COM2067 - Security Risk Analysis: MGB Ltd's Social Security System
VerifiedAdded on 2023/06/12
|20
|2542
|272
Report
AI Summary
This report presents a comprehensive risk analysis of MGB Ltd's social security system, addressing key aspects such as asset valuation, threat identification, vulnerability assessment, and countermeasure implementation. The analysis covers various risks, including unavailability of services, loss of assets, unauthorized disclosure, and unauthorized modification. It details the process of identifying and valuing assets, determining potential threats like software bugs and unauthorized access, and assessing the effectiveness of existing countermeasures. The report also discusses the impact of threat occurrences, categorizing losses as modification, disclosure, denial of service, and destruction, and proposes risk control strategies, including risk prevention, impact reduction, early detection, and recovery. Furthermore, the report touches upon ethical and social issues in IT security, challenges such as cybercrime, and the importance of system ethics, concluding with the need for continuous risk management to protect company assets and maintain information security. The report also mentions the use of GnuPG and the design of a security-related application.
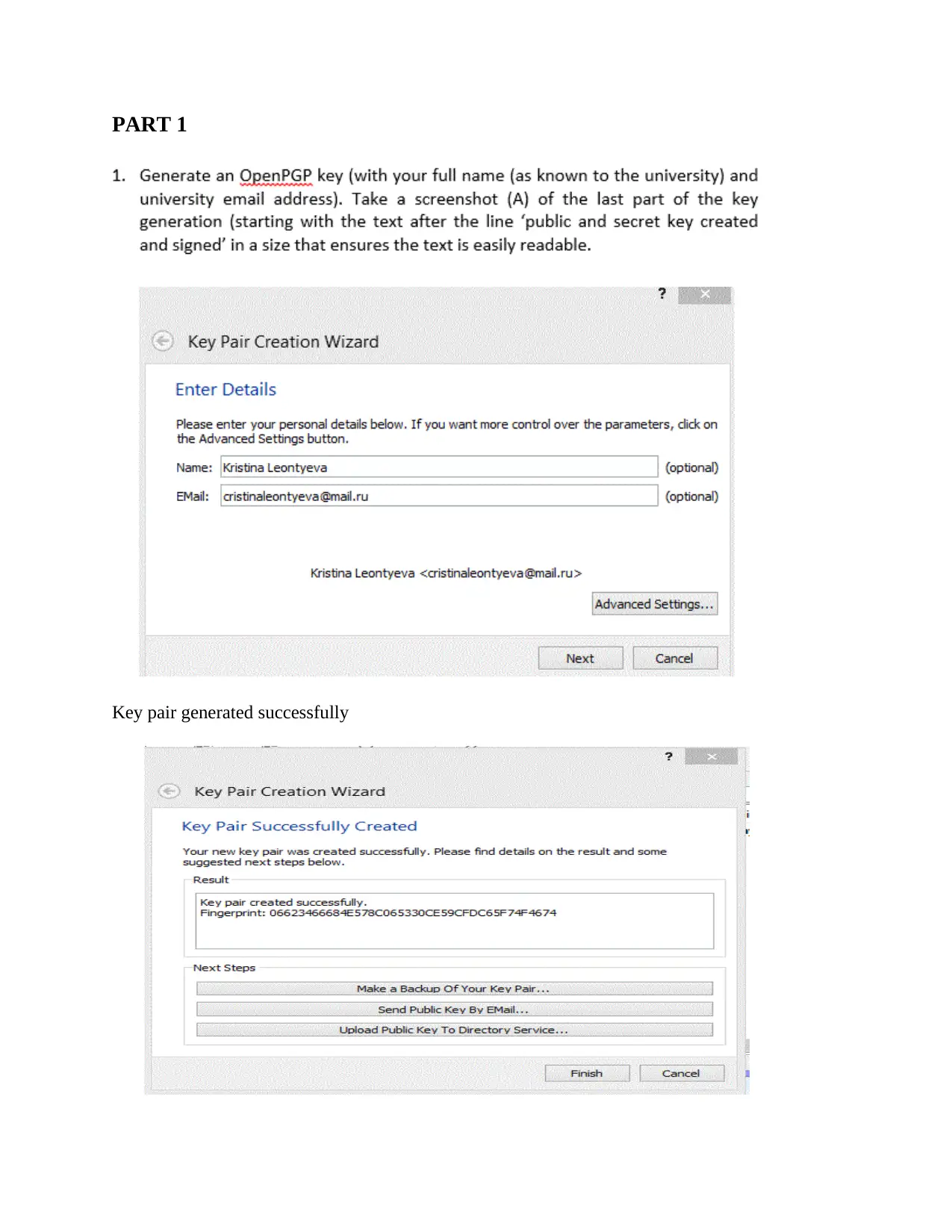
PART 1
Key pair generated successfully
Key pair generated successfully
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
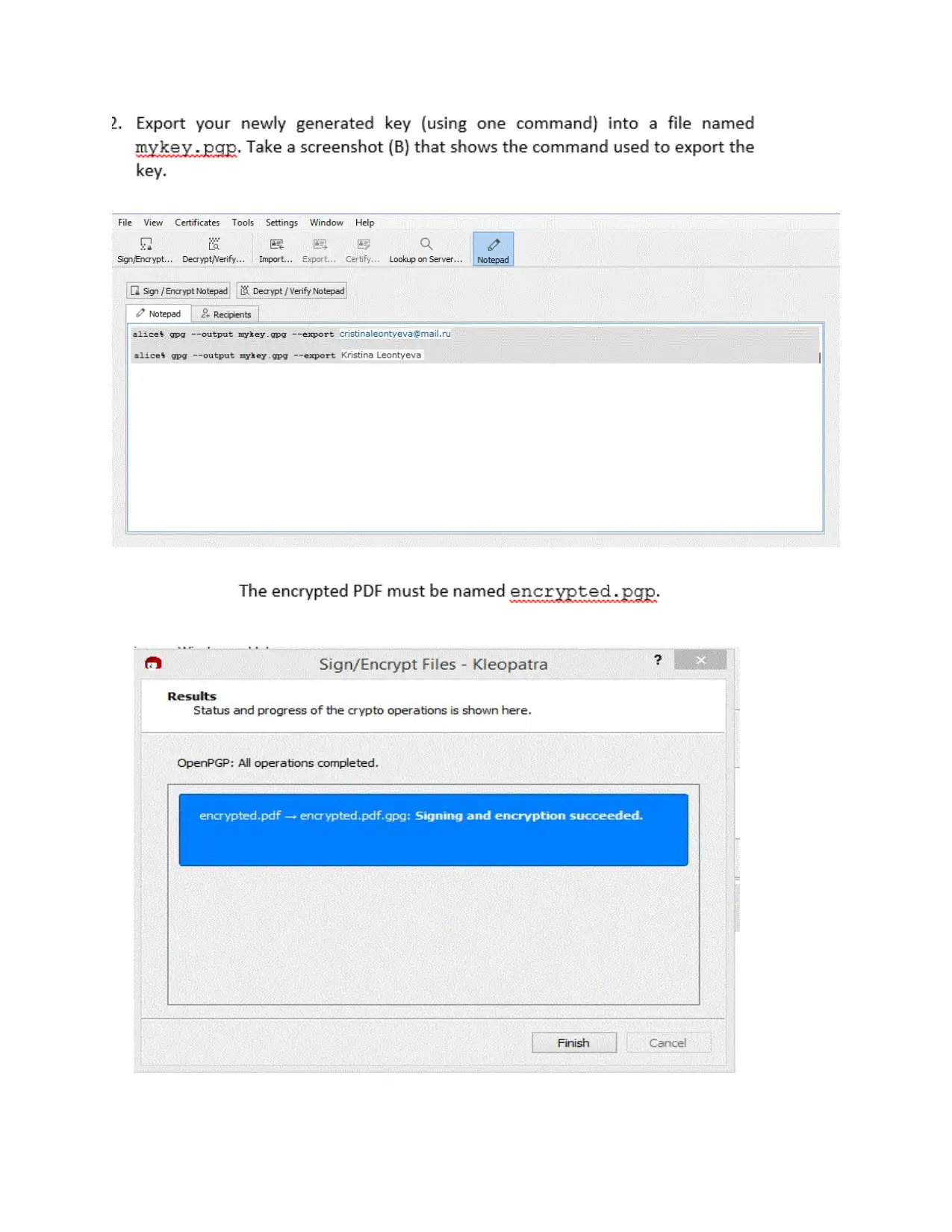
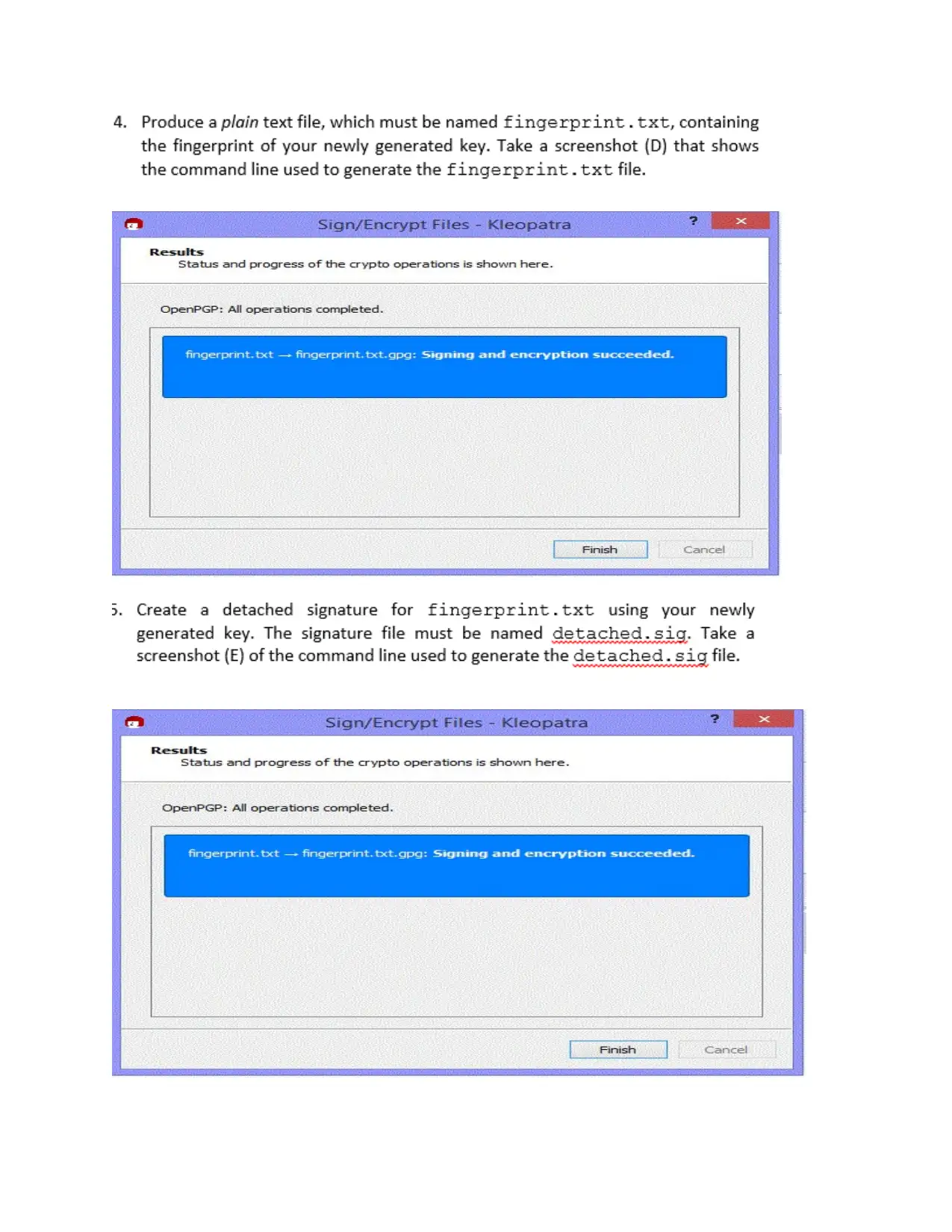
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

PART-2
Introduction:
Security of any organization is determined by security risk analysis which is also known
as risk assessment .100 % security is not assured by security risk analysis. Risk analysis consist of
checking system vulnerabilities and the threats facing it. These are the major part in risk assessment
program. Risk analysis ensure that controls and cost are fully commensurate with the risks to which
industry is exposed. Two important approaches in risk analysis one is quantitative another one is
qualitative. Qualitative risk analysis methods uses these elements threats, vulnerabilities, controls.
Quantitative risk analysis is based on unreliability and inaccuracy of data. Risk assessment on
business objectives is based on following features, key assets must be focused, and prevention and
production against threats .unavailability of services and facilities, loss of assets, unauthorized
disclosure and unauthorized modification are known as risk. Using cyber security risk assessment
techniques we can identify the various information assets that could be affected by vulnerability.
Cyber-attack on hardware, software, laptops, systems, personal data affect those assets. Risk is
reduced only through risk assessment. Organization must develop assessment criteria and assess
the risk and also prioritize the risk then finally avoid those risk.
