Detailed Analysis of Collin ATM Business Information System Report
VerifiedAdded on 2021/04/21
|14
|2357
|187
Report
AI Summary
This report provides a comprehensive analysis of the Collin ATM business information system. It begins with an introduction to business information systems, followed by a discussion of the Collin ATM system. The report details the system vision documents, outlining problem descriptions, system capabilities, and business benefits. It then identifies the resources required, including card readers, keypads, and display screens. A stakeholders map is presented, categorizing primary, secondary, and tertiary stakeholders. The report also examines various risks associated with ATM systems, such as card and currency fraud, physical attacks, and logical attacks. The discussion includes methods like skimming and anti-skimming modules. The report concludes with a summary of the key findings, emphasizing the importance of understanding business information systems and the challenges associated with ATM security. References to relevant academic sources are also included.

Running head: OBJECT AND DATA MODELLING
OBJECT AND DATA MODELLING
Name of the Student
Name of the University
Authors Note:
OBJECT AND DATA MODELLING
Name of the Student
Name of the University
Authors Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1OBJECT AND DATA MODELLING
Table of Contents
Introduction..........................................................................................................................2
Discussion............................................................................................................................2
Business Information System..........................................................................................2
System vision documents................................................................................................2
Resources required...........................................................................................................2
Stakeholders Map............................................................................................................2
Risk..................................................................................................................................2
Conclusion...........................................................................................................................2
References............................................................................................................................2
Table of Contents
Introduction..........................................................................................................................2
Discussion............................................................................................................................2
Business Information System..........................................................................................2
System vision documents................................................................................................2
Resources required...........................................................................................................2
Stakeholders Map............................................................................................................2
Risk..................................................................................................................................2
Conclusion...........................................................................................................................2
References............................................................................................................................2

2OBJECT AND DATA MODELLING
Introduction
Business information System can be easily stated as a group of interrelated components
which can work as a group of interrelated components which can work together for carrying out
inputs, storage and control actions (Kharchenko & Chynchenko, 2013). This is mainly done for
conversion of data into products of information which can be used for forecasting of support,
planning, control, coordination, decision making and various kinds of operation activities in an
organization. Components can be easily classified as five kind of basic resources namely people,
hardware, software, data and communication (Kamal et al., 2015). There are many kind of
information system like operation management system, management information system (MIS).
In the coming pages of the report an idea has been provided regarding business
information system for Collin ATM. After that an idea has provided regarding system vision
documents, various resources, stakeholders map and risk has been properly explained.
Transaction processing system will be the key business information system for this Collin ATM
system.
Discussion
System vision documents
Problem description
Various kinds of customer can easily access the bank from any sector of the world and
can easily conduct various kinds of banking services like deposit withdrawals. ATM generally
helps in minimizing the cost of various kinds of operation as it generally reduces human
interventions and also increases profit in various kinds of banks. Financial consequence which
can easily arise for an incorrect kind of machine also provides certain incentive to bank also
Introduction
Business information System can be easily stated as a group of interrelated components
which can work as a group of interrelated components which can work together for carrying out
inputs, storage and control actions (Kharchenko & Chynchenko, 2013). This is mainly done for
conversion of data into products of information which can be used for forecasting of support,
planning, control, coordination, decision making and various kinds of operation activities in an
organization. Components can be easily classified as five kind of basic resources namely people,
hardware, software, data and communication (Kamal et al., 2015). There are many kind of
information system like operation management system, management information system (MIS).
In the coming pages of the report an idea has been provided regarding business
information system for Collin ATM. After that an idea has provided regarding system vision
documents, various resources, stakeholders map and risk has been properly explained.
Transaction processing system will be the key business information system for this Collin ATM
system.
Discussion
System vision documents
Problem description
Various kinds of customer can easily access the bank from any sector of the world and
can easily conduct various kinds of banking services like deposit withdrawals. ATM generally
helps in minimizing the cost of various kinds of operation as it generally reduces human
interventions and also increases profit in various kinds of banks. Financial consequence which
can easily arise for an incorrect kind of machine also provides certain incentive to bank also
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3OBJECT AND DATA MODELLING
reduces malfunctions. ATMs also print each kind of transaction in a paper roll and also provide
information which is stored generally. For the security of customers, the lobbies generally have
extensive kind of security camera, a courtesy telephone for having courtesy with various kinds of
coverage of related to records along with disputes which can easily arise. For various kinds of
security lobbies an idea has bene provided regarding extensive kind of security camera coverage.
