COIT20262 - Advanced Network Security Assignment 1, Term 1, 2019
VerifiedAdded on 2023/01/20
|7
|1484
|89
Homework Assignment
AI Summary
This assignment solution for COIT20262, Advanced Network Security, covers three key areas: packet capture and analysis, cryptography, and denial-of-service (DoS) attacks. The packet analysis section includes a message sequence chart, extraction of information from packets (time, IP addresses, MAC addresses, timestamps, and checksums), and discussions on security measures to prevent unauthorized access. The cryptography section explores authenticated emails, digital signatures, and their security implications, including vulnerabilities like key conformation attacks and man-in-the-middle attacks. The DoS attack research section provides an overview of DDoS attacks, entities involved, and a specific analysis of ping flooding attacks, including mitigation techniques. The solution incorporates references to relevant research papers and provides a comprehensive understanding of network security principles and practices.
COIT20262 Term 1, 2019
COIT20262 - Advanced Network Security, Term 1, 2019
Due date: 5pm Friday 26 April 2019 (Week 6) ASSESSMENT
Weighting: 40%
1Length: N/A
Student Name: enter your name
Student ID: id
Campus: campus
Tutor: tutor
Page 1 of 7
COIT20262 - Advanced Network Security, Term 1, 2019
Due date: 5pm Friday 26 April 2019 (Week 6) ASSESSMENT
Weighting: 40%
1Length: N/A
Student Name: enter your name
Student ID: id
Campus: campus
Tutor: tutor
Page 1 of 7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
COIT20262 Term 1, 2019
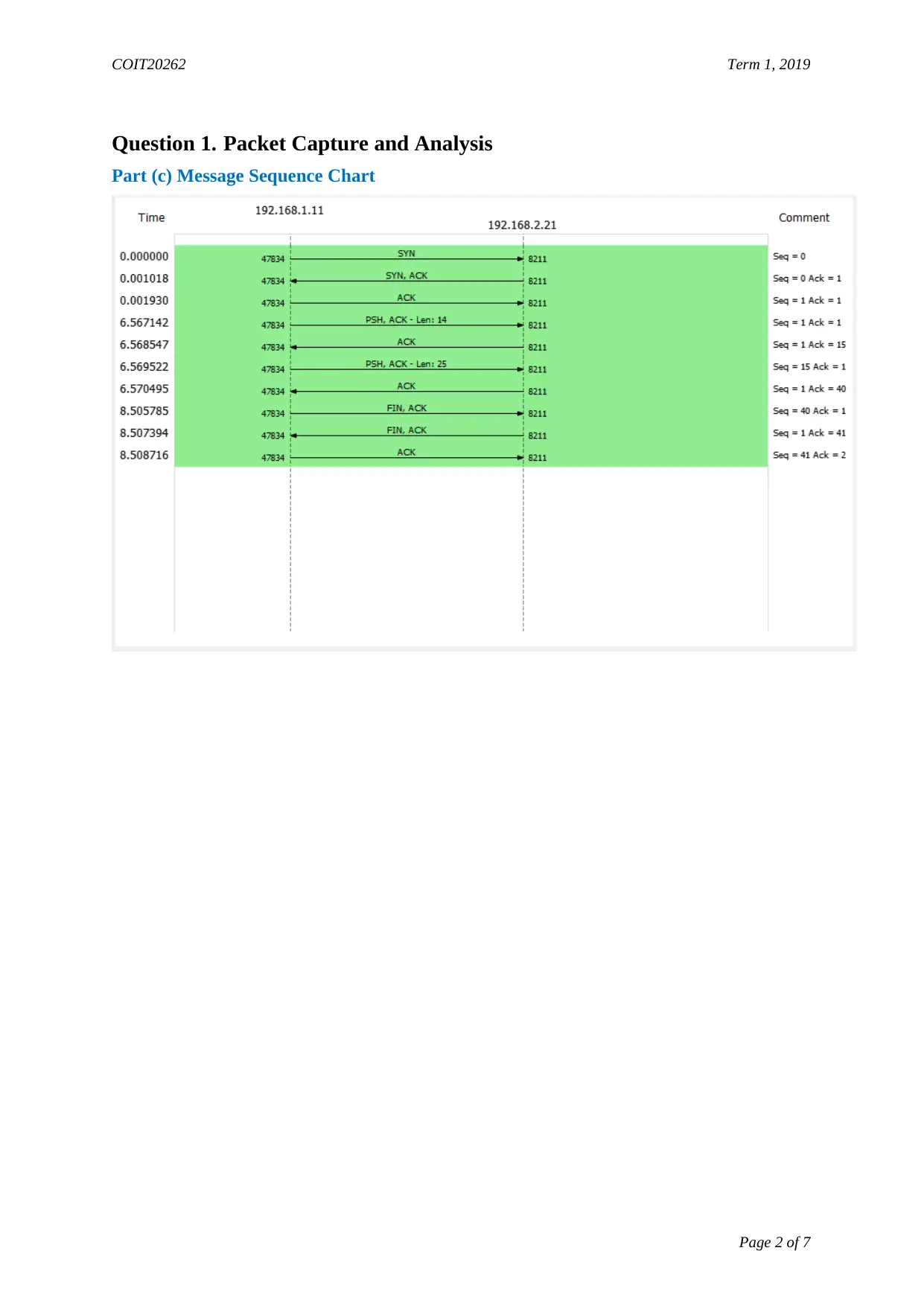
Question 1. Packet Capture and Analysis
Part (c) Message Sequence Chart
Page 2 of 7
Question 1. Packet Capture and Analysis
Part (c) Message Sequence Chart
Page 2 of 7
COIT20262 Term 1, 2019
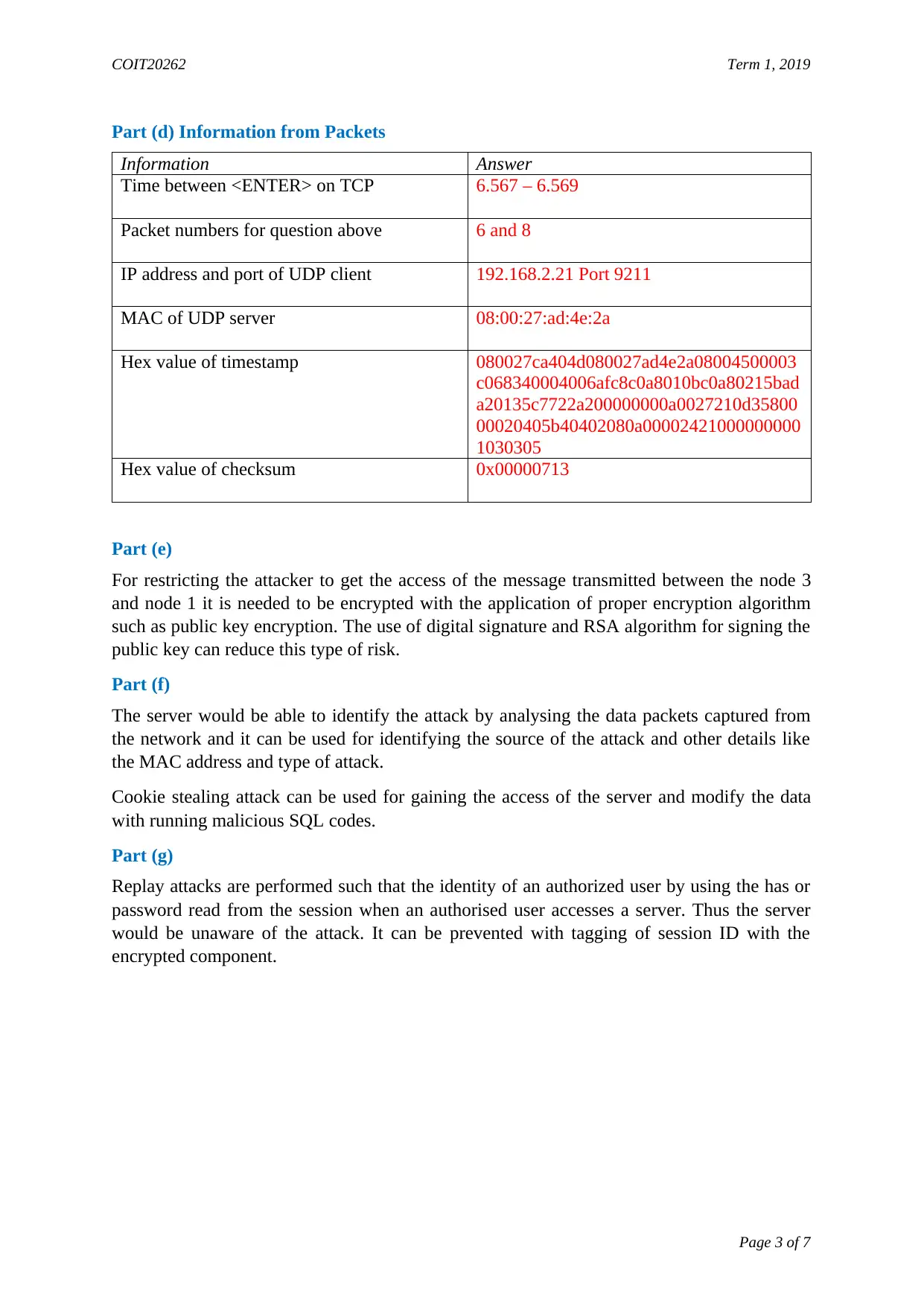
