The Security of Mobile Phone Communication Apps: A Detailed Report
VerifiedAdded on 2022/10/11
|13
|874
|14
Report
AI Summary
This report investigates the security of mobile phone communication applications, examining the vulnerabilities and threats associated with mobile devices. The research explores user awareness of security measures, the effectiveness of existing security protocols, and the significance of data protection within mobile applications. The study employs secondary data analysis and a questionnaire-based approach to gather information on user behavior and the implementation of security controls. Key findings highlight the importance of user awareness, the need for robust security measures, and the critical role of app developers in ensuring data security. The report recommends that users install antivirus software and regularly back up their data to mitigate risks. The research aims to provide valuable insights for enhancing the security of mobile communication apps, contributing to a safer digital environment for users.

An investigation into the
security of mobile phone
communication apps
NAME OF THE STUDENT
NAME OF THE UNIVERSITY
security of mobile phone
communication apps
NAME OF THE STUDENT
NAME OF THE UNIVERSITY
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Introduction:
• The mobile working frameworks allow the developers for
making apps which can be ran on a mobile device.
• The communication technology has undergone the swift
advances which have seen the rise of application related
to mobile devices.
• The developers and designers have given restless effort
for the configuration of programming for giving the
users a smooth and advantageous experience.
• The mobile working frameworks allow the developers for
making apps which can be ran on a mobile device.
• The communication technology has undergone the swift
advances which have seen the rise of application related
to mobile devices.
• The developers and designers have given restless effort
for the configuration of programming for giving the
users a smooth and advantageous experience.
Background:
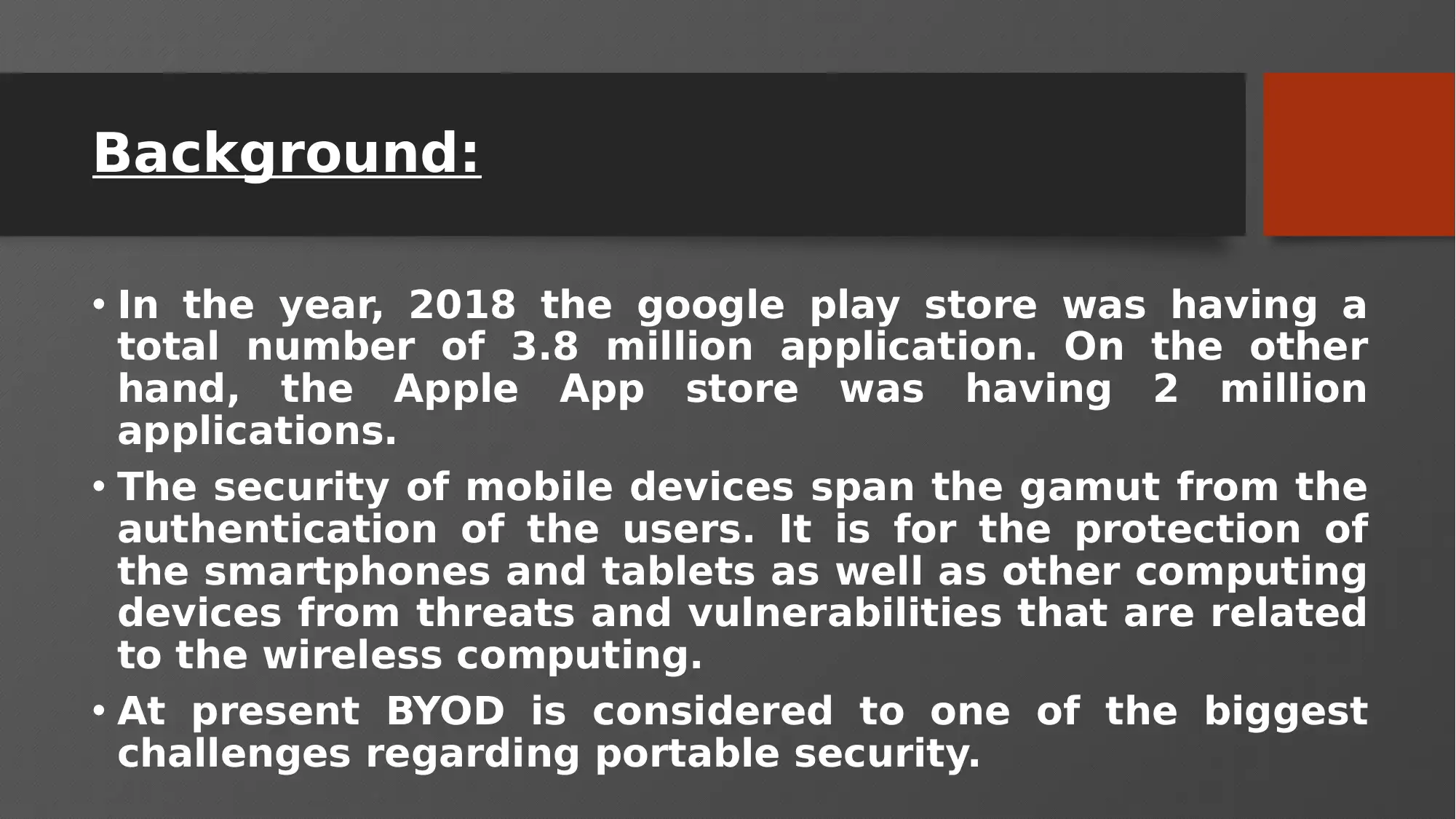
• In the year, 2018 the google play store was having a
total number of 3.8 million application. On the other
hand, the Apple App store was having 2 million
applications.
• The security of mobile devices span the gamut from the
authentication of the users. It is for the protection of
the smartphones and tablets as well as other computing
devices from threats and vulnerabilities that are related
to the wireless computing.
• At present BYOD is considered to one of the biggest
challenges regarding portable security.
• In the year, 2018 the google play store was having a
