ITECH1001 Annotated Bibliography: Communication & IT - Week 4
VerifiedAdded on 2023/05/29
|5
|814
|333
Annotated Bibliography
AI Summary
This annotated bibliography focuses on communication and information technology, featuring summaries and evaluations of articles related to data security, privacy, cryptography, and big data security. The annotations highlight the importance of data protection laws, the role of technology in safeguarding information, and the future implications of these technologies. It references articles discussing data security acts, cryptography techniques, and the challenges of securing big data, emphasizing the need for robust legal frameworks and technological advancements to protect user data. The bibliography also includes a mind map visualizing key concepts related to communication and information technology, providing a comprehensive overview of the subject matter. Desklib provides more solved assignments.

Running head: COMMUNICATION AND INFORMATION TECHNOLOGY
COMMUNICATION AND INFORMATION TECHNOLOGY
Name of the Student
Name of the University
Author Note:
COMMUNICATION AND INFORMATION TECHNOLOGY
Name of the Student
Name of the University
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

COMMUNICATION AND INFORMATION TECHNOLOGY
Annotated 1
Title of the article: Data security and Privacy Author: Carey, Peter
URL:https://www.sciencedirect.com/science/article/pii/S2210832715000204
Date of access: 6/12/2018
Book: Anna, Z., 2016. The salient features of personal data protection laws with special
reference to cloud technologies. A comparative study between European countries and
Russia. Applied Computing and Informatics, 12(1), pp.1-15.
Page number: 240
Year of publication: 2014 Issue no: 1
Volume number: 12
Summary of the article:
The summary of the article can be related to the concept of the data security and the
privacy which can be related to the sector of the technology of cloud computing. The main sector
which is stated in the is related to the laws which can be enforced in the sector which would be
directly protecting the security of the data.
Evaluation:
The main sector of evaluation which can be stated in the article is related to the solving of
the problem which is related to the technological aspect. The 1998 data protection act was one of
the first step which focused on protection of data of the customers and the employee from
different intruder activity. One of the other factor which can be stated here is how the technology
can be used in the near future.
Reason for use:
The main reason for the selection of the article is done due to the factor that it majorly
takes into consideration future prospective of the technology and how it would be playing a role
in the life of the people.
Annotated 1
Title of the article: Data security and Privacy Author: Carey, Peter
URL:https://www.sciencedirect.com/science/article/pii/S2210832715000204
Date of access: 6/12/2018
Book: Anna, Z., 2016. The salient features of personal data protection laws with special
reference to cloud technologies. A comparative study between European countries and
Russia. Applied Computing and Informatics, 12(1), pp.1-15.
Page number: 240
Year of publication: 2014 Issue no: 1
Volume number: 12
Summary of the article:
The summary of the article can be related to the concept of the data security and the
privacy which can be related to the sector of the technology of cloud computing. The main sector
which is stated in the is related to the laws which can be enforced in the sector which would be
directly protecting the security of the data.
Evaluation:
The main sector of evaluation which can be stated in the article is related to the solving of
the problem which is related to the technological aspect. The 1998 data protection act was one of
the first step which focused on protection of data of the customers and the employee from
different intruder activity. One of the other factor which can be stated here is how the technology
can be used in the near future.
Reason for use:
The main reason for the selection of the article is done due to the factor that it majorly
takes into consideration future prospective of the technology and how it would be playing a role
in the life of the people.

COMMUNICATION AND INFORMATION TECHNOLOGY
Annotated 2
Title of the article: Cryptography and data security Author: Robling Denning,
Dorothy Elizabeth
URL:https://faculty.nps.edu/dedennin/publications/Denning
CryptographyDataSecurity.pdf Date of access: 6/12/2018
Journal article: NA Page number: NA
Year of publication: 1982 Issue no: 1
Volume number: 1
Summary of the article:
The main summary of the article can be related is related to the cryptography and the data
security aspect which is linked to the sector. In most of the cases it can be stated that security of
the data is one of the important factor which plays a very vital role. The data protection act 2017
was implemented in the Data protection office (DPO) for government actions and policy to
protect the data.