Introduction:
Security of any organization is determined by security risk analysis which is also known
as risk assessment .100 % security is not assured by security risk analysis. Risk analysis consist of
checking system vulnerabilities and the threats facing it. These are the major part in risk assessment
program. Risk analysis ensure that controls and cost are fully commensurate with the risks to which
industry is exposed. Two important approaches in risk analysis one is quantitative another one is
qualitative. Qualitative risk analysis methods uses these elements threats, vulnerabilities, controls.
Quantitative risk analysis is based on unreliability and inaccuracy of data. Risk assessment on
business objectives is based on following features, key assets must be focused, and prevention and
production against threats .unavailability of services and facilities, loss of assets, unauthorized
disclosure and unauthorized modification are known as risk. Using cyber security risk assessment
techniques we can identify the various information assets that could be affected by vulnerability.
Cyber-attack on hardware, software, laptops, systems, personal data affect those assets. Risk is
reduced only through risk assessment. Organization must develop assessment criteria and assess
the risk and also prioritize the risk then finally avoid those risk.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Risk Analysis
Risk Analysis Terminology
Asset-Anything with value and in need of protection
Threat –An action which causes damage on assets.
Vulnerability - Being attacked or harmed, either physically or emotionally.
Countermeasure - Any action with the ability to reduce attack and vulnerability.
Expected Loss –loss due to attack and vulnerability
Risk analysis
Current level of risk is identified through examination on vulnerabilities, threats, assets. And
using countermeasures reduce the risk. First step of risk analysis is to identify and assign a value
to the assets in need of protection. Here significant factor is value of assets .Hardware, people,
data, software, documentation, supplies are affected by security problem. The first step is we have
to identify which are affected and we have to create a list. Cost, sensitivity and mission critically
these are the values of assets. Second step is to identify the threats. Threats are software bug,
unauthorized access, denial of service and misconfigured systems. Risk analysis process is used to
determine whether the countermeasures are active and effective.
Prepare a risk analysis report
The risk analysis process is used for minimizes the risk and identify the cost to each
countermeasures. Writing a security risk analysis report is biggest challenge. Organization only
focus on summary information and only focus on technical part. These report includes system
connectivity, the use of environment , applicable threats and their frequency, data sensitivity
level, residual risk, detailed annual loss and expectancy calculations.
Risk Analysis Terminology
Asset-Anything with value and in need of protection
Threat –An action which causes damage on assets.
Vulnerability - Being attacked or harmed, either physically or emotionally.
Countermeasure - Any action with the ability to reduce attack and vulnerability.
Expected Loss –loss due to attack and vulnerability
Risk analysis
Current level of risk is identified through examination on vulnerabilities, threats, assets. And
using countermeasures reduce the risk. First step of risk analysis is to identify and assign a value
to the assets in need of protection. Here significant factor is value of assets .Hardware, people,
data, software, documentation, supplies are affected by security problem. The first step is we have
to identify which are affected and we have to create a list. Cost, sensitivity and mission critically
these are the values of assets. Second step is to identify the threats. Threats are software bug,
unauthorized access, denial of service and misconfigured systems. Risk analysis process is used to
determine whether the countermeasures are active and effective.
Prepare a risk analysis report
The risk analysis process is used for minimizes the risk and identify the cost to each
countermeasures. Writing a security risk analysis report is biggest challenge. Organization only
focus on summary information and only focus on technical part. These report includes system
connectivity, the use of environment , applicable threats and their frequency, data sensitivity
level, residual risk, detailed annual loss and expectancy calculations.
