball,' iTunes' most popular free app.
[online] Edition.cnn.com. Available at:
http://edition.cnn.com/2011/TECH/mobile/01/21/bubble.ball.app/
URL : http://edition.cnn.com/2011/TECH/mobile/01/21/bubble.ball.app/
Summary: The main topic which is emphasized is the development of successful application.
This article mainly draws a point on the young and famous developer of application Robert
Nay, he has developed the most important free application ITunes. This article is mainly
chosen due to the factor of the person’s brilliant innovative ideas and its direct implementation
which would make the application field cross a certain level of boundary. On the other and the
developer also developed a famous app named bubble ball which was selected as the most
commonly used free application in the iTunes store and this application was invented by him
at the age of 14 only. This game was considered to be very much simple yet it was very much
attractive for the small kids. In the game there was series of puzzle that the player had to
guide the ball through in order to reach the goal of the game. Then most important aspect
which is very much needed for a game developer is that the person should have immense
knowledge of the programming language which is being used for the game and must have
creative thinking ideas in order to make the game look more realistic. On the other hand the
market need should be taken into account and the choice of the customers. From the above
discussion it can be concluded that the field of the development of a new application is
increasing on a day to day basis and knowledge and the creativity are very much required for
the development of the application.
Week 10
While information systems and technology deliver many benefits to society, they can also
result in (sometimes inadvertent) negative effects and outcomes. Find and summarise a
resource that describes ONE example of where the use of an information system or
technology has led to negative consequences for humans.
Title: Negative consequences of data warehousing
Reference: Burnside, K. 2017. The Disadvantages of a Data Warehouse. [online]
Smallbusiness.chron.com. Available at: http://smallbusiness.chron.com/disadvantages-data-
warehouse-73584.html
URL : http://smallbusiness.chron.com/disadvantages-data-warehouse-73584.html
Summary: the article puts direct emphasis on the concept of data warehousing with iot
bringing into account its negative impact. This article is mainly chosen due to the factor that
the warehouse technique is considered as the most important aspect in the information
system. This conceit is implemented in several information system and businesses. Data
warehousing is mainly used in order to find out in particular, the types of useful data from a
huge amount of data. Taking into account the practical aspect of the implementation there are
many disadvantages that can be taken in regards to the implementation. Data warehouse can
be considered as a technique which can be used to extract information which is mainly
collected from different department which can be directly be implemented for the betterment
of the different services that can improve the productivity of the organisation. The bad effect
of the data warehouse is the risk associated with the extra work which need to be done with
