Analyzing ICMP and IP Protocols: A Communications and Networking Study
VerifiedAdded on 2023/01/17
|46
|4791
|23
Practical Assignment
AI Summary
This report presents a detailed analysis of ICMP and IP protocols through practical experiments involving ping and traceroute. The study begins by examining ping activities to websites in different continents, analyzing IP addresses, port numbers, and the contents of ICMP request and reply packets using Wireshark. The report then delves into traceroute, investigating ICMP packets and comparing them with ping packets, including the identification of links with significant delays. Furthermore, the analysis extends to PingPlotter, providing a comprehensive view of router hops, their locations, and latency graphs across different packet sizes. The report examines IP fragmentation, analyzing the contents of IP headers across different packet sizes and fragments, concluding with a discussion on the observed patterns and changes in the IP datagram fields.

Running head: COMMUNICATIONS AND NETWORKING
Communications and Networking
Student Name
University Name
Note by the Author
Communications and Networking
Student Name
University Name
Note by the Author
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1COMMUNICATIONS AND NETWORKING
Summary
This report aims to record and study the pinging, and tracing activities of three different
websites located in a different continent (Europe and North America) than the place from
where the network analysis is being conducted that is Asia. First the report performs a ping of
the website www.ece.ust.eu and discusses the IP address and ports of the source and
destination hosts as well as goes in depth into the protocol contents of ping request and reply
packets. Then the trace of another website www.inria.fr is conducted and thorough research
on ICMP packets and their comparison with that of the ping are made before finding the link
with the longest delay. Thereafter, a trace is performed on gaia.cs.umass.edu is performed in
PingPlotter to get a more comprehensive look at the nearest first hop routers, their location as
also the graph of the latencies of each step. This is a composite process conducted for three
different packet sizes (56 bytes, 2000 bytes, 3500 bytes). Here, the contents of the IP protocol
get further analysed and it is checked if datagrams got fragmented and also details and
comparison of the identified fragments for different packet sizes are performed after which
the report ends with concluding notes.
Summary
This report aims to record and study the pinging, and tracing activities of three different
websites located in a different continent (Europe and North America) than the place from
where the network analysis is being conducted that is Asia. First the report performs a ping of
the website www.ece.ust.eu and discusses the IP address and ports of the source and
destination hosts as well as goes in depth into the protocol contents of ping request and reply
packets. Then the trace of another website www.inria.fr is conducted and thorough research
on ICMP packets and their comparison with that of the ping are made before finding the link
with the longest delay. Thereafter, a trace is performed on gaia.cs.umass.edu is performed in
PingPlotter to get a more comprehensive look at the nearest first hop routers, their location as
also the graph of the latencies of each step. This is a composite process conducted for three
different packet sizes (56 bytes, 2000 bytes, 3500 bytes). Here, the contents of the IP protocol
