COIT2062 Assignment: Analyzing Web Application Attacks and Mitigation
VerifiedAdded on 2020/03/04
|3
|999
|253
Homework Assignment
AI Summary
This assignment analyzes a packet capture from a web application, focusing on a Cross-Site Request Forgery (CSRF) attack. The student is tasked with identifying the actions of a user, determining the domain names and IP addresses of the web servers, and pinpointing the attack's purpose, attacker, and successful indicators within the capture. The solution details how the attack was performed, emphasizing the attacker's actions and relevant packets. Furthermore, the assignment explores mitigation strategies, specifically suggesting the use of unpredictable tokens to prevent similar attacks. The analysis highlights the importance of web application security and provides practical methods for protecting against common vulnerabilities.
Question 2. Web Application Attacks [12 marks]
Objective: Understand how real web application attacks work, and methods for mitigating them.
The file a1-q2-capture.pcap on Moodle contains packets captured in an exchange between
several computers. One of those computers was the Unit Coordinator’s (Steve) and has IP address
192.168.1.11. One action the Unit Coordinator was performing during the capture was viewing the
grades of students on the university web site http://www.myuni.edu/grades/. No other users were
accessing any of the websites during capture.
Answer the following questions based on the packet capture.
(a) Complete the following table that shows the actions the Unit Coordinator performed on his web
browser. Note that the actions are only those performed by the human user, such as:
Clicked on “XXX” link
Entered “YYY” in ZZZ field and pressed Submit
Give the time rounded to the nearest second. As a hint, the first two rows and the last row are
already completed for you, and you do not need to insert/delete rows from the table. [4 marks]
Time
(sec)
Action Destination URL
0 Visit My Uni Grade Website www.myuni.edu/grades
53 Clicked on “Login” link www.myuni.edu/grades/login.php
81 Clicked on “Submit” after entering
credentials (username and password)
www.myuni.edu/grades/index.php
98 Clicked on “View Grades” link www.myuni.edu/grades/query.php
138 Entered the user id of a student and
clicked “submit” to view his/her grades
www.myuni.edu/grades/view.php
175 Clicked on “View Grades” link www.myuni.edu/grades/query.php
195 Entered the user id of a student and
clicked “submit” to view his/her grades
www.myuni.edu/grades/view.php
236 Visited Freestuff website www.freestuff.com/freestuff
271 Clicked on “View Grades” link www.myuni.edu/grades/query.php
287 Entered the user id of a student and
clicked “submit” to view his/her grades
www.myuni.edu/grades/view.php
363 Clicked on “Logout” link www.myuni.edu/grades/login.php
(b) For all websites visited by the Unit Coordinator, give the domain name and corresponding IP
address of the web server. [1 mark]
Answer: The domain name and corresponding IP addresses are shown below –
Domain Name IP address
www.myuni.edu 192.168.2.21
www.freestuff.com 192.168.2.22
Objective: Understand how real web application attacks work, and methods for mitigating them.
The file a1-q2-capture.pcap on Moodle contains packets captured in an exchange between
several computers. One of those computers was the Unit Coordinator’s (Steve) and has IP address
192.168.1.11. One action the Unit Coordinator was performing during the capture was viewing the
grades of students on the university web site http://www.myuni.edu/grades/. No other users were
accessing any of the websites during capture.
Answer the following questions based on the packet capture.
(a) Complete the following table that shows the actions the Unit Coordinator performed on his web
browser. Note that the actions are only those performed by the human user, such as:
Clicked on “XXX” link
Entered “YYY” in ZZZ field and pressed Submit
Give the time rounded to the nearest second. As a hint, the first two rows and the last row are
already completed for you, and you do not need to insert/delete rows from the table. [4 marks]
Time
(sec)
Action Destination URL
0 Visit My Uni Grade Website www.myuni.edu/grades
53 Clicked on “Login” link www.myuni.edu/grades/login.php
81 Clicked on “Submit” after entering
credentials (username and password)
www.myuni.edu/grades/index.php
98 Clicked on “View Grades” link www.myuni.edu/grades/query.php
138 Entered the user id of a student and
clicked “submit” to view his/her grades
www.myuni.edu/grades/view.php
175 Clicked on “View Grades” link www.myuni.edu/grades/query.php
195 Entered the user id of a student and
clicked “submit” to view his/her grades
www.myuni.edu/grades/view.php
236 Visited Freestuff website www.freestuff.com/freestuff
271 Clicked on “View Grades” link www.myuni.edu/grades/query.php
287 Entered the user id of a student and
clicked “submit” to view his/her grades
www.myuni.edu/grades/view.php
363 Clicked on “Logout” link www.myuni.edu/grades/login.php
(b) For all websites visited by the Unit Coordinator, give the domain name and corresponding IP
address of the web server. [1 mark]
Answer: The domain name and corresponding IP addresses are shown below –
Domain Name IP address
www.myuni.edu 192.168.2.21
www.freestuff.com 192.168.2.22
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
(c) How did you find the domain name of each website? That is, what specific part of the capture
(e.g. which packet?, which field?) did you find the domain name? [1 mark]
Answer: We identified the domain name of the websites visited by the Unit Coordinator by observing
the HTTP GET/POST requests sent by him. The ‘Host’ field in the HTTP requests contains domain name of
the visited websites. The table shown below shows the details of the packets which identified domain
name of the websites visited by the Unit Coordinator.
