Comprehensive Risk Management: Analysis, Planning, and Implementation
VerifiedAdded on 2020/03/16
|11
|4857
|118
Report
AI Summary
This report provides a comprehensive overview of risk management within a business context. It begins by emphasizing the importance of identifying both present and future risks, followed by a detailed analysis to formulate effective solutions. The report outlines a structured risk management process, including planning for mitigation, implementing mitigation strategies, and continuous risk tracking. It highlights the significance of information security in protecting confidential data and ensuring the integrity of governance and management decisions. Various types of risks, such as systematic, unsystematic, credit, and market risks, are discussed, along with the crucial roles of governance bodies and management in risk analysis. The report further explores effective risk management protocols, including root cause analysis, proactive risk assessment, and the establishment of realistic program schedules and funding. It also covers the importance of information security, risk assessment classifications, and the identification of typical risk sources like threats, vulnerabilities, and requirements. Overall, the report provides a thorough guide to understanding and implementing robust risk management practices in business environments.

Executive Summary:
Initially the risk need to be identified, it could be either present risk or future risk. Once the risk is identified it
has to be analyzed to deliver the solutions. But to provide the solution the risk need to be properly planned for
the mitigation process. Soon after the planning the risk mitigation plan has to be implemented in a respective
environment. Risk tracking is required throughout the process till the solution has not been implemented as per
the plan. Information security is a policy which is typically involve in physical and digital measure to provide
security to the governing bodies and their decision. It is a good practice to prevent from the unauthorized access
and disclosure of the important data. As the decision taken by the governing bodies and the management are
confidential and it is very necessary to protect those data and involve the information security for the data.
Risk is a factor which decides the different types of uncertainties which are going to happen in future. The risk
may affect the routine goals and the objectives which are defined in the cost on performance constraints. It has
connected with different kinds of programs like threats, vulnerability, designing, and performance issues. The
Governance bodies and the management play a vital role for analysing the risk. Governance is a structure and
process which ensures the responsibility, simplicity, awareness for the different rule for the law, strength, equity
as well as the detail of the empowerment. Norms, values and the rules are being represented by governance.
Management is defined as the daily program with the execution of typical strategies, rules, and regulation, the
process, and procedures to execute the rules which should be designed by the governing bodies who are
concerned only with the right decision also the management is responsible for performing the right thing which
will execute and gives a right output.
Business applications are those which are used for keep the business running. Sometimes the critical
applications take a vital role for running the business. The critical business function may get interrupted by other
functionalities which may cause serious financial, legal, or other damages or penalties. The critical business
application requires a high-availability structural design that ensures that there should not have any breakdown
component such as a firewall, load balancer or database server will bring down the entire application
Introduction:
Risk is a factor which decides the different types of uncertainties which are going to happen in future. The risk
may affect the routine goals and the objectives which are defined in the cost on performance constraints. It has
connected with different kinds of programs like threats, vulnerability, designing, and performance issues.
Analysing the risk includes various approaches to protect the complete business system and provides valuable
solution towards to protective system. It has integrated with various effects and programs to create the
awareness for the expected risk for the individual systems as well as the organization.
A risk analysis has various components to achieve the goals.
Analysing the future risk and performing the RCA(Root Cause Analysis)
Determining the probability with a comparison between the present risk and the root cause analysis
with future risk.
Analysing the consequences of future risk.
Initially the risk need to be identified, it could be either present risk or future risk. Once the risk is identified it
has to be analyzed to deliver the solutions. But to provide the solution the risk need to be properly planned for
the mitigation process. Soon after the planning the risk mitigation plan has to be implemented in a respective
environment. Risk tracking is required throughout the process till the solution has not been implemented as per
the plan. Information security is a policy which is typically involve in physical and digital measure to provide
security to the governing bodies and their decision. It is a good practice to prevent from the unauthorized access
and disclosure of the important data. As the decision taken by the governing bodies and the management are
confidential and it is very necessary to protect those data and involve the information security for the data.
Risk is a factor which decides the different types of uncertainties which are going to happen in future. The risk
may affect the routine goals and the objectives which are defined in the cost on performance constraints. It has
connected with different kinds of programs like threats, vulnerability, designing, and performance issues. The
Governance bodies and the management play a vital role for analysing the risk. Governance is a structure and
process which ensures the responsibility, simplicity, awareness for the different rule for the law, strength, equity
as well as the detail of the empowerment. Norms, values and the rules are being represented by governance.
Management is defined as the daily program with the execution of typical strategies, rules, and regulation, the
process, and procedures to execute the rules which should be designed by the governing bodies who are
concerned only with the right decision also the management is responsible for performing the right thing which
will execute and gives a right output.
Business applications are those which are used for keep the business running. Sometimes the critical
applications take a vital role for running the business. The critical business function may get interrupted by other
functionalities which may cause serious financial, legal, or other damages or penalties. The critical business
application requires a high-availability structural design that ensures that there should not have any breakdown
component such as a firewall, load balancer or database server will bring down the entire application
Introduction:
Risk is a factor which decides the different types of uncertainties which are going to happen in future. The risk
may affect the routine goals and the objectives which are defined in the cost on performance constraints. It has
connected with different kinds of programs like threats, vulnerability, designing, and performance issues.
Analysing the risk includes various approaches to protect the complete business system and provides valuable
solution towards to protective system. It has integrated with various effects and programs to create the
awareness for the expected risk for the individual systems as well as the organization.
A risk analysis has various components to achieve the goals.
Analysing the future risk and performing the RCA(Root Cause Analysis)
Determining the probability with a comparison between the present risk and the root cause analysis
with future risk.