get further analysed and it is checked if datagrams got fragmented and also details and
comparison of the identified fragments for different packet sizes are performed after which
the report ends with concluding notes.

2COMMUNICATIONS AND NETWORKING
Table of Contents
Introduction................................................................................................................................5
Analysis of Traces......................................................................................................................5
Part A: Ping of website of another continent.........................................................................5
1. IP addresses of local host and that of destination host...................................................8
2. Reason for ICMP packets not having source port or destination port numbers.............8
3. Examining a ping request packet sent by local host (ICMP Type, Code numbers and
rest of the fields, number of bytes for checksum, sequence number and identifier fields)9
4. Examining a ping request packet sent by local host (ICMP Type, Code numbers and
rest of the fields, number of bytes for checksum, sequence number and identifier fields)
..........................................................................................................................................10
Part B: Trace route...............................................................................................................11
5. IP addresses of local host and that of destination host.................................................13
6. IP Protocol number if system was Linux or UNIX based and ICMP sent UDP
packets..............................................................................................................................13
7. Examining ICMP echo packet and whether it is different from ICMP ping query
packets..............................................................................................................................14
8. Examining contents of ICMP error packets which have more fields than ICMP echo
packets..............................................................................................................................15
9. Examining last 3 ICMP packets...................................................................................16
10. Link among tracert measurements where delay is significantly longer than the rest 17
Part C: Trace with PingPlotter and Latency Graph..............................................................17
Table of Contents
Introduction................................................................................................................................5
Analysis of Traces......................................................................................................................5
Part A: Ping of website of another continent.........................................................................5
1. IP addresses of local host and that of destination host...................................................8
2. Reason for ICMP packets not having source port or destination port numbers.............8
3. Examining a ping request packet sent by local host (ICMP Type, Code numbers and
rest of the fields, number of bytes for checksum, sequence number and identifier fields)9
4. Examining a ping request packet sent by local host (ICMP Type, Code numbers and
rest of the fields, number of bytes for checksum, sequence number and identifier fields)