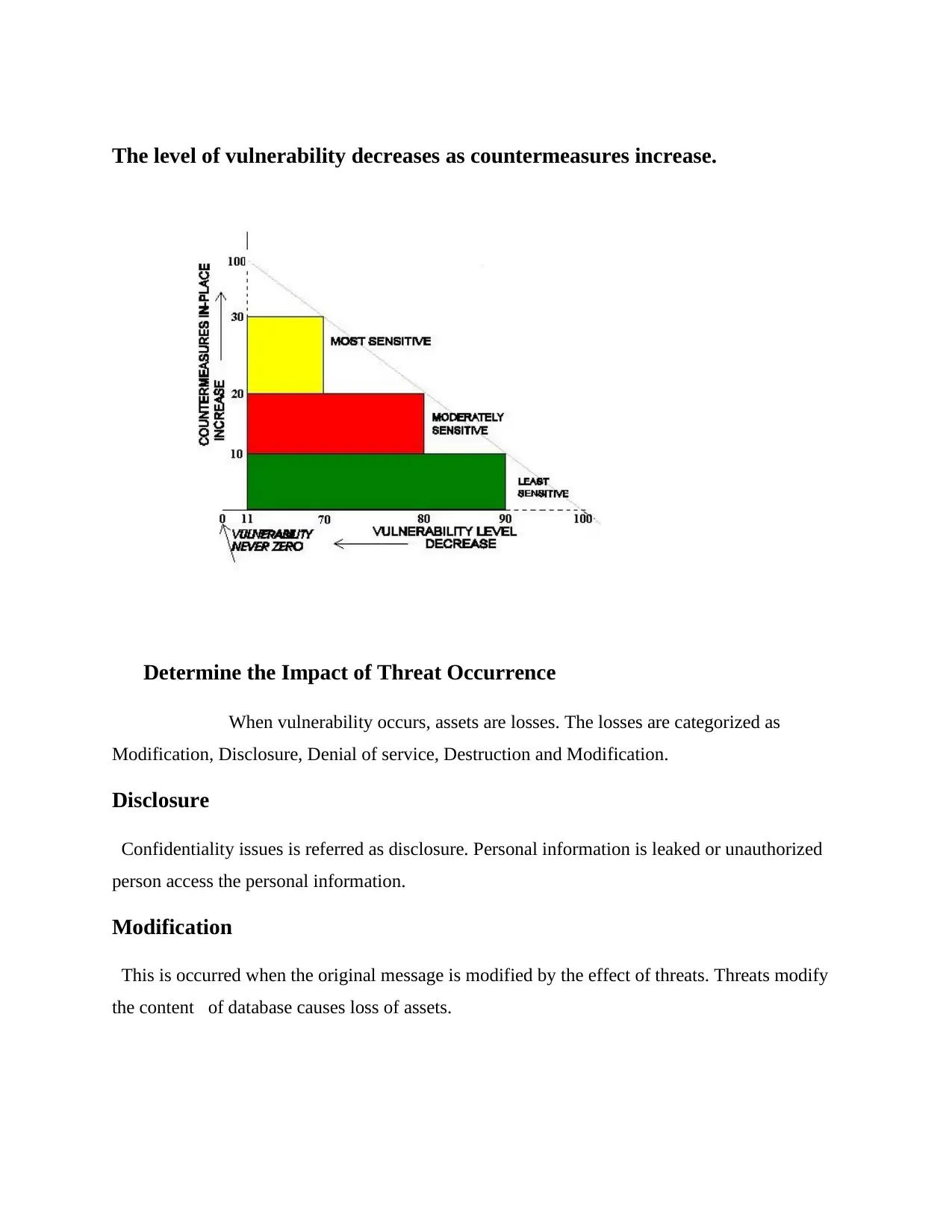
The level of vulnerability decreases as countermeasures increase.
Determine the Impact of Threat Occurrence
When vulnerability occurs, assets are losses. The losses are categorized as
Modification, Disclosure, Denial of service, Destruction and Modification.
Disclosure
Confidentiality issues is referred as disclosure. Personal information is leaked or unauthorized
person access the personal information.
Modification
This is occurred when the original message is modified by the effect of threats. Threats modify
the content of database causes loss of assets.
Determine the Impact of Threat Occurrence
When vulnerability occurs, assets are losses. The losses are categorized as
Modification, Disclosure, Denial of service, Destruction and Modification.
Disclosure
Confidentiality issues is referred as disclosure. Personal information is leaked or unauthorized
person access the personal information.