Analysing the consequences of future risk.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
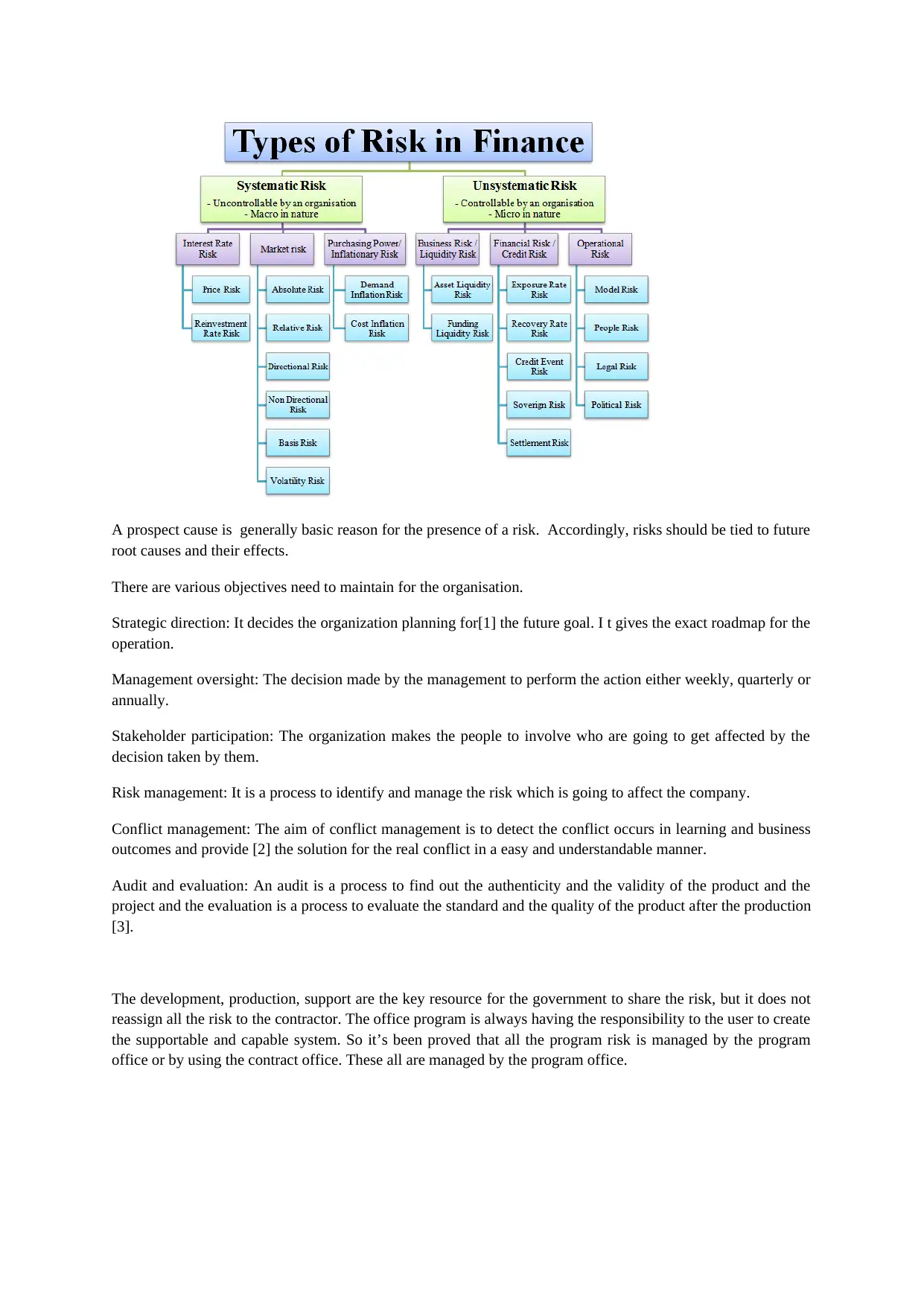
A prospect cause is generally basic reason for the presence of a risk. Accordingly, risks should be tied to future
root causes and their effects.
There are various objectives need to maintain for the organisation.
Strategic direction: It decides the organization planning for[1] the future goal. I t gives the exact roadmap for the
operation.
Management oversight: The decision made by the management to perform the action either weekly, quarterly or
annually.
Stakeholder participation: The organization makes the people to involve who are going to get affected by the
decision taken by them.
Risk management: It is a process to identify and manage the risk which is going to affect the company.
Conflict management: The aim of conflict management is to detect the conflict occurs in learning and business
outcomes and provide [2] the solution for the real conflict in a easy and understandable manner.
Audit and evaluation: An audit is a process to find out the authenticity and the validity of the product and the
project and the evaluation is a process to evaluate the standard and the quality of the product after the production
[3].
The development, production, support are the key resource for the government to share the risk, but it does not
reassign all the risk to the contractor. The office program is always having the responsibility to the user to create
the supportable and capable system. So it’s been proved that all the program risk is managed by the program
office or by using the contract office. These all are managed by the program office.
root causes and their effects.
There are various objectives need to maintain for the organisation.
Strategic direction: It decides the organization planning for[1] the future goal. I t gives the exact roadmap for the
operation.
Management oversight: The decision made by the management to perform the action either weekly, quarterly or
annually.
Stakeholder participation: The organization makes the people to involve who are going to get affected by the
decision taken by them.
Risk management: It is a process to identify and manage the risk which is going to affect the company.
Conflict management: The aim of conflict management is to detect the conflict occurs in learning and business
outcomes and provide [2] the solution for the real conflict in a easy and understandable manner.
Audit and evaluation: An audit is a process to find out the authenticity and the validity of the product and the
project and the evaluation is a process to evaluate the standard and the quality of the product after the production
[3].
The development, production, support are the key resource for the government to share the risk, but it does not
reassign all the risk to the contractor. The office program is always having the responsibility to the user to create
the supportable and capable system. So it’s been proved that all the program risk is managed by the program
office or by using the contract office. These all are managed by the program office.