..........................................................................................................................................10
Part B: Trace route...............................................................................................................11
5. IP addresses of local host and that of destination host.................................................13
6. IP Protocol number if system was Linux or UNIX based and ICMP sent UDP
packets..............................................................................................................................13
7. Examining ICMP echo packet and whether it is different from ICMP ping query
packets..............................................................................................................................14
8. Examining contents of ICMP error packets which have more fields than ICMP echo
packets..............................................................................................................................15
9. Examining last 3 ICMP packets...................................................................................16
10. Link among tracert measurements where delay is significantly longer than the rest 17
Part C: Trace with PingPlotter and Latency Graph..............................................................17
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3COMMUNICATIONS AND NETWORKING
1. Select the first ICMP Echo Request message sent by your computer, and expand the
Internet Protocol part of the packet in the packet details window. What is the IP address
of your computer?............................................................................................................25
2. Within the IP packet header, what is the value in the upper layer protocol field?.......26
3. How many bytes are in the IP header? How many bytes are in the payload of the IP
datagram? Explain how you determined the number of payload bytes...........................26
4. Has this IP datagram been fragmented? Explain how you determined whether or not
the datagram has been fragmented...................................................................................27
5. Which fields in the IP datagram always change from one datagram to the next within
this series of ICMP messages sent by your computer?....................................................29
6. Which fields stay constant? Which of the fields must stay constant? Which fields must
change? Why?..................................................................................................................30
7. Describe the pattern you see in the values in the Identification field of the IP datagram
..........................................................................................................................................30
8. What is the value in the Identification field and the TTL field?..................................31
9. Do these values remain unchanged for all of the ICMP TTL-exceeded replies sent to
your computer by the nearest (first hop) router? Why?...................................................34
10. Find the first ICMP Echo Request message that was sent by your computer after you
changed the Packet Size in pingplotter to be 2000. Has that message been fragmented
across more than one IP datagram?..................................................................................35
11. Print out the first fragment of the fragmented IP datagram. What information in the
