COIT12202 Network Security Concepts: Short-Answer Questions, Term 2
VerifiedAdded on 2023/06/04
|15
|2501
|364
Homework Assignment
AI Summary
This assignment focuses on network security concepts, featuring short-answer questions related to Network Address Translation (NAT), Wireshark analysis, Cisco Access Control Lists (ACLs), and Wi-Fi security vulnerabilities. It includes explanations of how NAT works, its security benefits, and its relevance in the context of IPv6. The assignment also involves capturing network traffic using Wireshark to analyze DNS and HTTP interactions, identifying key sections like DNS resolution, TCP handshaking, and connection termination. Furthermore, it requires creating Cisco IOS standard and extended IP access lists to manage network traffic. Finally, the assignment addresses security issues in public Wi-Fi networks, including potential attacks and mitigation strategies, and discusses the KRACK attack on WPA2-protected networks.

COIT12202 – Network Security Concepts
Term 2, 2018
Assessment 2 Short-Answer Questions
Name:
ID:
Due Date: 01October 2018, 11:45 AM
COIT12202 – Network Security Concepts 1
Term 2, 2018
Assessment 2 Short-Answer Questions
Name:
ID:
Due Date: 01October 2018, 11:45 AM
COIT12202 – Network Security Concepts 1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Instructions:...........................................................................................................................................3
Short-answer questions.........................................................................................................................4
Reference............................................................................................................................................11
Marking Criteria...................................................................................................................................12
COIT12202 – Network Security Concepts 2
Instructions:...........................................................................................................................................3
Short-answer questions.........................................................................................................................4
Reference............................................................................................................................................11
Marking Criteria...................................................................................................................................12
COIT12202 – Network Security Concepts 2

Instructions:
This short-answer question template contains a tabular marking criteria and your answers will be
assessed in regards to accuracy, clarity and detail. Please note:
Use the provided template to insert your responses for each question;
You should submit the completed templates online;
Please do not delete the marking criteria page in each template;
Harvard reference format is acceptable;
Late penalties will be applied (5% of the total scores per day late);
Use your own words to answer the questions;
Plagiarism detection will be used in this assignment;
To reduce similarity, the assignment questions can be deleted before submission;
Please don’t forget to update the template’s table of contents before you submit;
Needed files to be submitted: this completed template and a captured PCAP file.
COIT12202 – Network Security Concepts 3
This short-answer question template contains a tabular marking criteria and your answers will be
assessed in regards to accuracy, clarity and detail. Please note:
Use the provided template to insert your responses for each question;
You should submit the completed templates online;
Please do not delete the marking criteria page in each template;
Harvard reference format is acceptable;
Late penalties will be applied (5% of the total scores per day late);
Use your own words to answer the questions;
Plagiarism detection will be used in this assignment;
To reduce similarity, the assignment questions can be deleted before submission;
Please don’t forget to update the template’s table of contents before you submit;
Needed files to be submitted: this completed template and a captured PCAP file.
COIT12202 – Network Security Concepts 3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

PC Modem ISP World
Short-answer questions
Question 6:
Network address translation (NAT) is a method to remap one IP address space into another
space by modifying network address information in Internet Protocol datagram packet
headers while in transit across a traffic routing device.
Please complete the following tasks/question:
(1) Use an example to illustrate how packets are sent and received by using NAT
technology;
(2) Explain why NAT technology can provide a degree of security;
(3) One purpose of using NAT/PAT (Port Address Translation) is to save IP addresses.
IPv6 uses 128-bit addresses, instead of the meagre 32-bit IPv4 addresses. Does that
mean that IPV6 will eliminate NAT/PAT?
Your answer:
Question 1 Answer –
The network address translation is used for mapping the IP address with the
website URL and the following diagram is created for the demonstration of the
working of NAT.
Multiple device can be connected to the network using modem and router and
a single IP address given by the ISP is assigned to the router interface. The
modem is installed for assigning the IP address to the PC and the other device
connected in the network. When an IP data packet is sent to the IP address of
the destination the modem and the port number is used for routing the data
packet to the destination location. The modem maintains the record of the IP
COIT12202 – Network Security Concepts 4
Short-answer questions
Question 6:
Network address translation (NAT) is a method to remap one IP address space into another
space by modifying network address information in Internet Protocol datagram packet
headers while in transit across a traffic routing device.
Please complete the following tasks/question:
(1) Use an example to illustrate how packets are sent and received by using NAT
technology;
(2) Explain why NAT technology can provide a degree of security;
(3) One purpose of using NAT/PAT (Port Address Translation) is to save IP addresses.
