Digital Forensics Investigation Report - COIT12201, T2, 2019
VerifiedAdded on 2022/10/17
|18
|1486
|14
Report
AI Summary
This report presents a comprehensive digital forensics investigation, focusing on the analysis of digital evidence using the Autopsy tool. The investigation involves examining several E01 files, including charlie-2009-12-11.E01, charlie-work-usb-2009-12-11.E01, and charlie-2009-12-11.mddramimage.zip, to uncover hidden files, deleted data, and potential evidence of computer crime. The report details the steps taken using Autopsy, the types of files found (images, videos, audio, archives, databases, documents, HTML, MS Office files, PDF files, text files, rich text, and executable files), and the identification of specific methods and software used. The investigation reveals insights into potential spying activities, including the use of Xcopy software and remote server connections. The report also includes a detailed bibliography of relevant sources.

Running head: Electronic Crime and Digital Forensics
Electronic Crime and Digital Forensics
Name of the Student
Name of the University
Author Note
Electronic Crime and Digital Forensics
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Electronic Crime and Digital Forensics 1
Table of Contents
Digital forensic:..........................................................................................................................2
Activity One:..............................................................................................................................2
The steps for using autopsy in digital forensics are:..............................................................3
Investigation:..........................................................................................................................4
charlie-2009-12-11.E01:....................................................................................................4
charlie-work-usb-2009-12-11.E01:..................................................................................16
charlie-2009-12-11.mddramimage.zip:............................................................................22
Bibliography:............................................................................................................................30
Table of Contents
Digital forensic:..........................................................................................................................2
Activity One:..............................................................................................................................2
The steps for using autopsy in digital forensics are:..............................................................3
Investigation:..........................................................................................................................4
charlie-2009-12-11.E01:....................................................................................................4
charlie-work-usb-2009-12-11.E01:..................................................................................16
charlie-2009-12-11.mddramimage.zip:............................................................................22
Bibliography:............................................................................................................................30

2Electronic Crime and Digital Forensics
Digital forensic:
The digital forensics is a branch of forensic science that encompasses the
investigation and recovery of material that are found in devices that are digital. They have
relation with the computer crime. The term digital forensics was used as a synonym for the
forensics that are related to computer. It has been expanded in order to cover the investigation
of all the devices that are able to store data that are digital. The digital forensics has a variety
of applications. The most common applications among them is to support a hypothesis before
a civil or a criminal court. The criminal can also be featured in the sectors that are private like
during the investigations of the corporate or investigation of intrusion. The aspect of an
investigation that are technical are divided into sub branches that relates to the devices such
as computer forensics, network forensics, and forensics that are related to mobile devices.
The digital forensics requires the acquisition, preservation, documentation, analysis and
interpretation of the evidences from different storage media types. It is not only limited to the
hand held devices and laptops and desktops but it also extends to data in transit that are then
transmitted across networks that are private or public. The autopsy is a platform for the
forensics that are digital in nature and the interface that is graphical to the sleuth kit and the
other types of tools of digital forensics.
Activity One:
The autopsy tool will be used for the investigation of the files. The autopsy is software
that makes the employ of programs that are open source simpler. The open source programs
and the plug ins are used in the sleuth kit. The user interface that is graphical shows the
results from the search of forensics of the volume that are underlying thus making it easier for
the people who are investigating to flag the sections of data that are pertinent. The autopsy
tool is maintained by Basis Technology Corp. With the help of the programmers that are from
Digital forensic:
The digital forensics is a branch of forensic science that encompasses the
investigation and recovery of material that are found in devices that are digital. They have
relation with the computer crime. The term digital forensics was used as a synonym for the
forensics that are related to computer. It has been expanded in order to cover the investigation
of all the devices that are able to store data that are digital. The digital forensics has a variety
of applications. The most common applications among them is to support a hypothesis before
a civil or a criminal court. The criminal can also be featured in the sectors that are private like
during the investigations of the corporate or investigation of intrusion. The aspect of an
investigation that are technical are divided into sub branches that relates to the devices such
as computer forensics, network forensics, and forensics that are related to mobile devices.
The digital forensics requires the acquisition, preservation, documentation, analysis and
interpretation of the evidences from different storage media types. It is not only limited to the
hand held devices and laptops and desktops but it also extends to data in transit that are then
transmitted across networks that are private or public. The autopsy is a platform for the
forensics that are digital in nature and the interface that is graphical to the sleuth kit and the
other types of tools of digital forensics.
Activity One:
The autopsy tool will be used for the investigation of the files. The autopsy is software
that makes the employ of programs that are open source simpler. The open source programs
and the plug ins are used in the sleuth kit. The user interface that is graphical shows the
results from the search of forensics of the volume that are underlying thus making it easier for
the people who are investigating to flag the sections of data that are pertinent. The autopsy
tool is maintained by Basis Technology Corp. With the help of the programmers that are from
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3Electronic Crime and Digital Forensics
the community. The community sells training and the support services in order to use the
product. The autopsy tool is designed for the following purposes:
Centralized: The tool should offer a consistent and standard mechanism in order to access
all the modules and the characteristics.