Part (d) Information from Packets
Information Answer
Time between <ENTER> on TCP 6.567 – 6.569
Packet numbers for question above 6 and 8
IP address and port of UDP client 192.168.2.21 Port 9211
MAC of UDP server 08:00:27:ad:4e:2a
Hex value of timestamp 080027ca404d080027ad4e2a08004500003
c068340004006afc8c0a8010bc0a80215bad
a20135c7722a200000000a0027210d35800
00020405b40402080a00002421000000000
1030305
Hex value of checksum 0x00000713
Part (e)
For restricting the attacker to get the access of the message transmitted between the node 3
and node 1 it is needed to be encrypted with the application of proper encryption algorithm
such as public key encryption. The use of digital signature and RSA algorithm for signing the
public key can reduce this type of risk.
Part (f)
The server would be able to identify the attack by analysing the data packets captured from
the network and it can be used for identifying the source of the attack and other details like
the MAC address and type of attack.
Cookie stealing attack can be used for gaining the access of the server and modify the data
with running malicious SQL codes.
Part (g)
Replay attacks are performed such that the identity of an authorized user by using the has or
password read from the session when an authorised user accesses a server. Thus the server
would be unaware of the attack. It can be prevented with tagging of session ID with the
encrypted component.
Page 3 of 7
Part (d) Information from Packets
Information Answer
Time between <ENTER> on TCP 6.567 – 6.569
Packet numbers for question above 6 and 8
IP address and port of UDP client 192.168.2.21 Port 9211
MAC of UDP server 08:00:27:ad:4e:2a
Hex value of timestamp 080027ca404d080027ad4e2a08004500003
c068340004006afc8c0a8010bc0a80215bad
a20135c7722a200000000a0027210d35800
00020405b40402080a00002421000000000
1030305
