COIT20246: Network Storage, Security, and Enterprise System Trends
VerifiedAdded on 2023/03/31
|8
|3161
|234
Homework Assignment
AI Summary
This assignment solution covers a range of topics related to network technologies and enterprise systems. It includes summaries of resources on Network Attached Storage (NAS), the NTFS file system, Fibre to the Premises (FTTP) NBN technology, the Tor browser, cryptojacking, fiber optic cable cuts, and emerging trends in Enterprise Resource Planning (ERP) systems. Each summary explains the resource's content, selection rationale, key information, and usefulness. The assignment provides insights into network storage solutions, security measures, and the evolution of enterprise systems, offering a comprehensive overview of current and future trends in these areas.

COIT 20246 ASSIGNMENT SUBMISSION
Due date: Thursday Week 11 (2PM AEST)
Part: Written Assessment
Weighting: 30% of total assessment.
Submission: Electronic (see course website for details)
Please fill in the following details:
Student Name
Student Number
Tutor’s Name
Instructions
It will be necessary to use online resources to complete this assignment, please
ensure you cite and reference any such materials using the Harvard format.
DO NOT copy content directly from either the text or Internet resources: this
assignment is to be in your own words. You will lose marks if you do not use
your own words!
Please complete your assignment using this submission template file, inserting your
responses where indicated.
DO NOT delete the marking criteria page – changes are permitted to the
formatting of other pages including the headers and footers.
Tasks
There are ten (10) tasks, one for each week: the tasks are detailed below. There is
a table to complete for each task. Please fill in the information required.
Note: Each resource summary should be around 200-300 words.
Each summary should briefly explain:
- What the resource is about
- Why you selected it
- What are the main points or key information covered in the resource
- Why the resource was useful.
For more advice about how to complete the assignment, as well as examples and
information about selecting good resources, please see the assessment page on the
Moodle unit web site:
https://moodle.cqu.edu.au/mod/assign/view.php?id=886270
1
Due date: Thursday Week 11 (2PM AEST)
Part: Written Assessment
Weighting: 30% of total assessment.
Submission: Electronic (see course website for details)
Please fill in the following details:
Student Name
Student Number
Tutor’s Name
Instructions
It will be necessary to use online resources to complete this assignment, please
ensure you cite and reference any such materials using the Harvard format.
DO NOT copy content directly from either the text or Internet resources: this
assignment is to be in your own words. You will lose marks if you do not use
your own words!
Please complete your assignment using this submission template file, inserting your
responses where indicated.
DO NOT delete the marking criteria page – changes are permitted to the
formatting of other pages including the headers and footers.
Tasks
There are ten (10) tasks, one for each week: the tasks are detailed below. There is
a table to complete for each task. Please fill in the information required.
Note: Each resource summary should be around 200-300 words.
Each summary should briefly explain:
- What the resource is about
- Why you selected it
- What are the main points or key information covered in the resource
- Why the resource was useful.
For more advice about how to complete the assignment, as well as examples and
information about selecting good resources, please see the assessment page on the
Moodle unit web site:
https://moodle.cqu.edu.au/mod/assign/view.php?id=886270
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Week 1
The text discusses examples of traditional mass storage such as magnetic disk and
solid-state drives. While these still underpin most mass storage, in corporate
environments they are often accessed via Network Attached Storage (NAS) or
Storage Area Network (SAN) technologies. Find and summarise ONE resource that
describes EITHER NAS or SAN storage technologies. The resource, and your
summary, must focus on either NAS or SAN, NOT BOTH.
Title and Reference: NAS STORAGE TECHNOLOGIES
Wd.com. (2019). [online] Available at: https://www.wd.com/en-gb/solutions/what-is-
network-attached-storage-nas.html [Accessed 30 May 2019].
Summary:
in this resource, it has been been discussed that the network storage systems are
significantly useful in various operating system environments, allowing various
devices to access the files regardless of the operating systems. commonly the NAS
operates on the Ethernet networks of the IP/TCP and it could easily offer the
controlled access to the data over the WiFi as well as the internet. The NAS devices
along with increased hard drive frequently have the capabilities of the RAID for the
data redundancy and are significantly dependable on the backup solutions. The
RAID stands for the Redundant Array of the Independent Disks and with the feature
allowed the data is immensely duplicated across the several hard drives and if
something goes wrong with any one drive, the users could simply execute the
replacement and the content would easily repopulate this new drive automatically.
Week 2
Operating systems use file managers to interact with mass storage devices.
However, the way in which data is stored and retrieved is dictated by the file system.
There are many types of file systems used by modern operating systems. Find and
summarise ONE resource that describes ONE such file system that is NOT FAT,
FAT32 or ExFAT. The resource, and your summary, must focus on A SINGLE file
system.
