COIT20262 Term 1 Assignment 1: Advanced Network Security Analysis
VerifiedAdded on 2023/01/20
|7
|1565
|52
Homework Assignment
AI Summary
This assignment submission for COIT20262, Advanced Network Security, explores various aspects of network security. The assignment is divided into three main sections: Packet Capture and Analysis, Cryptography, and Denial of Service (DoS) Attacks. The Packet Capture section involves analyzing network traffic, including message sequence charts, identifying packet information like IP addresses, ports, MAC addresses, and timestamps, and discussing security risks and mitigation strategies. The Cryptography section delves into authenticated emails, digital signatures, and their properties, as well as their role in securing message exchanges and key distribution, including discussions on potential attacks such as "Key Conformation" and "Known Message Attack". The final section focuses on Denial of Service (DoS) attacks, providing an overview of DDoS attacks, including the Ping Flooding attack, its entities, and mitigation techniques. The submission includes a bibliography of relevant research papers.
COIT20262 Assignment 1 Submission Term 1, 2019
COIT20262 - Advanced Network Security, Term 1, 2019
Assignment 1 Submission
Due date: 5pm Friday 26 April 2019 (Week 6) ASSESSMENT
Weighting: 40%
1Length: N/A
Student Name: enter your name
Student ID: id
Campus: campus
Tutor: tutor
Advanced Network Security Page 1 of 7
COIT20262 - Advanced Network Security, Term 1, 2019
Assignment 1 Submission
Due date: 5pm Friday 26 April 2019 (Week 6) ASSESSMENT
Weighting: 40%
1Length: N/A
Student Name: enter your name
Student ID: id
Campus: campus
Tutor: tutor
Advanced Network Security Page 1 of 7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
COIT20262 Assignment 1 Submission Term 1, 2019
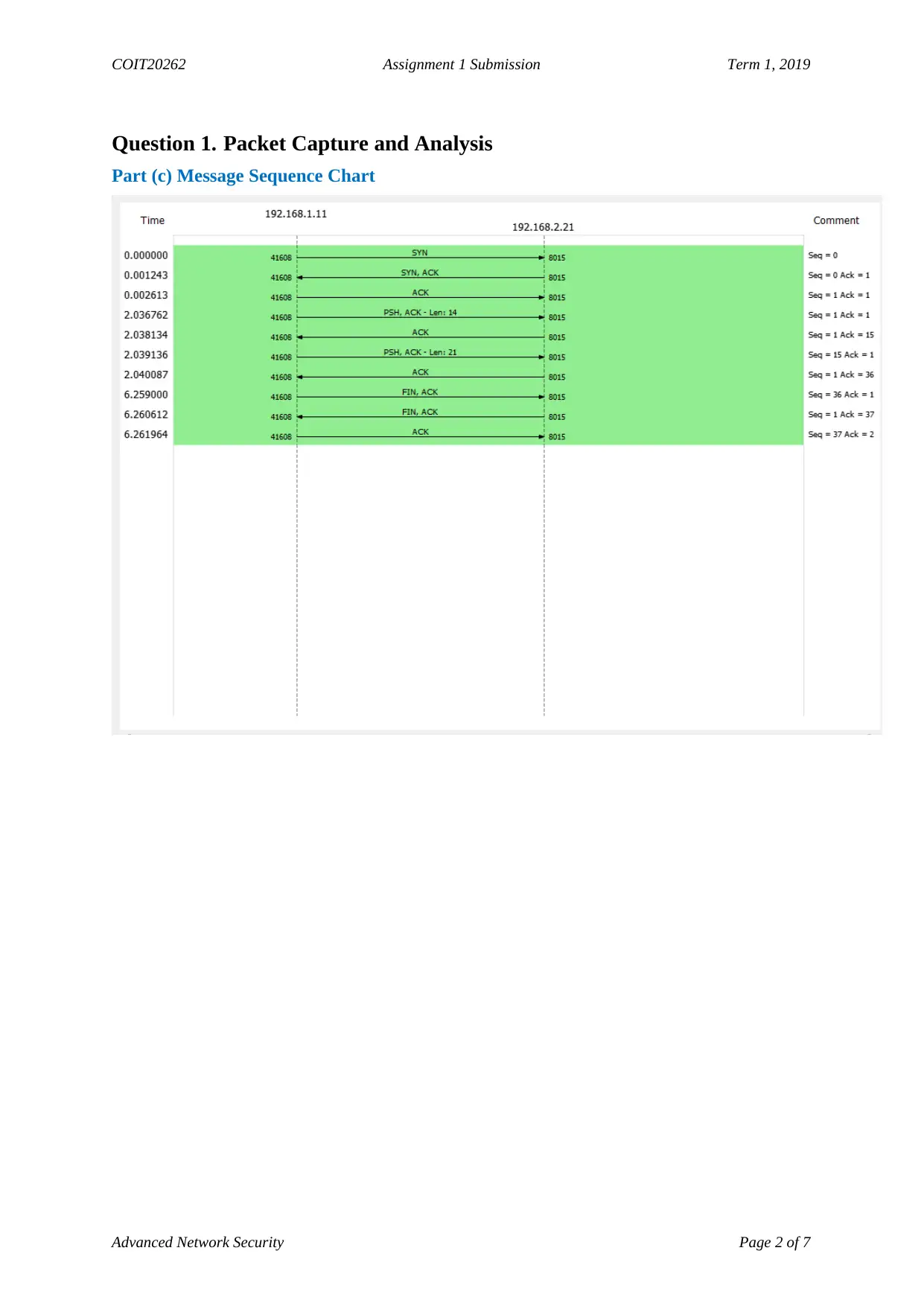
Question 1. Packet Capture and Analysis
Part (c) Message Sequence Chart
Advanced Network Security Page 2 of 7
Question 1. Packet Capture and Analysis
Part (c) Message Sequence Chart
Advanced Network Security Page 2 of 7
COIT20262 Assignment 1 Submission Term 1, 2019
Part (d) Information from Packets
Information Answer
Time between <ENTER> on TCP 2.036 – 2.039
Packet numbers for question above 4 and 6
IP address and port of UDP client 192.168.2.21 Port 9015
MAC of UDP server 08:00:27:33:07:53
Hex value of timestamp 080a0000ee5d00000000
Hex value of checksum 0x0000f9ac
Part (e)
The risk of access of the message transferred between node 2 and node 1 by an external agent
can be eliminated by encapsulating the data packets with the RSA encryption algorithm and
asymmetric key encryption techniques. For reducing the risk of public key distribution digital
signature can also be used for management of the identity of the user.
Part (f)
The modification attack took place on the server cannot be determined by the server since the
identity of an authorized user is forged for gaining access of the server and the hacker
behaves as the authorised user to make the modification in the database. Cookie stealing