Hex value of checksum 0x00000713
Part (e)
For restricting the attacker to get the access of the message transmitted between the node 3
and node 1 it is needed to be encrypted with the application of proper encryption algorithm
such as public key encryption. The use of digital signature and RSA algorithm for signing the
public key can reduce this type of risk.
Part (f)
The server would be able to identify the attack by analysing the data packets captured from
the network and it can be used for identifying the source of the attack and other details like
the MAC address and type of attack.
Cookie stealing attack can be used for gaining the access of the server and modify the data
with running malicious SQL codes.
Part (g)
Replay attacks are performed such that the identity of an authorized user by using the has or
password read from the session when an authorised user accesses a server. Thus the server
would be unaware of the attack. It can be prevented with tagging of session ID with the
encrypted component.
Page 3 of 7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

COIT20262 Term 1, 2019
Question 2. Cryptography
Part (c)
Authenticated emails are able to safeguards the sender and the receiver from any type of
external threats while they are exchanging data between themselves but it does not provide
any type of security against each other. Protection among the sender and the receiver is
required as there can be some fraud among themselves. For an instance the receiver may deny
that any type of mail has been arrived from sender. While that key is posted to the moodle
forum it become also vulnerable as hacker is able to get the key by hacking any of the
student’s account. Key conformation attack is a big concern in this case as through this
messages can be easily intercepted. Other attacks are the known message attack and key-only
attack.