Extensible: The user can be capable of adding new features by the creation of plug-in that
can examine all or part of the data source that are underlying.
Multiple users: The autopsy tool can be usable by one of the investigators or coordinate
the working of a time.
Ease of use: The autopsy tool should offer the historical tools and wizards in order to
make it easier for the users to repeat the stages without much reconfiguration.
The steps for using autopsy in digital forensics are:
Step 1: The first step is to open the autopsy tool. The autopsy tool can be opened in two
ways. First click on applications then 11- forensics and then autopsy.
Step 2: The autopsy application opens; a terminal opens that shows the information of the
program along with the details of the connection in order to open the browser of forensic
autopsy.
Step 3: In order to open the autopsy browser, the mouse should be positioned over the link
that s in the terminal, right click and choose the option of open link.
For doing the activity one the autopsy tool has been used. There are 3 files in the
activity one that are needed to be investigated.
the community. The community sells training and the support services in order to use the
product. The autopsy tool is designed for the following purposes:
Centralized: The tool should offer a consistent and standard mechanism in order to access
all the modules and the characteristics.
Extensible: The user can be capable of adding new features by the creation of plug-in that
can examine all or part of the data source that are underlying.
Multiple users: The autopsy tool can be usable by one of the investigators or coordinate
the working of a time.
Ease of use: The autopsy tool should offer the historical tools and wizards in order to
make it easier for the users to repeat the stages without much reconfiguration.
The steps for using autopsy in digital forensics are:
Step 1: The first step is to open the autopsy tool. The autopsy tool can be opened in two
ways. First click on applications then 11- forensics and then autopsy.
Step 2: The autopsy application opens; a terminal opens that shows the information of the
program along with the details of the connection in order to open the browser of forensic
autopsy.
Step 3: In order to open the autopsy browser, the mouse should be positioned over the link
that s in the terminal, right click and choose the option of open link.
For doing the activity one the autopsy tool has been used. There are 3 files in the
activity one that are needed to be investigated.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4Electronic Crime and Digital Forensics
Investigation:
charlie-2009-12-11.E01:
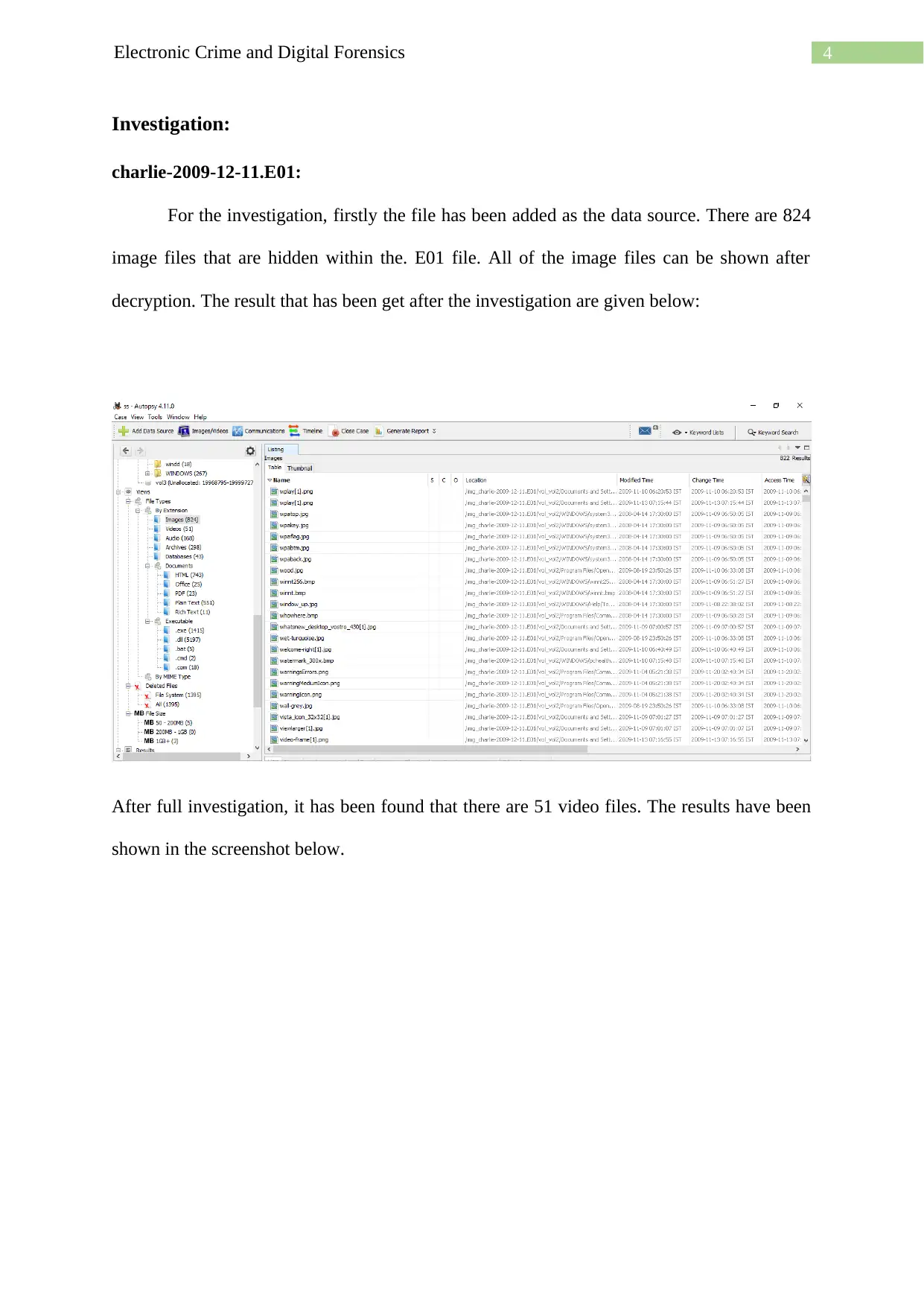
For the investigation, firstly the file has been added as the data source. There are 824
image files that are hidden within the. E01 file. All of the image files can be shown after
decryption. The result that has been get after the investigation are given below:
After full investigation, it has been found that there are 51 video files. The results have been
shown in the screenshot below.