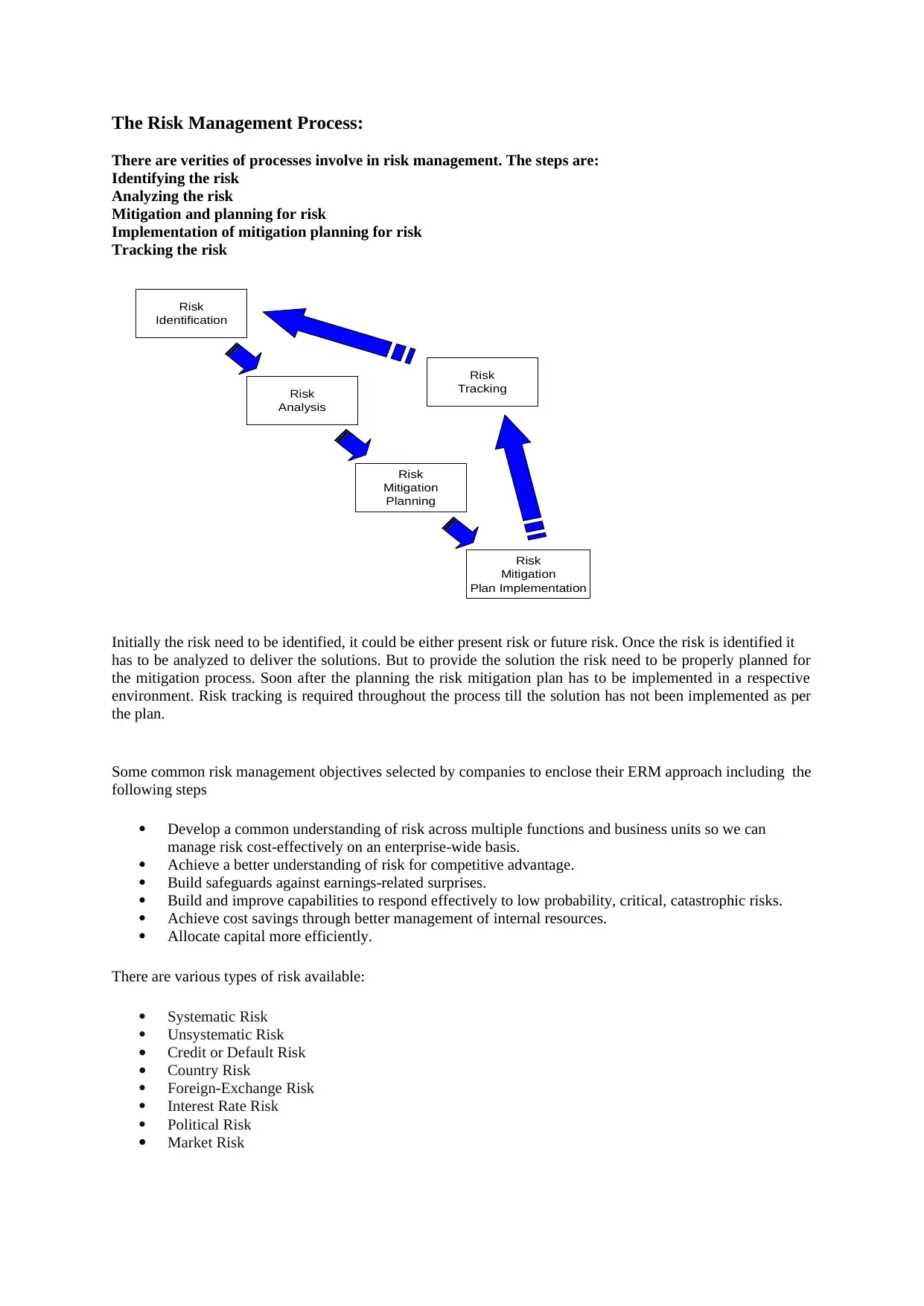
The Risk Management Process:
There are verities of processes involve in risk management. The steps are:
Identifying the risk
Analyzing the risk
Mitigation and planning for risk
Implementation of mitigation planning for risk
Tracking the risk
Initially the risk need to be identified, it could be either present risk or future risk. Once the risk is identified it
has to be analyzed to deliver the solutions. But to provide the solution the risk need to be properly planned for
the mitigation process. Soon after the planning the risk mitigation plan has to be implemented in a respective
environment. Risk tracking is required throughout the process till the solution has not been implemented as per
the plan.
Some common risk management objectives selected by companies to enclose their ERM approach including the
following steps
Develop a common understanding of risk across multiple functions and business units so we can
manage risk cost-effectively on an enterprise-wide basis.
Achieve a better understanding of risk for competitive advantage.
Build safeguards against earnings-related surprises.
Build and improve capabilities to respond effectively to low probability, critical, catastrophic risks.
Achieve cost savings through better management of internal resources.
Allocate capital more efficiently.
There are various types of risk available:
Systematic Risk
Unsystematic Risk
Credit or Default Risk
Country Risk
Foreign-Exchange Risk
Interest Rate Risk
Political Risk
Market Risk
Risk
Identification
Risk
Mitigation
Plan Implementation
Risk
Mitigation
Planning
Risk
Analysis
Risk
Tracking
There are verities of processes involve in risk management. The steps are:
Identifying the risk
Analyzing the risk
Mitigation and planning for risk
Implementation of mitigation planning for risk
Tracking the risk
Initially the risk need to be identified, it could be either present risk or future risk. Once the risk is identified it
has to be analyzed to deliver the solutions. But to provide the solution the risk need to be properly planned for
the mitigation process. Soon after the planning the risk mitigation plan has to be implemented in a respective
environment. Risk tracking is required throughout the process till the solution has not been implemented as per
the plan.
Some common risk management objectives selected by companies to enclose their ERM approach including the
following steps
Develop a common understanding of risk across multiple functions and business units so we can
manage risk cost-effectively on an enterprise-wide basis.
Achieve a better understanding of risk for competitive advantage.
Build safeguards against earnings-related surprises.
Build and improve capabilities to respond effectively to low probability, critical, catastrophic risks.
Achieve cost savings through better management of internal resources.
Allocate capital more efficiently.
There are various types of risk available:
Systematic Risk
Unsystematic Risk
Credit or Default Risk
Country Risk
Foreign-Exchange Risk
Interest Rate Risk
Political Risk
Market Risk
Risk
Identification
Risk
Mitigation
Plan Implementation
Risk
Mitigation
Planning
Risk
Analysis
Risk
Tracking
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

The systematic risk occurs in a specific situation which can be predict and analyse in a regular interval. Whereas
unsystematic risk is not in a regular manner. Default risk occurs in some default situation which can be easily
measurable and it is easy to protect the system by applying certain rules and regulation. Foreign risk, political
risk and the market risk are depending upon the economical condition of the organization which can be managed
through the calculation conducted by the auditor of the organization by keeping the annual capital value of the
organization.
The Governance bodies and the management play a vital role for analysing the risk. Governance is a structure
and process which ensures the responsibility, simplicity, awareness for the different rule for the law, strength,
equity as well as the detail of the empowerment. Norms, values and the rules are being represented by
governance. Using the different rules and regulation the public affairs are managed in a clean, broad and easy to
understand manner. The governance can be delicate but it cannot be easily noticeable. In another way where the
citizen and the stakeholders are communicating and also making themselves involved in different types of
public affairs are known as governance. It is an important part of the body of government.