followed by SQL injection attack can be used such that the server is certain that message was
not modified.
Part (g)
On performing replay attack on the TCP exchange the attacker maliciously or frauds valid
data transmission. This is done by intercepting the data packets and retransmitting it and
acting as a masquerade attack. The replay attack is the lower version of man in the middle
attack and the server would be unaware of this type of attack if session ID is not tagged with
the components transmitted by the valid user.
Advanced Network Security Page 3 of 7
Part (d) Information from Packets
Information Answer
Time between <ENTER> on TCP 2.036 – 2.039
Packet numbers for question above 4 and 6
IP address and port of UDP client 192.168.2.21 Port 9015
MAC of UDP server 08:00:27:33:07:53
Hex value of timestamp 080a0000ee5d00000000
Hex value of checksum 0x0000f9ac
Part (e)
The risk of access of the message transferred between node 2 and node 1 by an external agent
can be eliminated by encapsulating the data packets with the RSA encryption algorithm and
asymmetric key encryption techniques. For reducing the risk of public key distribution digital
signature can also be used for management of the identity of the user.
Part (f)
The modification attack took place on the server cannot be determined by the server since the
identity of an authorized user is forged for gaining access of the server and the hacker
behaves as the authorised user to make the modification in the database. Cookie stealing
followed by SQL injection attack can be used such that the server is certain that message was
not modified.
Part (g)
On performing replay attack on the TCP exchange the attacker maliciously or frauds valid
data transmission. This is done by intercepting the data packets and retransmitting it and
acting as a masquerade attack. The replay attack is the lower version of man in the middle
attack and the server would be unaware of this type of attack if session ID is not tagged with
the components transmitted by the valid user.
Advanced Network Security Page 3 of 7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

COIT20262 Assignment 1 Submission Term 1, 2019
Question 2. Cryptography
Part (c)
Authenticated emails are suitable for exchange some information between two parties. It can
save both receiver and the sender from external threats. However, sender and the receiver is
not protected against each other through authentication process. Protection is important
between those parties as one simply deny about the messages which is interchanged between
them. So, email is not the optimal way for key distribution and regarding the post of key in
the moodle forum this is also not secured as hacker might be able to hack any of the students
account and can get access to the key. “Key Conformation” attack can be performed by the
attacker in this case as there is a probability that the hacker can intercept the message. Other
significant attacks which can be performed by the attacker in this case are the “Known
Message Attack” and the “Key Only” attack.