Evaluation:
The main sector of evaluation which can be done in the sector is related to how the data
security would be prevailing into the system. One of the important concern area which is seen in
the sector is related to how the data of the employee and the user in a system would be secured.
Reason for use:
The main reason for the use can be related to the sector to the future use and how the
advancement of the technology would be playing a significant role. The laws which are enforced
in most of the sector are directly defined in the aspect of delivering a standard of security of the
data.
Annotated 2
Title of the article: Cryptography and data security Author: Robling Denning,
Dorothy Elizabeth
URL:https://faculty.nps.edu/dedennin/publications/Denning
CryptographyDataSecurity.pdf Date of access: 6/12/2018
Journal article: NA Page number: NA
Year of publication: 1982 Issue no: 1
Volume number: 1
Summary of the article:
The main summary of the article can be related is related to the cryptography and the data
security aspect which is linked to the sector. In most of the cases it can be stated that security of
the data is one of the important factor which plays a very vital role. The data protection act 2017
was implemented in the Data protection office (DPO) for government actions and policy to
protect the data.
Evaluation:
The main sector of evaluation which can be done in the sector is related to how the data
security would be prevailing into the system. One of the important concern area which is seen in
the sector is related to how the data of the employee and the user in a system would be secured.
Reason for use:
The main reason for the use can be related to the sector to the future use and how the
advancement of the technology would be playing a significant role. The laws which are enforced
in most of the sector are directly defined in the aspect of delivering a standard of security of the
data.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

COMMUNICATION AND INFORMATION TECHNOLOGY
Annotated 3
Title of the article: Big data security Author: Bertino
URL: https://scholarship.law.berkeley.edu/cgi/viewcontent.cgi?article=2197&context=btlj
Date of access: 6/12/2018
Journal article: Keller, D., 2018. The Right Tools: Europe's Intermediary Liability Laws and
the EU 2016 General Data Protection Regulation. Berkeley Tech. LJ, 33, p.287.
Page number: 293
Year of publication: 2015 Issue no: 1
Volume number: 33
Summary of the article:
The main summary of the article is related to the big data security aspect which would be
prevailing into the technology. One of the most important factor which is related to the concept
is how the organization and different people oblige with the laws and regulation. The article also
focusses on the protection act of 2014 to safe guard the data and policies which mainly focus on
protection mechanism.
Evaluation:
The main sector of engagement is related to the construction of the law when it is need
and how the enforcement of the laws is made into the different scenario of working.
Reason for use:
The main use of the article is due to the factor of the engagement of the different laws in
the sector of the working of the data security and protection mechanisms.
Annotated 3
Title of the article: Big data security Author: Bertino
URL: https://scholarship.law.berkeley.edu/cgi/viewcontent.cgi?article=2197&context=btlj
Date of access: 6/12/2018
Journal article: Keller, D., 2018. The Right Tools: Europe's Intermediary Liability Laws and
the EU 2016 General Data Protection Regulation. Berkeley Tech. LJ, 33, p.287.
Page number: 293
Year of publication: 2015 Issue no: 1
Volume number: 33
Summary of the article:
The main summary of the article is related to the big data security aspect which would be
prevailing into the technology. One of the most important factor which is related to the concept
is how the organization and different people oblige with the laws and regulation. The article also
focusses on the protection act of 2014 to safe guard the data and policies which mainly focus on
protection mechanism.
Evaluation:
The main sector of engagement is related to the construction of the law when it is need
and how the enforcement of the laws is made into the different scenario of working.