IP header indicates that the datagram been fragmented? What information in the IP
1. Select the first ICMP Echo Request message sent by your computer, and expand the
Internet Protocol part of the packet in the packet details window. What is the IP address
of your computer?............................................................................................................25
2. Within the IP packet header, what is the value in the upper layer protocol field?.......26
3. How many bytes are in the IP header? How many bytes are in the payload of the IP
datagram? Explain how you determined the number of payload bytes...........................26
4. Has this IP datagram been fragmented? Explain how you determined whether or not
the datagram has been fragmented...................................................................................27
5. Which fields in the IP datagram always change from one datagram to the next within
this series of ICMP messages sent by your computer?....................................................29
6. Which fields stay constant? Which of the fields must stay constant? Which fields must
change? Why?..................................................................................................................30
7. Describe the pattern you see in the values in the Identification field of the IP datagram
..........................................................................................................................................30
8. What is the value in the Identification field and the TTL field?..................................31
9. Do these values remain unchanged for all of the ICMP TTL-exceeded replies sent to
your computer by the nearest (first hop) router? Why?...................................................34
10. Find the first ICMP Echo Request message that was sent by your computer after you
changed the Packet Size in pingplotter to be 2000. Has that message been fragmented
across more than one IP datagram?..................................................................................35
11. Print out the first fragment of the fragmented IP datagram. What information in the
IP header indicates that the datagram been fragmented? What information in the IP
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4COMMUNICATIONS AND NETWORKING
header indicates whether this is the first fragment versus a latter fragment? How long is
this IP datagram?..............................................................................................................36
12. Print out the second fragment of the fragmented IP datagram. What information in
the IP header indicates that this is not the first datagram fragment? Are the more
fragments? How can you tell?..........................................................................................38
13. What fields change in the IP header between the first and second fragment?...........39
14. How many fragments were created from the original datagram?..............................40
15. What fields change in the IP header among the fragments?......................................41
Conclusion................................................................................................................................41
Bibliography.............................................................................................................................42
header indicates whether this is the first fragment versus a latter fragment? How long is