total number of 3.8 million application. On the other
hand, the Apple App store was having 2 million
applications.
• The security of mobile devices span the gamut from the
authentication of the users. It is for the protection of
the smartphones and tablets as well as other computing
devices from threats and vulnerabilities that are related
to the wireless computing.
• At present BYOD is considered to one of the biggest
challenges regarding portable security.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Research aims:
• The aim of the research is to assess the security
of communication related application of mobile
devices.
• The importance of protection of application
related to mobile phone for the performance as
this is having the ability to transform the way of
the operation of the applications.
• The aim of the research is to assess the security
of communication related application of mobile
devices.
• The importance of protection of application
related to mobile phone for the performance as
this is having the ability to transform the way of
the operation of the applications.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Research problem:
• The security of the mobile apps start with the
measurement which can be put in place by the
developers, designers as well as the mobile phone
communication app users.
• This is important for both the users, designers and
developers to take suitable step with the inclusion of
threats, vulnerability as well as security control against
the threats.
• According to ENISA, the lack of awareness by the users
on the protection is vulnerable for the security of
mobile communication apps.
• The security of the mobile apps start with the
measurement which can be put in place by the
developers, designers as well as the mobile phone
communication app users.
• This is important for both the users, designers and
developers to take suitable step with the inclusion of
threats, vulnerability as well as security control against
the threats.
• According to ENISA, the lack of awareness by the users
on the protection is vulnerable for the security of
mobile communication apps.

Research question & Research
objective
Questions:
• Are users aware of mobile communication security?
• Are their security measures put in place for the
mobile application security?
Objectives:
• To investigate user awareness of security on mobile
communications application.
• To investigate the effectiveness of the security
measures put in place for the applications.
objective
Questions:
• Are users aware of mobile communication security?
• Are their security measures put in place for the
mobile application security?
Objectives:
• To investigate user awareness of security on mobile
communications application.