IPv6 uses 128-bit addresses, instead of the meagre 32-bit IPv4 addresses. Does that
mean that IPV6 will eliminate NAT/PAT?
Your answer:
Question 1 Answer –
The network address translation is used for mapping the IP address with the
website URL and the following diagram is created for the demonstration of the
working of NAT.
Multiple device can be connected to the network using modem and router and
a single IP address given by the ISP is assigned to the router interface. The
modem is installed for assigning the IP address to the PC and the other device
connected in the network. When an IP data packet is sent to the IP address of
the destination the modem and the port number is used for routing the data
packet to the destination location. The modem maintains the record of the IP
COIT12202 – Network Security Concepts 4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

address using the routing table and management of the source and the client
network address.
Question 2 Answer –
The use of the NAT improves the security of the network because public
networks are also used for the transmission of the data. The NAT is used
protecting the internal network of the organization from the outside world and
configuration of the router with NAT helps it to work like a firewall by blocking
the unknown packets to reach the internal network of the organization.
Question 3 Answer –
The limitation of the IPv4 address can be resolved with the use of the IPv6 because the IPv4 is based
on 32 bit memory while IPv6 uses 128 bit. It is designed for meeting the growing demands of the
users and elimination of the need of Nat.
Question 7
Note: This task should not be conducted in CQU computer labs. Please use your home computer or
any other computer not connected to CQU premises.
Using Wireshark, your task is to capture an interaction between the client (your home computer)
and the CQU Webfuse webserver. In doing so, attempt to retrieve the following web page:
http://webfuse.cqu.edu.au/12021871.html
use this as (Student number = 12021871)
where YourStudentNumber needs to be replaced by your actual student number. Please use your
student number only. No other page name should be used.
Use the appropriate filters in Wireshark to capture only DNS and HTTP traffic.
COIT12202 – Network Security Concepts 5
network address.
Question 2 Answer –
The use of the NAT improves the security of the network because public
networks are also used for the transmission of the data. The NAT is used
protecting the internal network of the organization from the outside world and
configuration of the router with NAT helps it to work like a firewall by blocking
the unknown packets to reach the internal network of the organization.
Question 3 Answer –
The limitation of the IPv4 address can be resolved with the use of the IPv6 because the IPv4 is based
on 32 bit memory while IPv6 uses 128 bit. It is designed for meeting the growing demands of the
users and elimination of the need of Nat.
Question 7