Management is defined as the daily program with the execution of typical strategies, rules, and regulation, the
process, and procedures to execute the rules which should be designed by the governing bodies who are
concerned only with the right decision also the management is responsible for performing the right thing which
will execute and gives a right output.
The governing bodies of GRPPs typically exercise six core functions:
Strategic direction: It decides the organization planning for[1] the future goal. I t gives the exact roadmap for the
operation.
Management oversight: The decision made by the management to perform the action either weekly, quarterly or
annually.
Stakeholder participation: The organization makes the people to involve who are going to get affected by the
decision taken by them.
Risk management: It is a process to identify and manage the risk which is going to affect the company.
Conflict management: The aim of conflict management is to detect the conflict occurs in learning and business
outcomes and provide [2] the solution for the real conflict in a easy and understandable manner.
Audit and evaluation: An audit is a process to find out the authenticity and the validity of the product and the
project and the evaluation is a process to evaluate the standard and the quality of the product after the production
[3].
Effective Risk Management:
There are various protocols we need to follow for an effective risk management.
1. Performing a root cause analysis and store the methods in knowledge base line.
2. Analyse the risk as early as possible and apply the rules created by the management.
3. Perform the entire test evaluate the risk using different simulation and modelling techniques.
4. Industry participation risk needs to be included and the roadmap needs to be clearly defined
for the system.
5. Proactive, structured risk assessment and analysis activity should be conducted to identify and
analyze root causes.
6. Technical review of the assessment has to be established periodically to reduce the risk.
7. Establish a realistic schedule and funding baseline for the program as early as possible in the
program, incorporating not only an acceptable level of risk, but adequate schedule and funding
margins.
8. An evaluation criterion needs to be clearly defined for the organization to mention whether the
risk is low, moderate or high.
Information security is a policy which is typically involve in physical and digital measure to provide security to
the governing bodies and their decision. It is a good practice to prevent from the unauthorized access and
disclosure of the important data. As the decision taken by the governing bodies and the management are
confidential and it is very necessary to protect those data and involve the information security for the data.
unsystematic risk is not in a regular manner. Default risk occurs in some default situation which can be easily
measurable and it is easy to protect the system by applying certain rules and regulation. Foreign risk, political
risk and the market risk are depending upon the economical condition of the organization which can be managed
through the calculation conducted by the auditor of the organization by keeping the annual capital value of the
organization.
The Governance bodies and the management play a vital role for analysing the risk. Governance is a structure
and process which ensures the responsibility, simplicity, awareness for the different rule for the law, strength,
equity as well as the detail of the empowerment. Norms, values and the rules are being represented by
governance. Using the different rules and regulation the public affairs are managed in a clean, broad and easy to
understand manner. The governance can be delicate but it cannot be easily noticeable. In another way where the
citizen and the stakeholders are communicating and also making themselves involved in different types of
public affairs are known as governance. It is an important part of the body of government.
Management is defined as the daily program with the execution of typical strategies, rules, and regulation, the
process, and procedures to execute the rules which should be designed by the governing bodies who are
concerned only with the right decision also the management is responsible for performing the right thing which
will execute and gives a right output.
The governing bodies of GRPPs typically exercise six core functions:
Strategic direction: It decides the organization planning for[1] the future goal. I t gives the exact roadmap for the
operation.
Management oversight: The decision made by the management to perform the action either weekly, quarterly or
annually.
Stakeholder participation: The organization makes the people to involve who are going to get affected by the
decision taken by them.
Risk management: It is a process to identify and manage the risk which is going to affect the company.
Conflict management: The aim of conflict management is to detect the conflict occurs in learning and business
outcomes and provide [2] the solution for the real conflict in a easy and understandable manner.
Audit and evaluation: An audit is a process to find out the authenticity and the validity of the product and the
project and the evaluation is a process to evaluate the standard and the quality of the product after the production
[3].
Effective Risk Management:
There are various protocols we need to follow for an effective risk management.
1. Performing a root cause analysis and store the methods in knowledge base line.
2. Analyse the risk as early as possible and apply the rules created by the management.
3. Perform the entire test evaluate the risk using different simulation and modelling techniques.
4. Industry participation risk needs to be included and the roadmap needs to be clearly defined
for the system.
5. Proactive, structured risk assessment and analysis activity should be conducted to identify and
analyze root causes.
6. Technical review of the assessment has to be established periodically to reduce the risk.
7. Establish a realistic schedule and funding baseline for the program as early as possible in the
program, incorporating not only an acceptable level of risk, but adequate schedule and funding
margins.
8. An evaluation criterion needs to be clearly defined for the organization to mention whether the
risk is low, moderate or high.
Information security is a policy which is typically involve in physical and digital measure to provide security to
the governing bodies and their decision. It is a good practice to prevent from the unauthorized access and
disclosure of the important data. As the decision taken by the governing bodies and the management are
confidential and it is very necessary to protect those data and involve the information security for the data.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Purpose for Risk Assessment:
There is certain classification through which the risk assessment needs to be performed.
Observing at recent and projected staffing, process, design, supplier, operational employment,
resources, dependencies, etc.,
Monitoring test results especially test failures.
Reviewing potential shortfalls against expectations.
Analyzing negative trends.
Typical risk sources include:
Threat, is the sensitiveness of the program to describe the uncertainty of the degree to which the
system would have to change the design pattern. The vulnerability also describes the collection of
the foreign intelligence effort which needs to be programmes.
Requirements are the understanding of the program to indecision in the system description and
requirements, excluding those caused by threat uncertainty. Requirements include operational needs,
attributes, performance and readiness parameters (including KPPs), constraints, technology, design
processes, and WBS elements.
Technical Baseline is the ability of the system configuration to achieve the program's engineering
objectives based on the available technology, design tools, design maturity, etc. Program
uncertainties and the processes associated with the “ilities” (reliability, supportability,
maintainability, etc.) must be considered. The system arrangement is an agreed-to description (an
approved and released document or a set of documents) of the attributes of a product, at a point in
time, which serves as a basis for defining change.
Test and Evaluation. The adequacy and capability of the test and evaluation program to assess
attainment of significant performance specifications and determine whether the system is
operationally effective, operationally suitable, and interoperable.
Modeling and Simulation (M&S). The adequacy and capability of M&S to support all life-cycle
phases of a program using verified, validated, and accredited models and simulations.
Technology. The degree to which the technology proposed for the program has demonstrated
sufficient maturity to be realistically capable of meeting all of the program's objectives.