Investigation:
charlie-2009-12-11.E01:
For the investigation, firstly the file has been added as the data source. There are 824
image files that are hidden within the. E01 file. All of the image files can be shown after
decryption. The result that has been get after the investigation are given below:
After full investigation, it has been found that there are 51 video files. The results have been
shown in the screenshot below.
5Electronic Crime and Digital Forensics
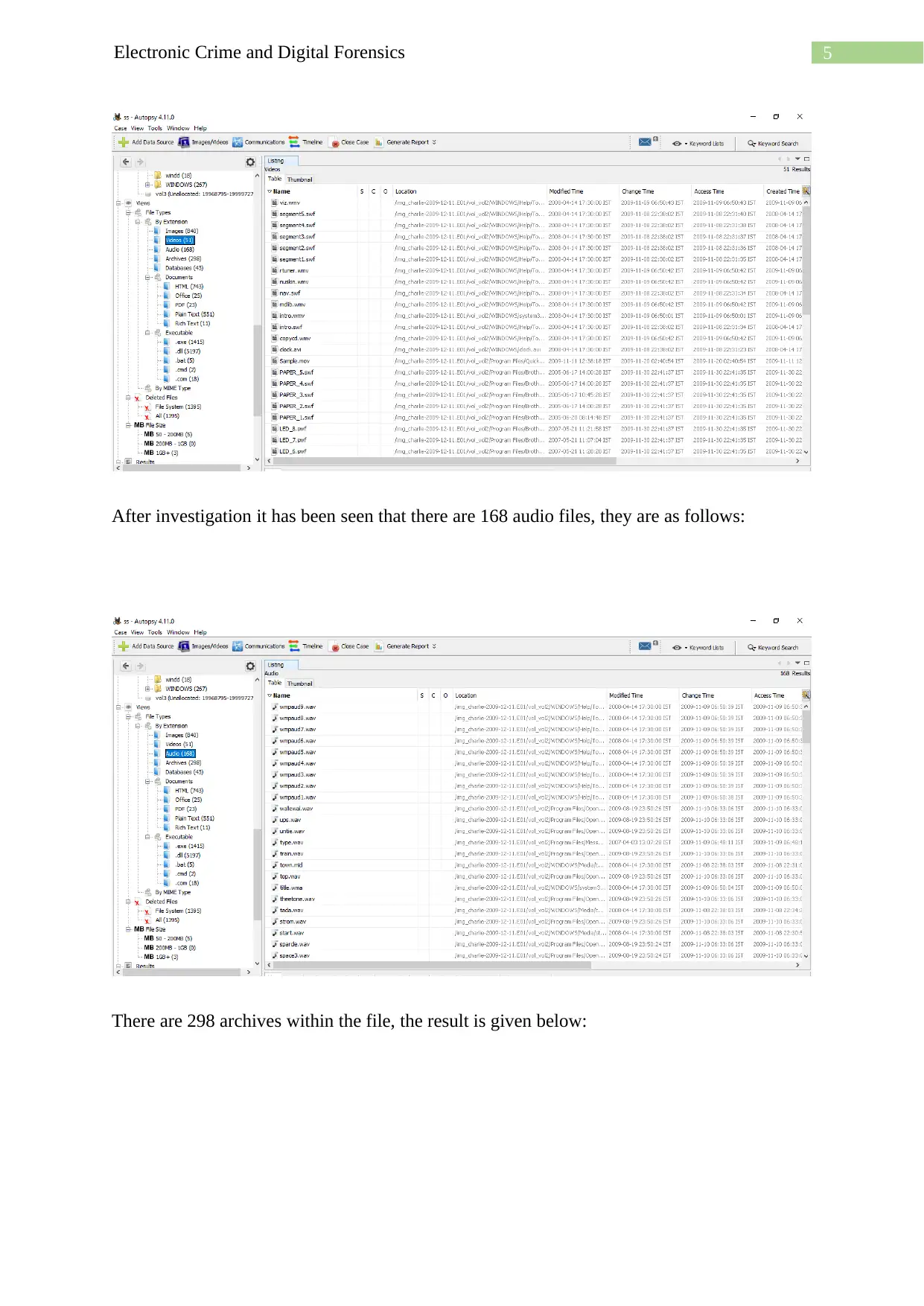
After investigation it has been seen that there are 168 audio files, they are as follows:
There are 298 archives within the file, the result is given below:
After investigation it has been seen that there are 168 audio files, they are as follows:
There are 298 archives within the file, the result is given below:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6Electronic Crime and Digital Forensics
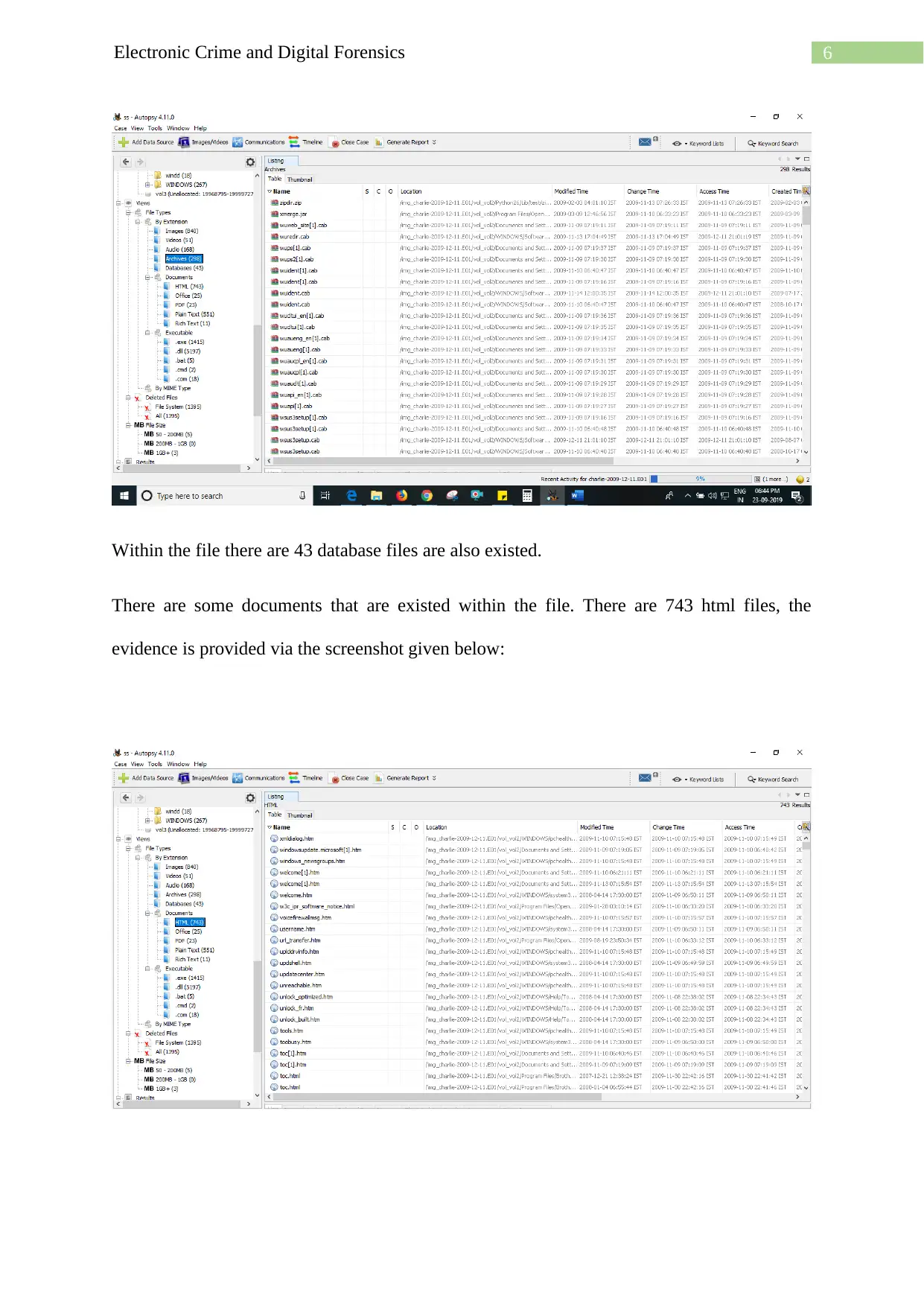
Within the file there are 43 database files are also existed.
There are some documents that are existed within the file. There are 743 html files, the
evidence is provided via the screenshot given below:
Within the file there are 43 database files are also existed.