Part (d)
The simple authentication process is not ideal when sender and the receiver does not trust
each other. Digital signatures can be leveraged in this case for verifying that the key is
distributed properly. Some properties of a perfect digital signature are:
1. Digital signature must be saved into the secondary type of storage for any type of
future requirement.
2. Digital signature must have some exclusive information for stopping forgery and the
denial incidents.
3. Digital signature need to follow a bit pattern and it decided upon signed message.
Part (e)
Digital signature’s security scheme is providing high level of confidentiality for the
exchanged messages as the whole message is sent in encrypted condition. Thus the public
key is distributed securely in form of message. This process of encryption can stop the attack
such as man in the middle. The main problem with the digital signature is that private keys
generated from the encryption does not have any type of protection by itself.
Advanced Network Security Page 4 of 7
Question 2. Cryptography
Part (c)
Authenticated emails are suitable for exchange some information between two parties. It can
save both receiver and the sender from external threats. However, sender and the receiver is
not protected against each other through authentication process. Protection is important
between those parties as one simply deny about the messages which is interchanged between
them. So, email is not the optimal way for key distribution and regarding the post of key in
the moodle forum this is also not secured as hacker might be able to hack any of the students
account and can get access to the key. “Key Conformation” attack can be performed by the
attacker in this case as there is a probability that the hacker can intercept the message. Other
significant attacks which can be performed by the attacker in this case are the “Known
Message Attack” and the “Key Only” attack.
Part (d)
The simple authentication process is not ideal when sender and the receiver does not trust
each other. Digital signatures can be leveraged in this case for verifying that the key is
distributed properly. Some properties of a perfect digital signature are:
1. Digital signature must be saved into the secondary type of storage for any type of
future requirement.
2. Digital signature must have some exclusive information for stopping forgery and the
denial incidents.
3. Digital signature need to follow a bit pattern and it decided upon signed message.
Part (e)
Digital signature’s security scheme is providing high level of confidentiality for the
exchanged messages as the whole message is sent in encrypted condition. Thus the public
key is distributed securely in form of message. This process of encryption can stop the attack
such as man in the middle. The main problem with the digital signature is that private keys
generated from the encryption does not have any type of protection by itself.
Advanced Network Security Page 4 of 7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
COIT20262 Assignment 1 Submission Term 1, 2019
Question 3. Denial of Service Attack Research
Overview of DDoS Attacks
The DoS attack or the Denial of Service attack related with attack on network which can
create problem in the execution of normal functions for a system. This attack causes lost of
services and network in a system on which it is performed. The targeted computer is
overloaded with huge amount of data packets and stop functioning, this is how the DoS
performs.