Modification
This is occurred when the original message is modified by the effect of threats. Threats modify
the content of database causes loss of assets.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
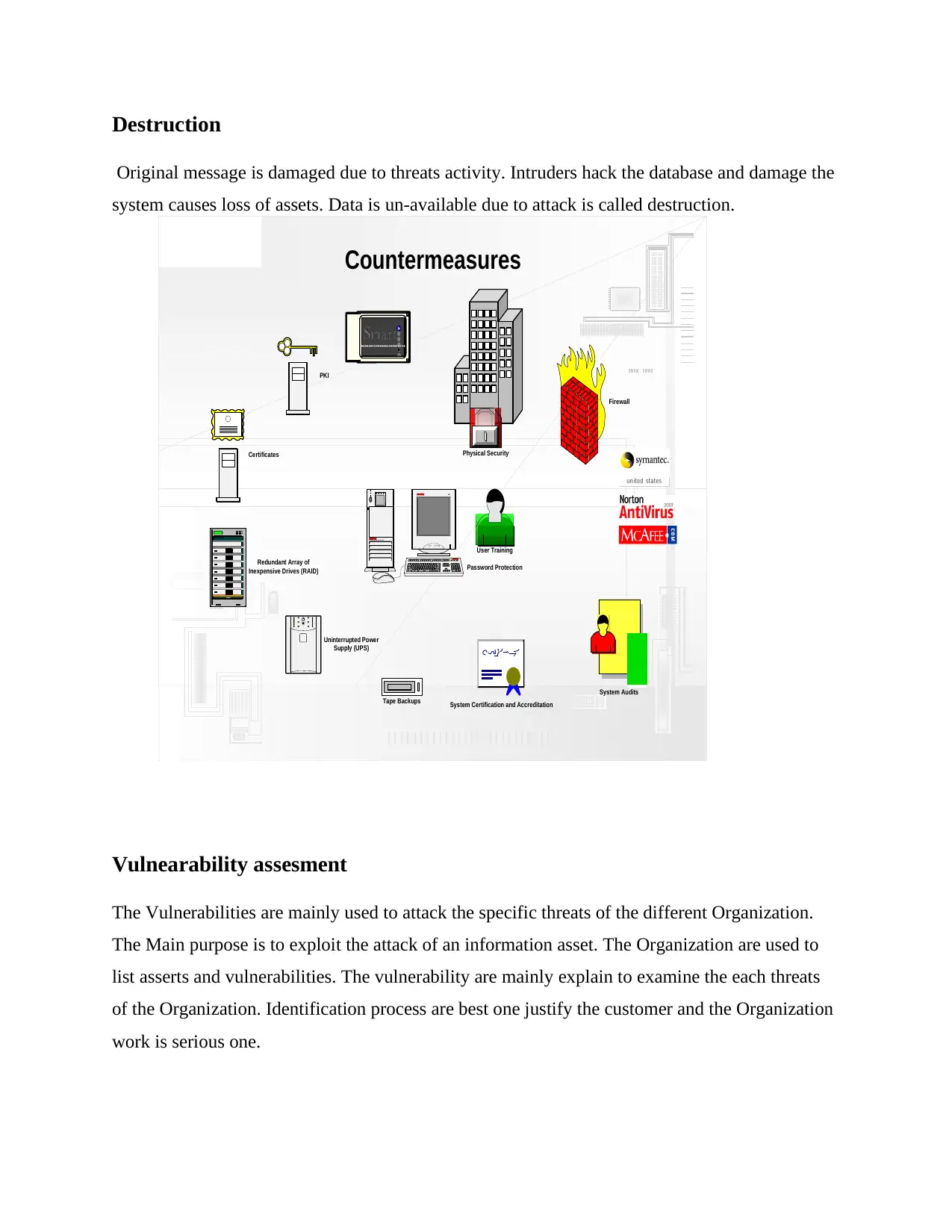
Destruction
Original message is damaged due to threats activity. Intruders hack the database and damage the
system causes loss of assets. Data is un-available due to attack is called destruction.
Vulnearability assesment
The Vulnerabilities are mainly used to attack the specific threats of the different Organization.
The Main purpose is to exploit the attack of an information asset. The Organization are used to
list asserts and vulnerabilities. The vulnerability are mainly explain to examine the each threats
of the Organization. Identification process are best one justify the customer and the Organization
work is serious one.
SD
Firewall
Certificates
PKI
System Audits
Physical Security
Redundant Array of
Inexpensive Drives (RAID)
Uninterrupted Power
Supply (UPS)
SD
Professional Workstation 6000
PRO
Tape Backups
User Training
Password Protection
Countermeasures
System Certification and Accreditation
Original message is damaged due to threats activity. Intruders hack the database and damage the
system causes loss of assets. Data is un-available due to attack is called destruction.
Vulnearability assesment
The Vulnerabilities are mainly used to attack the specific threats of the different Organization.
The Main purpose is to exploit the attack of an information asset. The Organization are used to
list asserts and vulnerabilities. The vulnerability are mainly explain to examine the each threats
of the Organization. Identification process are best one justify the customer and the Organization
work is serious one.
SD
Firewall
Certificates
PKI
System Audits
Physical Security
Redundant Array of
Inexpensive Drives (RAID)
Uninterrupted Power
Supply (UPS)
SD
Professional Workstation 6000
PRO
Tape Backups
User Training
Password Protection
Countermeasures
System Certification and Accreditation
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Risk assesment
Using risk assenment process we can determine risk and vulnerabilities.,Risk assesment
procss assigns a value to each specific informationj assets .Likelihood,uncertaninty,value of
information assets and percent of risk are the estimate factors of risk.