Part (d)
Simple authentication is not enough security in present situation for exchanging important
information. Thus digital signature can be implemented in this case for verifying the
distributed keys. A proper digital signature needs to fulfil some requirements which are:
1. Digital signature copy must be stored in secondary type of storage.
2. Proper bit pattern must be followed which depends on signed message.
3. Signature must be capable of preventing forgery and denial.
Part (e)
The digital signature is having a high security scheme and provides a high level of
confidentiality compared with the previous steps of key distribution. In this case digital
signature encrypts entire message. Thus public can be distributed more securely. In this
aspect the digital signature successfully eliminates man in the middle attack. The main
drawback of this system is that if the private key is stolen somehow then it can be used
against the user from whom the key is stolen.
Page 4 of 7
Question 2. Cryptography
Part (c)
Authenticated emails are able to safeguards the sender and the receiver from any type of
external threats while they are exchanging data between themselves but it does not provide
any type of security against each other. Protection among the sender and the receiver is
required as there can be some fraud among themselves. For an instance the receiver may deny
that any type of mail has been arrived from sender. While that key is posted to the moodle
forum it become also vulnerable as hacker is able to get the key by hacking any of the
student’s account. Key conformation attack is a big concern in this case as through this
messages can be easily intercepted. Other attacks are the known message attack and key-only
attack.
Part (d)
Simple authentication is not enough security in present situation for exchanging important
information. Thus digital signature can be implemented in this case for verifying the
distributed keys. A proper digital signature needs to fulfil some requirements which are:
1. Digital signature copy must be stored in secondary type of storage.
2. Proper bit pattern must be followed which depends on signed message.
3. Signature must be capable of preventing forgery and denial.
Part (e)
The digital signature is having a high security scheme and provides a high level of
confidentiality compared with the previous steps of key distribution. In this case digital
signature encrypts entire message. Thus public can be distributed more securely. In this
aspect the digital signature successfully eliminates man in the middle attack. The main
drawback of this system is that if the private key is stolen somehow then it can be used
against the user from whom the key is stolen.
Page 4 of 7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
COIT20262 Term 1, 2019
Question 3. Denial of Service Attack Research
Overview of DDoS Attacks
The DoS attack or the Denial of service attack is one of the common attack which is
performed on computers for shutting down the system and the networks. This DoS attack
makes the system machine and the network inaccessible to the users. Malicious information
is send by the attacker for performing the DoS attack and due to this system of the victim
computer crashes. Here the DoS attack is performed by flooding the victim system with a