Title and Reference: NTFS FILE SYSTEM
Base, K. (2019). Introduction to file systems – UFS Explorer. [online] UFS Explorer.
Available at: https://www.ufsexplorer.com/articles/file-systems-basics.php [Accessed
30 May 2019].
Summary:
The NTFS or the New Technology File System had been introduced in the year of
1993 with the Windows NT and it is presently the major mutual file system for the
end user computers running on Windows. Majority of the operating systems of
windows server line utilises the format along with it. This file system is significantly
dependable to the journaling and then supporting the several features that includes
the access control, and the encryption. Each of the file in the NTFS is stored as the
descriptor of the file within the master file table and the file content. This Master file
table comprises of the entries along with all the information regarding the files that
includes the details of the size, name and the allocation. The initial 16 entries of
Master File Table are recalled for BitMap that keeps the records as free and then
used the clusters, the log utilised for the journaling documents and BadClus
comprising of the information regarding the bad clusters.
2
The text discusses examples of traditional mass storage such as magnetic disk and
solid-state drives. While these still underpin most mass storage, in corporate
environments they are often accessed via Network Attached Storage (NAS) or
Storage Area Network (SAN) technologies. Find and summarise ONE resource that
describes EITHER NAS or SAN storage technologies. The resource, and your
summary, must focus on either NAS or SAN, NOT BOTH.
Title and Reference: NAS STORAGE TECHNOLOGIES
Wd.com. (2019). [online] Available at: https://www.wd.com/en-gb/solutions/what-is-
network-attached-storage-nas.html [Accessed 30 May 2019].
Summary:
in this resource, it has been been discussed that the network storage systems are
significantly useful in various operating system environments, allowing various
devices to access the files regardless of the operating systems. commonly the NAS
operates on the Ethernet networks of the IP/TCP and it could easily offer the
controlled access to the data over the WiFi as well as the internet. The NAS devices
along with increased hard drive frequently have the capabilities of the RAID for the
data redundancy and are significantly dependable on the backup solutions. The
RAID stands for the Redundant Array of the Independent Disks and with the feature
allowed the data is immensely duplicated across the several hard drives and if
something goes wrong with any one drive, the users could simply execute the
replacement and the content would easily repopulate this new drive automatically.
Week 2
Operating systems use file managers to interact with mass storage devices.
However, the way in which data is stored and retrieved is dictated by the file system.
There are many types of file systems used by modern operating systems. Find and
summarise ONE resource that describes ONE such file system that is NOT FAT,
FAT32 or ExFAT. The resource, and your summary, must focus on A SINGLE file
system.
Title and Reference: NTFS FILE SYSTEM
Base, K. (2019). Introduction to file systems – UFS Explorer. [online] UFS Explorer.
Available at: https://www.ufsexplorer.com/articles/file-systems-basics.php [Accessed
30 May 2019].
Summary:
The NTFS or the New Technology File System had been introduced in the year of
1993 with the Windows NT and it is presently the major mutual file system for the
end user computers running on Windows. Majority of the operating systems of
windows server line utilises the format along with it. This file system is significantly
dependable to the journaling and then supporting the several features that includes
the access control, and the encryption. Each of the file in the NTFS is stored as the
descriptor of the file within the master file table and the file content. This Master file
table comprises of the entries along with all the information regarding the files that
includes the details of the size, name and the allocation. The initial 16 entries of
Master File Table are recalled for BitMap that keeps the records as free and then
used the clusters, the log utilised for the journaling documents and BadClus
comprising of the information regarding the bad clusters.
2

Week 3
The National Broadband Network (NBN) is currently being rolled-out across Australia
and there is a mix of technologies that are being used to deliver Internet services (for
example, FTTN, FTTC, FTTP, HFC, fixed wireless and satellite). Find and
summarise ONE resource that describes ONE of these delivery technologies. The
resource, and your summary, must focus on A SINGLE technology.
Title and Reference: Fibre to the Premises or FTTP
Cableorganizer.com. (2019). Understanding Fiber to the Premises (FTTP) - Fiber
Optic Tutorial. [online] Available at: https://www.cableorganizer.com/learning-
center/articles/fiber-optics-tutorial/understanding-fttp.html [Accessed 30 May 2019].