Using risk assenment process we can determine risk and vulnerabilities.,Risk assesment
procss assigns a value to each specific informationj assets .Likelihood,uncertaninty,value of
information assets and percent of risk are the estimate factors of risk.

RISK = vulnerabilty of occurrences
Risk Control Strategy
• Risk prevention
• Reduction of impact
• Reduction of likelihood
• Early detection
• Recovery
• Risk transfer
• Fits company culture
• Flexible
• Easy and quick to use
• Modelling capability
• Secure
Avoidance, loss prevention, loss reduction, Separation, duplication and diversification are the
fundamental techniques for risk control.
Vulnerability
Threat
Countermeasures
Risk
Management
Risk Control Strategy
• Risk prevention
• Reduction of impact
• Reduction of likelihood
• Early detection
• Recovery
• Risk transfer
• Fits company culture
• Flexible
• Easy and quick to use
• Modelling capability
• Secure
Avoidance, loss prevention, loss reduction, Separation, duplication and diversification are the
fundamental techniques for risk control.
Vulnerability
Threat
Countermeasures
Risk
Management
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

The additional details needed for the design of the system.
Access control techniques
DAC
MACs
NDC
Discretionary Access Control are implemented by the database user. MACs is an expansion of
Mandatory access controls. NDC is an expansion of Non-discretionary controls. Lattice based
control is another type of Non-discretionary. The structure of lattice based control is matrix. The
structure have rows and columns. Row is referred to subject .Colum is referred to objects.
Specific Requirements
Use at any stage of Project Life Cycle
Identify all or selected risks
Classify systems and projects
Countermeasure guidance
Audit trail
Organization must do
Information security risk criteria is identified, established and maintained. Repeat risk
assessment process to ensure the consistent, valid and comparable results. Protect the company
from knowable challenges is done by risk assessment Evaluating the potential, financial damages
and loss of assets. Understand mission and objectives of an organization and risk associated with.
Take risk assessment to generate value. Company must follow weakly risk assessment process to
generate value to protect from loss assets.
Access control techniques
DAC
MACs
NDC
Discretionary Access Control are implemented by the database user. MACs is an expansion of
Mandatory access controls. NDC is an expansion of Non-discretionary controls. Lattice based
control is another type of Non-discretionary. The structure of lattice based control is matrix. The
structure have rows and columns. Row is referred to subject .Colum is referred to objects.
Specific Requirements
Use at any stage of Project Life Cycle
Identify all or selected risks
Classify systems and projects
Countermeasure guidance
Audit trail
Organization must do
Information security risk criteria is identified, established and maintained. Repeat risk
assessment process to ensure the consistent, valid and comparable results. Protect the company
from knowable challenges is done by risk assessment Evaluating the potential, financial damages
and loss of assets. Understand mission and objectives of an organization and risk associated with.
Take risk assessment to generate value. Company must follow weakly risk assessment process to
generate value to protect from loss assets.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
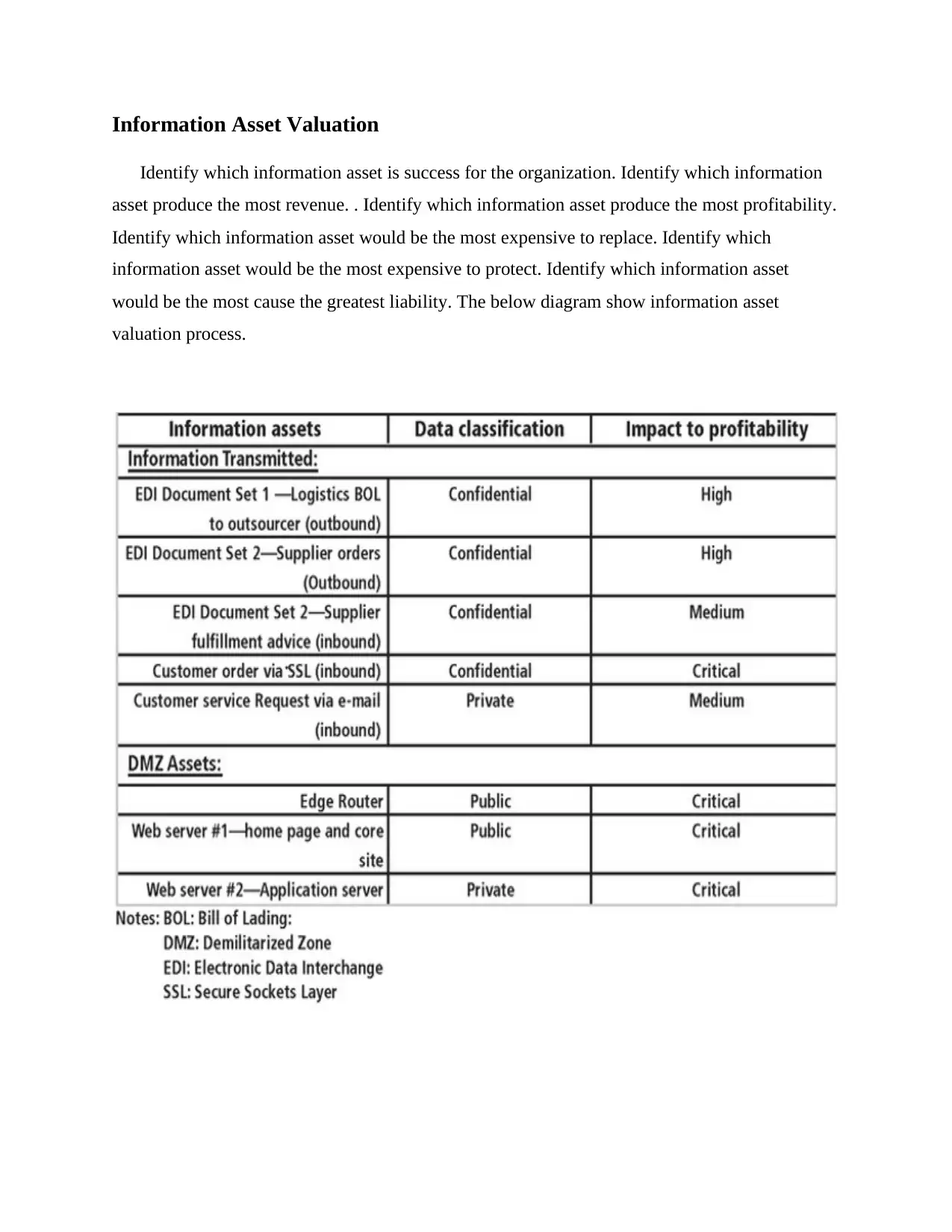