large number of data packets or in many cases malicious codes are send to the system of
victim which leads to system crash.
The Distributed Denial of Service attack is the DDoS attack and it also targets the
network of the victim. Trojans are used in this case for performing this attack while in DoS
high amount of data packets are used.
In this case the DDoS attack is different from the DoS attack as the DDoS attack
targets network connection that are multiple in nature. In the case of DoS attack only targets
some single network connection or some single computer system.
In the current situation DoS attack targets information for a specific type of
information requirement while the DDoS attack is able to get the access of the server
resources. Thus the DoS attack provides specific data while access on the server resources
provides a bulk amount of data.
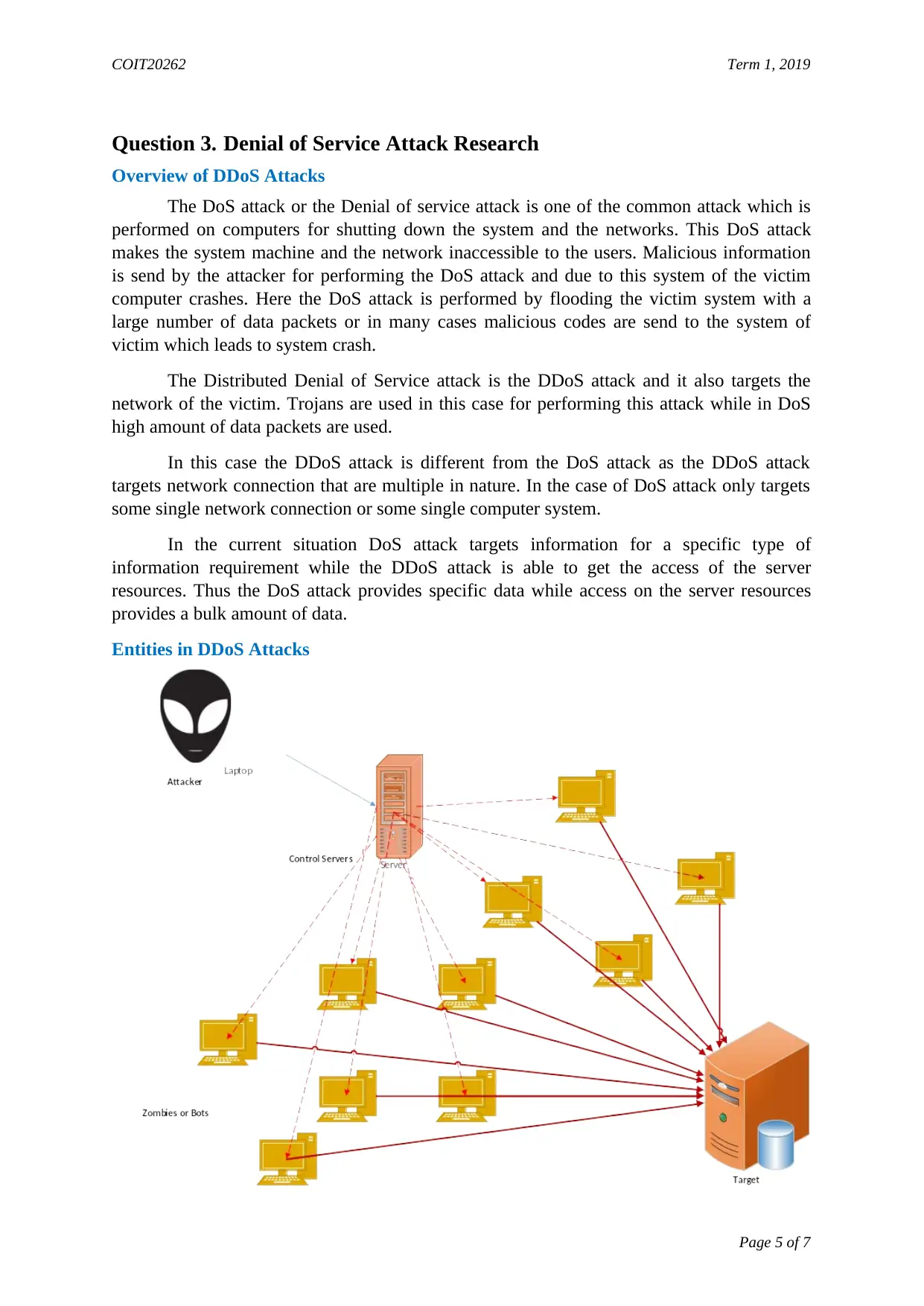
Entities in DDoS Attacks
Page 5 of 7
Question 3. Denial of Service Attack Research
Overview of DDoS Attacks
The DoS attack or the Denial of service attack is one of the common attack which is
performed on computers for shutting down the system and the networks. This DoS attack
makes the system machine and the network inaccessible to the users. Malicious information
is send by the attacker for performing the DoS attack and due to this system of the victim
computer crashes. Here the DoS attack is performed by flooding the victim system with a
large number of data packets or in many cases malicious codes are send to the system of
victim which leads to system crash.
The Distributed Denial of Service attack is the DDoS attack and it also targets the
network of the victim. Trojans are used in this case for performing this attack while in DoS
high amount of data packets are used.
In this case the DDoS attack is different from the DoS attack as the DDoS attack
targets network connection that are multiple in nature. In the case of DoS attack only targets
some single network connection or some single computer system.
In the current situation DoS attack targets information for a specific type of
information requirement while the DDoS attack is able to get the access of the server
resources. Thus the DoS attack provides specific data while access on the server resources
provides a bulk amount of data.
Entities in DDoS Attacks
Page 5 of 7

COIT20262 Term 1, 2019
Ping Flooding Attack
The ping flooding attack is also a specific type of DDoS attack. Another instance of
this attack is the ICMP attack. Here for taking down the computers of the victim ICMP echo
requests is used. The echo requests is also compared with the ping.
The ping is generally used for verification of an active network connection among
two different computers. Ping response time is successfully used for determination of the
newt wok speed. For performing the ping flooding attack the computer of the victim is
flooded by huge amount of data packets. Here the whole system need to follow some aspects
that are very much important. These are discussed below.
Ping commands must be used for performing the ping flooding attack.
IP of the victim must be known by the attacker.
Attacker need to have greater bandwidth compared with the victim.
Mitigating Ping Flooding Attack
Firewall can be reconfigured in this case for the mitigation of the ping flooding attack.