Opening of customer side of ATMs are generally covered by mechanical shutters which is
covered by mechanical shutters with various kinds of mechanism which is not in use. Alarm
sensors are generally placed inside various kinds of ATM and in service areas for various kinds
of ATM and also come in alert of operating doors which cannot be easily opened by any kind of
unauthorized persons (Montefusco et al., 2016). The main components of system vision
documents of Collin’s ATM are key switch, card reader, screen, key pad, cash dispenser, deposit
slot, printer and lastly network infrastructure in which cash can be easily deposited.
System Capabilities
The various system capabilities of ATM system are:
It provides 24 hours of service
It provides a large number of convenience to bank customers.
It generally reduces the workload of banks staff.
It generally provides service any kind of error.
It is considered to be beneficial for various kinds of travelers as people does not
need to carry large amount of cash (De Gramatica et al., 2015).
It may provide the customers with new kind of notes of currency and not the
soiled notes.
reduces malfunctions. ATMs also print each kind of transaction in a paper roll and also provide
information which is stored generally. For the security of customers, the lobbies generally have
extensive kind of security camera, a courtesy telephone for having courtesy with various kinds of
coverage of related to records along with disputes which can easily arise. For various kinds of
security lobbies an idea has bene provided regarding extensive kind of security camera coverage.
Opening of customer side of ATMs are generally covered by mechanical shutters which is
covered by mechanical shutters with various kinds of mechanism which is not in use. Alarm
sensors are generally placed inside various kinds of ATM and in service areas for various kinds
of ATM and also come in alert of operating doors which cannot be easily opened by any kind of
unauthorized persons (Montefusco et al., 2016). The main components of system vision
documents of Collin’s ATM are key switch, card reader, screen, key pad, cash dispenser, deposit
slot, printer and lastly network infrastructure in which cash can be easily deposited.
System Capabilities
The various system capabilities of ATM system are:
It provides 24 hours of service
It provides a large number of convenience to bank customers.
It generally reduces the workload of banks staff.
It generally provides service any kind of error.
It is considered to be beneficial for various kinds of travelers as people does not
need to carry large amount of cash (De Gramatica et al., 2015).
It may provide the customers with new kind of notes of currency and not the
soiled notes.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4OBJECT AND DATA MODELLING
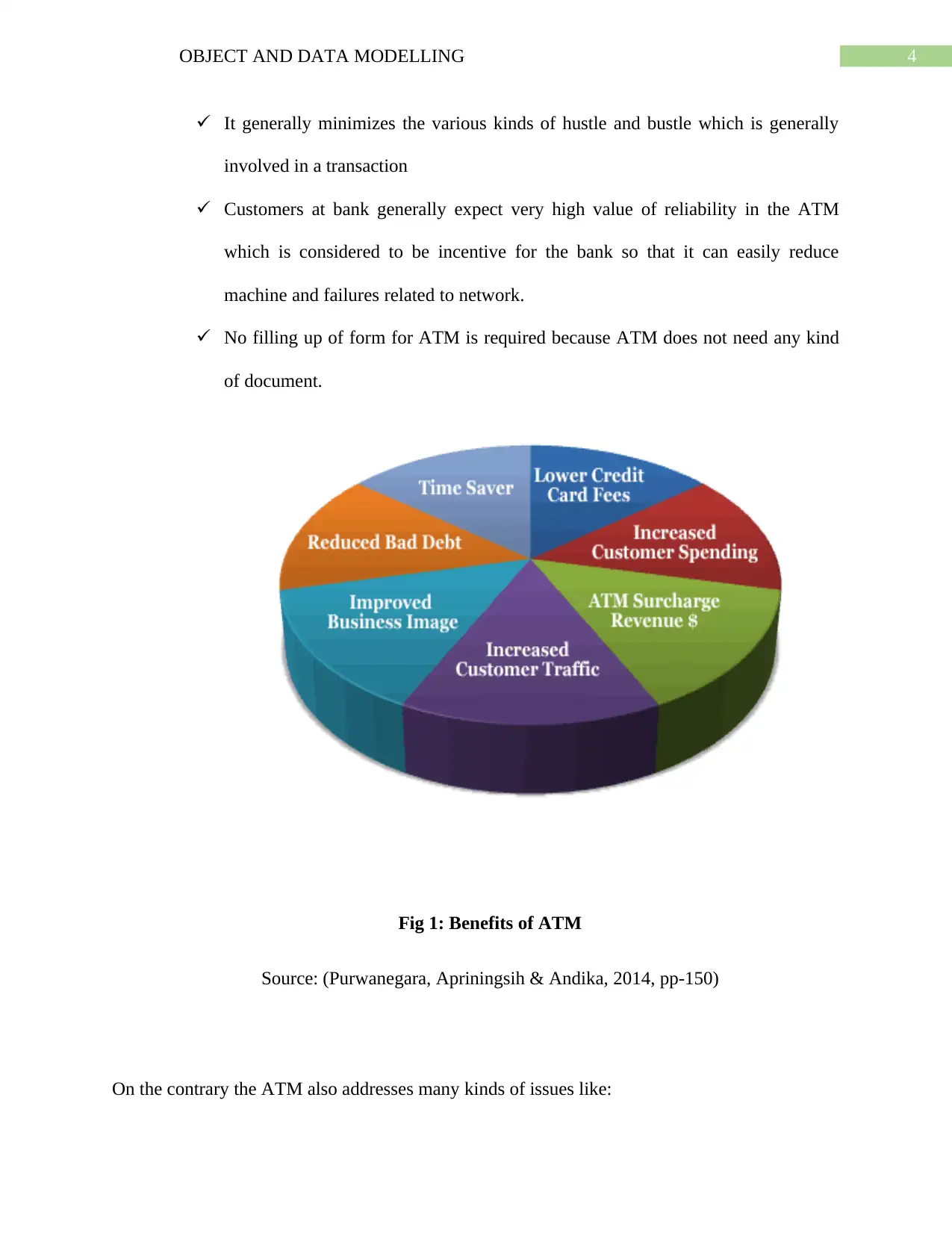
It generally minimizes the various kinds of hustle and bustle which is generally
involved in a transaction