There are some documents that are existed within the file. There are 743 html files, the
evidence is provided via the screenshot given below:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7Electronic Crime and Digital Forensics
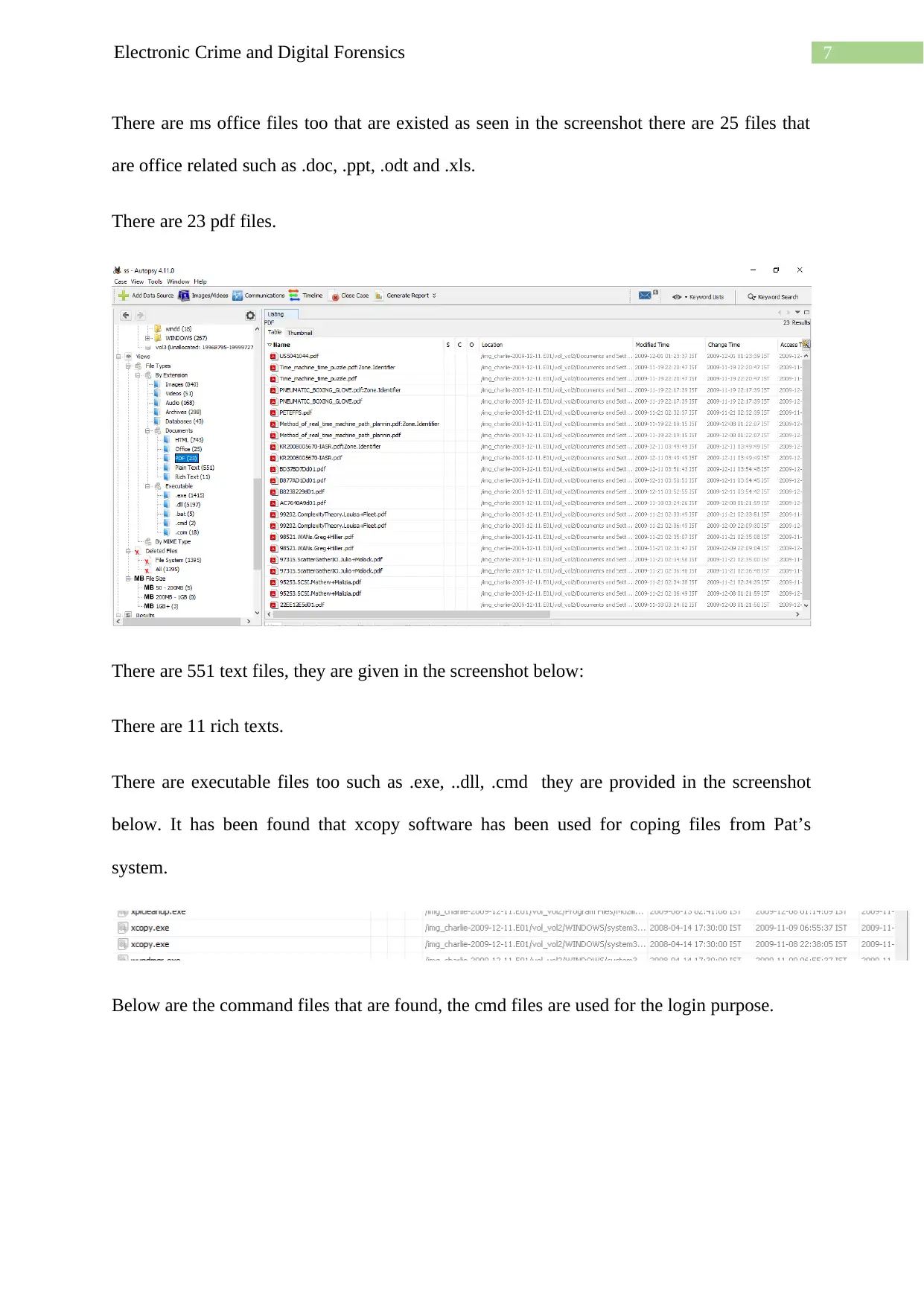
There are ms office files too that are existed as seen in the screenshot there are 25 files that
are office related such as .doc, .ppt, .odt and .xls.
There are 23 pdf files.
There are 551 text files, they are given in the screenshot below:
There are 11 rich texts.
There are executable files too such as .exe, ..dll, .cmd they are provided in the screenshot
below. It has been found that xcopy software has been used for coping files from Pat’s
system.
Below are the command files that are found, the cmd files are used for the login purpose.
There are ms office files too that are existed as seen in the screenshot there are 25 files that
are office related such as .doc, .ppt, .odt and .xls.
There are 23 pdf files.
There are 551 text files, they are given in the screenshot below:
There are 11 rich texts.
There are executable files too such as .exe, ..dll, .cmd they are provided in the screenshot
below. It has been found that xcopy software has been used for coping files from Pat’s
system.
Below are the command files that are found, the cmd files are used for the login purpose.
