BIT243: In-depth Analysis of Com Bank's Network Security Architecture
VerifiedAdded on 2022/10/11
|13
|2680
|15
Report
AI Summary
This report provides a comprehensive analysis of Com Bank's network security, fulfilling the requirements of a BIT243 assignment. It begins with an executive summary and table of contents, followed by an introduction that highlights the importance of network security for financial institutions. The report delves into the essential components of network security, including network access control, firewall security, intrusion prevention systems, and security information management. It describes Com Bank's network architecture, detailing the use of LAN, WAN, and Internet connections, as well as the client-server model. The report then examines the networking devices used, such as switches, wireless access points, servers, and firewalls, along with their respective security considerations. It also identifies Com Bank's security components, like the Microsoft baseline security analyzer, and offers recommendations for enhancing security, including securing web servers and host servers. The report includes figures illustrating network architecture and concludes with a list of references. The analysis covers vulnerability assessments, security weaknesses, and recommended solutions for various network devices and services.

COURSE TITLE:
COURSE CODE:
NAME OF STUDENT:
DATE:
COURSE CODE:
NAME OF STUDENT:
DATE:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

i
Com Bank Network Security
Executive summary
Over the years, network security has gained much attention with organizations associated with
computers and computer networks. Financial institutions e.g. banks, make use of computer
networks as they strive to provide banking services closer to their customers. Computer networks
offer an infrastructure for banks to deliver customer oriented services to customers e.g.
Electronic Bill Presentation and Payment and in delivery of ancillary services including
electronic payments and Customer Relations Management. To provide this, Com Bank makes
use of three levels of network- LAN, WAN and Internet. However, these networks are a target
for security attacks. Therefore, there is a need to access the Network security issue by focusing
on network architecture and components that make up the network.
Failure in a network as a result of security breach is detrimental to Com Bank’s operation. It
means that confidential customer data is in the breach of misuse. Financial information can be
accessed and this can result in huge losses.
Com Bank Network Security
Executive summary
Over the years, network security has gained much attention with organizations associated with
computers and computer networks. Financial institutions e.g. banks, make use of computer
networks as they strive to provide banking services closer to their customers. Computer networks
offer an infrastructure for banks to deliver customer oriented services to customers e.g.
Electronic Bill Presentation and Payment and in delivery of ancillary services including
electronic payments and Customer Relations Management. To provide this, Com Bank makes
use of three levels of network- LAN, WAN and Internet. However, these networks are a target
for security attacks. Therefore, there is a need to access the Network security issue by focusing
on network architecture and components that make up the network.
Failure in a network as a result of security breach is detrimental to Com Bank’s operation. It
means that confidential customer data is in the breach of misuse. Financial information can be
accessed and this can result in huge losses.

ii
Com Bank Network Security
Table of Contents
Executive summary.......................................................................................................................................i
Figures.........................................................................................................................................................ii
Introduction.................................................................................................................................................1
Network security.........................................................................................................................................1
Essential components of Network Security.................................................................................................2
Network Access Control..........................................................................................................................2
Firewall security......................................................................................................................................2
Intrusion Prevention Systems.................................................................................................................2
Security information and management.................................................................................................2
Network architecture for Com Bank............................................................................................................2
Networking devices.....................................................................................................................................5
a. Switches..........................................................................................................................................6
b. Wireless access points....................................................................................................................6
c. Servers.............................................................................................................................................6
d. Firewalls..........................................................................................................................................7
Com Bank’s Security components...............................................................................................................7
Microsoft baseline security analyzer...........................................................................................................8
Recommendations.......................................................................................................................................8
Secure web server...................................................................................................................................8
Host Server security................................................................................................................................8
References.................................................................................................................................................10
Figures
Figure 1: Client-Server model.........................................................................................................5
Figure 2: LAN and WAN networks.................................................................................................6
Figure 3: LAN network in Com Bank.............................................................................................6
Figure 4: Branches connected over WAN.......................................................................................7
Com Bank Network Security
Table of Contents
Executive summary.......................................................................................................................................i
Figures.........................................................................................................................................................ii
Introduction.................................................................................................................................................1
Network security.........................................................................................................................................1
Essential components of Network Security.................................................................................................2
Network Access Control..........................................................................................................................2
Firewall security......................................................................................................................................2
Intrusion Prevention Systems.................................................................................................................2
Security information and management.................................................................................................2
Network architecture for Com Bank............................................................................................................2
Networking devices.....................................................................................................................................5
a. Switches..........................................................................................................................................6
b. Wireless access points....................................................................................................................6
c. Servers.............................................................................................................................................6
d. Firewalls..........................................................................................................................................7
Com Bank’s Security components...............................................................................................................7
Microsoft baseline security analyzer...........................................................................................................8
Recommendations.......................................................................................................................................8
Secure web server...................................................................................................................................8
Host Server security................................................................................................................................8
References.................................................................................................................................................10
Figures
Figure 1: Client-Server model.........................................................................................................5
Figure 2: LAN and WAN networks.................................................................................................6
Figure 3: LAN network in Com Bank.............................................................................................6
Figure 4: Branches connected over WAN.......................................................................................7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

1
COM Bank Network Security
Introduction
Com Bank, like any other financial institution, provides banking services to customers across
Australia. It is making use of Internet Banking in meeting customer banking services. Internet
Banking has emerged and gained popularity as a result of the following key drivers;
Globalization – greater range of easy-to-find products and services(speed, reliability and
access)
Pace of technology- there is a need to adapt tech in motion. Banking has to cope up with
new technologies that drive increase reliability and convenience.