Summary:
The fibre to the premises is the kind of the fiber optic communication delivery where
the optical fibre is provided directly into the premises of the customers. This
innovative technology introduces the remarkable speed and the altogether innovative
experience of broadband. The Fiber to the Premises utilises the cables of fiber optic
and the linked optical electronics rather than the copper wire for connecting the
customer to the network. The Central office helps in the distribution of the optical
signal over the optical distribution network. At end of the network, the optical network
terminals would easily convert all the optical signal into the electrical signal. Optical
network terminals are situated on the private property for the FTTP network
architectures as well as the signal commonly travels with the electrical medium
among the devices of the end users and the ONT. With the effective utilisation of the
FTTP, the innovative services and the products could be easily activated remotely,
either permanently or on the demand according the preferences of the customer. The
performance of FTTP could be monitored and prior any identification of any kind of
problem, the problem is repaired.
Week 4
The Internet is made up of many interconnected servers and networks. Users are
increasingly aware and concerned that their Internet communications can be
intercepted and monitored. Tor is one technology that allows users to obscure or
hide online their online activities. Find and summarise ONE resource that describes
what Tor is and how it works. The resource, and your summary, must focus purely on
Tor.
Title and Reference: Tor
Vpnmentor.com. (2019). The Ultimate Guide to Tor Browser (with Important Tips)
2019. [online] Available at: https://www.vpnmentor.com/blog/tor-browser-work-relate-
using-vpn/ [Accessed 30 May 2019].
Summary:
The browser TOR could be considered as similar to the normal web browser in
several manners. It is not so difficult to utilise than the Google Chrome or Microsoft
Edge. The major difference among these browser and the TOR browser is that the
Tor browser helps in creating the connection among the user and the internet using
the Tor network. The Tor is the software that is open source and it helps in staying
hidden in the online platform for executing the effective use of the internet. when any
user browse the internet with the utilisation of the Tor browser, this traffic of the user
is haphazardly directed via the network of servers prior reaching the ultimate
3
The National Broadband Network (NBN) is currently being rolled-out across Australia
and there is a mix of technologies that are being used to deliver Internet services (for
example, FTTN, FTTC, FTTP, HFC, fixed wireless and satellite). Find and
summarise ONE resource that describes ONE of these delivery technologies. The
resource, and your summary, must focus on A SINGLE technology.
Title and Reference: Fibre to the Premises or FTTP
Cableorganizer.com. (2019). Understanding Fiber to the Premises (FTTP) - Fiber
Optic Tutorial. [online] Available at: https://www.cableorganizer.com/learning-
center/articles/fiber-optics-tutorial/understanding-fttp.html [Accessed 30 May 2019].
Summary:
The fibre to the premises is the kind of the fiber optic communication delivery where
the optical fibre is provided directly into the premises of the customers. This
innovative technology introduces the remarkable speed and the altogether innovative
experience of broadband. The Fiber to the Premises utilises the cables of fiber optic
and the linked optical electronics rather than the copper wire for connecting the
customer to the network. The Central office helps in the distribution of the optical
signal over the optical distribution network. At end of the network, the optical network
terminals would easily convert all the optical signal into the electrical signal. Optical
network terminals are situated on the private property for the FTTP network
architectures as well as the signal commonly travels with the electrical medium
among the devices of the end users and the ONT. With the effective utilisation of the
FTTP, the innovative services and the products could be easily activated remotely,
either permanently or on the demand according the preferences of the customer. The
performance of FTTP could be monitored and prior any identification of any kind of
problem, the problem is repaired.
Week 4
The Internet is made up of many interconnected servers and networks. Users are
increasingly aware and concerned that their Internet communications can be
intercepted and monitored. Tor is one technology that allows users to obscure or
hide online their online activities. Find and summarise ONE resource that describes
what Tor is and how it works. The resource, and your summary, must focus purely on
Tor.
Title and Reference: Tor
Vpnmentor.com. (2019). The Ultimate Guide to Tor Browser (with Important Tips)
2019. [online] Available at: https://www.vpnmentor.com/blog/tor-browser-work-relate-
using-vpn/ [Accessed 30 May 2019].
Summary:
The browser TOR could be considered as similar to the normal web browser in
several manners. It is not so difficult to utilise than the Google Chrome or Microsoft
Edge. The major difference among these browser and the TOR browser is that the
Tor browser helps in creating the connection among the user and the internet using
the Tor network. The Tor is the software that is open source and it helps in staying
hidden in the online platform for executing the effective use of the internet. when any
user browse the internet with the utilisation of the Tor browser, this traffic of the user
is haphazardly directed via the network of servers prior reaching the ultimate
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
destination for providing the effective protection and security to the user. in spite of
the complex system of the browser, it is significantly easy to use. The Tor utilises the
distinct systems that had been developed by US navy for providing the required
protection to the intelligence communications of the government. The data is
efficiently coupled into the layers of the encrypted packets prior entering the Tor
Network. It is therefore routed via the series of nodes that could be considered as the
servers operated by volunteer or the relays. Each time any amount of data passes
from one of the relays, the layer of encryption is eliminated for revealing the location
of next relay. When the data reaches the ultimate relay on the path, that is referred
as the exit node, the last layer of the encryption is eliminated and the data is easily
transmitted to the destination.