the aspect. As the data warehouse can be directly be related to the data collection from a
wide range of customers in some cases it is seen that the organisations database have the
same time of data or content thus as a result of which the data can be copied. Data
warehouse can also affect the flexibility aspect in any organisation. From the above
discussion it can be stated that data warehouse has a lot in hand with the advantages with it
many disadvantage related to the aspect.
discussion it can be stated that data warehouse has a lot in hand with the advantages with it
many disadvantage related to the aspect.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
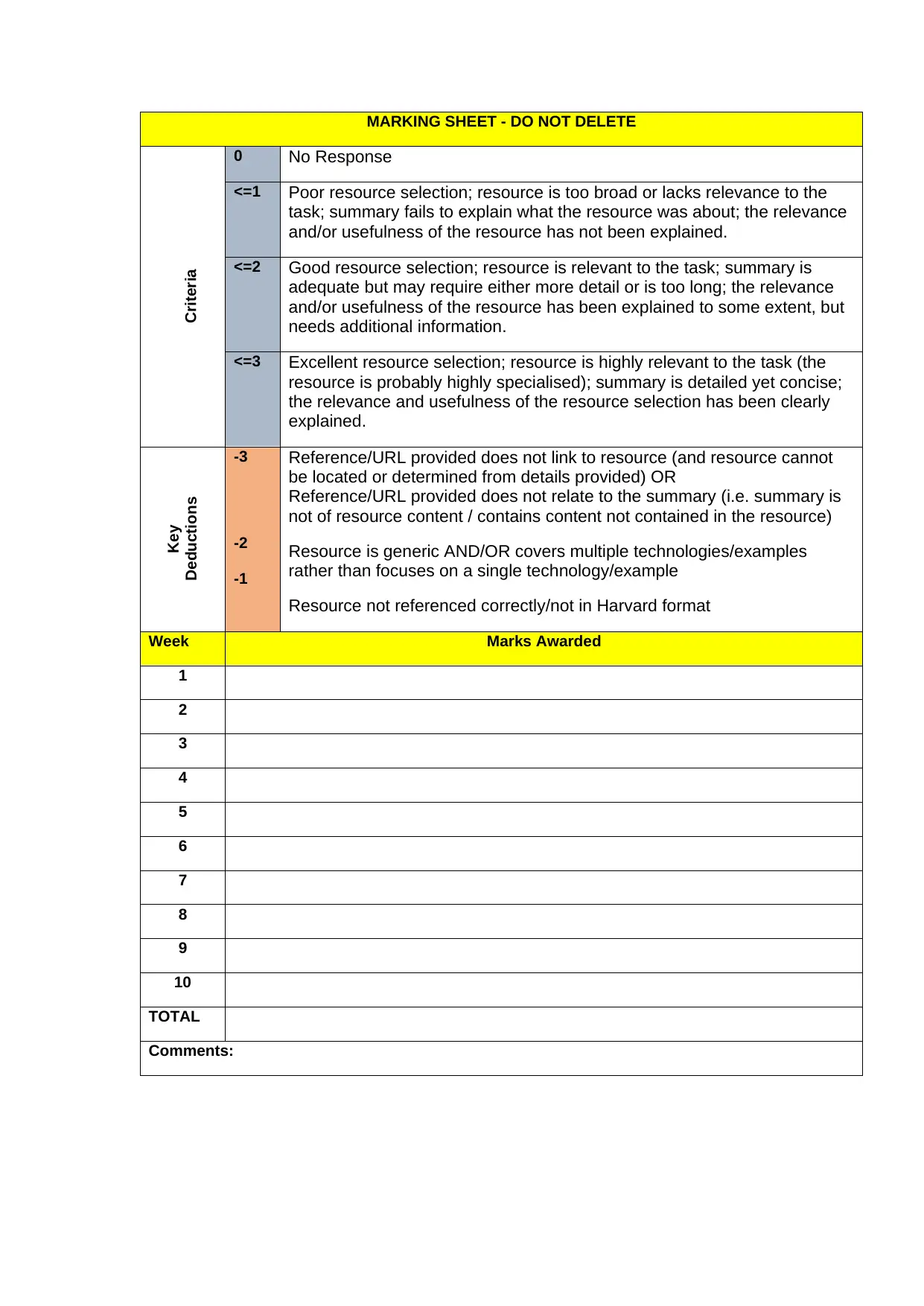
MARKING SHEET - DO NOT DELETE
Criteria
0 No Response
<=1 Poor resource selection; resource is too broad or lacks relevance to the
task; summary fails to explain what the resource was about; the relevance
and/or usefulness of the resource has not been explained.
<=2 Good resource selection; resource is relevant to the task; summary is
adequate but may require either more detail or is too long; the relevance
and/or usefulness of the resource has been explained to some extent, but
needs additional information.
<=3 Excellent resource selection; resource is highly relevant to the task (the
resource is probably highly specialised); summary is detailed yet concise;
the relevance and usefulness of the resource selection has been clearly
explained.
Key
Deductions
-3
-2
-1
Reference/URL provided does not link to resource (and resource cannot
be located or determined from details provided) OR
Reference/URL provided does not relate to the summary (i.e. summary is
not of resource content / contains content not contained in the resource)
Resource is generic AND/OR covers multiple technologies/examples
rather than focuses on a single technology/example
Resource not referenced correctly/not in Harvard format
Week Marks Awarded
1
2
3
4
5
6
7
8
9
10
TOTAL
Comments:
Criteria
0 No Response
<=1 Poor resource selection; resource is too broad or lacks relevance to the
task; summary fails to explain what the resource was about; the relevance
and/or usefulness of the resource has not been explained.
<=2 Good resource selection; resource is relevant to the task; summary is
adequate but may require either more detail or is too long; the relevance
and/or usefulness of the resource has been explained to some extent, but
needs additional information.
<=3 Excellent resource selection; resource is highly relevant to the task (the
resource is probably highly specialised); summary is detailed yet concise;
the relevance and usefulness of the resource selection has been clearly
explained.
Key
Deductions
-3
-2
-1
Reference/URL provided does not link to resource (and resource cannot
be located or determined from details provided) OR
Reference/URL provided does not relate to the summary (i.e. summary is
not of resource content / contains content not contained in the resource)
Resource is generic AND/OR covers multiple technologies/examples
rather than focuses on a single technology/example
Resource not referenced correctly/not in Harvard format
Week Marks Awarded
1
2
3
4
5
6
7
8
9
10
TOTAL
Comments:
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