Customer perception – internet banking makes it easy to perform own inquiries, gaining
updated information, sharing data and access from different locations.
Network security
Network security involves providing protection against attacks on the overall network and on
network components and devices (citation). It involves safeguarding integrity, privacy and
usability of data transmitted on a network. An effective network security is one which provides
secure access to the network; it targets and neutralizes threats and vulnerabilities while
preventing these threats from casing harm to operations and data. Threats vary from one network
to another, or from intensity and mode of execution. The most prevalent network security threats
include;
Distributed denial of service attacks
Spyware
Malware and computer worms
Botnets etc.
The above threats are common targets to unsecured wireless networks which also form entries
from which wired networks are connected. Network security is thus comprised of software,
hardware and network procedures that aim to prevent security breaches from internal and
external threats.
COM Bank Network Security
Introduction
Com Bank, like any other financial institution, provides banking services to customers across
Australia. It is making use of Internet Banking in meeting customer banking services. Internet
Banking has emerged and gained popularity as a result of the following key drivers;
Globalization – greater range of easy-to-find products and services(speed, reliability and
access)
Pace of technology- there is a need to adapt tech in motion. Banking has to cope up with
new technologies that drive increase reliability and convenience.
Customer perception – internet banking makes it easy to perform own inquiries, gaining
updated information, sharing data and access from different locations.
Network security
Network security involves providing protection against attacks on the overall network and on
network components and devices (citation). It involves safeguarding integrity, privacy and
usability of data transmitted on a network. An effective network security is one which provides
secure access to the network; it targets and neutralizes threats and vulnerabilities while
preventing these threats from casing harm to operations and data. Threats vary from one network
to another, or from intensity and mode of execution. The most prevalent network security threats
include;
Distributed denial of service attacks
Spyware
Malware and computer worms
Botnets etc.
The above threats are common targets to unsecured wireless networks which also form entries
from which wired networks are connected. Network security is thus comprised of software,
hardware and network procedures that aim to prevent security breaches from internal and
external threats.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2
COM Bank Network Security
Essential components of Network Security
There are four essential elements of network security.
Network Access Control
Network access control allows network administrators to determine who has access to the
network and who doesn’t. Through NAC, devices and users are allowed on the network and at
what time. Organizations have to make use of Behavioral analytic tools that help network admin
to monitor network anomalies.
Firewall security
Firewalls are security devices that monitor both inbound and outbound network traffics, forming
a barrier between untrusted and trusted connections. They are a network’s fist line of defense.
Firewall security range from application aware firewalls to proxy firewalls among others.
Intrusion Prevention Systems
This is a technology that identifies, examines and prevents unusual traffic on a network from
exploiting network vulnerabilities (citation). These systems are positioned to sit behind network
firewall to provide complementary analysis. In an event of vulnerability exploit, IPS is able to
reset connection and blocks unauthorized traffic from source device/address.
Security information and management
This is a security management that gathers relevant data from different network sources to assist
in identifying anomalies and taking appropriate actions to curb them. It does this by generating
logs in an event that such anomalies happen.
In order to ensure network security, it is important to understand network architecture and the
network devices that collaboratively provide network support facility in Com Bank. Com bank
operates a ‘click and Mortar’ banking operation. It has both online and offline banking services.
Network architecture for Com Bank
Network architecture refers to the logical and physical arrangement of computers and
other network devices to enable sharing of data and information. The architecture can be one of
two types; peer-to-peer or Client-server network architecture. Peer-to-peer architecture is one in
COM Bank Network Security
Essential components of Network Security
There are four essential elements of network security.