Logistics. The ability of the system configuration and associated documentation to achieve the
program's logistics objectives based on the system design, maintenance concept, support system
design, and availability of support data and resources.
Production/Facilities. The ability of the system configuration to achieve the program's production
objectives based on the system design, manufacturing processes chosen, and availability of
manufacturing resources (repair resources in the sustainment phase).
Concurrency. The sensitivity of the program to uncertainty resulting from the combining or
overlapping of life-cycle phases or activities.
Industrial Capabilities. The abilities, experience, resources, and knowledge of the contractors to
design, develop, manufacture, and support the system.
Cost. The ability of the system to achieve the program's life-cycle support objectives. This includes
the effects of budget and affordability decisions and the effects of inherent errors in the cost
estimating technique(s) used (given that the technical requirements were properly defined and taking
into account known and unknown program information).
Management. The degree to which program plans and strategies exist and are realistic and
consistent. The government’s acquisition and support team should be qualified and sufficiently
staffed to manage the program.
Schedule. The sufficiency of the time allocated for performing the defined acquisition tasks. This
factor includes the effects of programmatic schedule decisions, the inherent errors in schedule
estimating, and external physical constraints.
External Factors. The availability of government resources external to the program office that are
required to support the program such as facilities, resources, personnel, government furnished
equipment, etc.
Budget. The sensitivity of the program to budget variations and reductions and the resultant program
turbulence.
Earned Value Management System. The adequacy of the contractor’s EVM process and the realism
of the integrated baseline for managing the program.
There is certain classification through which the risk assessment needs to be performed.
Observing at recent and projected staffing, process, design, supplier, operational employment,
resources, dependencies, etc.,
Monitoring test results especially test failures.
Reviewing potential shortfalls against expectations.
Analyzing negative trends.
Typical risk sources include:
Threat, is the sensitiveness of the program to describe the uncertainty of the degree to which the
system would have to change the design pattern. The vulnerability also describes the collection of
the foreign intelligence effort which needs to be programmes.
Requirements are the understanding of the program to indecision in the system description and
requirements, excluding those caused by threat uncertainty. Requirements include operational needs,
attributes, performance and readiness parameters (including KPPs), constraints, technology, design
processes, and WBS elements.
Technical Baseline is the ability of the system configuration to achieve the program's engineering
objectives based on the available technology, design tools, design maturity, etc. Program
uncertainties and the processes associated with the “ilities” (reliability, supportability,
maintainability, etc.) must be considered. The system arrangement is an agreed-to description (an
approved and released document or a set of documents) of the attributes of a product, at a point in
time, which serves as a basis for defining change.
Test and Evaluation. The adequacy and capability of the test and evaluation program to assess
attainment of significant performance specifications and determine whether the system is
operationally effective, operationally suitable, and interoperable.
Modeling and Simulation (M&S). The adequacy and capability of M&S to support all life-cycle
phases of a program using verified, validated, and accredited models and simulations.
Technology. The degree to which the technology proposed for the program has demonstrated
sufficient maturity to be realistically capable of meeting all of the program's objectives.
Logistics. The ability of the system configuration and associated documentation to achieve the
program's logistics objectives based on the system design, maintenance concept, support system
design, and availability of support data and resources.
Production/Facilities. The ability of the system configuration to achieve the program's production
objectives based on the system design, manufacturing processes chosen, and availability of
manufacturing resources (repair resources in the sustainment phase).
Concurrency. The sensitivity of the program to uncertainty resulting from the combining or
overlapping of life-cycle phases or activities.
Industrial Capabilities. The abilities, experience, resources, and knowledge of the contractors to
design, develop, manufacture, and support the system.
Cost. The ability of the system to achieve the program's life-cycle support objectives. This includes
the effects of budget and affordability decisions and the effects of inherent errors in the cost
estimating technique(s) used (given that the technical requirements were properly defined and taking
into account known and unknown program information).
Management. The degree to which program plans and strategies exist and are realistic and
consistent. The government’s acquisition and support team should be qualified and sufficiently
staffed to manage the program.
Schedule. The sufficiency of the time allocated for performing the defined acquisition tasks. This
factor includes the effects of programmatic schedule decisions, the inherent errors in schedule
estimating, and external physical constraints.
External Factors. The availability of government resources external to the program office that are
required to support the program such as facilities, resources, personnel, government furnished
equipment, etc.
Budget. The sensitivity of the program to budget variations and reductions and the resultant program
turbulence.
Earned Value Management System. The adequacy of the contractor’s EVM process and the realism
of the integrated baseline for managing the program.

Different IT Key Functionality:
Network, desktop management and application development plays a vital role for risk management. Network is
a collection of more than one computer connected with each other for transmitting the data among themselves.
There are various key features through which the risk can be handled with low cost and high reliability.
1. Maintaining the active directory for the network device.
2. Maintaining and monitoring the network automatically.
3. Patch management for a secure, compliant network.
4. Robust, flexible reporting tools.
5. Mobile device management.
6. Web protection against malware, phishing, proxies, spyware, adware and spam.
Role of IPV6:
IPV6 is otherwise known as internet protocol version 6. It supports auto-configuration of network packets and
datasets.
IPV6 includes special features like:
Source and destination addresses having 128 bits (16 bytes) long.
Provides IPSec support.
Contains Flow Label field to identify packet flow for quality of service managing by router.
It allows the host to send the fragments packets.
It doesn't include a checksum in the header.
IPV6 use a link-local scope all-nodes multicast address.
Does not require manual configuration or DHCP.
Uses host address (AAAA) resource records in DNS to map host names to IPv6 addresses.
Uses pointer (PTR) resource records in the IP6.ARPA DNS domain to map IPv6 addresses to host names.
Supports a 1280-byte packet size (without fragmentation).
Moves optional data to IPv6 extension headers.
IPV6 has Multicast Neighbor Solicitation messages to resolve IP addresses to link-layer addresses.
Uses Multicast Listener Discovery (MLD) messages to manage membership in local subnet groups.
Uses ICMPv6 Router Solicitation and Router Advertisement messages to determine the IP address of the
best default gateway.
Advantages:
1. IPV6 has increased the size and range of the packets.
2. It provides efficient routing techniques.
Network, desktop management and application development plays a vital role for risk management. Network is
a collection of more than one computer connected with each other for transmitting the data among themselves.
There are various key features through which the risk can be handled with low cost and high reliability.