this IP datagram?..............................................................................................................36
12. Print out the second fragment of the fragmented IP datagram. What information in
the IP header indicates that this is not the first datagram fragment? Are the more
fragments? How can you tell?..........................................................................................38
13. What fields change in the IP header between the first and second fragment?...........39
14. How many fragments were created from the original datagram?..............................40
15. What fields change in the IP header among the fragments?......................................41
Conclusion................................................................................................................................41
Bibliography.............................................................................................................................42

5COMMUNICATIONS AND NETWORKING
Introduction
The following report records and studies the ping, and traceroute activities of three
different websites located in different continents (Europe and North America) than the place
from where the network analysis is being conducted that is Asia. The report begins by
performing a ping of the website www.ece.ust.eu and discusses the IP address and ports of
the source and destination hosts as well as goes in depth into the protocol contents of ping
request and reply packets. Then the trace of another website www.inria.fr is conducted and
thorough research on ICMP packets and their comparison with that of the ping are made
before finding the link with the longest delay. Thereafter, a trace is performed on
gaia.cs.umass.edu is performed in PingPlotter to get a more comprehensive look at the
nearest first hop routers, their location as also the graph of the latencies of each step. This is a
composite process conducted for three different packet sizes (56 bytes, 2000 bytes, 3500
bytes). Here, the contents of the IP protocol get further analysed and it is checked if
datagrams got fragmented and also details and comparison of the identified fragments for
different packet sizes are performed after which the report ends with concluding notes.
Introduction
The following report records and studies the ping, and traceroute activities of three
different websites located in different continents (Europe and North America) than the place
from where the network analysis is being conducted that is Asia. The report begins by
performing a ping of the website www.ece.ust.eu and discusses the IP address and ports of
the source and destination hosts as well as goes in depth into the protocol contents of ping
request and reply packets. Then the trace of another website www.inria.fr is conducted and
thorough research on ICMP packets and their comparison with that of the ping are made
before finding the link with the longest delay. Thereafter, a trace is performed on
gaia.cs.umass.edu is performed in PingPlotter to get a more comprehensive look at the
nearest first hop routers, their location as also the graph of the latencies of each step. This is a
composite process conducted for three different packet sizes (56 bytes, 2000 bytes, 3500
bytes). Here, the contents of the IP protocol get further analysed and it is checked if
datagrams got fragmented and also details and comparison of the identified fragments for