Network Access Control
Network access control allows network administrators to determine who has access to the
network and who doesn’t. Through NAC, devices and users are allowed on the network and at
what time. Organizations have to make use of Behavioral analytic tools that help network admin
to monitor network anomalies.
Firewall security
Firewalls are security devices that monitor both inbound and outbound network traffics, forming
a barrier between untrusted and trusted connections. They are a network’s fist line of defense.
Firewall security range from application aware firewalls to proxy firewalls among others.
Intrusion Prevention Systems
This is a technology that identifies, examines and prevents unusual traffic on a network from
exploiting network vulnerabilities (citation). These systems are positioned to sit behind network
firewall to provide complementary analysis. In an event of vulnerability exploit, IPS is able to
reset connection and blocks unauthorized traffic from source device/address.
Security information and management
This is a security management that gathers relevant data from different network sources to assist
in identifying anomalies and taking appropriate actions to curb them. It does this by generating
logs in an event that such anomalies happen.
In order to ensure network security, it is important to understand network architecture and the
network devices that collaboratively provide network support facility in Com Bank. Com bank
operates a ‘click and Mortar’ banking operation. It has both online and offline banking services.
Network architecture for Com Bank
Network architecture refers to the logical and physical arrangement of computers and
other network devices to enable sharing of data and information. The architecture can be one of
two types; peer-to-peer or Client-server network architecture. Peer-to-peer architecture is one in
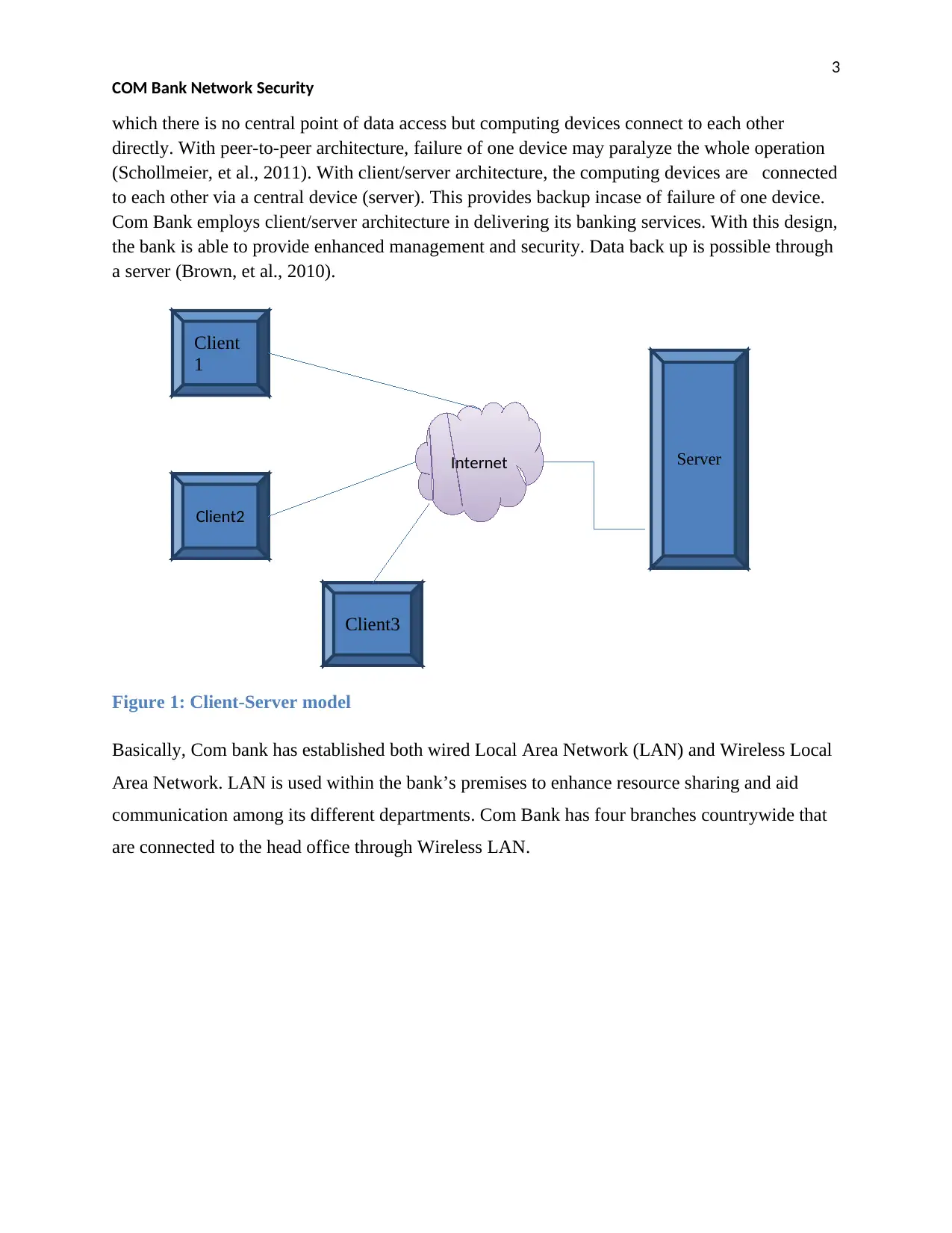
Internet Server
Client2
Client3
Client
1
3
COM Bank Network Security
which there is no central point of data access but computing devices connect to each other
directly. With peer-to-peer architecture, failure of one device may paralyze the whole operation
(Schollmeier, et al., 2011). With client/server architecture, the computing devices are connected
to each other via a central device (server). This provides backup incase of failure of one device.