Note: This task should not be conducted in CQU computer labs. Please use your home computer or
any other computer not connected to CQU premises.
Using Wireshark, your task is to capture an interaction between the client (your home computer)
and the CQU Webfuse webserver. In doing so, attempt to retrieve the following web page:
http://webfuse.cqu.edu.au/12021871.html
use this as (Student number = 12021871)
where YourStudentNumber needs to be replaced by your actual student number. Please use your
student number only. No other page name should be used.
Use the appropriate filters in Wireshark to capture only DNS and HTTP traffic.
COIT12202 – Network Security Concepts 5
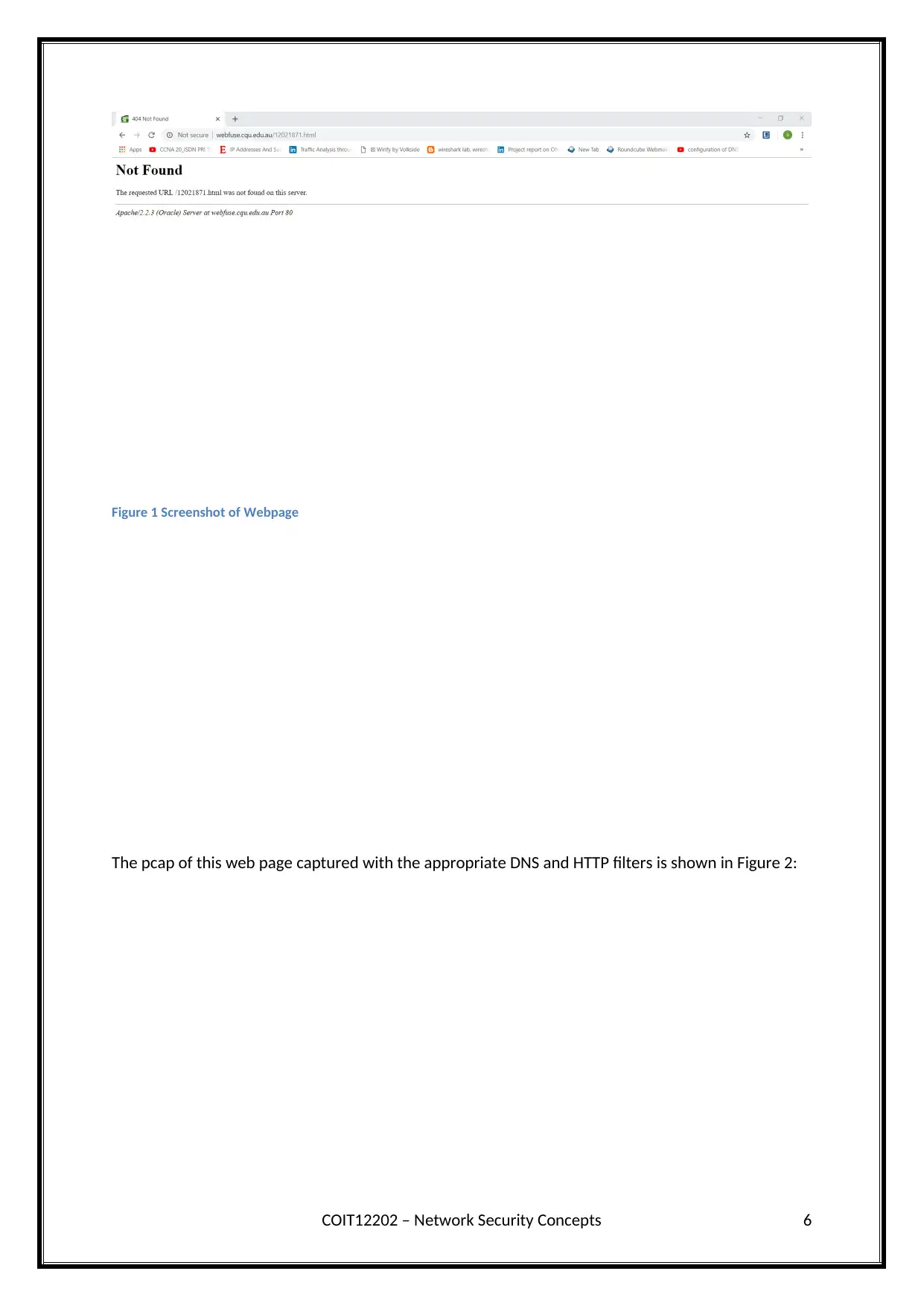
Figure 1 Screenshot of Webpage
The pcap of this web page captured with the appropriate DNS and HTTP filters is shown in Figure 2:
COIT12202 – Network Security Concepts 6
The pcap of this web page captured with the appropriate DNS and HTTP filters is shown in Figure 2:
COIT12202 – Network Security Concepts 6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Figure 2 PCAP of Webpage with DNS and HTTP filters
To reproduce a capture similar to Figure 2, you may need to research how to:
Flush the DNS resolver cache of your client
Flush the cache of your web browser; and
Make sure Wireshark is running with the appropriate DNS and HTTP filters before
requesting the webpage from the Webfuse webserver.
Tasks:
a) Capture and Submit the PCAP file of the interaction [0.5 mark]
b) Identify the following three sections in the PCAP: [1.5 marks]
DNS domain name resolution
The three-way handshaking for connection establishment;
Connection termination
For each of the sections, list the frames/packets associated with the section and
highlight the section with a red ellipse in the screenshot.
[1.5 marks, 0.5 mark for each section with frames correctly listed and highlighted]
c) For the three sections identified in b), explain each of the packet components in a similar
way done in the Packet Capture Exercise 3 – Week 8. You do not have to explain all the
captured frames, only the relevant frames. You may have to copy the information from the
PCAP and paste it in the relevant fields of the table. For each section use the following
template (similar to the one used in the Packet Capture Exercise 3 available in the Moodle
site – Week8):
COIT12202 – Network Security Concepts 7
To reproduce a capture similar to Figure 2, you may need to research how to:
Flush the DNS resolver cache of your client
Flush the cache of your web browser; and
Make sure Wireshark is running with the appropriate DNS and HTTP filters before
requesting the webpage from the Webfuse webserver.
Tasks:
a) Capture and Submit the PCAP file of the interaction [0.5 mark]
b) Identify the following three sections in the PCAP: [1.5 marks]
DNS domain name resolution
The three-way handshaking for connection establishment;
Connection termination
For each of the sections, list the frames/packets associated with the section and
highlight the section with a red ellipse in the screenshot.