• To investigate the effectiveness of the security
measures put in place for the applications.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Research time table:
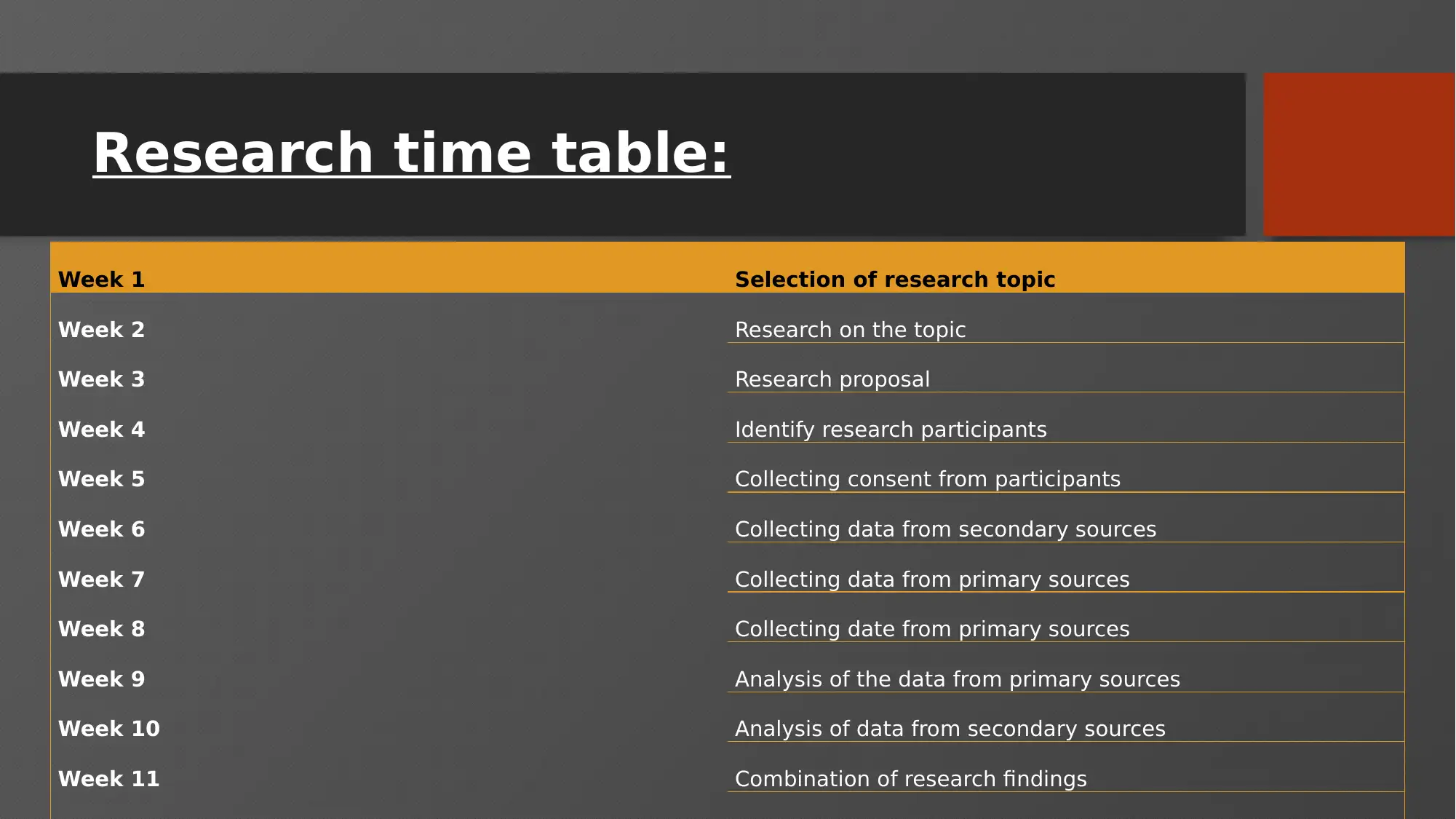
Week 1 Selection of research topic
Week 2 Research on the topic
Week 3 Research proposal
Week 4 Identify research participants
Week 5 Collecting consent from participants
Week 6 Collecting data from secondary sources
Week 7 Collecting data from primary sources
Week 8 Collecting date from primary sources
Week 9 Analysis of the data from primary sources
Week 10 Analysis of data from secondary sources
Week 11 Combination of research findings
Week 1 Selection of research topic
Week 2 Research on the topic
Week 3 Research proposal
Week 4 Identify research participants
Week 5 Collecting consent from participants
Week 6 Collecting data from secondary sources
Week 7 Collecting data from primary sources
Week 8 Collecting date from primary sources
Week 9 Analysis of the data from primary sources
Week 10 Analysis of data from secondary sources
Week 11 Combination of research findings
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Research methodology:
• For this research secondary data will be used for providing
adequate information and discussion for the researchers to
better understand deeply about the variables that relate to
the security of mobile phone communication apps.