Com Bank employs client/server architecture in delivering its banking services. With this design,
the bank is able to provide enhanced management and security. Data back up is possible through
a server (Brown, et al., 2010).
Figure 1: Client-Server model
Basically, Com bank has established both wired Local Area Network (LAN) and Wireless Local
Area Network. LAN is used within the bank’s premises to enhance resource sharing and aid
communication among its different departments. Com Bank has four branches countrywide that
are connected to the head office through Wireless LAN.
Client2
Client3
Client
1
3
COM Bank Network Security
which there is no central point of data access but computing devices connect to each other
directly. With peer-to-peer architecture, failure of one device may paralyze the whole operation
(Schollmeier, et al., 2011). With client/server architecture, the computing devices are connected
to each other via a central device (server). This provides backup incase of failure of one device.
Com Bank employs client/server architecture in delivering its banking services. With this design,
the bank is able to provide enhanced management and security. Data back up is possible through
a server (Brown, et al., 2010).
Figure 1: Client-Server model
Basically, Com bank has established both wired Local Area Network (LAN) and Wireless Local
Area Network. LAN is used within the bank’s premises to enhance resource sharing and aid
communication among its different departments. Com Bank has four branches countrywide that
are connected to the head office through Wireless LAN.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
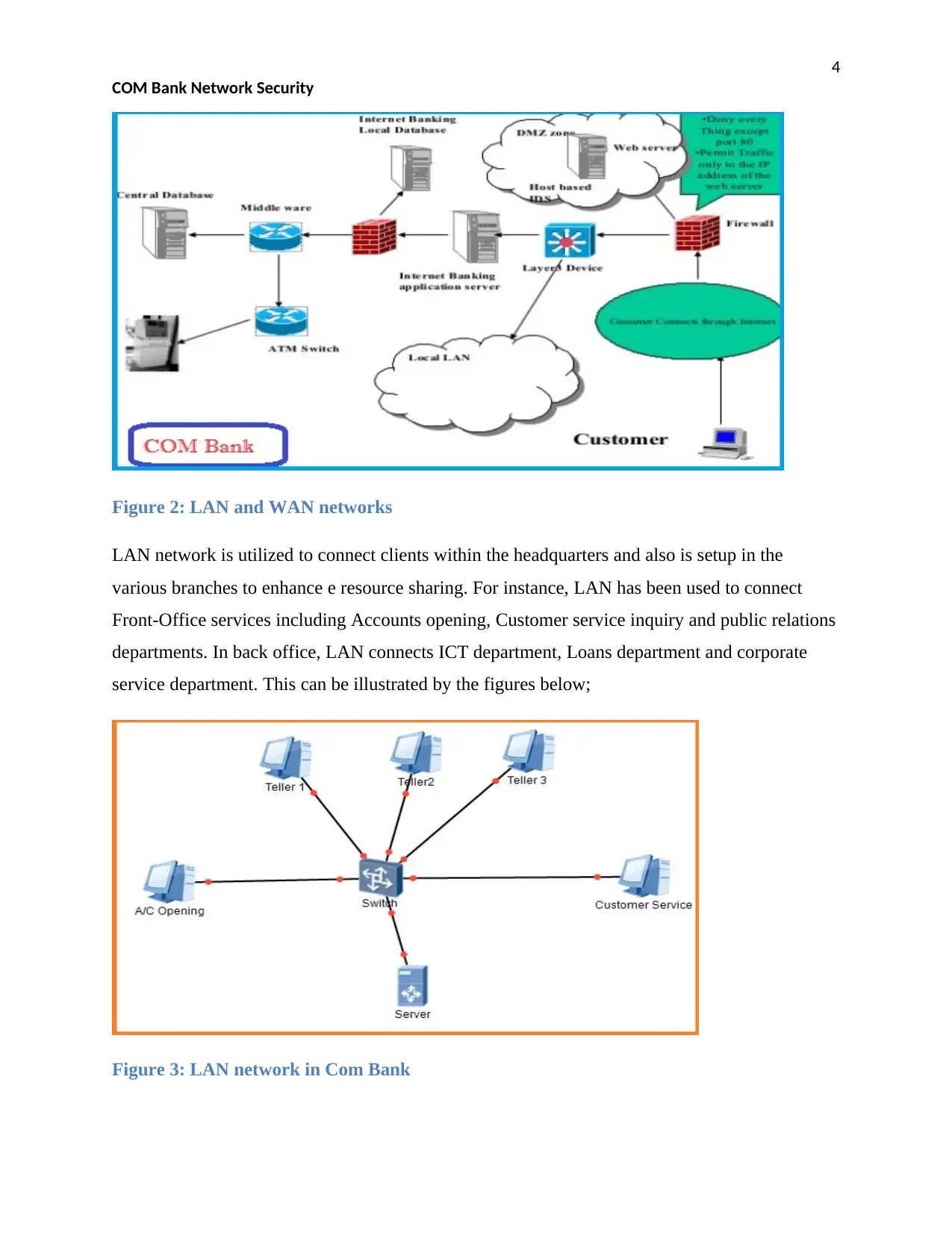
4
COM Bank Network Security
Figure 2: LAN and WAN networks
LAN network is utilized to connect clients within the headquarters and also is setup in the
various branches to enhance e resource sharing. For instance, LAN has been used to connect
Front-Office services including Accounts opening, Customer service inquiry and public relations
departments. In back office, LAN connects ICT department, Loans department and corporate