[1.5 marks, 0.5 mark for each section with frames correctly listed and highlighted]
c) For the three sections identified in b), explain each of the packet components in a similar
way done in the Packet Capture Exercise 3 – Week 8. You do not have to explain all the
captured frames, only the relevant frames. You may have to copy the information from the
PCAP and paste it in the relevant fields of the table. For each section use the following
template (similar to the one used in the Packet Capture Exercise 3 available in the Moodle
site – Week8):
COIT12202 – Network Security Concepts 7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
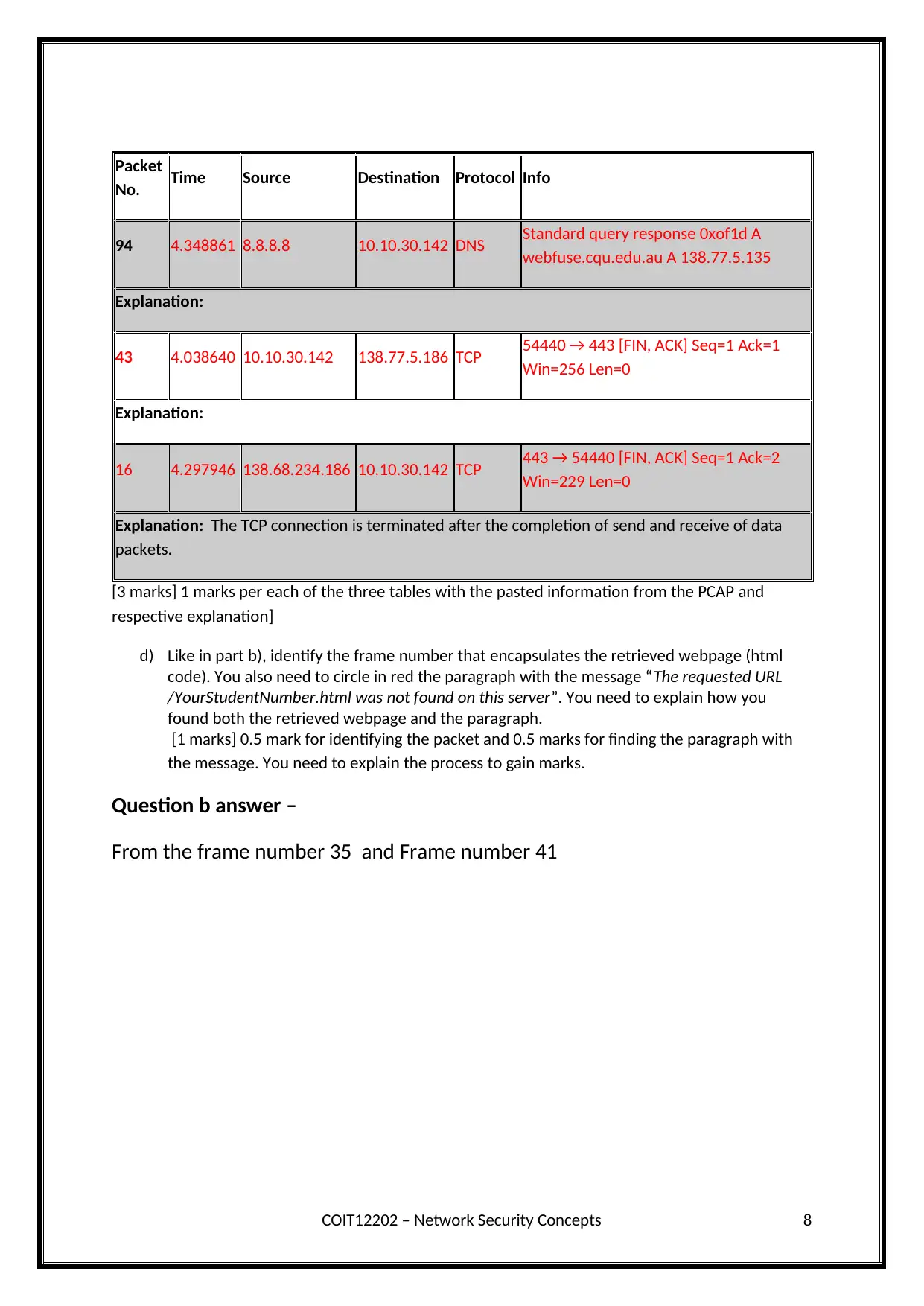
Packet
No. Time Source Destination Protocol Info
94 4.348861 8.8.8.8 10.10.30.142 DNS Standard query response 0xof1d A
webfuse.cqu.edu.au A 138.77.5.135
Explanation:
43 4.038640 10.10.30.142 138.77.5.186 TCP 54440 → 443 [FIN, ACK] Seq=1 Ack=1
Win=256 Len=0
Explanation:
16 4.297946 138.68.234.186 10.10.30.142 TCP 443 → 54440 [FIN, ACK] Seq=1 Ack=2
Win=229 Len=0
Explanation: The TCP connection is terminated after the completion of send and receive of data
packets.