• For the research the ethical issues fall into three phases of
the research process – research design, data collection, and
data analysis. All of the phases have been considered
during the procedure.
• A questionnaire will be designed that will contain relevant
questions, and before its distribution, a letter will be sent
to possible participants explaining the purpose of the
research.
• For this research secondary data will be used for providing
adequate information and discussion for the researchers to
better understand deeply about the variables that relate to
the security of mobile phone communication apps.
• For the research the ethical issues fall into three phases of
the research process – research design, data collection, and
data analysis. All of the phases have been considered
during the procedure.
• A questionnaire will be designed that will contain relevant
questions, and before its distribution, a letter will be sent
to possible participants explaining the purpose of the
research.
Significance of the study:
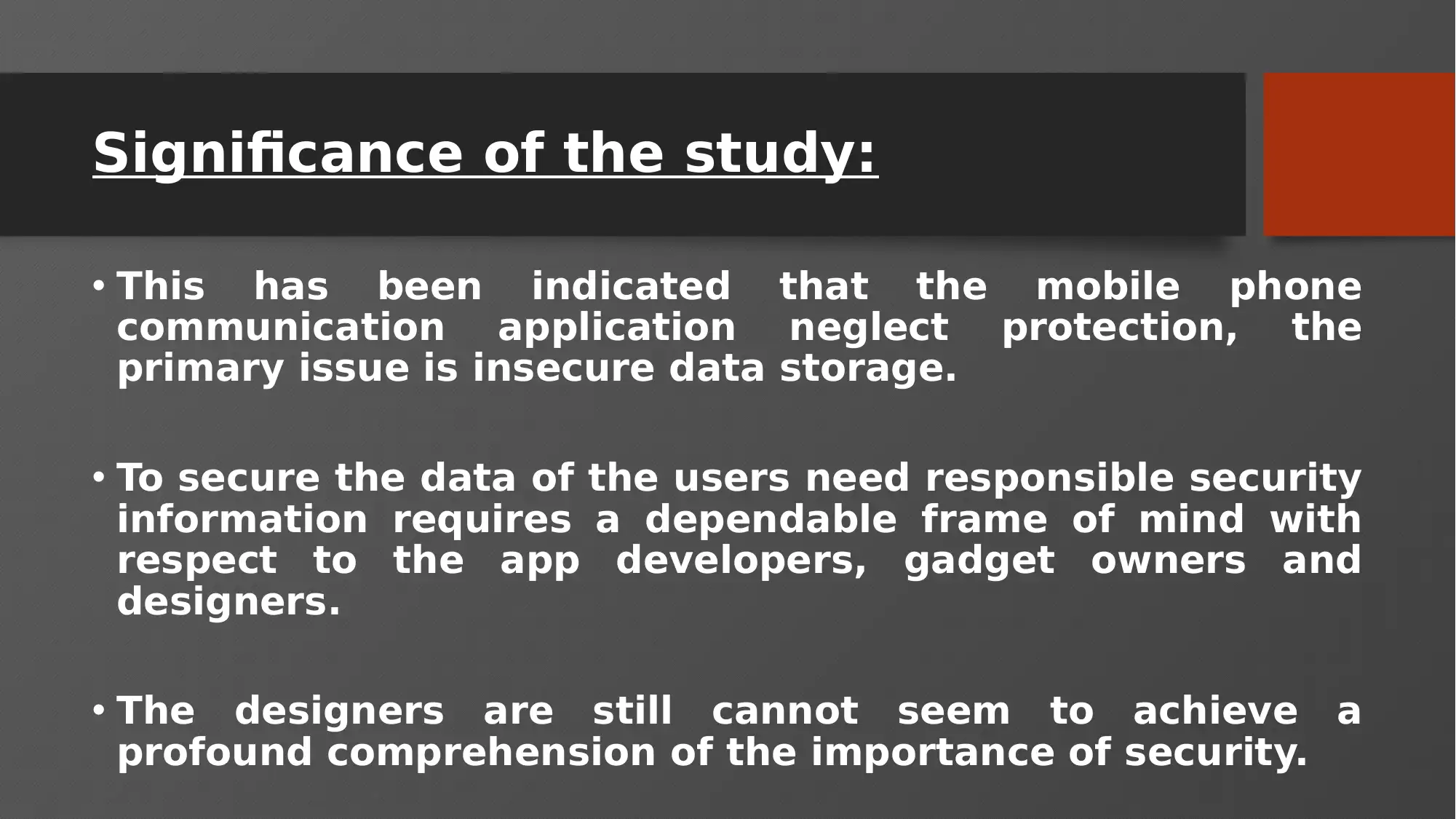
• This has been indicated that the mobile phone
communication application neglect protection, the
primary issue is insecure data storage.