Customers at bank generally expect very high value of reliability in the ATM
which is considered to be incentive for the bank so that it can easily reduce
machine and failures related to network.
No filling up of form for ATM is required because ATM does not need any kind
of document.
Fig 1: Benefits of ATM
Source: (Purwanegara, Apriningsih & Andika, 2014, pp-150)
On the contrary the ATM also addresses many kinds of issues like:
It generally minimizes the various kinds of hustle and bustle which is generally
involved in a transaction
Customers at bank generally expect very high value of reliability in the ATM
which is considered to be incentive for the bank so that it can easily reduce
machine and failures related to network.
No filling up of form for ATM is required because ATM does not need any kind
of document.
Fig 1: Benefits of ATM
Source: (Purwanegara, Apriningsih & Andika, 2014, pp-150)
On the contrary the ATM also addresses many kinds of issues like:

5OBJECT AND DATA MODELLING
Cloning of ATM card may result in many kinds of fraud activities.
There also some cases of fake kinds of ATM.
A hacker can easily track the PIN of an individual.
If ATM network goes out of service, then an individual will left without any kind of
ability for making transactions until and unless the beginning of bank’s next time of
opening hours (Patriarca, 2016).
ATM machines does not provide guarantee of the fact there will be no amount cash left in
it. It may run low due to funds and customers have to wait till the management takes care
of it.
Consumers round the globe generally faces issues regarding increase number of scams.
Fig 2: Drawbacks of ATM
(Source: Patriarca, 2016, pp-130)
Cloning of ATM card may result in many kinds of fraud activities.
There also some cases of fake kinds of ATM.
A hacker can easily track the PIN of an individual.
If ATM network goes out of service, then an individual will left without any kind of
ability for making transactions until and unless the beginning of bank’s next time of
opening hours (Patriarca, 2016).
ATM machines does not provide guarantee of the fact there will be no amount cash left in
it. It may run low due to funds and customers have to wait till the management takes care
of it.
Consumers round the globe generally faces issues regarding increase number of scams.
Fig 2: Drawbacks of ATM
(Source: Patriarca, 2016, pp-130)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6OBJECT AND DATA MODELLING
Business benefits
It can be easily assumed that deployment of ATM machine can easily bring a large
number of benefits like:
Increases foot traffic
Increases sales
Reduces Card fees
Surcharges Revenue.
Retention of Customers.
Resources required
There are certain number of resources are required for different kinds of activities like
card reader for reading of various kinds of cards for customers, a keypad with pin number can be
easily inserted as per the needs, a screen for displaying of required information (De Gramatica et
al., 2015).