[3 marks] 1 marks per each of the three tables with the pasted information from the PCAP and
respective explanation]
d) Like in part b), identify the frame number that encapsulates the retrieved webpage (html
code). You also need to circle in red the paragraph with the message “The requested URL
/YourStudentNumber.html was not found on this server”. You need to explain how you
found both the retrieved webpage and the paragraph.
[1 marks] 0.5 mark for identifying the packet and 0.5 marks for finding the paragraph with
the message. You need to explain the process to gain marks.
Question b answer –
From the frame number 35 and Frame number 41
COIT12202 – Network Security Concepts 8
No. Time Source Destination Protocol Info
94 4.348861 8.8.8.8 10.10.30.142 DNS Standard query response 0xof1d A
webfuse.cqu.edu.au A 138.77.5.135
Explanation:
43 4.038640 10.10.30.142 138.77.5.186 TCP 54440 → 443 [FIN, ACK] Seq=1 Ack=1
Win=256 Len=0
Explanation:
16 4.297946 138.68.234.186 10.10.30.142 TCP 443 → 54440 [FIN, ACK] Seq=1 Ack=2
Win=229 Len=0
Explanation: The TCP connection is terminated after the completion of send and receive of data
packets.
[3 marks] 1 marks per each of the three tables with the pasted information from the PCAP and
respective explanation]
d) Like in part b), identify the frame number that encapsulates the retrieved webpage (html
code). You also need to circle in red the paragraph with the message “The requested URL
/YourStudentNumber.html was not found on this server”. You need to explain how you
found both the retrieved webpage and the paragraph.