1. Maintaining the active directory for the network device.
2. Maintaining and monitoring the network automatically.
3. Patch management for a secure, compliant network.
4. Robust, flexible reporting tools.
5. Mobile device management.
6. Web protection against malware, phishing, proxies, spyware, adware and spam.
Role of IPV6:
IPV6 is otherwise known as internet protocol version 6. It supports auto-configuration of network packets and
datasets.
IPV6 includes special features like:
Source and destination addresses having 128 bits (16 bytes) long.
Provides IPSec support.
Contains Flow Label field to identify packet flow for quality of service managing by router.
It allows the host to send the fragments packets.
It doesn't include a checksum in the header.
IPV6 use a link-local scope all-nodes multicast address.
Does not require manual configuration or DHCP.
Uses host address (AAAA) resource records in DNS to map host names to IPv6 addresses.
Uses pointer (PTR) resource records in the IP6.ARPA DNS domain to map IPv6 addresses to host names.
Supports a 1280-byte packet size (without fragmentation).
Moves optional data to IPv6 extension headers.
IPV6 has Multicast Neighbor Solicitation messages to resolve IP addresses to link-layer addresses.
Uses Multicast Listener Discovery (MLD) messages to manage membership in local subnet groups.
Uses ICMPv6 Router Solicitation and Router Advertisement messages to determine the IP address of the
best default gateway.
Advantages:
1. IPV6 has increased the size and range of the packets.
2. It provides efficient routing techniques.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3. It supports new services.
4. High Security
5. Packet processing is more effective.
Evaluatation IT security risks:
It is more important to evaluate the assets, risk, threats, and vulnerabilities. Risk Assessment feature to check
discovered computers for a wide range of potential issues and generate a report of findings. The assessment
report can help you determine the overall risk level across computers in your organization and specific areas
where you have the most exposure. The report also highlights steps you can take to reduce risk and improve
security, compliance, and operational efficiency.
The results of each assessment you run are stored in the Direct Manage Deployment Manager database, so you
have a historical record of activity and an archive of past assessment results.
With Deployment Manager, there are four simple steps to complete the security assessment:
1. Identify the computers to evaluate.
You can specify how to find the remote computers you want to evaluate, for example, by specifying a local
subnet or range of IP addresses of interest.
2. Download the assessment tools software.
The assessment tools software package contains the platform-specific surveyor program for the computers you
want to evaluate.
3. Start the assessment on remote computers.
The surveyor program runs on the computers you have selected for evaluation and checks for a wide range of
potential issues that you might want to address to improve security in your organization.
4Generate the identity risk assessment report.
Migrating Business Critical Application:
Business applications are those which are used for keep the business running. Sometimes the critical
applications take a vital role for running the business. The critical business function may get interrupted by other
4. High Security
5. Packet processing is more effective.
Evaluatation IT security risks:
It is more important to evaluate the assets, risk, threats, and vulnerabilities. Risk Assessment feature to check
discovered computers for a wide range of potential issues and generate a report of findings. The assessment
report can help you determine the overall risk level across computers in your organization and specific areas
where you have the most exposure. The report also highlights steps you can take to reduce risk and improve
security, compliance, and operational efficiency.
The results of each assessment you run are stored in the Direct Manage Deployment Manager database, so you
have a historical record of activity and an archive of past assessment results.
With Deployment Manager, there are four simple steps to complete the security assessment:
1. Identify the computers to evaluate.
You can specify how to find the remote computers you want to evaluate, for example, by specifying a local
subnet or range of IP addresses of interest.
2. Download the assessment tools software.
The assessment tools software package contains the platform-specific surveyor program for the computers you
want to evaluate.
3. Start the assessment on remote computers.
The surveyor program runs on the computers you have selected for evaluation and checks for a wide range of
potential issues that you might want to address to improve security in your organization.
4Generate the identity risk assessment report.
Migrating Business Critical Application:
Business applications are those which are used for keep the business running. Sometimes the critical
applications take a vital role for running the business. The critical business function may get interrupted by other
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

functionalities which may cause serious financial, legal, or other damages or penalties. The critical business
application requires a high-availability structural design that ensures that there should not have any breakdown
component such as a firewall, load balancer or database server will bring down the entire application. Also,
business-critical applications need a recovery potential so that the application can be speedily transitioned to
another data centre. If something wrong happens to the primary data centre, it will become a great challenge for
each module of the critical application.
The business critical application needs a high security to protect them from the hackers and also from other bad
resources. If some application goes down due to some hardware failure, or some service attacks the availability
and the capability will get increase gradually. Finally, all these added capabilities, availability, recovery and
security – need experts to be available 24×7 to manage these systems.
Disaster Recovery planning, are unfortunately when we spoke to some cloud vendors they were not
able to satisfy our need using our existing tools. For some, if we switched to Zerto we could do this.
Others, they supported esoteric backup solutions that I had never heard of in context of 100% virtual
environments. The ones that claim to have Veeam support, really did not have effective support, they
were just a repository with no means to run the workloads or are not ready for usage. Due to these
limitations, this option was closed to us, however, I still think it is the best option if you have the time
to put it together. Our problem, was we had a shrinking time schedule based on outside influences that
required us to attempt to use what we have.
As part of vCloud Director or Connector, unfortunately we did not have our virtual machines within a
vCloud yet, they were just a standard 100% virtual environment running vSphere. While we could have
migrated our data via convert to OVA, import, etc. from our backups, we did not find a vCloud vendor
that was priced properly. This is one of the more expensive options and would require us to setup
vCloud Connector, migrate our VMs into vCloud to use effectively. Since we did not have this setup
yet, we had to go with what we had.
Setup brand new virtual machines and migrate over the applications and data. This option was initially
unattractive due to the work implicated, the lack of automation, and the lack of scripts to setup our
applications on the other side. However, this option would permit you to unite the workloads and run
them one by one until the final cut over date. However, when we went this route, requires intimate
knowledge of your data, what data is changing, what data is static, what data is critical to move and the
mechanisms to move the data. All these need to be known before you head down this path. What made
this path attractive was the recent update we did of our business critical email services. We had the
techniques, used them recently and it all worked as expected. Experience won out, but we did not script
everything previously.
There are numerous financial and operational reasons to make the move to a private, public or hybrid cloud, but
you must understand the impact on applications as we’re in an application-driven business environment. If a
critical application is down or performing at a non-peak level, the business will suffer. At a technical level, it’s
understanding that most firewall changes are driven by business application connectivity needs and
understanding the impact to these applications and to the network by making sure that you can associate all
firewall change requests to the appropriate application.