Card reader: Card Reader is nothing but an input kind of device which generally reads
data from a particular kind of card (Onuoha & Fatokun, 2014). Card is generally swiped or
pressed on the card which can easily provide information related to particular kind of account.
The host processor makes use of data for getting information regarding the card holders.
Keypad: Card is properly recognized by making use of machine which provides details
like personal identification number with the card which is provided to each and every kind of
person (Purwanegara, Apriningsih & Andika, 2014). There are separate kind of laws which can
be used for protection of PIN code when providing it to the processor. PIN number is generally
Business benefits
It can be easily assumed that deployment of ATM machine can easily bring a large
number of benefits like:
Increases foot traffic
Increases sales
Reduces Card fees
Surcharges Revenue.
Retention of Customers.
Resources required
There are certain number of resources are required for different kinds of activities like
card reader for reading of various kinds of cards for customers, a keypad with pin number can be
easily inserted as per the needs, a screen for displaying of required information (De Gramatica et
al., 2015).
Card reader: Card Reader is nothing but an input kind of device which generally reads
data from a particular kind of card (Onuoha & Fatokun, 2014). Card is generally swiped or
pressed on the card which can easily provide information related to particular kind of account.
The host processor makes use of data for getting information regarding the card holders.
Keypad: Card is properly recognized by making use of machine which provides details
like personal identification number with the card which is provided to each and every kind of
person (Purwanegara, Apriningsih & Andika, 2014). There are separate kind of laws which can
be used for protection of PIN code when providing it to the processor. PIN number is generally
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7OBJECT AND DATA MODELLING
provided in encrypted form. The key board generally contains 48 keys which can be used for
interface processors.
Speaker: Speakers generally provides information regarding audio key when a particular
kind of key is pressed.
Display Screen: Display screen provides details related to transaction information. Each
and every step of withdrawal is generally provided by the screen which is provided (Mandari &
Koloseni, 2016). A CRT screen or a LCD screen is generally used by most of the ATMs round
the globe.
Receipt printers: The receipt printers generally provide information related to recording
of withdrawal, date and time and the value of withdrawn and also provides information related to
account receipt.
provided in encrypted form. The key board generally contains 48 keys which can be used for
interface processors.
Speaker: Speakers generally provides information regarding audio key when a particular
kind of key is pressed.
Display Screen: Display screen provides details related to transaction information. Each
and every step of withdrawal is generally provided by the screen which is provided (Mandari &