[1 marks] 0.5 mark for identifying the packet and 0.5 marks for finding the paragraph with
the message. You need to explain the process to gain marks.
Question b answer –
From the frame number 35 and Frame number 41
COIT12202 – Network Security Concepts 8
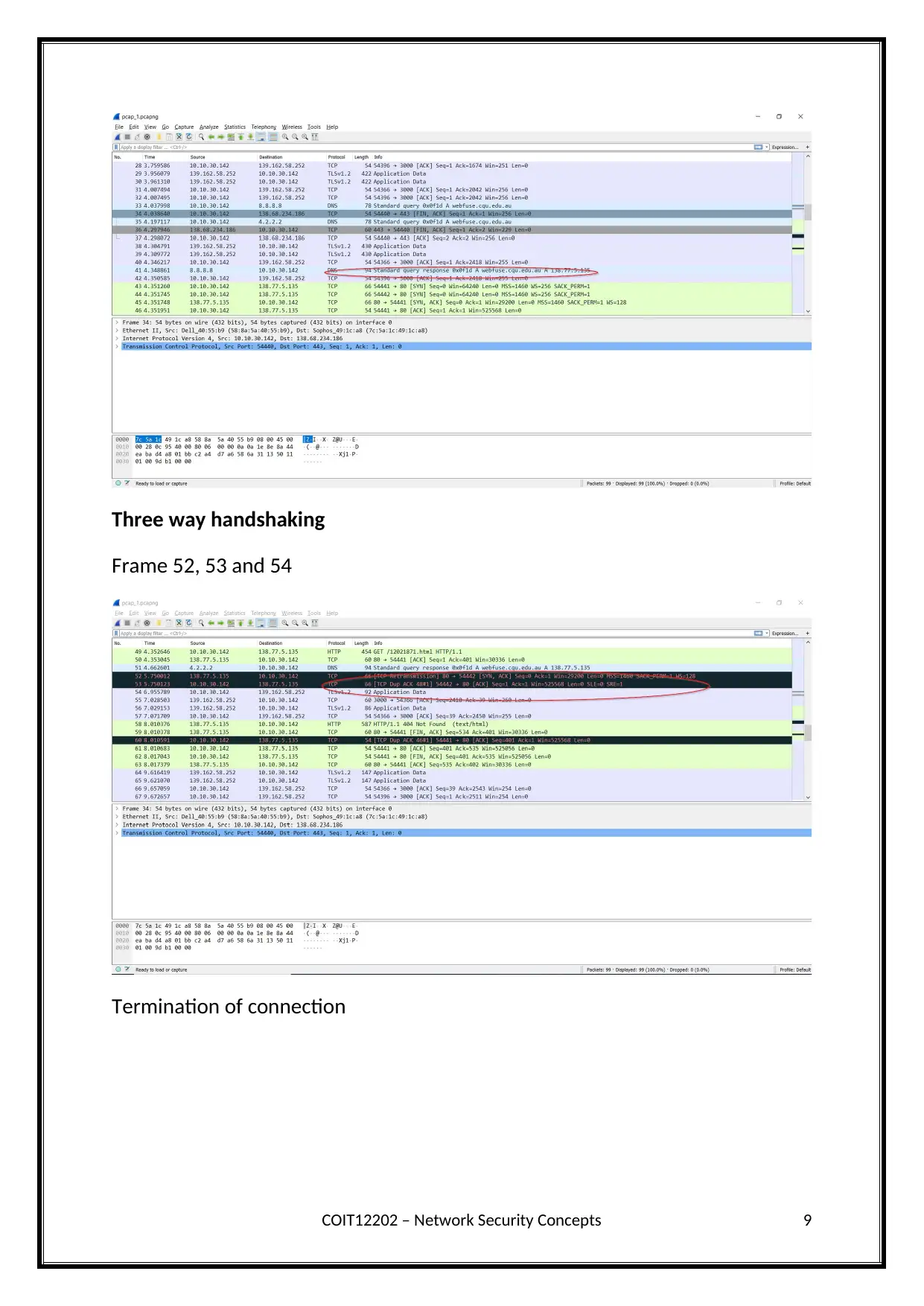
Three way handshaking
Frame 52, 53 and 54
Termination of connection
COIT12202 – Network Security Concepts 9
Frame 52, 53 and 54
Termination of connection
COIT12202 – Network Security Concepts 9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
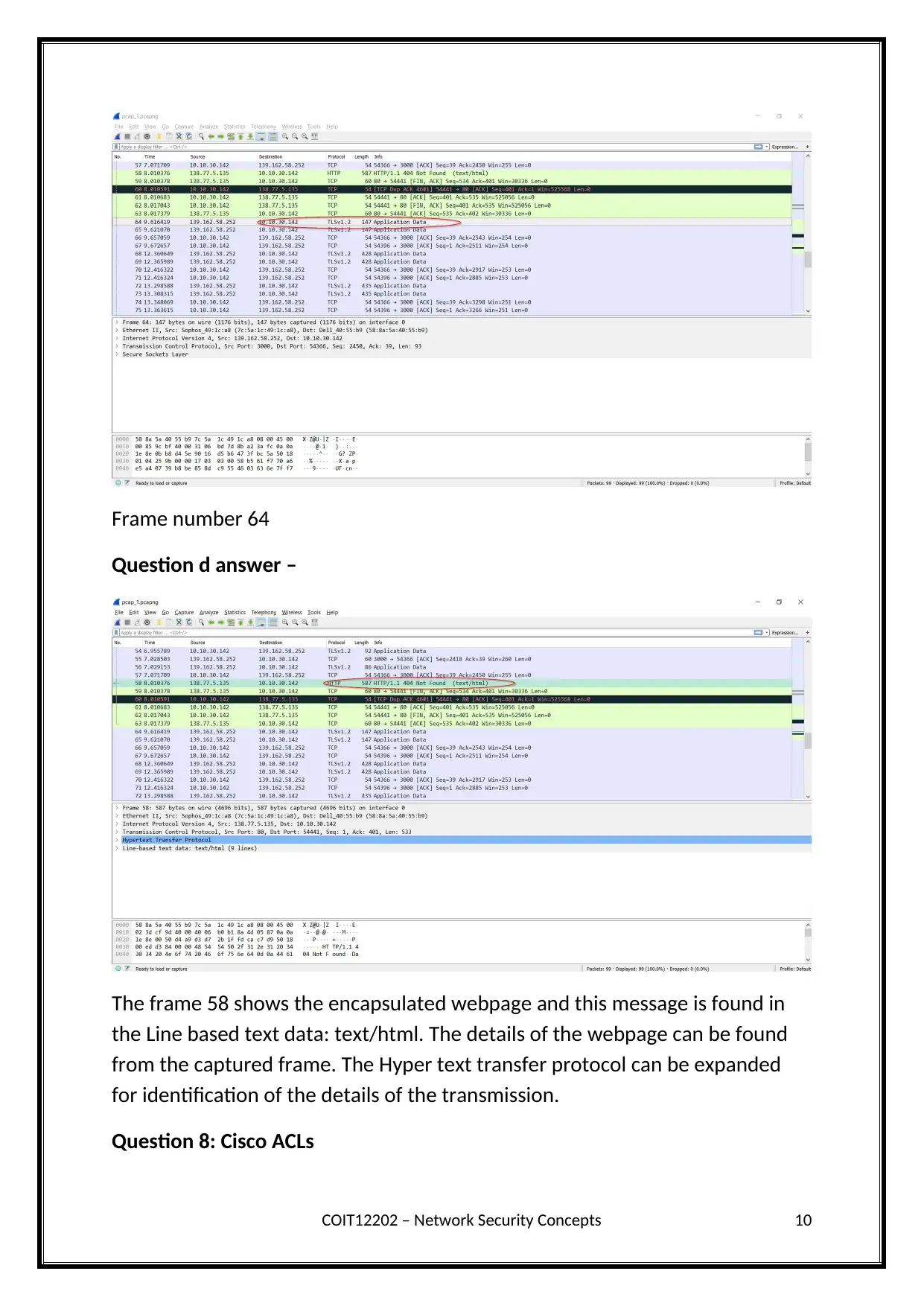
Frame number 64
Question d answer –
The frame 58 shows the encapsulated webpage and this message is found in
the Line based text data: text/html. The details of the webpage can be found
from the captured frame. The Hyper text transfer protocol can be expanded
for identification of the details of the transmission.
Question 8: Cisco ACLs
COIT12202 – Network Security Concepts 10
Question d answer –
The frame 58 shows the encapsulated webpage and this message is found in
the Line based text data: text/html. The details of the webpage can be found
from the captured frame. The Hyper text transfer protocol can be expanded
for identification of the details of the transmission.
Question 8: Cisco ACLs
COIT12202 – Network Security Concepts 10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cisco IOS (Internetworking Operating System) allows both standard and extended IP access lists
as follows:
Standard access lists are numbered 1-99 and filter based only on source IP.
o access-list <1-99> <permit|deny> <source IP> <source
wildcard>