service department. This can be illustrated by the figures below;
Figure 3: LAN network in Com Bank
COM Bank Network Security
Figure 2: LAN and WAN networks
LAN network is utilized to connect clients within the headquarters and also is setup in the
various branches to enhance e resource sharing. For instance, LAN has been used to connect
Front-Office services including Accounts opening, Customer service inquiry and public relations
departments. In back office, LAN connects ICT department, Loans department and corporate
service department. This can be illustrated by the figures below;
Figure 3: LAN network in Com Bank
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
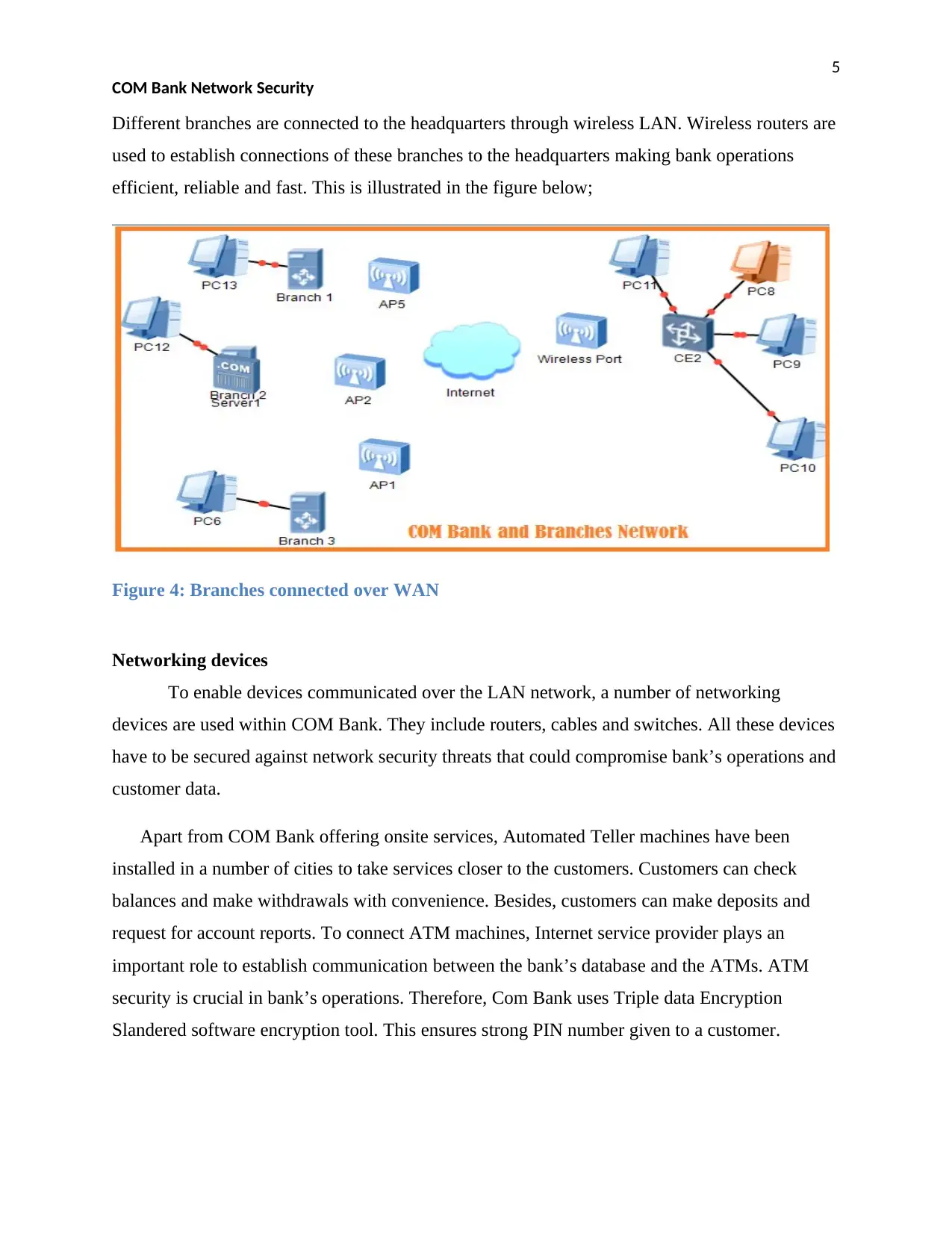
5
COM Bank Network Security
Different branches are connected to the headquarters through wireless LAN. Wireless routers are
used to establish connections of these branches to the headquarters making bank operations
efficient, reliable and fast. This is illustrated in the figure below;
Figure 4: Branches connected over WAN
Networking devices
To enable devices communicated over the LAN network, a number of networking
devices are used within COM Bank. They include routers, cables and switches. All these devices
have to be secured against network security threats that could compromise bank’s operations and
customer data.
Apart from COM Bank offering onsite services, Automated Teller machines have been
installed in a number of cities to take services closer to the customers. Customers can check
balances and make withdrawals with convenience. Besides, customers can make deposits and
request for account reports. To connect ATM machines, Internet service provider plays an
important role to establish communication between the bank’s database and the ATMs. ATM
security is crucial in bank’s operations. Therefore, Com Bank uses Triple data Encryption
Slandered software encryption tool. This ensures strong PIN number given to a customer.
COM Bank Network Security
Different branches are connected to the headquarters through wireless LAN. Wireless routers are