different packet sizes are performed after which the report ends with concluding notes.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
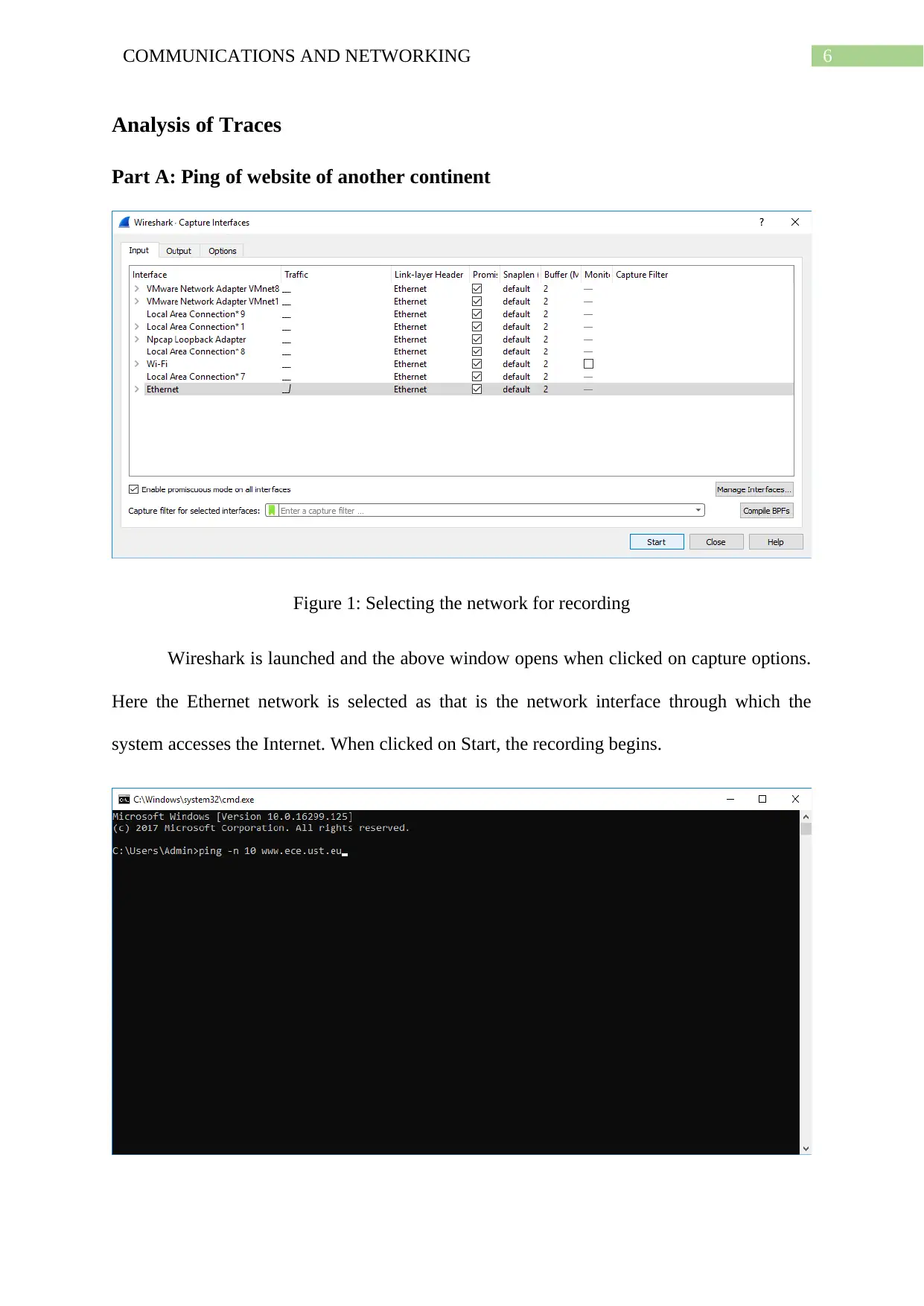
6COMMUNICATIONS AND NETWORKING
Analysis of Traces
Part A: Ping of website of another continent
Figure 1: Selecting the network for recording
Wireshark is launched and the above window opens when clicked on capture options.
Here the Ethernet network is selected as that is the network interface through which the
system accesses the Internet. When clicked on Start, the recording begins.
Analysis of Traces
Part A: Ping of website of another continent
Figure 1: Selecting the network for recording
Wireshark is launched and the above window opens when clicked on capture options.
Here the Ethernet network is selected as that is the network interface through which the
system accesses the Internet. When clicked on Start, the recording begins.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
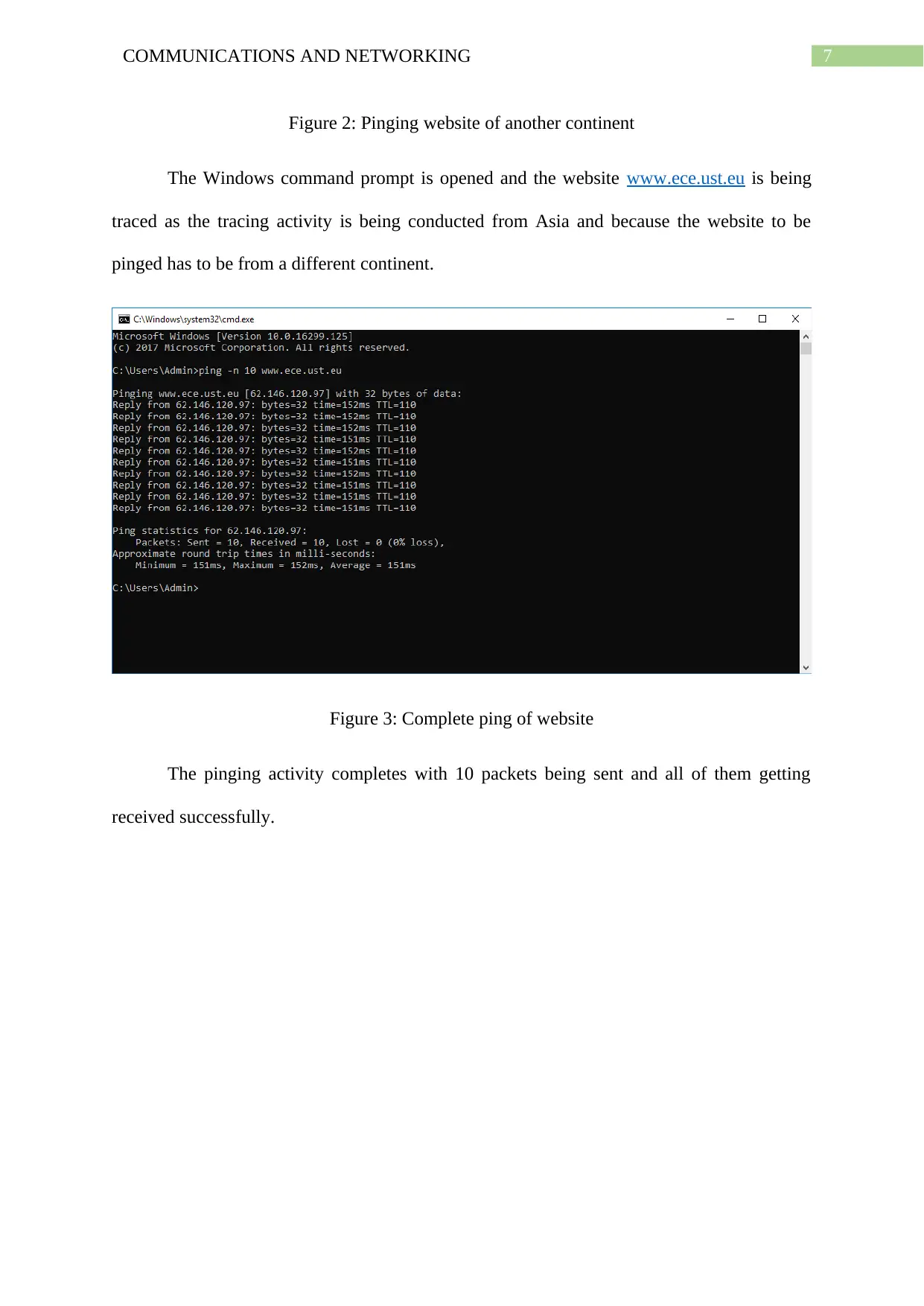
7COMMUNICATIONS AND NETWORKING
Figure 2: Pinging website of another continent
The Windows command prompt is opened and the website www.ece.ust.eu is being
traced as the tracing activity is being conducted from Asia and because the website to be
pinged has to be from a different continent.
Figure 3: Complete ping of website
The pinging activity completes with 10 packets being sent and all of them getting
received successfully.
Figure 2: Pinging website of another continent
The Windows command prompt is opened and the website www.ece.ust.eu is being
traced as the tracing activity is being conducted from Asia and because the website to be
pinged has to be from a different continent.
Figure 3: Complete ping of website
The pinging activity completes with 10 packets being sent and all of them getting
received successfully.
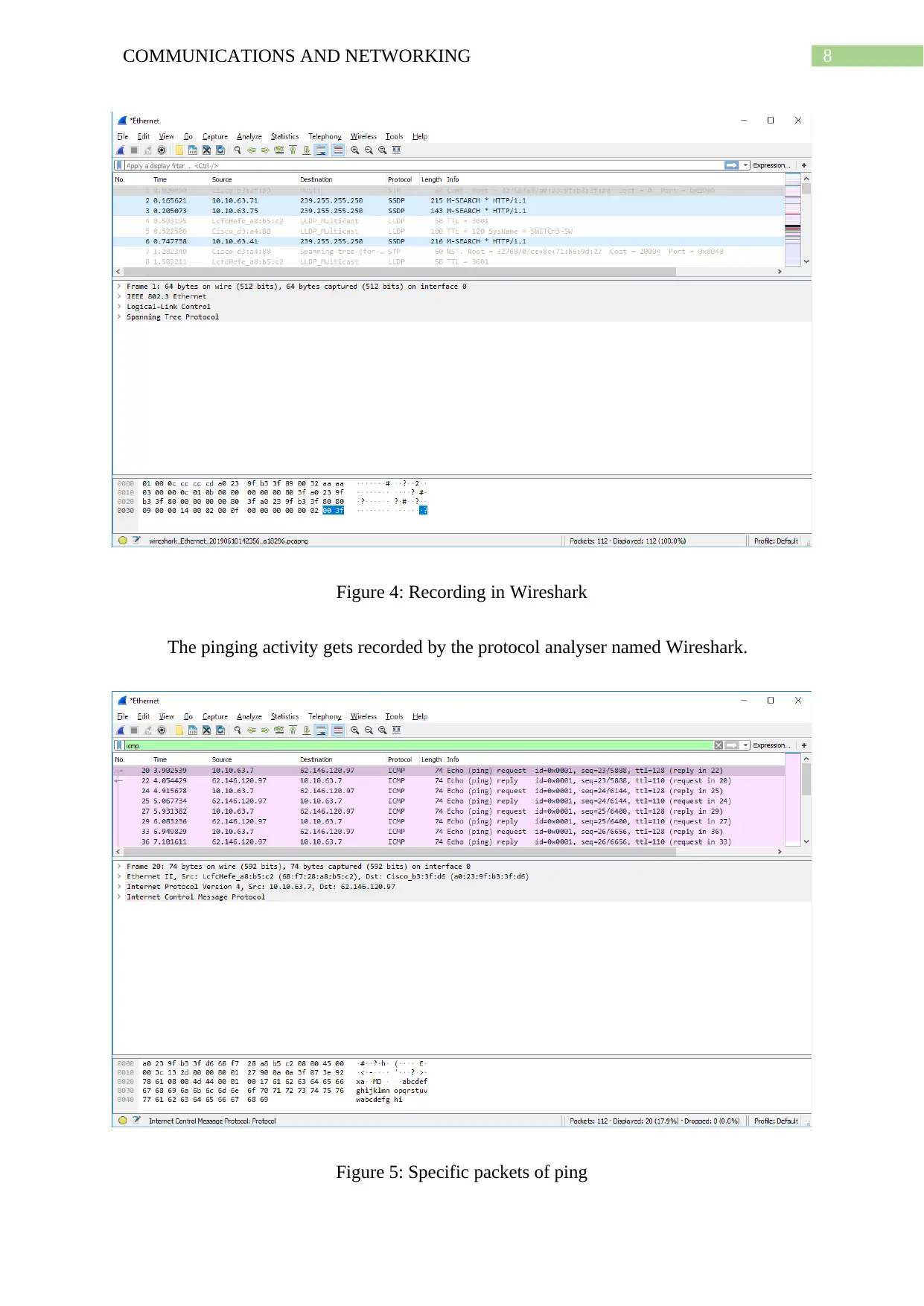
8COMMUNICATIONS AND NETWORKING
Figure 4: Recording in Wireshark
The pinging activity gets recorded by the protocol analyser named Wireshark.
Figure 5: Specific packets of ping
Figure 4: Recording in Wireshark
The pinging activity gets recorded by the protocol analyser named Wireshark.
Figure 5: Specific packets of ping
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9COMMUNICATIONS AND NETWORKING
Next the packets involved in the ping activity is separately listed by applying a filter
to show all packets of ICMP protocol. Thus the packets shown by Wireshark now are either
ping (request) or ping (reply) packet.
1. What is the IP address of your host? What is the IP address of the destination host?
As can be seen in Wireshark the IP address of the local host from where the ping of
the website is being made is 10.10.63.7 and the IP address of the destination host is
62.146.120.97.
2. Why is it that an ICMP packet does not have source and destination port numbers?
ICMP packets do not have port numbers for the source and destination because it is
designed for communicating with network layer information between the routers and hosts
instead of among processes of application layer.
Next the packets involved in the ping activity is separately listed by applying a filter
to show all packets of ICMP protocol. Thus the packets shown by Wireshark now are either
ping (request) or ping (reply) packet.
1. What is the IP address of your host? What is the IP address of the destination host?
As can be seen in Wireshark the IP address of the local host from where the ping of
the website is being made is 10.10.63.7 and the IP address of the destination host is
62.146.120.97.