Week 5
An emerging form of malware is cryptojacking (also known as malicious
cryptomining). Find and summarise ONE resource that describes what cryptojacking
is and how it works. The resource, and your summary, should focus purely on
cryptojacking and NO OTHER form(s) of malware.
Title and Reference: Cryptojacking
Us.norton.com. (2019). What is cryptojacking? How it works and how to prevent it.
[online] Available at: https://us.norton.com/internetsecurity-malware-what-is-
cryptojacking.html [Accessed 30 May 2019].
Summary:
The cryptojacking could be described as the unauthorised utilisation of any
computer, the tablets, any mobile phone or the connected home devices by the
cybercriminals for the mining for cryptocurrency. The cryptocurrency could be
described as the form of digital money that could be utilised in the online platform for
the executing the shopping of the goods, services, the real money. The users could
perform the mining of the cryptocurrency on the computers by the utilisation of the
privileged programs for the solving of complex, the encrypted math equations for
gaining any piece of the currency. The monetary value of cryptocurrency could not
be described efficiently, moreover it is founded on the section on ideology of the
supply as well as demand, and the difficulty of gaining the cryptocurrency. As an
example, it could be considered that there are solely finite number of the bitcoins that
are not totally mined. There are significant other variables like how easy this currency
for using, the equipment and the energy that is required for the mining of the
currency.
Week 6
Redundancy is a critical aspect of network design, implemented in order to cope link
or equipment failure. One frequent cause of failure is damage to fibre optic cables
that connect countries and/or continents. Find and summarise ONE resource that
describes ONE example of such a cable being cut or damaged. The resource, and
your summary, should describe the impacts of A SINGLE EXAMPLE of a link failure.
Note that the failure must relate to a link that connects countries and/or continents.
Title and Reference: Fault in the optical fibre communication in Ghana
Iosrjournals.org. (2019). [online] Available at:
http://www.iosrjournals.org/iosr-jece/papers/Vol.%2012%20Issue%201/Version-1/
H1201014664.pdf [Accessed 30 May 2019].
Summary:
4
the complex system of the browser, it is significantly easy to use. The Tor utilises the
distinct systems that had been developed by US navy for providing the required
protection to the intelligence communications of the government. The data is
efficiently coupled into the layers of the encrypted packets prior entering the Tor
Network. It is therefore routed via the series of nodes that could be considered as the
servers operated by volunteer or the relays. Each time any amount of data passes
from one of the relays, the layer of encryption is eliminated for revealing the location
of next relay. When the data reaches the ultimate relay on the path, that is referred
as the exit node, the last layer of the encryption is eliminated and the data is easily
transmitted to the destination.
Week 5
An emerging form of malware is cryptojacking (also known as malicious
cryptomining). Find and summarise ONE resource that describes what cryptojacking
is and how it works. The resource, and your summary, should focus purely on
cryptojacking and NO OTHER form(s) of malware.
Title and Reference: Cryptojacking
Us.norton.com. (2019). What is cryptojacking? How it works and how to prevent it.
[online] Available at: https://us.norton.com/internetsecurity-malware-what-is-
cryptojacking.html [Accessed 30 May 2019].
Summary:
The cryptojacking could be described as the unauthorised utilisation of any
computer, the tablets, any mobile phone or the connected home devices by the
cybercriminals for the mining for cryptocurrency. The cryptocurrency could be
described as the form of digital money that could be utilised in the online platform for
the executing the shopping of the goods, services, the real money. The users could
perform the mining of the cryptocurrency on the computers by the utilisation of the
privileged programs for the solving of complex, the encrypted math equations for
gaining any piece of the currency. The monetary value of cryptocurrency could not
be described efficiently, moreover it is founded on the section on ideology of the
supply as well as demand, and the difficulty of gaining the cryptocurrency. As an
example, it could be considered that there are solely finite number of the bitcoins that
are not totally mined. There are significant other variables like how easy this currency
for using, the equipment and the energy that is required for the mining of the
currency.
Week 6
Redundancy is a critical aspect of network design, implemented in order to cope link
or equipment failure. One frequent cause of failure is damage to fibre optic cables
that connect countries and/or continents. Find and summarise ONE resource that
describes ONE example of such a cable being cut or damaged. The resource, and
your summary, should describe the impacts of A SINGLE EXAMPLE of a link failure.
Note that the failure must relate to a link that connects countries and/or continents.