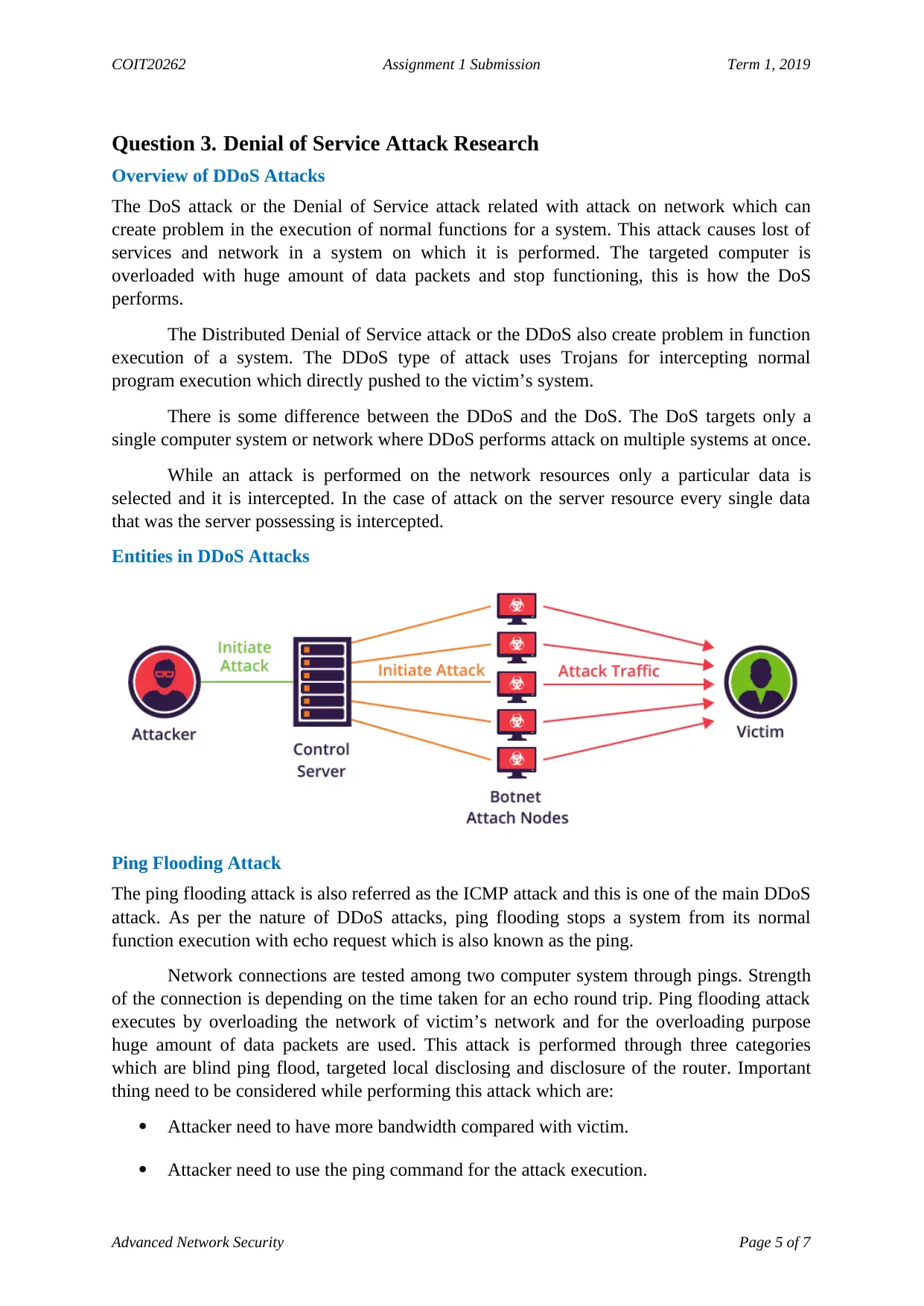
The Distributed Denial of Service attack or the DDoS also create problem in function
execution of a system. The DDoS type of attack uses Trojans for intercepting normal
program execution which directly pushed to the victim’s system.
There is some difference between the DDoS and the DoS. The DoS targets only a
single computer system or network where DDoS performs attack on multiple systems at once.
While an attack is performed on the network resources only a particular data is
selected and it is intercepted. In the case of attack on the server resource every single data
that was the server possessing is intercepted.
Entities in DDoS Attacks
Ping Flooding Attack
The ping flooding attack is also referred as the ICMP attack and this is one of the main DDoS
attack. As per the nature of DDoS attacks, ping flooding stops a system from its normal
function execution with echo request which is also known as the ping.
Network connections are tested among two computer system through pings. Strength
of the connection is depending on the time taken for an echo round trip. Ping flooding attack
executes by overloading the network of victim’s network and for the overloading purpose
huge amount of data packets are used. This attack is performed through three categories
which are blind ping flood, targeted local disclosing and disclosure of the router. Important
thing need to be considered while performing this attack which are:
Attacker need to have more bandwidth compared with victim.
Attacker need to use the ping command for the attack execution.
Advanced Network Security Page 5 of 7
Question 3. Denial of Service Attack Research
Overview of DDoS Attacks
The DoS attack or the Denial of Service attack related with attack on network which can
create problem in the execution of normal functions for a system. This attack causes lost of
services and network in a system on which it is performed. The targeted computer is
overloaded with huge amount of data packets and stop functioning, this is how the DoS
performs.
The Distributed Denial of Service attack or the DDoS also create problem in function
execution of a system. The DDoS type of attack uses Trojans for intercepting normal
program execution which directly pushed to the victim’s system.
There is some difference between the DDoS and the DoS. The DoS targets only a
single computer system or network where DDoS performs attack on multiple systems at once.
While an attack is performed on the network resources only a particular data is
selected and it is intercepted. In the case of attack on the server resource every single data
that was the server possessing is intercepted.
Entities in DDoS Attacks
Ping Flooding Attack
The ping flooding attack is also referred as the ICMP attack and this is one of the main DDoS
attack. As per the nature of DDoS attacks, ping flooding stops a system from its normal
function execution with echo request which is also known as the ping.
Network connections are tested among two computer system through pings. Strength
of the connection is depending on the time taken for an echo round trip. Ping flooding attack
executes by overloading the network of victim’s network and for the overloading purpose
huge amount of data packets are used. This attack is performed through three categories
which are blind ping flood, targeted local disclosing and disclosure of the router. Important
thing need to be considered while performing this attack which are:
Attacker need to have more bandwidth compared with victim.