Packet # Protocol Field Domain Name Identified
4 HTTP Host www.myuni.edu
91 HTTP Host www.freestuff.com
(d) An attack was performed during the capture. What was the purpose of the attack, who was the
likely attacker, and what part of the capture indicates the attack was successful (refer to specific
packets)? [2 marks]
Answer: The purpose of the attack was to update the grades of course ‘coit2062’ without the
knowledge of the Unit Coordinator. The likely attacker was a student with ID: s0000000. The
packets – 98 & 100 confirm that that the attack was successful. The attack is confirmed by the fact
that when Unit Coordinator visited ‘www.freestuff.com’ at time=236 sec (236 seconds after the Unit
Coordinator initiated the activity), there was also a ‘update grade’ request sent observed in packet
number 98. The ‘OK’ received in packet number-100 shows that the attack was successful.
(e) Explain how the attack was performed, including what the attacker did (either in advance of the
capture or during the capture) and which packets in the capture indicate the attack taking place. [3
marks]
Answer: The attacker managed to let the Unit Coordinator click on the URL
‘www.freestuff.com/freestuff’. The URL had the link ‘www.myuni.edu//grades/updategrade.php?
id=s0000000&course=coit20262&newgrade=HD’ embedded in it’s source code possibly as a fake image
of zero size. When the Unit coordinator visited the freestuff website, the browser encountered the URL
‘www.myuni.edu /grades/updategrade.php?id=s0000000&course=coit20262&newgrade=HD’ and
visited the link. The visited page was not displayed because most probably it was indeed embedded as
the source of a fake image. Now, this all became possible only because the Unit Coordinator (userid:
’steve’) was logged in and the cookies of ‘steve’ were sent to the domain: ‘www.myuni.edu’. The
participating packets are depicted in the image shown below-
(e.g. which packet?, which field?) did you find the domain name? [1 mark]
Answer: We identified the domain name of the websites visited by the Unit Coordinator by observing
the HTTP GET/POST requests sent by him. The ‘Host’ field in the HTTP requests contains domain name of
the visited websites. The table shown below shows the details of the packets which identified domain
name of the websites visited by the Unit Coordinator.
Packet # Protocol Field Domain Name Identified
4 HTTP Host www.myuni.edu
91 HTTP Host www.freestuff.com
(d) An attack was performed during the capture. What was the purpose of the attack, who was the
likely attacker, and what part of the capture indicates the attack was successful (refer to specific
packets)? [2 marks]
Answer: The purpose of the attack was to update the grades of course ‘coit2062’ without the
knowledge of the Unit Coordinator. The likely attacker was a student with ID: s0000000. The
packets – 98 & 100 confirm that that the attack was successful. The attack is confirmed by the fact
that when Unit Coordinator visited ‘www.freestuff.com’ at time=236 sec (236 seconds after the Unit
Coordinator initiated the activity), there was also a ‘update grade’ request sent observed in packet
number 98. The ‘OK’ received in packet number-100 shows that the attack was successful.
(e) Explain how the attack was performed, including what the attacker did (either in advance of the
capture or during the capture) and which packets in the capture indicate the attack taking place. [3
marks]
Answer: The attacker managed to let the Unit Coordinator click on the URL
‘www.freestuff.com/freestuff’. The URL had the link ‘www.myuni.edu//grades/updategrade.php?