Reason for use:
The main use of the article is due to the factor of the engagement of the different laws in
the sector of the working of the data security and protection mechanisms.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
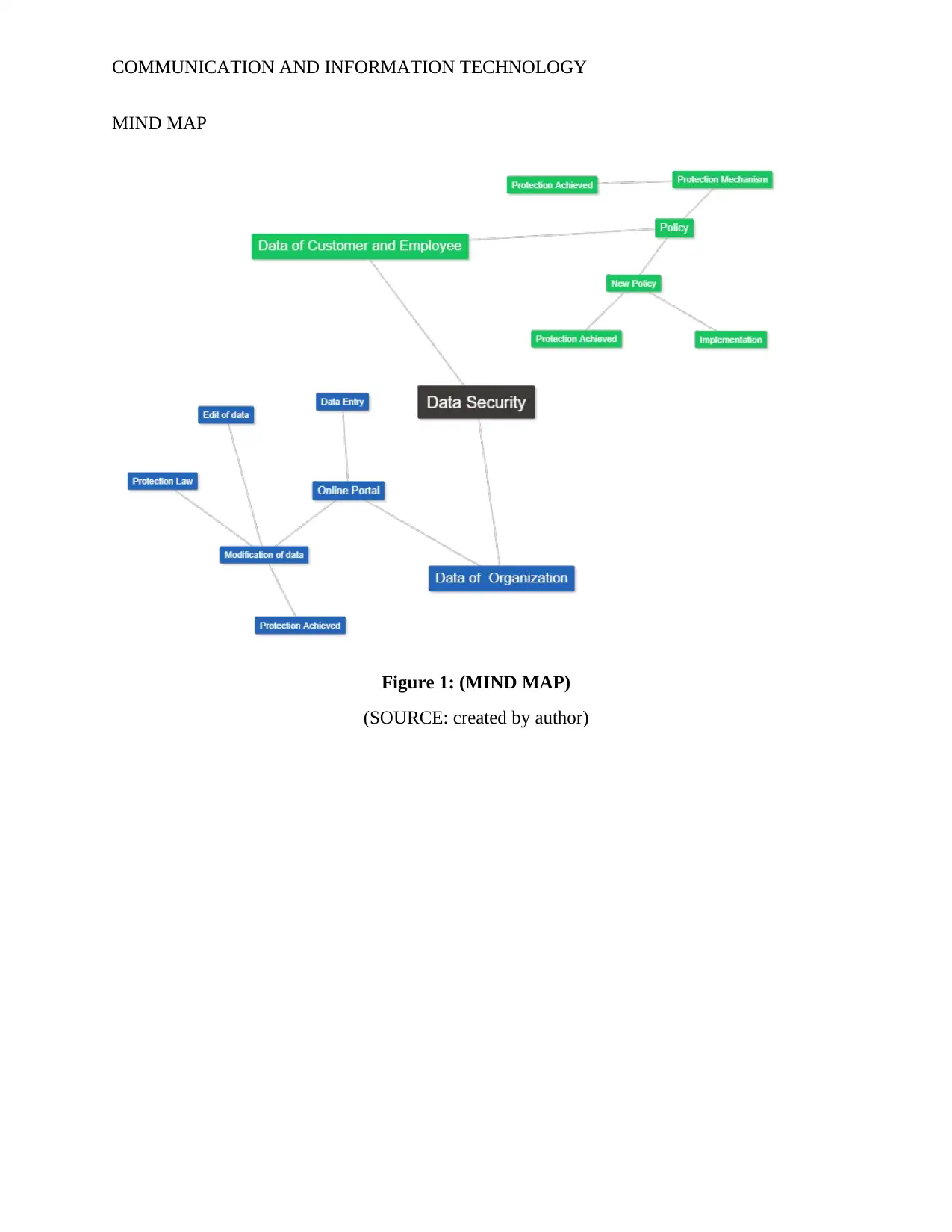
COMMUNICATION AND INFORMATION TECHNOLOGY
MIND MAP
Figure 1: (MIND MAP)
(SOURCE: created by author)
MIND MAP
Figure 1: (MIND MAP)
(SOURCE: created by author)
1 out of 5
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