Title and Reference: Fault in the optical fibre communication in Ghana
Iosrjournals.org. (2019). [online] Available at:
http://www.iosrjournals.org/iosr-jece/papers/Vol.%2012%20Issue%201/Version-1/
H1201014664.pdf [Accessed 30 May 2019].
Summary:
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
The technology of optical fiber has significantly transformed the landscape of the
telecom industry within Ghana in the past recent years and this modification is
majorly owed to the overwhelming advantages over conventional medium of
transmission. Even though this technology is significantly immune to the
electromagnetic waves, it provides the increased capacity of bandwidth for the voice
and the data activities. The infrastructure of fiber within Ghana has immensely
experienced significant lot to the incidences of the fiber cuts. And this particular event
has immensely affected the quality delivery of the network, the increased expenditure
in the operations and the decline in the revenue margins of telecommunications. The
research in this resources determined that the activities of the projects that are
sponsored by the government and the private developers are majorly responsible for
the damage of the optic fibres because of the negligence, the ignorance, and the lack
of effective coordination. The impact of this damage to the fiber optics led to the
unavailability of internet for the common people all across the sections where the
projects are executed.
Week 7
Since the 1990s, Enterprise Systems (also known as Enterprise Resource Planning
systems) have become critical to the operation modern organisations. Over this
time, ES/ERPs have evolved and continue to change in response to new demands
and emerging technologies. Find and summarise ONE resource that discusses
emerging or future trends for ES/ERPs. The resource should be recent (published
since the beginning of 2017) and it and your summary should clearly identify how
ES/ERPs are, or are about to, change.
Title and Reference: Future trends of ERP systems
Accenture.com. (2019). [online] Available at:
https://www.accenture.com/_acnmedia/PDF-90/Accenture-Unleashing-Exponential-
Evolution-PDF.pdf [Accessed 30 May 2019].
Summary:
The technology is developing at exponential rate and the companies are immensely
struggling to manage the pace with the digital revolution with the enterprise
technologies, which are increasingly inflexible and are increasingly obsolete, even
though the customers are increasingly demanding for the improved products and the
enhanced services from the organisation. The research conducted in this resources
indicates that the future trends for the development of the enhanced ERP systems
are presently being tested and it is being severely implemented. The major future
trends could be the integration of the ERP systems to the cloud storage of the
companies that suggests the development of balanced strategy of cloud that is
appropriate for the ambitions of the business. The proper engineering of the cloud
storage as the section of the larger strategy around the digital transformation, the
cost savings and the innovative business models. The ERP systems could be further
developed with the integration of the automation within the business that is powered
by the use of artificial intelligence, analytics and the machine learning.
Week 8
Databases, mass data storage and interrogation technologies underpin virtually all
Information Systems and applications. However, the same tools also make it easier
5
telecom industry within Ghana in the past recent years and this modification is
majorly owed to the overwhelming advantages over conventional medium of
transmission. Even though this technology is significantly immune to the
electromagnetic waves, it provides the increased capacity of bandwidth for the voice
and the data activities. The infrastructure of fiber within Ghana has immensely
experienced significant lot to the incidences of the fiber cuts. And this particular event
has immensely affected the quality delivery of the network, the increased expenditure
in the operations and the decline in the revenue margins of telecommunications. The
research in this resources determined that the activities of the projects that are
sponsored by the government and the private developers are majorly responsible for
the damage of the optic fibres because of the negligence, the ignorance, and the lack
of effective coordination. The impact of this damage to the fiber optics led to the
unavailability of internet for the common people all across the sections where the
projects are executed.
Week 7
Since the 1990s, Enterprise Systems (also known as Enterprise Resource Planning
systems) have become critical to the operation modern organisations. Over this
time, ES/ERPs have evolved and continue to change in response to new demands
and emerging technologies. Find and summarise ONE resource that discusses
emerging or future trends for ES/ERPs. The resource should be recent (published
since the beginning of 2017) and it and your summary should clearly identify how
ES/ERPs are, or are about to, change.
Title and Reference: Future trends of ERP systems
Accenture.com. (2019). [online] Available at:
https://www.accenture.com/_acnmedia/PDF-90/Accenture-Unleashing-Exponential-
Evolution-PDF.pdf [Accessed 30 May 2019].
Summary:
The technology is developing at exponential rate and the companies are immensely
struggling to manage the pace with the digital revolution with the enterprise
technologies, which are increasingly inflexible and are increasingly obsolete, even
though the customers are increasingly demanding for the improved products and the
enhanced services from the organisation. The research conducted in this resources
indicates that the future trends for the development of the enhanced ERP systems
are presently being tested and it is being severely implemented. The major future
trends could be the integration of the ERP systems to the cloud storage of the
companies that suggests the development of balanced strategy of cloud that is
appropriate for the ambitions of the business. The proper engineering of the cloud
storage as the section of the larger strategy around the digital transformation, the
cost savings and the innovative business models. The ERP systems could be further
developed with the integration of the automation within the business that is powered
by the use of artificial intelligence, analytics and the machine learning.