id=s0000000&course=coit20262&newgrade=HD’ embedded in it’s source code possibly as a fake image
of zero size. When the Unit coordinator visited the freestuff website, the browser encountered the URL
‘www.myuni.edu /grades/updategrade.php?id=s0000000&course=coit20262&newgrade=HD’ and
visited the link. The visited page was not displayed because most probably it was indeed embedded as
the source of a fake image. Now, this all became possible only because the Unit Coordinator (userid:
’steve’) was logged in and the cookies of ‘steve’ were sent to the domain: ‘www.myuni.edu’. The
participating packets are depicted in the image shown below-
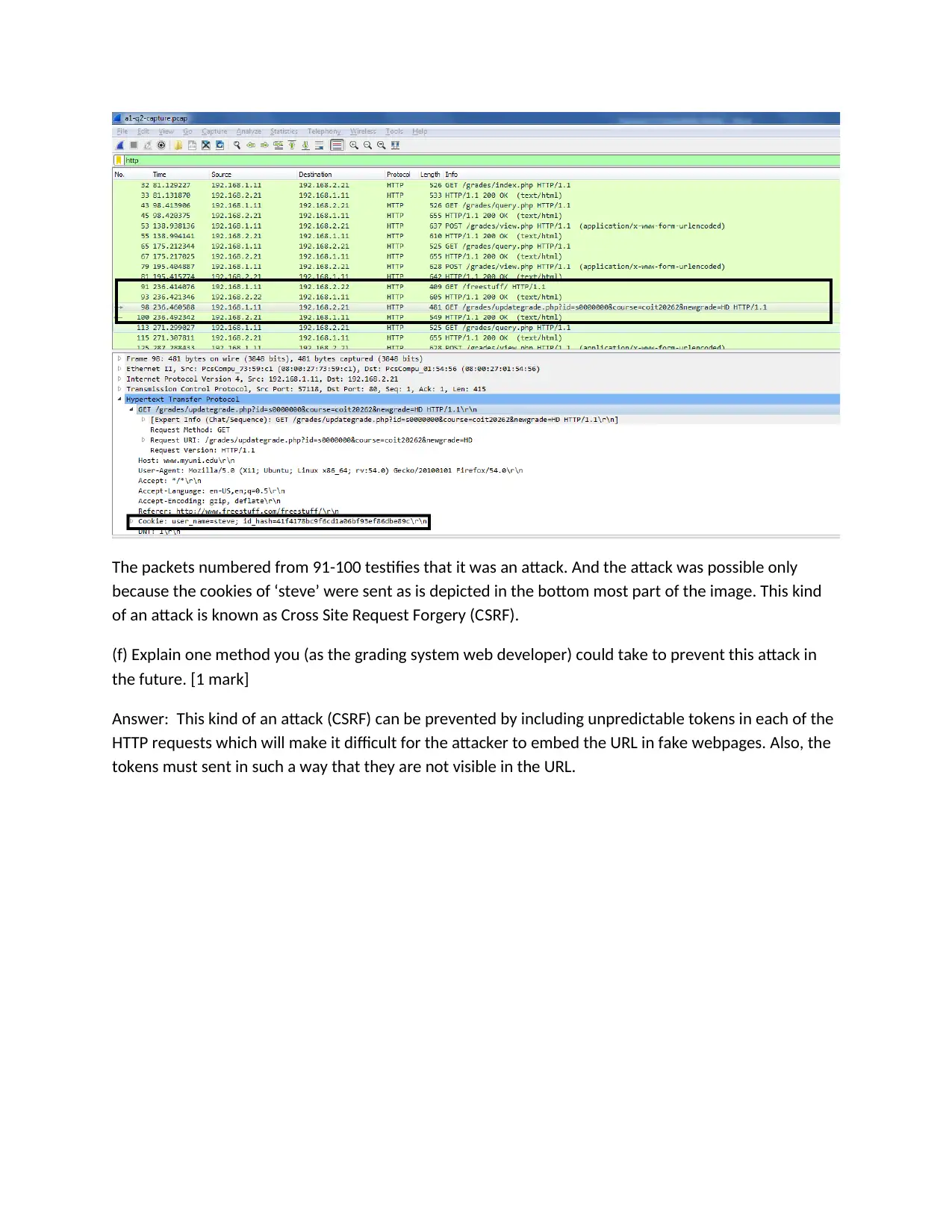
The packets numbered from 91-100 testifies that it was an attack. And the attack was possible only
because the cookies of ‘steve’ were sent as is depicted in the bottom most part of the image. This kind
of an attack is known as Cross Site Request Forgery (CSRF).
(f) Explain one method you (as the grading system web developer) could take to prevent this attack in
the future. [1 mark]
Answer: This kind of an attack (CSRF) can be prevented by including unpredictable tokens in each of the
HTTP requests which will make it difficult for the attacker to embed the URL in fake webpages. Also, the
tokens must sent in such a way that they are not visible in the URL.
because the cookies of ‘steve’ were sent as is depicted in the bottom most part of the image. This kind
of an attack is known as Cross Site Request Forgery (CSRF).
(f) Explain one method you (as the grading system web developer) could take to prevent this attack in
the future. [1 mark]
Answer: This kind of an attack (CSRF) can be prevented by including unpredictable tokens in each of the
HTTP requests which will make it difficult for the attacker to embed the URL in fake webpages. Also, the
tokens must sent in such a way that they are not visible in the URL.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 3
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