2. Why is it that an ICMP packet does not have source and destination port numbers?
ICMP packets do not have port numbers for the source and destination because it is
designed for communicating with network layer information between the routers and hosts
instead of among processes of application layer.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
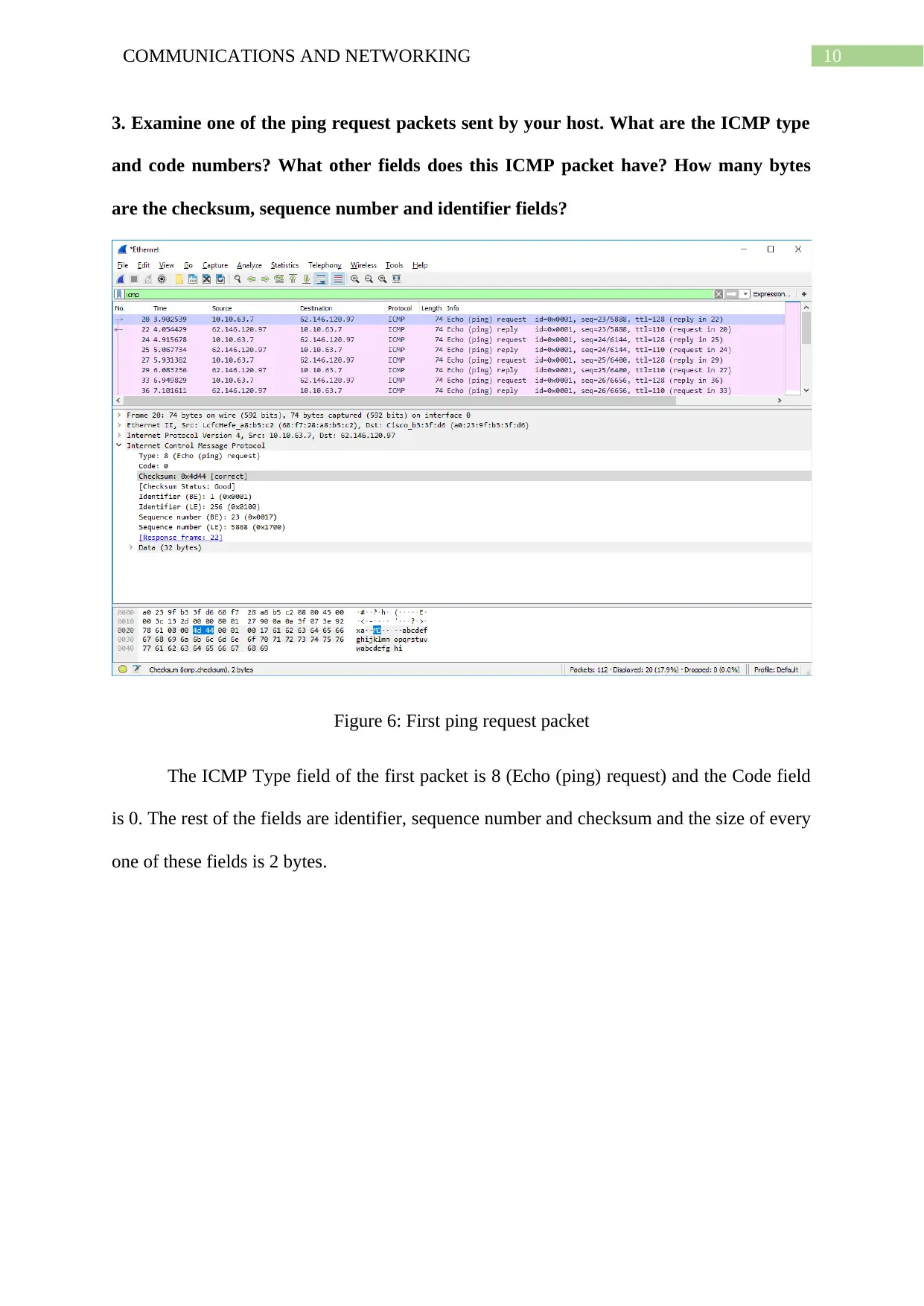
10COMMUNICATIONS AND NETWORKING
3. Examine one of the ping request packets sent by your host. What are the ICMP type
and code numbers? What other fields does this ICMP packet have? How many bytes
are the checksum, sequence number and identifier fields?
Figure 6: First ping request packet
The ICMP Type field of the first packet is 8 (Echo (ping) request) and the Code field
is 0. The rest of the fields are identifier, sequence number and checksum and the size of every
one of these fields is 2 bytes.
3. Examine one of the ping request packets sent by your host. What are the ICMP type
and code numbers? What other fields does this ICMP packet have? How many bytes
are the checksum, sequence number and identifier fields?
Figure 6: First ping request packet
The ICMP Type field of the first packet is 8 (Echo (ping) request) and the Code field
is 0. The rest of the fields are identifier, sequence number and checksum and the size of every
one of these fields is 2 bytes.