Consider the Risk of Decommissioned Applications
When decommissioning applications or servers in the data center, many IT professionals have to manually
identify firewall rules to change and if left in place, many unnecessary access rules are left creating security risk.
Oftentimes, organizations simply leave those access rules in place because they don’t have the comfort level to
remove those rules for fear of causing an outage. While you certainly don’t want to break the connectivity for a
critical application, you also should have a plan to remove that unneeded access because more access leaves
gaps for bad guys to exploit. Use your firewall rules (hopefully there is decent firewall rule documentation) to
identify network components and applications that may be related to effectively remove unneeded access,
without impacting the business.
Prioritize Network Vulnerabilities the Way You Want
application requires a high-availability structural design that ensures that there should not have any breakdown
component such as a firewall, load balancer or database server will bring down the entire application. Also,
business-critical applications need a recovery potential so that the application can be speedily transitioned to
another data centre. If something wrong happens to the primary data centre, it will become a great challenge for
each module of the critical application.
The business critical application needs a high security to protect them from the hackers and also from other bad
resources. If some application goes down due to some hardware failure, or some service attacks the availability
and the capability will get increase gradually. Finally, all these added capabilities, availability, recovery and
security – need experts to be available 24×7 to manage these systems.
Disaster Recovery planning, are unfortunately when we spoke to some cloud vendors they were not
able to satisfy our need using our existing tools. For some, if we switched to Zerto we could do this.
Others, they supported esoteric backup solutions that I had never heard of in context of 100% virtual
environments. The ones that claim to have Veeam support, really did not have effective support, they
were just a repository with no means to run the workloads or are not ready for usage. Due to these
limitations, this option was closed to us, however, I still think it is the best option if you have the time
to put it together. Our problem, was we had a shrinking time schedule based on outside influences that
required us to attempt to use what we have.
As part of vCloud Director or Connector, unfortunately we did not have our virtual machines within a
vCloud yet, they were just a standard 100% virtual environment running vSphere. While we could have
migrated our data via convert to OVA, import, etc. from our backups, we did not find a vCloud vendor
that was priced properly. This is one of the more expensive options and would require us to setup
vCloud Connector, migrate our VMs into vCloud to use effectively. Since we did not have this setup
yet, we had to go with what we had.
Setup brand new virtual machines and migrate over the applications and data. This option was initially
unattractive due to the work implicated, the lack of automation, and the lack of scripts to setup our
applications on the other side. However, this option would permit you to unite the workloads and run
them one by one until the final cut over date. However, when we went this route, requires intimate
knowledge of your data, what data is changing, what data is static, what data is critical to move and the
mechanisms to move the data. All these need to be known before you head down this path. What made
this path attractive was the recent update we did of our business critical email services. We had the
techniques, used them recently and it all worked as expected. Experience won out, but we did not script
everything previously.
There are numerous financial and operational reasons to make the move to a private, public or hybrid cloud, but
you must understand the impact on applications as we’re in an application-driven business environment. If a
critical application is down or performing at a non-peak level, the business will suffer. At a technical level, it’s
understanding that most firewall changes are driven by business application connectivity needs and
understanding the impact to these applications and to the network by making sure that you can associate all
firewall change requests to the appropriate application.
Consider the Risk of Decommissioned Applications
When decommissioning applications or servers in the data center, many IT professionals have to manually
identify firewall rules to change and if left in place, many unnecessary access rules are left creating security risk.
Oftentimes, organizations simply leave those access rules in place because they don’t have the comfort level to
remove those rules for fear of causing an outage. While you certainly don’t want to break the connectivity for a
critical application, you also should have a plan to remove that unneeded access because more access leaves
gaps for bad guys to exploit. Use your firewall rules (hopefully there is decent firewall rule documentation) to
identify network components and applications that may be related to effectively remove unneeded access,
without impacting the business.
Prioritize Network Vulnerabilities the Way You Want

Organizations want to prioritize network vulnerabilities by business application. Nearly half of respondents in
the survey wanted to view risk by the business application. With this type of visibility, security teams can more
effectively communicate with business owners and enable them to “own the risk”.
Reduce Complexity
Complexity is a killer of security and agility. Today’s enterprise network has more business applications with
complex, multi-tier architectures, multiple components, and intricate, underlying communication patterns that
are driving network security policies. An individual “communication” may need to cross several policy
enforcement points, while individual rules, in turn, support multiple distinct applications. This complexity
typically involves hundreds, or even thousands of rules, with many potential interdependencies, configured
across tens to hundreds of devices, which equally supports as many business-critical applications. The sheer
complexity of any given network can lead to a lot of mistakes, especially when it comes to multiple firewalls
with complex rule sets. Simplifying security management processes through automation and an application-
centric approach is a must.
These are just a few security management considerations to take in while you continue in your plans to move
critical business applications to the cloud. There are many valid reasons for moving to the cloud, but you must
remember the implications of poor security management and how improvements here can not only ensure
tighter security, but also a data centre that is more agile and supportive of the business.
A decade ago, only Enterprise businesses could declare that software applications were business-critical to
them, in that IT system failure would directly result in loss of revenue and profits. Recognising the business risk
and their dependence on IT, the majority spent vast sums on implementing fault tolerant solutions, including
disaster recovery to manage the risk of catastrophic Data Centre failure.
Meanwhile, the majority of mid-market companies employed software solutions on a piecemeal basis
to improve efficiency and gain a better understanding of business performance. However, manual processes
could always prevail if IT systems fell over. It was rare that a midmarket business had implemented and
genuinely relied on a business-critical application.
Fast-forward to the present day where application costs have decreased, whilst functionality has
increased tenfold, and those companies who relied on manual process when systems broke down find
themselves in a new era – just like Enterprise organisations before them – IT systems have become intrinsic to
their existence with the majority of business functions heavily reliant on them.
Crucially, if business-critical systems fail, mid-market companies’ revenue and profits are adversely affected
and manual processes are no longer able to provide a credible safety net.
Whilst Enterprise organisations have always aligned the support and management of critical applications
with business risk, many mid-market companies do not recognise the risk and are left vulnerable and
hurting when systems fail.
Conclusion:
Risk is a factor which decides the different types of uncertainties which are going to happen in future. The risk
may affect the routine goals and the objectives which are defined in the cost on performance constraints. It has
connected with different kinds of programs like threats, vulnerability, designing, and performance issues.