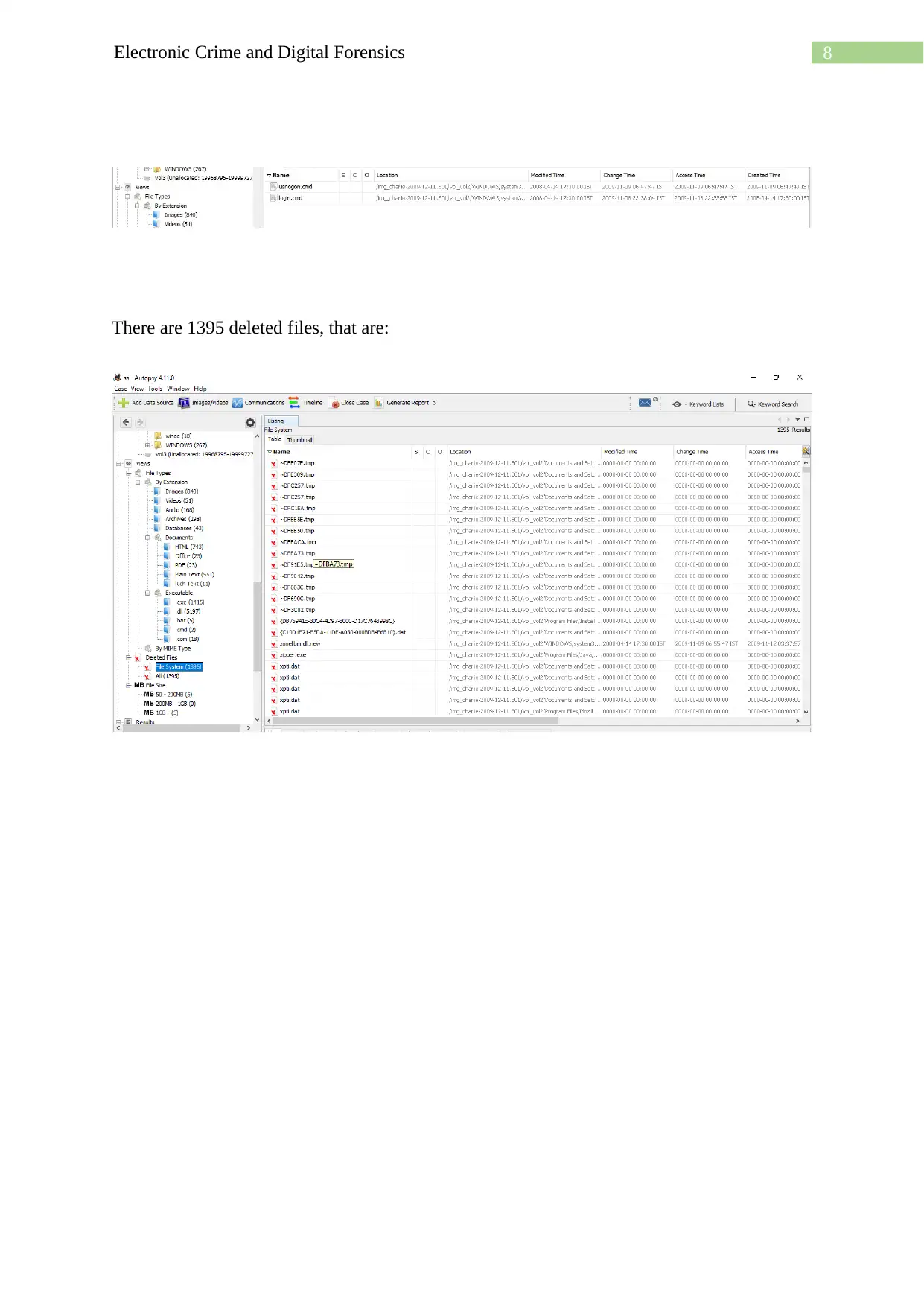
8Electronic Crime and Digital Forensics
There are 1395 deleted files, that are:
There are 1395 deleted files, that are:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
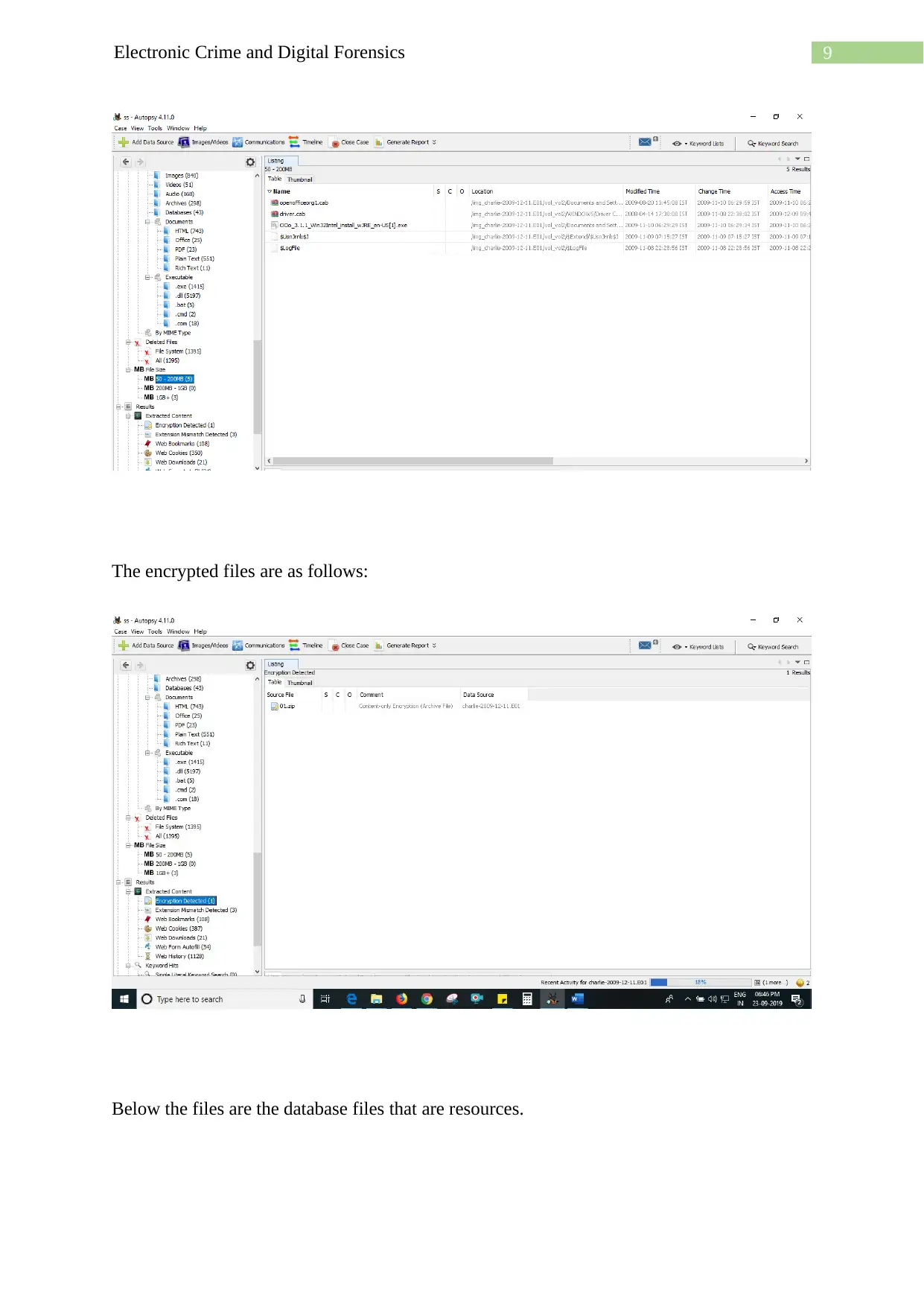
9Electronic Crime and Digital Forensics
The encrypted files are as follows:
Below the files are the database files that are resources.