11COMMUNICATIONS AND NETWORKING
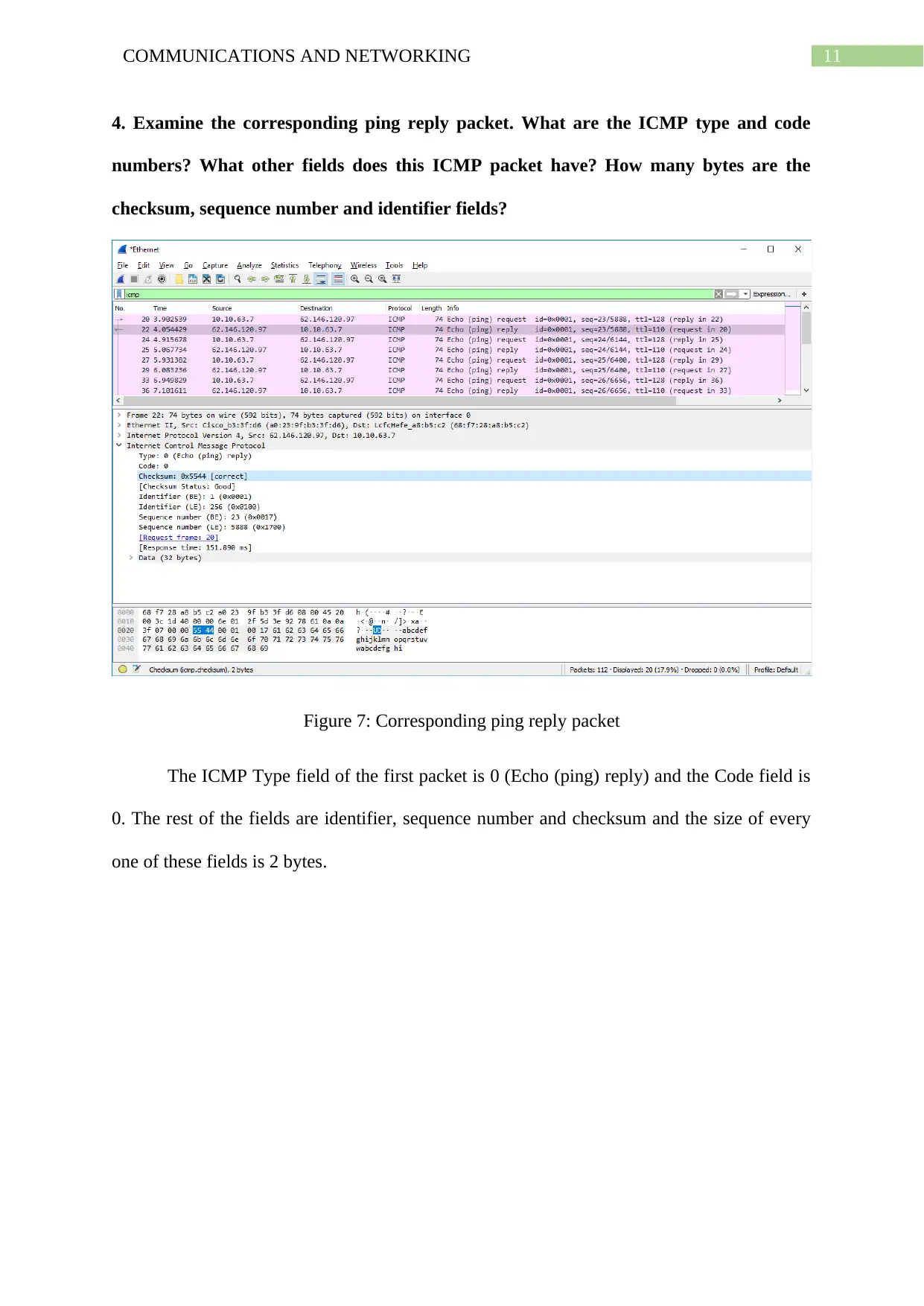
4. Examine the corresponding ping reply packet. What are the ICMP type and code
numbers? What other fields does this ICMP packet have? How many bytes are the
checksum, sequence number and identifier fields?
Figure 7: Corresponding ping reply packet
The ICMP Type field of the first packet is 0 (Echo (ping) reply) and the Code field is
0. The rest of the fields are identifier, sequence number and checksum and the size of every
one of these fields is 2 bytes.
4. Examine the corresponding ping reply packet. What are the ICMP type and code
numbers? What other fields does this ICMP packet have? How many bytes are the
checksum, sequence number and identifier fields?
Figure 7: Corresponding ping reply packet
The ICMP Type field of the first packet is 0 (Echo (ping) reply) and the Code field is
0. The rest of the fields are identifier, sequence number and checksum and the size of every
one of these fields is 2 bytes.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 46
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