Information Asset Valuation
Identify which information asset is success for the organization. Identify which information
asset produce the most revenue. . Identify which information asset produce the most profitability.
Identify which information asset would be the most expensive to replace. Identify which
information asset would be the most expensive to protect. Identify which information asset
would be the most cause the greatest liability. The below diagram show information asset
valuation process.
Identify which information asset is success for the organization. Identify which information
asset produce the most revenue. . Identify which information asset produce the most profitability.
Identify which information asset would be the most expensive to replace. Identify which
information asset would be the most expensive to protect. Identify which information asset
would be the most cause the greatest liability. The below diagram show information asset
valuation process.

Security Risk Management:
The Risk Management is one of the important process for the Organization. The
process contain the controlling of threats of a business organization. The threats from a large
different of information, including organization Errors. Finally, a risk management increasing a
process for finding the treats and sophic character.
Risk Management contains two types are given below:
Risk Authority
Risk Determination
1. Risk Authority:
Risk Authority is used for the important concepts for the System Security. Risk
authority applying the Control to remit the risk to an Organization. Thus the reduce risk are
applicable for the data and information of the organization business.
2. Risk Determination:
Risk Determination is used to identify the Current information of the System. It’s
mainly used for the determining the data from the Organization. Risk management
identifying the knowledge of the organization and clarifying the organization attack. The
threats are important one for the Organization System, the large number of the threats are
attacked by assets.
Conformation determination and Valuation:
The following process involving the determination are given below:
User
Information and data
System Software
System Hardware
Networking
The Risk Management is one of the important process for the Organization. The
process contain the controlling of threats of a business organization. The threats from a large
different of information, including organization Errors. Finally, a risk management increasing a
process for finding the treats and sophic character.
Risk Management contains two types are given below:
Risk Authority
Risk Determination
1. Risk Authority:
Risk Authority is used for the important concepts for the System Security. Risk
authority applying the Control to remit the risk to an Organization. Thus the reduce risk are
applicable for the data and information of the organization business.
2. Risk Determination:
Risk Determination is used to identify the Current information of the System. It’s
mainly used for the determining the data from the Organization. Risk management
identifying the knowledge of the organization and clarifying the organization attack. The
threats are important one for the Organization System, the large number of the threats are
attacked by assets.
Conformation determination and Valuation:
The following process involving the determination are given below:
User
Information and data
System Software
System Hardware
Networking
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