Analysing the risk includes various approaches to protect the complete business system and provides valuable
solution towards to protective system. It has integrated with various effects and programs to create the
awareness for the expected risk for the individual systems as well as the organization.
The governance and the management are not unbendable in accordance with the limit between them. Exactly in
the program both the maturity and the size can perform the manipulation. The manipulation intern gives the
result about the separation between the structure of the management and the governance. The programs having
the survey wanted to view risk by the business application. With this type of visibility, security teams can more
effectively communicate with business owners and enable them to “own the risk”.
Reduce Complexity
Complexity is a killer of security and agility. Today’s enterprise network has more business applications with
complex, multi-tier architectures, multiple components, and intricate, underlying communication patterns that
are driving network security policies. An individual “communication” may need to cross several policy
enforcement points, while individual rules, in turn, support multiple distinct applications. This complexity
typically involves hundreds, or even thousands of rules, with many potential interdependencies, configured
across tens to hundreds of devices, which equally supports as many business-critical applications. The sheer
complexity of any given network can lead to a lot of mistakes, especially when it comes to multiple firewalls
with complex rule sets. Simplifying security management processes through automation and an application-
centric approach is a must.
These are just a few security management considerations to take in while you continue in your plans to move
critical business applications to the cloud. There are many valid reasons for moving to the cloud, but you must
remember the implications of poor security management and how improvements here can not only ensure
tighter security, but also a data centre that is more agile and supportive of the business.
A decade ago, only Enterprise businesses could declare that software applications were business-critical to
them, in that IT system failure would directly result in loss of revenue and profits. Recognising the business risk
and their dependence on IT, the majority spent vast sums on implementing fault tolerant solutions, including
disaster recovery to manage the risk of catastrophic Data Centre failure.
Meanwhile, the majority of mid-market companies employed software solutions on a piecemeal basis
to improve efficiency and gain a better understanding of business performance. However, manual processes
could always prevail if IT systems fell over. It was rare that a midmarket business had implemented and
genuinely relied on a business-critical application.
Fast-forward to the present day where application costs have decreased, whilst functionality has
increased tenfold, and those companies who relied on manual process when systems broke down find
themselves in a new era – just like Enterprise organisations before them – IT systems have become intrinsic to
their existence with the majority of business functions heavily reliant on them.
Crucially, if business-critical systems fail, mid-market companies’ revenue and profits are adversely affected
and manual processes are no longer able to provide a credible safety net.
Whilst Enterprise organisations have always aligned the support and management of critical applications
with business risk, many mid-market companies do not recognise the risk and are left vulnerable and
hurting when systems fail.
Conclusion:
Risk is a factor which decides the different types of uncertainties which are going to happen in future. The risk
may affect the routine goals and the objectives which are defined in the cost on performance constraints. It has
connected with different kinds of programs like threats, vulnerability, designing, and performance issues.
Analysing the risk includes various approaches to protect the complete business system and provides valuable
solution towards to protective system. It has integrated with various effects and programs to create the
awareness for the expected risk for the individual systems as well as the organization.
The governance and the management are not unbendable in accordance with the limit between them. Exactly in
the program both the maturity and the size can perform the manipulation. The manipulation intern gives the
result about the separation between the structure of the management and the governance. The programs having
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

low maturity level will take some time to create a formal mechanism. The programs having small in size may
tend to have a higher responsibility in staffing and financial resources. Those programs can manage the
governing bodies and are moreover involved in taking management decision in a daily basis.
The activity of executing the risk mitigation plan to ensure successful risk mitigation occurs. It determines what
planning, budget, and requirements and contractual changes are needed, provides a coordination vehicle with
management and other stakeholders, directs the teams to execute the defined and approved risk mitigation plans,
outlines the risk reporting requirements for on-going monitoring, and documents the change history.
References:
1. https://www.careersinaudit.com/article/the-importance-of-risk-management-in-an-
organisation/
2. http://businessfinancemag.com/business-performance-management/risk-strategic-
planning-process
3. www.diffen.com/difference/Audit_vs_Evaluation
4. http://www.latrobe.edu.au/about/governance/committees/induction-toolkit/decision-
making-bodies
5. http://www.innovationgame.com/invgame/srpaper.htm
6. https://www2.deloitte.com/content/dam/Deloitte/global/Documents/Governance-Risk-
Compliance/dttl-grc-exploring-strategic-risk.pdf
7. https://www.careersinaudit.com/article/the-importance-of-risk-management-in-an-
organisation/
8. http://businessfinancemag.com/business-performance-management/risk-strategic-
planning-process
9. HarborResearch:
http://ww1.prweb.com/prfiles/2007/02/08/503838/HRINewVenueChart.jpg
10. . IHS, Industrial Internet of Things, 2013 and 2014
11. Sierra Monitor QuickServer Field Server
tend to have a higher responsibility in staffing and financial resources. Those programs can manage the
governing bodies and are moreover involved in taking management decision in a daily basis.
The activity of executing the risk mitigation plan to ensure successful risk mitigation occurs. It determines what
planning, budget, and requirements and contractual changes are needed, provides a coordination vehicle with
management and other stakeholders, directs the teams to execute the defined and approved risk mitigation plans,
outlines the risk reporting requirements for on-going monitoring, and documents the change history.
References:
1. https://www.careersinaudit.com/article/the-importance-of-risk-management-in-an-
organisation/
2. http://businessfinancemag.com/business-performance-management/risk-strategic-
planning-process
3. www.diffen.com/difference/Audit_vs_Evaluation
4. http://www.latrobe.edu.au/about/governance/committees/induction-toolkit/decision-
making-bodies
5. http://www.innovationgame.com/invgame/srpaper.htm
6. https://www2.deloitte.com/content/dam/Deloitte/global/Documents/Governance-Risk-
Compliance/dttl-grc-exploring-strategic-risk.pdf
7. https://www.careersinaudit.com/article/the-importance-of-risk-management-in-an-
organisation/
8. http://businessfinancemag.com/business-performance-management/risk-strategic-
planning-process
9. HarborResearch:
http://ww1.prweb.com/prfiles/2007/02/08/503838/HRINewVenueChart.jpg
10. . IHS, Industrial Internet of Things, 2013 and 2014
11. Sierra Monitor QuickServer Field Server
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