Week 8
Databases, mass data storage and interrogation technologies underpin virtually all
Information Systems and applications. However, the same tools also make it easier
5

for data breaches to occur in government departments or private
companies/organisations. In simple terms, a data breach is where private
information is illegally obtained or disclosed. Find and summarise ONE resource that
describes ONE example of a data breach that has occurred since the beginning of
2017. The resource, and your summary, should focus purely on A SINGLE
EXAMPLE of a data breach.
Title and Reference: Equifax data breach
Ec.unipi.it. (2019). [online] Available at:
https://www.ec.unipi.it/wp-content/uploads/2019/03/EquiFaxCase.pdf [Accessed 30
May 2019].
Summary:
The case of Equifax is considered as one of the major data breaches to have ever
occurred and it is the massive breach of the sensitive financial and the personal
information that included the social security numbers, the addresses and the birth
dates and in some of the situations the driver license numbers, the credit card
information and the documents of the financial disputes. The Equifax is considered
as the major agency for credit reporting, which are tasked with the safeguarding the
sensitive records of the credit cards and the personal information of the customers
who have placed their data within the system of the company. This breach within the
servers of Equifax initiated with major exploitation of the vulnerability on March 10,
2017. All the major actors behind this attack spent almost two months elevating the
access and the exploration of network of Equifax, till the time they were finally able to
execute this attack and initiated the accessing of the files with the Personally
Identifiable Information on May 13 of 2017 and the security vulnerabilities allowed the
access had been remedied on July 30 of 2017.
Week 9
Agile development is an iterative and incremental approach to delivering systems - it
is particularly useful where the requirements are unclear or evolving. Scrum is a
framework for undertaking agile development. Find and summarise ONE resource
that describes Scrum. The resource, and your summary, should focus purely on
Scrum and discuss some of its key features and attributes.
Title and Reference: SCRUM features
Patel, C., Espy, L. and Bashyam, M. (2019). 4 Features That Make Scrum
Successful. [online] KnowledgeHut Blog. Available at:
https://www.knowledgehut.com/blog/agile/4-features-that-make-scrum-successful
[Accessed 30 May 2019].
Summary:
In the present years, there have been the major development of one tool that has
significantly proved to be successful on many situations and in the multiple projects
all across the globe is the Scrum methodology. The scrum could be considered as
the procedure that could be used for implementing the agile structure into the project
with significant success. The scrum has some of the features because of which this
technique is particularly preferred by the professionals all across the globe. This
methodology is extensively utilised because it helps in reducing the effort and it helps
in getting the work done in the systematic manner. Some of the features of the scrum
methodology could be described as sprint sessions, the display of the progress, the
6
companies/organisations. In simple terms, a data breach is where private
information is illegally obtained or disclosed. Find and summarise ONE resource that
describes ONE example of a data breach that has occurred since the beginning of
2017. The resource, and your summary, should focus purely on A SINGLE
EXAMPLE of a data breach.
Title and Reference: Equifax data breach
Ec.unipi.it. (2019). [online] Available at:
https://www.ec.unipi.it/wp-content/uploads/2019/03/EquiFaxCase.pdf [Accessed 30
May 2019].
Summary:
The case of Equifax is considered as one of the major data breaches to have ever
occurred and it is the massive breach of the sensitive financial and the personal
information that included the social security numbers, the addresses and the birth
dates and in some of the situations the driver license numbers, the credit card
information and the documents of the financial disputes. The Equifax is considered
as the major agency for credit reporting, which are tasked with the safeguarding the
sensitive records of the credit cards and the personal information of the customers
who have placed their data within the system of the company. This breach within the
servers of Equifax initiated with major exploitation of the vulnerability on March 10,
2017. All the major actors behind this attack spent almost two months elevating the
access and the exploration of network of Equifax, till the time they were finally able to
execute this attack and initiated the accessing of the files with the Personally
Identifiable Information on May 13 of 2017 and the security vulnerabilities allowed the
access had been remedied on July 30 of 2017.
Week 9
Agile development is an iterative and incremental approach to delivering systems - it
is particularly useful where the requirements are unclear or evolving. Scrum is a
framework for undertaking agile development. Find and summarise ONE resource
that describes Scrum. The resource, and your summary, should focus purely on
Scrum and discuss some of its key features and attributes.
Title and Reference: SCRUM features
Patel, C., Espy, L. and Bashyam, M. (2019). 4 Features That Make Scrum
Successful. [online] KnowledgeHut Blog. Available at:
https://www.knowledgehut.com/blog/agile/4-features-that-make-scrum-successful
[Accessed 30 May 2019].