o Example: This access list denies packets from host IP 139.78.5.100 but allows
packets from any other host that starts with 139.78.5
access-list 5 deny 139.78.5.100 0.0.0.0
access-list 5 permit 139.78.5.0 0.0.0.255
Extended access lists are numbered 100-199 and filter based on source, destination,
protocol, and port:
o access-list <100-199> <permit|deny> <tcp|udp|icmp>
<source IP> <source wildcard> <destination IP>
<destination wildcard> eq <port>
o ‘eq’ stands for ‘equal to’ (meaning port number equal to)
o Example: This extended access list discards packets from any host with an IP
starting with 128.1 trying to send to the SMTP port (25).
access-list 105 deny tcp 128.1.0.0 0.0.255.255 0.0.0.0 255.255.255.255 eq
25
Note the source/destination IP address wildcard format (it is the opposite of the IP address usual
subnet mask format):
o Example: To represent all IP addresses that start with 139.78.5:
IP = 139.78.5.0 WILDCARD=0.0.0.255
o Example: To represent all IP addresses that start with 128.1:
IP = 128.1.0.0 WILDCARD=0.0.255.255
o Example: To represent any address:
IP = 0.0.0.0 WILDCARD= 255.255.255.255
o Example: To represent a single address (172.30.16.29):
IP = 172.30.16.29 WILDCARD= 0.0.0.0 (check all bits)
If you want to place additional restrictions or admissions in the same access list, you just need to
add lines in the same format above with the same list number. Access list items are processed in
the order they appear in the list from top to bottom and any packet that does not match a list entry
is discarded (there is effectively a hidden ‘deny all’ rule at the end of the access list).