Koloseni, 2016). A CRT screen or a LCD screen is generally used by most of the ATMs round
the globe.
Receipt printers: The receipt printers generally provide information related to recording
of withdrawal, date and time and the value of withdrawn and also provides information related to
account receipt.
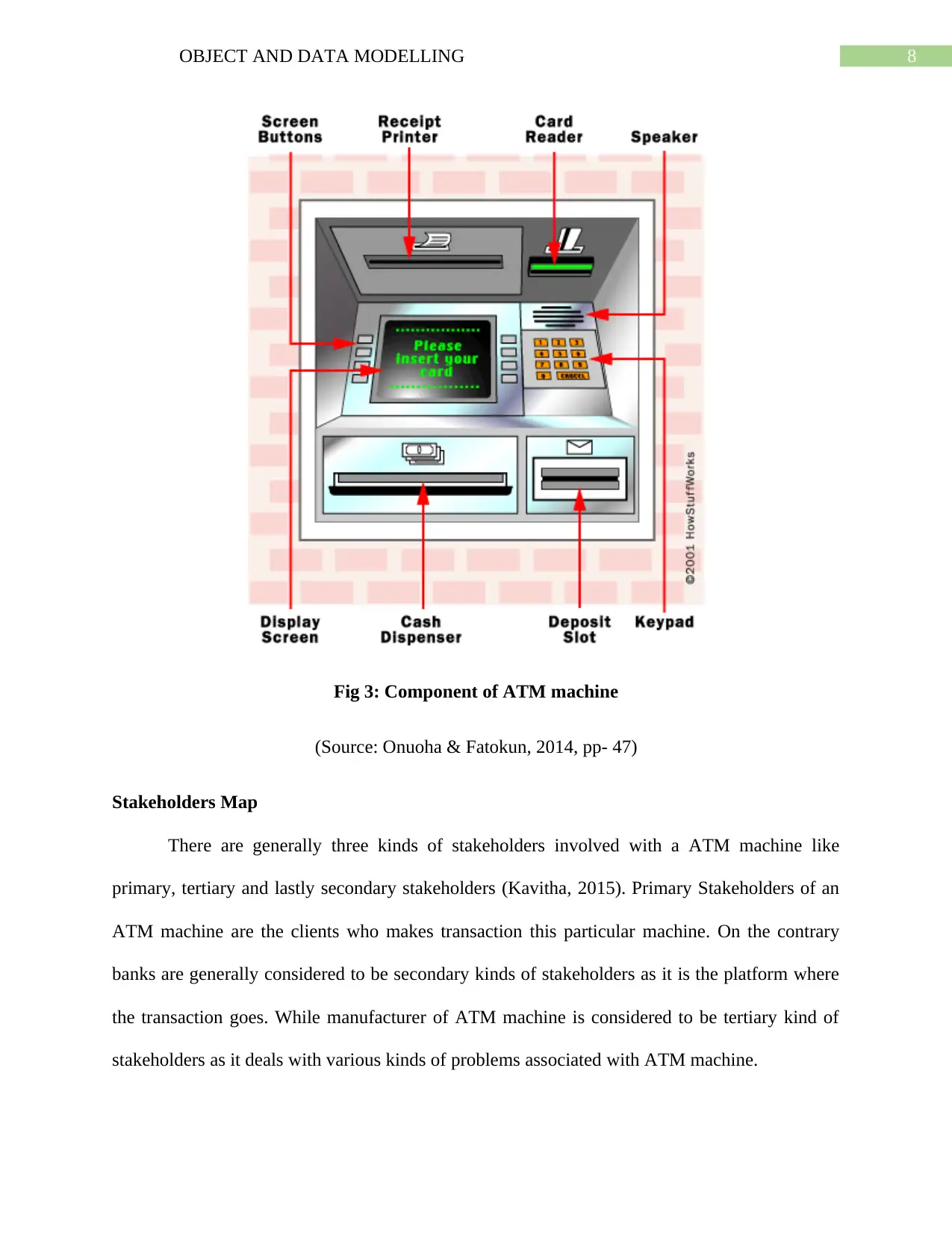
8OBJECT AND DATA MODELLING
Fig 3: Component of ATM machine
(Source: Onuoha & Fatokun, 2014, pp- 47)
Stakeholders Map
There are generally three kinds of stakeholders involved with a ATM machine like
primary, tertiary and lastly secondary stakeholders (Kavitha, 2015). Primary Stakeholders of an
ATM machine are the clients who makes transaction this particular machine. On the contrary
banks are generally considered to be secondary kinds of stakeholders as it is the platform where
the transaction goes. While manufacturer of ATM machine is considered to be tertiary kind of
stakeholders as it deals with various kinds of problems associated with ATM machine.
Fig 3: Component of ATM machine
(Source: Onuoha & Fatokun, 2014, pp- 47)
Stakeholders Map
There are generally three kinds of stakeholders involved with a ATM machine like
primary, tertiary and lastly secondary stakeholders (Kavitha, 2015). Primary Stakeholders of an
ATM machine are the clients who makes transaction this particular machine. On the contrary
banks are generally considered to be secondary kinds of stakeholders as it is the platform where
the transaction goes. While manufacturer of ATM machine is considered to be tertiary kind of
stakeholders as it deals with various kinds of problems associated with ATM machine.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9OBJECT AND DATA MODELLING
There are large number of benefits and drawbacks of stakeholders. There are large
number of benefits for making use of ATM like it makes transaction at a much faster rate and
also it reduces various kinds of technical errors (Purwanegara, Apriningsih & Andika, 2014). For
secondary kind of stakeholders that is bank can easily some amount of money in the form of
interest from various customers. If the transaction works in a better way, then various customers
can easily recommend it the other banks associated and more number of ATMs can be easily
build.
There are large number of benefits and drawbacks of stakeholders. There are large
number of benefits for making use of ATM like it makes transaction at a much faster rate and
also it reduces various kinds of technical errors (Purwanegara, Apriningsih & Andika, 2014). For
secondary kind of stakeholders that is bank can easily some amount of money in the form of
interest from various customers. If the transaction works in a better way, then various customers
can easily recommend it the other banks associated and more number of ATMs can be easily
build.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10OBJECT AND DATA MODELLING
Operational Executive
Fig 4: Stakeholders of a ATM Machine
(Source: Created by Author)
Risk
There are three different kinds of attacks namely card and fraud of currency, physical
kinds of attacks and logical kinds of attacks. ATM security can be easily divided into three core
areas namely protection of currency, physical security and various kinds of logical security.