Summary:
In the present years, there have been the major development of one tool that has
significantly proved to be successful on many situations and in the multiple projects
all across the globe is the Scrum methodology. The scrum could be considered as
the procedure that could be used for implementing the agile structure into the project
with significant success. The scrum has some of the features because of which this
technique is particularly preferred by the professionals all across the globe. This
methodology is extensively utilised because it helps in reducing the effort and it helps
in getting the work done in the systematic manner. Some of the features of the scrum
methodology could be described as sprint sessions, the display of the progress, the
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
burndown chart, and specific meetings. The main feature that is used by the project
managers is the burndown chart. Majority of the organisation use the conventional
progress charts or the graphs that effectively depicts the quantity of the work that has
to be done by the various teams. It is commonly believed that it would help in
boosting the morale of the employees and then encourage them to work harder as
the progress is precisely presented in the chart.
Week 10
The textbook discusses activities associated with project management. However, it
could be argued that project governance is equally important, especially in very large
projects. Find and summarise ONE resource that describes what project governance
is and what activities it entails. The resource, and your summary, should focus purely
on project governance.
Title and Reference: Project governance
Wrike.com. (2019). What is Governance in Project Management?. [online] Available
at: https://www.wrike.com/project-management-guide/faq/what-is-governance-in-
project-management/ [Accessed 30 May 2019].
Summary:
The project governance could be described as the infrastructure that covers the
project dealing with accountability and the responsibility. Commonly, it could be
described as the structure for taking the effective decisions with the regards to
project. The governance in the project management covers all the queries of the
individuals associated with the project. It provides the basis framework of the
oversight to complete project. The key role in the project governance is that of
sponsor who significantly serves as liaison among the project manager, the board as
well as the stakeholders. The project governance could help in the proper
maintenance of the project aspects and the various tasks that are to be executed
within the projects.
7
managers is the burndown chart. Majority of the organisation use the conventional
progress charts or the graphs that effectively depicts the quantity of the work that has
to be done by the various teams. It is commonly believed that it would help in
boosting the morale of the employees and then encourage them to work harder as
the progress is precisely presented in the chart.
Week 10
The textbook discusses activities associated with project management. However, it
could be argued that project governance is equally important, especially in very large
projects. Find and summarise ONE resource that describes what project governance
is and what activities it entails. The resource, and your summary, should focus purely
on project governance.
Title and Reference: Project governance
Wrike.com. (2019). What is Governance in Project Management?. [online] Available
at: https://www.wrike.com/project-management-guide/faq/what-is-governance-in-