It is one of the efficient way of mitigating the ping flooding attack as in this reconfiguration
process, all the network packets which comes from outside of the network is dismissed. Only
the data packets come from the within the network is passed by the firewall. One major flaw
of the firewall protection is that in this case when the attacker will send the unnecessary data
packets within the network system then this firewall will allow the malicious data packets
which will lead to system crash of the victim.
Page 6 of 7
Ping Flooding Attack
The ping flooding attack is also a specific type of DDoS attack. Another instance of
this attack is the ICMP attack. Here for taking down the computers of the victim ICMP echo
requests is used. The echo requests is also compared with the ping.
The ping is generally used for verification of an active network connection among
two different computers. Ping response time is successfully used for determination of the
newt wok speed. For performing the ping flooding attack the computer of the victim is
flooded by huge amount of data packets. Here the whole system need to follow some aspects
that are very much important. These are discussed below.
Ping commands must be used for performing the ping flooding attack.
IP of the victim must be known by the attacker.
Attacker need to have greater bandwidth compared with the victim.
Mitigating Ping Flooding Attack
Firewall can be reconfigured in this case for the mitigation of the ping flooding attack.
It is one of the efficient way of mitigating the ping flooding attack as in this reconfiguration
process, all the network packets which comes from outside of the network is dismissed. Only
the data packets come from the within the network is passed by the firewall. One major flaw
of the firewall protection is that in this case when the attacker will send the unnecessary data
packets within the network system then this firewall will allow the malicious data packets
which will lead to system crash of the victim.
Page 6 of 7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

COIT20262 Term 1, 2019
Reference:
Guo, Y., Ten, C.W., Hu, S. and Weaver, W.W., 2015, February. Modeling distributed denial
of service attack in advanced metering infrastructure. In 2015 IEEE Power & Energy Society
Innovative Smart Grid Technologies Conference (ISGT) (pp. 1-5). IEEE.
Jenny, R.S. and Narayanaswamy, S., 2017. Impact of Ping Flood Attack and its Mitigation
Technique: A Performance Evaluation. Journal of Network Security, 5(1), pp.11-21.
Lai, H., Luo, M., Pieprzyk, J., Qu, Z., Li, S. and Orgun, M.A., 2017. An efficient quantum
blind digital signature scheme. Science China Information Sciences, 60(8), p.082501.
Qin, J., Li, M., Shi, L. and Yu, X., 2018. Optimal denial-of-service attack scheduling with
energy constraint over packet-dropping networks. IEEE Transactions on Automatic
Control, 63(6), pp.1648-1663.
Tripathi, S.K. and Gupta, B., 2016. A New Probabilistic Digital Signature Scheme Based on
Integer Factorization Problem. In Information Science and Applications (ICISA) 2016 (pp.
613-621). Springer, Singapore.
Xue, Y., Tan, Y.A., Liang, C., Li, Y., Zheng, J. and Zhang, Q., 2018. RootAgency: A digital
signature-based root privilege management agency for cloud terminal devices. Information
Sciences, 444, pp.36-50.
Page 7 of 7
Reference:
Guo, Y., Ten, C.W., Hu, S. and Weaver, W.W., 2015, February. Modeling distributed denial
of service attack in advanced metering infrastructure. In 2015 IEEE Power & Energy Society
Innovative Smart Grid Technologies Conference (ISGT) (pp. 1-5). IEEE.
Jenny, R.S. and Narayanaswamy, S., 2017. Impact of Ping Flood Attack and its Mitigation
Technique: A Performance Evaluation. Journal of Network Security, 5(1), pp.11-21.
Lai, H., Luo, M., Pieprzyk, J., Qu, Z., Li, S. and Orgun, M.A., 2017. An efficient quantum
blind digital signature scheme. Science China Information Sciences, 60(8), p.082501.
Qin, J., Li, M., Shi, L. and Yu, X., 2018. Optimal denial-of-service attack scheduling with
energy constraint over packet-dropping networks. IEEE Transactions on Automatic
Control, 63(6), pp.1648-1663.
Tripathi, S.K. and Gupta, B., 2016. A New Probabilistic Digital Signature Scheme Based on
Integer Factorization Problem. In Information Science and Applications (ICISA) 2016 (pp.
613-621). Springer, Singapore.
Xue, Y., Tan, Y.A., Liang, C., Li, Y., Zheng, J. and Zhang, Q., 2018. RootAgency: A digital
signature-based root privilege management agency for cloud terminal devices. Information
Sciences, 444, pp.36-50.
Page 7 of 7
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