The encrypted files are as follows:
Below the files are the database files that are resources.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
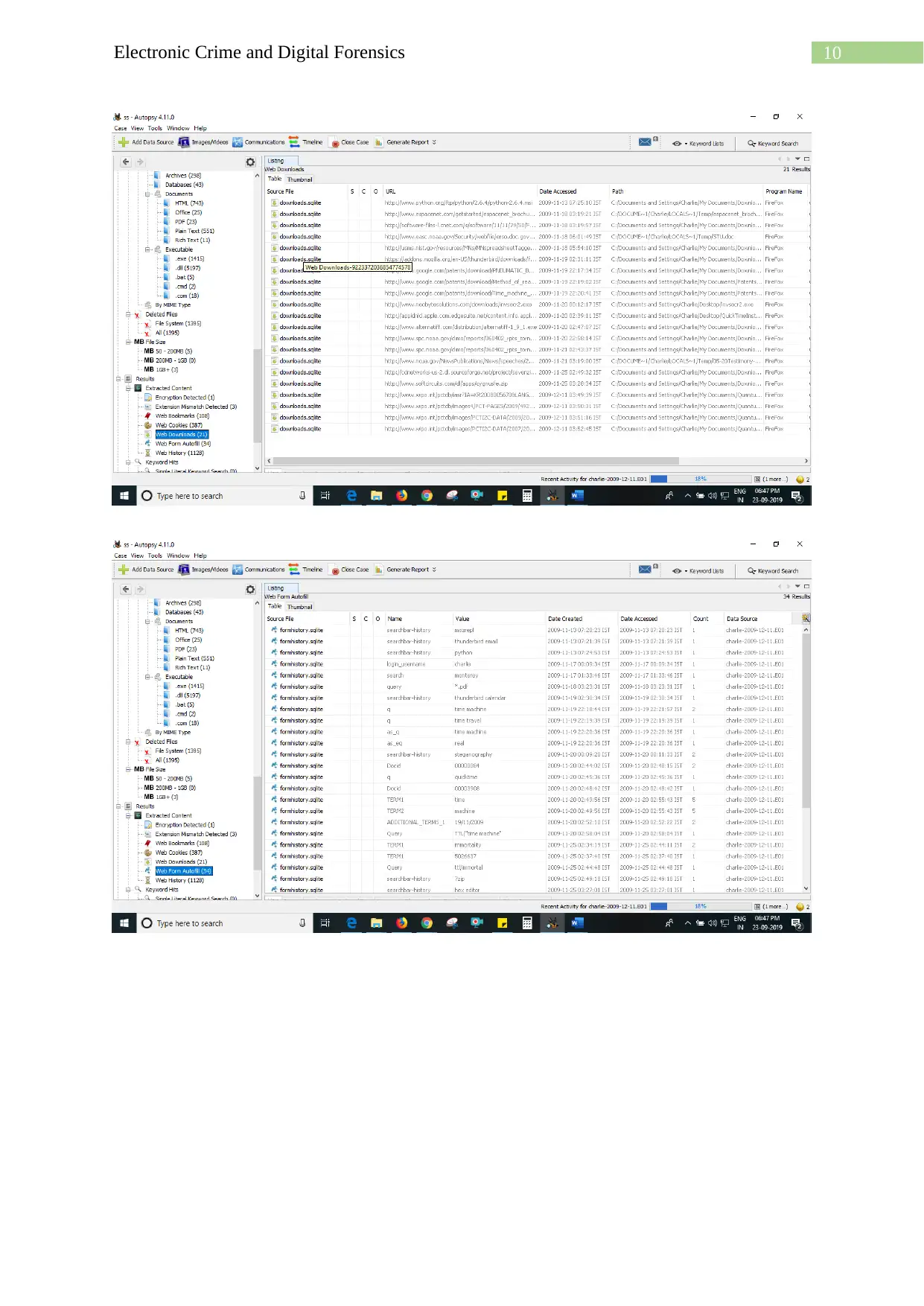
10Electronic Crime and Digital Forensics
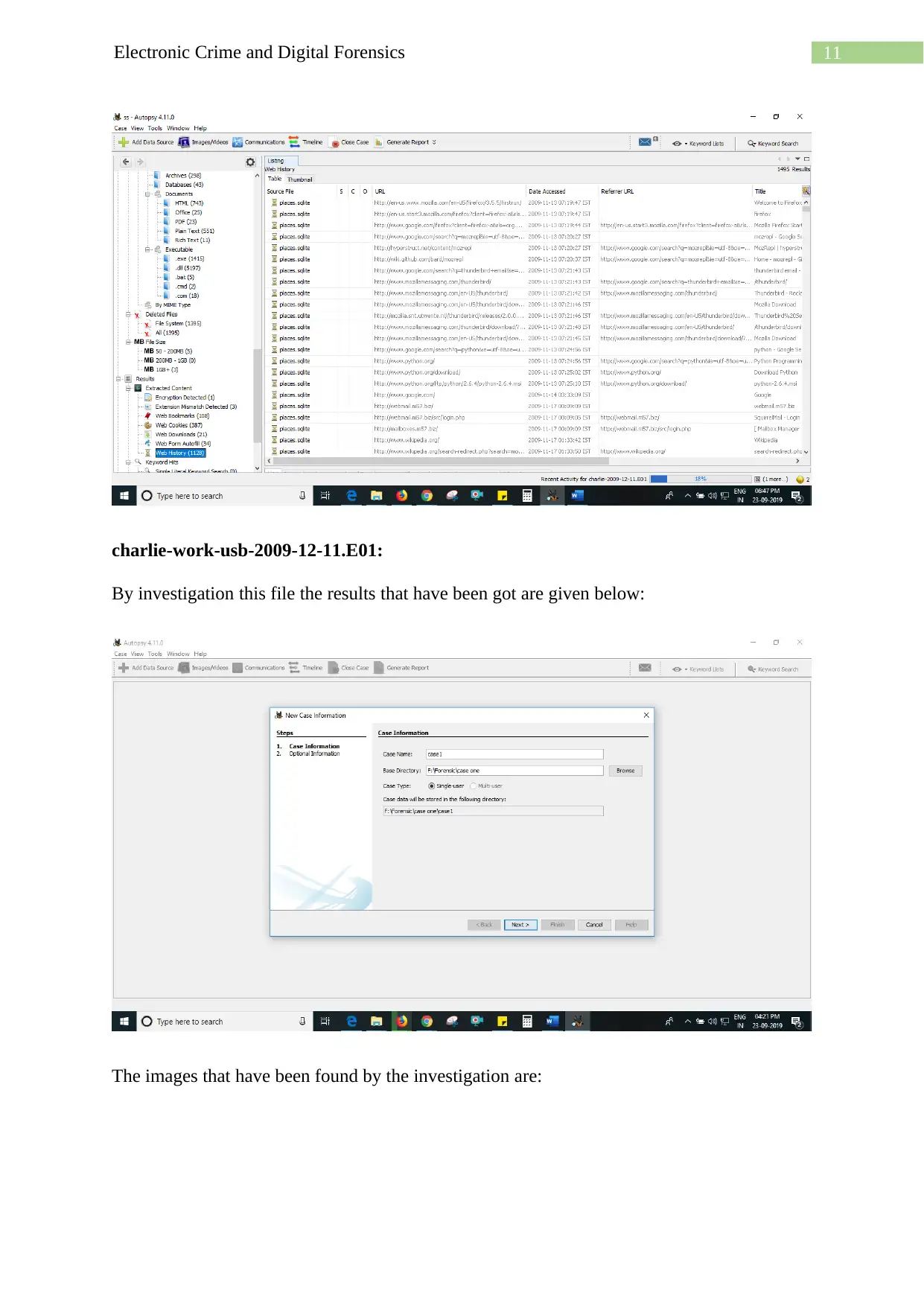
11Electronic Crime and Digital Forensics
charlie-work-usb-2009-12-11.E01:
By investigation this file the results that have been got are given below:
The images that have been found by the investigation are:
charlie-work-usb-2009-12-11.E01:
By investigation this file the results that have been got are given below:
The images that have been found by the investigation are:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