project-management/ [Accessed 30 May 2019].
Summary:
The project governance could be described as the infrastructure that covers the
project dealing with accountability and the responsibility. Commonly, it could be
described as the structure for taking the effective decisions with the regards to
project. The governance in the project management covers all the queries of the
individuals associated with the project. It provides the basis framework of the
oversight to complete project. The key role in the project governance is that of
sponsor who significantly serves as liaison among the project manager, the board as
well as the stakeholders. The project governance could help in the proper
maintenance of the project aspects and the various tasks that are to be executed
within the projects.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
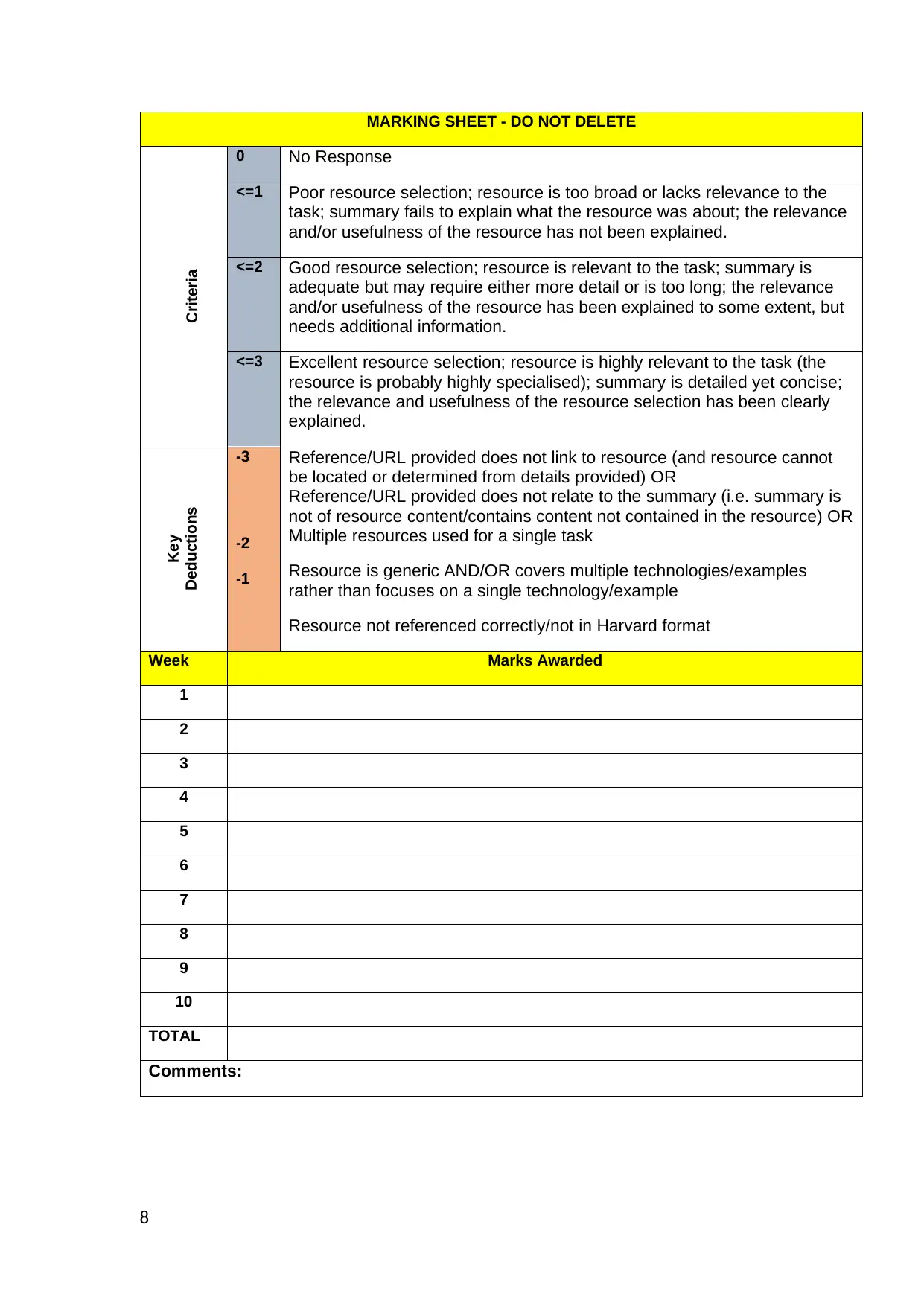
MARKING SHEET - DO NOT DELETE
Criteria
0 No Response
<=1 Poor resource selection; resource is too broad or lacks relevance to the
task; summary fails to explain what the resource was about; the relevance
and/or usefulness of the resource has not been explained.
<=2 Good resource selection; resource is relevant to the task; summary is
adequate but may require either more detail or is too long; the relevance
and/or usefulness of the resource has been explained to some extent, but
needs additional information.
<=3 Excellent resource selection; resource is highly relevant to the task (the
resource is probably highly specialised); summary is detailed yet concise;
the relevance and usefulness of the resource selection has been clearly
explained.
Key
Deductions
-3
-2
-1
Reference/URL provided does not link to resource (and resource cannot
be located or determined from details provided) OR
Reference/URL provided does not relate to the summary (i.e. summary is
not of resource content/contains content not contained in the resource) OR
Multiple resources used for a single task
Resource is generic AND/OR covers multiple technologies/examples
rather than focuses on a single technology/example
Resource not referenced correctly/not in Harvard format
Week Marks Awarded
1
2
3
4
5
6
7
8
9
10
TOTAL
Comments:
8
Criteria
0 No Response
<=1 Poor resource selection; resource is too broad or lacks relevance to the
task; summary fails to explain what the resource was about; the relevance
and/or usefulness of the resource has not been explained.
<=2 Good resource selection; resource is relevant to the task; summary is
adequate but may require either more detail or is too long; the relevance
and/or usefulness of the resource has been explained to some extent, but
needs additional information.
<=3 Excellent resource selection; resource is highly relevant to the task (the
resource is probably highly specialised); summary is detailed yet concise;
the relevance and usefulness of the resource selection has been clearly
explained.
Key
Deductions
-3
-2
-1
Reference/URL provided does not link to resource (and resource cannot
be located or determined from details provided) OR
Reference/URL provided does not relate to the summary (i.e. summary is
not of resource content/contains content not contained in the resource) OR
Multiple resources used for a single task
Resource is generic AND/OR covers multiple technologies/examples
rather than focuses on a single technology/example
Resource not referenced correctly/not in Harvard format
Week Marks Awarded
1
2
3
4
5
6
7
8
9
10
TOTAL
Comments:
8
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