used to establish connections of these branches to the headquarters making bank operations
efficient, reliable and fast. This is illustrated in the figure below;
Figure 4: Branches connected over WAN
Networking devices
To enable devices communicated over the LAN network, a number of networking
devices are used within COM Bank. They include routers, cables and switches. All these devices
have to be secured against network security threats that could compromise bank’s operations and
customer data.
Apart from COM Bank offering onsite services, Automated Teller machines have been
installed in a number of cities to take services closer to the customers. Customers can check
balances and make withdrawals with convenience. Besides, customers can make deposits and
request for account reports. To connect ATM machines, Internet service provider plays an
important role to establish communication between the bank’s database and the ATMs. ATM
security is crucial in bank’s operations. Therefore, Com Bank uses Triple data Encryption
Slandered software encryption tool. This ensures strong PIN number given to a customer.

6
COM Bank Network Security
a. Switches
Switches are hardware devices used to enable communication over Local Area Network.
Ethernet LAN cables are used to connect various client computers to the switch which then
connects them to a central server. RJ-45 Ethernet cables are used to establish the physical
connections.
b. Wireless access points
These devices are used to allow Wi-Fi-enabled devices to connect to wired networks. The access
point is directly connected to Wired LAN (Ethernet) and then uses wireless technologies to
provide wireless connection to other client devices. Since wireless communication is prone to
security threats, these wireless access points are given special considerations in security design.
Many devices can attach to the WAP making it vulnerable to attacks. To ensure security of
communication among devices and the bank’s server, traffic encryption is essential. Wi-Fi
Protected Access (WAP) is a protocol used to provide wireless security in computer networks.