• To secure the data of the users need responsible security
information requires a dependable frame of mind with
respect to the app developers, gadget owners and
designers.
• The designers are still cannot seem to achieve a
profound comprehension of the importance of security.
• This has been indicated that the mobile phone
communication application neglect protection, the
primary issue is insecure data storage.
• To secure the data of the users need responsible security
information requires a dependable frame of mind with
respect to the app developers, gadget owners and
designers.
• The designers are still cannot seem to achieve a
profound comprehension of the importance of security.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Expected outcome:
• The rise of mobile phones and internet has made
the communication more effective.
• The mobile phones can contain data and
information that are profitable.
• A hacked or lost mobile phone may cause harmful
or dangerous for the user.
• The mindfulness is one of the basic factors for the
security of application of mobile phones.
• The rise of mobile phones and internet has made
the communication more effective.
• The mobile phones can contain data and
information that are profitable.
• A hacked or lost mobile phone may cause harmful
or dangerous for the user.
• The mindfulness is one of the basic factors for the
security of application of mobile phones.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Conclusion & Recommendation:
• The mobile phone is becoming one of the most
important objectives for the human.
• As it contains personal and sensitive information and
mobile phones are using to make the everyday life
charming and effective.
• Thus, it can be recommended that the users have to
install antivirus on their mobile phone and always
need to back up the data on everyday basis.
• The mobile phone is becoming one of the most
important objectives for the human.
• As it contains personal and sensitive information and
mobile phones are using to make the everyday life
charming and effective.
• Thus, it can be recommended that the users have to
install antivirus on their mobile phone and always
need to back up the data on everyday basis.

References:
Eklund, L. (2016). The Sociality of Gaming:A mixed methods approach to understanding digital gaming as a
social leisure activity. Stockholm: Stockholm University.
Eslake, S. (2017). Productivity: The lost decade. Paper presented at the Annual Policy Conference of the
Reserve Bank of Australia, Sydney, 15 August 2011. Gartner (2010) Leading in times of transition: The 2010
CIO Agenda. .
Farotech. (2017). A beginner’s guide to pay per click. Available at http://www.farotech.com/blog/how-does-ppc-
work-a-beginners-guide-to-pay-per-click/.
Fiverr. (2017). Pay per click management and marketing. Available at http://www.fiverr.com/gig/.
JuKaria, R. (2015). F. Parke “Security awareness and adoption of security controls by smartphone users,” in
Proceedings of Second International Conference on Information Security and Cyber Forensics (InfoSec). 99–
104.
Koh-Diego, J. (2015). ASEE Annual Conference and Exposition Proceedings. Exploring Ethical Validation as a
Key Consideration in Interpretive Research Quality.
Eklund, L. (2016). The Sociality of Gaming:A mixed methods approach to understanding digital gaming as a
social leisure activity. Stockholm: Stockholm University.
Eslake, S. (2017). Productivity: The lost decade. Paper presented at the Annual Policy Conference of the
Reserve Bank of Australia, Sydney, 15 August 2011. Gartner (2010) Leading in times of transition: The 2010
CIO Agenda. .
Farotech. (2017). A beginner’s guide to pay per click. Available at http://www.farotech.com/blog/how-does-ppc-
work-a-beginners-guide-to-pay-per-click/.
Fiverr. (2017). Pay per click management and marketing. Available at http://www.fiverr.com/gig/.
JuKaria, R. (2015). F. Parke “Security awareness and adoption of security controls by smartphone users,” in
Proceedings of Second International Conference on Information Security and Cyber Forensics (InfoSec). 99–
104.
Koh-Diego, J. (2015). ASEE Annual Conference and Exposition Proceedings. Exploring Ethical Validation as a
Key Consideration in Interpretive Research Quality.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