COIT12202 – Network Security Concepts 11
as follows:
Standard access lists are numbered 1-99 and filter based only on source IP.
o access-list <1-99> <permit|deny> <source IP> <source
wildcard>
o Example: This access list denies packets from host IP 139.78.5.100 but allows
packets from any other host that starts with 139.78.5
access-list 5 deny 139.78.5.100 0.0.0.0
access-list 5 permit 139.78.5.0 0.0.0.255
Extended access lists are numbered 100-199 and filter based on source, destination,
protocol, and port:
o access-list <100-199> <permit|deny> <tcp|udp|icmp>
<source IP> <source wildcard> <destination IP>
<destination wildcard> eq <port>
o ‘eq’ stands for ‘equal to’ (meaning port number equal to)
o Example: This extended access list discards packets from any host with an IP
starting with 128.1 trying to send to the SMTP port (25).
access-list 105 deny tcp 128.1.0.0 0.0.255.255 0.0.0.0 255.255.255.255 eq
25
Note the source/destination IP address wildcard format (it is the opposite of the IP address usual
subnet mask format):
o Example: To represent all IP addresses that start with 139.78.5:
IP = 139.78.5.0 WILDCARD=0.0.0.255
o Example: To represent all IP addresses that start with 128.1:
IP = 128.1.0.0 WILDCARD=0.0.255.255
o Example: To represent any address:
IP = 0.0.0.0 WILDCARD= 255.255.255.255
o Example: To represent a single address (172.30.16.29):
IP = 172.30.16.29 WILDCARD= 0.0.0.0 (check all bits)
If you want to place additional restrictions or admissions in the same access list, you just need to
add lines in the same format above with the same list number. Access list items are processed in
the order they appear in the list from top to bottom and any packet that does not match a list entry
is discarded (there is effectively a hidden ‘deny all’ rule at the end of the access list).
COIT12202 – Network Security Concepts 11

To complete this exercise:
a) Create an Access Control List that will prevent hosts in the network range of
192.168.176.0 to 192.168.191.0
[1 mark]
b) Create a Cisco IOS extended IP access list that allows any host to access a web server
(HTTP protocol over TLS/SSL) on TCP port 443 whose IP address is 138.77.236.58
[0.5 marks]
c) Create a Cisco IOS extended IP access list that allows any host to access the internal
SMTP server at 138.77.15.77 (TCP port 25), and the DNS servers at 138.77. 232.10
(TCP and UDP port 53).
[1.5 mark]
For this assessment item, you should submit the standard and extended access lists that you create
for the exercise (these do not need to be implemented on an actual router). For further
information on Cisco ACLs see:
http://www.cisco.com/en/US/tech/tk648/tk361/
technologies_configuration_example09186a0080100548.shtml
Answer to Question a
Access-list 5 deny 192.168.176.0 0.0.15.255
Answer to question b
Access-list 105 permit TCP any 138.77.236.58 0.0.0.0 eq 443
Answer to question c
ip access-group 105 in
access-list 10 permit tcp any host 138.77.15.77 eq smtp
access-list 102 permit tcp any host 138.77.15.77 eq 25
ip access-group 105 in
access-list 110 permit udp any 138.77. 232.10 eq domain
COIT12202 – Network Security Concepts 12
a) Create an Access Control List that will prevent hosts in the network range of
192.168.176.0 to 192.168.191.0
[1 mark]
b) Create a Cisco IOS extended IP access list that allows any host to access a web server
(HTTP protocol over TLS/SSL) on TCP port 443 whose IP address is 138.77.236.58
[0.5 marks]
c) Create a Cisco IOS extended IP access list that allows any host to access the internal
SMTP server at 138.77.15.77 (TCP port 25), and the DNS servers at 138.77. 232.10
(TCP and UDP port 53).
[1.5 mark]
For this assessment item, you should submit the standard and extended access lists that you create
for the exercise (these do not need to be implemented on an actual router). For further
information on Cisco ACLs see:
http://www.cisco.com/en/US/tech/tk648/tk361/
technologies_configuration_example09186a0080100548.shtml
Answer to Question a
Access-list 5 deny 192.168.176.0 0.0.15.255
Answer to question b
Access-list 105 permit TCP any 138.77.236.58 0.0.0.0 eq 443
Answer to question c
ip access-group 105 in
access-list 10 permit tcp any host 138.77.15.77 eq smtp
access-list 102 permit tcp any host 138.77.15.77 eq 25
ip access-group 105 in
access-list 110 permit udp any 138.77. 232.10 eq domain
COIT12202 – Network Security Concepts 12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



![Network Management Assignment Solution - [Course Code] - [Semester]](/_next/image/?url=https%3A%2F%2Fdesklib.com%2Fmedia%2Fimages%2Fla%2F5bdeac662a0b48479c60f14aac4bb9a2.jpg&w=256&q=75)