Although WAP is considered a secure protocol over Wired Equivalent Privacy, it is still
vulnerable to security attacks. Use of weak passwords can be easily cracked (Cazier & Medlin,
2006). Brute force attacks can be exploited using Aircrack Suite to crack weak passwords (Yan,
2001). Another security issue related to WAP is a lack of forward secrecy (He & Lee, 2009).
Once a hacker successfully discovers a pre-shared encryption key, he can decrypt all packets that
were encrypted using PSK
c. Servers
Servers are computer devices that provide crucial services in Com Bank. They provide dedicated
services to client computers in delivery of bank’s services. There are a number of servers ranging
from application servers, proxy servers and web servers among others. Since they hold sensitive
data, servers provide a good target for attackers. Therefore, server security is majorly concerned
with protection of data and other resources stored in them. It is concerned with preventing
intrusion and other malicious activities. Server security encompasses areas that include;
Operating system- critical services and components of the operating system have to be
protected against cyber attacks.
COM Bank Network Security
a. Switches
Switches are hardware devices used to enable communication over Local Area Network.
Ethernet LAN cables are used to connect various client computers to the switch which then
connects them to a central server. RJ-45 Ethernet cables are used to establish the physical
connections.
b. Wireless access points
These devices are used to allow Wi-Fi-enabled devices to connect to wired networks. The access
point is directly connected to Wired LAN (Ethernet) and then uses wireless technologies to
provide wireless connection to other client devices. Since wireless communication is prone to
security threats, these wireless access points are given special considerations in security design.
Many devices can attach to the WAP making it vulnerable to attacks. To ensure security of
communication among devices and the bank’s server, traffic encryption is essential. Wi-Fi
Protected Access (WAP) is a protocol used to provide wireless security in computer networks.
Although WAP is considered a secure protocol over Wired Equivalent Privacy, it is still
vulnerable to security attacks. Use of weak passwords can be easily cracked (Cazier & Medlin,
2006). Brute force attacks can be exploited using Aircrack Suite to crack weak passwords (Yan,
2001). Another security issue related to WAP is a lack of forward secrecy (He & Lee, 2009).
Once a hacker successfully discovers a pre-shared encryption key, he can decrypt all packets that
were encrypted using PSK
c. Servers
Servers are computer devices that provide crucial services in Com Bank. They provide dedicated
services to client computers in delivery of bank’s services. There are a number of servers ranging
from application servers, proxy servers and web servers among others. Since they hold sensitive
data, servers provide a good target for attackers. Therefore, server security is majorly concerned
with protection of data and other resources stored in them. It is concerned with preventing
intrusion and other malicious activities. Server security encompasses areas that include;
Operating system- critical services and components of the operating system have to be
protected against cyber attacks.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

7
COM Bank Network Security
Hosted applications – services and contents of applications running on the servers have to
be protected.
Network – servers have to be protected from online exploits and attacks. Vulnerabilities
should be explored and appropriate measures taken to breach them.
d. Firewalls
A firewall is a computer device that controls and monitors inbound and outbound traffic. It
basically provides a barrier between an internal trusted network and external untrusted network
(Oppliger, 1997).
Com Bank has established both network firewalls and host based firewalls. Network firewalls
filter traffic between networks, providing secure communication between the networks. Host
based firewalls ensure that traffic is filtered into and out of the client computers (citation).
Firewalls provide packet filter capabilities. Packets are inspected as they are transmitted from
one computer to another or from one network to another.
Modern firewalls have been extended to include intrusion detection and intrusion prevention
systems, user identity management integration and Web Application Firewall. An application
layer firewall sits on layer 4 of the TCP/IP protocol suite (Canavan, 2001). An application layer
firewall functions by determining whether a given process has to accept connection or not. They
filter traffic based on processes rather than port basis (Ingham & Forrest, 2011).
Com Bank’s Security components
As far as network security is concerned in Con Bank, a number of components have to be
secured. These include; web server, firewalls, web browser, banking application server and
internal network. There is need also to consider management and employees as potential security
risks.
Web browser – web browsers are used by customers to log into their accounts to be able
to view account statements and carry out online transactions at the comfort of their
locations. Web browsers can be security threat as a result of browser crash and system
damage. This leads to a lack of privacy to customers and misuse of their confidential
information.
COM Bank Network Security
Hosted applications – services and contents of applications running on the servers have to
be protected.
Network – servers have to be protected from online exploits and attacks. Vulnerabilities
should be explored and appropriate measures taken to breach them.
d. Firewalls
A firewall is a computer device that controls and monitors inbound and outbound traffic. It
basically provides a barrier between an internal trusted network and external untrusted network
(Oppliger, 1997).