Attacker need to use the ping command for the attack execution.
Advanced Network Security Page 5 of 7

COIT20262 Assignment 1 Submission Term 1, 2019
Attacker must know victim’s IP address.
Ping flooding attack targets server of some organizations from which it intercepts a large
amount of data.
Mitigating Ping Flooding Attack
Perimeter of the firewall and the settings regarding it can be reconfigured for stopping the
ping flooding attack. In this case reconfiguration is done so that the firewall can block every
pings of which source is outside of the secured network. Thus this will effectively block the
unnecessary pings and the system will be safeguarded. Though there is a problem also in this
firewall planning. While the attacker will distribute the pings within the secured network, this
pings will also be considered as the trusted pings and the system will face ping flooding
attack, due to which the system might stop functioning its normal processes.
Advanced Network Security Page 6 of 7
Attacker must know victim’s IP address.
Ping flooding attack targets server of some organizations from which it intercepts a large
amount of data.
Mitigating Ping Flooding Attack
Perimeter of the firewall and the settings regarding it can be reconfigured for stopping the
ping flooding attack. In this case reconfiguration is done so that the firewall can block every
pings of which source is outside of the secured network. Thus this will effectively block the
unnecessary pings and the system will be safeguarded. Though there is a problem also in this
firewall planning. While the attacker will distribute the pings within the secured network, this
pings will also be considered as the trusted pings and the system will face ping flooding
attack, due to which the system might stop functioning its normal processes.
Advanced Network Security Page 6 of 7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

COIT20262 Assignment 1 Submission Term 1, 2019
Bibliography:
Adi, E., Baig, Z. and Hingston, P., 2017. Stealthy denial of service (DoS) attack modelling
and detection for HTTP/2 services. Journal of Network and Computer Applications, 91, pp.1-
13.
Ambrosin, M., Conti, M., De Gaspari, F. and Devarajan, N., 2016, November. Amplified
distributed denial of service attack in software defined networking. In 2016 8th IFIP
International Conference on New Technologies, Mobility and Security (NTMS) (pp. 1-4).
IEEE.
Baldi, M., Barenghi, A., Chiaraluce, F., Pelosi, G., Rosenthal, J., Santini, P. and Schipani, D.,
2018. Design and Implementation of a Digital Signature Scheme Based on Low-density
Generator Matrix Codes. arXiv preprint arXiv:1807.06127.
Bhandari, A., Sangal, A.L. and Kumar, K., 2015. Destination address entropy based detection
and traceback approach against distributed denial of service attacks. International Journal of
Computer Network and Information Security, 7(8), p.9.
Cao, J., Yu, B., Dong, F., Zhu, X. and Xu, S., 2015. Entropy‐based denial‐of‐service attack
detection in cloud data center. Concurrency and Computation: Practice and
Experience, 27(18), pp.5623-5639.
Sadeghpour, M., 2017. Security Analysis of Digital Signature Scheme with Message
Recovery using Self-Certified Public Keys. International Journal of Computer (IJC), 24(1),
pp.43-55.
Advanced Network Security Page 7 of 7
Bibliography:
Adi, E., Baig, Z. and Hingston, P., 2017. Stealthy denial of service (DoS) attack modelling
and detection for HTTP/2 services. Journal of Network and Computer Applications, 91, pp.1-
13.
Ambrosin, M., Conti, M., De Gaspari, F. and Devarajan, N., 2016, November. Amplified
distributed denial of service attack in software defined networking. In 2016 8th IFIP
International Conference on New Technologies, Mobility and Security (NTMS) (pp. 1-4).
IEEE.
Baldi, M., Barenghi, A., Chiaraluce, F., Pelosi, G., Rosenthal, J., Santini, P. and Schipani, D.,
2018. Design and Implementation of a Digital Signature Scheme Based on Low-density
Generator Matrix Codes. arXiv preprint arXiv:1807.06127.
Bhandari, A., Sangal, A.L. and Kumar, K., 2015. Destination address entropy based detection
and traceback approach against distributed denial of service attacks. International Journal of
Computer Network and Information Security, 7(8), p.9.
Cao, J., Yu, B., Dong, F., Zhu, X. and Xu, S., 2015. Entropy‐based denial‐of‐service attack
detection in cloud data center. Concurrency and Computation: Practice and
Experience, 27(18), pp.5623-5639.
Sadeghpour, M., 2017. Security Analysis of Digital Signature Scheme with Message
Recovery using Self-Certified Public Keys. International Journal of Computer (IJC), 24(1),
pp.43-55.
Advanced Network Security Page 7 of 7
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