Card and Currency Fraud: Card and Currency fraud is generally inclusive of attack
which steals details of card and cash as well as indirect kind of attacks like stealing of sensitive
kind of data which can be easily used for fraudulent kinds of withdrawal (Kavitha, 2015). The
ultimately kinds of targets in a single kind of ATM can be considered to be manipulation for
skimming, tapping of currency and fishing of card. Skimming is nothing but a kind of approach
Accounting System
Internal Auditors
Senior Manager
Board of Directors of Collin ATM Bank
Various Organization attached with Colin
bank
Customers
Investors
Regulators
Operational Executive
Fig 4: Stakeholders of a ATM Machine
(Source: Created by Author)
Risk
There are three different kinds of attacks namely card and fraud of currency, physical
kinds of attacks and logical kinds of attacks. ATM security can be easily divided into three core
areas namely protection of currency, physical security and various kinds of logical security.
Card and Currency Fraud: Card and Currency fraud is generally inclusive of attack
which steals details of card and cash as well as indirect kind of attacks like stealing of sensitive
kind of data which can be easily used for fraudulent kinds of withdrawal (Kavitha, 2015). The
ultimately kinds of targets in a single kind of ATM can be considered to be manipulation for
skimming, tapping of currency and fishing of card. Skimming is nothing but a kind of approach
Accounting System
Internal Auditors
Senior Manager
Board of Directors of Collin ATM Bank
Various Organization attached with Colin
bank
Customers
Investors
Regulators

11OBJECT AND DATA MODELLING
which can be used for installing additional kinds of services. There are several kinds of security
methods which deals with various kinds of security threats. Jitters is a well-known kind of
example of vary speed and movement of cards or introduce motion. In other kinds of other
words, it affects the details of magnetic stripes and makes it really difficult for various kinds of
skimmers to read data related to it (Martins, Oliveira & Popovič, 2014). A next module is the
approach of anti-skimming module is a jammer which mainly affects the skimmer which is
attached to ATM dashboard. A jammer makes use of anti-skimming module which mainly
affects which affects the skimmer which is attached
Conclusion
From the above discussion it can be easily concluded that this report is all about Business
information system. Various information system focus on conversion of data into information
kinds of products. In the discussion portion of the report system vision documents of Collin’s
ATM system has been provided. Various kinds of benefits and drawbacks of Colin’s ATM
system has been provided. Various kinds of resources like card reader, keypad, speaker, display
screen and receipt printers has been provided. Various kinds of stakeholders involved with ATM
machine like clients making transaction and banks has been discussed in details. Various kinds
of risk associated with ATM card like fraud currency, logical attacks and physical attacks has
been discussed in details. An idea has been provided regarding skimming, which is used for
manipulation, tapping currency and fishing card. In the system vision section an idea has been
provided regarding system vision documents.
which can be used for installing additional kinds of services. There are several kinds of security
methods which deals with various kinds of security threats. Jitters is a well-known kind of
example of vary speed and movement of cards or introduce motion. In other kinds of other
words, it affects the details of magnetic stripes and makes it really difficult for various kinds of
skimmers to read data related to it (Martins, Oliveira & Popovič, 2014). A next module is the
approach of anti-skimming module is a jammer which mainly affects the skimmer which is
attached to ATM dashboard. A jammer makes use of anti-skimming module which mainly
affects which affects the skimmer which is attached
Conclusion
From the above discussion it can be easily concluded that this report is all about Business
information system. Various information system focus on conversion of data into information
kinds of products. In the discussion portion of the report system vision documents of Collin’s
ATM system has been provided. Various kinds of benefits and drawbacks of Colin’s ATM
system has been provided. Various kinds of resources like card reader, keypad, speaker, display
screen and receipt printers has been provided. Various kinds of stakeholders involved with ATM
machine like clients making transaction and banks has been discussed in details. Various kinds
of risk associated with ATM card like fraud currency, logical attacks and physical attacks has
been discussed in details. An idea has been provided regarding skimming, which is used for
manipulation, tapping currency and fishing card. In the system vision section an idea has been
provided regarding system vision documents.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