Com Bank has established both network firewalls and host based firewalls. Network firewalls
filter traffic between networks, providing secure communication between the networks. Host
based firewalls ensure that traffic is filtered into and out of the client computers (citation).
Firewalls provide packet filter capabilities. Packets are inspected as they are transmitted from
one computer to another or from one network to another.
Modern firewalls have been extended to include intrusion detection and intrusion prevention
systems, user identity management integration and Web Application Firewall. An application
layer firewall sits on layer 4 of the TCP/IP protocol suite (Canavan, 2001). An application layer
firewall functions by determining whether a given process has to accept connection or not. They
filter traffic based on processes rather than port basis (Ingham & Forrest, 2011).
Com Bank’s Security components
As far as network security is concerned in Con Bank, a number of components have to be
secured. These include; web server, firewalls, web browser, banking application server and
internal network. There is need also to consider management and employees as potential security
risks.
Web browser – web browsers are used by customers to log into their accounts to be able
to view account statements and carry out online transactions at the comfort of their
locations. Web browsers can be security threat as a result of browser crash and system
damage. This leads to a lack of privacy to customers and misuse of their confidential
information.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8
COM Bank Network Security
Firewall – firewalls can fail as a result of system failure, misconfiguration and improper
firewall administration.
Web host-security breaches in a web host include unrestricted access to users and running
unnecessary services on the OS. This is caused by presence of loop holes like missing
patches and upgrades.
Web server-web servers are crucial components that provide banking services over the
internet. Web server security issues result from system failure, presence of unnecessary
services running on the server, misconfiguration of the server, and failure to include a
firewall behind the server to filter traffic.
Internal network – internal network for Com bank has to be protected from unauthorized
access to network resources. Internal network issues result from poor network
maintenance and social engineering security issues.
Microsoft baseline security analyzer
To assess the network security of Com Bank, Microsoft Baseline Security Analyzer was used to
scan for vulnerabilities in wireless network. Network vulnerabilities identified included
misconfigurations of the server, firewalls and switches.
Recommendations
Secure web server
Use WAP 3 that provides more security as compared to WAP and WAP2. Alternatively,
Transport Security Layer protocol can be used together with WAP2. The network admin should
enable logging on any services and review the logs on a regular basis for any suspicious activity.
Host Server security
To ensure server security, Com Bank should employ server hardening. Server hardening is a
way of ensuring server security by;
Use data encryption for communication. Servers that interface with the web have to be
encrypted using cryptographic protocols e.g. Secure Socket Layer protocol or Transport
COM Bank Network Security
Firewall – firewalls can fail as a result of system failure, misconfiguration and improper
firewall administration.
Web host-security breaches in a web host include unrestricted access to users and running
unnecessary services on the OS. This is caused by presence of loop holes like missing
patches and upgrades.
Web server-web servers are crucial components that provide banking services over the
internet. Web server security issues result from system failure, presence of unnecessary
services running on the server, misconfiguration of the server, and failure to include a
firewall behind the server to filter traffic.
Internal network – internal network for Com bank has to be protected from unauthorized
access to network resources. Internal network issues result from poor network
maintenance and social engineering security issues.
Microsoft baseline security analyzer
To assess the network security of Com Bank, Microsoft Baseline Security Analyzer was used to
scan for vulnerabilities in wireless network. Network vulnerabilities identified included
misconfigurations of the server, firewalls and switches.
Recommendations
Secure web server
Use WAP 3 that provides more security as compared to WAP and WAP2. Alternatively,
Transport Security Layer protocol can be used together with WAP2. The network admin should
enable logging on any services and review the logs on a regular basis for any suspicious activity.
Host Server security
To ensure server security, Com Bank should employ server hardening. Server hardening is a
way of ensuring server security by;
Use data encryption for communication. Servers that interface with the web have to be
encrypted using cryptographic protocols e.g. Secure Socket Layer protocol or Transport

9
COM Bank Network Security
Layer Security protocol. More precisely, Com Bank should employ use of TSL since it is
more secure than SSL.
Consider removing unnecessary software and services running on the servers.
Perform regular updates and upgrades of the operating system and application of security
patches.
Performing regular back ups of data
COM Bank Network Security
Layer Security protocol. More precisely, Com Bank should employ use of TSL since it is
more secure than SSL.
Consider removing unnecessary software and services running on the servers.
Perform regular updates and upgrades of the operating system and application of security
patches.
Performing regular back ups of data
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



